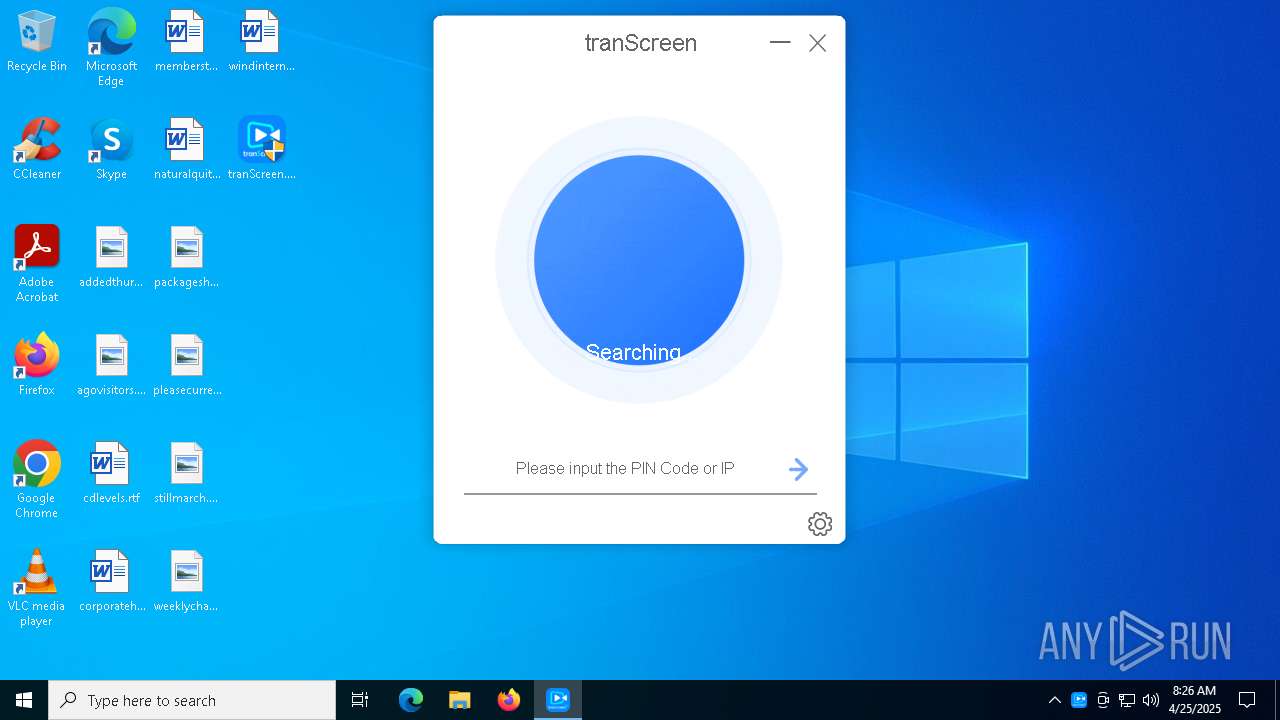
| File name: | tranScreen.exe |
| Full analysis: | https://app.any.run/tasks/f61731eb-4c40-47bc-8768-211250441ff8 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2025, 08:26:10 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 6DFEAC9500F6AF2359E2487044F8FAAF |
| SHA1: | E53365412860B2E4F67C8CA64E6376254F4448A7 |
| SHA256: | CBC906DD7A5A564DD639772C359EE5F1C62AE45FB3D4ED21A2D8C163CC950338 |
| SSDEEP: | 98304:zOKfSQHcKwAkYkK+wV+mIkYkK+wV+m/f10BCnL6ePmzYWt9l52Xr+iHnn8keoO+m:f+tzw3FsOBfLS+JedMmE3yBgchNj |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
- tranScreen.exe (PID: 7340)
Executable content was dropped or overwritten
- tranScreen.exe (PID: 7340)
- devcon.exe (PID: 8132)
- TranscreenSoftware.exe (PID: 7480)
- drvinst.exe (PID: 5124)
- drvinst.exe (PID: 2236)
- devcon.exe (PID: 2772)
- devcon.exe (PID: 6512)
- drvinst.exe (PID: 8060)
- drvinst.exe (PID: 7988)
- drvinst.exe (PID: 8168)
- drvinst.exe (PID: 8024)
Process drops legitimate windows executable
- tranScreen.exe (PID: 7340)
- TranscreenSoftware.exe (PID: 7480)
Reads security settings of Internet Explorer
- tranScreen.exe (PID: 7340)
- TranscreenSoftware.exe (PID: 7480)
- InstallDeviceDriver.exe (PID: 7976)
- devcon.exe (PID: 8132)
- InstallDeviceDriver.exe (PID: 7236)
- InstallDeviceDriver.exe (PID: 7316)
- devcon.exe (PID: 6512)
- devcon.exe (PID: 2772)
Drops a system driver (possible attempt to evade defenses)
- TranscreenSoftware.exe (PID: 7480)
- devcon.exe (PID: 8132)
- drvinst.exe (PID: 2236)
- drvinst.exe (PID: 5124)
- drvinst.exe (PID: 7988)
- devcon.exe (PID: 6512)
- drvinst.exe (PID: 8024)
Creates or modifies Windows services
- drvinst.exe (PID: 5124)
- drvinst.exe (PID: 8168)
- drvinst.exe (PID: 8024)
There is functionality for taking screenshot (YARA)
- TranscreenSoftware.exe (PID: 7480)
Creates files in the driver directory
- drvinst.exe (PID: 5124)
- drvinst.exe (PID: 2236)
- drvinst.exe (PID: 7988)
- drvinst.exe (PID: 8060)
- drvinst.exe (PID: 8024)
- drvinst.exe (PID: 8168)
Executes as Windows Service
- WUDFHost.exe (PID: 7624)
Creates/Modifies COM task schedule object
- drvinst.exe (PID: 8024)
INFO
The sample compiled with russian language support
- tranScreen.exe (PID: 7340)
- TranscreenSoftware.exe (PID: 7480)
Creates files or folders in the user directory
- tranScreen.exe (PID: 7340)
- TranscreenSoftware.exe (PID: 7480)
- InstallDeviceDriver.exe (PID: 7976)
- InstallDeviceDriver.exe (PID: 7316)
The sample compiled with chinese language support
- tranScreen.exe (PID: 7340)
- TranscreenSoftware.exe (PID: 7480)
- devcon.exe (PID: 8132)
- drvinst.exe (PID: 2236)
- drvinst.exe (PID: 5124)
- devcon.exe (PID: 2772)
- drvinst.exe (PID: 8060)
- drvinst.exe (PID: 8168)
Reads the computer name
- tranScreen.exe (PID: 7340)
- TranscreenSoftware.exe (PID: 7480)
- InstallDeviceDriver.exe (PID: 7976)
- devcon.exe (PID: 8132)
- drvinst.exe (PID: 2236)
- drvinst.exe (PID: 5124)
- devcon.exe (PID: 6512)
- InstallDeviceDriver.exe (PID: 7236)
- InstallDeviceDriver.exe (PID: 7316)
- devcon.exe (PID: 2772)
- drvinst.exe (PID: 8060)
- drvinst.exe (PID: 8168)
- drvinst.exe (PID: 7988)
- drvinst.exe (PID: 8024)
The sample compiled with english language support
- tranScreen.exe (PID: 7340)
- TranscreenSoftware.exe (PID: 7480)
- devcon.exe (PID: 6512)
- drvinst.exe (PID: 7988)
- drvinst.exe (PID: 8024)
Creates files in the program directory
- tranScreen.exe (PID: 7340)
Checks supported languages
- tranScreen.exe (PID: 7340)
- TranscreenSoftware.exe (PID: 7480)
- devcon.exe (PID: 8088)
- InstallDeviceDriver.exe (PID: 7976)
- devcon.exe (PID: 8132)
- drvinst.exe (PID: 5124)
- drvinst.exe (PID: 2236)
- InstallDeviceDriver.exe (PID: 7316)
- InstallDeviceDriver.exe (PID: 7236)
- devcon.exe (PID: 1672)
- devcon.exe (PID: 4108)
- devcon.exe (PID: 6512)
- devcon.exe (PID: 2772)
- drvinst.exe (PID: 7988)
- drvinst.exe (PID: 8060)
- drvinst.exe (PID: 8024)
- drvinst.exe (PID: 8168)
Process checks computer location settings
- tranScreen.exe (PID: 7340)
- TranscreenSoftware.exe (PID: 7480)
- InstallDeviceDriver.exe (PID: 7976)
- InstallDeviceDriver.exe (PID: 7236)
- InstallDeviceDriver.exe (PID: 7316)
Reads the machine GUID from the registry
- devcon.exe (PID: 8132)
- drvinst.exe (PID: 2236)
- devcon.exe (PID: 2772)
- devcon.exe (PID: 6512)
- drvinst.exe (PID: 7988)
- drvinst.exe (PID: 8060)
- drvinst.exe (PID: 8024)
Reads the software policy settings
- devcon.exe (PID: 8132)
- drvinst.exe (PID: 2236)
- devcon.exe (PID: 2772)
- devcon.exe (PID: 6512)
- drvinst.exe (PID: 8060)
- drvinst.exe (PID: 7988)
- drvinst.exe (PID: 8024)
- slui.exe (PID: 6132)
Create files in a temporary directory
- devcon.exe (PID: 8132)
- devcon.exe (PID: 2772)
- devcon.exe (PID: 6512)
Checks proxy server information
- slui.exe (PID: 6132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:03:24 07:05:15+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.25 |
| CodeSize: | 130048 |
| InitializedDataSize: | 12712960 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb285 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.6.8.11 |
| ProductVersionNumber: | 2.6.8.11 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| CompanyName: | TranscreenSoft |
| FileDescription: | TranscreenSoftClient |
| FileVersion: | 2.6.8.11 |
| InternalName: | TranscreenSoft |
| LegalCopyright: | - |
| OriginalFileName: | - |
| ProductName: | TranscreenSoft |
| ProductVersion: | 2.6.8.11 |
Total processes
169
Monitored processes
29
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1672 | "C:\Users\admin\AppData\Roaming\Transcreen\Software\Drivers\tools\amd64\devcon.exe" -remove root\SHARECAMERA | C:\Users\admin\AppData\Roaming\Transcreen\Software\Drivers\tools\amd64\devcon.exe | — | InstallDeviceDriver.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 10.0.14393.0 (rs1_release.160715-1616) Modules
| |||||||||||||||
| 2236 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{50a65d31-bfa0-e84f-8093-09f3e8e6e16a}\tff_virtaudio.inf" "9" "4a5756487" "00000000000001D4" "WinSta0\Default" "000000000000008C" "208" "c:\users\admin\appdata\roaming\transcreen\software\drivers\tffaudio\x64" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | devcon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2772 | "C:\Users\admin\AppData\Roaming\Transcreen\Software\Drivers\vmonitor\x64\devcon.exe" -install "C:\Users\admin\AppData\Roaming\Transcreen\Software\Drivers\vmonitor\DisplayProxy.inf" hid\vid_1b36&pid_0d11 | C:\Users\admin\AppData\Roaming\Transcreen\Software\Drivers\vmonitor\x64\devcon.exe | InstallDeviceDriver.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 10.0.14393.0 (rs1_release.160715-1616) Modules
| |||||||||||||||
| 4108 | "C:\Users\admin\AppData\Roaming\Transcreen\Software\Drivers\vmonitor\x64\devcon.exe" -remove hid\vid_1b36&pid_0d11 | C:\Users\admin\AppData\Roaming\Transcreen\Software\Drivers\vmonitor\x64\devcon.exe | — | InstallDeviceDriver.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 10.0.14393.0 (rs1_release.160715-1616) Modules
| |||||||||||||||
| 5124 | DrvInst.exe "2" "211" "ROOT\MEDIA\0000" "C:\WINDOWS\INF\oem1.inf" "oem1.inf:ed86ca119389ada1:tff_virtaudio:1.0.0.4:*tff_virtaudio," "4a5756487" "0000000000000088" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5544 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | devcon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5964 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | devcon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6132 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6512 | "C:\Users\admin\AppData\Roaming\Transcreen\Software\Drivers\tools\amd64\devcon.exe" -install "C:\Users\admin\AppData\Roaming\Transcreen\Software\Drivers\vcamera\amd64\TranScreenCamera.inf" root\SHARECAMERA | C:\Users\admin\AppData\Roaming\Transcreen\Software\Drivers\tools\amd64\devcon.exe | InstallDeviceDriver.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 10.0.14393.0 (rs1_release.160715-1616) Modules
| |||||||||||||||
Total events
27 970
Read events
26 599
Write events
1 356
Delete events
15
Modification events
| (PID) Process: | (7480) TranscreenSoftware.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\ActiveMovie\devenum\{33D9A762-90C8-11D0-BD43-00A0C911CE86}\wave:{A14F8BF5-56E3-412D-AF34-D2240261ED67} |
| Operation: | write | Name: | FriendlyName |
Value: Line In (2- Realtek AC'97 Audio) | |||
| (PID) Process: | (7480) TranscreenSoftware.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\ActiveMovie\devenum\{33D9A762-90C8-11D0-BD43-00A0C911CE86}\wave:{A14F8BF5-56E3-412D-AF34-D2240261ED67} |
| Operation: | write | Name: | CLSID |
Value: {E30629D2-27E5-11CE-875D-00608CB78066} | |||
| (PID) Process: | (7480) TranscreenSoftware.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\ActiveMovie\devenum\{33D9A762-90C8-11D0-BD43-00A0C911CE86}\wave:{A14F8BF5-56E3-412D-AF34-D2240261ED67} |
| Operation: | write | Name: | FilterData |
Value: 02000000000020000000000000000000 | |||
| (PID) Process: | (7480) TranscreenSoftware.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\ActiveMovie\devenum\{33D9A762-90C8-11D0-BD43-00A0C911CE86}\wave:{A14F8BF5-56E3-412D-AF34-D2240261ED67} |
| Operation: | write | Name: | EndpointId |
Value: {0.0.1.00000000}.{a14f8bf5-56e3-412d-af34-d2240261ed67} | |||
| (PID) Process: | (7480) TranscreenSoftware.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\ActiveMovie\devenum\{33D9A762-90C8-11D0-BD43-00A0C911CE86}\wave:{A14F8BF5-56E3-412D-AF34-D2240261ED67} |
| Operation: | write | Name: | EndpointGuid |
Value: {A14F8BF5-56E3-412D-AF34-D2240261ED67} | |||
| (PID) Process: | (7480) TranscreenSoftware.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\ActiveMovie\devenum\{33D9A762-90C8-11D0-BD43-00A0C911CE86}\wave:{A14F8BF5-56E3-412D-AF34-D2240261ED67} |
| Operation: | write | Name: | WaveInId |
Value: 1 | |||
| (PID) Process: | (7480) TranscreenSoftware.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\ActiveMovie\devenum\{33D9A762-90C8-11D0-BD43-00A0C911CE86}\wave:{05B02C95-C55A-499C-A533-120810B973DF} |
| Operation: | write | Name: | FriendlyName |
Value: Microphone (2- Realtek AC'97 Audio) | |||
| (PID) Process: | (7480) TranscreenSoftware.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\ActiveMovie\devenum\{33D9A762-90C8-11D0-BD43-00A0C911CE86}\wave:{05B02C95-C55A-499C-A533-120810B973DF} |
| Operation: | write | Name: | CLSID |
Value: {E30629D2-27E5-11CE-875D-00608CB78066} | |||
| (PID) Process: | (7480) TranscreenSoftware.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\ActiveMovie\devenum\{33D9A762-90C8-11D0-BD43-00A0C911CE86}\wave:{05B02C95-C55A-499C-A533-120810B973DF} |
| Operation: | write | Name: | FilterData |
Value: 02000000000020000000000000000000 | |||
| (PID) Process: | (7480) TranscreenSoftware.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\ActiveMovie\devenum\{33D9A762-90C8-11D0-BD43-00A0C911CE86}\wave:{05B02C95-C55A-499C-A533-120810B973DF} |
| Operation: | write | Name: | EndpointId |
Value: {0.0.1.00000000}.{05b02c95-c55a-499c-a533-120810b973df} | |||
Executable files
109
Suspicious files
41
Text files
377
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7340 | tranScreen.exe | C:\Users\admin\AppData\Roaming\Transcreen\Software\Drivers.zip | compressed | |
MD5:1273B0C68E1129096838414C15647BF1 | SHA256:0627B303956462624628416D283EA71B1B426C41AF5171E3C82B7E74417D109C | |||
| 7340 | tranScreen.exe | C:\Users\admin\AppData\Roaming\Transcreen\Software\TranscreenSoftware.exe | executable | |
MD5:C689B511592310446D7F8B56F52A4910 | SHA256:D59D65911A8F1C0AB4C64B083165FCC8337A1E8959D8C92A37423B79D4C30633 | |||
| 7340 | tranScreen.exe | C:\Users\admin\AppData\Roaming\Transcreen\Software\libVMonitor-New.dll | executable | |
MD5:7AF20E3C8A63222A56A74B2929CB518C | SHA256:A94890DCCBD78C94598DABA1C39147377885906B0E1C801CA50EFB004E5CF62A | |||
| 7340 | tranScreen.exe | C:\Users\admin\AppData\Roaming\Transcreen\Software\TFFPowerpoint.exe | executable | |
MD5:9D576A59B70D86BDE2879080614A0749 | SHA256:9EE57C36B770A266794F3904CF5B213766C06D86DDF8463E09C7EF399449A81D | |||
| 7340 | tranScreen.exe | C:\Users\admin\AppData\Roaming\Transcreen\Software\libgcc_s_dw2-1.dll | executable | |
MD5:3C63B3B19004FBF2429171352BD0E4AF | SHA256:77C66C8FDE5706A2E82199001D0082CC61AEAE46536DD3BF6BB53AC001E5058E | |||
| 7340 | tranScreen.exe | C:\Users\admin\AppData\Roaming\Transcreen\Software\DuiLib.dll | executable | |
MD5:FEF2483D0B3F41E59767893681249F87 | SHA256:DD8FA304426DAC773B6B42D103F6AD8EAD673402EE506C7BB7E566EEF041A5EE | |||
| 7340 | tranScreen.exe | C:\Users\admin\AppData\Roaming\Transcreen\Software\wz264.dll | executable | |
MD5:19D2075402C800939A34ED7EB417AD94 | SHA256:38DC6C3C6E3A0652483F2E884544412EF2B6578A05570E9DA0B1E6D4B0BF105E | |||
| 7340 | tranScreen.exe | C:\Users\admin\AppData\Roaming\Transcreen\Software\libx264-146.dll | executable | |
MD5:BB927B4A2DAF63516AFB2D73805949E7 | SHA256:907534D4B1007FB660C21F17AF0F110AB768F42ABCED223825C4DD31A5653FFA | |||
| 7340 | tranScreen.exe | C:\Users\admin\AppData\Roaming\Transcreen\Software\libVMonitor.dll | executable | |
MD5:91EC8074D3F068EA6EDD027D9351717D | SHA256:2D11EE5AFAC02EA89DF4C35DC1C6A928FEEE2ADF06E8B714CED3D557E8E02C14 | |||
| 7340 | tranScreen.exe | C:\Users\admin\AppData\Roaming\Transcreen\Software\TranScreenCameraAPI.dll | executable | |
MD5:BFB70A0F5C9F70DBB69479DABAD52823 | SHA256:E9960C222F4CF0E002A987469C9590394A8B653194DB64C7FFE439148BC665B3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
33
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.161:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3100 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3100 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.161:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
— | — | 255.255.255.255:6889 | — | — | — | unknown |
6544 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |