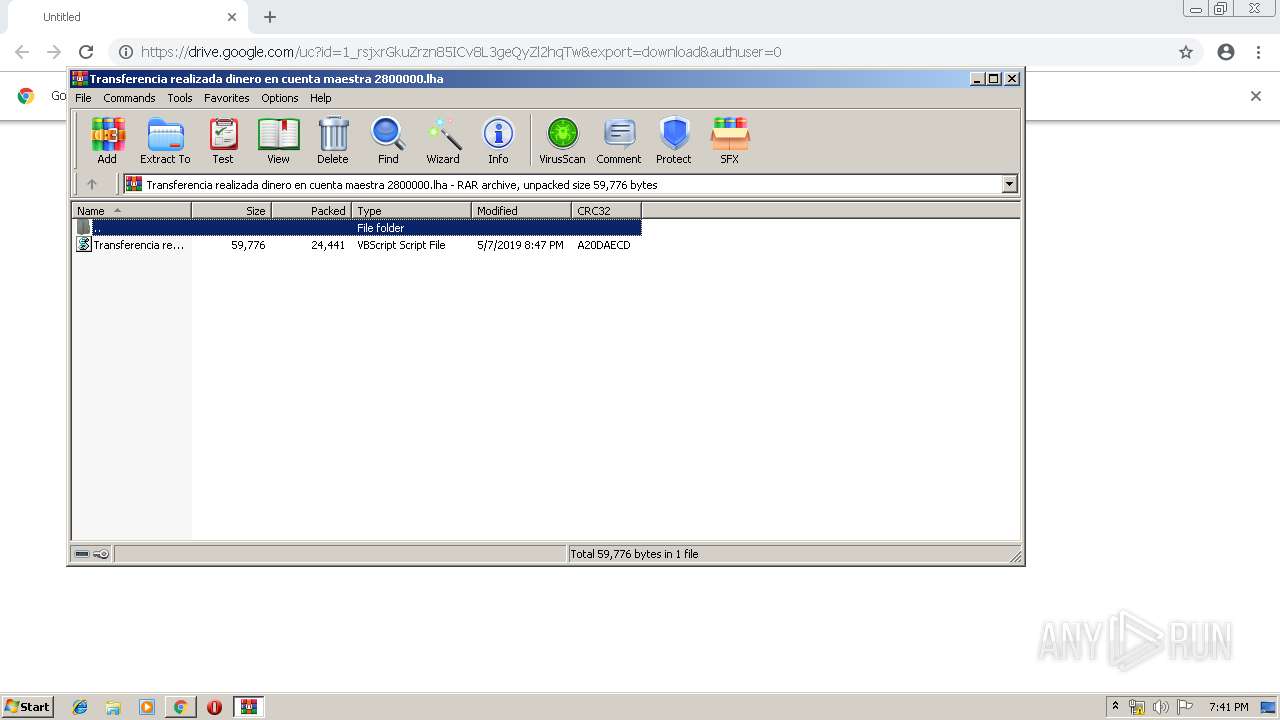
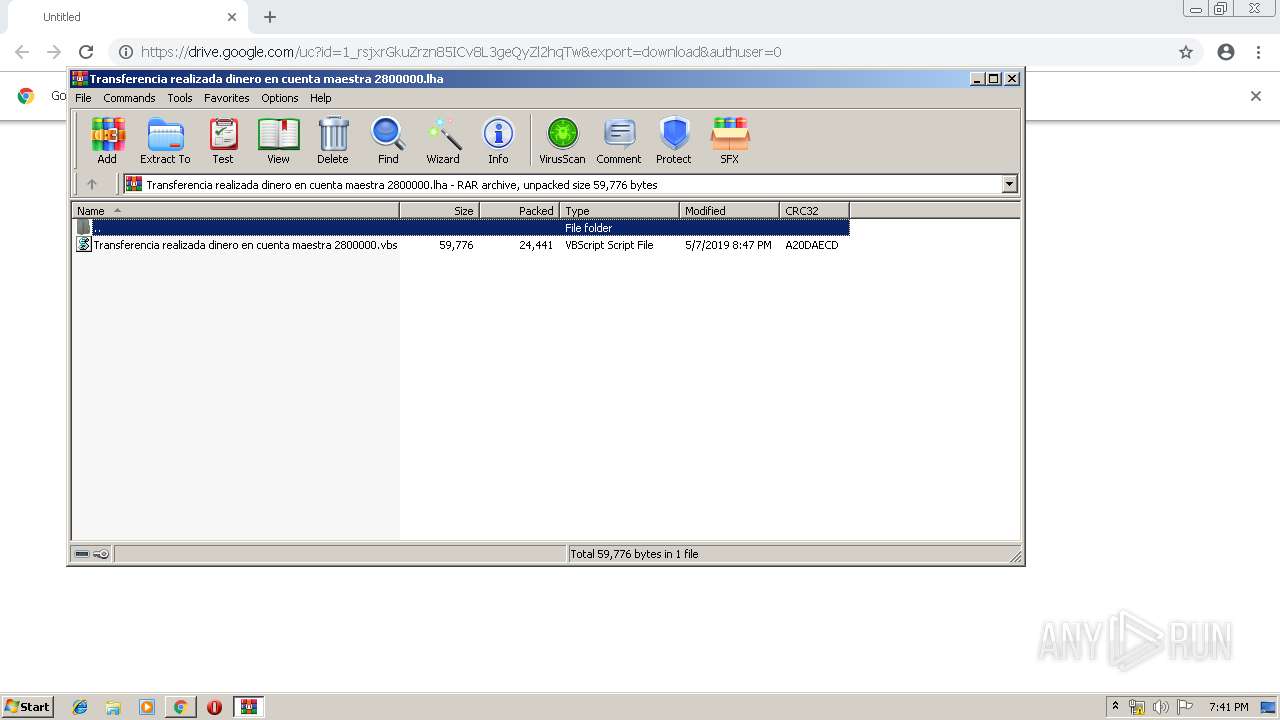
| URL: | https://drive.google.com/uc?id=1_rsjxrGkuZrzn85ICv8L3geQyZl2hqTw&export=download&authuser=0 |
| Full analysis: | https://app.any.run/tasks/9c113802-204a-43b6-889a-8a5088f5bee5 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2019, 18:40:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 7365946BBCFDB274CF93F65CD1FFBC92 |
| SHA1: | 5D2FBD7A6E9B4D7E5F95E7C821B61A507E0B510A |
| SHA256: | CB43BB5C2D6ECCB627B0D25AE07ABE9F162BEB263DD2DBEB4A78643D4B87E3D4 |
| SSDEEP: | 3:N8PMMtZJu2NMujXWUfh4HcbPcWCaIn:2A2HjXlh+cbPc1jn |
MALICIOUS
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3640)
- cmd.exe (PID: 4032)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3716)
- schtasks.exe (PID: 3876)
Writes to a start menu file
- wscript.exe (PID: 1252)
- WScript.exe (PID: 2428)
- wscript.exe (PID: 1004)
Changes the autorun value in the registry
- WScript.exe (PID: 2428)
- wscript.exe (PID: 1252)
- wscript.exe (PID: 1004)
SUSPICIOUS
Creates files in the user directory
- WScript.exe (PID: 2428)
- wscript.exe (PID: 1252)
Application launched itself
- WScript.exe (PID: 2428)
- wscript.exe (PID: 1004)
Executes scripts
- WinRAR.exe (PID: 3320)
- WScript.exe (PID: 2428)
- wscript.exe (PID: 1004)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 1252)
- wscript.exe (PID: 3088)
INFO
Reads settings of System Certificates
- chrome.exe (PID: 2140)
Reads Internet Cache Settings
- chrome.exe (PID: 2140)
Application launched itself
- chrome.exe (PID: 2140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
52
Monitored processes
18
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 692 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=940,1202593172576514276,2785419405118137926,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=12093851127285970670 --mojo-platform-channel-handle=968 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1004 | "C:\Windows\System32\wscript.exe" //B "C:\Users\admin\AppData\Local\Temp\Transferencia realizada dinero en cuenta maestra 2800000.vbs" | C:\Windows\System32\wscript.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1252 | "C:\Windows\System32\wscript.exe" //B "C:\Users\admin\AppData\Roaming\hDJmPnyWmy.vbs" | C:\Windows\System32\wscript.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2140 | "C:\Program Files\Google\Chrome\Application\chrome.exe" https://drive.google.com/uc?id=1_rsjxrGkuZrzn85ICv8L3geQyZl2hqTw&export=download&authuser=0 | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2176 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=940,1202593172576514276,2785419405118137926,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=13707481506112229233 --mojo-platform-channel-handle=1844 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2428 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa3320.20232\Transferencia realizada dinero en cuenta maestra 2800000.vbs" | C:\Windows\System32\WScript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3088 | "C:\Windows\System32\wscript.exe" //B "C:\Users\admin\AppData\Roaming\hDJmPnyWmy.vbs" | C:\Windows\System32\wscript.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3212 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=940,1202593172576514276,2785419405118137926,131072 --enable-features=PasswordImport --service-pipe-token=17596412431970965992 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17596412431970965992 --renderer-client-id=3 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2404 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 3272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3116 --on-initialized-event-handle=308 --parent-handle=312 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 3320 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Transferencia realizada dinero en cuenta maestra 2800000.lha" | C:\Program Files\WinRAR\WinRAR.exe | — | chrome.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
1 787
Read events
1 662
Write events
122
Delete events
3
Modification events
| (PID) Process: | (2140) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2140) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2140) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2140) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2140) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2140) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2140) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2140) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3488-13197474229333984 |
Value: 0 | |||
| (PID) Process: | (2140) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2140) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
0
Suspicious files
12
Text files
52
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2140 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 2140 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 2140 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 2140 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_2 | — | |
MD5:— | SHA256:— | |||
| 2140 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_3 | — | |
MD5:— | SHA256:— | |||
| 2140 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\b4a5f9e1-01ea-471f-a98b-87c0bb2180e8.tmp | — | |
MD5:— | SHA256:— | |||
| 2140 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000018.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2140 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 2140 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 2140 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
17
DNS requests
8
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1004 | wscript.exe | POST | — | 192.169.69.25:5561 | http://ofinuevamayo.duckdns.org:5561/is-ready | US | — | — | malicious |
1004 | wscript.exe | POST | — | 192.169.69.25:5561 | http://ofinuevamayo.duckdns.org:5561/is-ready | US | — | — | malicious |
1004 | wscript.exe | POST | — | 192.169.69.25:5561 | http://ofinuevamayo.duckdns.org:5561/is-ready | US | — | — | malicious |
1004 | wscript.exe | POST | — | 192.169.69.25:5561 | http://ofinuevamayo.duckdns.org:5561/is-ready | US | — | — | malicious |
1004 | wscript.exe | POST | — | 192.169.69.25:5561 | http://ofinuevamayo.duckdns.org:5561/is-ready | US | — | — | malicious |
1004 | wscript.exe | POST | — | 192.169.69.25:5561 | http://ofinuevamayo.duckdns.org:5561/is-ready | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2140 | chrome.exe | 172.217.23.174:443 | drive.google.com | Google Inc. | US | whitelisted |
2140 | chrome.exe | 216.58.206.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2140 | chrome.exe | 172.217.16.129:443 | doc-0g-8o-docs.googleusercontent.com | Google Inc. | US | whitelisted |
2140 | chrome.exe | 172.217.22.110:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
2140 | chrome.exe | 172.217.16.141:443 | accounts.google.com | Google Inc. | US | suspicious |
1004 | wscript.exe | 192.169.69.25:5561 | ofinuevamayo.duckdns.org | Wowrack.com | US | malicious |
2140 | chrome.exe | 172.217.16.132:443 | www.google.com | Google Inc. | US | whitelisted |
2140 | chrome.exe | 216.58.207.67:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
drive.google.com |
| shared |
accounts.google.com |
| shared |
doc-0g-8o-docs.googleusercontent.com |
| shared |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| malicious |
ssl.gstatic.com |
| whitelisted |
ofinuevamayo.duckdns.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1056 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |