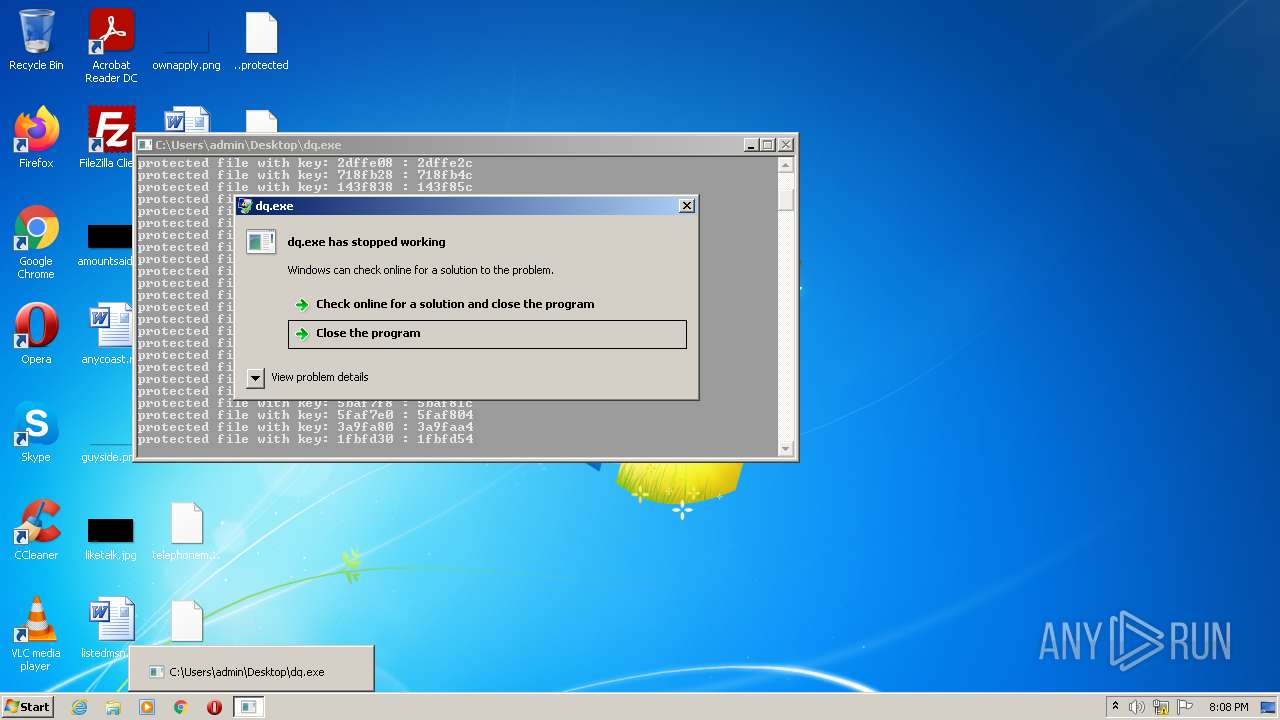
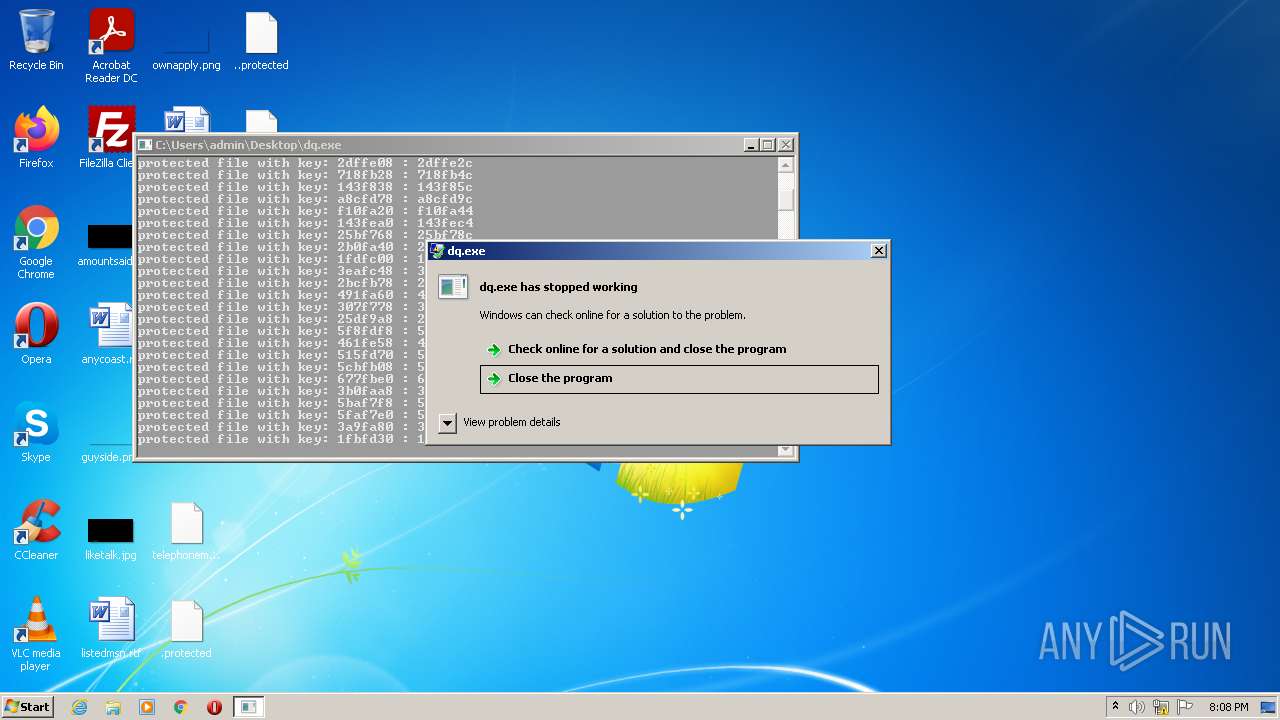
| File name: | dq.exe |
| Full analysis: | https://app.any.run/tasks/22501ffb-33eb-4a60-9a10-f6271234f635 |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 19:08:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 6FB99953C19C6ECE7FA10C134D60DF08 |
| SHA1: | 6BED7C4E779AA9D05D3FCF14B83F9A79D88C6407 |
| SHA256: | CA7967AB5082CB6D54E4AD03F6E2C7813A8634D296C2B01B3A261A1A98ACEBE5 |
| SSDEEP: | 24576:9+p+BIIpLwHHDhFfPTUV0qd9Csu6G2hMKP/NJAfV3:A+BDG8KuFG2KKP/N+fV3 |
MALICIOUS
Modifies files in Chrome extension folder
- dq.exe (PID: 3128)
SUSPICIOUS
Checks supported languages
- dq.exe (PID: 3128)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| Subsystem: | Windows command line |
|---|---|
| SubsystemVersion: | 6 |
| ImageVersion: | - |
| OSVersion: | 6 |
| EntryPoint: | 0x966ca |
| UninitializedDataSize: | - |
| InitializedDataSize: | 380416 |
| CodeSize: | 723968 |
| LinkerVersion: | 14.29 |
| PEType: | PE32 |
| TimeStamp: | 2022:08:12 21:08:18+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 12-Aug-2022 19:08:18 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000108 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 12-Aug-2022 19:08:18 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000B0B34 | 0x000B0C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.6154 |
.rdata | 0x000B2000 | 0x0004AD74 | 0x0004AE00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.20402 |
.data | 0x000FD000 | 0x00007E34 | 0x00005200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.88548 |
.rsrc | 0x00105000 | 0x000001E0 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.7123 |
.reloc | 0x00106000 | 0x00009C60 | 0x00009E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.58979 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.91161 | 381 | UNKNOWN | English - United States | RT_MANIFEST |
Imports
ADVAPI32.dll |
CRYPT32.dll |
KERNEL32.dll |
USER32.dll |
WS2_32.dll |
Total processes
37
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3128 | "C:\Users\admin\Desktop\dq.exe" | C:\Users\admin\Desktop\dq.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
133
Read events
133
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
5
Text files
36
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3128 | dq.exe | C:\Users\admin\AppData\Local\Adobe\A0A2C719-B8B1-4DC7-B33B-C50E709F20B0\status_icon_caution_100.png.protected | text | |
MD5:— | SHA256:— | |||
| 3128 | dq.exe | C:\Users\admin\Desktop\telephonemartin.png.protected | text | |
MD5:— | SHA256:— | |||
| 3128 | dq.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Reader\Files\TESTING.protected | text | |
MD5:— | SHA256:— | |||
| 3128 | dq.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CertificateTransparency\1256\_platform_specific\all\sths\07b75c1be57d68fff1b0c61d2315c7bae6577c5794b76aeebc613a1a69d3a21c.sth.protected | text | |
MD5:— | SHA256:— | |||
| 3128 | dq.exe | C:\Users\admin\AppData\Local\FileZilla\default_synchronize20x20.png.protected | text | |
MD5:— | SHA256:— | |||
| 3128 | dq.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CertificateTransparency\1256\_metadata\verified_contents.json.protected | text | |
MD5:— | SHA256:— | |||
| 3128 | dq.exe | C:\Users\admin\Favorites\Microsoft Websites\Microsoft Store.url.protected | text | |
MD5:— | SHA256:— | |||
| 3128 | dq.exe | C:\Users\admin\Favorites\Windows Live\Windows Live Spaces.url.protected | text | |
MD5:— | SHA256:— | |||
| 3128 | dq.exe | C:\Users\admin\AppData\Local\Adobe\A0A2C719-B8B1-4DC7-B33B-C50E709F20B0\yellow_button_short_200.png.protected | text | |
MD5:— | SHA256:— | |||
| 3128 | dq.exe | C:\Users\admin\AppData\Local\Adobe\A0A2C719-B8B1-4DC7-B33B-C50E709F20B0\warning_icon_200.png.protected | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report