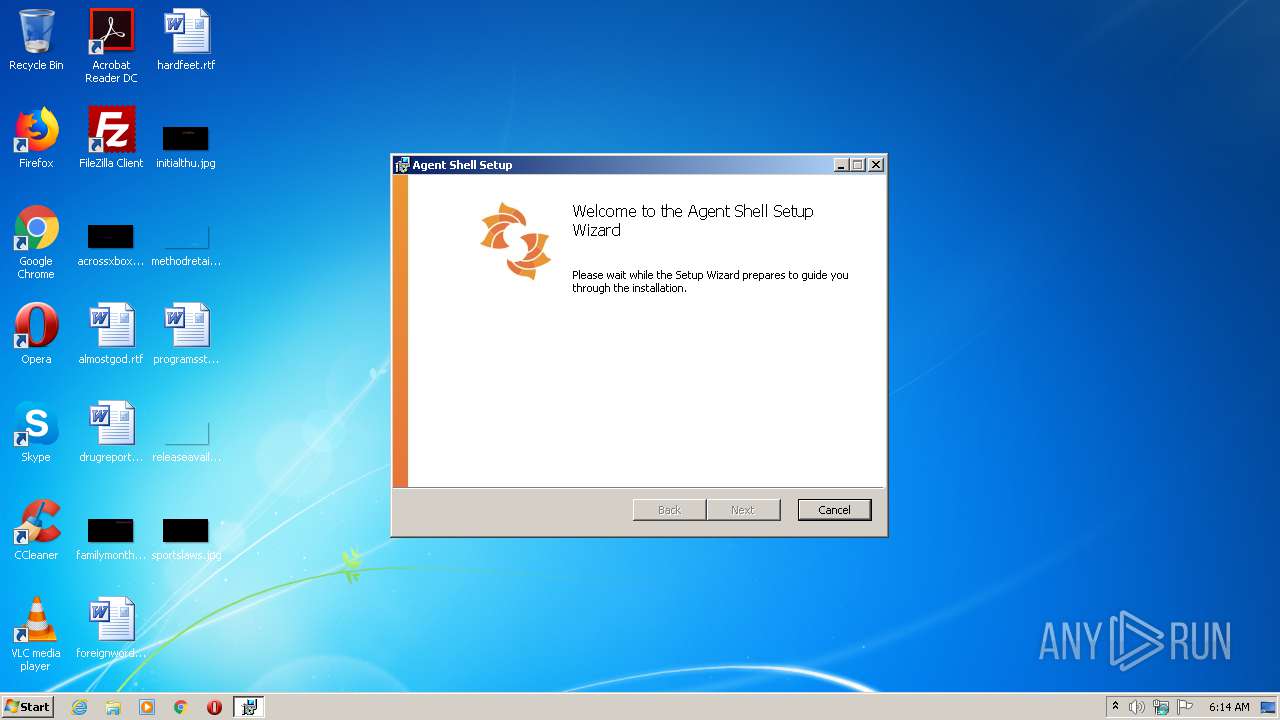
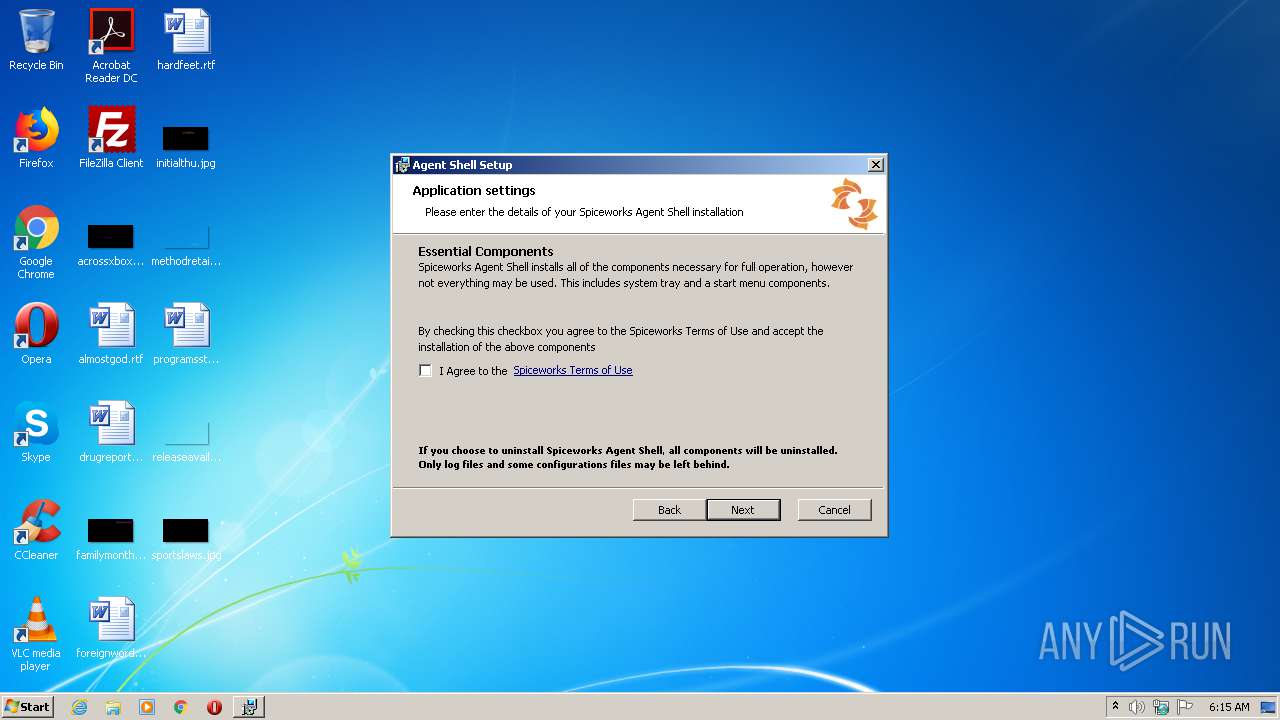
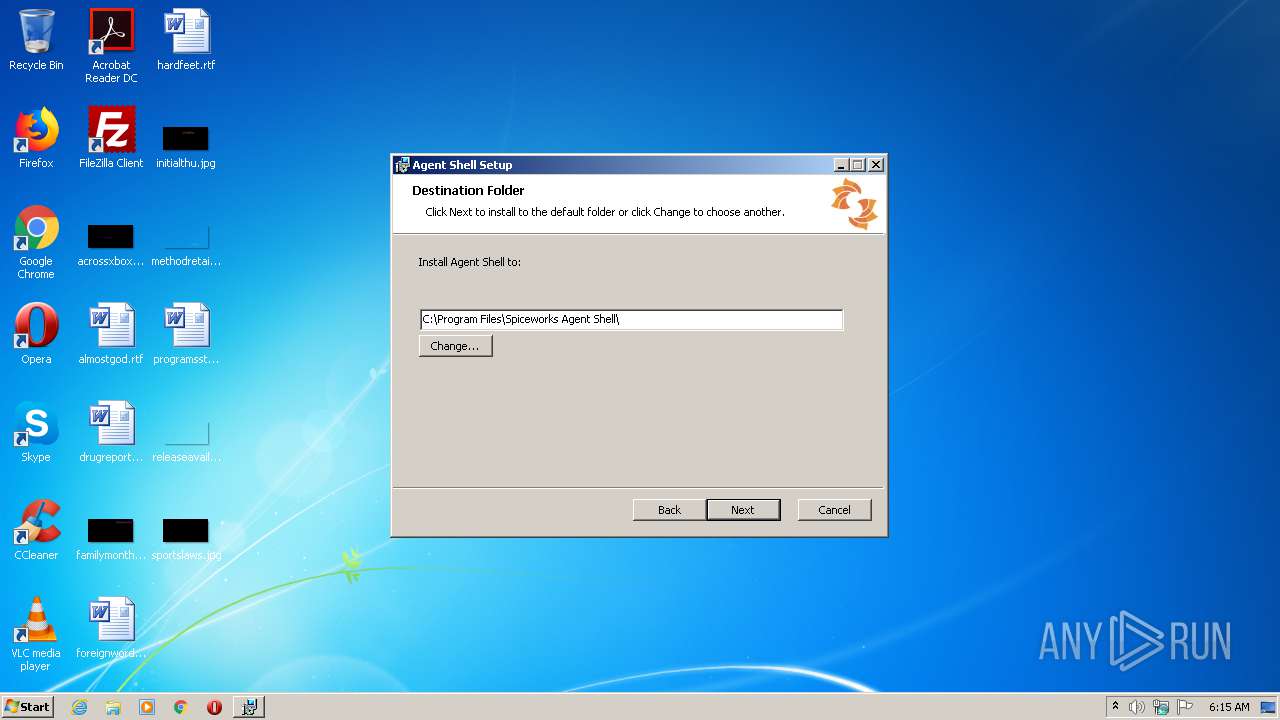
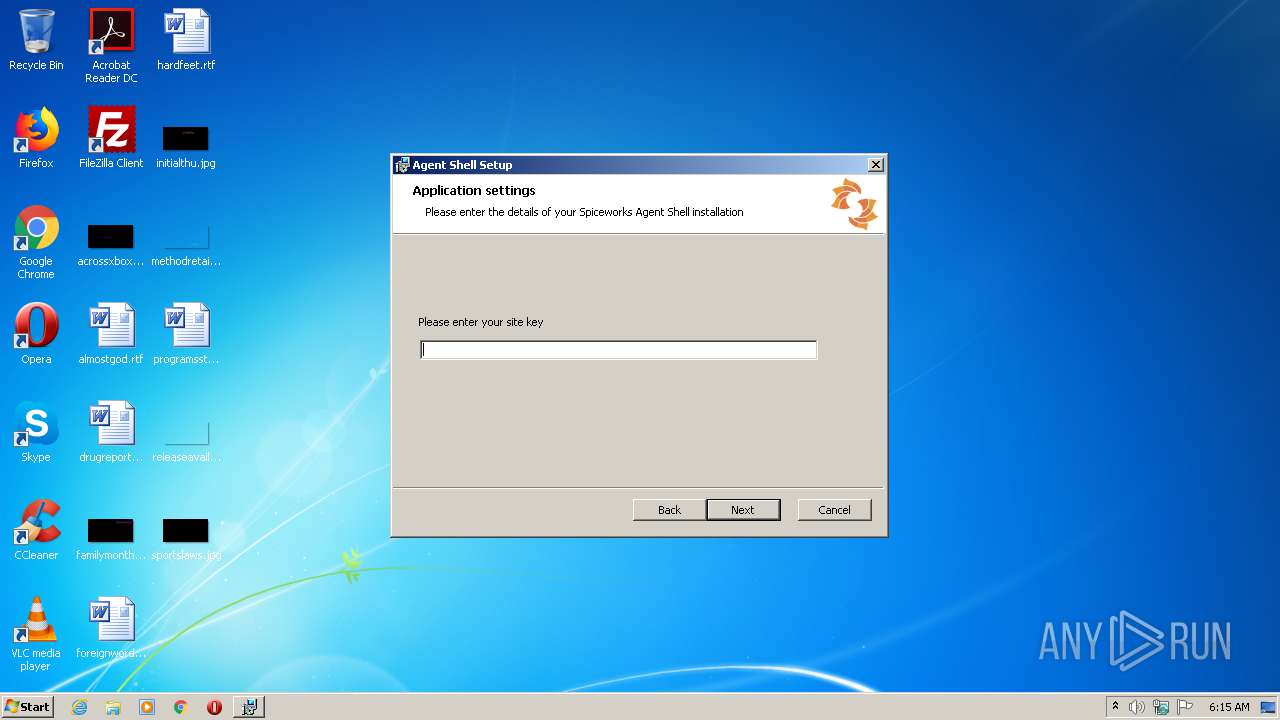
| File name: | SpiceworksAgentShell_Collection_Agent.msi |
| Full analysis: | https://app.any.run/tasks/67e19db7-0310-4972-a020-9a5f96f24740 |
| Verdict: | Malicious activity |
| Analysis date: | April 10, 2021, 05:14:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.3, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Product Description, Author: Spiceworks, Keywords: Installer, Comments: This installer database contains the logic and data required to install Agent Shell., Template: Intel;1033, Revision Number: {F87B1234-A3C6-405C-9C94-870E719822CB}, Create Time/Date: Mon Mar 9 22:35:44 2020, Last Saved Time/Date: Mon Mar 9 22:35:44 2020, Number of Pages: 500, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.11.1.2318), Security: 2 |
| MD5: | 4964F4481AA0F9E9980DA1447517E959 |
| SHA1: | 96F60A3C7F5A41AF522A745E2E8726BDBBFCD181 |
| SHA256: | CAA994EF7D21BF915D87E9ACED3F76BC1D5E8AFA438273E6810ABFE0557D0BD2 |
| SSDEEP: | 98304:TCsvBiMqDzwCudt6wveWzW/Ux30hslGxA2RCVXCwkhtT2aBtGaw:TCskZK6wveigSks/NXCwWt60N |
MALICIOUS
Drops executable file immediately after starts
- rundll32.exe (PID: 1856)
- rundll32.exe (PID: 3932)
Loads dropped or rewritten executable
- rundll32.exe (PID: 1856)
- rundll32.exe (PID: 3932)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- MsiExec.exe (PID: 3772)
Executable content was dropped or overwritten
- msiexec.exe (PID: 976)
- rundll32.exe (PID: 3932)
- rundll32.exe (PID: 1856)
Drops a file with too old compile date
- rundll32.exe (PID: 1856)
- rundll32.exe (PID: 3932)
Drops a file that was compiled in debug mode
- rundll32.exe (PID: 3932)
- msiexec.exe (PID: 976)
- rundll32.exe (PID: 1856)
INFO
Application launched itself
- msiexec.exe (PID: 3964)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 3772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Security: | Read-only recommended |
|---|---|
| Software: | Windows Installer XML Toolset (3.11.1.2318) |
| Words: | 2 |
| Pages: | 500 |
| ModifyDate: | 2020:03:09 22:35:44 |
| CreateDate: | 2020:03:09 22:35:44 |
| RevisionNumber: | {F87B1234-A3C6-405C-9C94-870E719822CB} |
| Template: | Intel;1033 |
| Comments: | This installer database contains the logic and data required to install Agent Shell. |
| Keywords: | Installer |
| Author: | Spiceworks |
| Subject: | Product Description |
| Title: | Installation Database |
| CodePage: | Windows Latin 1 (Western European) |
Total processes
43
Monitored processes
5
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 976 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\SpiceworksAgentShell_Collection_Agent.msi" | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1856 | rundll32.exe "C:\Users\admin\AppData\Local\Temp\MSI87F9.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_297046 1 InstallerCustomizations!InstallerCustomizations.CustomActions.ReadInProperties | C:\Windows\system32\rundll32.exe | MsiExec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3772 | C:\Windows\system32\MsiExec.exe -Embedding B6DB96B6DC74D0E94929A75103A0C7F5 C | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3932 | rundll32.exe "C:\Users\admin\AppData\Local\Temp\MSIAECB.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_306953 9 InstallerCustomizations!InstallerCustomizations.CustomActions.TestAgentSiteKey | C:\Windows\system32\rundll32.exe | MsiExec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3964 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
134
Read events
119
Write events
15
Delete events
0
Modification events
| (PID) Process: | (976) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (976) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\p2pcollab.dll,-8042 |
Value: Peer to Peer Trust | |||
| (PID) Process: | (976) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\qagentrt.dll,-10 |
Value: System Health Authentication | |||
| (PID) Process: | (976) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dnsapi.dll,-103 |
Value: Domain Name System (DNS) Server Trust | |||
| (PID) Process: | (976) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\fveui.dll,-843 |
Value: BitLocker Drive Encryption | |||
| (PID) Process: | (976) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\fveui.dll,-844 |
Value: BitLocker Data Recovery Agent | |||
Executable files
25
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1856 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI87F9.tmp-\Quartz.dll | executable | |
MD5:061CE3D8BB7202A602768E5F79F6A0B3 | SHA256:48FA4AC584E28DAF019BCD8C629873E1C4DBC9225450C79513761B386FBB77AC | |||
| 1856 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI87F9.tmp-\AgentShell.exe | executable | |
MD5:C9F146E9CC7D9512DE5244324A4EA4B8 | SHA256:AD659C9EB6A1E314EB4DDF19C0A6F692FE77CCA41B786964494C957824C81BFD | |||
| 1856 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI87F9.tmp-\InstallerCustomizations.dll | executable | |
MD5:32615D07EB4CCCF83B1344999894F460 | SHA256:4B0473602C9C79F71C594088772411C0CC4C4D50E89DDC9F52ED210ACFA9A9E1 | |||
| 1856 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI87F9.tmp-\Common.dll | executable | |
MD5:564D50EDD9C3E74253DBEA20C3EC41D7 | SHA256:0C9D6C65CCF0B90FD272BDEEE576AB8F945FAA3225F45B6124D6C2A126509823 | |||
| 1856 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI87F9.tmp-\CommandLine.dll | executable | |
MD5:3109B0C44BDA1182B1E26AAC75A8E47B | SHA256:ED734AADC426A0FA26DD67F8A8EA8A6864447EEA726E4CEDA778421C5FADECAB | |||
| 1856 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI87F9.tmp-\NLog.dll | executable | |
MD5:B70274014C925937F0F2E79DE6A17615 | SHA256:08F1F52716216FDBF4E918C88BEDD87C13D06D914E4F39673F2528237638107C | |||
| 1856 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI87F9.tmp-\Newtonsoft.Json.dll | executable | |
MD5:A6BE9EFDAA744E9947F4EE18DE5423BD | SHA256:6CC0CBCD5C4709C6A1C97F5581C347D93E586E7CC0D64BFFB4D32C6E753476A4 | |||
| 1856 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI87F9.tmp-\Microsoft.Win32.TaskScheduler.dll | executable | |
MD5:5B20A2A400174D3C05F5829FD3D23292 | SHA256:4EEB2CF066AAB0B67FBB3212C8E4CD1BB60A3DF8F962EA725AB14EDA0C92A730 | |||
| 976 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI87F9.tmp | executable | |
MD5:F35116A2D7DB54183698493AD15937B6 | SHA256:CBE7323F87B8922A36EFC638B4DCF99885566252010CCFCA3F6E7EF2585C4555 | |||
| 1856 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI87F9.tmp-\Common.Logging.Core.dll | executable | |
MD5:1830CD72D0EA37BAB9AF9FDF81FC96DE | SHA256:43D21A6EF97B8B9E02994BE1EAEE2D73EAAD10F2DC1FA100FD57636FFAFF446C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report