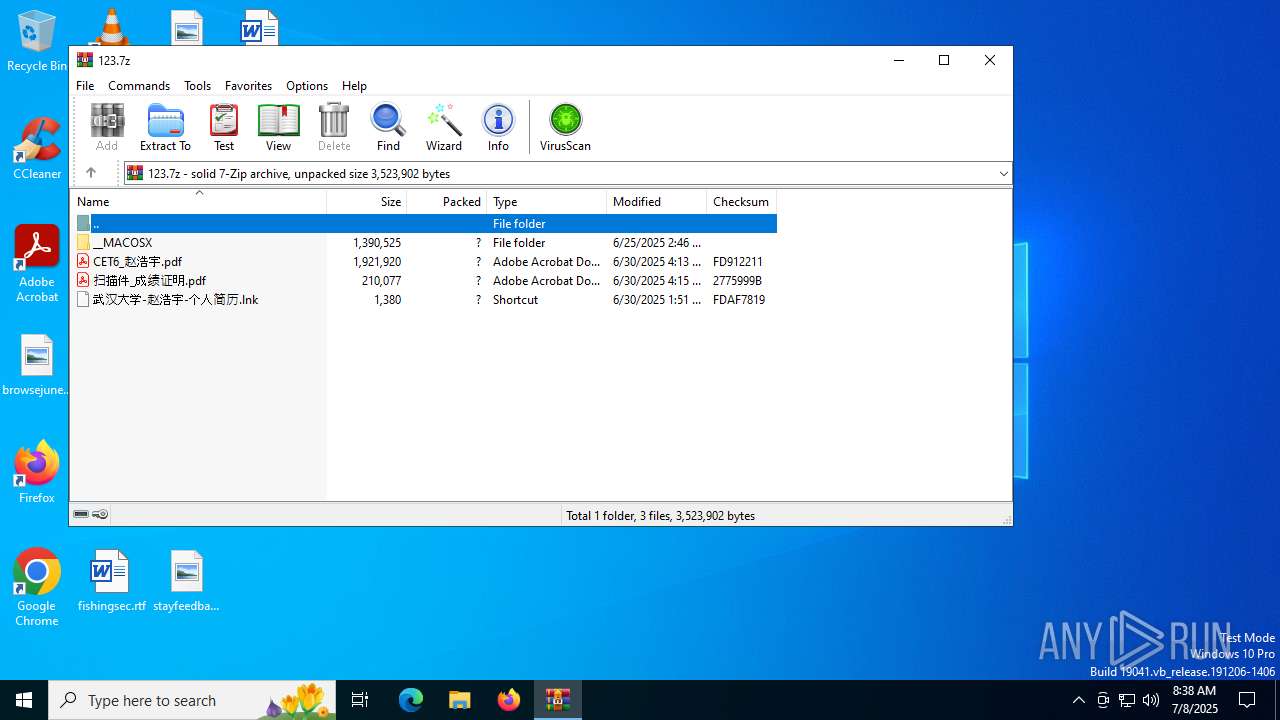
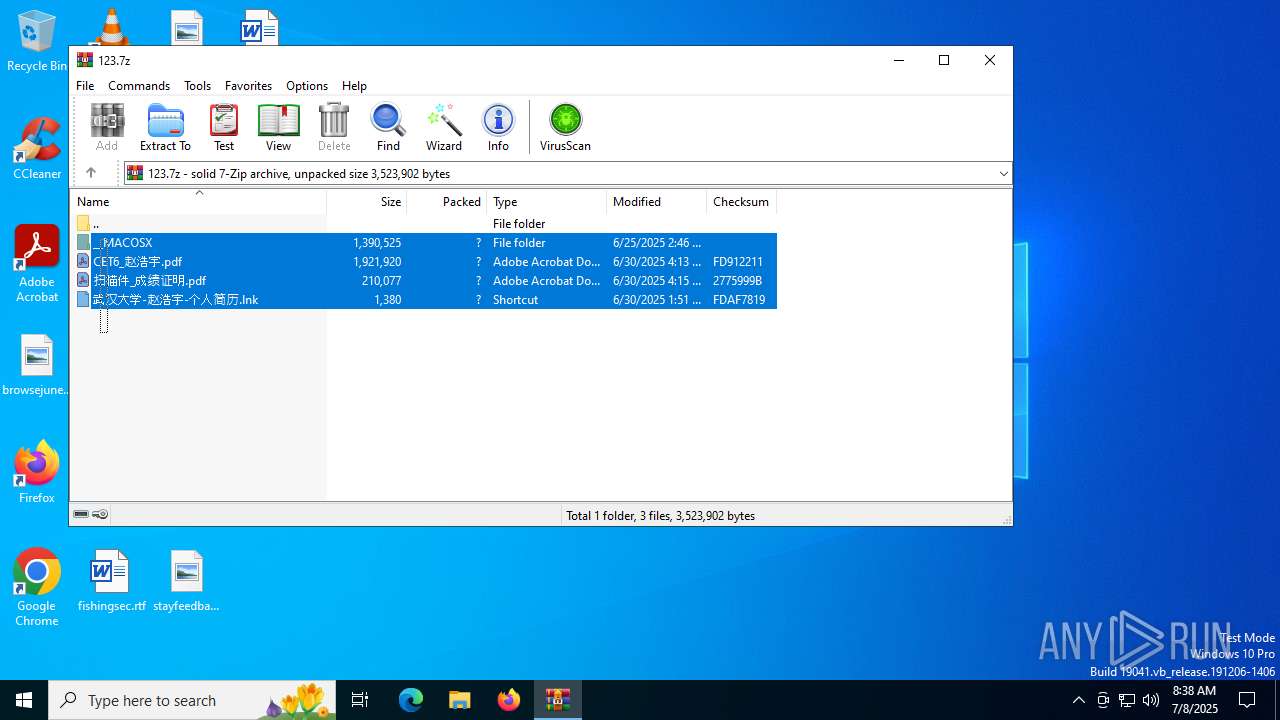
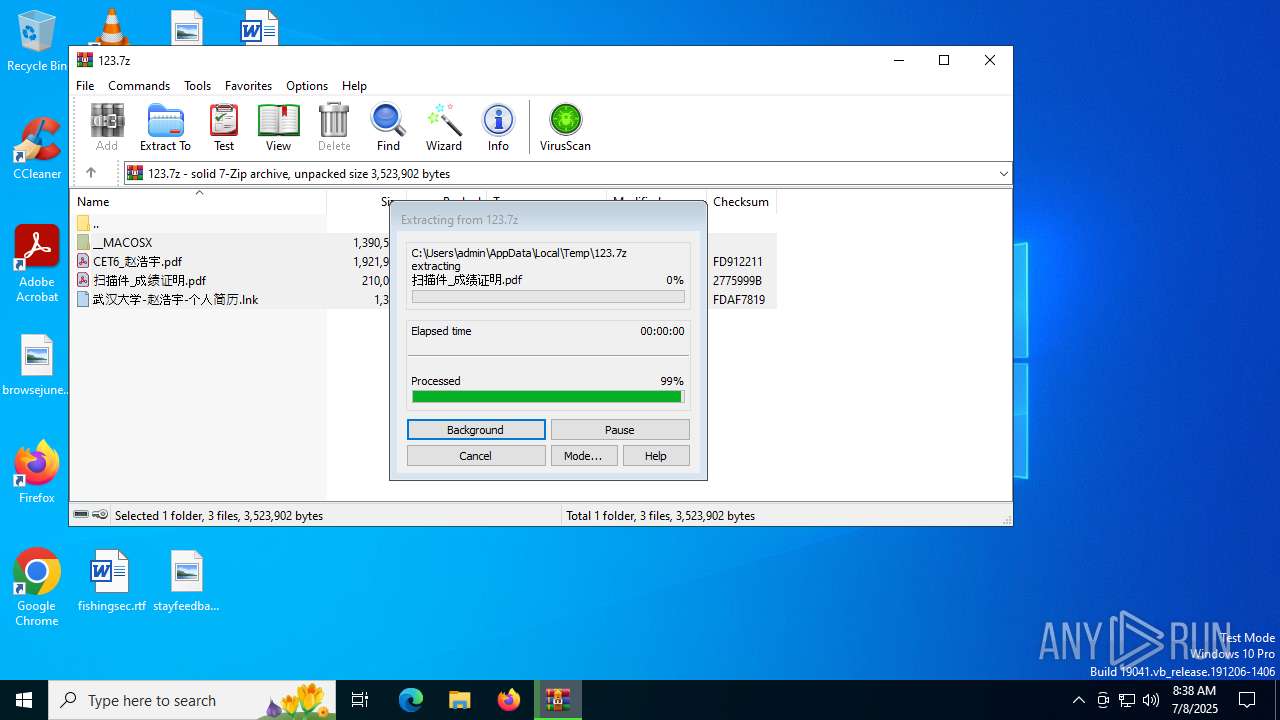
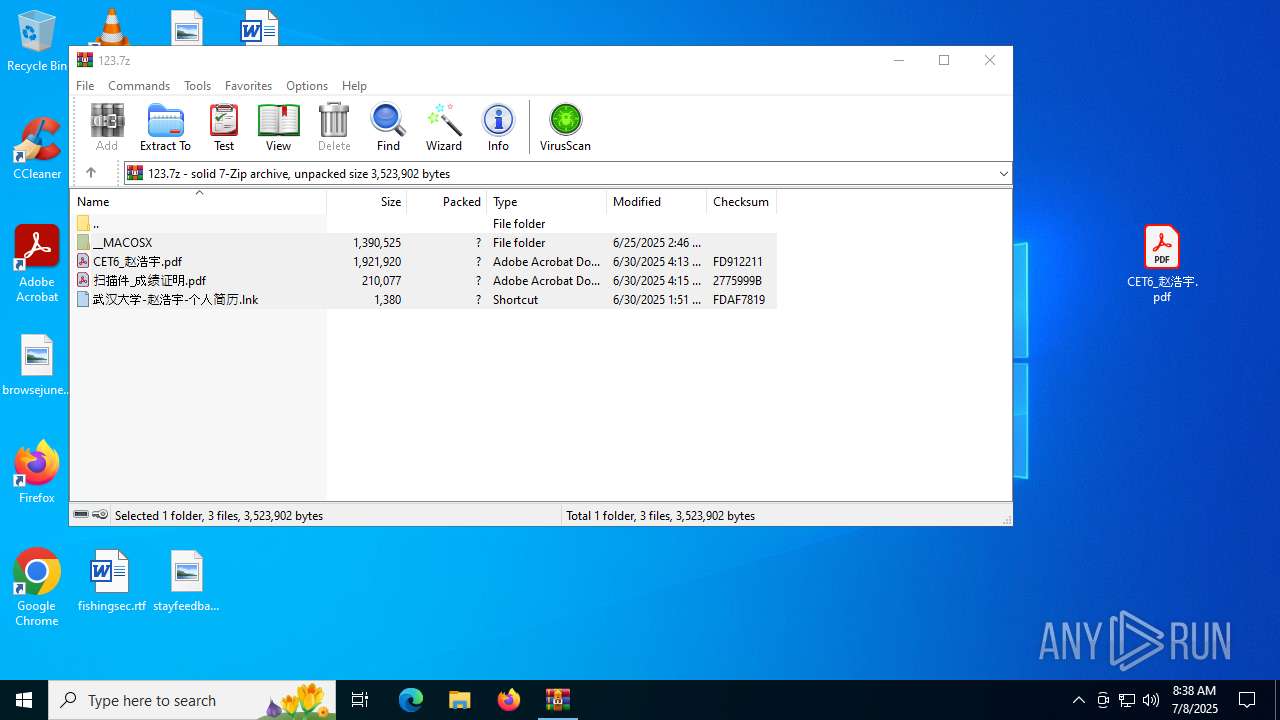
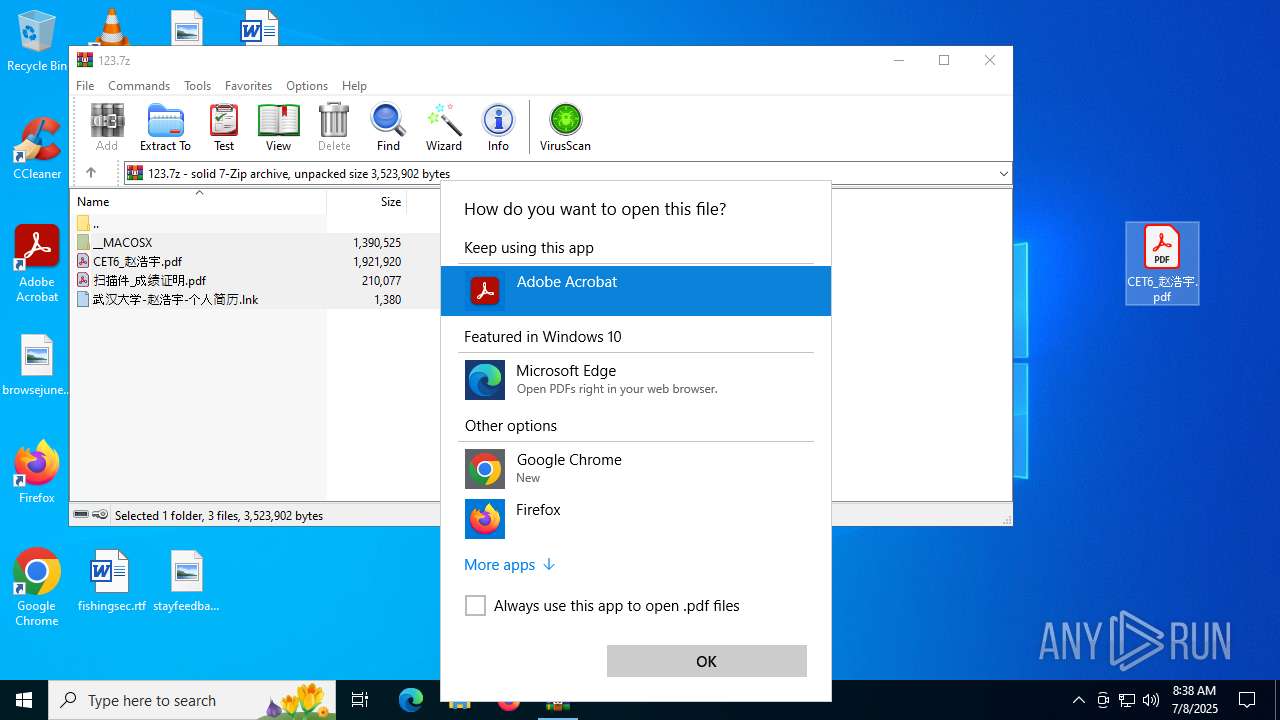
| File name: | 123.7z |
| Full analysis: | https://app.any.run/tasks/5271976e-36ac-4947-a385-cd094a9c1abf |
| Verdict: | Malicious activity |
| Analysis date: | July 08, 2025, 08:38:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.3 |
| MD5: | E7D80B84B767C0214342C74097B4747A |
| SHA1: | E957D1CAC0228AC75D3DF441CBF578D727D52FA4 |
| SHA256: | CA7CC9488E112AF8179A5E8FB1F1831C6754D0AC16E508A0F75B6304D015A7A2 |
| SSDEEP: | 98304:fOgTVCK7gn3makcOs/adrbuNSYJJ6GNtYW3DQ4YzMutg3M1O5KNll6gPN9ZgW2op:HRSxhii4r |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4412)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 4412)
Explorer used for Indirect Command Execution
- explorer.exe (PID: 6016)
Executes application which crashes
- ssvagent.exe (PID: 6536)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 4412)
Manual execution by a user
- explorer.exe (PID: 6016)
Checks supported languages
- ssvagent.exe (PID: 6536)
Reads security settings of Internet Explorer
- explorer.exe (PID: 2692)
- OpenWith.exe (PID: 6400)
Reads the computer name
- ssvagent.exe (PID: 6536)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 684)
- ssvagent.exe (PID: 6536)
- OpenWith.exe (PID: 6400)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4412)
Creates files or folders in the user directory
- WerFault.exe (PID: 1352)
Checks proxy server information
- WerFault.exe (PID: 1352)
- slui.exe (PID: 1192)
Reads the software policy settings
- WerFault.exe (PID: 1352)
- slui.exe (PID: 1192)
Application launched itself
- Acrobat.exe (PID: 3780)
- AcroCEF.exe (PID: 2140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (gen) (100) |
|---|
EXIF
ZIP
| FileVersion: | 7z v0.03 |
|---|---|
| ModifyDate: | 2025:06:30 13:49:31+00:00 |
| ArchivedFileName: | __MACOSX/__MACOSX/__MACOSX/__MACOSX/deploy.dll |
Total processes
159
Monitored processes
21
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 684 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=3592 --field-trial-handle=1616,i,16476954325420466849,15411458724651072537,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1192 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1352 | C:\WINDOWS\system32\WerFault.exe -u -p 6536 -s 1080 | C:\Windows\System32\WerFault.exe | ssvagent.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1352 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2628 --field-trial-handle=1616,i,16476954325420466849,15411458724651072537,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2140 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2432 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=disabled --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2140 --field-trial-handle=1616,i,16476954325420466849,15411458724651072537,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2692 | C:\WINDOWS\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3388 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 "C:\Users\admin\Desktop\武汉大学-赵浩宇-个人简历.pdf" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Version: 23.1.20093.0 Modules
| |||||||||||||||
Total events
27 905
Read events
27 760
Write events
140
Delete events
5
Modification events
| (PID) Process: | (4412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\123.7z | |||
| (PID) Process: | (4412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
5
Suspicious files
163
Text files
12
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1352 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_ssvagent.exe_abad3f87def37f8643e3de85ed4164a7da6cc_4fe05147_e47f17a7-48c0-47b5-9144-dc17d2909e0c\Report.wer | — | |
MD5:— | SHA256:— | |||
| 4412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4412.20641\__MACOSX\__MACOSX\__MACOSX\__MACOSX\vcruntime140_1.dll | executable | |
MD5:9410EE0771FF1C2007D9087A8C316A4B | SHA256:E4E85EEA1106D361923995E53A0B961A28D4FB58555F40945003F35E5BF2C273 | |||
| 4412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4412.20641\__MACOSX\__MACOSX\__MACOSX\__MACOSX\武汉大学-赵浩宇-个人简历.pdf | ||
MD5:25F3E3666AF896222D76A582143E7694 | SHA256:564BAA4D35CF9090D6711B645E2774BADA843D763E4B0283194D3955F903856B | |||
| 4412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4412.20641\__MACOSX\__MACOSX\__MACOSX\__MACOSX\ssvagent.exe | executable | |
MD5:3976020962F603903D7B32C10E8B8555 | SHA256:571BEFB396DCEB75CAB26821E4524036B257501E5B98975E1FC29D00E90FC3C6 | |||
| 4412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4412.20641\__MACOSX\__MACOSX\__MACOSX\__MACOSX\vcruntime140.dll | executable | |
MD5:699DD61122D91E80ABDFCC396CE0EC10 | SHA256:F843CD00D9AFF9A902DD7C98D6137639A10BD84904D81A085C28A3B29F8223C1 | |||
| 4412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4412.20641\CET6_赵浩宇.pdf | ||
MD5:DDE5989E8D1F4C18D98A7179DE310FE0 | SHA256:CDD5D3FA601B37685293985B634E9F4D864BDFD0FC271ACFD25E5D2943C5CC6D | |||
| 4412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4412.20641\武汉大学-赵浩宇-个人简历.lnk | lnk | |
MD5:B81938B4A08A215F0CBC29F064DD81BD | SHA256:D563B241CCDA81512122AB39E09CF4CE6088B6F20821F86CBA6B3F6D7A51785F | |||
| 4412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4412.20641\扫描件_成绩证明.pdf | ||
MD5:942E6CAD0D6372D127F57C1784252109 | SHA256:CB83F51940FC30DC7A91ACEE49A99AFF0F55F23151B243314C8B56EDE7108E2D | |||
| 1352 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERA133.tmp.xml | xml | |
MD5:E2F6DC76FCC61E8AC109AB89B706F1FC | SHA256:5C3E879002E3122A16D94EF14A127923AC8570D34EE8854B7842131D9E07EDBA | |||
| 1352 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | der | |
MD5:0F7B8F6A846AA9CA52FA562DDDCDB5ED | SHA256:AFF90E65A81289B80D1FCC5E71B3D88E5D1AAFE22CE358EB6E28A56D1845263D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
34
DNS requests
26
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.5:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2292 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1352 | WerFault.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1352 | WerFault.exe | GET | 200 | 23.216.77.5:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5556 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5556 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3780 | Acrobat.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3396 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.216.77.5:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2292 | svchost.exe | 20.190.160.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2292 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
cb3.qianbaba.top |
| unknown |
watson.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |