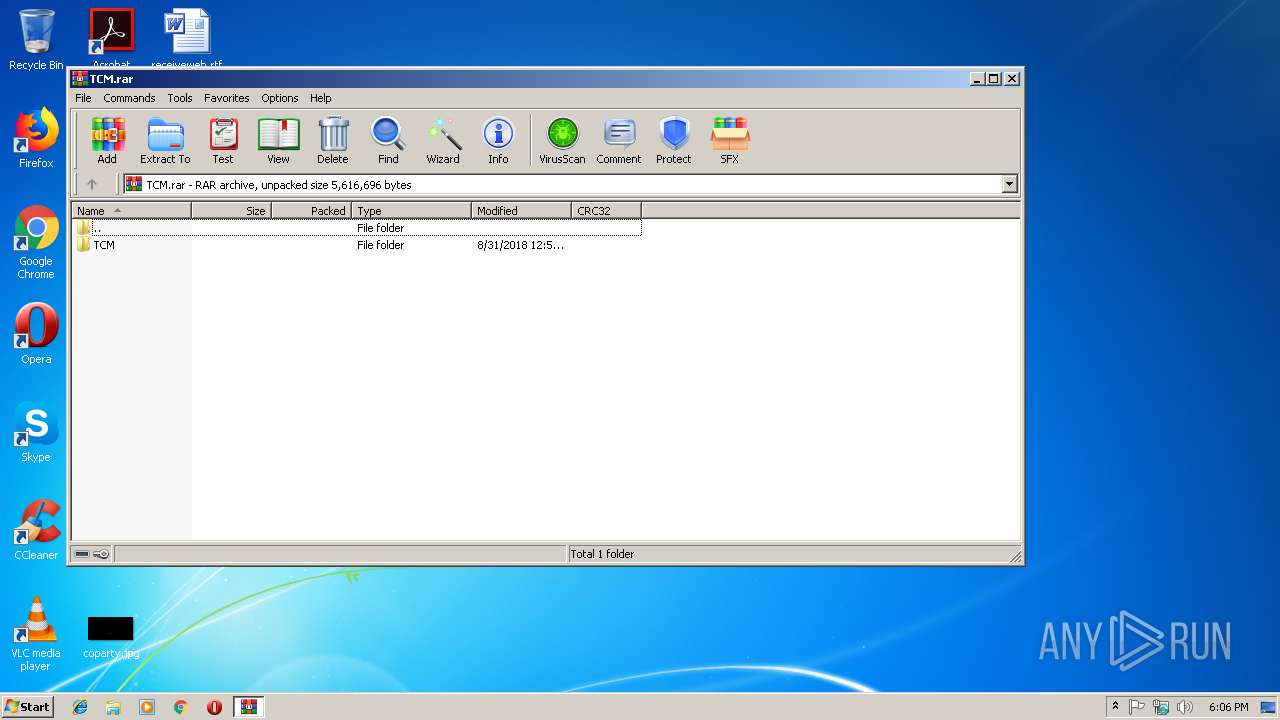
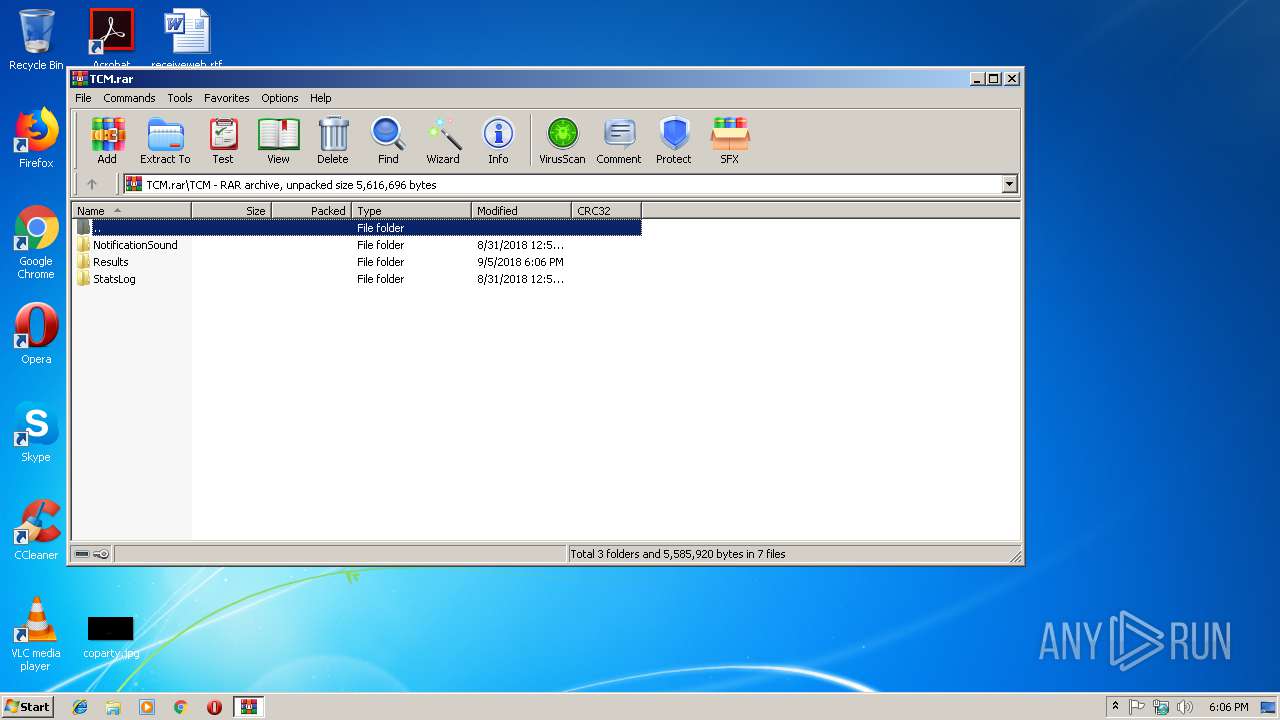
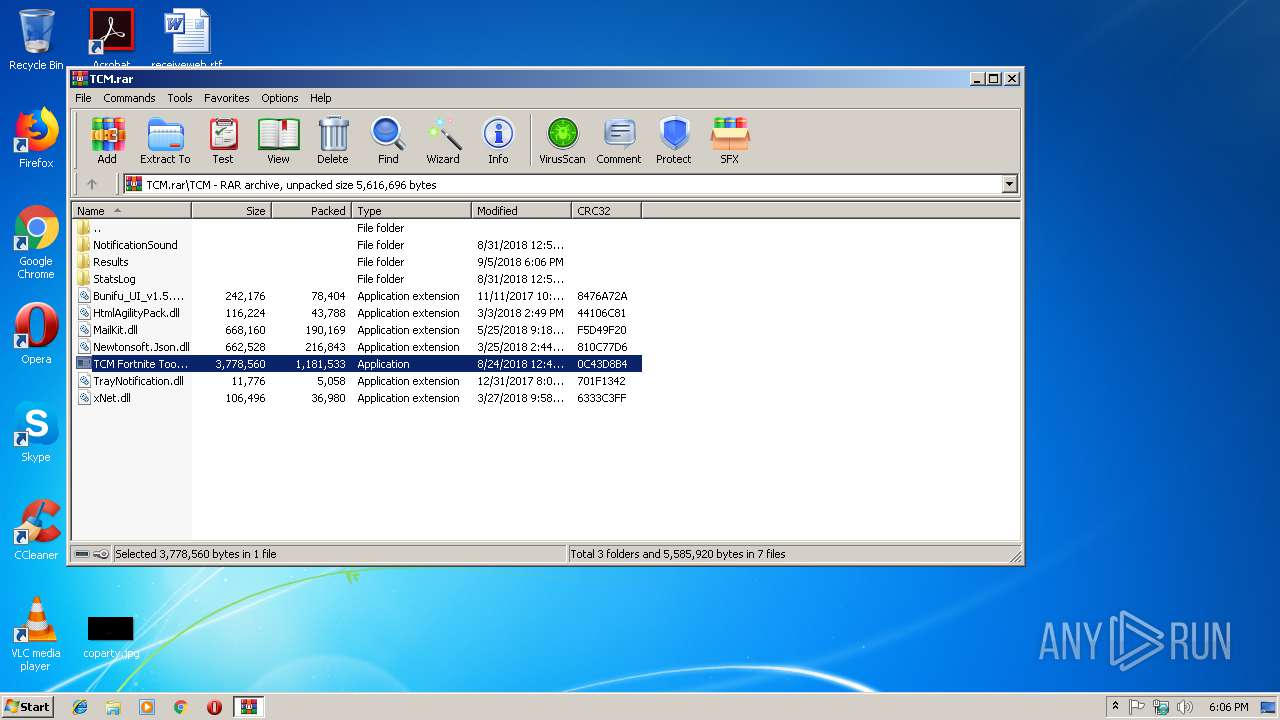
| File name: | TCM.rar |
| Full analysis: | https://app.any.run/tasks/5227bf57-e4cb-421d-b583-a8b81df3ead8 |
| Verdict: | Malicious activity |
| Analysis date: | December 18, 2018, 18:06:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 7DC33EFCFD0FFEF566861246E2742341 |
| SHA1: | A5EF256CF5EEAB56C7421524642FE1F9A682F809 |
| SHA256: | CAF30FE53C3F776CAC6F33558427F1DE4F85AC9CD7B437167C04D22AD802AEAF |
| SSDEEP: | 24576:VfX/EzLLZQJJItMoGtrO8d4W6KFV1XRJyyfNAr9Kin1VGdjcy8NHDs6pEAq45iIB:9idOiM5xiiSr7n1VGtxC/pEp6 |
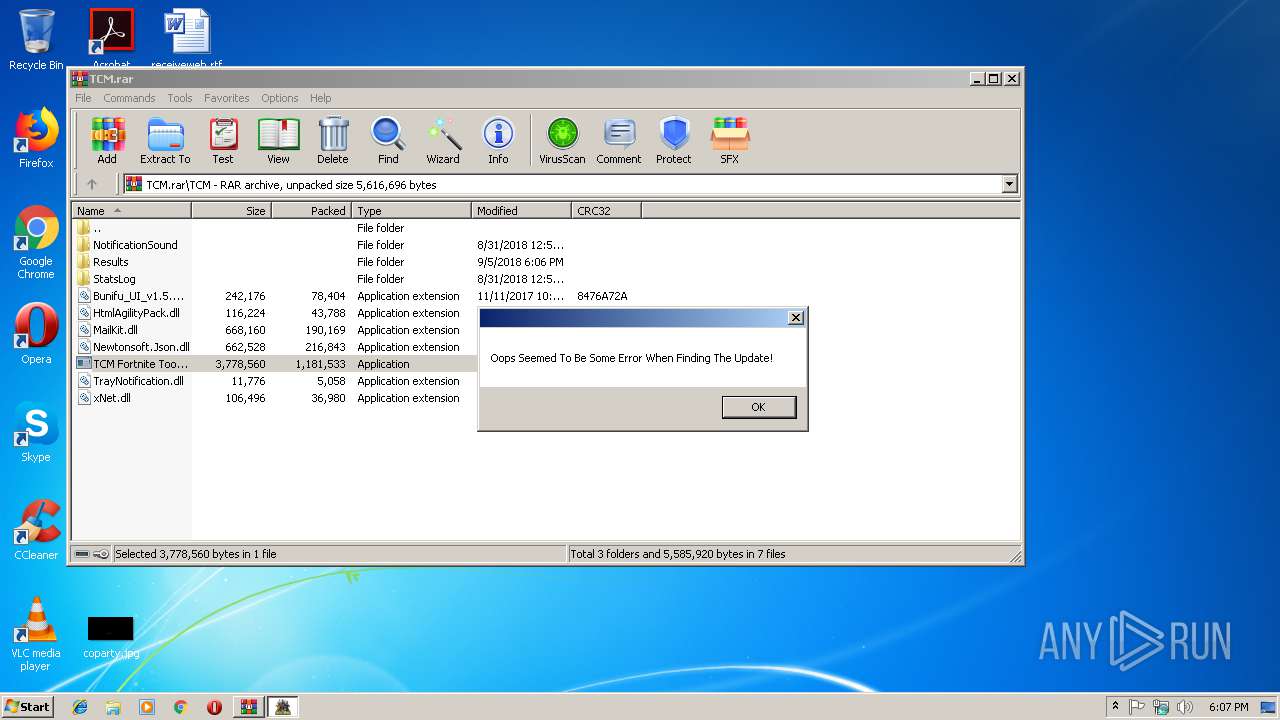
MALICIOUS
Loads dropped or rewritten executable
- TCM Fortnite Tool.exe (PID: 3132)
- TCM Fortnite Tool.exe (PID: 3228)
Application was dropped or rewritten from another process
- TCM Fortnite Tool.exe (PID: 3132)
- TCM Fortnite Tool.exe (PID: 3228)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2852)
- TCM Fortnite Tool.exe (PID: 3132)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
31
Monitored processes
3
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2852 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\TCM.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3132 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2852.41788\TCM\TCM Fortnite Tool.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2852.41788\TCM\TCM Fortnite Tool.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: TCM Fortnite Tool Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3228 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2852.46352\TCM\TCM Fortnite Tool.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2852.46352\TCM\TCM Fortnite Tool.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: TCM Fortnite Tool Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
513
Read events
469
Write events
44
Delete events
0
Modification events
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\TCM.rar | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
15
Suspicious files
0
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2852.41788\TCM\HtmlAgilityPack.dll | executable | |
MD5:— | SHA256:— | |||
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2852.41788\TCM\NotificationSound\beep.wav | wav | |
MD5:— | SHA256:— | |||
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2852.41788\TCM\TCM Fortnite Tool.exe | executable | |
MD5:— | SHA256:— | |||
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2852.41788\TCM\TrayNotification.dll | executable | |
MD5:— | SHA256:— | |||
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2852.41788\TCM\MailKit.dll | executable | |
MD5:BE99F9896236C6106887959541D22F05 | SHA256:786E2126D22AFABCB42D57CF07760690C18C21007C93ABAED0CB4C7FE2044EB6 | |||
| 3132 | TCM Fortnite Tool.exe | C:\Users\admin\AppData\Local\Temp\Protect8ce200b4.dll | executable | |
MD5:8CE200B443328ABCDA844FCC391DA7B5 | SHA256:248144DD3D877FD6C20E78BB2E4C5886B96D14903B4FAEF470A36DA656FC83AF | |||
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2852.41788\TCM\Newtonsoft.Json.dll | executable | |
MD5:5AFDA7C7D4F7085E744C2E7599279DB3 | SHA256:F58C374FFCAAE4E36D740D90FBF7FE70D0ABB7328CD9AF3A0A7B70803E994BA4 | |||
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2852.46352\TCM\Bunifu_UI_v1.5.3.dll | executable | |
MD5:2ECB51AB00C5F340380ECF849291DBCF | SHA256:F1B3E0F2750A9103E46A6A4A34F1CF9D17779725F98042CC2475EC66484801CF | |||
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2852.41788\TCM\xNet.dll | executable | |
MD5:158DEFD55A804AA8D4D67BFDF7A4AF9C | SHA256:6C7EC4CC31A2CE0B97703B7A42E3448E9B87D96DDA12761CA24D8787AC27CFF1 | |||
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2852.46352\TCM\NotificationSound\beep.wav | wav | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3132 | TCM Fortnite Tool.exe | 104.18.32.242:443 | www.gamersocial.co | Cloudflare Inc | US | shared |
3228 | TCM Fortnite Tool.exe | 104.18.32.242:443 | www.gamersocial.co | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.gamersocial.co |
| malicious |
gamersocial.co |
| malicious |