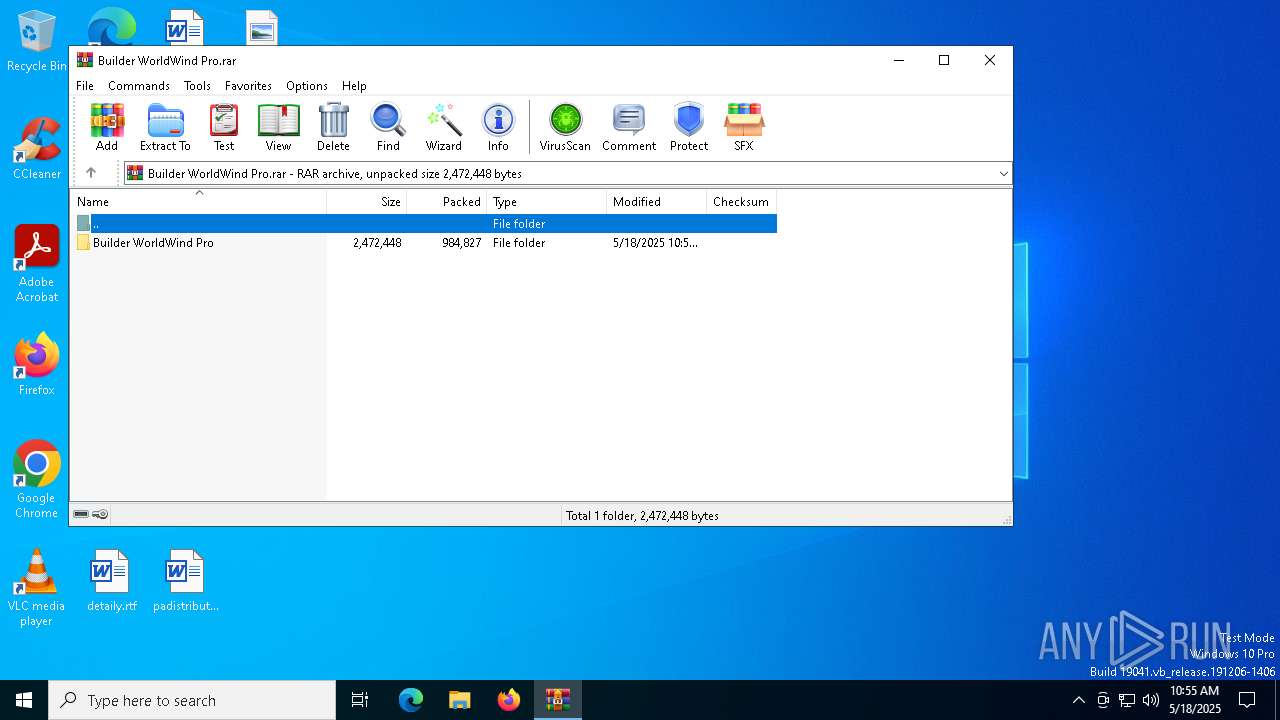
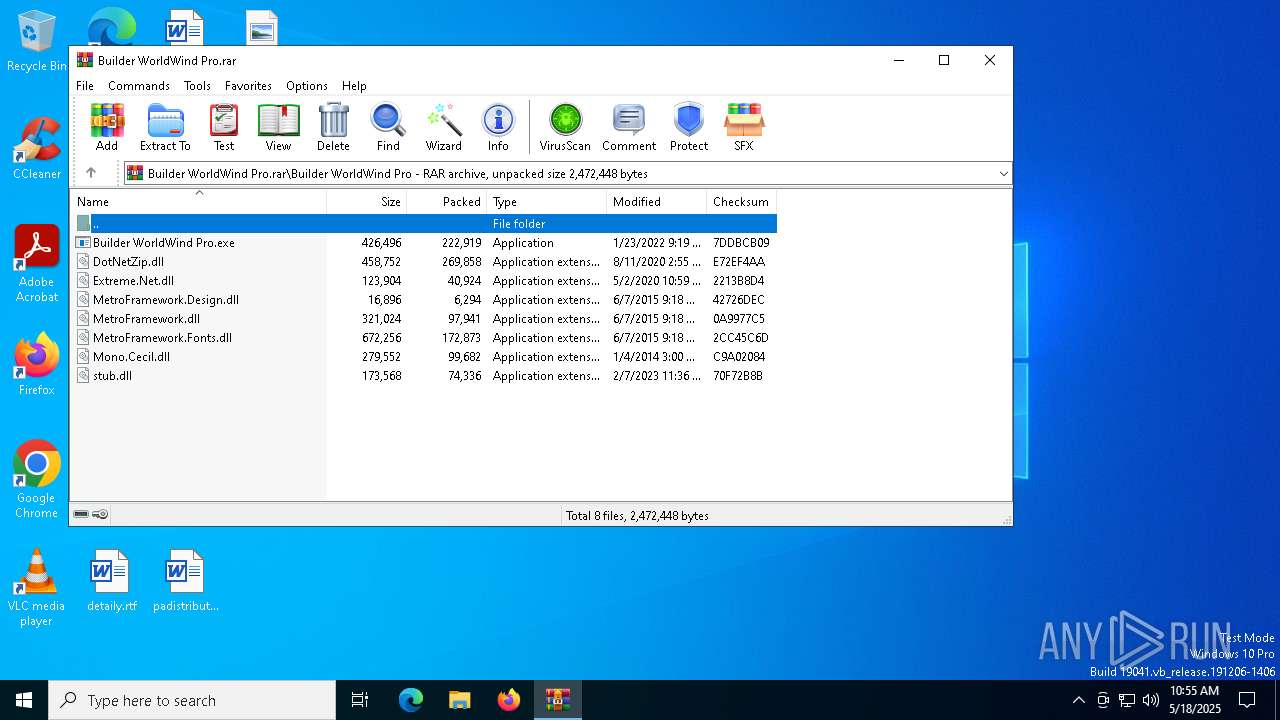
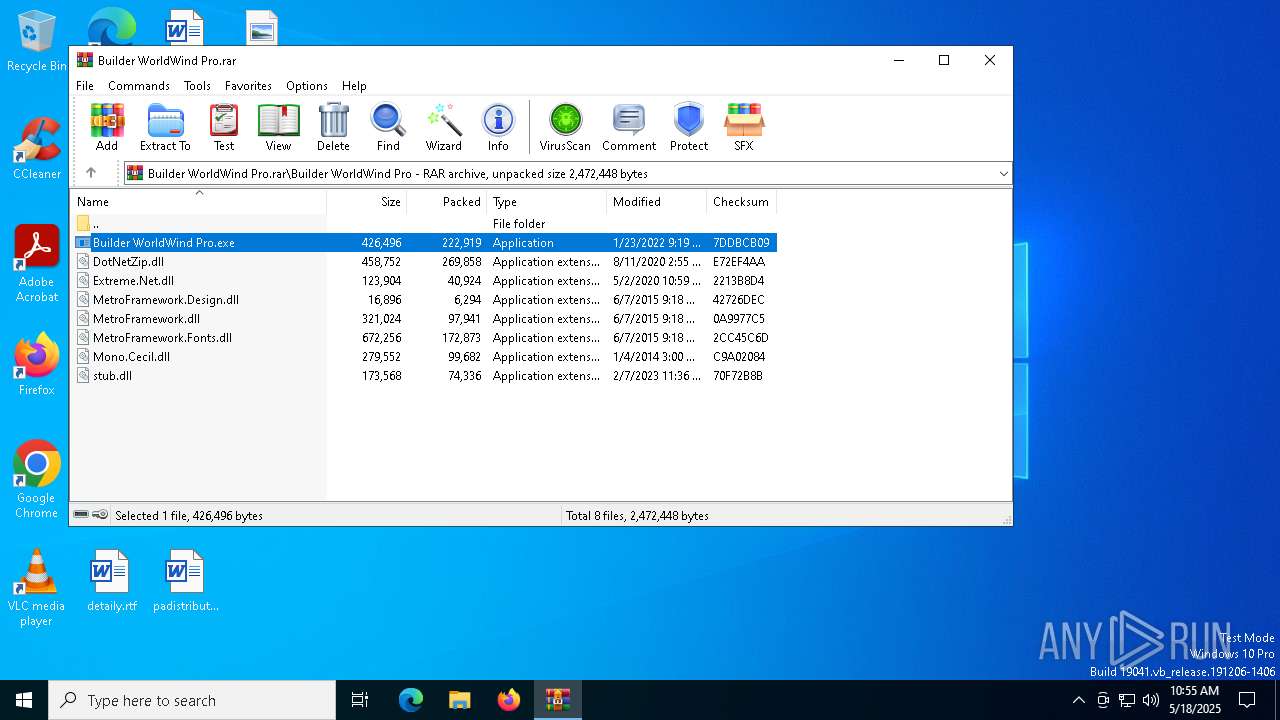
| File name: | Builder WorldWind Pro.rar |
| Full analysis: | https://app.any.run/tasks/35765b3d-4540-4a47-80eb-8e83dd52a373 |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 10:55:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 88F6A381E725DFA5EBAC377BD3DE1AA2 |
| SHA1: | 07C2379A49DCBB55582C42848139EF0ECE7E8A52 |
| SHA256: | CA53F7C8CB848CB8CA0055D76E0AAFF59A9AE515BE13C4D35A6E2D44DBFDDD26 |
| SSDEEP: | 49152:1DOnweDFp6hmF/AaYguoEW4iZOzX0VObkGnFbLB6PiDOPWhIu1UXg2SrOm2G3Fl5:gwQFpq+IaTEW4iuX0VOPnFXB00aWhLay |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6964)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6964)
- Builder WorldWind Pro.exe (PID: 3888)
Executable content was dropped or overwritten
- Builder WorldWind Pro.exe (PID: 3888)
Reads Internet Explorer settings
- Builder WorldWind Pro.exe (PID: 3888)
Possible usage of Discord/Telegram API has been detected (YARA)
- Builder WorldWind Pro.exe (PID: 3888)
INFO
Reads the computer name
- Builder WorldWind Pro.exe (PID: 3888)
Checks supported languages
- Builder WorldWind Pro.exe (PID: 3888)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6964)
Reads the machine GUID from the registry
- Builder WorldWind Pro.exe (PID: 3888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(3888) Builder WorldWind Pro.exe
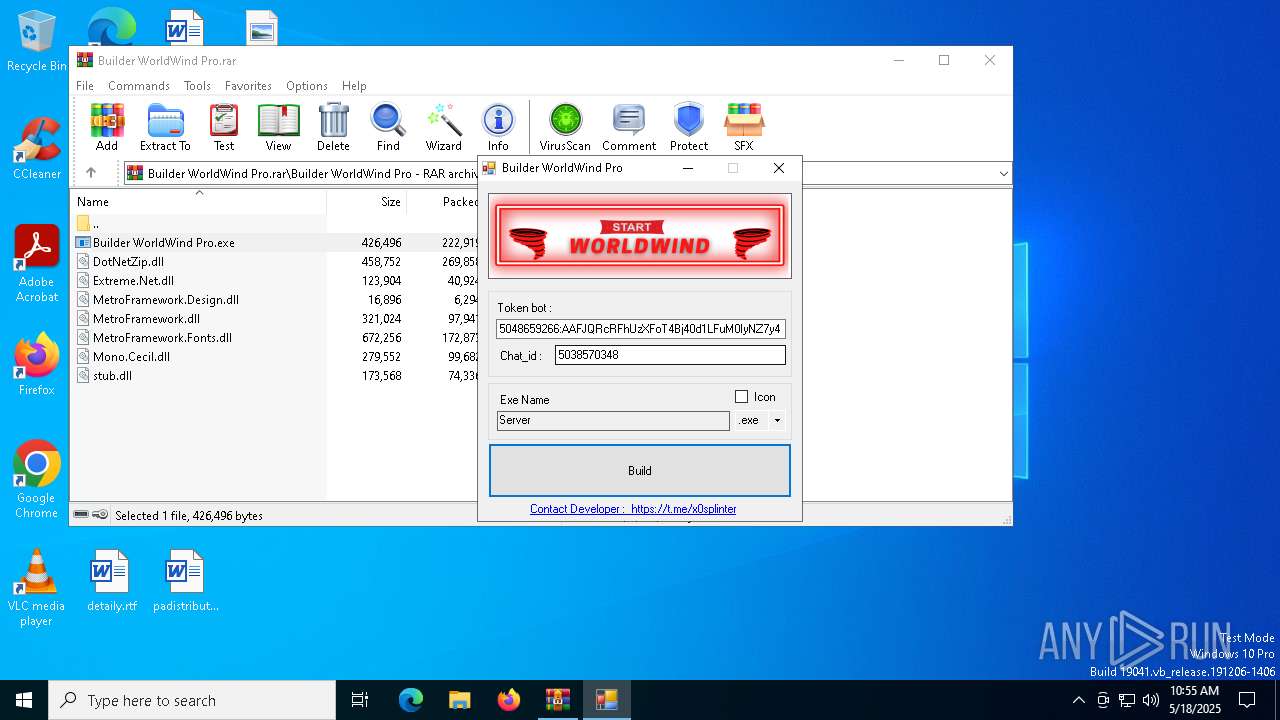
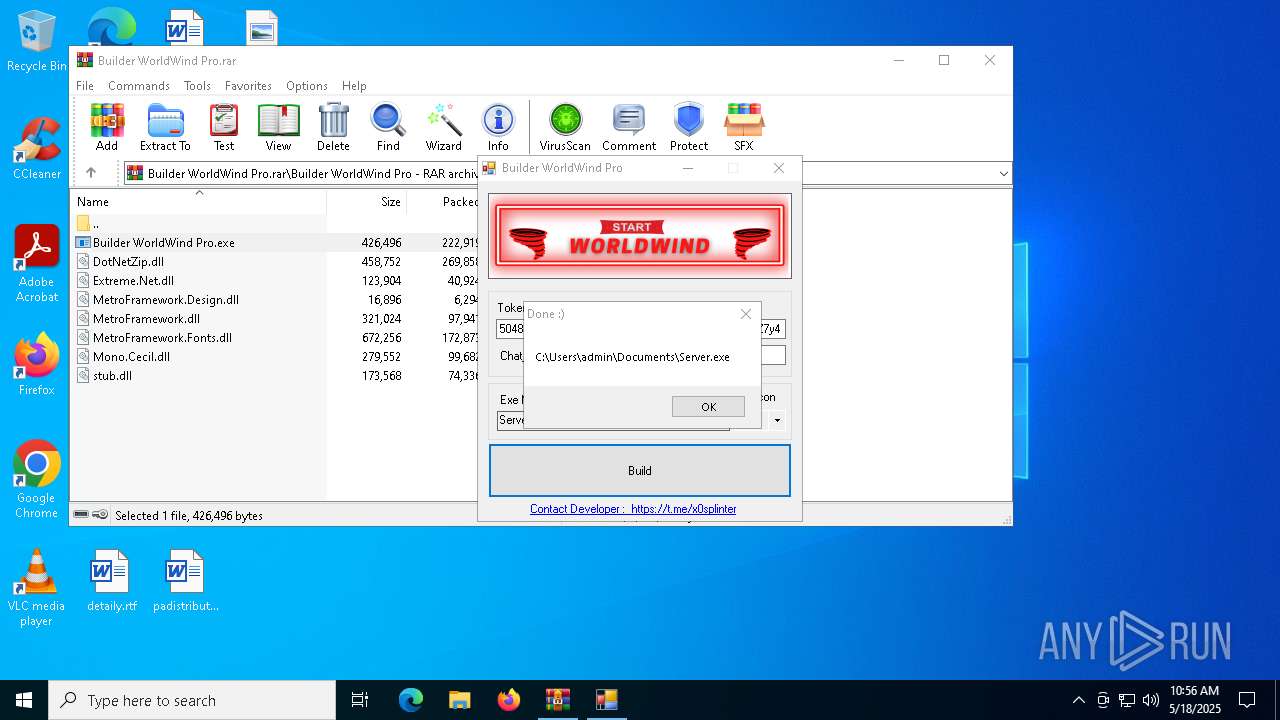
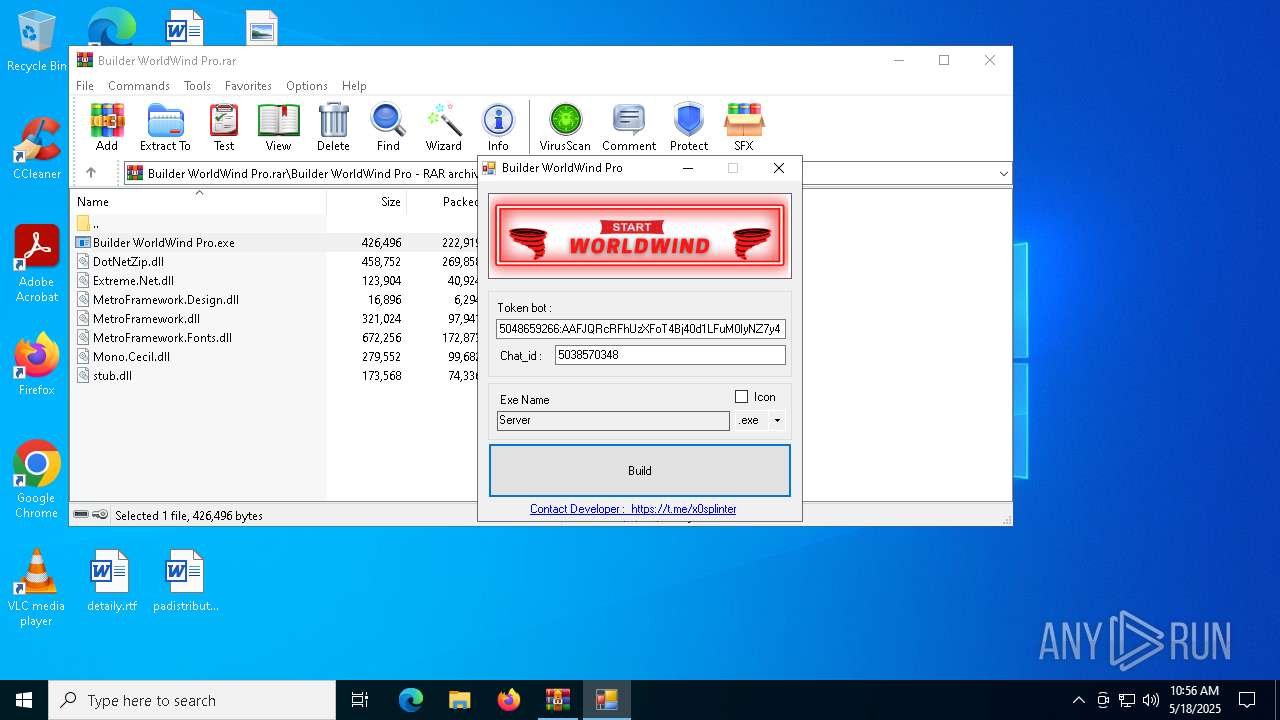
Telegram-Tokens (1)5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4
Telegram-Info-Links
5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4
Get info about bothttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/getMe
Get incoming updateshttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/getUpdates
Get webhookhttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/deleteWebhook?drop_pending_updates=true
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
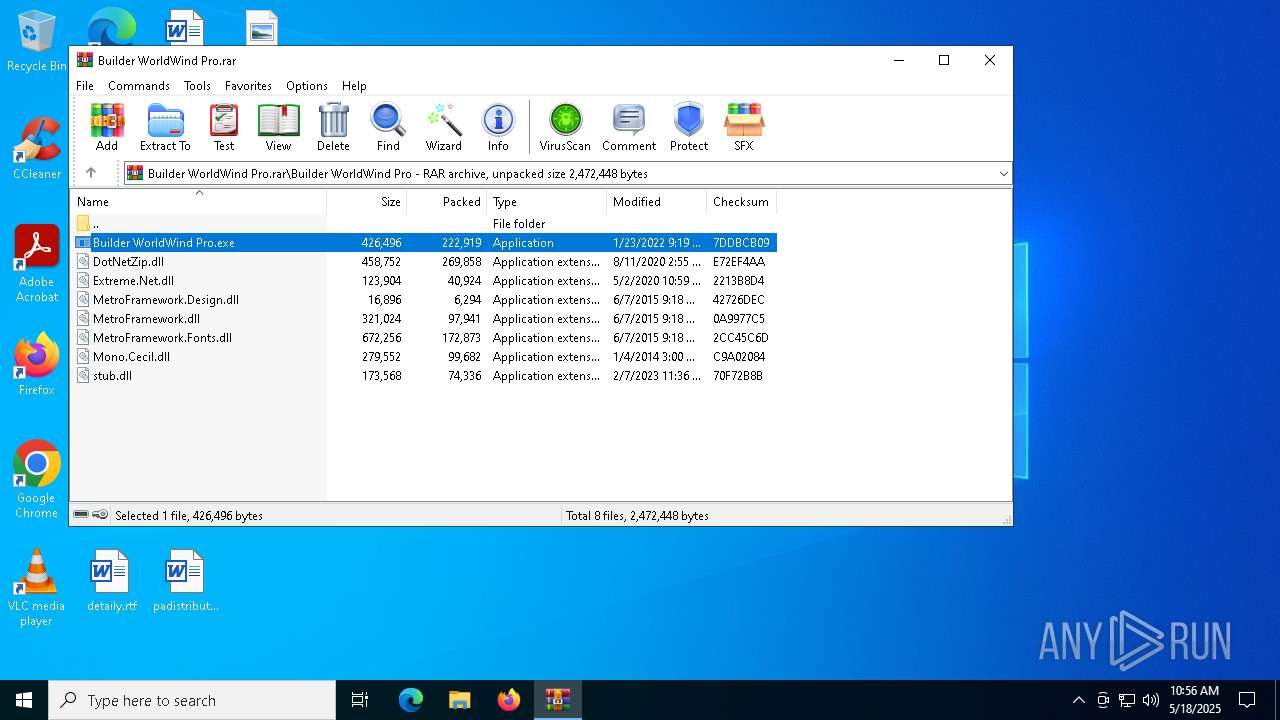
| CompressedSize: | 222919 |
| UncompressedSize: | 426496 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Builder WorldWind Pro/Builder WorldWind Pro.exe |
Total processes
130
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3888 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6964.6236\Builder WorldWind Pro\Builder WorldWind Pro.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6964.6236\Builder WorldWind Pro\Builder WorldWind Pro.exe | WinRAR.exe | ||||||||||||
User: admin Company: Builder_WorldWind_Pro Integrity Level: MEDIUM Description: Builder_WorldWind_Pro Exit code: 0 Version: 1.9.9.9 Modules
ims-api(PID) Process(3888) Builder WorldWind Pro.exe Telegram-Tokens (1)5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4 Telegram-Info-Links 5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4 Get info about bothttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/getMe Get incoming updateshttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/getUpdates Get webhookhttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/getWebhookInfo Delete webhookhttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/deleteWebhook Drop incoming updateshttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/deleteWebhook?drop_pending_updates=true | |||||||||||||||
| 4868 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6032 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6964 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Builder WorldWind Pro.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
5 744
Read events
5 696
Write events
47
Delete events
1
Modification events
| (PID) Process: | (6964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Builder WorldWind Pro.rar | |||
| (PID) Process: | (6964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3888) Builder WorldWind Pro.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3888) Builder WorldWind Pro.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000000E00000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
Executable files
9
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6964 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6964.6236\Builder WorldWind Pro\Extreme.Net.dll | executable | |
MD5:F79F0E3A0361CAC000E2D3553753CD68 | SHA256:8A6518AB7419FBEC3AC9875BAA3AFB410AD1398C7AA622A09CD9084EC6CADFCD | |||
| 6964 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6964.6236\Builder WorldWind Pro\MetroFramework.Design.dll | executable | |
MD5:C853E9E8C720249198FF376F42328EF9 | SHA256:28089707733C92C7FADE97E7B6FAB4007E7B8BFD6DC7A8526A3EA597F1A30845 | |||
| 6964 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6964.6236\Builder WorldWind Pro\Mono.Cecil.dll | executable | |
MD5:80EA4BFE7944E2F384D97488C83D9D25 | SHA256:1A1565804348C2E621E0A509CEDAA516EEB7E9FADFBEEFE58E1E9CF8EC16B915 | |||
| 6964 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6964.6236\Builder WorldWind Pro\MetroFramework.dll | executable | |
MD5:B20F1B5E3D4E3DF2D826E9870637CD06 | SHA256:9E58F13DEB328455F216F165588B5F5111ECD12042D7DD196686DFB0F0FC68EB | |||
| 6964 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6964.6236\Builder WorldWind Pro\stub.dll | executable | |
MD5:FA88F24EAB7DE6A32660B75BB72352CB | SHA256:EC3AA251B8FC99C510F9F6F7D59BFE57F1B79D925D3E5FAA0E2E08610597FE09 | |||
| 6964 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6964.6236\Builder WorldWind Pro\MetroFramework.Fonts.dll | executable | |
MD5:B8C8A532438C4B421081EFB258355469 | SHA256:15A605129CAC3663BA1DDB98F5798334FBA5E7954EE36A69727299B4E366C2EB | |||
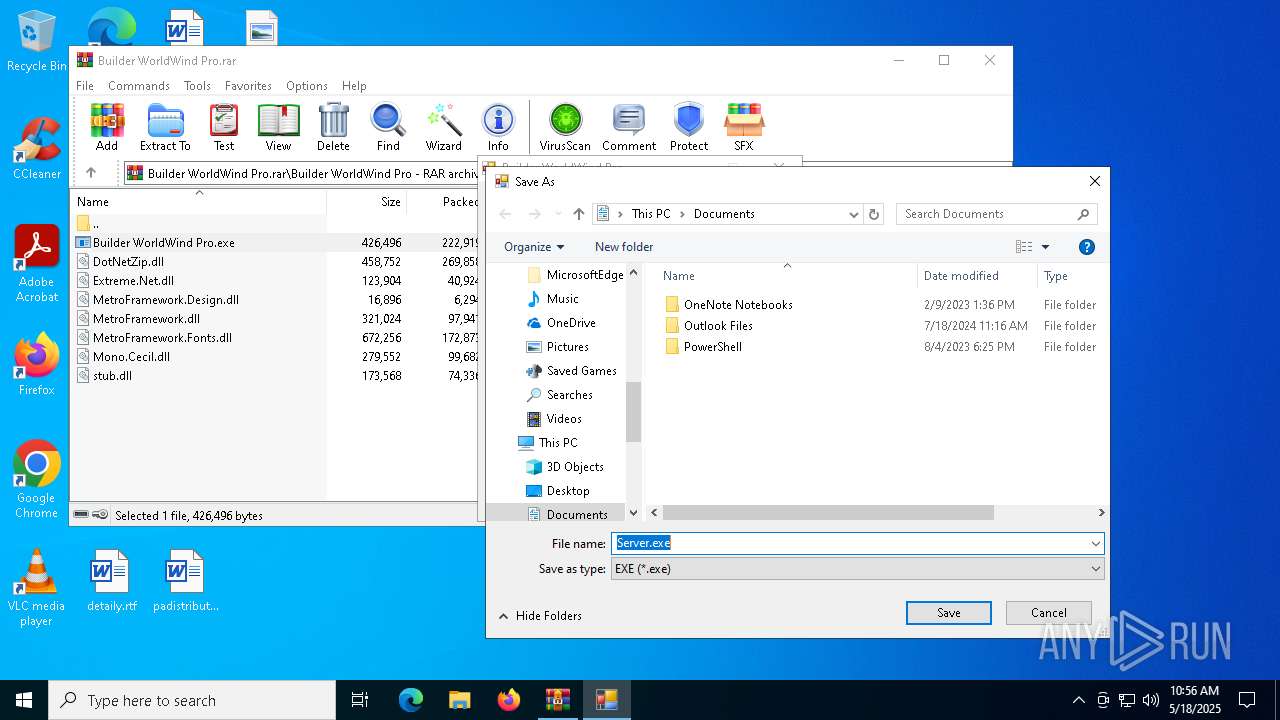
| 3888 | Builder WorldWind Pro.exe | C:\Users\admin\Documents\Server.exe | executable | |
MD5:0C5D93A7C74CF8CBECE405362EC5EAEA | SHA256:A658FD9E1CF3BAB84BE17119E35792BF8075E32791D01D9E0FDFC50CE05212A4 | |||
| 6964 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6964.6236\Builder WorldWind Pro\DotNetZip.dll | executable | |
MD5:6D1C62EC1C2EF722F49B2D8DD4A4DF16 | SHA256:00DA1597D92235D3F84DA979E2FA5DBF049BAFB52C33BD6FC8EE7B29570C124C | |||
| 6964 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6964.6236\Builder WorldWind Pro\Builder WorldWind Pro.exe | executable | |
MD5:5E503D24CA178DB83E5D931990C1BAA6 | SHA256:E0E74379954ACB4D9847C0CFB63E8A4028217D859C74AD97B40504627277D16B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
19
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2392 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2392 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.10:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.10:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |