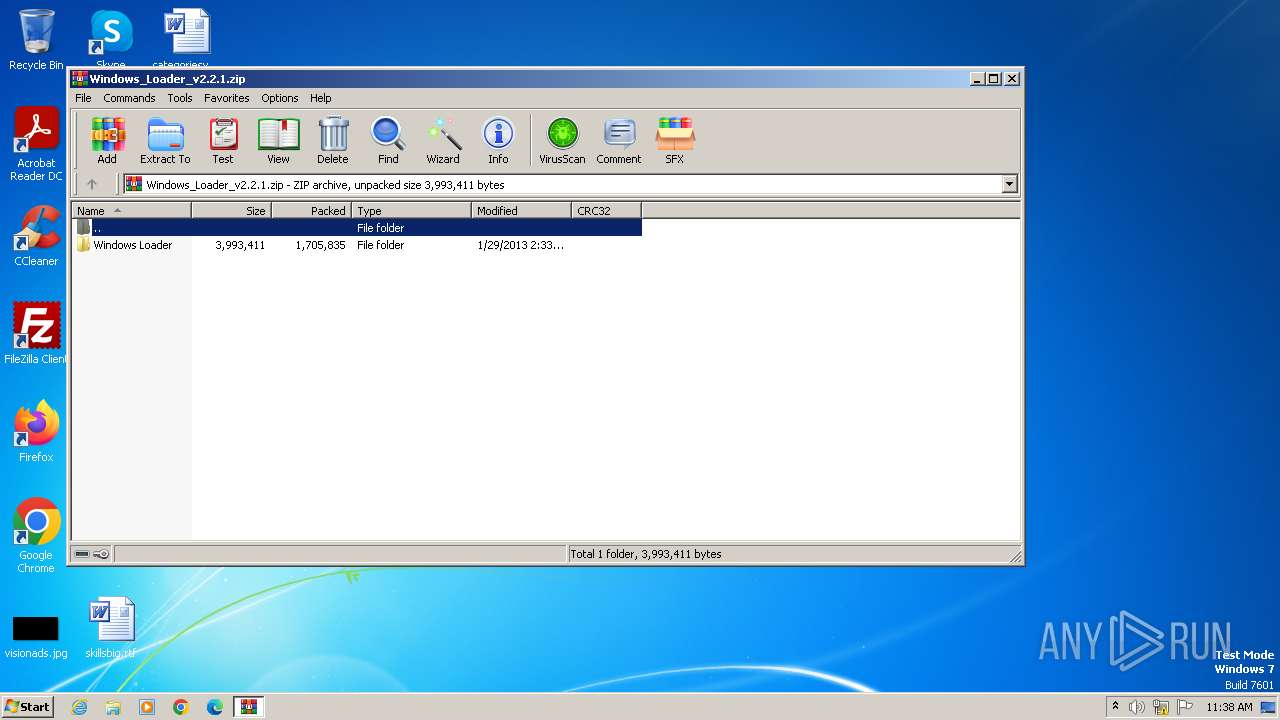
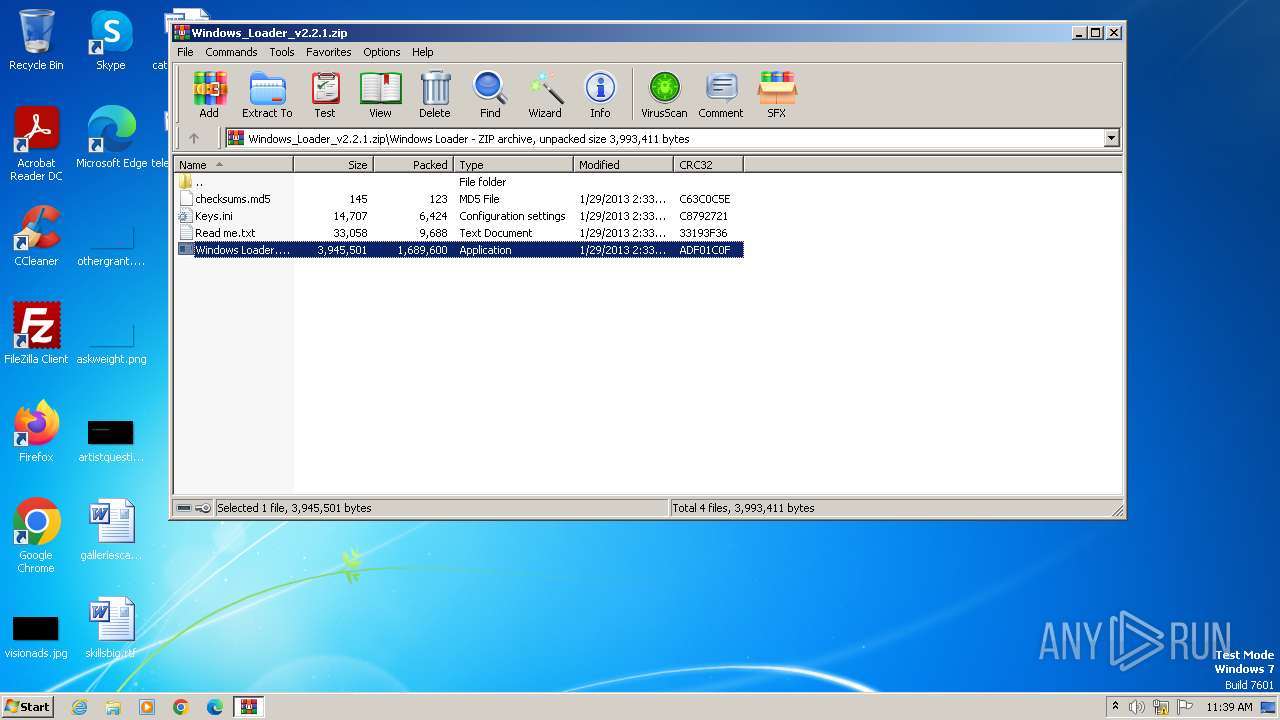
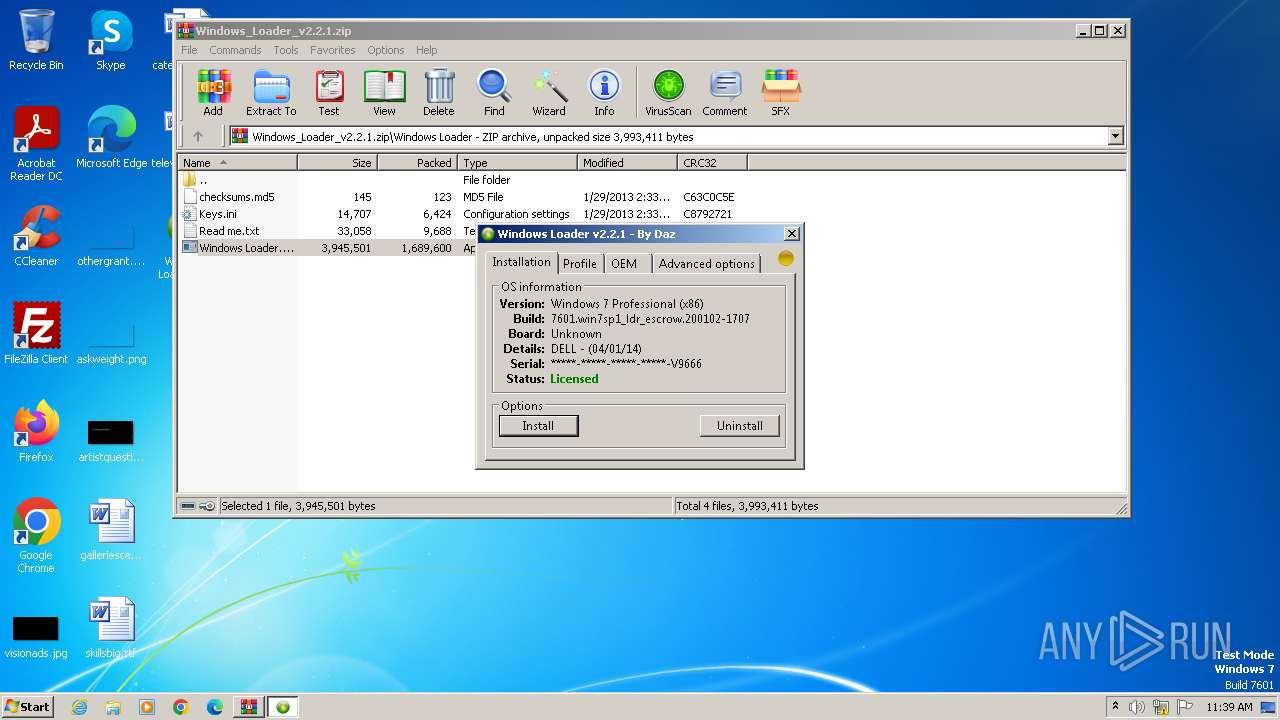
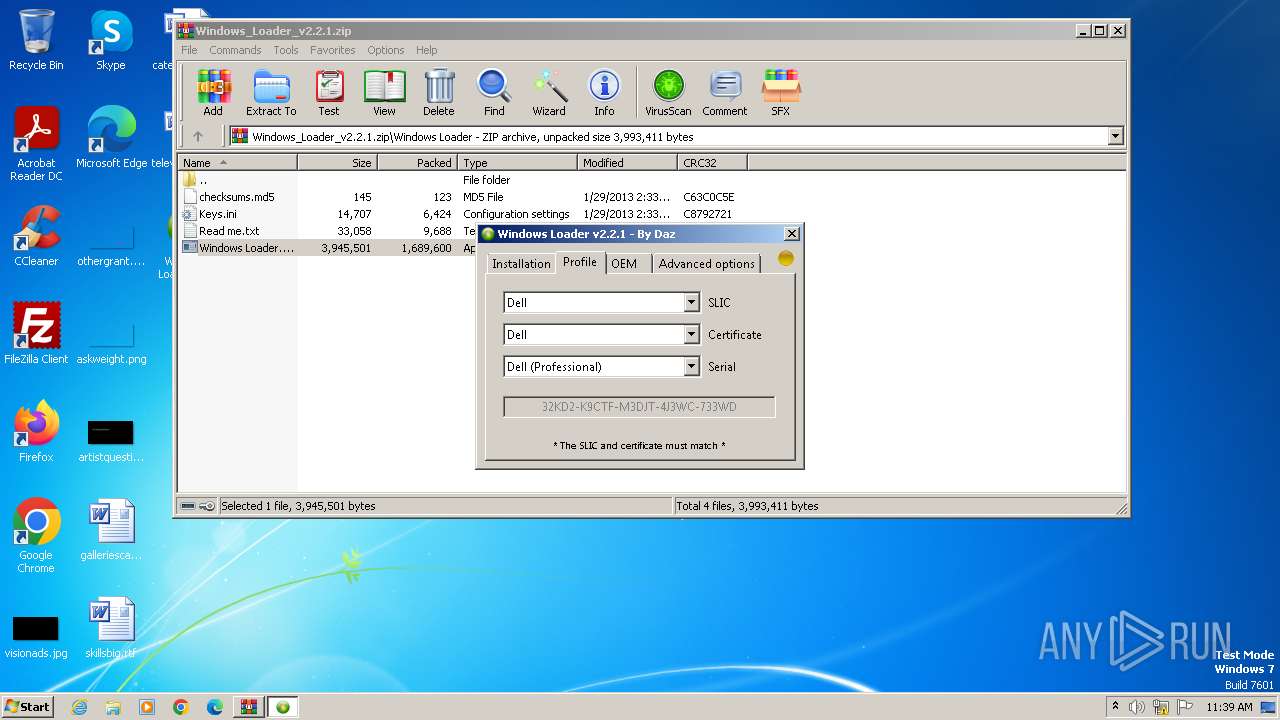
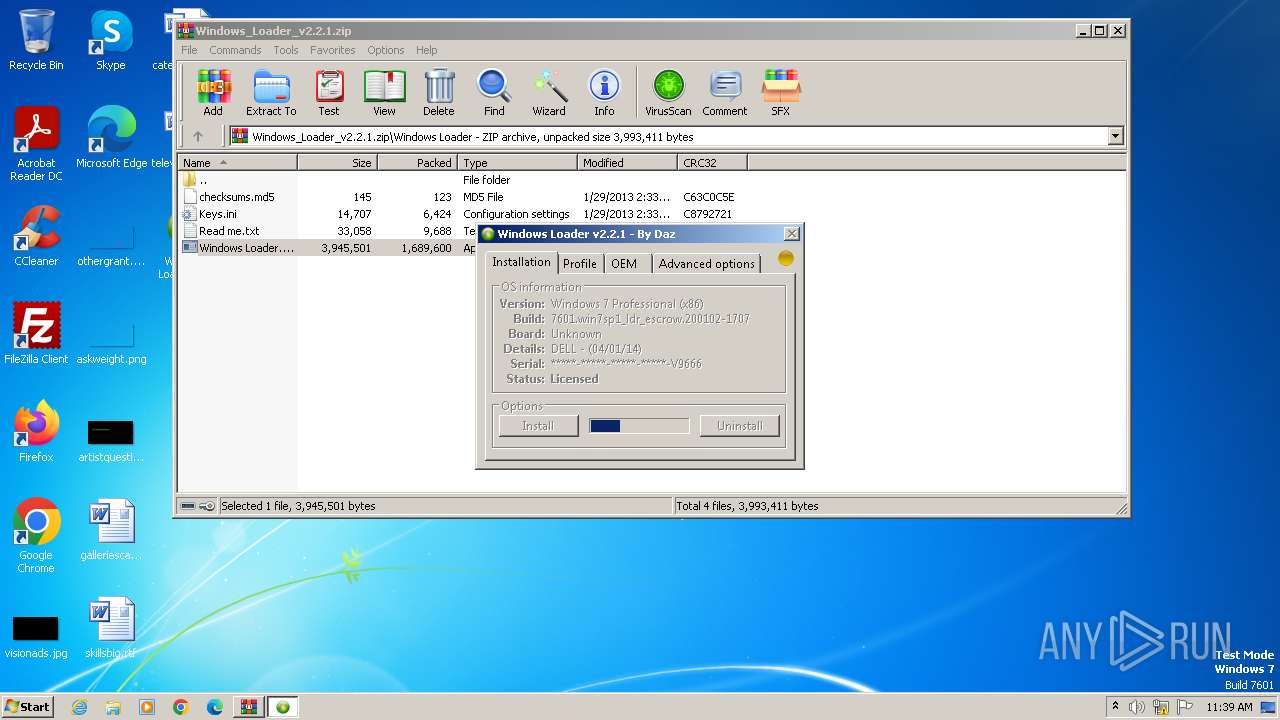
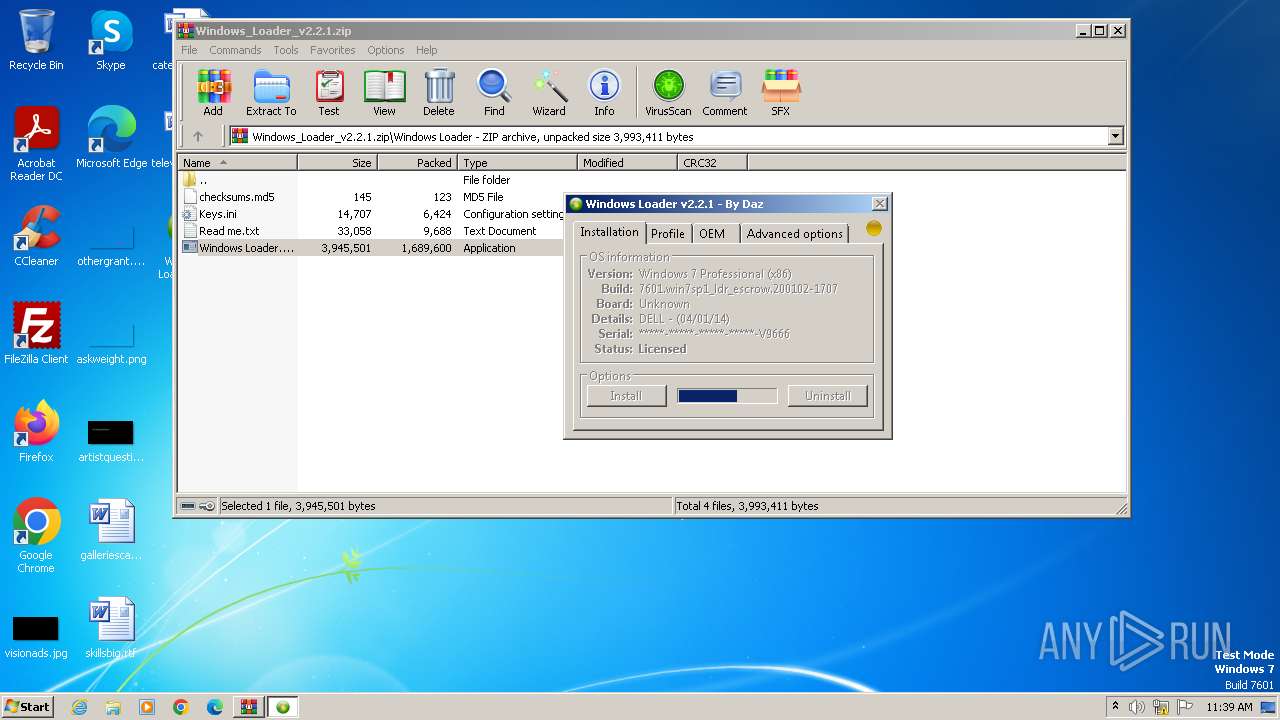
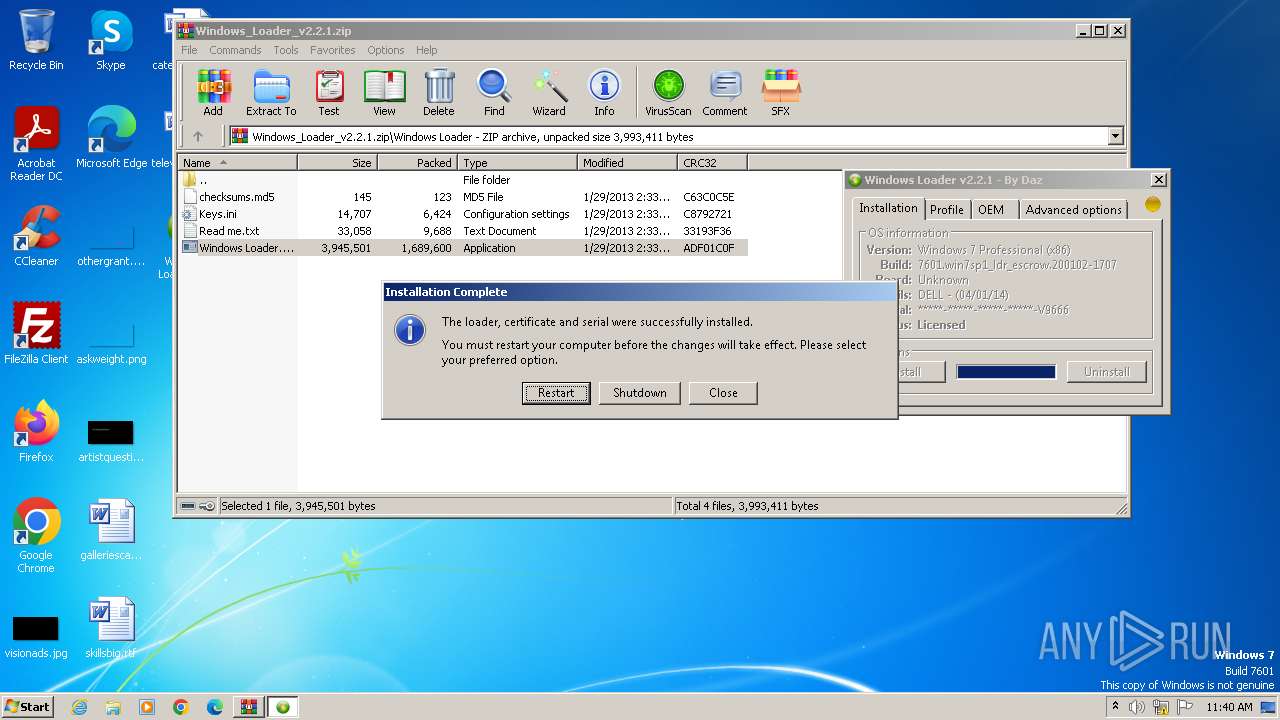
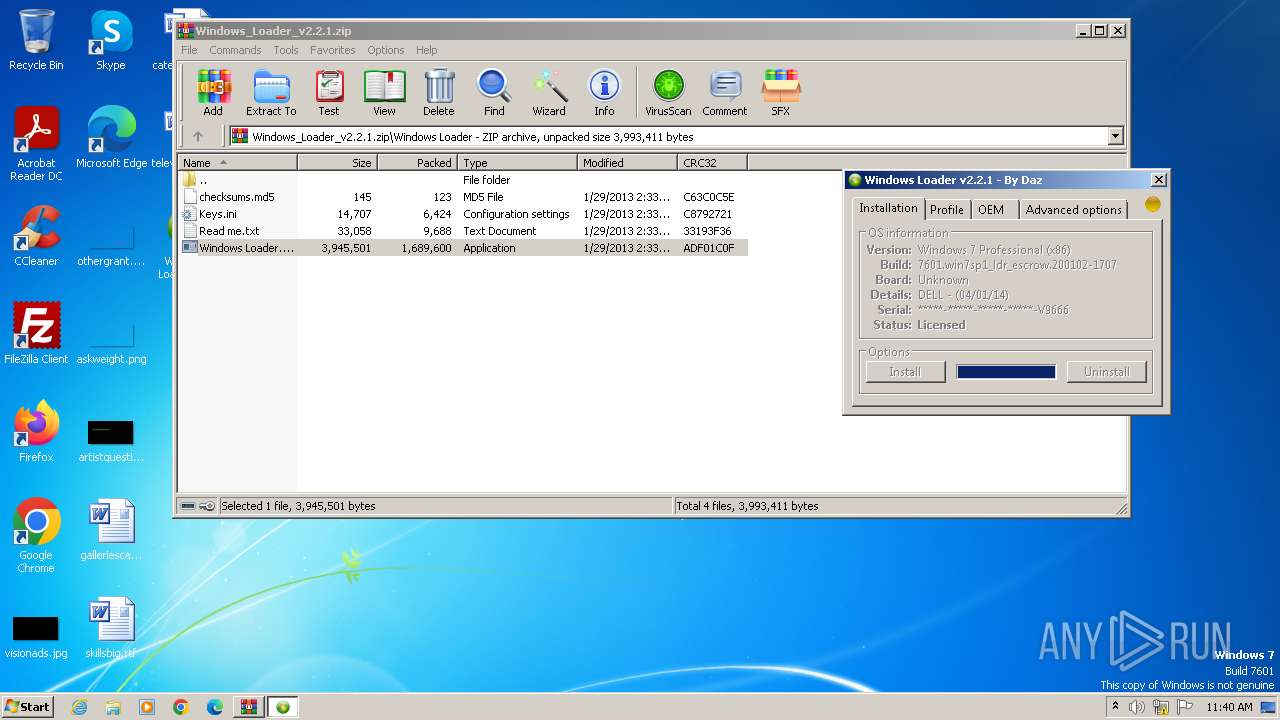
| File name: | Windows_Loader_v2.2.1.zip |
| Full analysis: | https://app.any.run/tasks/48ef4754-84cc-490a-b1af-42b72f902969 |
| Verdict: | Malicious activity |
| Analysis date: | June 04, 2024, 10:38:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | E4D0F51884FDAE5B3C0CCC1E114F9F00 |
| SHA1: | F901FEEFE2DD5AB8145211305D94A7E3E5389774 |
| SHA256: | CB2F418B6471D3FEEC8E9682E0939BA59412858B9286555BE0640E8154065CEA |
| SSDEEP: | 49152:aiquh2LncDEkl16dvQByTfxA1VvEQJUx2JKjrSMrlVKBhZTrjASWBqhFVBFvclDt:a7Y0aHE4oWTEAUAJ9YXKnJANkhzvvS9f |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3976)
- Windows Loader.exe (PID: 864)
Opens a text file (SCRIPT)
- cscript.exe (PID: 2636)
- cscript.exe (PID: 936)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3976)
Reads the BIOS version
- Windows Loader.exe (PID: 864)
Starts CMD.EXE for commands execution
- Windows Loader.exe (PID: 864)
- cmd.exe (PID: 2516)
- cmd.exe (PID: 664)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 1960)
- cmd.exe (PID: 1012)
Application launched itself
- cmd.exe (PID: 2516)
- cmd.exe (PID: 664)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 1980)
- cmd.exe (PID: 2188)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 936)
- cscript.exe (PID: 2636)
The process executes VB scripts
- cmd.exe (PID: 1848)
- cmd.exe (PID: 1880)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 936)
- cscript.exe (PID: 2636)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 936)
- cscript.exe (PID: 2636)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 936)
Changes charset (SCRIPT)
- cscript.exe (PID: 936)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 2636)
- cscript.exe (PID: 936)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 2636)
- cscript.exe (PID: 936)
Creates file in the systems drive root
- Windows Loader.exe (PID: 864)
- bootsect.exe (PID: 2564)
- cmd.exe (PID: 916)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 2636)
- cscript.exe (PID: 936)
Executable content was dropped or overwritten
- Windows Loader.exe (PID: 864)
Process drops legitimate windows executable
- Windows Loader.exe (PID: 864)
The system shut down or reboot
- cmd.exe (PID: 2916)
The process executes via Task Scheduler
- ctfmon.exe (PID: 284)
- sipnotify.exe (PID: 240)
Reads settings of System Certificates
- sipnotify.exe (PID: 240)
Reads the Internet Settings
- sipnotify.exe (PID: 240)
Reads data from a file (SCRIPT)
- cscript.exe (PID: 936)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3976)
Reads Environment values
- Windows Loader.exe (PID: 864)
Reads the computer name
- Windows Loader.exe (PID: 864)
- IMEKLMG.EXE (PID: 2216)
- IMEKLMG.EXE (PID: 2224)
- wmpnscfg.exe (PID: 2452)
- wmpnscfg.exe (PID: 2484)
Checks supported languages
- Windows Loader.exe (PID: 864)
- Windows Loader.exe (PID: 1592)
- Windows Loader.exe (PID: 1804)
- bootsect.exe (PID: 2564)
- IMEKLMG.EXE (PID: 2216)
- IMEKLMG.EXE (PID: 2224)
- wmpnscfg.exe (PID: 2484)
- wmpnscfg.exe (PID: 2452)
Reads product name
- Windows Loader.exe (PID: 864)
Reads the machine GUID from the registry
- Windows Loader.exe (PID: 864)
Manual execution by a user
- Windows Loader.exe (PID: 1640)
- Windows Loader.exe (PID: 1804)
- IMEKLMG.EXE (PID: 2216)
- IMEKLMG.EXE (PID: 2224)
- wmpnscfg.exe (PID: 2452)
- wmpnscfg.exe (PID: 2484)
- taskmgr.exe (PID: 2728)
- taskmgr.exe (PID: 2608)
Reads security settings of Internet Explorer
- cscript.exe (PID: 936)
- cscript.exe (PID: 2636)
- sipnotify.exe (PID: 240)
Reads the software policy settings
- sipnotify.exe (PID: 240)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2216)
- IMEKLMG.EXE (PID: 2224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2013:01:29 14:33:00 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
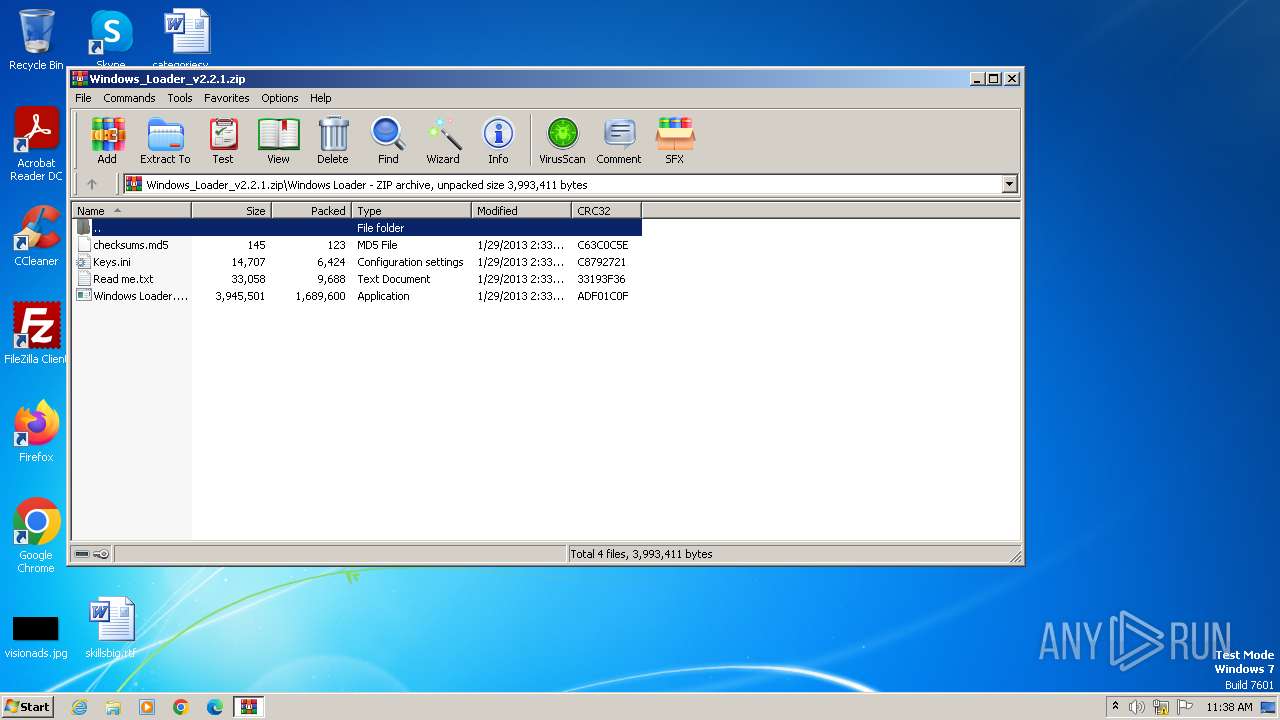
| ZipFileName: | Windows Loader/ |
Total processes
137
Monitored processes
35
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 284 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 664 | cmd.exe /A /C "cmd.exe /c takeown /f C:\ldrscan\bootwin" | C:\Windows\System32\cmd.exe | — | Windows Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 848 | compact /u \\?\Volume{e1a82db3-a9f0-11e7-b142-806e6f6e6963}\AGKHS | C:\Windows\System32\compact.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: File Compress Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 864 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3976.32815\Windows Loader\Windows Loader.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3976.32815\Windows Loader\Windows Loader.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 916 | cmd.exe /A /C "C:\bootsect.exe /nt60 SYS /force" | C:\Windows\System32\cmd.exe | — | Windows Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 936 | C:\Windows\System32\cscript.exe //nologo C:\Windows\System32\slmgr.vbs -ilc "C:\Dell.XRM-MS" | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1012 | cmd.exe /c takeown /f C:\ldrscan\bootwin | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1468 | takeown /f C:\ldrscan\bootwin | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1592 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3976.34240\Windows Loader\Windows Loader.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3976.34240\Windows Loader\Windows Loader.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
9 494
Read events
9 433
Write events
48
Delete events
13
Modification events
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Windows_Loader_v2.2.1.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
5
Suspicious files
2
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2564 | bootsect.exe | \Device\HarddiskVolume1 | — | |
MD5:— | SHA256:— | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3976.34240\Windows Loader\checksums.md5 | text | |
MD5:672BFA5463DF7B6EF79DAFE7FBAD4AC4 | SHA256:2ADEF5BF1E6C62FC4DC9A3FA30C3C9B981F6311E2E468142B9046D43F0722B1D | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3976.32815\Windows Loader\checksums.md5 | text | |
MD5:672BFA5463DF7B6EF79DAFE7FBAD4AC4 | SHA256:2ADEF5BF1E6C62FC4DC9A3FA30C3C9B981F6311E2E468142B9046D43F0722B1D | |||
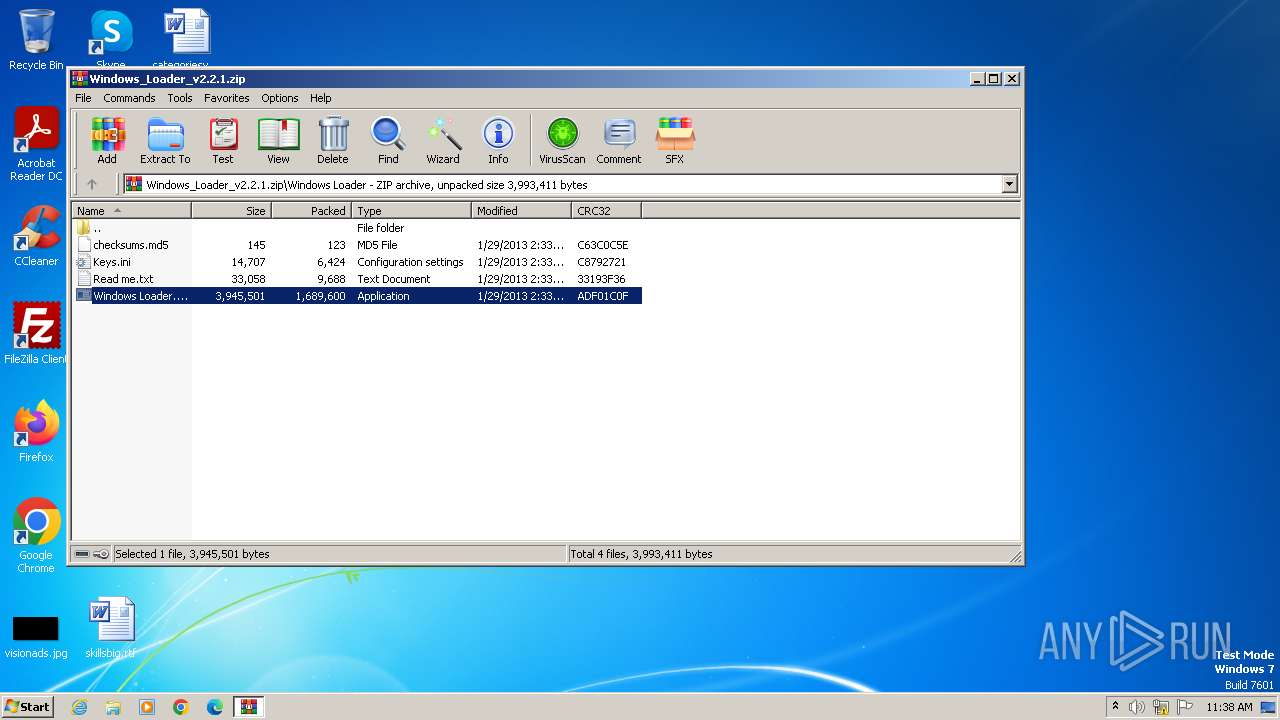
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3976.32815\Windows Loader\Windows Loader.exe | executable | |
MD5:3976BD5FCBB7CD13F0C12BB69AFC2ADC | SHA256:BF5070EF8CF03A11D25460B3E09A479183CC0FA03D0EA32E4499998F509B1A40 | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3976.34240\Windows Loader\Keys.ini | text | |
MD5:3BB894D0D458970E1EEA0A45E21918CB | SHA256:898A61C5527BC13D45DDD6E9DA23A14673065EC389438710AECDCFB254DF87D8 | |||
| 864 | Windows Loader.exe | C:\Dell.XRM-MS | xml | |
MD5:18B1E45BF56F40C3C4BBE65831178216 | SHA256:D072A059D3ED3E75C98B85B41E4319E8D5CFAE0E0C239B62436A3AD34003AB4A | |||
| 864 | Windows Loader.exe | C:\bootsect.dat | executable | |
MD5:33BBB956A27C8AE5FF96E69FB5B0E184 | SHA256:0B1B0E18255F00E6E63E394C4071C9EC4CBFA8EB2C815C2797F8FF7AC8FB68A4 | |||
| 240 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\main.jpg | image | |
MD5:B342ACE63F77961249A084C61EABC884 | SHA256:E5067BBA2095B5DA7C3171EC116E9A92337E24E471339B0860A160076EFE49B9 | |||
| 864 | Windows Loader.exe | \\?\Volume{e1a82db3-a9f0-11e7-b142-806e6f6e6963}\AGKHS | binary | |
MD5:30F052AACDF0DB2DDA527C64101A6F02 | SHA256:A6E5143FC38651C79987FDEAA7A531BA5BCF00D0BE29D9498FF40A9144E4EC04 | |||
| 240 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\styles.css | text | |
MD5:3383EEF350240253D7C2C2564381B3CB | SHA256:85443493D86D6D7FB0E07BC9705DFC9C858086FBA1B0E508092AB328D5F145E8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
13
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
240 | sipnotify.exe | HEAD | 200 | 104.110.23.132:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133619748449210000 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1116 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1452 | svchost.exe | 239.255.255.250:3702 | — | — | — | unknown |
240 | sipnotify.exe | 104.110.23.132:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | NO | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |