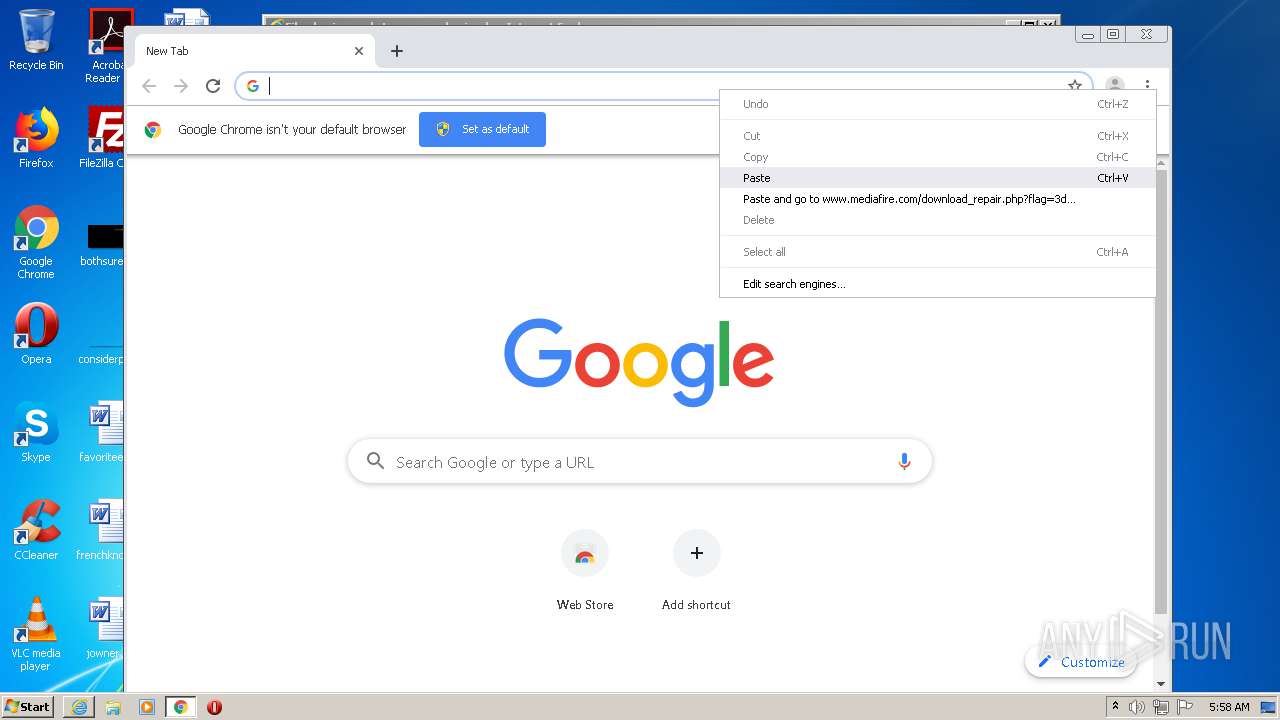
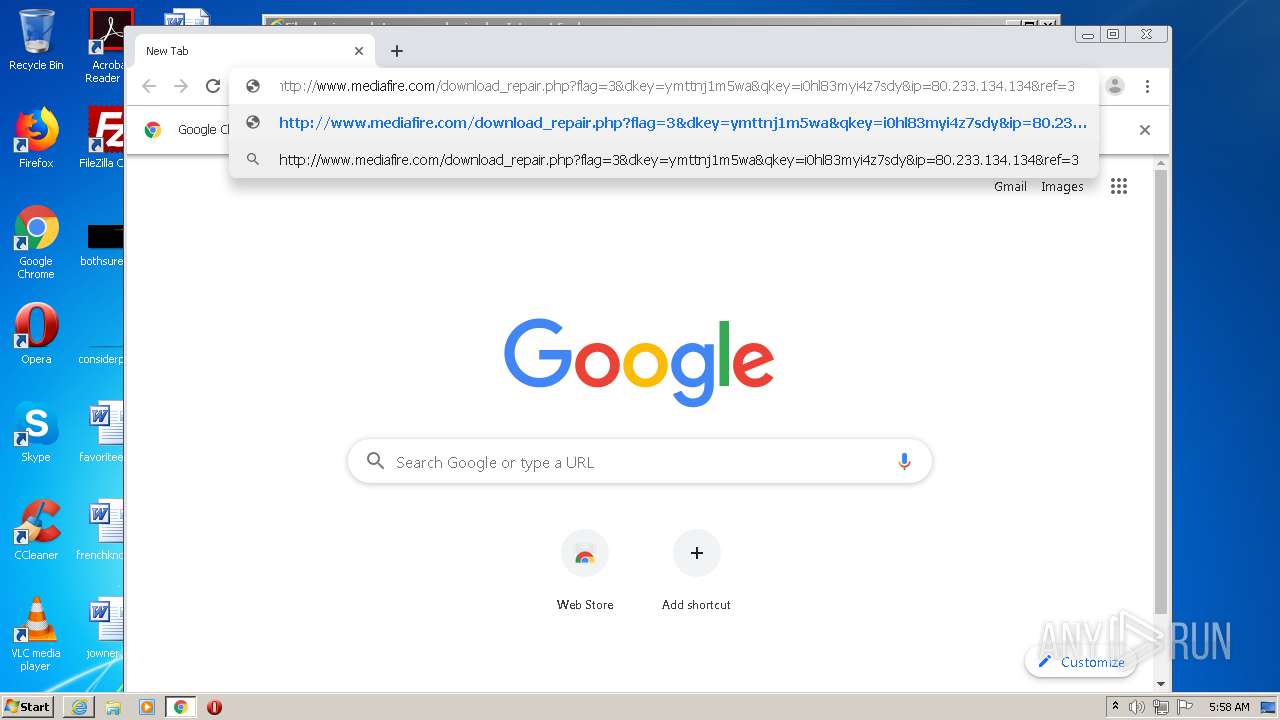
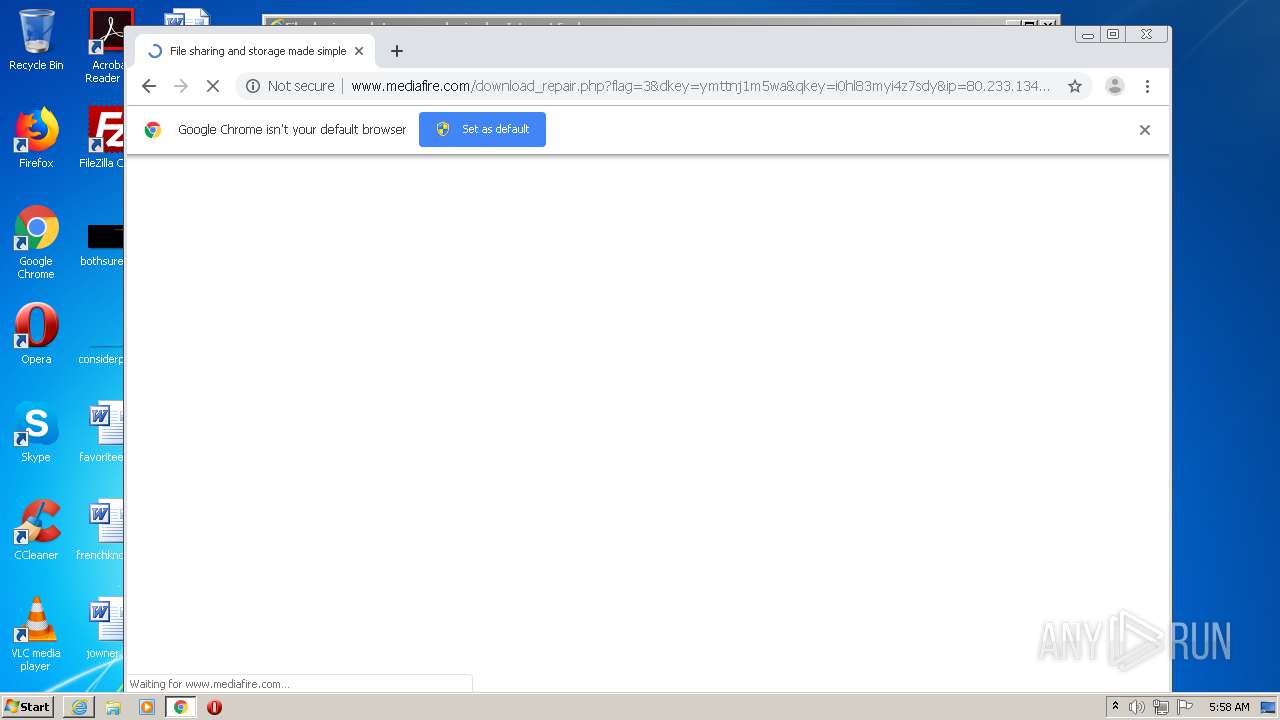
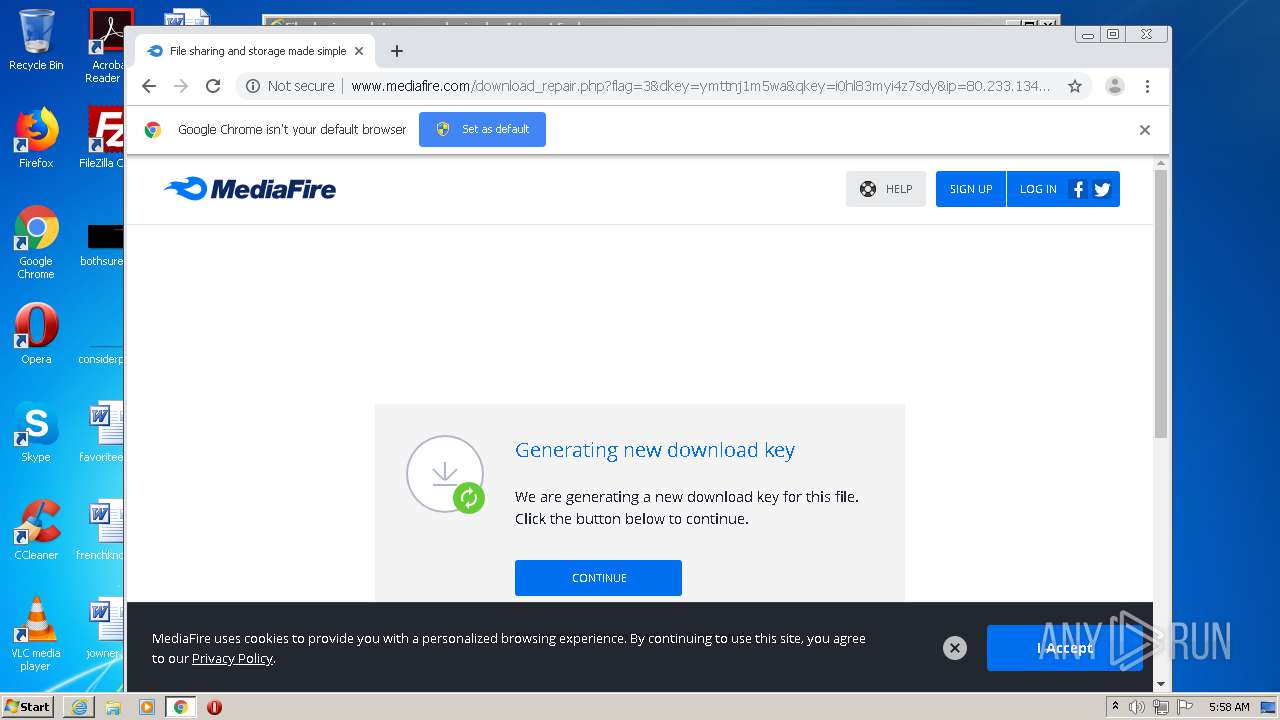
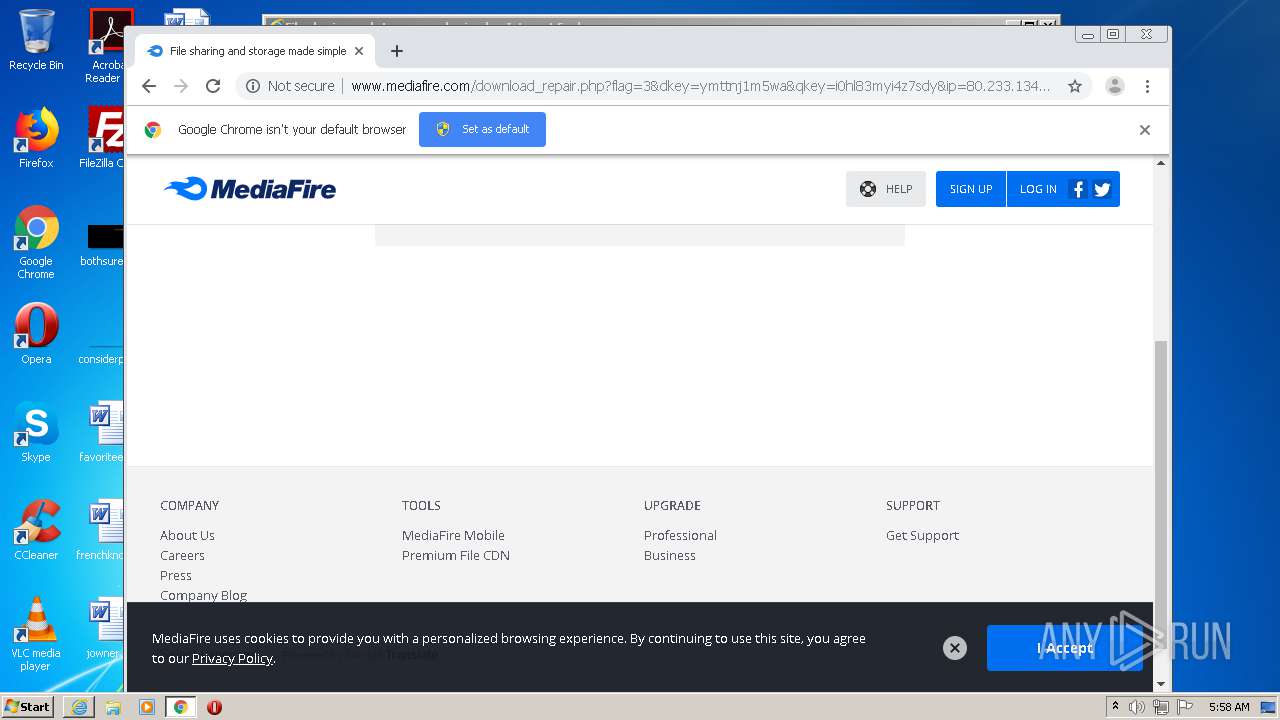
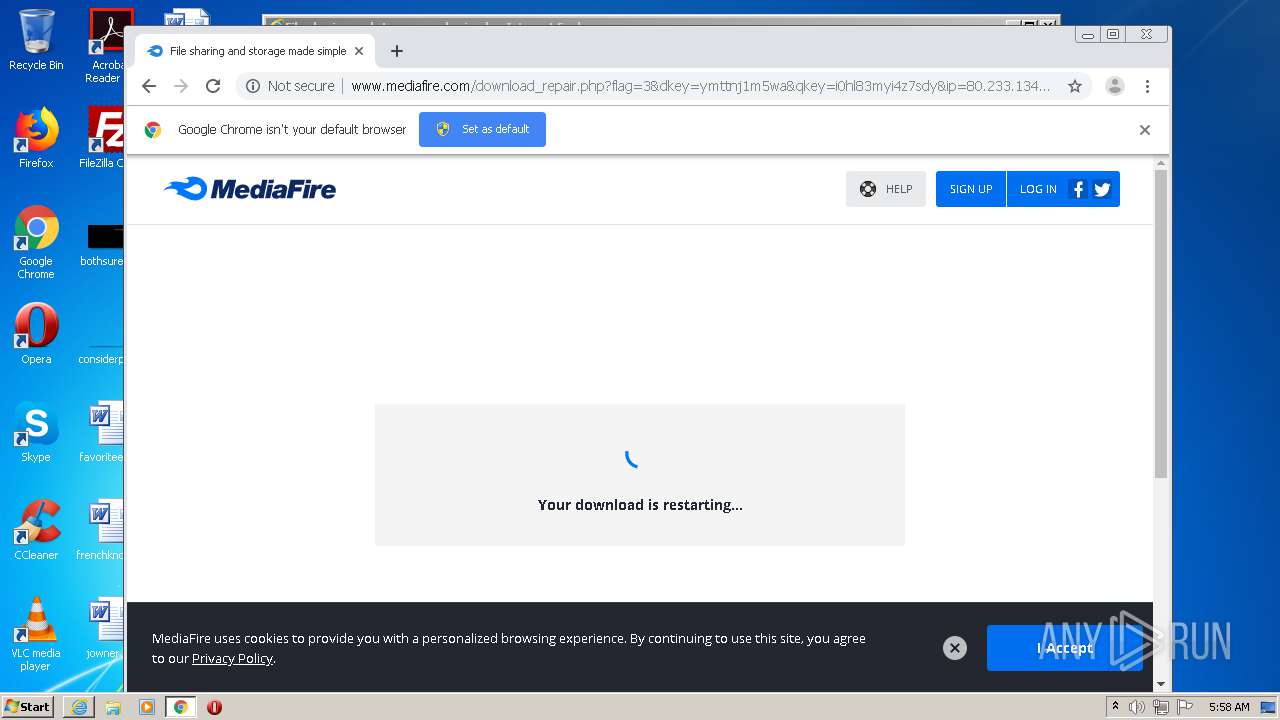
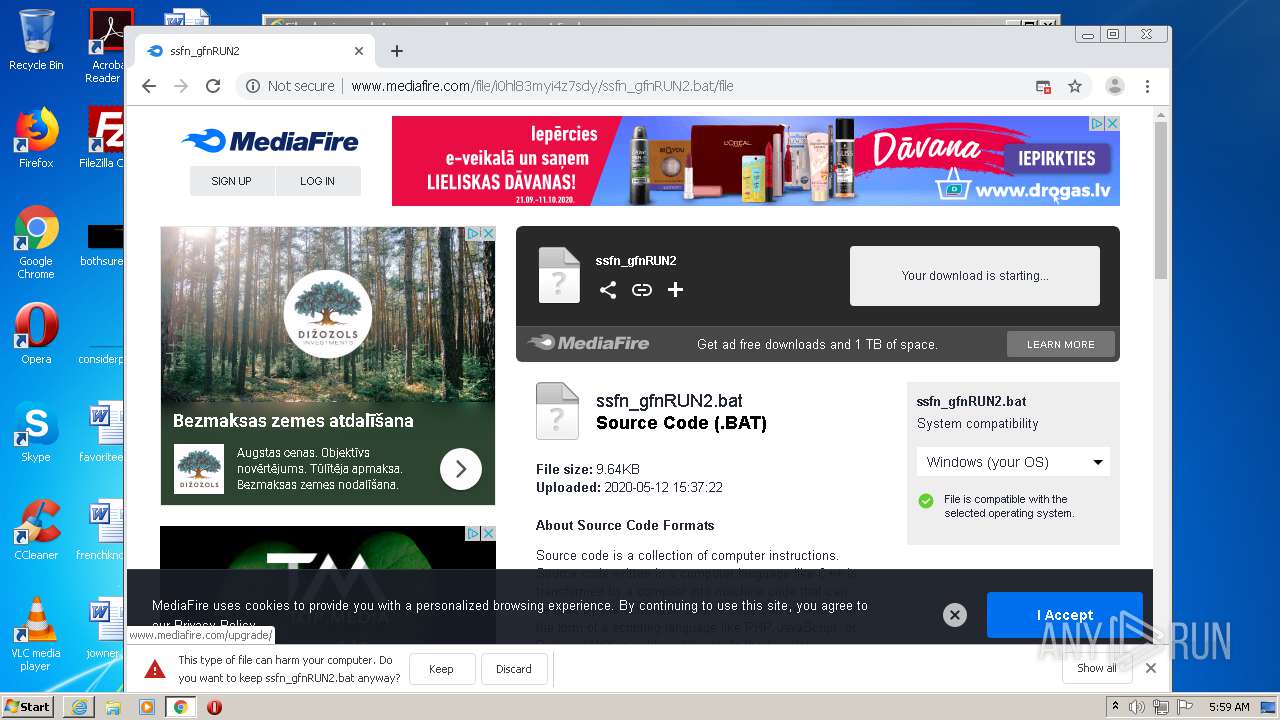
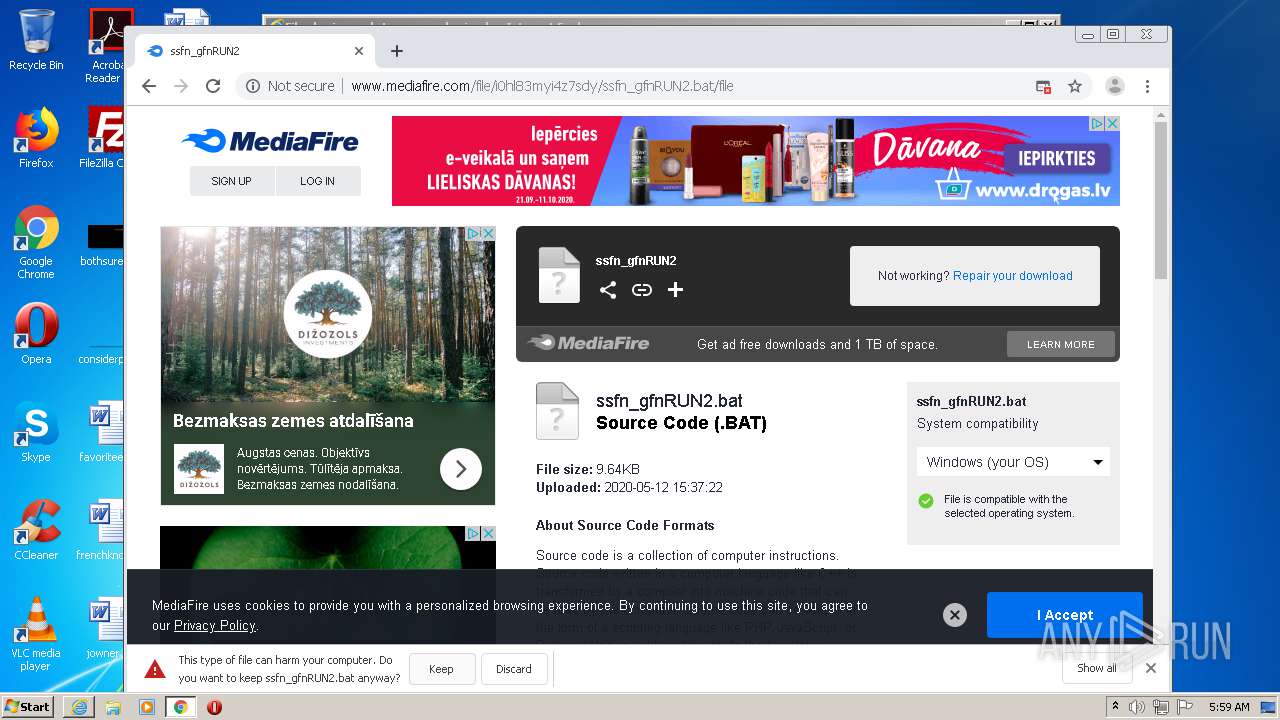
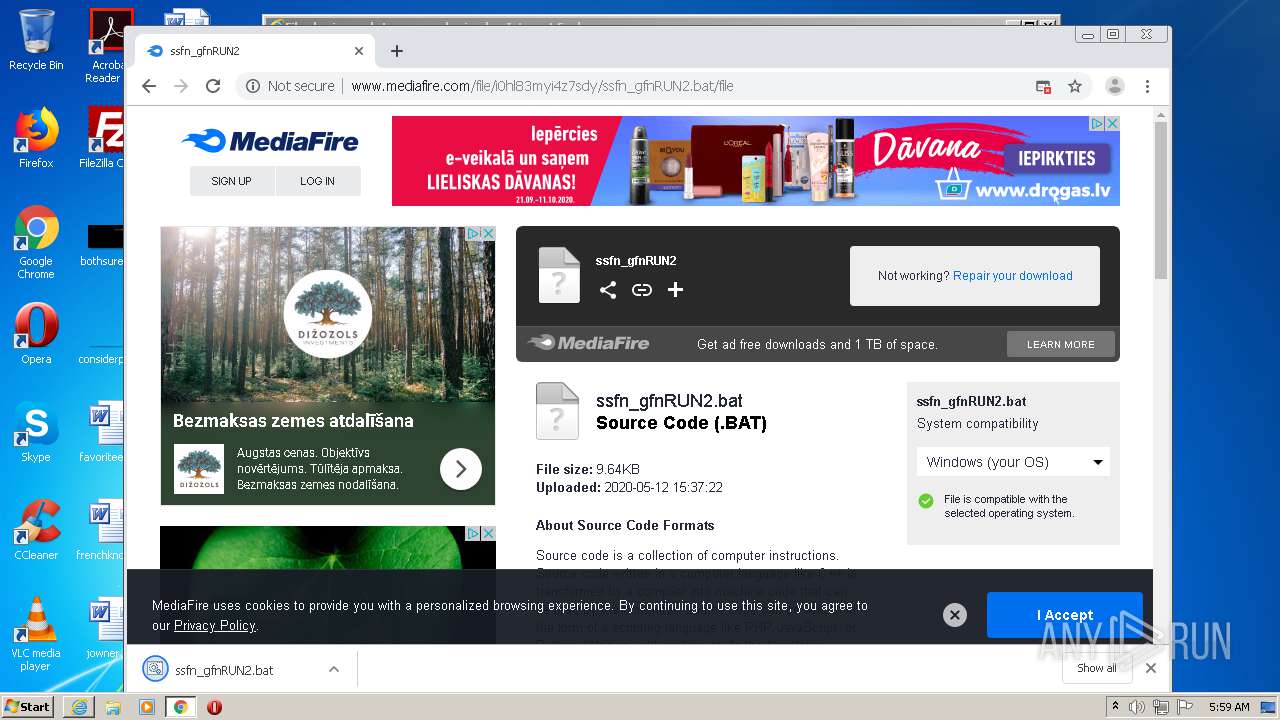
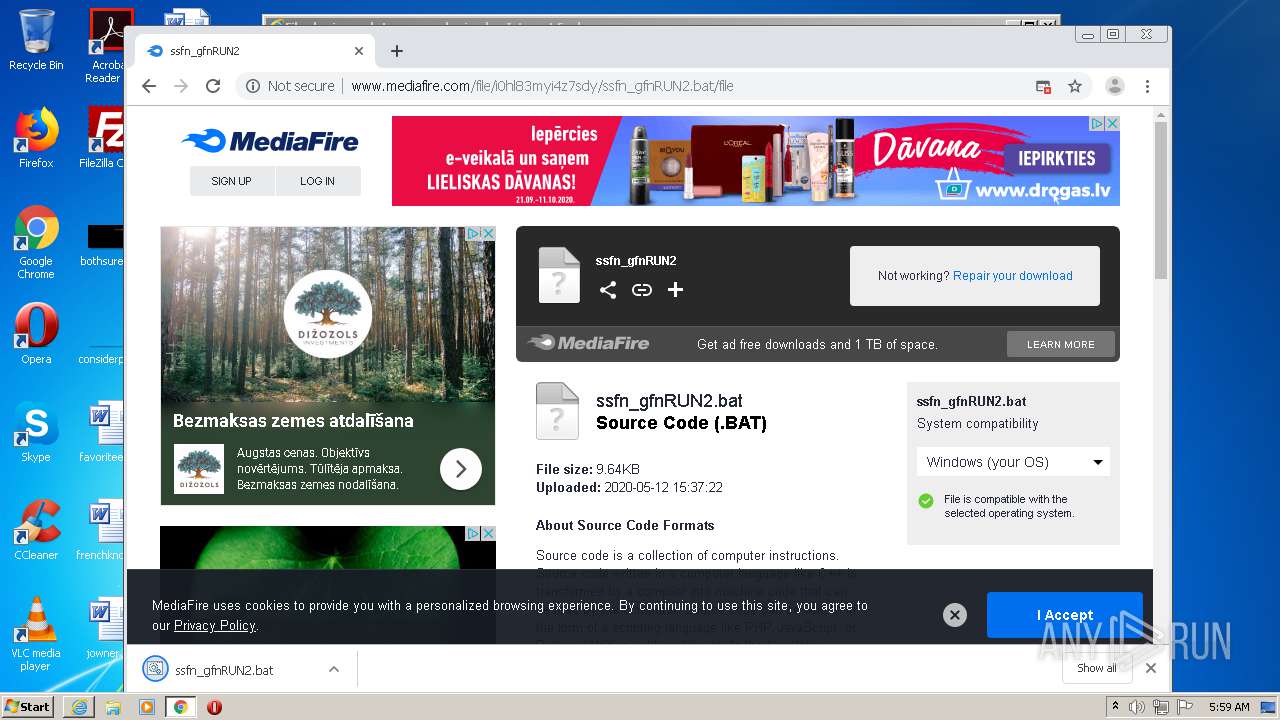
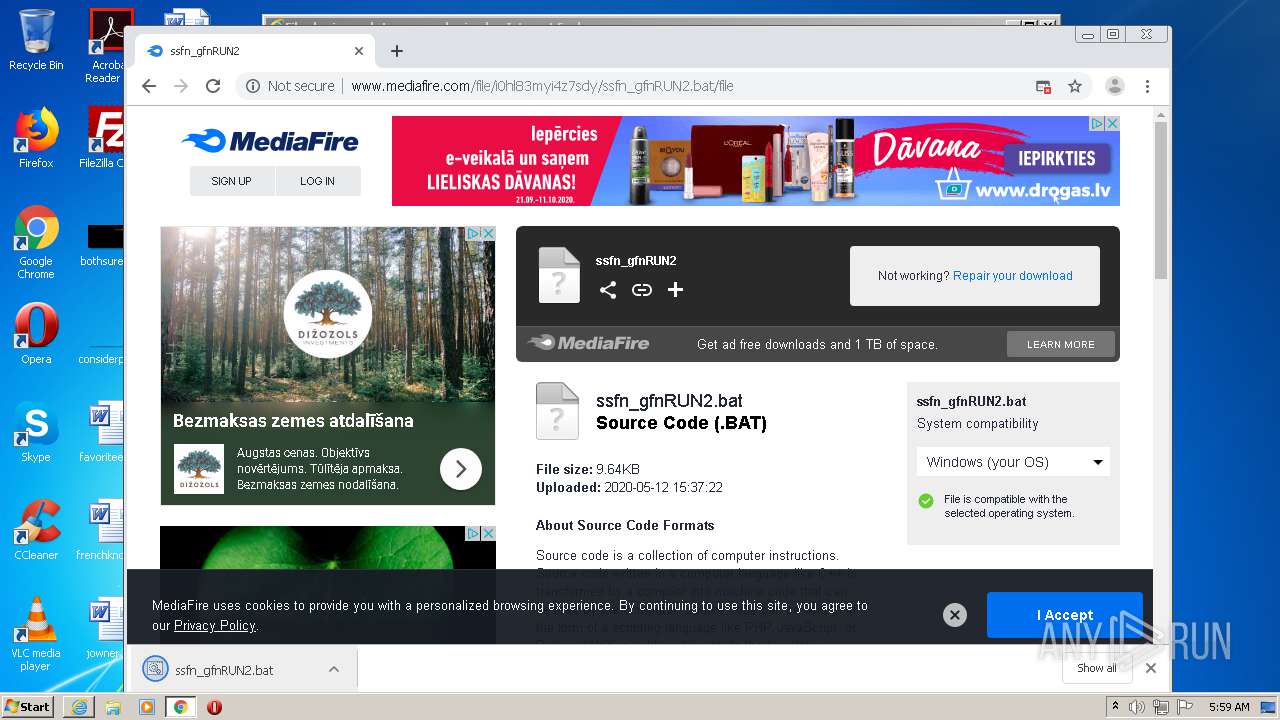
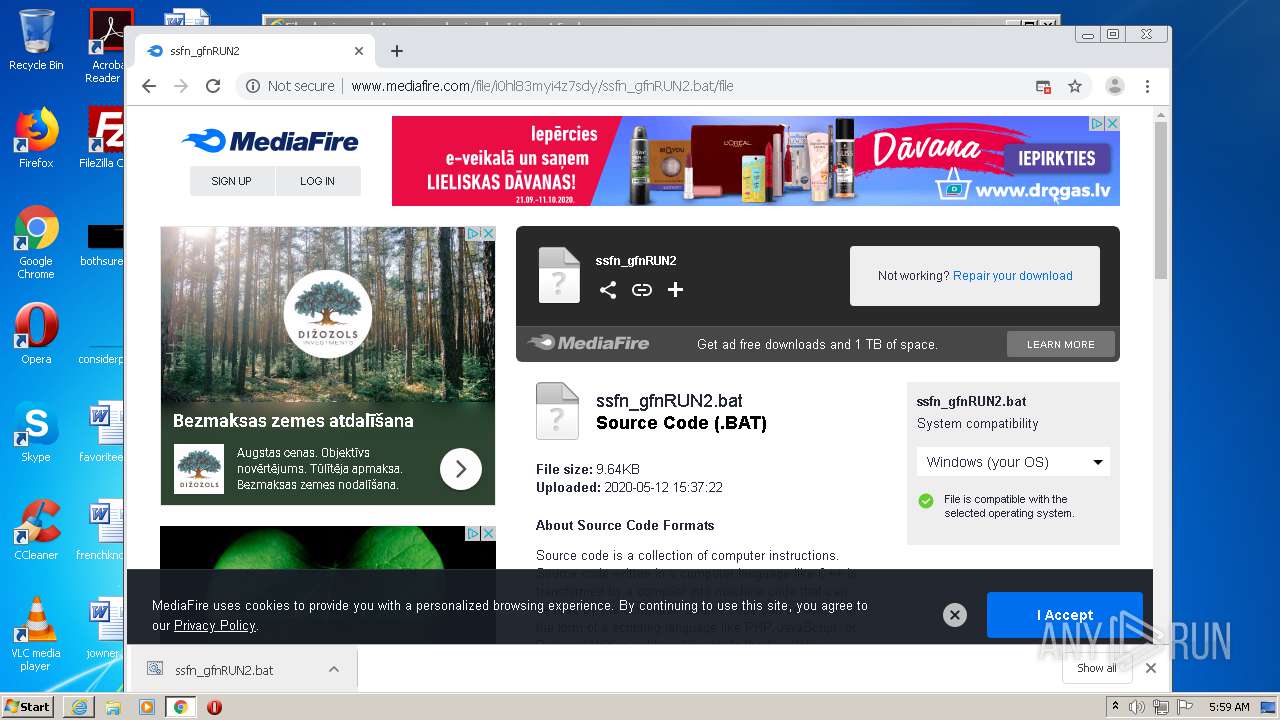
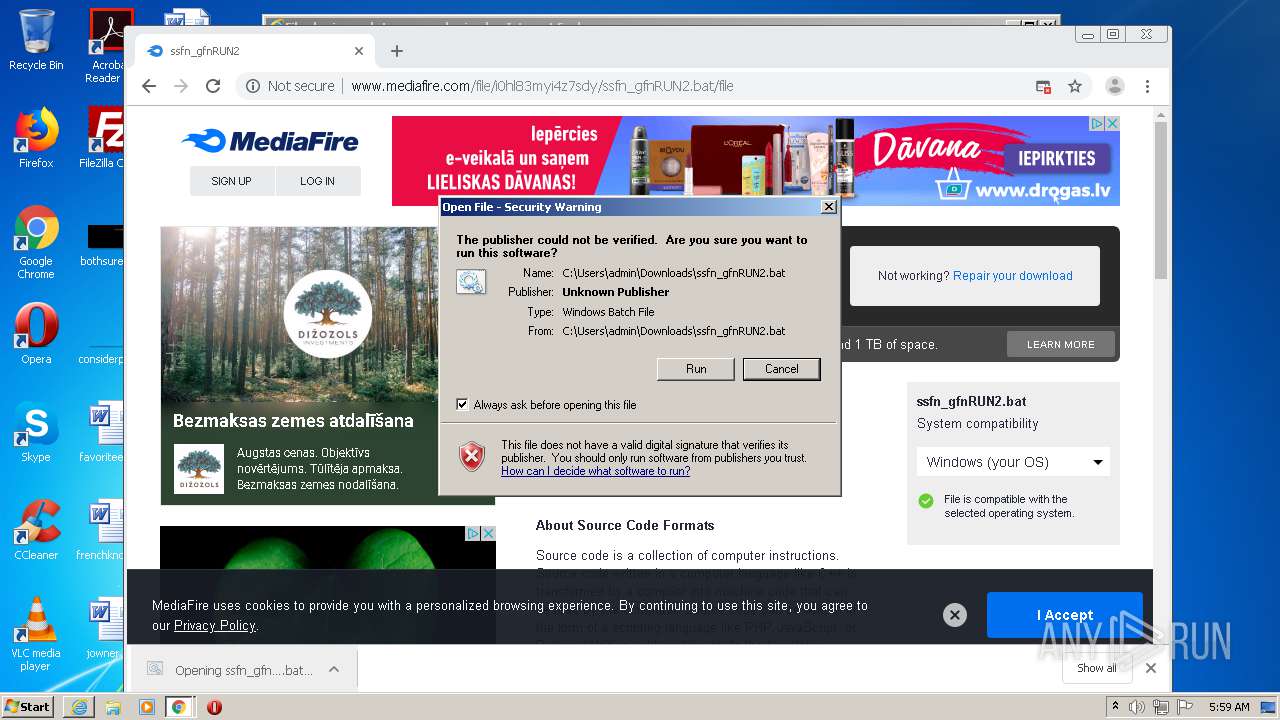
| File name: | file |
| Full analysis: | https://app.any.run/tasks/5841adf8-752b-48ab-8614-98af6bf1ea61 |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 04:57:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines, with CRLF, LF line terminators |
| MD5: | 1FF4738B61A63E5FDBB0C62E38CA255D |
| SHA1: | 5E8FDEB78683E34504CF55C12771A52559A82BF7 |
| SHA256: | CB93F9385BDFAC9C0125B40BD7BFA832119FD8ED1BE5397051CA45694EE34D5A |
| SSDEEP: | 3072:J1igAkHnjkQ6KSwXNXL4oNF5bYZpHCXvkWvLgsKNkhILAU0OY3giLa:egAkHnjkQBSwXN7v98HiXvNgsUO3giLa |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts CMD.EXE for commands execution
- chrome.exe (PID: 3052)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2536)
- iexplore.exe (PID: 2132)
- chrome.exe (PID: 3052)
Application launched itself
- iexplore.exe (PID: 2536)
- iexplore.exe (PID: 1748)
- chrome.exe (PID: 3052)
Changes internet zones settings
- iexplore.exe (PID: 2536)
Changes settings of System certificates
- iexplore.exe (PID: 1748)
- iexplore.exe (PID: 2536)
Reads internet explorer settings
- iexplore.exe (PID: 1748)
- iexplore.exe (PID: 2132)
Reads settings of System Certificates
- iexplore.exe (PID: 1748)
- iexplore.exe (PID: 2536)
- iexplore.exe (PID: 2132)
- chrome.exe (PID: 2940)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1748)
- iexplore.exe (PID: 2536)
Creates files in the user directory
- iexplore.exe (PID: 1748)
- iexplore.exe (PID: 2132)
- iexplore.exe (PID: 2536)
Manual execution by user
- chrome.exe (PID: 3052)
Reads the hosts file
- chrome.exe (PID: 3052)
- chrome.exe (PID: 2940)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .htm/html | | | HyperText Markup Language with DOCTYPE (80.6) |
|---|---|---|
| .html | | | HyperText Markup Language (19.3) |
EXIF
HTML
| twitterCard: | summary_large_image |
|---|---|
| twitterSite: | @MediaFire |
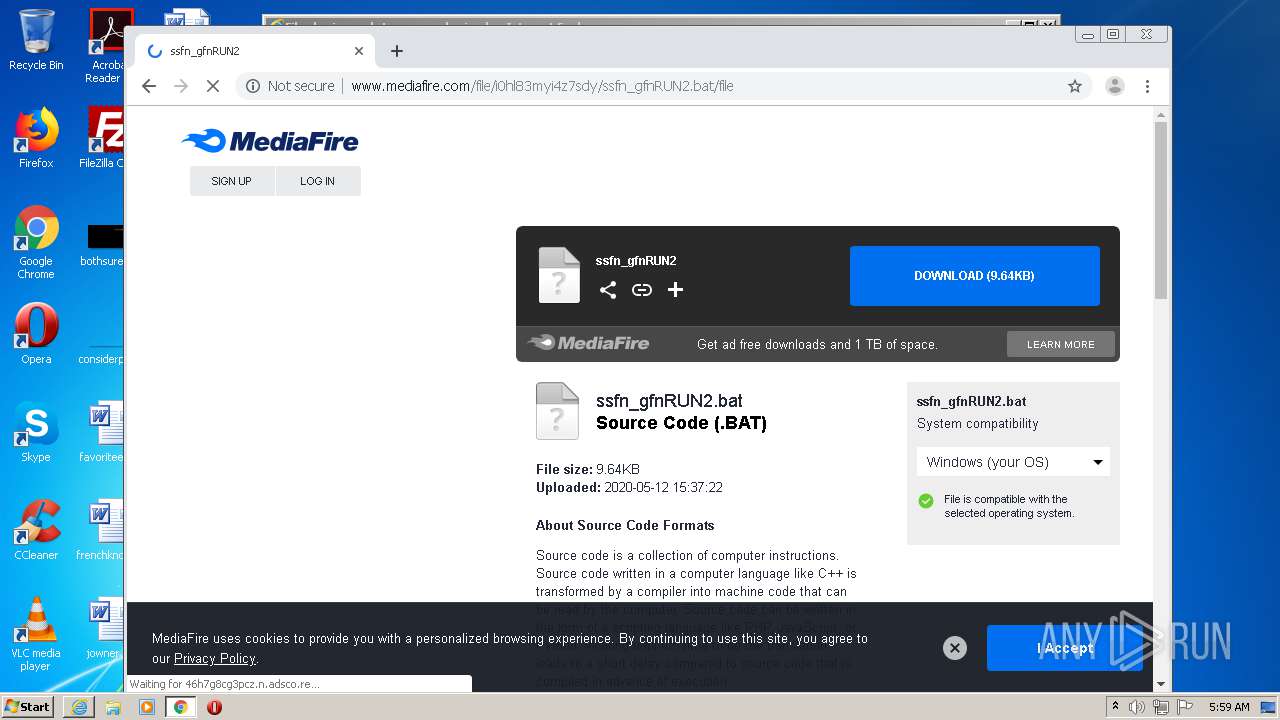
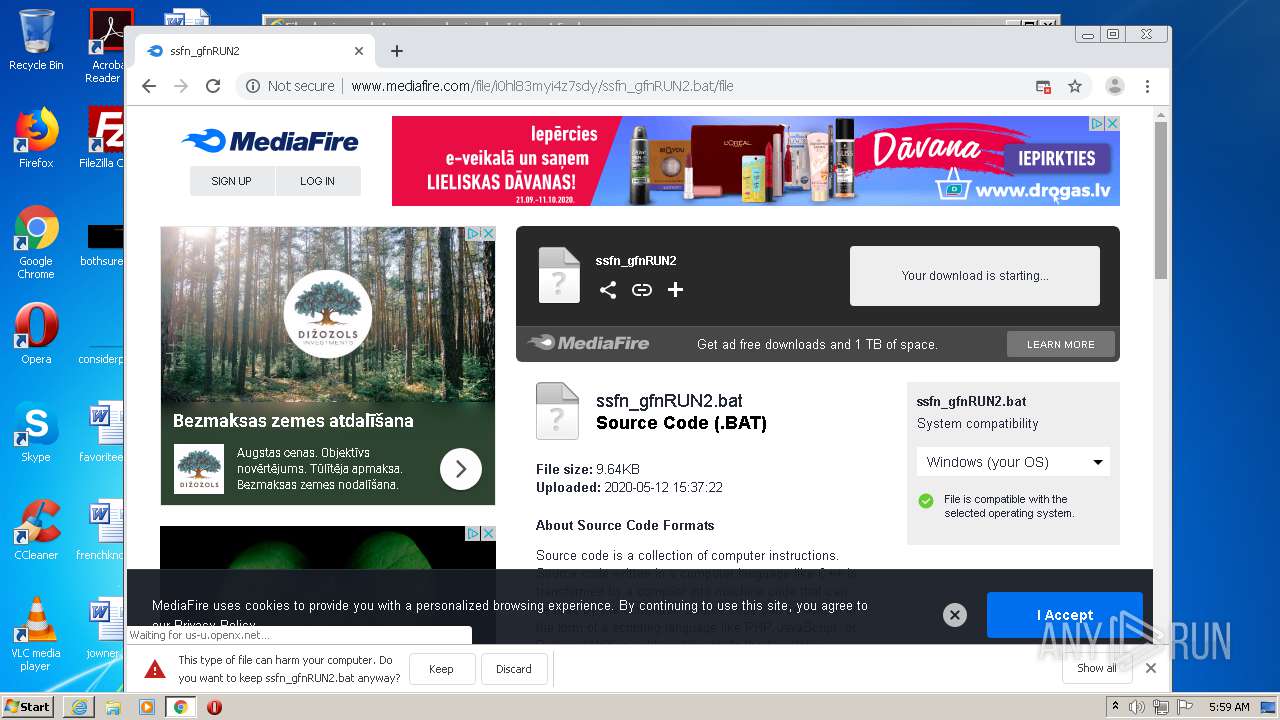
| twitterUrl: | http://www.mediafire.com/file/i0hl83myi4z7sdy/ssfn_gfnRUN2.bat/file |
| twitterTitle: | ssfn_gfnRUN2 |
| twitterImage: | https://static.mediafire.com/images/filetype/download/web.jpg |
| twitterDescription: | - |
Total processes
89
Monitored processes
49
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 544 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1064,7454031971207988136,8046830832309247114,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=8338338650801302742 --mojo-platform-channel-handle=3860 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 780 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1064,7454031971207988136,8046830832309247114,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=18379148598696130475 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2252 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 940 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1064,7454031971207988136,8046830832309247114,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=1172973188071118686 --mojo-platform-channel-handle=3616 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1256 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1064,7454031971207988136,8046830832309247114,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=6510733520434276463 --mojo-platform-channel-handle=4788 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1492 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1064,7454031971207988136,8046830832309247114,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=18050688254433389526 --renderer-client-id=27 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3468 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1496 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1064,7454031971207988136,8046830832309247114,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15995023821740927235 --renderer-client-id=19 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3460 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1504 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1064,7454031971207988136,8046830832309247114,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9043749471434677162 --renderer-client-id=33 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3584 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1556 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1064,7454031971207988136,8046830832309247114,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=52897513633232290 --mojo-platform-channel-handle=3424 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1560 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1064,7454031971207988136,8046830832309247114,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7146116521437931047 --renderer-client-id=32 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3476 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1600 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6ee2a9d0,0x6ee2a9e0,0x6ee2a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
3 221
Read events
2 890
Write events
320
Delete events
11
Modification events
| (PID) Process: | (2536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1021009700 | |||
| (PID) Process: | (2536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30840550 | |||
| (PID) Process: | (2536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2536) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
181
Text files
161
Unknown types
39
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1748 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\CabC3FD.tmp | — | |
MD5:— | SHA256:— | |||
| 1748 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\TarC3FE.tmp | — | |
MD5:— | SHA256:— | |||
| 1748 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\ns[1].htm | — | |
MD5:— | SHA256:— | |||
| 1748 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CC197601BE0898B7B0FCC91FA15D8A69_F77E93D3799E633E2032BE8305A3BF08 | der | |
MD5:— | SHA256:— | |||
| 1748 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CC197601BE0898B7B0FCC91FA15D8A69_F77E93D3799E633E2032BE8305A3BF08 | binary | |
MD5:— | SHA256:— | |||
| 1748 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CC197601BE0898B7B0FCC91FA15D8A69_93BB5A29A73AA40D558BAE7D8E0C12DD | binary | |
MD5:— | SHA256:— | |||
| 1748 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CC197601BE0898B7B0FCC91FA15D8A69_93BB5A29A73AA40D558BAE7D8E0C12DD | der | |
MD5:— | SHA256:— | |||
| 1748 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_5FDD03068CBBD8A96F3AB9595BA10093 | binary | |
MD5:— | SHA256:— | |||
| 1748 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9FF67FB3141440EED32363089565AE60_65D8C47CB675C70272C50C4C3BC2CC03 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
107
TCP/UDP connections
215
DNS requests
134
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1748 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEAesusUTtVSRAgAAAAB6SwU%3D | US | der | 471 b | whitelisted |
1748 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
1748 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
1748 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEAyDrs7o0RpNCAAAAABXoKo%3D | US | der | 471 b | whitelisted |
1748 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEAWRAacF5BksN9S2vaFyNWQ%3D | US | der | 280 b | whitelisted |
1748 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDOs%2FDKHsIMiAIAAAAAeksR | US | der | 472 b | whitelisted |
1748 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEBN9U5yqfDGppDNwGWiEeo0%3D | US | der | 727 b | whitelisted |
1748 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
1748 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQh80WaEMqmyEvaHjlisSfVM4p8SAQUF9nWJSdn%2BTHCSUPZMDZEjGypT%2BsCEQCrtlwvlTWIWiXUsXkGJuoO | US | der | 472 b | whitelisted |
1748 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQh80WaEMqmyEvaHjlisSfVM4p8SAQUF9nWJSdn%2BTHCSUPZMDZEjGypT%2BsCEQCrtlwvlTWIWiXUsXkGJuoO | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 172.217.18.174:445 | translate.google.com | Google Inc. | US | whitelisted |
4 | System | 172.217.18.174:139 | translate.google.com | Google Inc. | US | whitelisted |
2536 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1748 | iexplore.exe | 142.250.74.195:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
1748 | iexplore.exe | 172.217.18.174:443 | translate.google.com | Google Inc. | US | whitelisted |
1748 | iexplore.exe | 216.58.212.130:443 | securepubads.g.doubleclick.net | Google Inc. | US | whitelisted |
1748 | iexplore.exe | 104.111.245.249:443 | c.aaxads.com | Akamai International B.V. | NL | whitelisted |
1748 | iexplore.exe | 104.19.214.37:443 | cdn.otnolatrnup.com | Cloudflare Inc | US | shared |
1748 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1748 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.googletagmanager.com |
| whitelisted |
translate.google.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
fundingchoicesmessages.google.com |
| whitelisted |
securepubads.g.doubleclick.net |
| whitelisted |
c.aaxads.com |
| whitelisted |
cdn.otnolatrnup.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2132 | iexplore.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
2940 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |
2940 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |
2940 | chrome.exe | A Network Trojan was detected | AV MALWARE Observed AuXML EK Redirect |
2940 | chrome.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |