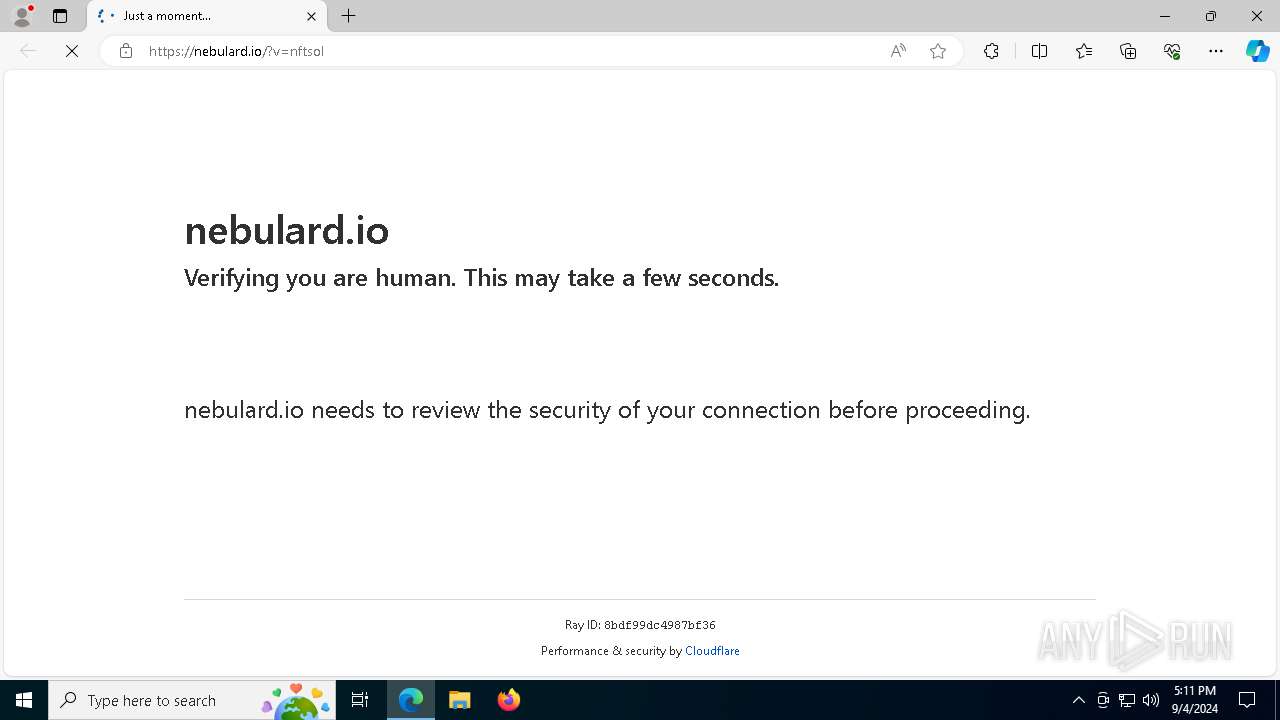
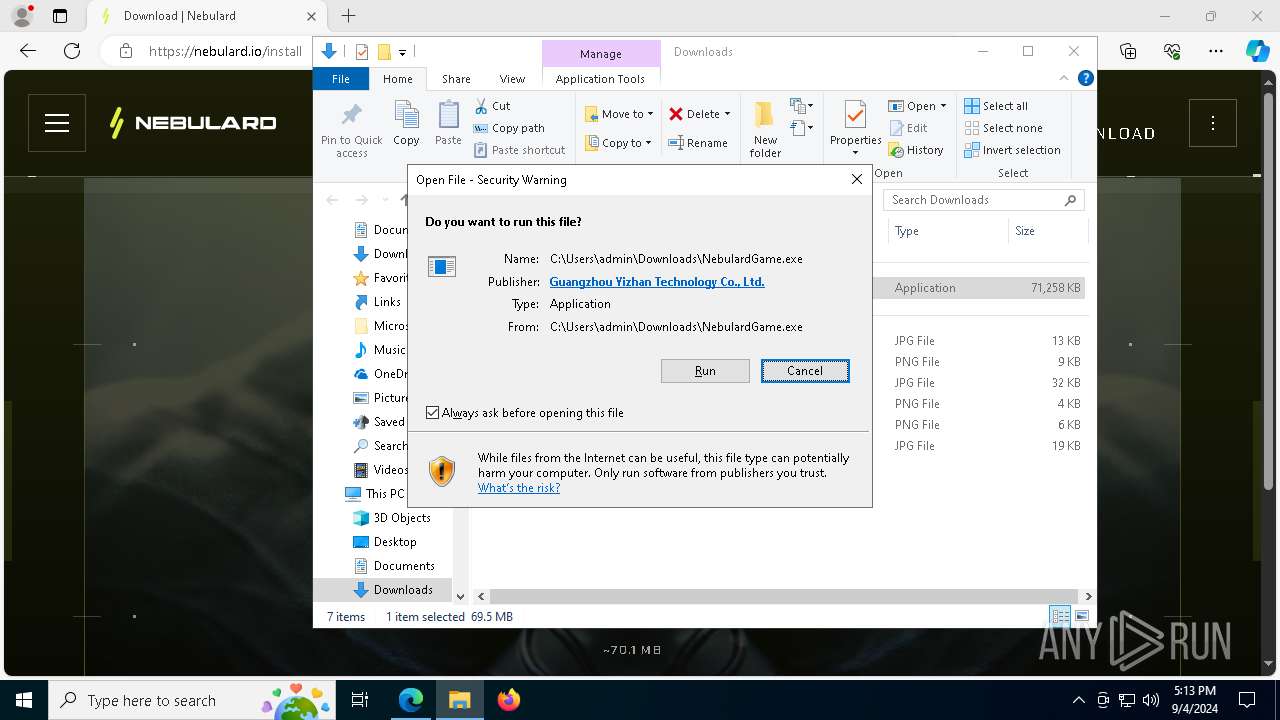
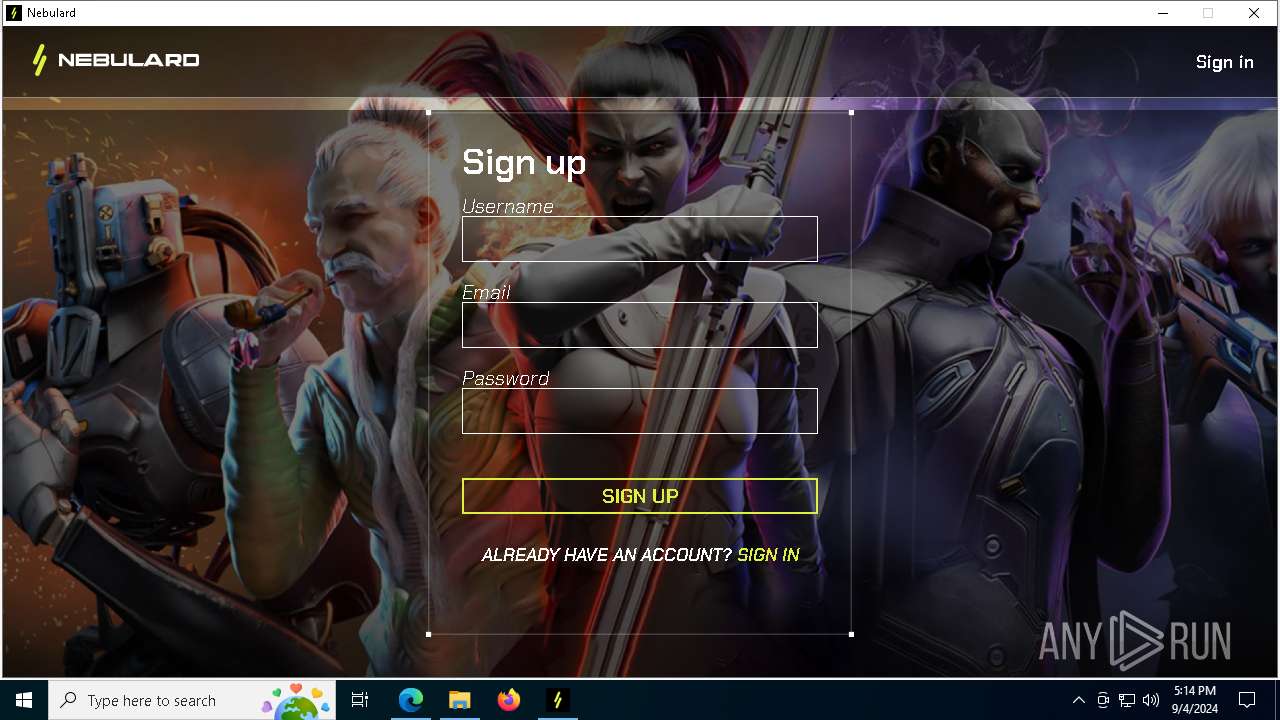
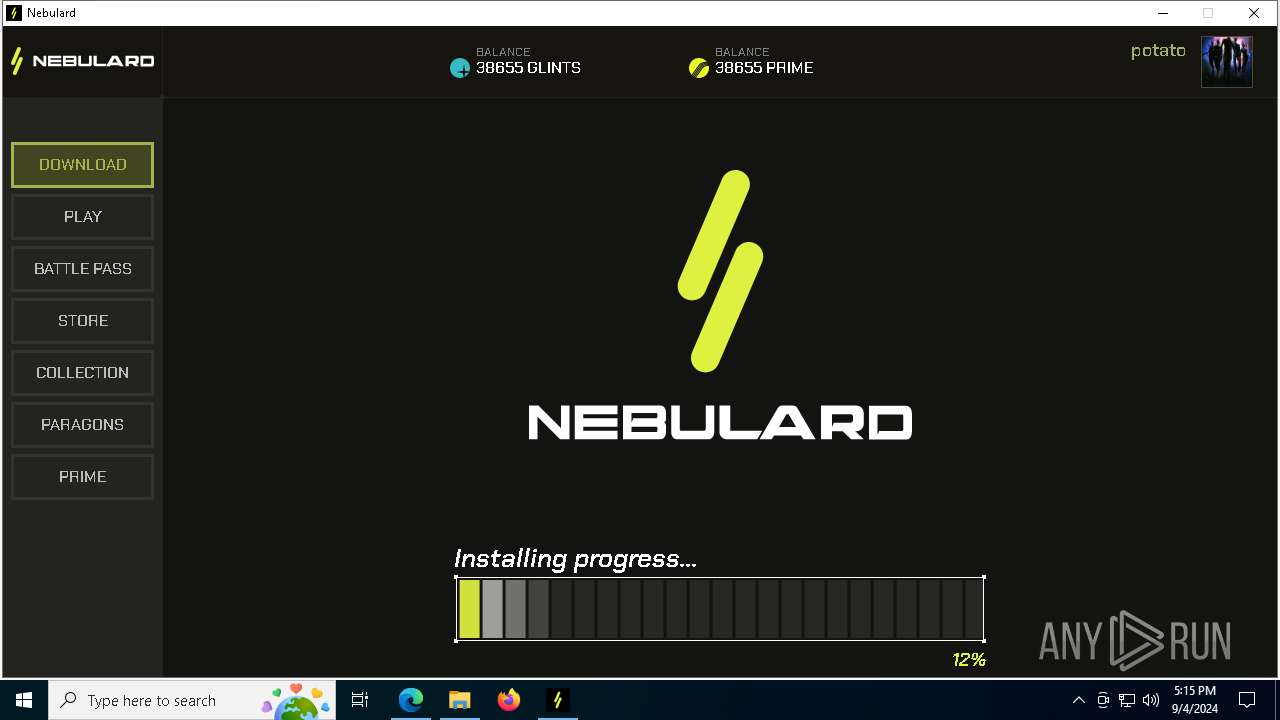
| URL: | https://nebulard.io/?v=nftsol |
| Full analysis: | https://app.any.run/tasks/6aaca556-e095-451b-81b3-1d8ae58c726b |
| Verdict: | Malicious activity |
| Analysis date: | September 04, 2024, 17:11:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | 59D1E03F44C86DAD712EA3DE82F00637 |
| SHA1: | 3022AF2160CB022CD7660377FC17F4C3A97118E7 |
| SHA256: | CA819839780ACE0FCADF9FF312AC1F967AD10E824379A1B0151BBAA7B5BF7900 |
| SSDEEP: | 3:N8tC0/Jn:2tb/Jn |
MALICIOUS
Changes powershell execution policy (Unrestricted)
- Nebulard.exe (PID: 2080)
SUSPICIOUS
The process creates files with name similar to system file names
- NebulardGame.exe (PID: 188)
Executable content was dropped or overwritten
- NebulardGame.exe (PID: 188)
Malware-specific behavior (creating "System.dll" in Temp)
- NebulardGame.exe (PID: 188)
Starts CMD.EXE for commands execution
- NebulardGame.exe (PID: 188)
- Nebulard.exe (PID: 6120)
- Nebulard.exe (PID: 2080)
Get information on the list of running processes
- NebulardGame.exe (PID: 188)
- cmd.exe (PID: 3896)
Drops 7-zip archiver for unpacking
- NebulardGame.exe (PID: 188)
Process drops legitimate windows executable
- NebulardGame.exe (PID: 188)
Application launched itself
- Nebulard.exe (PID: 6020)
Reads security settings of Internet Explorer
- NebulardGame.exe (PID: 188)
Creates a software uninstall entry
- NebulardGame.exe (PID: 188)
Starts application with an unusual extension
- cmd.exe (PID: 6248)
- cmd.exe (PID: 252)
Starts POWERSHELL.EXE for commands execution
- Nebulard.exe (PID: 2080)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3256)
The process hides Powershell's copyright startup banner
- Nebulard.exe (PID: 2080)
The process bypasses the loading of PowerShell profile settings
- Nebulard.exe (PID: 2080)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 1828)
INFO
Checks supported languages
- identity_helper.exe (PID: 3980)
- NebulardGame.exe (PID: 188)
- Nebulard.exe (PID: 2616)
- Nebulard.exe (PID: 6268)
- Nebulard.exe (PID: 6120)
- Nebulard.exe (PID: 2080)
- chcp.com (PID: 876)
- Nebulard.exe (PID: 6020)
- chcp.com (PID: 3996)
- Nebulard.exe (PID: 7848)
Application launched itself
- msedge.exe (PID: 7052)
Reads Environment values
- identity_helper.exe (PID: 3980)
- Nebulard.exe (PID: 6120)
- Nebulard.exe (PID: 2080)
Creates files or folders in the user directory
- explorer.exe (PID: 4552)
- NebulardGame.exe (PID: 188)
- Nebulard.exe (PID: 6020)
- Nebulard.exe (PID: 6268)
- Nebulard.exe (PID: 7848)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4552)
Reads the computer name
- identity_helper.exe (PID: 3980)
- NebulardGame.exe (PID: 188)
- Nebulard.exe (PID: 6268)
- Nebulard.exe (PID: 2616)
- Nebulard.exe (PID: 6020)
- Nebulard.exe (PID: 2080)
- Nebulard.exe (PID: 7848)
Executable content was dropped or overwritten
- msedge.exe (PID: 7052)
The process uses the downloaded file
- msedge.exe (PID: 2628)
- explorer.exe (PID: 4552)
- NebulardGame.exe (PID: 188)
- powershell.exe (PID: 1828)
- powershell.exe (PID: 6488)
- powershell.exe (PID: 6548)
- powershell.exe (PID: 1608)
- powershell.exe (PID: 1936)
- powershell.exe (PID: 4100)
- powershell.exe (PID: 7916)
- powershell.exe (PID: 6488)
- powershell.exe (PID: 7788)
- powershell.exe (PID: 7804)
- powershell.exe (PID: 7932)
- powershell.exe (PID: 7648)
- powershell.exe (PID: 7860)
- powershell.exe (PID: 7832)
- powershell.exe (PID: 7880)
- powershell.exe (PID: 5040)
- powershell.exe (PID: 3996)
- powershell.exe (PID: 6200)
- powershell.exe (PID: 2608)
- powershell.exe (PID: 7536)
Reads the software policy settings
- explorer.exe (PID: 4552)
- Nebulard.exe (PID: 6020)
Checks proxy server information
- explorer.exe (PID: 4552)
- Nebulard.exe (PID: 6020)
Create files in a temporary directory
- NebulardGame.exe (PID: 188)
- Nebulard.exe (PID: 6020)
Process checks computer location settings
- Nebulard.exe (PID: 6020)
- Nebulard.exe (PID: 6120)
- Nebulard.exe (PID: 2080)
Reads product name
- Nebulard.exe (PID: 6120)
- Nebulard.exe (PID: 2080)
Reads the machine GUID from the registry
- Nebulard.exe (PID: 6020)
- Nebulard.exe (PID: 7848)
Changes the display of characters in the console
- chcp.com (PID: 876)
- chcp.com (PID: 3996)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4100)
- powershell.exe (PID: 6200)
- powershell.exe (PID: 7932)
- powershell.exe (PID: 7860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
253
Monitored processes
122
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7008 --field-trial-handle=2348,i,4703200550763593350,2838853294570714690,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
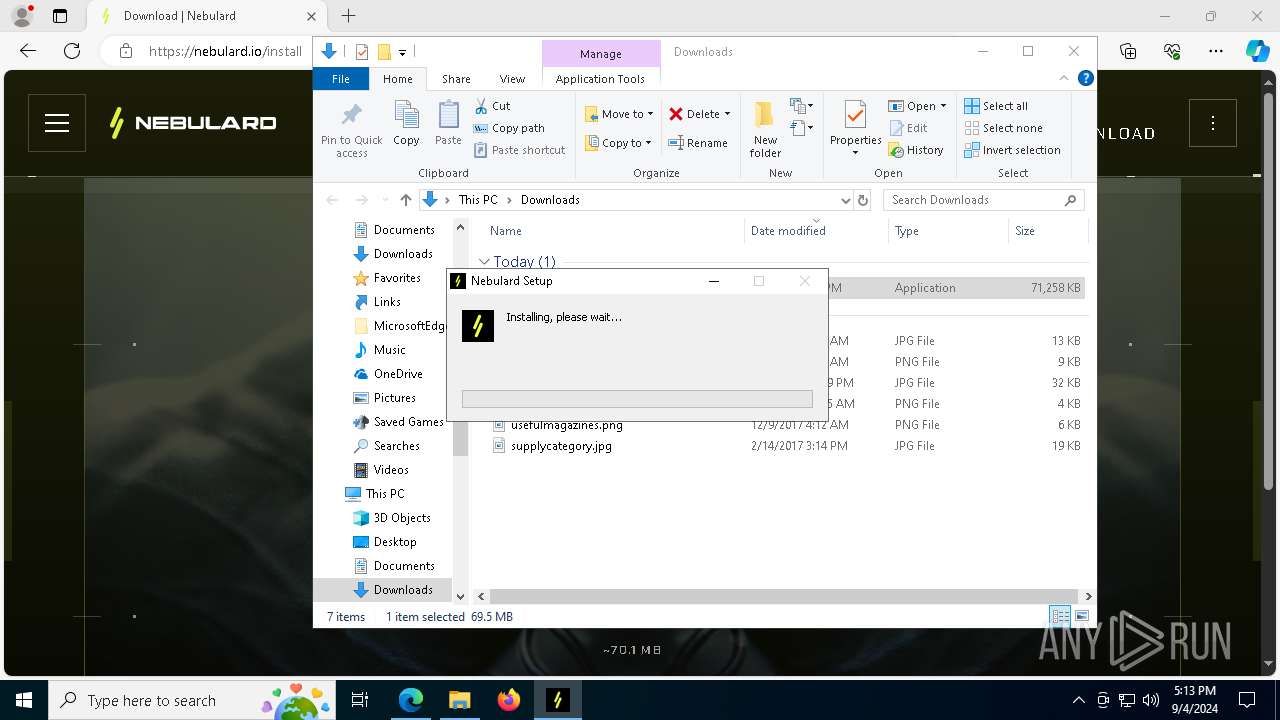
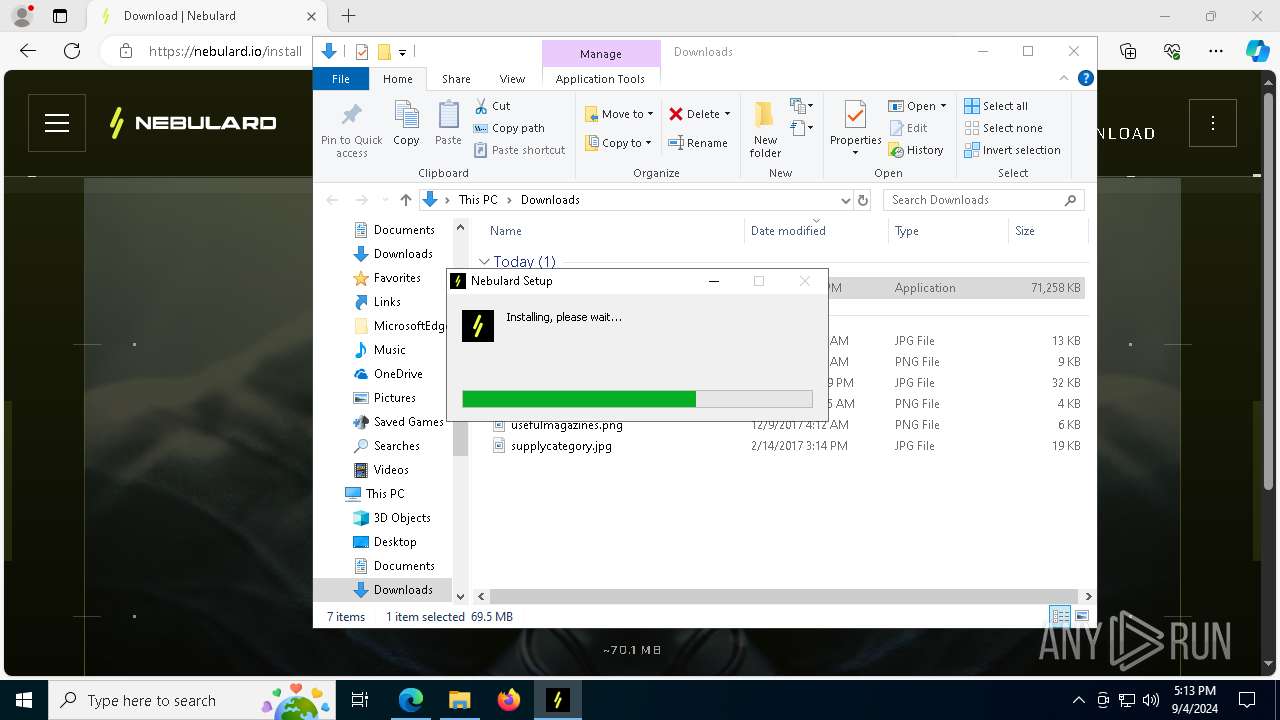
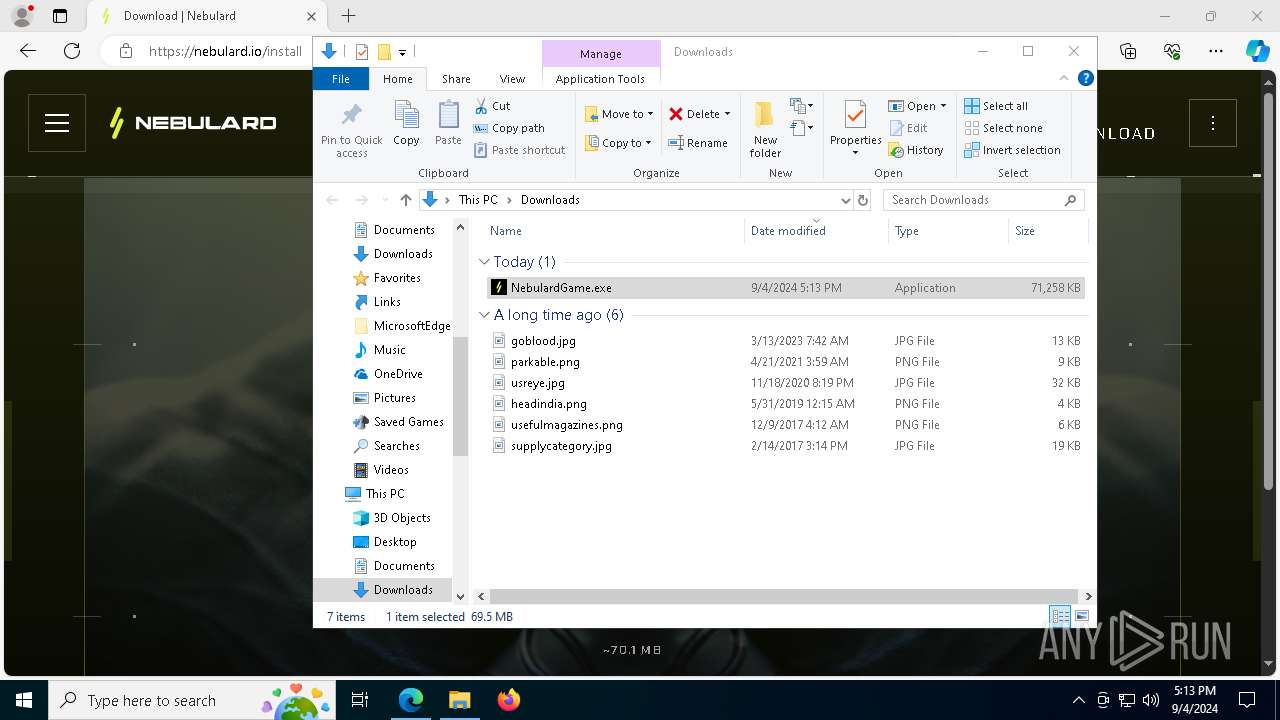
| 188 | "C:\Users\admin\Downloads\NebulardGame.exe" | C:\Users\admin\Downloads\NebulardGame.exe | explorer.exe | ||||||||||||
User: admin Company: Nebulard Integrity Level: MEDIUM Description: Nebulard Exit code: 0 Version: 3.5.4 Modules
| |||||||||||||||
| 208 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3732 --field-trial-handle=2348,i,4703200550763593350,2838853294570714690,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 252 | C:\WINDOWS\system32\cmd.exe /d /s /c "chcp" | C:\Windows\System32\cmd.exe | — | Nebulard.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=7388 --field-trial-handle=2348,i,4703200550763593350,2838853294570714690,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 488 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6848 --field-trial-handle=2348,i,4703200550763593350,2838853294570714690,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 876 | chcp | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5496 --field-trial-handle=2348,i,4703200550763593350,2838853294570714690,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1044 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1084 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=4352 --field-trial-handle=2348,i,4703200550763593350,2838853294570714690,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
123 493
Read events
123 404
Write events
69
Delete events
20
Modification events
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000070320 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456033BCEE44DE41B4E8AEC331E84F566D2 | |||
| (PID) Process: | (7052) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7052) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7052) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7052) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7052) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 0A9D858DE47F2F00 | |||
| (PID) Process: | (7052) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 2F608A8DE47F2F00 | |||
| (PID) Process: | (7052) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459552 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {5E7AA122-B6B0-42F9-A7CC-57026B0F0B86} | |||
| (PID) Process: | (7052) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459552 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {F6F659AD-2F1F-4F70-83A4-665932251901} | |||
| (PID) Process: | (7052) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459552 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {5AD7339C-ADCF-40C5-888D-372A76642083} | |||
Executable files
22
Suspicious files
517
Text files
201
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF12ad4f.TMP | — | |
MD5:— | SHA256:— | |||
| 7052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF12ad4f.TMP | — | |
MD5:— | SHA256:— | |||
| 7052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF12ad4f.TMP | — | |
MD5:— | SHA256:— | |||
| 7052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF12ad5f.TMP | — | |
MD5:— | SHA256:— | |||
| 7052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF12ad5f.TMP | — | |
MD5:— | SHA256:— | |||
| 7052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7052 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
121
DNS requests
140
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6252 | svchost.exe | GET | 200 | 72.246.158.76:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4552 | explorer.exe | GET | 200 | 34.237.184.165:80 | http://ocsps.ssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQg3SSkKA74hABkhmlBtJTz8w3hlAQU%2BWC71OPVNPa49QaAJadz20ZpqJ4CEEJLalPOx2YUHCpjsaUcQQQ%3D | unknown | — | — | whitelisted |
6268 | Nebulard.exe | POST | 403 | 104.21.42.101:80 | http://nebulard.io/api.php | unknown | — | — | unknown |
6160 | svchost.exe | HEAD | 200 | 146.75.94.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/cea821c9-eb81-47bf-8df8-0a52010d0e39?P1=1726040679&P2=404&P3=2&P4=EPg%2fvtaId13fD6hxTSgOMpPP%2fXwbdHNFOGeXjGZUOrbvj0%2bRdDKzKEzl8eNQ3vPabcIljjLHjqyJ64OUcqq2EQ%3d%3d | unknown | — | — | whitelisted |
6160 | svchost.exe | GET | 200 | 146.75.94.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/cea821c9-eb81-47bf-8df8-0a52010d0e39?P1=1726040679&P2=404&P3=2&P4=EPg%2fvtaId13fD6hxTSgOMpPP%2fXwbdHNFOGeXjGZUOrbvj0%2bRdDKzKEzl8eNQ3vPabcIljjLHjqyJ64OUcqq2EQ%3d%3d | unknown | — | — | whitelisted |
6160 | svchost.exe | HEAD | 200 | 146.75.94.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a1310cb6-94be-46c6-b8dc-986450234260?P1=1725571405&P2=404&P3=2&P4=GiMw%2f0N%2bEpATNkorU6DsmoEg%2bg8%2bHr9CcysozlwvRoBniKdM%2brxp85%2bs84xA01QjCRIVMGfVssWd3ypZHdaaUw%3d%3d | unknown | — | — | whitelisted |
6160 | svchost.exe | GET | 206 | 146.75.94.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a1310cb6-94be-46c6-b8dc-986450234260?P1=1725571405&P2=404&P3=2&P4=GiMw%2f0N%2bEpATNkorU6DsmoEg%2bg8%2bHr9CcysozlwvRoBniKdM%2brxp85%2bs84xA01QjCRIVMGfVssWd3ypZHdaaUw%3d%3d | unknown | — | — | whitelisted |
6160 | svchost.exe | GET | 206 | 146.75.94.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a1310cb6-94be-46c6-b8dc-986450234260?P1=1725571405&P2=404&P3=2&P4=GiMw%2f0N%2bEpATNkorU6DsmoEg%2bg8%2bHr9CcysozlwvRoBniKdM%2brxp85%2bs84xA01QjCRIVMGfVssWd3ypZHdaaUw%3d%3d | unknown | — | — | whitelisted |
6160 | svchost.exe | GET | 206 | 146.75.94.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a1310cb6-94be-46c6-b8dc-986450234260?P1=1725571405&P2=404&P3=2&P4=GiMw%2f0N%2bEpATNkorU6DsmoEg%2bg8%2bHr9CcysozlwvRoBniKdM%2brxp85%2bs84xA01QjCRIVMGfVssWd3ypZHdaaUw%3d%3d | unknown | — | — | whitelisted |
6160 | svchost.exe | GET | 206 | 146.75.94.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a1310cb6-94be-46c6-b8dc-986450234260?P1=1725571405&P2=404&P3=2&P4=GiMw%2f0N%2bEpATNkorU6DsmoEg%2bg8%2bHr9CcysozlwvRoBniKdM%2brxp85%2bs84xA01QjCRIVMGfVssWd3ypZHdaaUw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4276 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6252 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5096 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7052 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5096 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5096 | msedge.exe | 131.253.33.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5096 | msedge.exe | 13.107.246.71:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5096 | msedge.exe | 104.21.42.101:443 | nebulard.io | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
nebulard.io |
| unknown |
edge.microsoft.com |
| whitelisted |
api.edgeoffer.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
www.bing.com |
| whitelisted |
challenges.cloudflare.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
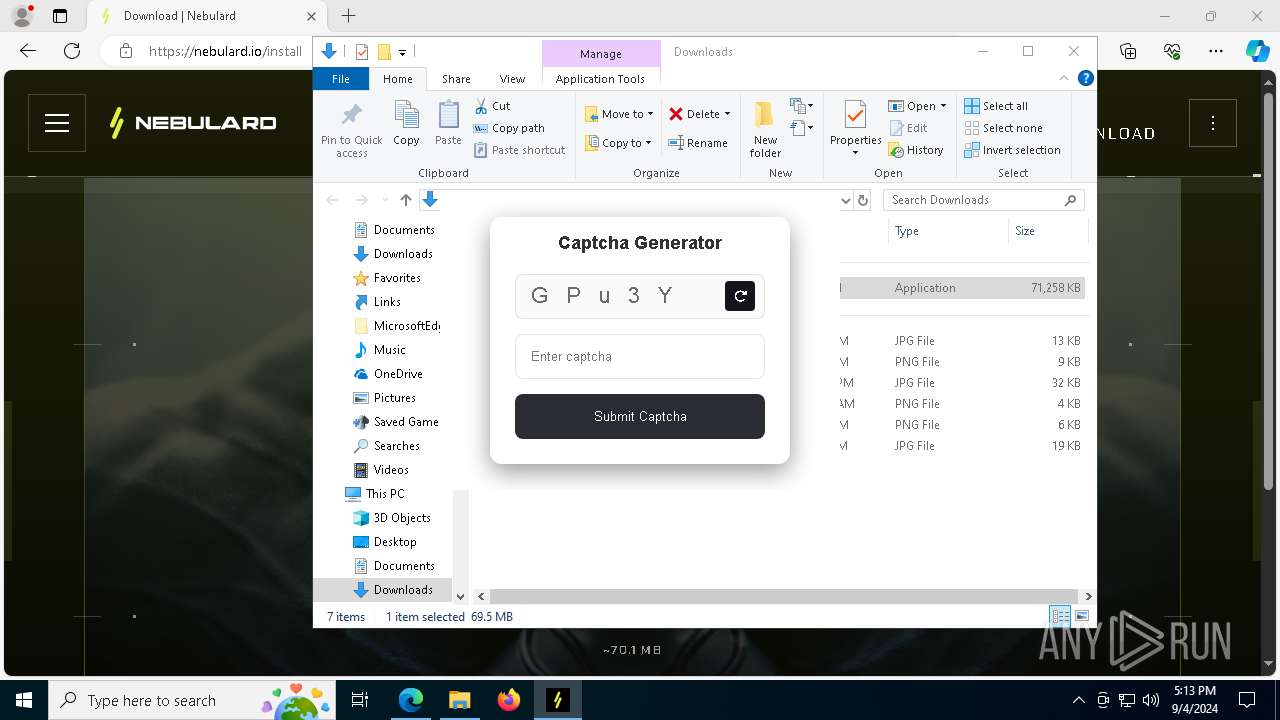
5096 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
5096 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
5096 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
5096 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
5096 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
5096 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
5096 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
5096 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
5096 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
5096 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |