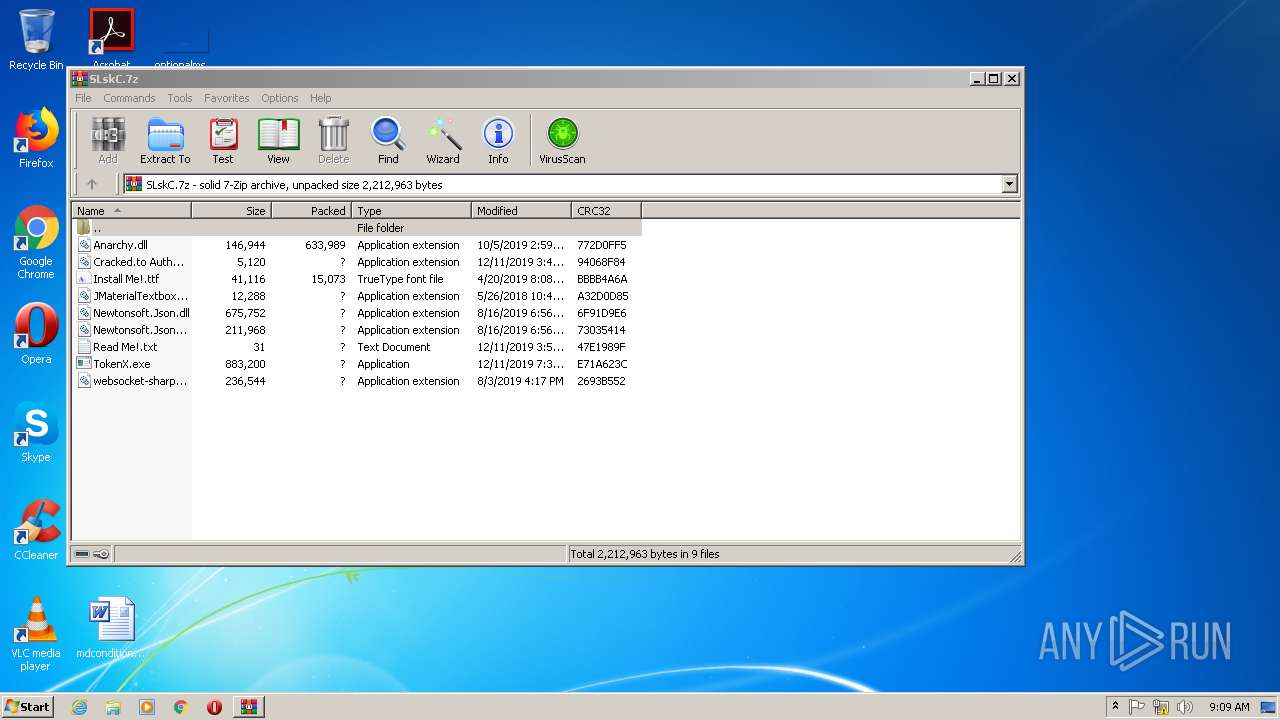
| File name: | SLskC.7z |
| Full analysis: | https://app.any.run/tasks/99692aa8-941e-4bb0-b79f-cc80bcf353b0 |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2020, 08:09:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 9F97BAD35B8084440E655218C923A8B7 |
| SHA1: | AFBA38FB39102652E78D74AC731BF754EEFE38BE |
| SHA256: | CB11DE448907B2AA4D14243E6D36AA07AB1F46418C15F8229B2A0070AEA691AC |
| SSDEEP: | 12288:lY3qg569F389C++ia10x8lI97Goc8JdTfhiUI/cRHmpkzpIKFtPjD:llF3hu26Tq+dThi505lJt/ |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1624)
- TokenX.exe (PID: 3944)
Application was dropped or rewritten from another process
- TokenX.exe (PID: 3944)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3328)
Executed via COM
- DllHost.exe (PID: 3408)
Creates files in the Windows directory
- DllHost.exe (PID: 3408)
INFO
Manual execution by user
- WinRAR.exe (PID: 3328)
- fontview.exe (PID: 2188)
- TokenX.exe (PID: 3944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
44
Monitored processes
6
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1624 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
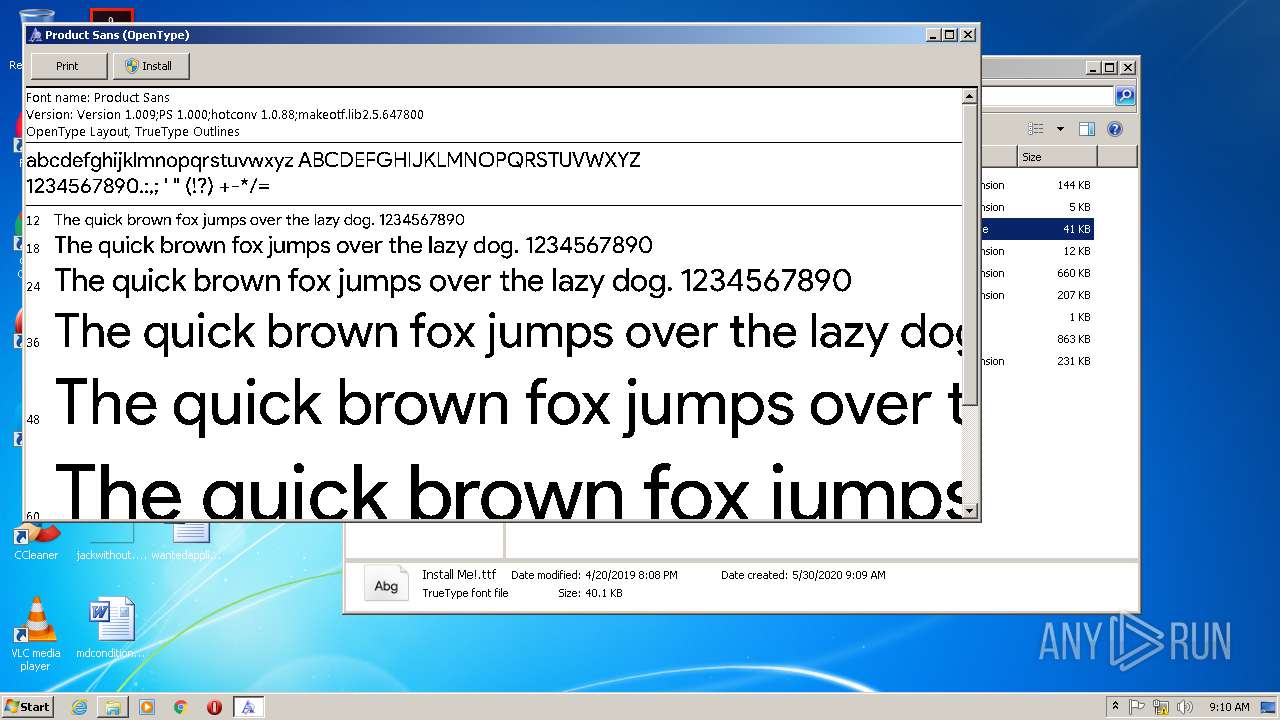
| 2188 | "C:\Windows\System32\fontview.exe" C:\Users\admin\Desktop\SLskC\Install Me!.ttf | C:\Windows\System32\fontview.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Font Viewer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2872 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\SLskC.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3328 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\SLskC.7z" C:\Users\admin\Desktop\SLskC\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3408 | C:\Windows\system32\DllHost.exe /Processid:{642EF9D6-48A5-476B-919A-A507CFD02C0F} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
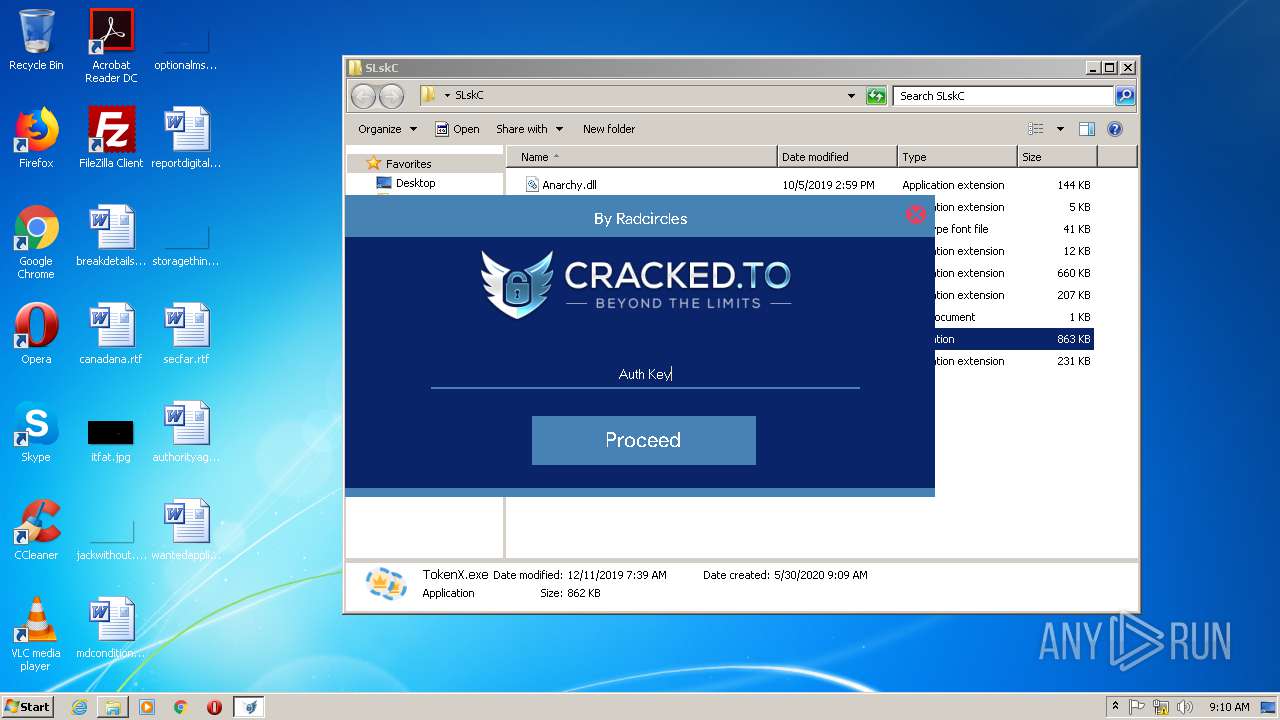
| 3944 | "C:\Users\admin\Desktop\SLskC\TokenX.exe" | C:\Users\admin\Desktop\SLskC\TokenX.exe | — | explorer.exe | |||||||||||
User: admin Company: HP Inc. Integrity Level: MEDIUM Description: TokenX Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
734
Read events
703
Write events
31
Delete events
0
Modification events
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\SLskC.7z | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
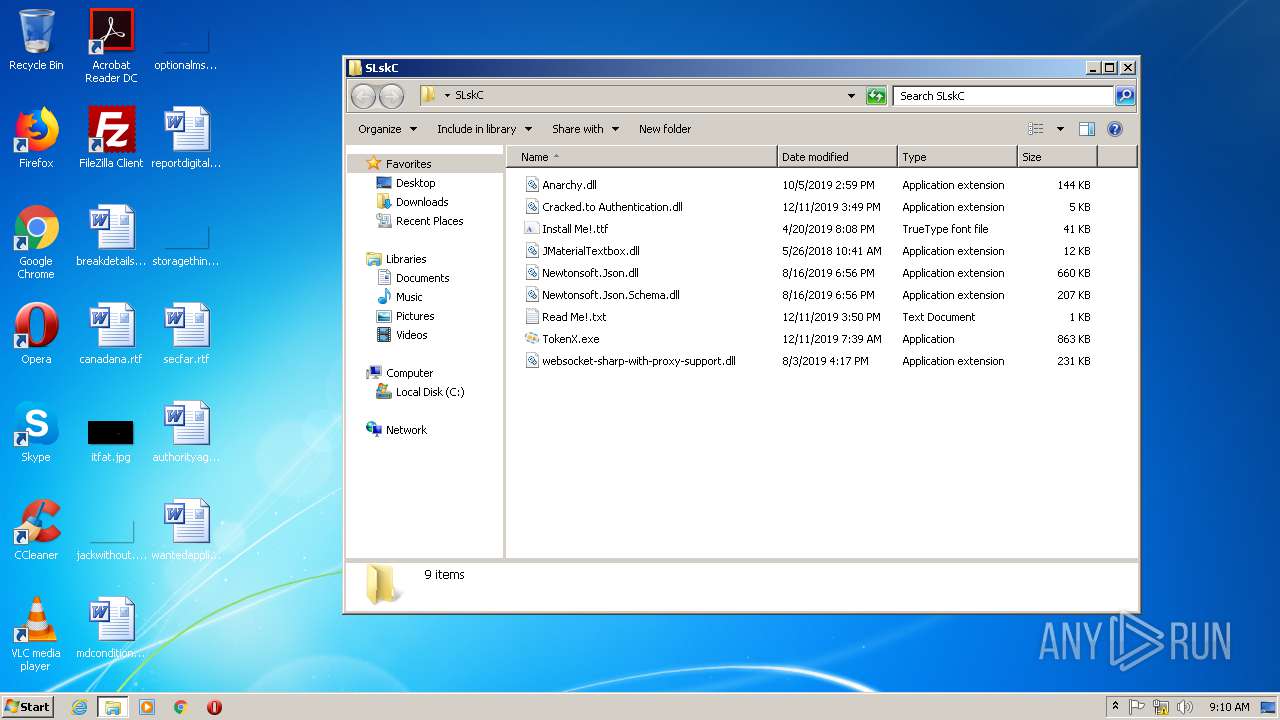
Executable files
7
Suspicious files
0
Text files
1
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3328 | WinRAR.exe | C:\Users\admin\Desktop\SLskC\Read Me!.txt | text | |
MD5:— | SHA256:— | |||
| 3328 | WinRAR.exe | C:\Users\admin\Desktop\SLskC\Cracked.to Authentication.dll | executable | |
MD5:— | SHA256:— | |||
| 3328 | WinRAR.exe | C:\Users\admin\Desktop\SLskC\Anarchy.dll | executable | |
MD5:— | SHA256:— | |||
| 3328 | WinRAR.exe | C:\Users\admin\Desktop\SLskC\JMaterialTextbox.dll | executable | |
MD5:— | SHA256:— | |||
| 3328 | WinRAR.exe | C:\Users\admin\Desktop\SLskC\Newtonsoft.Json.dll | executable | |
MD5:4DF6C8781E70C3A4912B5BE796E6D337 | SHA256:3598CCCAD5B535FEA6F93662107A4183BFD6167BF1D0F80260436093EDC2E3AF | |||
| 3328 | WinRAR.exe | C:\Users\admin\Desktop\SLskC\TokenX.exe | executable | |
MD5:— | SHA256:— | |||
| 3328 | WinRAR.exe | C:\Users\admin\Desktop\SLskC\Install Me!.ttf | ttf | |
MD5:EAE9C18CEE82A8A1A52E654911F8FE83 | SHA256:B34CBB71D75B84EB4925F51E050249F65FB3E3550133ABA0A4C161C6820AEC82 | |||
| 3408 | DllHost.exe | C:\Windows\Fonts\Install Me!.ttf | ttf | |
MD5:EAE9C18CEE82A8A1A52E654911F8FE83 | SHA256:B34CBB71D75B84EB4925F51E050249F65FB3E3550133ABA0A4C161C6820AEC82 | |||
| 3328 | WinRAR.exe | C:\Users\admin\Desktop\SLskC\websocket-sharp-with-proxy-support.dll | executable | |
MD5:70B6B4E92485D389D5E89F4A1871771D | SHA256:BF9A54934E94A76697E83299E87DEE14F87B85691D84D353D53E97107DB8C64F | |||
| 3328 | WinRAR.exe | C:\Users\admin\Desktop\SLskC\Newtonsoft.Json.Schema.dll | executable | |
MD5:9C4CA74DF958F8CBEC953FE756245B73 | SHA256:D27E6413382FB31FA30D1AB95C956284C4F8B1C1834CF22B79A83C894F5A8DD0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report