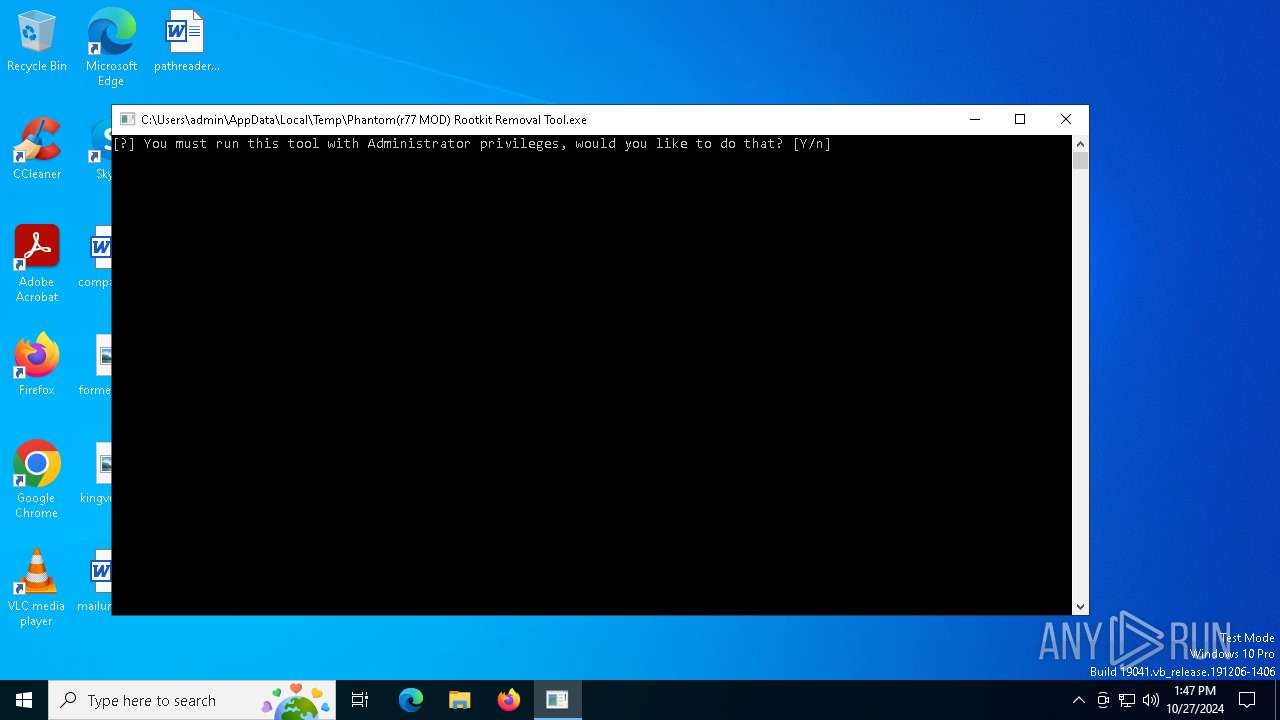
| File name: | Phantom(r77 MOD) Rootkit Removal Tool.exe |
| Full analysis: | https://app.any.run/tasks/1d24ed77-f3b6-4ea2-be99-7555e3daa710 |
| Verdict: | Malicious activity |
| Analysis date: | October 27, 2024, 13:46:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 8F982405A77CBE5C064A3E8C6D605387 |
| SHA1: | 0DB945630DE6D5EEFB40B8FD4EC2E82137B9D462 |
| SHA256: | CA4FBF0E7FD2F275577D19F209C2A10C9AA4FC8AD0E38D2E34293F1A36C74A67 |
| SSDEEP: | 6144:OaDgag+BglZwA6bSpNeamJw0ZNNnPoaRvqi7Pb1:TDgagnL6bSpgar0BPRr |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- Phantom(r77 MOD) Rootkit Removal Tool.exe (PID: 6836)
- Phantom(r77 MOD) Rootkit Removal Tool.exe (PID: 6676)
Application launched itself
- Phantom(r77 MOD) Rootkit Removal Tool.exe (PID: 6836)
Reads the date of Windows installation
- Phantom(r77 MOD) Rootkit Removal Tool.exe (PID: 6836)
- Phantom(r77 MOD) Rootkit Removal Tool.exe (PID: 6676)
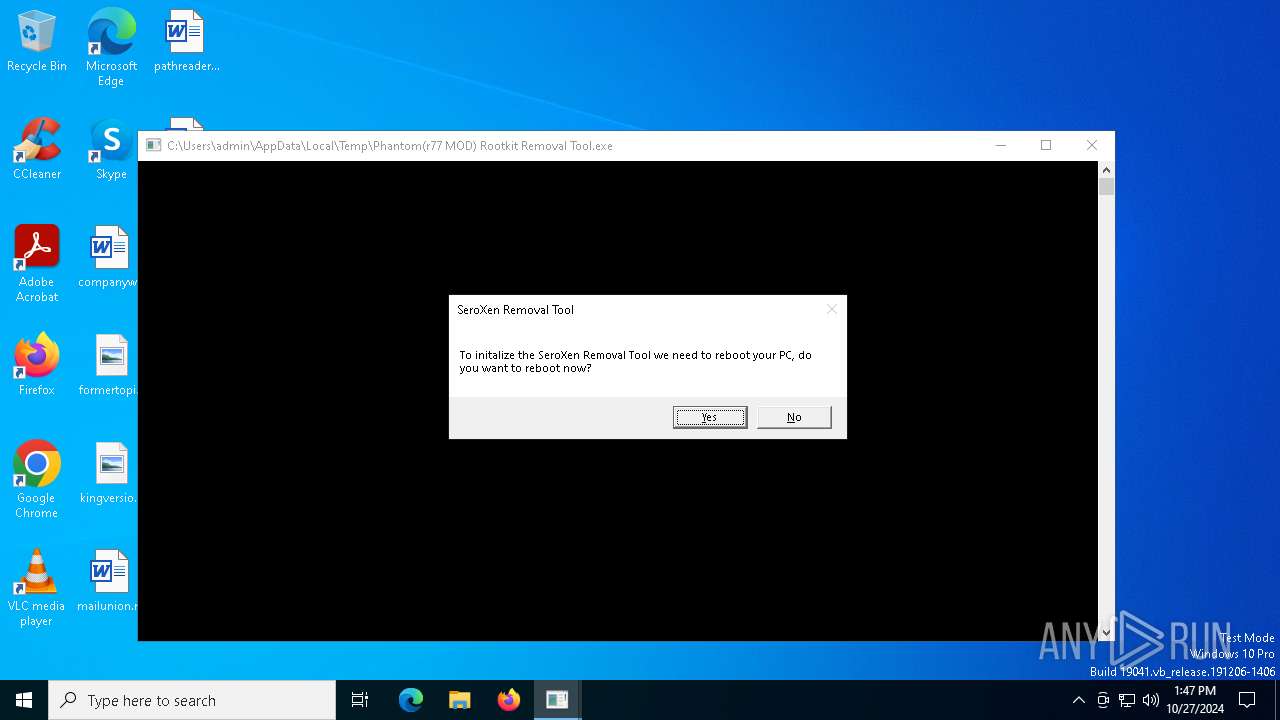
The system shut down or reboot
- Phantom(r77 MOD) Rootkit Removal Tool.exe (PID: 6676)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 3068)
- Phantom(r77 MOD) Rootkit Removal Tool.exe (PID: 2180)
INFO
Reads the computer name
- Phantom(r77 MOD) Rootkit Removal Tool.exe (PID: 6836)
- Phantom(r77 MOD) Rootkit Removal Tool.exe (PID: 6676)
Checks supported languages
- Phantom(r77 MOD) Rootkit Removal Tool.exe (PID: 6836)
- Phantom(r77 MOD) Rootkit Removal Tool.exe (PID: 6676)
The process uses the downloaded file
- Phantom(r77 MOD) Rootkit Removal Tool.exe (PID: 6836)
- Phantom(r77 MOD) Rootkit Removal Tool.exe (PID: 6676)
Reads the machine GUID from the registry
- Phantom(r77 MOD) Rootkit Removal Tool.exe (PID: 6836)
- Phantom(r77 MOD) Rootkit Removal Tool.exe (PID: 6676)
Process checks computer location settings
- Phantom(r77 MOD) Rootkit Removal Tool.exe (PID: 6836)
- Phantom(r77 MOD) Rootkit Removal Tool.exe (PID: 6676)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2079:12:08 16:04:49+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 219648 |
| InitializedDataSize: | 2560 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3786e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | SeroXen Removal Tool |
| FileVersion: | 1.0.0.0 |
| InternalName: | SeroXen_Removal_Tool.exe |
| LegalCopyright: | Copyright © 2024 |
| LegalTrademarks: | - |
| OriginalFileName: | SeroXen_Removal_Tool.exe |
| ProductName: | SeroXen Removal Tool |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
280
Monitored processes
9
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 700 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Phantom(r77 MOD) Rootkit Removal Tool.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2180 | "C:\Users\admin\AppData\Local\Temp\Phantom(r77 MOD) Rootkit Removal Tool.exe" --force | C:\Users\admin\AppData\Local\Temp\Phantom(r77 MOD) Rootkit Removal Tool.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: HIGH Description: SeroXen Removal Tool Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3020 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | shutdown.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3068 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3740 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Phantom(r77 MOD) Rootkit Removal Tool.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4472 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Phantom(r77 MOD) Rootkit Removal Tool.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6308 | "C:\Windows\System32\shutdown.exe" /r /f /t 0 | C:\Windows\System32\shutdown.exe | — | Phantom(r77 MOD) Rootkit Removal Tool.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6676 | "C:\Users\admin\AppData\Local\Temp\Phantom(r77 MOD) Rootkit Removal Tool.exe" | C:\Users\admin\AppData\Local\Temp\Phantom(r77 MOD) Rootkit Removal Tool.exe | Phantom(r77 MOD) Rootkit Removal Tool.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: SeroXen Removal Tool Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6836 | "C:\Users\admin\AppData\Local\Temp\Phantom(r77 MOD) Rootkit Removal Tool.exe" | C:\Users\admin\AppData\Local\Temp\Phantom(r77 MOD) Rootkit Removal Tool.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: SeroXen Removal Tool Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 306
Read events
1 306
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
28
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3068 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.037.etl | etl | |
MD5:FA358BFEE9B4E1FFB7394D13CBBC4898 | SHA256:6FF97BBF8A56286A4C71623829514CC14B7F8CBBCF09748D939F733968478A22 | |||
| 3068 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.027.etl | etl | |
MD5:A23907B6FDD47DCABFDFD7CF2FCD7671 | SHA256:0C9C33FE9E984A2E5A70EBA51F36B9929A86199E424AF2F8080E1267B87DC970 | |||
| 3068 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.033.etl | etl | |
MD5:2F36C598EBFF5B5CDD898C9691D6BCCB | SHA256:8900C5931ED8E0D1B68082B45CF2F4E8C1025D36825508E0804C916D781B9F50 | |||
| 3068 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.034.etl | etl | |
MD5:079890A8EC8D5CB6523FCEC2209780AA | SHA256:0E12D2D76DD738CE196BED522E35F75E2CC91294F78CDDCBE8CE7787AAA70049 | |||
| 3068 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.026.etl | etl | |
MD5:FED961067F664B5381B65A534B7AB728 | SHA256:652F31A8284AE812D1D9D24192BC800976BF74C240591C6AC443A28C4709FB7C | |||
| 3068 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.031.etl | etl | |
MD5:44A0E917AD0C126931B1BCD959285A9A | SHA256:DDFBE47E7DFD6D8B7517F2F6FF9808ECF3C0A25F588A9F96D04F4E2B4A578573 | |||
| 3068 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.028.etl | etl | |
MD5:5EA68411BF8E9EAF4621BAF73F61449E | SHA256:9D4CA5A1D871F819C139A498BB910A63576C2FE6367853544F8D172D8B6EBFF7 | |||
| 3068 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.025.etl | etl | |
MD5:A7A21FBC9D00F33F186B34A50E170C13 | SHA256:64CAC91E46D4FC832958232A658431CBF9D8D9F265653ACA2BEB32428D4688EC | |||
| 3068 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.024.etl | etl | |
MD5:89BD161BF7B46C9078937CF832786737 | SHA256:2B83DF5532E9F54ED301C8F82E2CDD489799C8D5222A2D44C97DCB151A96FAA9 | |||
| 3068 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.035.etl | etl | |
MD5:673727AF7C6805E869C9F8BE1E468F4A | SHA256:6B16B7DE97F397BCEC36EB3F18C7B64CD3DB6D2974DDF319A251CE27B80D837B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
87
DNS requests
32
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
624 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
812 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6500 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6500 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5968 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.194:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4360 | SearchApp.exe | 92.123.104.54:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
624 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |