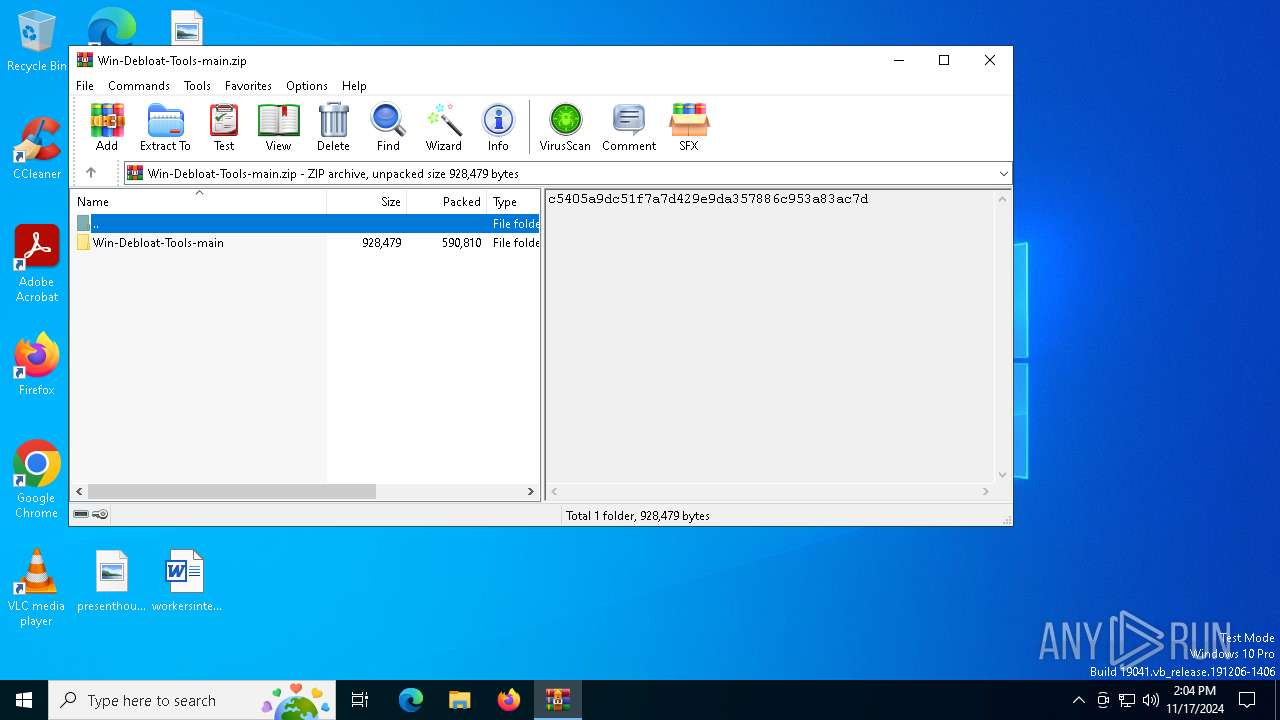
| File name: | Win-Debloat-Tools-main.zip |
| Full analysis: | https://app.any.run/tasks/607120c9-354e-4bfd-bb4c-5e0e606dcb33 |
| Verdict: | Malicious activity |
| Analysis date: | November 17, 2024, 14:03:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | A9D6B5A0B0C33B50A12A774AD7A591DE |
| SHA1: | ED5AE1F78E303591BF91E86588C51C4C05D0EC13 |
| SHA256: | CA5F16FAE14AF774DA7DDB95593DA6602C929E53D2A7687E26F205AD26B58F9A |
| SSDEEP: | 24576:U0JIvfAeiHVPvGqTZzvkm5Q9r3CKz18hGaooh:U0JIvfAei1PvGqTZzvkm5Q9r3CKz18hf |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2428)
SUSPICIOUS
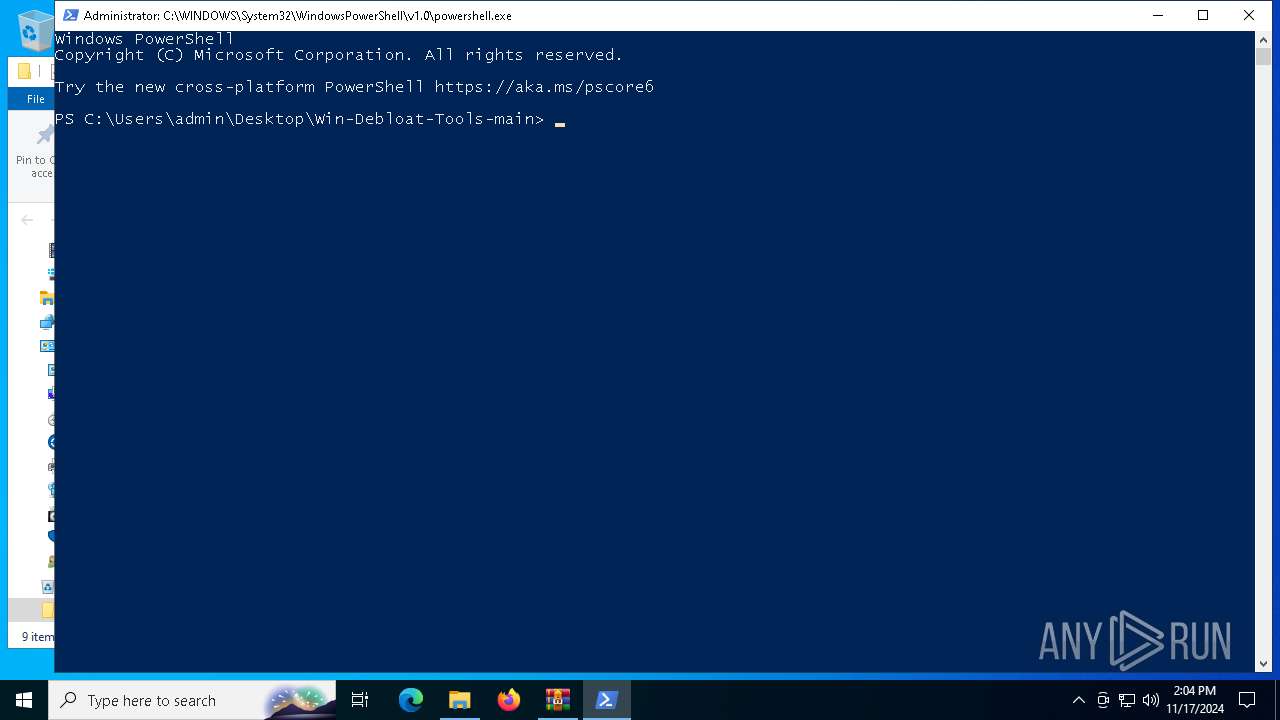
Executing commands from ".cmd" file
- wscript.exe (PID: 6024)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6024)
- powershell.exe (PID: 6168)
The process executes VB scripts
- cmd.exe (PID: 4956)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6024)
Checks a user's role membership (POWERSHELL)
- powershell.exe (PID: 6168)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6752)
CSC.EXE is used to compile C# code
- csc.exe (PID: 4432)
Executable content was dropped or overwritten
- csc.exe (PID: 4432)
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 6168)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 2428)
Manual execution by a user
- cmd.exe (PID: 4956)
Checks current location (POWERSHELL)
- powershell.exe (PID: 6168)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 6168)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6168)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6168)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:09:09 06:30:52 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Win-Debloat-Tools-main/ |
Total processes
152
Monitored processes
18
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1500 | "C:\WINDOWS\system32\cmd.exe" /c color A | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2428 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Win-Debloat-Tools-main.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2444 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3620 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4432 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\nsioike0\nsioike0.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 4448 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4956 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Win-Debloat-Tools-main\OpenTerminalHere.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5912 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6024 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\OEgetPriv_OpenTerminalHere.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6168 | PowerShell | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 018
Read events
14 012
Write events
6
Delete events
0
Modification events
| (PID) Process: | (2428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Win-Debloat-Tools-main.zip | |||
| (PID) Process: | (2428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
2
Text files
101
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2428.5748\Win-Debloat-Tools-main\src\assets\peepo-leaving.gif | image | |
MD5:E9323C28671AE3994701BC1A2A1C9D4C | SHA256:39E41556222057E556FA0F61A8F7A75414CD3B531BDE53FD9630F3002CD7FC1B | |||
| 2428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2428.5748\Win-Debloat-Tools-main\.github\FUNDING.yml | text | |
MD5:8036B96D969A5B0B1FD7FF58225DBEED | SHA256:E3BF49781EE39ADD4FE0DC5AC4053B71F96F94F6F3EAB3CF63A2B820C7B2F8CD | |||
| 2428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2428.5748\Win-Debloat-Tools-main\.github\ISSUE_TEMPLATE\feature_request.yaml | text | |
MD5:3FD3566853A9CC3CB464F06205DBA403 | SHA256:346F9627844FF7244430BCEFE92EC60AC10C275F1F2E66CA432F41A57C80436C | |||
| 2428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2428.5748\Win-Debloat-Tools-main\.github\dependabot.yml | text | |
MD5:8C519E8DE6FAE4B9CF7416F3F7106883 | SHA256:4F6E0846E9FA37CD88EE20882EA668C40786E0F9D572854C44597DBF69E015A6 | |||
| 2428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2428.5748\Win-Debloat-Tools-main\.github\ISSUE_TEMPLATE\config.yml | text | |
MD5:90D7947AE73B441DCAD76B1DB220B316 | SHA256:05905C8F244D51298BBD1778C286C8A6C9F7ADF0D0E5A5F72F764D71EC82CC64 | |||
| 2428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2428.5748\Win-Debloat-Tools-main\OpenTerminalHere.cmd | text | |
MD5:9B1E72E70C36EA5FB9ABECAD23658404 | SHA256:0B51ABB96A5DEFC59A50EF720EB8E8B7146EADA59E65E95CFF32B18B66F71C06 | |||
| 2428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2428.5748\Win-Debloat-Tools-main\.gitignore | text | |
MD5:403A179DA0D83A2D8BAC5E94CE014C50 | SHA256:3E0AB0FEC709346514D8B36722B4C40FBD0B907483E5E413CCC9F904A02CBD18 | |||
| 2428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2428.5748\Win-Debloat-Tools-main\CONTRIBUTING.md | text | |
MD5:7920D5EE42F6BA40B1ACBD90B98B58C2 | SHA256:246933910CB405FE7A16E78B12FE7CB00770033BB0F607357D827886A2EFA5AC | |||
| 2428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2428.5748\Win-Debloat-Tools-main\LICENSE.txt | text | |
MD5:E4026026262F7A3A1D42211A4395BEC3 | SHA256:3D553C114304685492BC754EAE936CC87E423DE7BCC7AB9B04D2E6DAE2F952D4 | |||
| 2428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2428.5748\Win-Debloat-Tools-main\ROADMAP.md | text | |
MD5:4E716FB97725A2DD53D7566B807F8F96 | SHA256:154D28120E2E509EC13D5F593A2CB7BE0023D58F27D8C3BEA6FCBC2AA3BD838F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
44
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
632 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.18.121.216:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5952 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6248 | SIHClient.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6248 | SIHClient.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2444 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 2.16.106.196:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
632 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
632 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
780 | svchost.exe | 23.218.210.69:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |