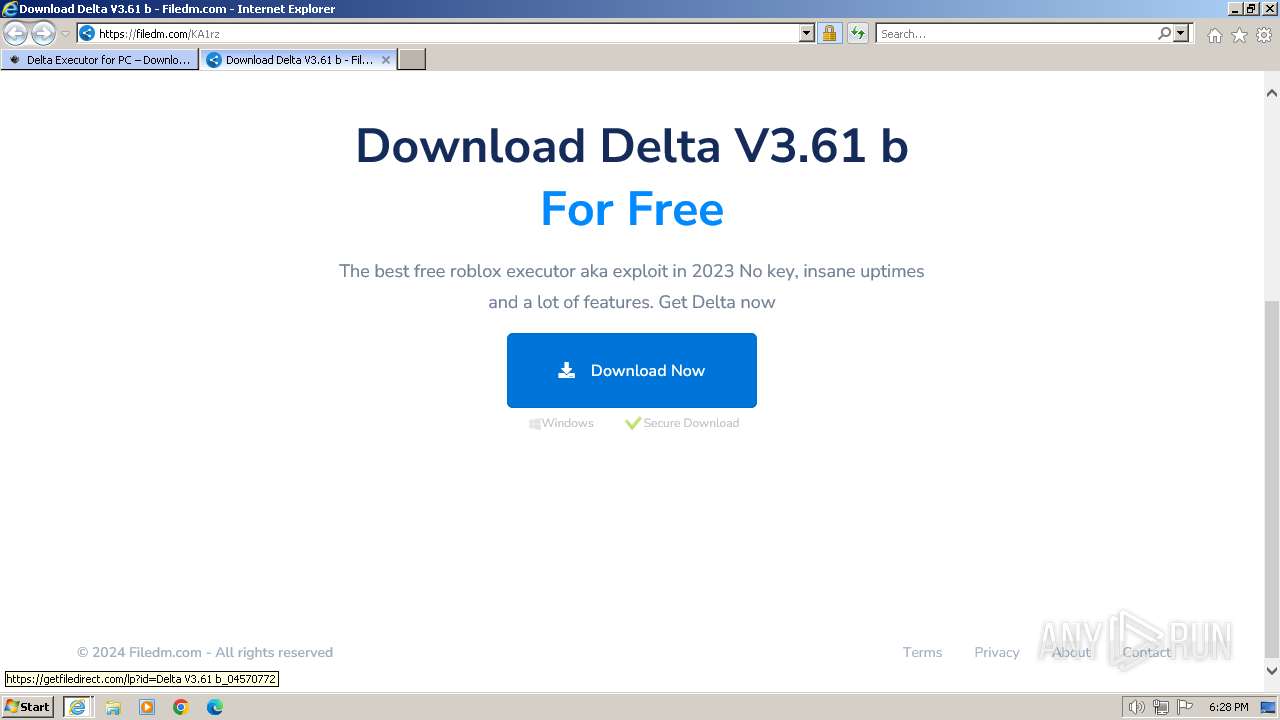
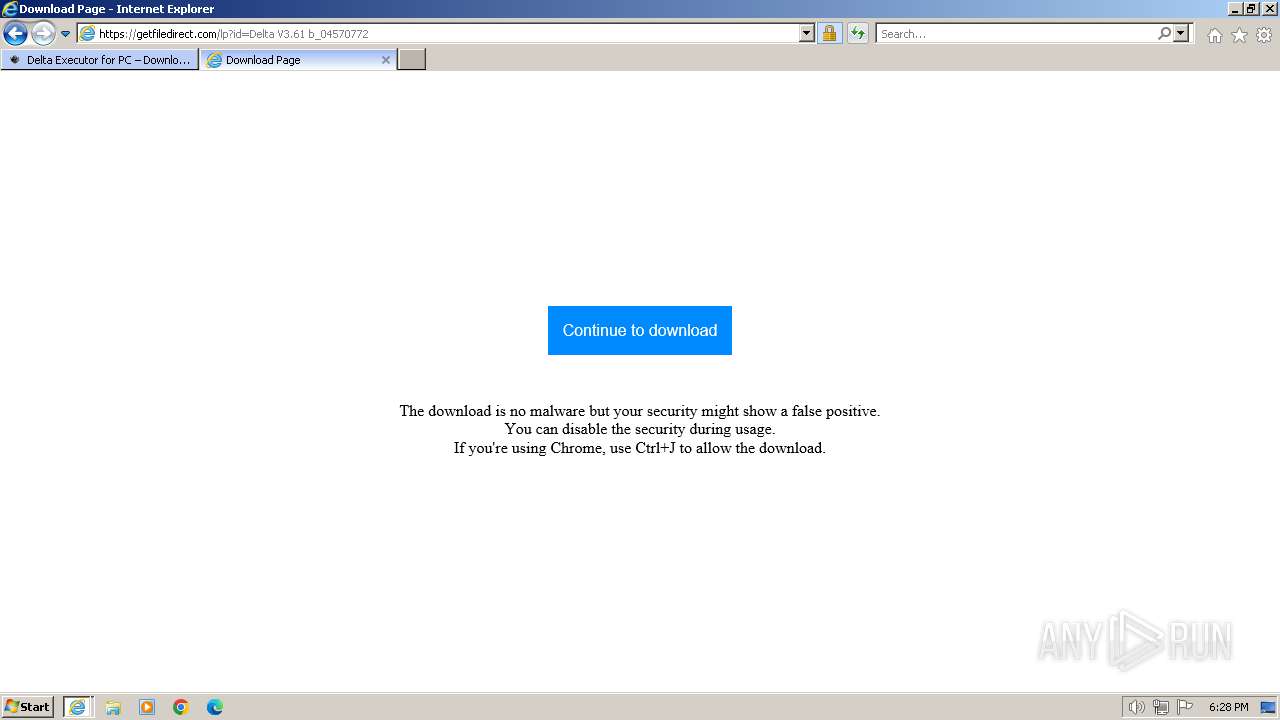
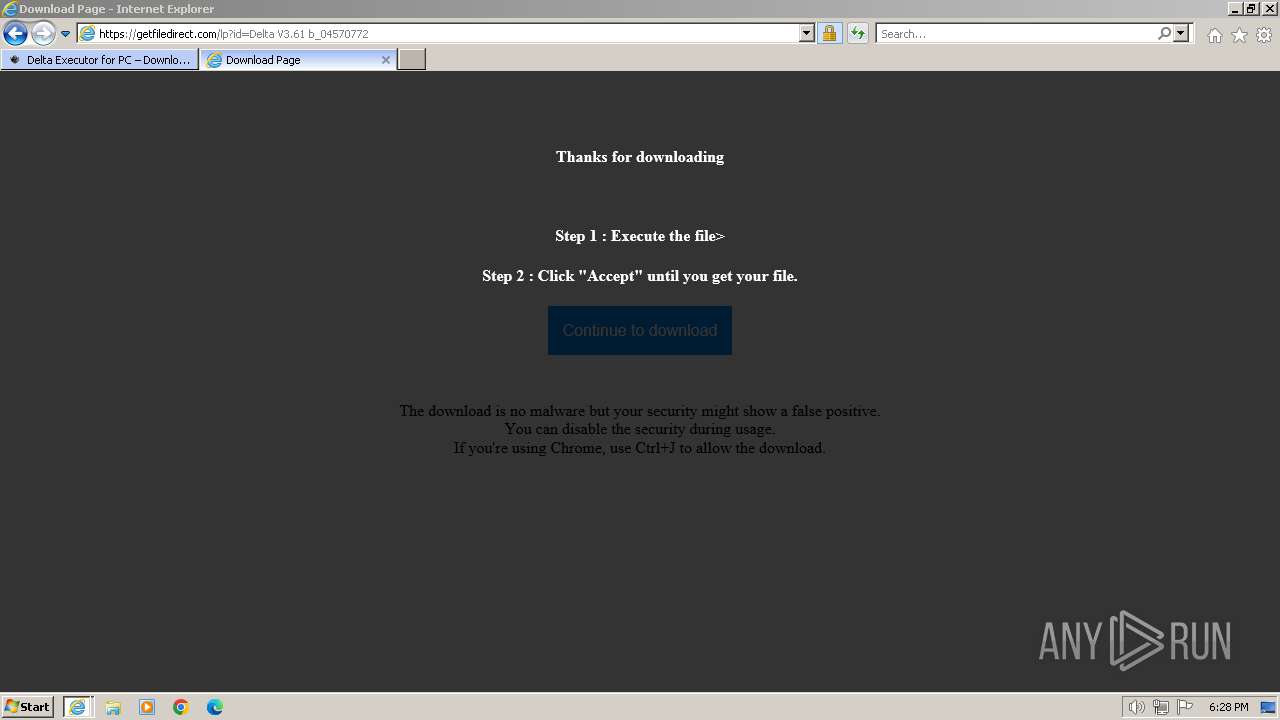
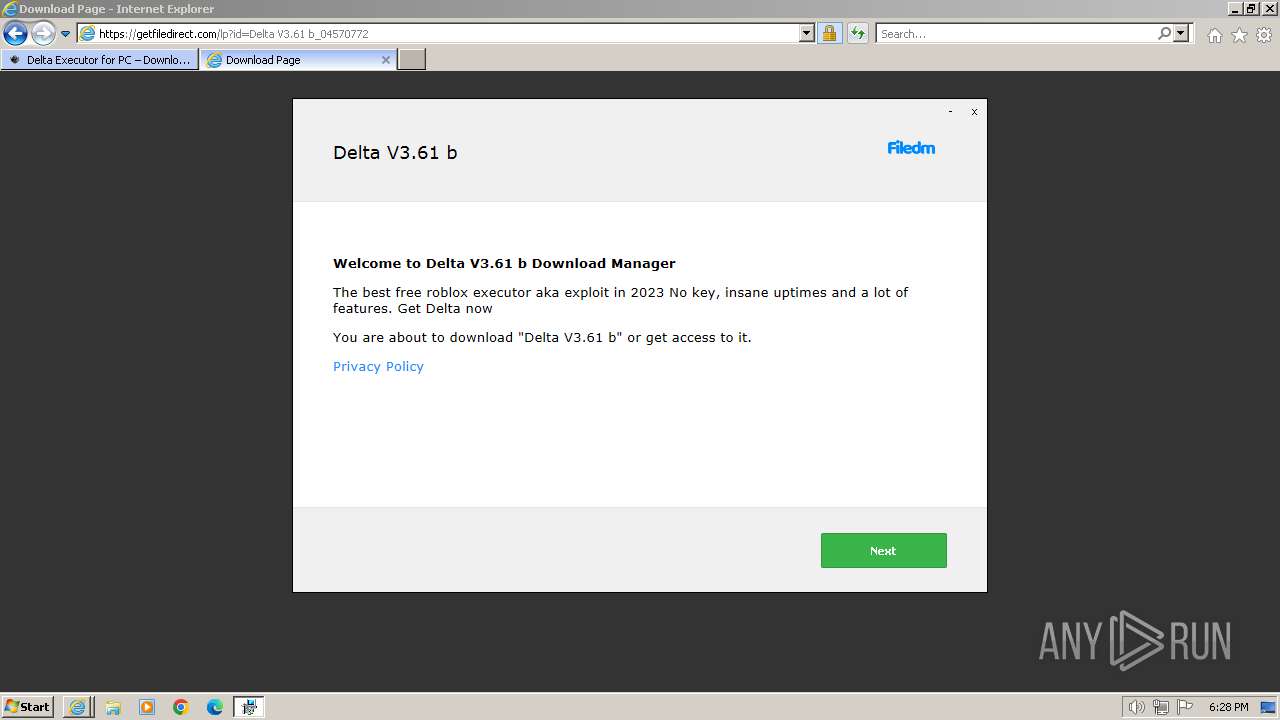
| URL: | https://deltaexecutor.io/delta-executor-for-pc/ |
| Full analysis: | https://app.any.run/tasks/0d381714-f285-4c1a-8c82-20435bc00fd8 |
| Verdict: | Malicious activity |
| Analysis date: | March 21, 2024, 18:27:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | C91183CC096D71213ECB58EFA1C710C1 |
| SHA1: | 6B58E90A401452103E74F06174092C8BCDADC865 |
| SHA256: | CB891863306B7D571DED4B0D1D8E48EF1DC787D777CBFBB8AE176C8AAD489870 |
| SSDEEP: | 3:N8YL/9i9qRNKXIVd:2YBi9qRNKXIVd |
MALICIOUS
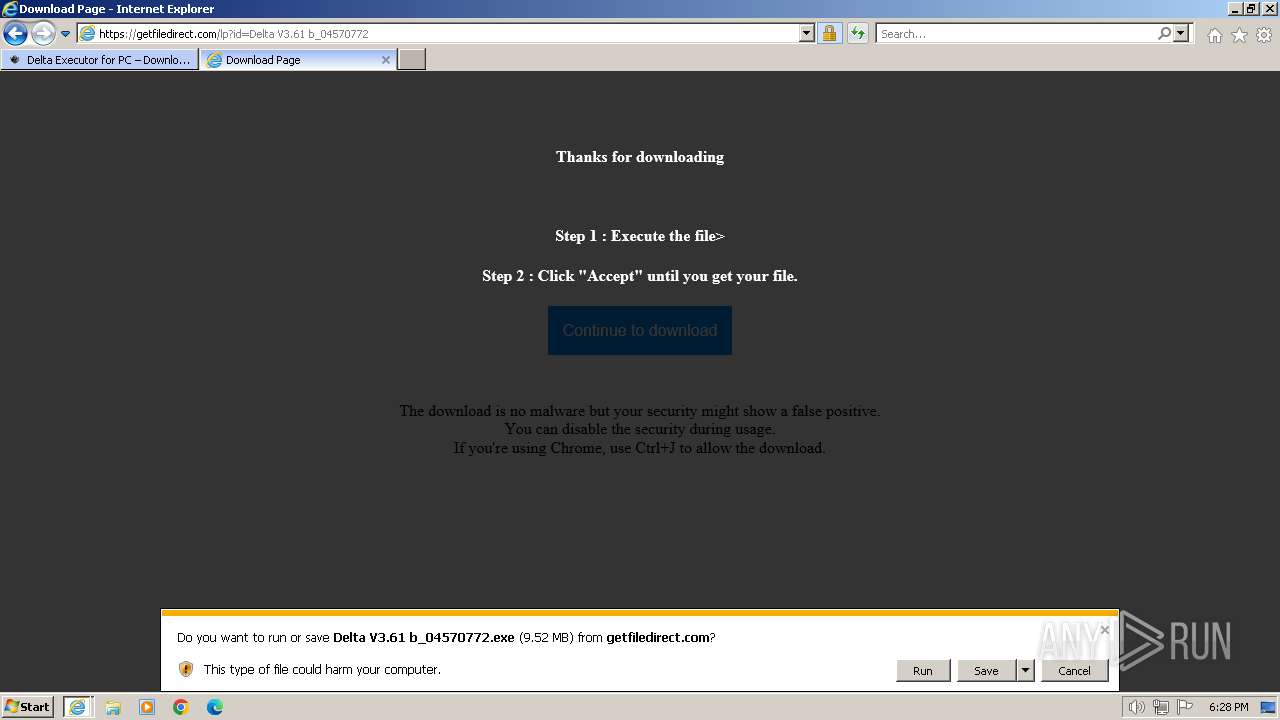
Drops the executable file immediately after the start
- Delta V3.61 b_04570772.exe (PID: 1232)
- setup04570772.exe (PID: 2588)
Actions looks like stealing of personal data
- setup04570772.exe (PID: 2588)
- OfferInstaller.exe (PID: 4072)
SUSPICIOUS
Reads security settings of Internet Explorer
- Delta V3.61 b_04570772.exe (PID: 1232)
- setup04570772.exe (PID: 2588)
- setup04570772.exe (PID: 2344)
- OfferInstaller.exe (PID: 4072)
Reads the Internet Settings
- Delta V3.61 b_04570772.exe (PID: 1232)
- setup04570772.exe (PID: 2588)
- setup04570772.exe (PID: 2344)
- OfferInstaller.exe (PID: 4072)
- cmd.exe (PID: 2556)
Reads settings of System Certificates
- Delta V3.61 b_04570772.exe (PID: 1232)
- setup04570772.exe (PID: 2588)
- OfferInstaller.exe (PID: 4072)
Checks Windows Trust Settings
- Delta V3.61 b_04570772.exe (PID: 1232)
- setup04570772.exe (PID: 2588)
Executable content was dropped or overwritten
- Delta V3.61 b_04570772.exe (PID: 1232)
- setup04570772.exe (PID: 2588)
Process drops legitimate windows executable
- setup04570772.exe (PID: 2588)
The process drops C-runtime libraries
- setup04570772.exe (PID: 2588)
The process creates files with name similar to system file names
- setup04570772.exe (PID: 2588)
Reads the Windows owner or organization settings
- setup04570772.exe (PID: 2588)
- OfferInstaller.exe (PID: 4072)
Adds/modifies Windows certificates
- setup04570772.exe (PID: 2588)
- Delta V3.61 b_04570772.exe (PID: 1232)
Starts CMD.EXE for commands execution
- setup04570772.exe (PID: 2588)
- OfferInstaller.exe (PID: 4072)
Executing commands from a ".bat" file
- setup04570772.exe (PID: 2588)
- OfferInstaller.exe (PID: 4072)
Searches for installed software
- setup04570772.exe (PID: 2588)
Get information on the list of running processes
- cmd.exe (PID: 1264)
- cmd.exe (PID: 2152)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1264)
- cmd.exe (PID: 2152)
Start notepad (likely ransomware note)
- Delta V3.61 b_04570772.exe (PID: 1232)
INFO
Drops the executable file immediately after the start
- iexplore.exe (PID: 1352)
- iexplore.exe (PID: 2124)
Checks supported languages
- Delta V3.61 b_04570772.exe (PID: 1232)
- setup04570772.exe (PID: 2588)
- setup04570772.exe (PID: 2344)
- OfferInstaller.exe (PID: 4072)
Executable content was dropped or overwritten
- iexplore.exe (PID: 2124)
- iexplore.exe (PID: 1352)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2124)
Reads the computer name
- Delta V3.61 b_04570772.exe (PID: 1232)
- setup04570772.exe (PID: 2588)
- setup04570772.exe (PID: 2344)
- OfferInstaller.exe (PID: 4072)
The process uses the downloaded file
- iexplore.exe (PID: 2124)
Checks proxy server information
- Delta V3.61 b_04570772.exe (PID: 1232)
Reads the machine GUID from the registry
- Delta V3.61 b_04570772.exe (PID: 1232)
- setup04570772.exe (PID: 2588)
- setup04570772.exe (PID: 2344)
- OfferInstaller.exe (PID: 4072)
Reads the software policy settings
- Delta V3.61 b_04570772.exe (PID: 1232)
- setup04570772.exe (PID: 2588)
- OfferInstaller.exe (PID: 4072)
Creates files or folders in the user directory
- Delta V3.61 b_04570772.exe (PID: 1232)
- setup04570772.exe (PID: 2588)
- OfferInstaller.exe (PID: 4072)
Application launched itself
- iexplore.exe (PID: 2124)
Create files in a temporary directory
- setup04570772.exe (PID: 2588)
- setup04570772.exe (PID: 2344)
- OfferInstaller.exe (PID: 4072)
Reads product name
- setup04570772.exe (PID: 2588)
- OfferInstaller.exe (PID: 4072)
Reads Environment values
- setup04570772.exe (PID: 2588)
- OfferInstaller.exe (PID: 4072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
75
Monitored processes
27
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2124 CREDAT:1447214 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 680 | timeout 1 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 784 | find /I "4072" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 968 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\Delta V3.61 b_04570772.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\Delta V3.61 b_04570772.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Download Manager Exit code: 3221226540 Version: 1 Modules
| |||||||||||||||
| 1232 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\Delta V3.61 b_04570772.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\Delta V3.61 b_04570772.exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Download Manager Exit code: 0 Version: 1 Modules
| |||||||||||||||
| 1264 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\H2OCleanup.bat"" | C:\Windows\System32\cmd.exe | — | setup04570772.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1352 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2124 CREDAT:3544328 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1644 | tasklist /FI "PID eq 4072" /fo csv | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1784 | timeout 5 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1832 | find /I "4072" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
76 258
Read events
75 784
Write events
325
Delete events
149
Modification events
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31095741 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31095741 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
26
Suspicious files
46
Text files
138
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3276 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\delta-executor-for-pc[1].htm | html | |
MD5:4165D40A912DAB4BFA847FC27F8A7C32 | SHA256:5DCF1C3424F0AD05668739816E94F642A7840485A901B60A5A8CA23BB9C80CCB | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:E74078AD57B78A955E62033380373C61 | SHA256:23871E0126135C1D68926075B5B06A962EBE3763663CDE3905134D972768A4A0 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:4B9A5099394ECADD3B90D3C9C2F1BCD5 | SHA256:68F9E4FBC92999C30F3862F365254637E5A758DCDDC040297F93CFCA605E9625 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | der | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:608881BCCD83BD848D8E1C5E44052740 | SHA256:FE4388C8A609D41BF65A8925F7002372FD327DE30AF9CBF98C0CDD93D395F7D5 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:21D83A23A0F0EF691E41F21D17A7DCDA | SHA256:C1B46ADF6B6EC12122EA3E75A3A51B5F4F097B1E17D72CFD9CB1231237FA6C0F | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\99dcc34588d28936d20fddedf28c189e[1].js | text | |
MD5:D4E2CC40B93D01B499540895A18D141B | SHA256:58BE289D9FB1732377111525D26BBB08FFF8C43911CE0DCA9415347C5C63EC59 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:12F3FCAB4E09D4C415F729EBF97BF4A8 | SHA256:B103E7E3F2FD929F438A01B6FCF27BADF55D555D496CFAC11DEEB651998798B0 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\265C0DEB29181DD1891051371C5F863A_EBA017AD8B5E69D2B53583F745E38C07 | der | |
MD5:8248D4F4D3EA4A08289DE7B51F965094 | SHA256:2C09CC9E960032BBA97F463D6BC531E65F6ECCE74A3E27D46626339876627E25 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
114
DNS requests
60
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3276 | iexplore.exe | GET | 304 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7f30423e8f7249ff | unknown | — | — | unknown |
3276 | iexplore.exe | GET | 304 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5259f1aa84763c8c | unknown | — | — | unknown |
3276 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3276 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
3276 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3276 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDS57q68k6VpwlSRtIvj9A4 | unknown | binary | 472 b | unknown |
3276 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQD6BeWhIbleexId20FpK0af | unknown | binary | 472 b | unknown |
3276 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDBS5NY4gwYhxCot62SBiap | unknown | binary | 472 b | unknown |
2124 | iexplore.exe | GET | 304 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?70d85e3b0e586cab | unknown | — | — | unknown |
2124 | iexplore.exe | GET | 304 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e55f0cb727843010 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3276 | iexplore.exe | 188.114.97.3:443 | deltaexecutor.io | CLOUDFLARENET | NL | unknown |
3276 | iexplore.exe | 184.24.77.194:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3276 | iexplore.exe | 172.217.18.99:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3276 | iexplore.exe | 172.217.23.98:443 | pagead2.googlesyndication.com | GOOGLE | US | whitelisted |
3276 | iexplore.exe | 172.217.16.200:443 | www.googletagmanager.com | GOOGLE | US | whitelisted |
3276 | iexplore.exe | 172.217.16.202:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
deltaexecutor.io |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
region1.google-analytics.com |
| whitelisted |
tpc.googlesyndication.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
Threats
7 ETPRO signatures available at the full report
Process | Message |
|---|---|
Delta V3.61 b_04570772.exe | |
Delta V3.61 b_04570772.exe | at getFileInfo.@285@39 (this://app/main.html(307))
|
Delta V3.61 b_04570772.exe | Error: (undefined) has no property - value
|
Delta V3.61 b_04570772.exe | at initializeDynamicVariables (this://app/main.html(329))
|
Delta V3.61 b_04570772.exe | |
setup04570772.exe | at sciter:init-script.tis
|
setup04570772.exe | file:resources/tis/TranslateOfferTemplate.tis(82) : warning :'async' does not contain any 'await'
|
setup04570772.exe | |
setup04570772.exe | |
setup04570772.exe | Error: File not found - sciterwrapper:console.tis
|