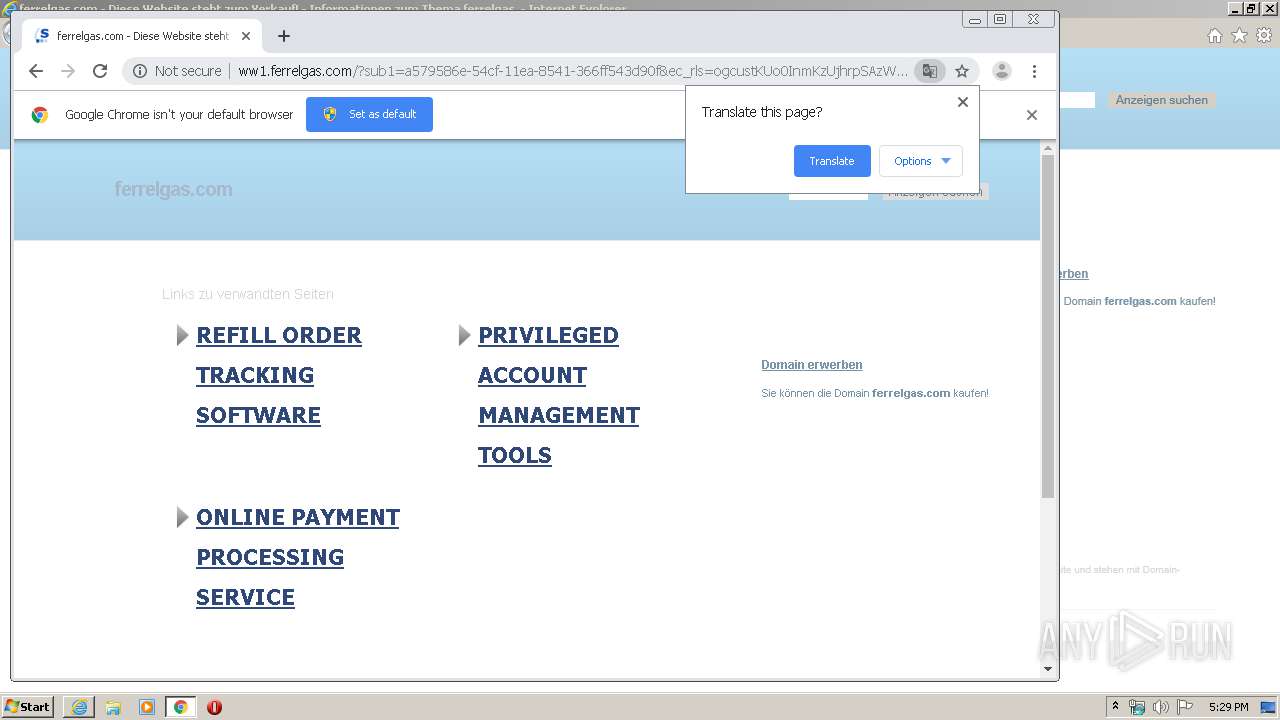
| URL: | http://ferrelgas.com |
| Full analysis: | https://app.any.run/tasks/9eb2bffe-b25c-4f58-802b-0e90d812e8e1 |
| Verdict: | Malicious activity |
| Analysis date: | February 21, 2020, 17:28:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 7CFBEE88F859A4E9BF3CD7B089AD6021 |
| SHA1: | 8A53B87FBA9515EE78AC59442D3D94C29676BF7B |
| SHA256: | CBD5A23CA380D9EB1953A4D6FF8A4BFD5348B4DABDE83E40A6A58378C6026B8F |
| SSDEEP: | 3:N1KYnKIn:CYTn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 2192)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 3172)
- iexplore.exe (PID: 3148)
Changes internet zones settings
- iexplore.exe (PID: 3172)
Creates files in the user directory
- iexplore.exe (PID: 3148)
- iexplore.exe (PID: 3172)
Reads internet explorer settings
- iexplore.exe (PID: 3148)
Manual execution by user
- chrome.exe (PID: 2192)
Reads the hosts file
- chrome.exe (PID: 1232)
- chrome.exe (PID: 2192)
Application launched itself
- chrome.exe (PID: 2192)
Reads settings of System Certificates
- iexplore.exe (PID: 3172)
- iexplore.exe (PID: 3148)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3172)
Changes settings of System certificates
- iexplore.exe (PID: 3172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
70
Monitored processes
34
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 348 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3952 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,2281785545762161517,14815996722198865169,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=17510949707045437274 --mojo-platform-channel-handle=1564 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1544 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,2281785545762161517,14815996722198865169,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=4079210740740494386 --mojo-platform-channel-handle=4484 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1720 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,2281785545762161517,14815996722198865169,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=7972209804558304818 --mojo-platform-channel-handle=3392 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1840 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,2281785545762161517,14815996722198865169,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=18189669188778052181 --mojo-platform-channel-handle=4224 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,2281785545762161517,14815996722198865169,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4512427511346588884 --renderer-client-id=12 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3784 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2192 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2412 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,2281785545762161517,14815996722198865169,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=18412448037718146442 --mojo-platform-channel-handle=3296 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2464 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1044,2281785545762161517,14815996722198865169,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=7625647727056440409 --mojo-platform-channel-handle=4812 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2464 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,2281785545762161517,14815996722198865169,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=925056457738500231 --renderer-client-id=29 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4264 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
11 563
Read events
2 030
Write events
6 382
Delete events
3 151
Modification events
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1988658184 | |||
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30795996 | |||
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3172) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
54
Text files
265
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3172 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3148 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab8351.tmp | — | |
MD5:— | SHA256:— | |||
| 3148 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar8352.tmp | — | |
MD5:— | SHA256:— | |||
| 3148 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\0N7XOESD.txt | — | |
MD5:— | SHA256:— | |||
| 3148 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\239H7LYX.txt | — | |
MD5:— | SHA256:— | |||
| 3148 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\8QU1CQCK.txt | text | |
MD5:— | SHA256:— | |||
| 3148 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\453HF2UZ.htm | html | |
MD5:— | SHA256:— | |||
| 3148 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\MSIMGSIZ.DAT | smt | |
MD5:— | SHA256:— | |||
| 3148 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\caf[1].js | text | |
MD5:— | SHA256:— | |||
| 2192 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5E50136C-890.pma | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
61
DNS requests
40
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
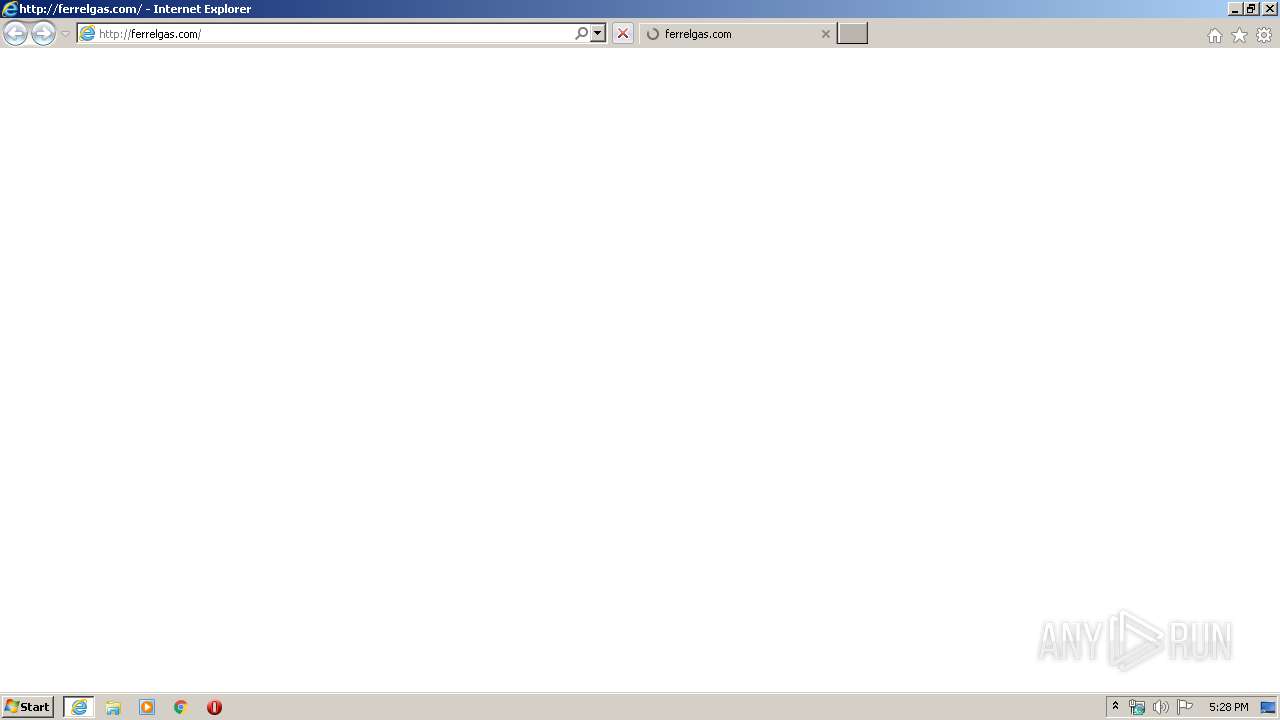
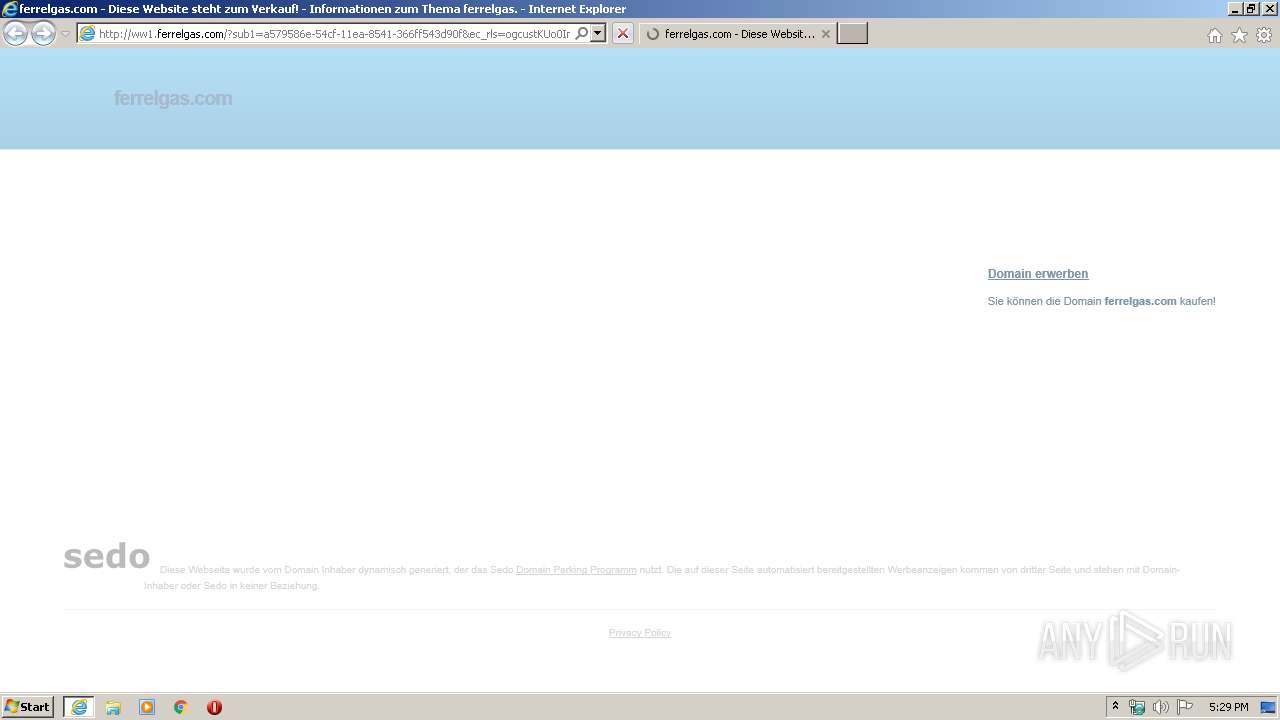
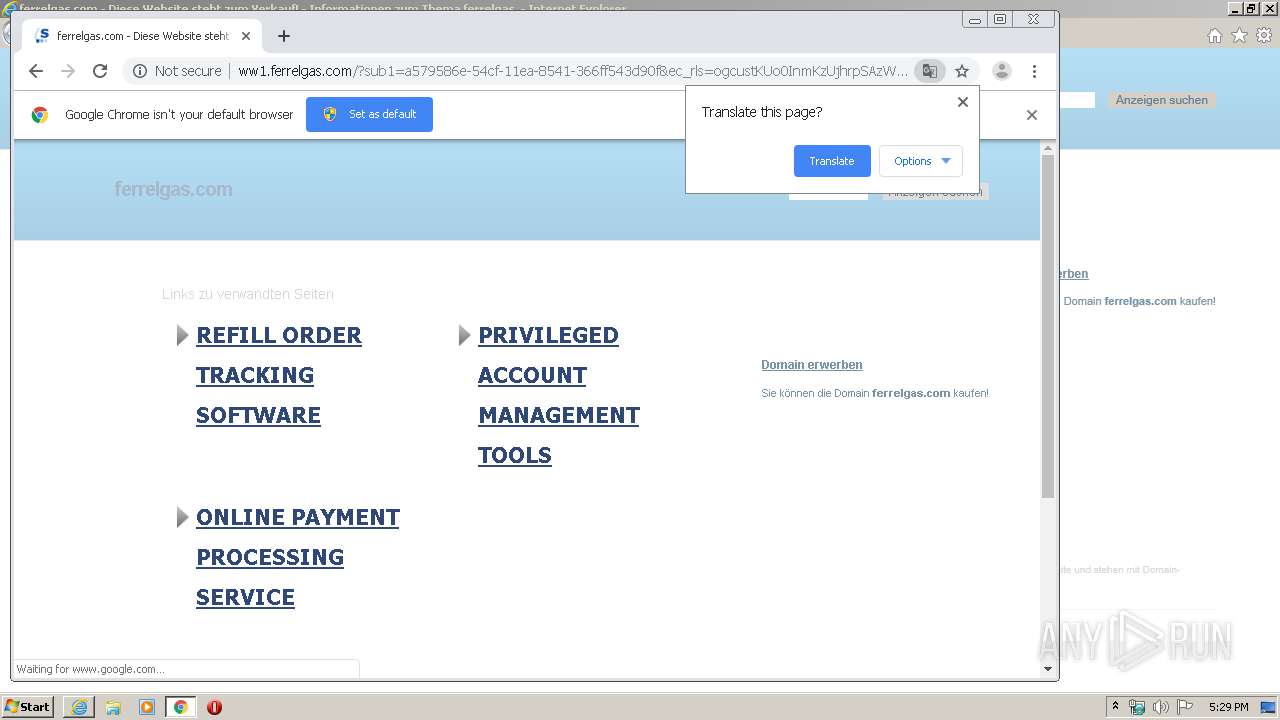
3148 | iexplore.exe | GET | 200 | 91.195.240.136:80 | http://ww1.ferrelgas.com/?sub1=a579586e-54cf-11ea-8541-366ff543d90f&ec_rls=ogcustKUo0InmKzUjhrpSAzWlFt6NIC21Q_WDJvSonP0AuykVCvjyJUkTWsvdhh0v8x61npkH1cS5cBEQsYnTHOnpPfwfIx8UUcO8YRC9ufJcKYv4_cwgBrb9B83cQavDhr7J0IPkUSEI3fZZq-atTp2gQ1ACsj9Hpo3EV23EsdiP2yhFk3QqdNPVBTbEwOpns | DE | html | 21.7 Kb | malicious |
3148 | iexplore.exe | GET | 200 | 172.217.23.163:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDvdxhhS3x8DggAAAAALnGY | US | der | 472 b | whitelisted |
3148 | iexplore.exe | GET | 200 | 172.217.23.163:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDvdxhhS3x8DggAAAAALnGY | US | der | 472 b | whitelisted |
3148 | iexplore.exe | GET | 200 | 172.217.23.163:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
1232 | chrome.exe | GET | 200 | 91.195.240.136:80 | http://ww1.ferrelgas.com/?sub1=a579586e-54cf-11ea-8541-366ff543d90f&ec_rls=ogcustKUo0InmKzUjhrpSAzWlFt6NIC21Q_WDJvSonP0AuykVCvjyJUkTWsvdhh0v8x61npkH1cS5cBEQsYnTHOnpPfwfIx8UUcO8YRC9ufJcKYv4_cwgBrb9B83cQavDhr7J0IPkUSEI3fZZq-atTp2gQ1ACsj9Hpo3EV23EsdiP2yhFk3QqdNPVBTbEwOpns | DE | html | 21.8 Kb | malicious |
3148 | iexplore.exe | GET | 200 | 172.217.22.4:80 | http://www.google.com/adsense/domains/caf.js | US | text | 55.5 Kb | malicious |
1232 | chrome.exe | GET | 200 | 91.195.240.136:80 | http://ww1.ferrelgas.com/search/tsc.php?200=MjIyMDU5MzUw&21=NDUuNDEuMTM4LjIwNA==&681=MTU4MjMwNjE2MjlhMzMyNTcwNjFiNDZkZjM3NjFhYzBiZjUwMmU5OTIz&crc=b64680ccea3a57c8a8f6c149548275c1432eed69&cv=1 | DE | compressed | 21.8 Kb | malicious |
3148 | iexplore.exe | GET | 200 | 172.217.23.163:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
3172 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
3148 | iexplore.exe | GET | 200 | 205.234.175.175:80 | http://img.sedoparking.com/templates/brick_gfx/common/logo_2016_bbbbbb.svg | US | image | 2.02 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3148 | iexplore.exe | 69.162.80.61:80 | ferrelgas.com | Limestone Networks, Inc. | US | malicious |
3148 | iexplore.exe | 91.195.240.136:80 | ww1.ferrelgas.com | SEDO GmbH | DE | malicious |
3148 | iexplore.exe | 172.217.22.4:80 | www.google.com | Google Inc. | US | whitelisted |
3148 | iexplore.exe | 205.234.175.175:80 | img.sedoparking.com | CacheNetworks, Inc. | US | suspicious |
3148 | iexplore.exe | 172.217.22.4:443 | www.google.com | Google Inc. | US | whitelisted |
3172 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1232 | chrome.exe | 216.58.207.45:443 | accounts.google.com | Google Inc. | US | whitelisted |
1232 | chrome.exe | 172.217.21.227:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1232 | chrome.exe | 172.217.18.10:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
1232 | chrome.exe | 172.217.23.99:443 | www.google.com.ua | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ferrelgas.com |
| malicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ww1.ferrelgas.com |
| malicious |
img.sedoparking.com |
| whitelisted |
www.google.com |
| malicious |
www.gstatic.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1232 | chrome.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |