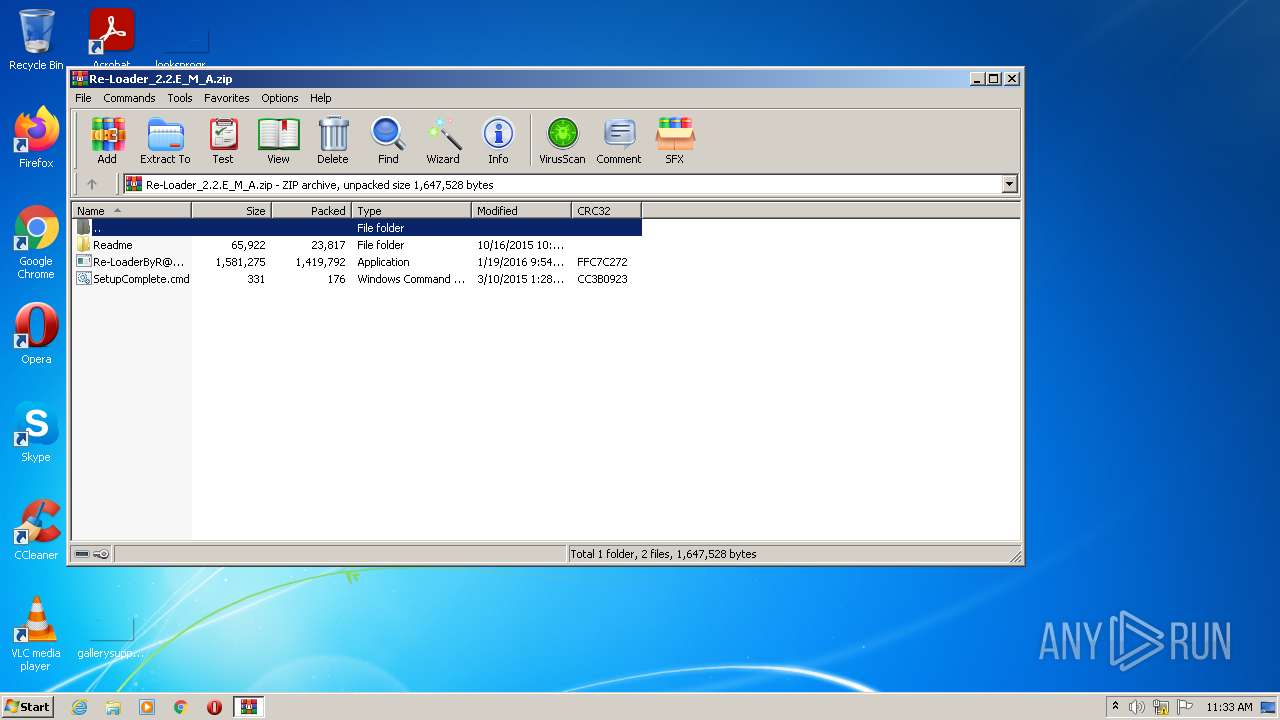
| File name: | Re-Loader_2.2.E_M_A.zip |
| Full analysis: | https://app.any.run/tasks/861d298e-a374-453c-a24d-bd00f7a6b2e8 |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2022, 10:33:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 4AD97213F92C5A65F64DA72B5A168A53 |
| SHA1: | 2ED8A07092F476155ECFDF6962CD70F772794F99 |
| SHA256: | CB7A1E88EBEEF643537CA8ACEDFF68F8EA5BE7802A7768813B4D2EACBC4B5368 |
| SSDEEP: | 24576:wEK6GoKe1iMRwQAp/U3seqXs+fqtWg0UspguYR2lnTnrUGh1OGo:lZKewMRwQ3pqDfqQgFuo2xTRhBo |
MALICIOUS
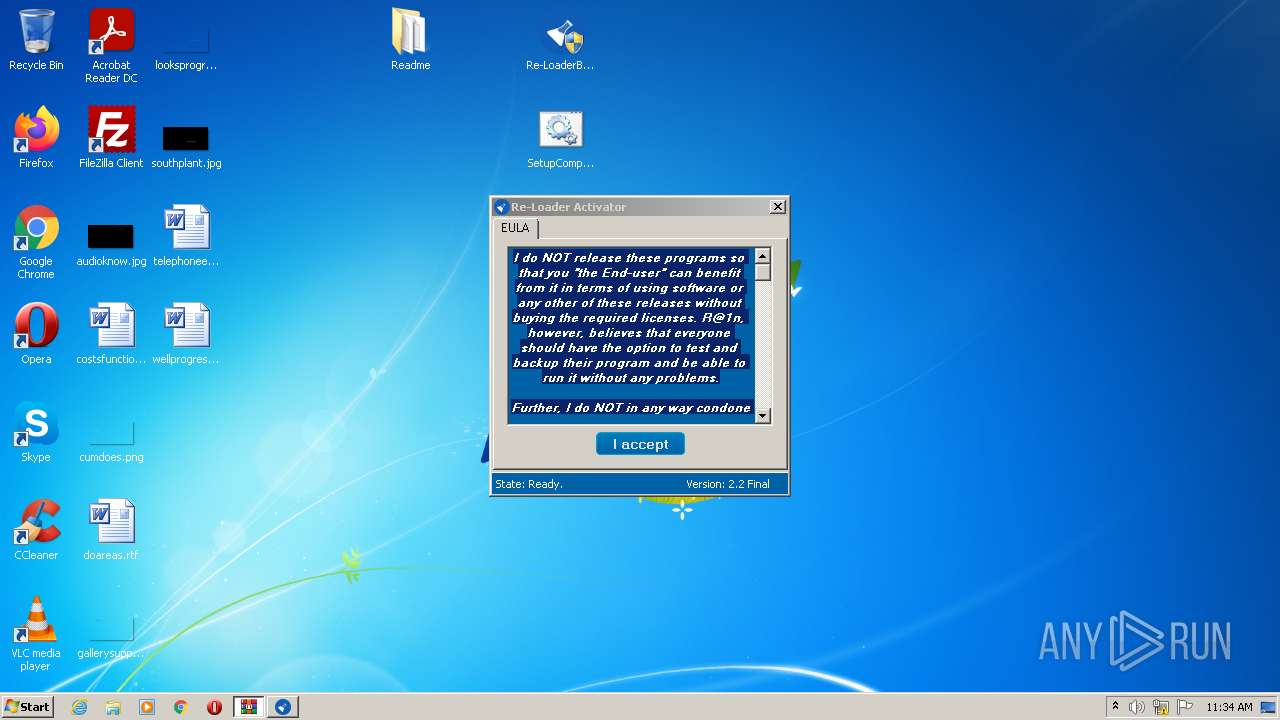
Application was dropped or rewritten from another process
- Re-LoaderByR@1n.exe (PID: 940)
- Re-LoaderByR@1n.exe (PID: 3664)
Drops executable file immediately after starts
- WinRAR.exe (PID: 2976)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 2976)
- Re-LoaderByR@1n.exe (PID: 940)
Checks supported languages
- WinRAR.exe (PID: 2976)
- Re-LoaderByR@1n.exe (PID: 940)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2976)
Reads Environment values
- Re-LoaderByR@1n.exe (PID: 940)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 2976)
Reads Windows Product ID
- Re-LoaderByR@1n.exe (PID: 940)
INFO
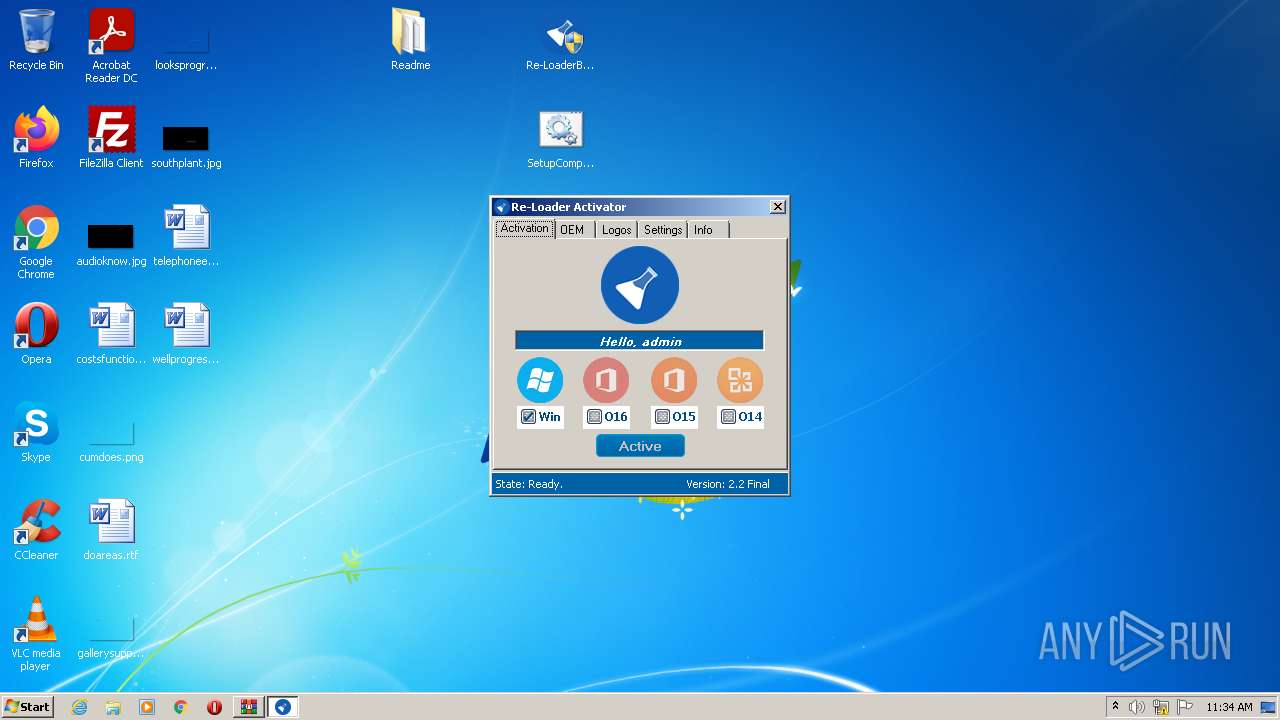
Manual execution by user
- Re-LoaderByR@1n.exe (PID: 3664)
- Re-LoaderByR@1n.exe (PID: 940)
Reads Microsoft Office registry keys
- Re-LoaderByR@1n.exe (PID: 940)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | SetupComplete.cmd |
|---|---|
| ZipUncompressedSize: | 331 |
| ZipCompressedSize: | 176 |
| ZipCRC: | 0xcc3b0923 |
| ZipModifyDate: | 2015:03:10 14:28:20 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
43
Monitored processes
3
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 940 | "C:\Users\admin\Desktop\Re-LoaderByR@1n.exe" | C:\Users\admin\Desktop\Re-LoaderByR@1n.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Description: Activator Exit code: 0 Version: 2.2.3.0 Modules
| |||||||||||||||
| 2976 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Re-Loader_2.2.E_M_A.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3664 | "C:\Users\admin\Desktop\Re-LoaderByR@1n.exe" | C:\Users\admin\Desktop\Re-LoaderByR@1n.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: Activator Exit code: 3221226540 Version: 2.2.3.0 Modules
| |||||||||||||||
Total events
1 423
Read events
1 403
Write events
20
Delete events
0
Modification events
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Re-Loader_2.2.E_M_A.zip | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
0
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2976.41039\Readme\自述.txt | text | |
MD5:932390B97A626CFFCAC17E821CCE1013 | SHA256:3616FFEA81B4193A3C4A78CF25659F6B7AEC9AD57CBA5D6BEE6EE7133D828D53 | |||
| 2976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2976.41039\Readme\Leggimi.txt | text | |
MD5:40FE72F3FE7A700E6809201308CDC888 | SHA256:0DBDA4AA5446490825E80B2B4432134EA263E78FFB614F9FFDD808E951E9CC91 | |||
| 2976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2976.41039\SetupComplete.cmd | text | |
MD5:21A93C0F93EE99F60ADF82478FC19C65 | SHA256:353413C1C76EF3FB63EE05414474A1B90537B34E0D1584BD79D159A0B0602AEA | |||
| 2976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2976.41039\Readme\Readme.txt | text | |
MD5:963F908CE0ED3D8EB251F2205F91139F | SHA256:46AFEE6C920CE80769A0C845CDCB4B4E2F571E0E238FA6087A14BC71171E7F06 | |||
| 2976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2976.41039\Re-LoaderByR@1n.exe | executable | |
MD5:3C8289913E7994117532856CAEE1C06C | SHA256:391C989D2103DD488D9D4C2C8E1776BC6264F613656BB5BEBCD7722DB22160E7 | |||
| 2976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2976.41039\Readme\Lisezmoi.txt | text | |
MD5:E2C6426E8F78CF30F14D93968A90CF7F | SHA256:E08EA033BF758F3F9601D6AA2D23ACA55EE307473B42DB9A63367597C048D07A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report