| download: | RWipeAndClean20.exe |
| Full analysis: | https://app.any.run/tasks/8b51f3fc-9763-4cc1-a56c-7061e6bdfedb |
| Verdict: | Malicious activity |
| Analysis date: | March 14, 2019, 08:49:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 02425174347FF2E5421AD17C3ED8076C |
| SHA1: | 0FF8022F6D5BB461732E795069F5BCB906B2FB1A |
| SHA256: | CA988B691A8EFFD6BA6F07E8EE3BB1AB74B35FEDB3DFC8B94D3A7BCD9E6BA597 |
| SSDEEP: | 393216:nNUujjjjDjjmxGan02xb7wG40PS1azsuiIOT1+zg9rCbHA1xRA2hgQF:nNxjjjjDjjmdH7d4nnZ+zg9ebHA1A4X |
MALICIOUS
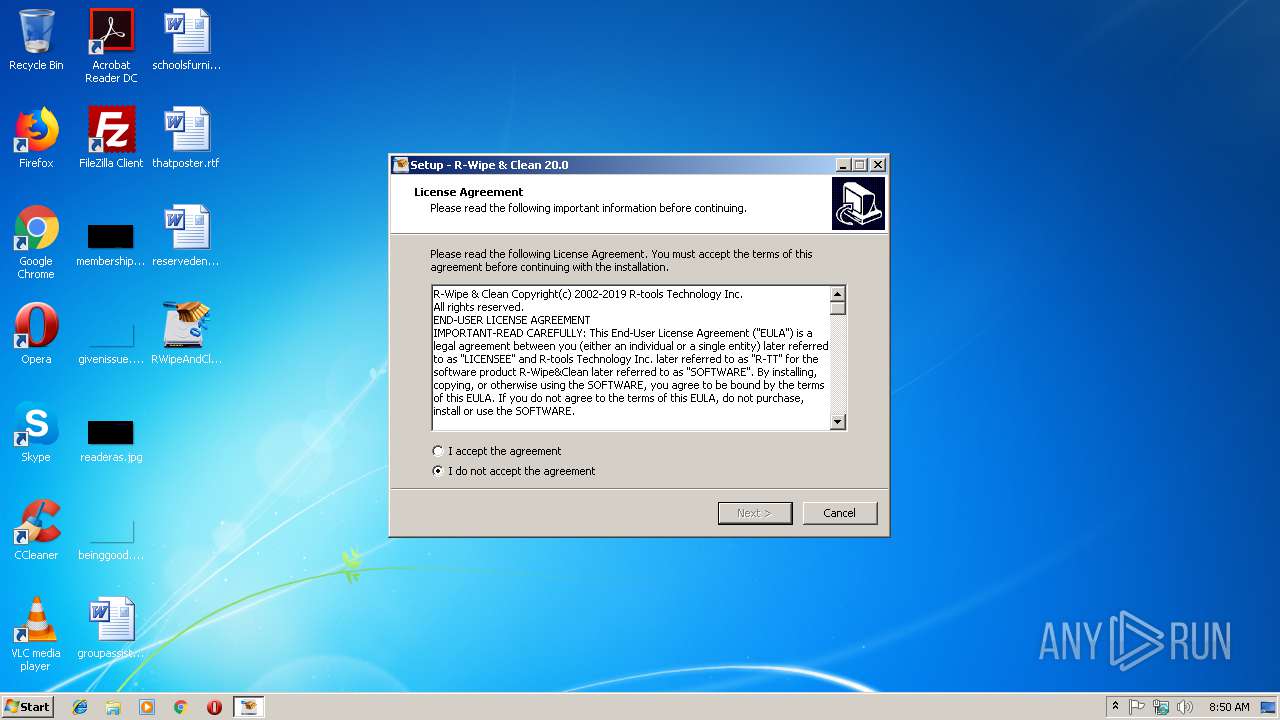
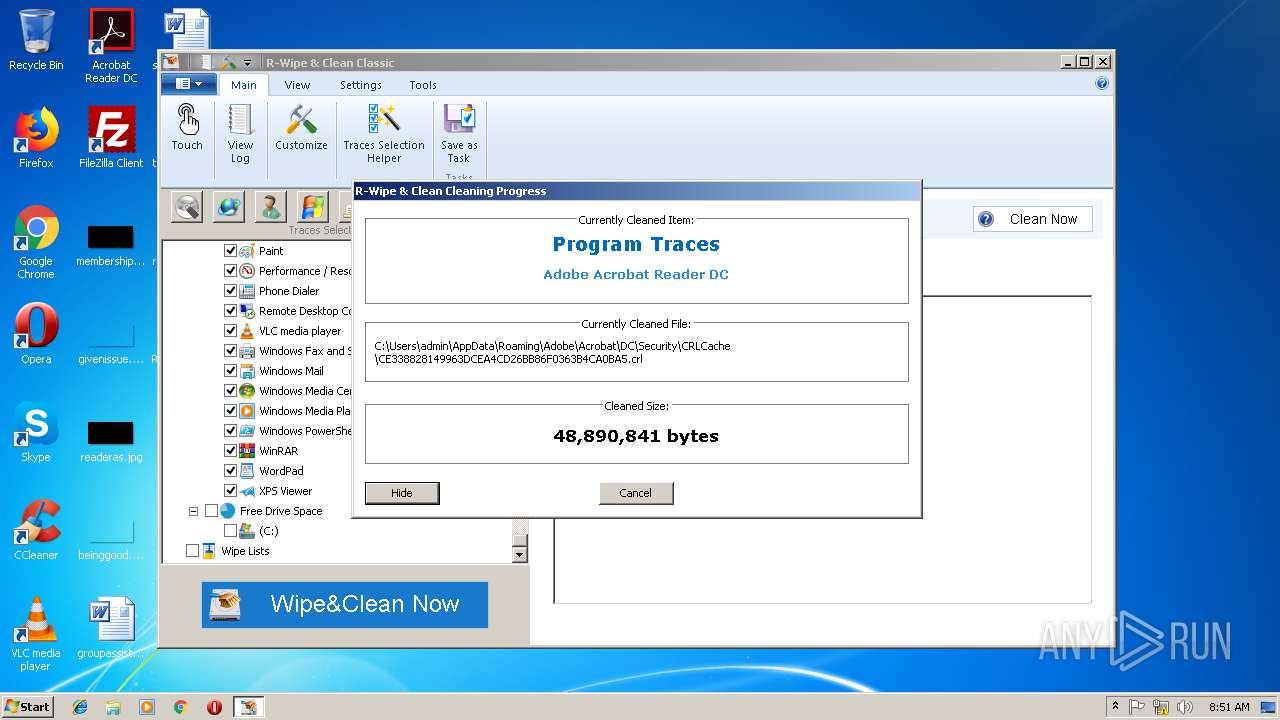
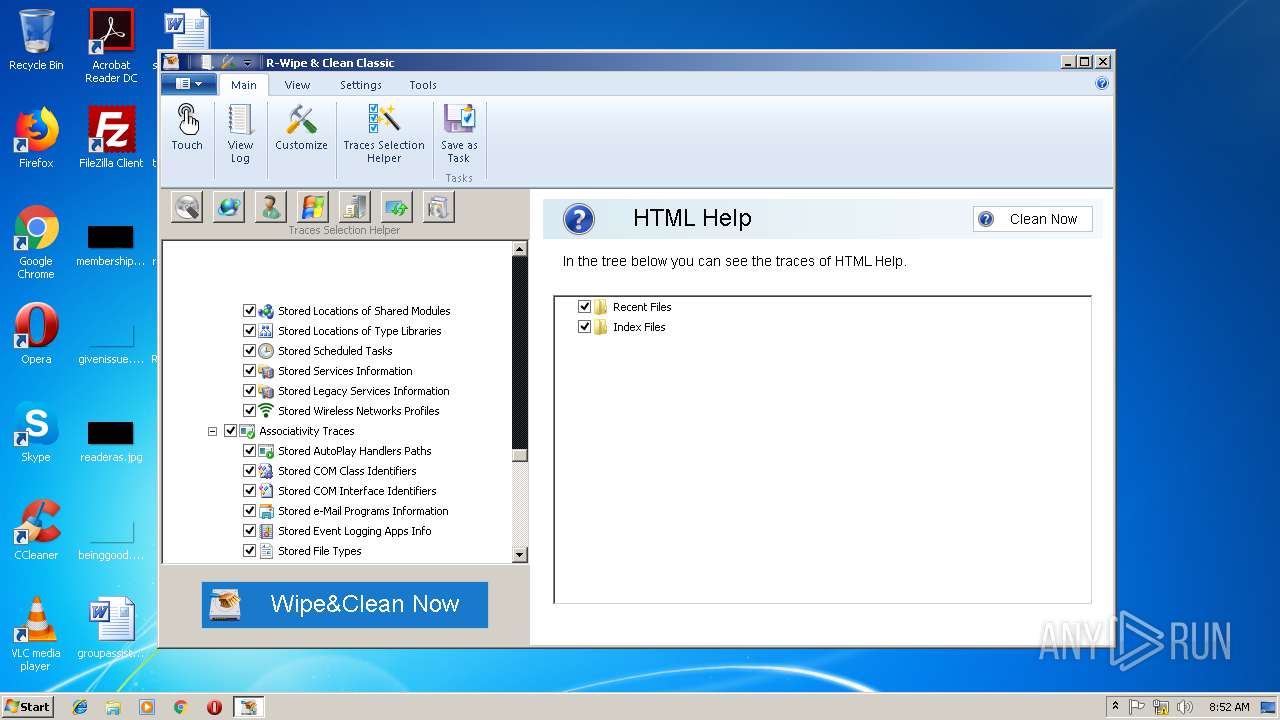
Registers / Runs the DLL via REGSVR32.EXE
- _RwcSetup.exe (PID: 3928)
Loads dropped or rewritten executable
- regsvr32.exe (PID: 1920)
- RwcRun.exe (PID: 3320)
- RwcRun.exe (PID: 2976)
Application was dropped or rewritten from another process
- _RwcSetup.exe (PID: 3928)
- RwcRun.exe (PID: 2392)
- RwcRun.exe (PID: 2976)
- RwcRun.exe (PID: 3320)
SUSPICIOUS
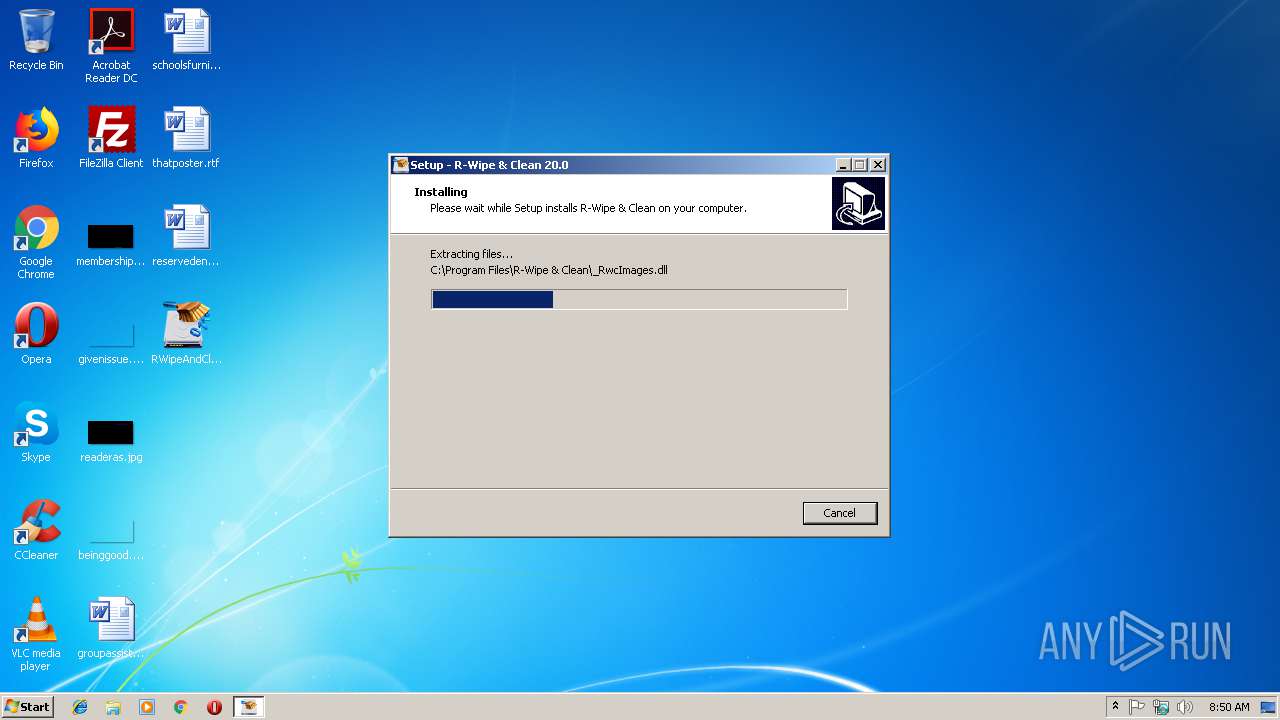
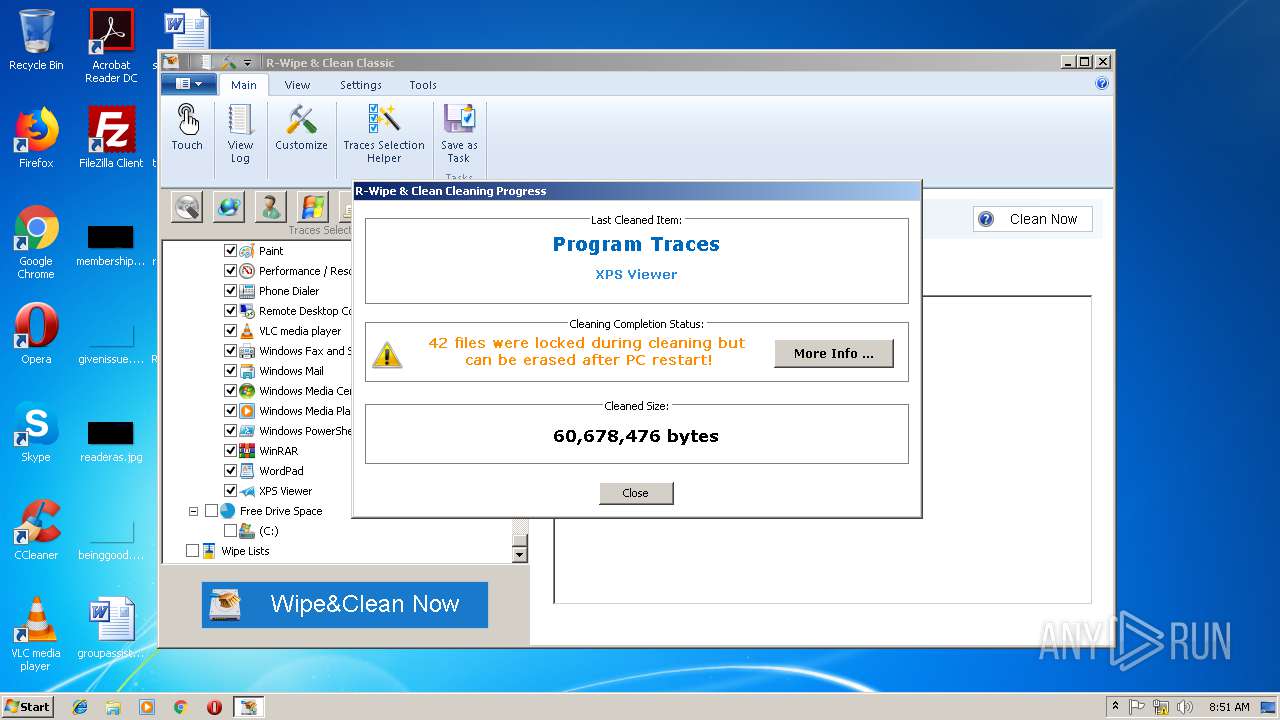
Executable content was dropped or overwritten
- RWipeAndClean20.exe (PID: 2236)
- RWipeAndClean20.exe (PID: 3424)
- RWipeAndClean20.tmp (PID: 4036)
- _RwcSetup.exe (PID: 3928)
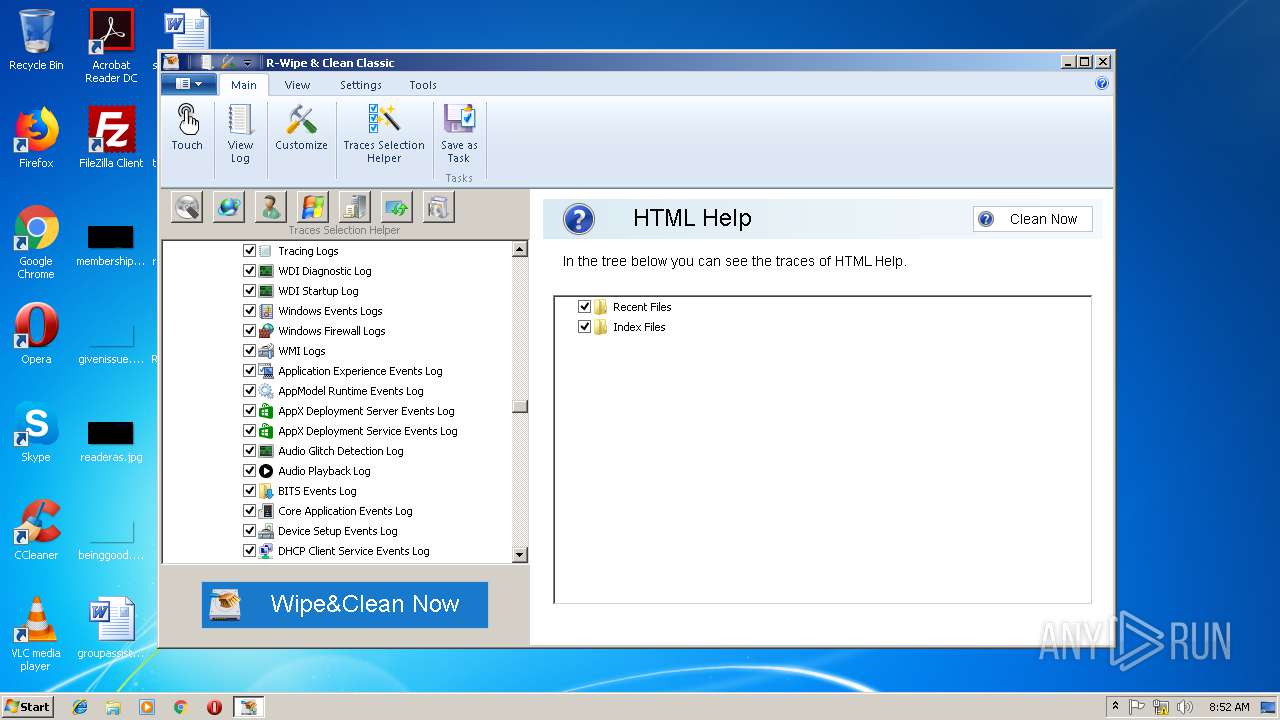
Reads the Windows organization settings
- RWipeAndClean20.tmp (PID: 4036)
Reads Windows owner or organization settings
- RWipeAndClean20.tmp (PID: 4036)
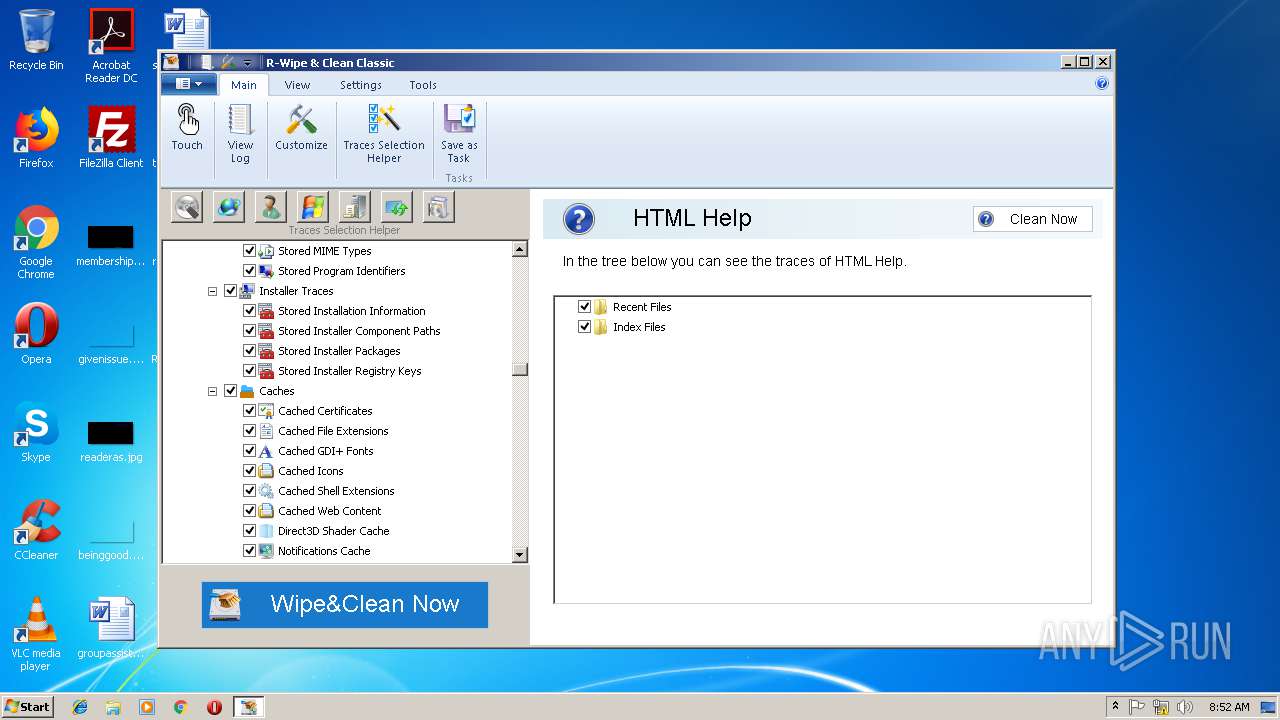
Creates files in the program directory
- _RwcSetup.exe (PID: 3928)
Creates COM task schedule object
- regsvr32.exe (PID: 1920)
Application launched itself
- RwcRun.exe (PID: 2976)
INFO
Application was dropped or rewritten from another process
- RWipeAndClean20.tmp (PID: 3256)
- RWipeAndClean20.tmp (PID: 4036)
Creates files in the program directory
- RWipeAndClean20.tmp (PID: 4036)
Creates a software uninstall entry
- RWipeAndClean20.tmp (PID: 4036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (42.6) |
|---|---|---|
| .exe | | | Win16/32 Executable Delphi generic (19.5) |
| .exe | | | Generic Win/DOS Executable (18.9) |
| .exe | | | DOS Executable Generic (18.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:06:14 15:27:46+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 66560 |
| InitializedDataSize: | 628736 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1181c |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | R-Tools Technology Inc. |
| FileDescription: | R-Wipe & Clean Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | R-Wipe & Clean |
| ProductVersion: | 20.0.2227 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 14-Jun-2018 13:27:46 |
| Detected languages: |
|
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | R-Tools Technology Inc. |
| FileDescription: | R-Wipe & Clean Setup |
| FileVersion: | - |
| LegalCopyright: | - |
| ProductName: | R-Wipe & Clean |
| ProductVersion: | 20.0.2227 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 14-Jun-2018 13:27:46 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0000F25C | 0x0000F400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.37588 |
.itext | 0x00011000 | 0x00000FA4 | 0x00001000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.77877 |
.data | 0x00012000 | 0x00000C8C | 0x00000E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.30283 |
.bss | 0x00013000 | 0x000056BC | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x00019000 | 0x00000E04 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.59781 |
.tls | 0x0001A000 | 0x00000008 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x0001B000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0.204488 |
.rsrc | 0x0001C000 | 0x0009762C | 0x00097800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.92229 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.13965 | 1580 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 5.26696 | 199800 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 5.2328 | 128168 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 5.30528 | 67624 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 5.72553 | 38056 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 5.89369 | 26600 | Latin 1 / Western European | English - United States | RT_ICON |
7 | 5.96955 | 21640 | Latin 1 / Western European | English - United States | RT_ICON |
8 | 6.14005 | 16936 | Latin 1 / Western European | English - United States | RT_ICON |
9 | 6.20983 | 9640 | Latin 1 / Western European | English - United States | RT_ICON |
10 | 5.36489 | 4264 | Latin 1 / Western European | English - United States | RT_ICON |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
oleaut32.dll |
user32.dll |
Total processes
48
Monitored processes
9
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1920 | regsvr32 /s RwcShl32.dll | C:\Windows\system32\regsvr32.exe | — | _RwcSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
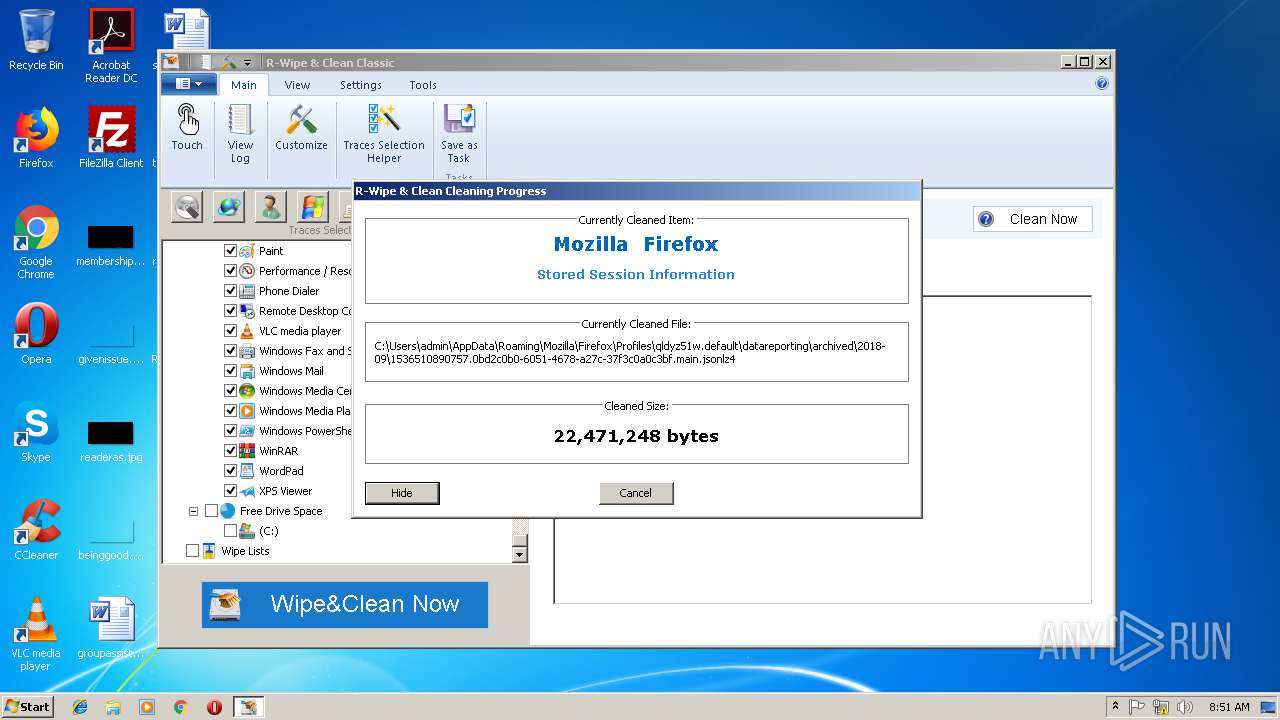
| 2236 | "C:\Users\admin\Desktop\RWipeAndClean20.exe" | C:\Users\admin\Desktop\RWipeAndClean20.exe | explorer.exe | ||||||||||||
User: admin Company: R-Tools Technology Inc. Integrity Level: MEDIUM Description: R-Wipe & Clean Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2392 | "C:\Program Files\R-Wipe & Clean\RwcRun.exe" | C:\Program Files\R-Wipe & Clean\RwcRun.exe | — | explorer.exe | |||||||||||
User: admin Company: R-Tools Inc. Integrity Level: MEDIUM Description: R-Wipe & Clean Exit code: 3221226540 Version: 20.0.0.2227 Modules
| |||||||||||||||
| 2976 | "C:\Program Files\R-Wipe & Clean\RwcRun.exe" | C:\Program Files\R-Wipe & Clean\RwcRun.exe | explorer.exe | ||||||||||||
User: admin Company: R-Tools Inc. Integrity Level: HIGH Description: R-Wipe & Clean Exit code: 0 Version: 20.0.0.2227 Modules
| |||||||||||||||
| 3256 | "C:\Users\admin\AppData\Local\Temp\is-S5M3F.tmp\RWipeAndClean20.tmp" /SL5="$30110,18491707,696320,C:\Users\admin\Desktop\RWipeAndClean20.exe" | C:\Users\admin\AppData\Local\Temp\is-S5M3F.tmp\RWipeAndClean20.tmp | — | RWipeAndClean20.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3320 | "C:\Program Files\R-Wipe & Clean\RwcRun.exe" /changeinterface | C:\Program Files\R-Wipe & Clean\RwcRun.exe | — | RwcRun.exe | |||||||||||
User: admin Company: R-Tools Inc. Integrity Level: HIGH Description: R-Wipe & Clean Exit code: 0 Version: 20.0.0.2227 Modules
| |||||||||||||||
| 3424 | "C:\Users\admin\Desktop\RWipeAndClean20.exe" /SPAWNWND=$20122 /NOTIFYWND=$30110 | C:\Users\admin\Desktop\RWipeAndClean20.exe | RWipeAndClean20.tmp | ||||||||||||
User: admin Company: R-Tools Technology Inc. Integrity Level: HIGH Description: R-Wipe & Clean Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3928 | "C:\Program Files\R-Wipe & Clean\_RwcSetup.exe" /installrwc | C:\Program Files\R-Wipe & Clean\_RwcSetup.exe | RWipeAndClean20.tmp | ||||||||||||
User: admin Company: R-Tools Inc. Integrity Level: HIGH Description: R-Wipe & Clean Installer Exit code: 0 Version: 20.0.0.2227 Modules
| |||||||||||||||
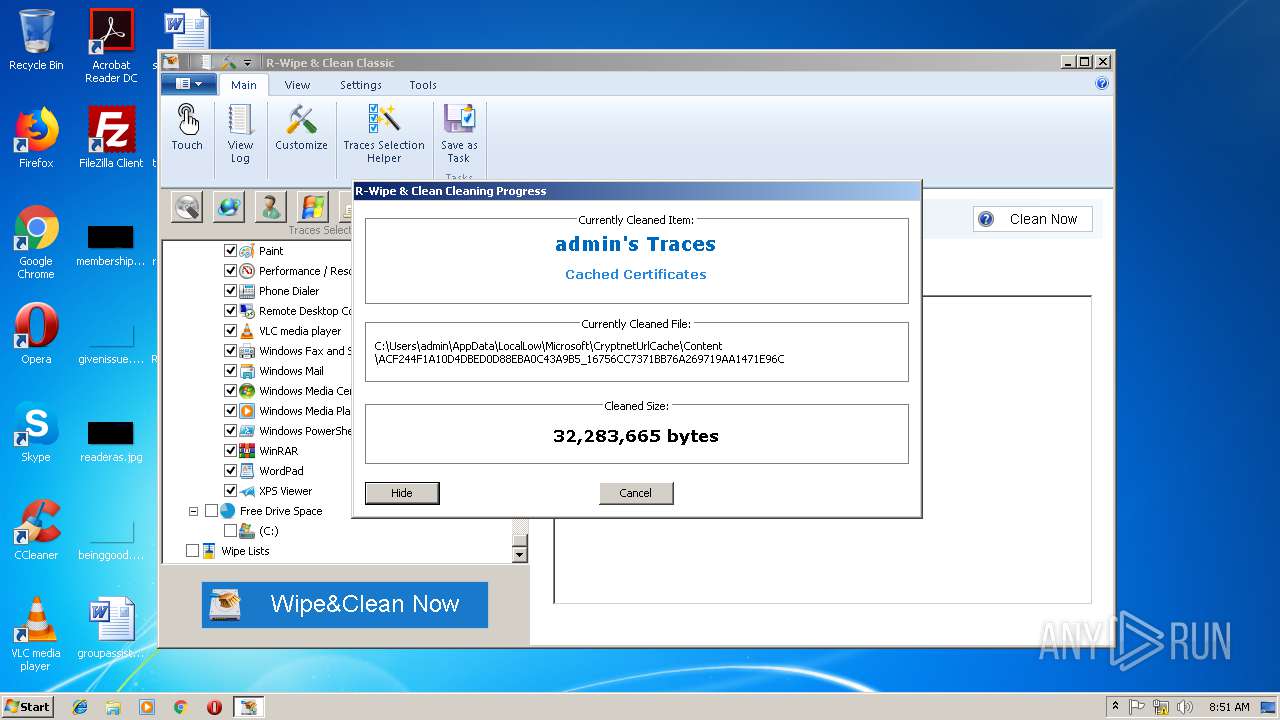
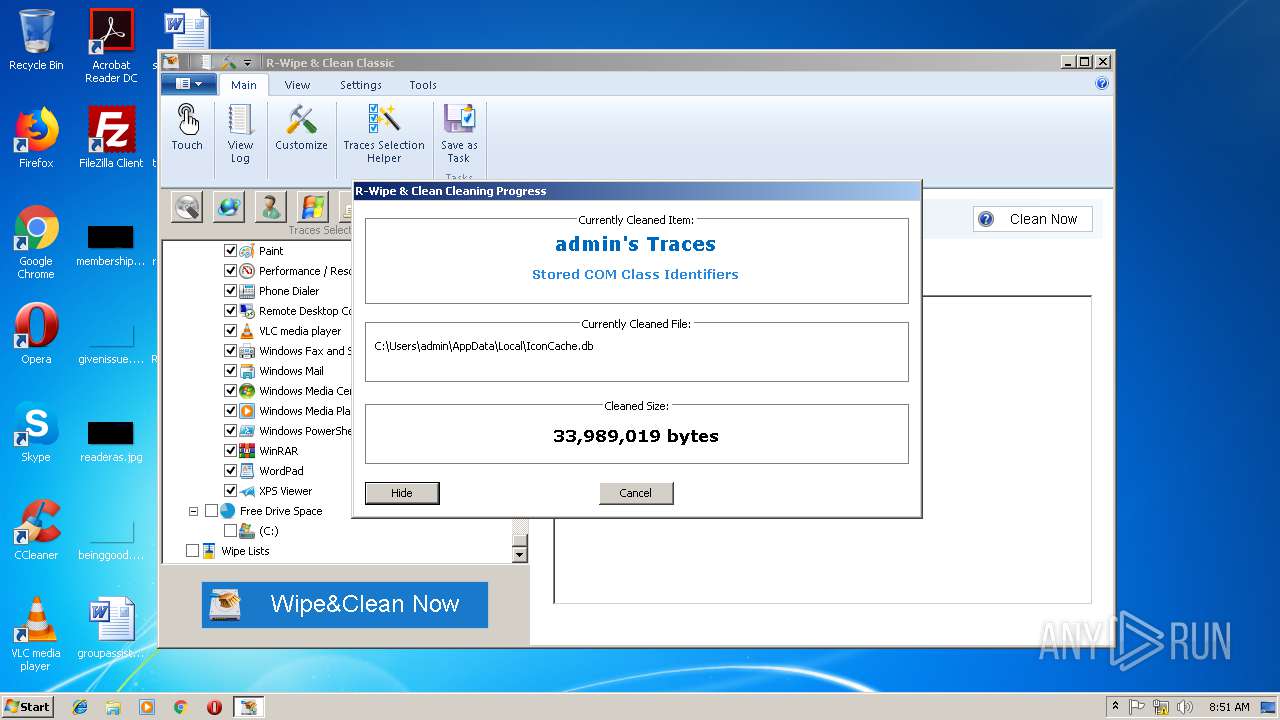
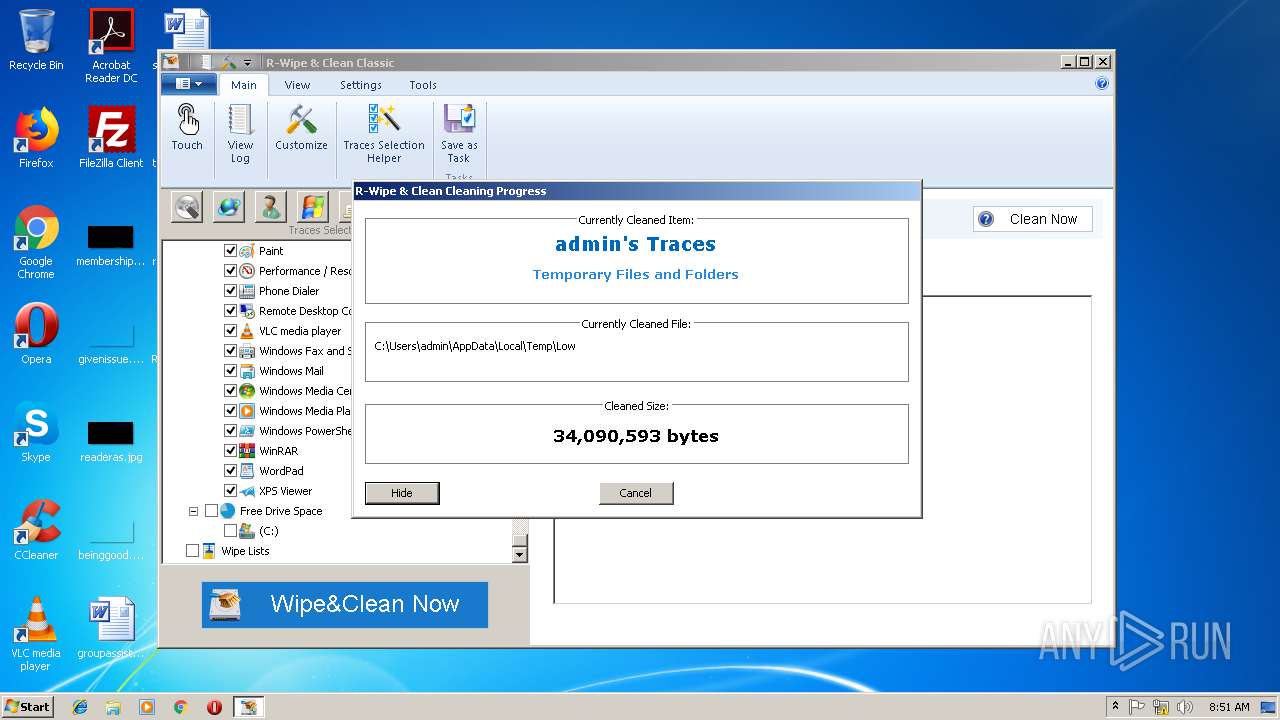
| 4036 | "C:\Users\admin\AppData\Local\Temp\is-JC2QJ.tmp\RWipeAndClean20.tmp" /SL5="$20128,18491707,696320,C:\Users\admin\Desktop\RWipeAndClean20.exe" /SPAWNWND=$20122 /NOTIFYWND=$30110 | C:\Users\admin\AppData\Local\Temp\is-JC2QJ.tmp\RWipeAndClean20.tmp | RWipeAndClean20.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
318
Read events
260
Write events
52
Delete events
6
Modification events
| (PID) Process: | (4036) RWipeAndClean20.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: C40F0000E44409E942DAD401 | |||
| (PID) Process: | (4036) RWipeAndClean20.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: E466EB2F5E4B5ACC6E11708F89A590F29E85373C22398F5D39C2EFA4F60BF357 | |||
| (PID) Process: | (4036) RWipeAndClean20.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (4036) RWipeAndClean20.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\R-Wipe & Clean\_RwcAdds.dll | |||
| (PID) Process: | (4036) RWipeAndClean20.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 7BA2A99D242187599765E9DE2F71C7A8DBB0309B67379591ACC5E20535651712 | |||
| (PID) Process: | (4036) RWipeAndClean20.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\R-Wipe & Clean_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.6.1 (u) | |||
| (PID) Process: | (4036) RWipeAndClean20.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\R-Wipe & Clean_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\R-Wipe & Clean | |||
| (PID) Process: | (4036) RWipeAndClean20.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\R-Wipe & Clean_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\R-Wipe & Clean\ | |||
| (PID) Process: | (4036) RWipeAndClean20.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\R-Wipe & Clean_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: R-Wipe & Clean | |||
| (PID) Process: | (4036) RWipeAndClean20.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\R-Wipe & Clean_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
Executable files
30
Suspicious files
0
Text files
3
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4036 | RWipeAndClean20.tmp | C:\Program Files\R-Wipe & Clean\is-VHE3U.tmp | — | |
MD5:— | SHA256:— | |||
| 4036 | RWipeAndClean20.tmp | C:\Program Files\R-Wipe & Clean\is-E83JI.tmp | — | |
MD5:— | SHA256:— | |||
| 4036 | RWipeAndClean20.tmp | C:\Program Files\R-Wipe & Clean\is-NT79U.tmp | — | |
MD5:— | SHA256:— | |||
| 4036 | RWipeAndClean20.tmp | C:\Program Files\R-Wipe & Clean\is-D9R32.tmp | — | |
MD5:— | SHA256:— | |||
| 4036 | RWipeAndClean20.tmp | C:\Program Files\R-Wipe & Clean\is-G9CEV.tmp | — | |
MD5:— | SHA256:— | |||
| 4036 | RWipeAndClean20.tmp | C:\Program Files\R-Wipe & Clean\is-NVJHO.tmp | — | |
MD5:— | SHA256:— | |||
| 4036 | RWipeAndClean20.tmp | C:\Program Files\R-Wipe & Clean\is-5OG3S.tmp | — | |
MD5:— | SHA256:— | |||
| 4036 | RWipeAndClean20.tmp | C:\Program Files\R-Wipe & Clean\is-GI4JQ.tmp | — | |
MD5:— | SHA256:— | |||
| 4036 | RWipeAndClean20.tmp | C:\Program Files\R-Wipe & Clean\is-J1FDO.tmp | — | |
MD5:— | SHA256:— | |||
| 4036 | RWipeAndClean20.tmp | C:\Program Files\R-Wipe & Clean\is-GC32O.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report