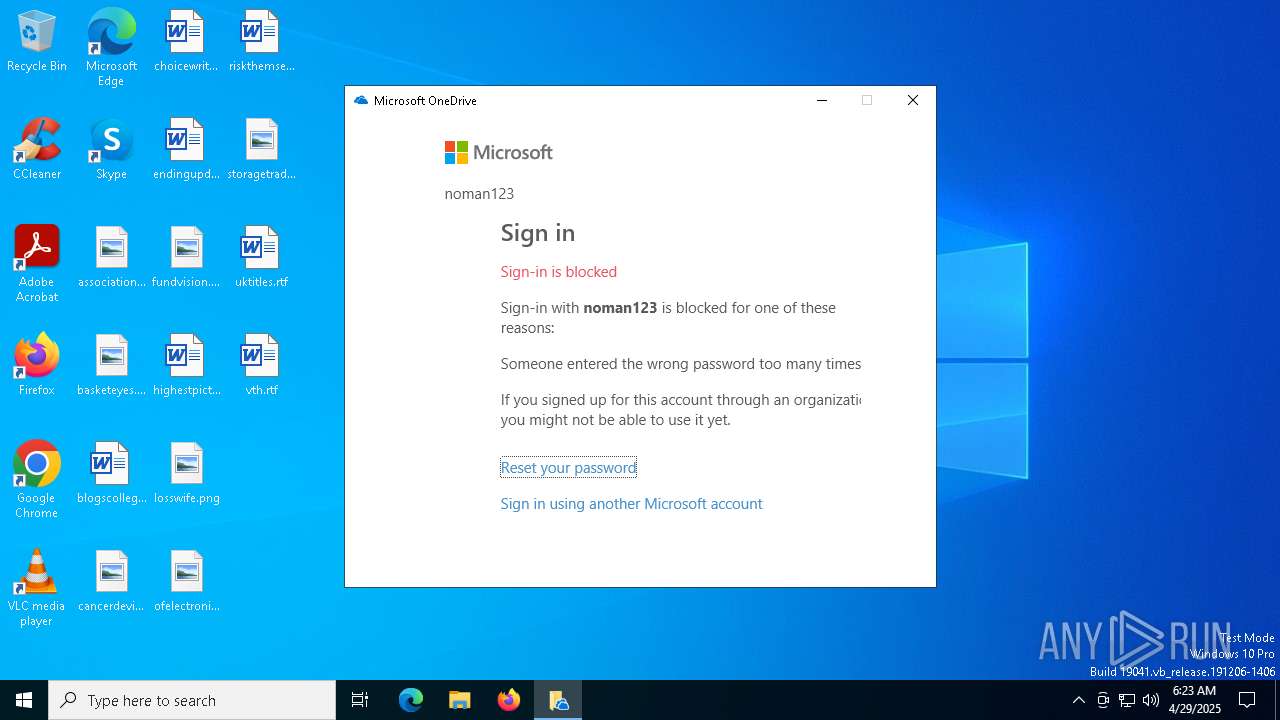
| File name: | Personal Vault.lnk |
| Full analysis: | https://app.any.run/tasks/1d4ac2c8-9b15-43d7-8cc3-fa38aebb998b |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 06:22:12 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-ms-shortcut |
| File info: | MS Windows shortcut, Item id list present, Icon number=-524, Unicoded, HasExpIcon "%ProgramFiles%\Microsoft OneDrive\25.065.0406.0002\FileSync.Resources.dll", length=0, window=normal, IDListSize 0x0076, Root folder "871C5380-42A0-1069-A2EA-08002B30309D" |
| MD5: | B7BAFFAA9D6291E51151E3187F075A6C |
| SHA1: | 981E00D2AC7A1E47B7B4636885CBA90A2514AB28 |
| SHA256: | CB4FB003D806B1A41BFA5FBFFC0B46AB990AEA16CF59466D5FD20DEC1B8867CF |
| SSDEEP: | 12:8NPHalsOXccldu/+bdpEL3ewmJPkuSqfc3AtbOwL3ewm:8NPHalsOXflAadBwm3vfcwtkwm |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates/Modifies COM task schedule object
- OneDrive.exe (PID: 1072)
Reads security settings of Internet Explorer
- OneDrive.exe (PID: 1072)
Reads Microsoft Outlook installation path
- OneDrive.exe (PID: 1072)
There is functionality for taking screenshot (YARA)
- OneDrive.exe (PID: 1072)
Reads Internet Explorer settings
- OneDrive.exe (PID: 1072)
INFO
Reads the machine GUID from the registry
- OneDrive.exe (PID: 1072)
Checks supported languages
- OneDrive.exe (PID: 1072)
Creates files or folders in the user directory
- OneDrive.exe (PID: 1072)
Create files in a temporary directory
- OneDrive.exe (PID: 1072)
Reads CPU info
- OneDrive.exe (PID: 1072)
Reads the computer name
- OneDrive.exe (PID: 1072)
Reads the time zone
- OneDrive.exe (PID: 1072)
Checks proxy server information
- OneDrive.exe (PID: 1072)
- slui.exe (PID: 3240)
Reads the software policy settings
- OneDrive.exe (PID: 1072)
- slui.exe (PID: 5280)
- slui.exe (PID: 3240)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | IDList, IconFile, Unicode, ExpIcon |
|---|---|
| FileAttributes: | (none) |
| TargetFileSize: | - |
| IconIndex: | 4294966772 |
| RunWindow: | Normal |
| HotKey: | (none) |
| IconFileName: | C:\Program Files\Microsoft OneDrive\25.065.0406.0002\FileSync.Resources.dll |
Total processes
134
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1072 | "C:\Users\admin\AppData\Local\Microsoft\OneDrive\OneDrive.exe" /url:"odopen://unlockVault/?accounttype=personal" | C:\Users\admin\AppData\Local\Microsoft\OneDrive\OneDrive.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDrive Version: 19.043.0304.0013 Modules
| |||||||||||||||
| 3240 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4268 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5280 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 147
Read events
4 976
Write events
164
Delete events
7
Modification events
| (PID) Process: | (1072) OneDrive.exe | Key: | HKEY_CLASSES_ROOT\AppID\OneDrive.EXE |
| Operation: | write | Name: | AppID |
Value: {EEABD3A3-784D-4334-AAFC-BB13234F17CF} | |||
| (PID) Process: | (1072) OneDrive.exe | Key: | HKEY_CLASSES_ROOT\FileSyncClient.AutoPlayHandler\shell\import\DropTarget |
| Operation: | write | Name: | CLSID |
Value: {5999E1EE-711E-48D2-9884-851A709F543D} | |||
| (PID) Process: | (1072) OneDrive.exe | Key: | HKEY_CLASSES_ROOT\BannerNotificationHandler.BannerNotificationHandler\shell\import\DropTarget |
| Operation: | write | Name: | CLSID |
Value: {2e7c0a19-0438-41e9-81e3-3ad3d64f55ba} | |||
| (PID) Process: | (1072) OneDrive.exe | Key: | HKEY_CLASSES_ROOT\Interface\{F0AF7C30-EAE4-4644-961D-54E6E28708D6}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (1072) OneDrive.exe | Key: | HKEY_CLASSES_ROOT\WOW6432Node\Interface\{F0AF7C30-EAE4-4644-961D-54E6E28708D6}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (1072) OneDrive.exe | Key: | HKEY_CLASSES_ROOT\Interface\{9D613F8A-B30E-4938-8490-CB5677701EBF}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (1072) OneDrive.exe | Key: | HKEY_CLASSES_ROOT\WOW6432Node\Interface\{9D613F8A-B30E-4938-8490-CB5677701EBF}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (1072) OneDrive.exe | Key: | HKEY_CLASSES_ROOT\Interface\{79A2A54C-3916-41FD-9FAB-F26ED0BBA755}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (1072) OneDrive.exe | Key: | HKEY_CLASSES_ROOT\WOW6432Node\Interface\{79A2A54C-3916-41FD-9FAB-F26ED0BBA755}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (1072) OneDrive.exe | Key: | HKEY_CLASSES_ROOT\Interface\{0299ECA9-80B6-43C8-A79A-FB1C5F19E7D8}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
Executable files
0
Suspicious files
63
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1072 | OneDrive.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Personal\telemetryCache.otc.session | binary | |
MD5:580BD824DEBBA908591408D7A5A3D01F | SHA256:B3218FF93047231A34C6962C758A36D412C2EB928C33F7EE537023EB6E489974 | |||
| 1072 | OneDrive.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Personal\SyncEngine-2025-04-29.0622.1072.1.aodl | binary | |
MD5:28DCA2FF4B34B5A52A2E59DF202A6ED3 | SHA256:33BACCB7296F1ED1F995FC77A23049F261CF391AC0388F9E8DD161F8C17B7F94 | |||
| 1072 | OneDrive.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:5EB5DEF34748487EED3D8E6DCA5EB602 | SHA256:C0812947766BE364B42982863484259B68AA17B56977410060B47F501AB118FE | |||
| 1072 | OneDrive.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\update100[1].xml | xml | |
MD5:53244E542DDF6D280A2B03E28F0646B7 | SHA256:36A6BD38A8A6F5A75B73CAFFAE5AE66DFABCAEFD83DA65B493FA881EA8A64E7D | |||
| 1072 | OneDrive.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Personal\TraceArchive.0304.0013-36.etl | binary | |
MD5:97596EEBD1886A7637AEC1F4739959FC | SHA256:43A342C94BDA9B236D3D1F45711C0B2FB9FA179CF7E0C9252E6DB0EE1930811F | |||
| 1072 | OneDrive.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:C34AC1799819FB5714A68FED8151E5AD | SHA256:51FC76DB443E4844B93E07DAD39FD5613F8EC1561E43D63DEF1E7BFB3510ECD4 | |||
| 1072 | OneDrive.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:DA6E9864BBFF48AB396CAEF80F97CEE7 | SHA256:D5AF67D3F89A3E92F8A658DA6D855844591BF765F7D52E4E849F72F3CF98A9BB | |||
| 1072 | OneDrive.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\Update\update.xml | xml | |
MD5:53244E542DDF6D280A2B03E28F0646B7 | SHA256:36A6BD38A8A6F5A75B73CAFFAE5AE66DFABCAEFD83DA65B493FA881EA8A64E7D | |||
| 1072 | OneDrive.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\settings\PreSignInSettingsConfig.json | binary | |
MD5:E516A60BC980095E8D156B1A99AB5EEE | SHA256:543796A1B343B4EBC0285D89CB8EB70667AC7B513DA37495E38003704E9D88D7 | |||
| 1072 | OneDrive.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Personal\telemetryCache.otc.session-journal | binary | |
MD5:C464CD2F6DC43EF9C6DE5A2381BDFE3A | SHA256:6627326F35E3D65F025EE1AF77F87BFA9ABA2F647D9F9B1D5E8314E8FC46999B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
35
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1072 | OneDrive.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1072 | OneDrive.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
1072 | OneDrive.exe | GET | 302 | 95.100.186.9:80 | http://go.microsoft.com/fwlink/?LinkId=735053 | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1276 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1276 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1072 | OneDrive.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
1072 | OneDrive.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5780 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1072 | OneDrive.exe | 13.74.129.92:443 | g.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1072 | OneDrive.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
g.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
oneclient.sfx.ms |
| unknown |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |