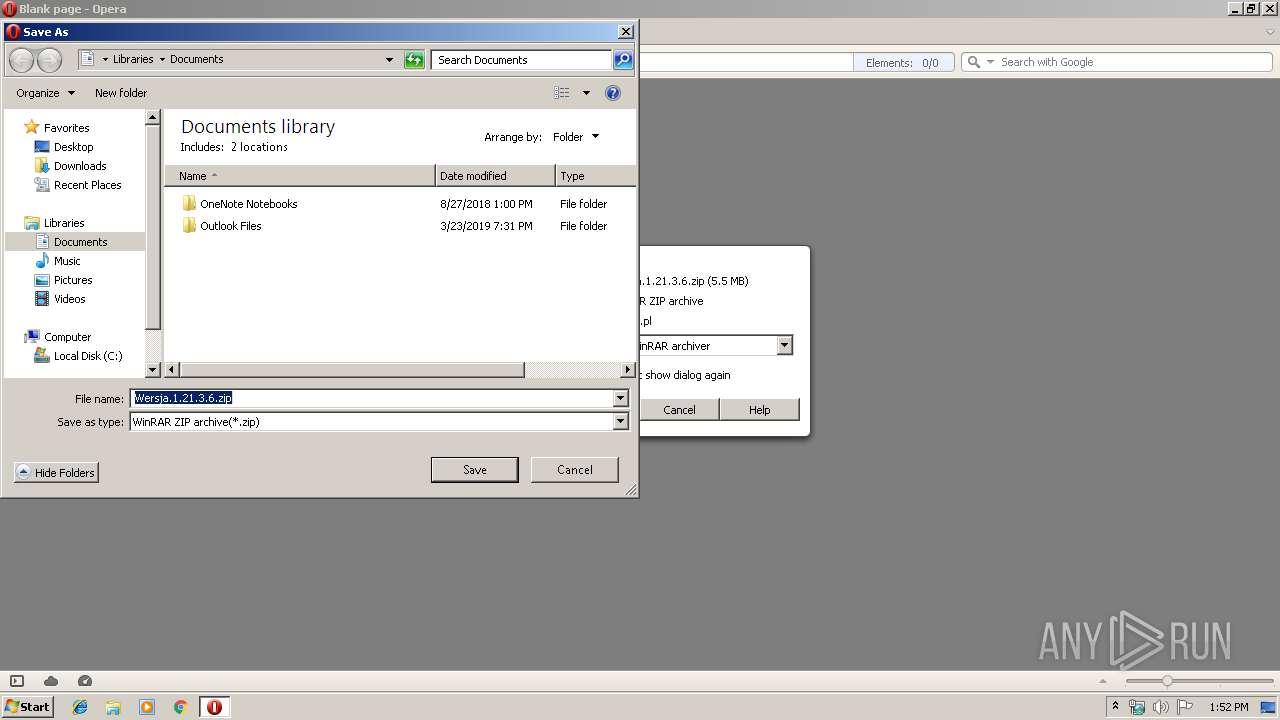
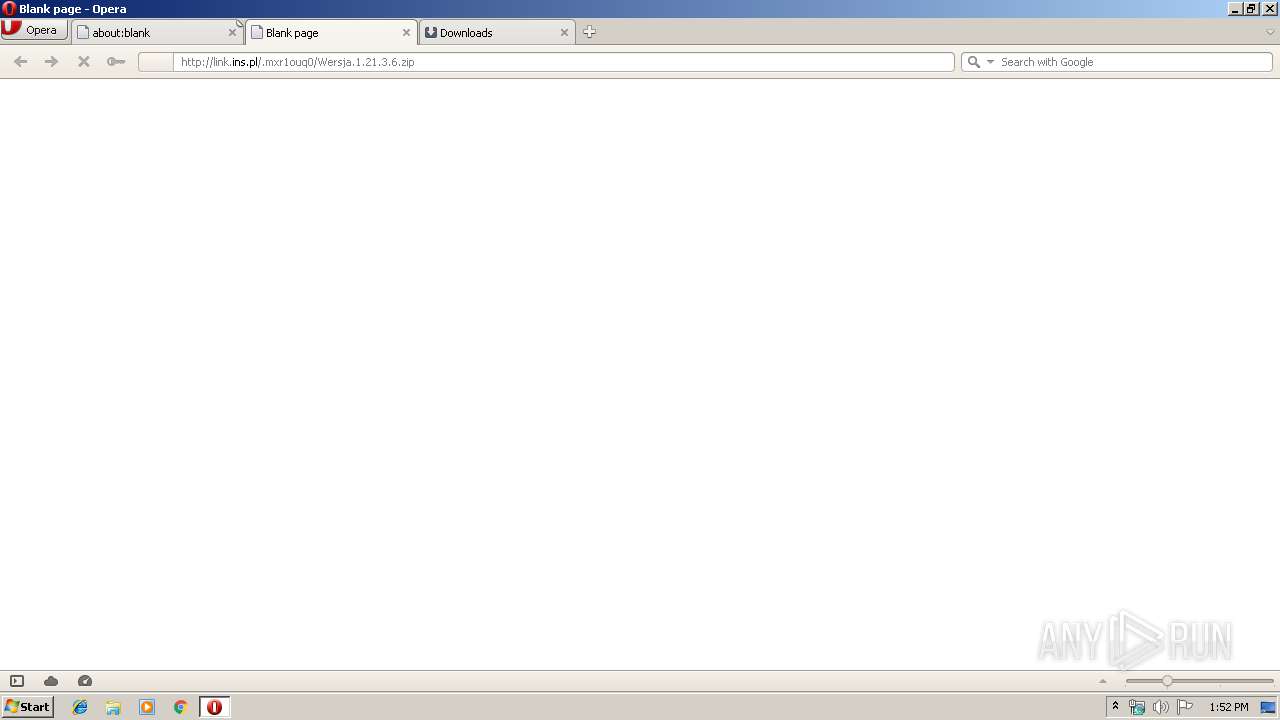
| URL: | http://link.ins.pl/.mxr1ouq0/Wersja.1.21.3.6.zip |
| Full analysis: | https://app.any.run/tasks/9706b0d8-db1b-49ba-9eca-62082f73443a |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2019, 12:51:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 501F05148F530DDE032F2EDD7C7A1FD4 |
| SHA1: | 7255221BCC28BDCD758E92135F2A9D62F315AE01 |
| SHA256: | CA0DB7FDE2441EE52491C775ABF82C040CE261E58F4A190FBBD328E61D8F71A2 |
| SSDEEP: | 3:N1KSMgKMjfXyTYELkSW4n:CShKMeTYiJdn |
MALICIOUS
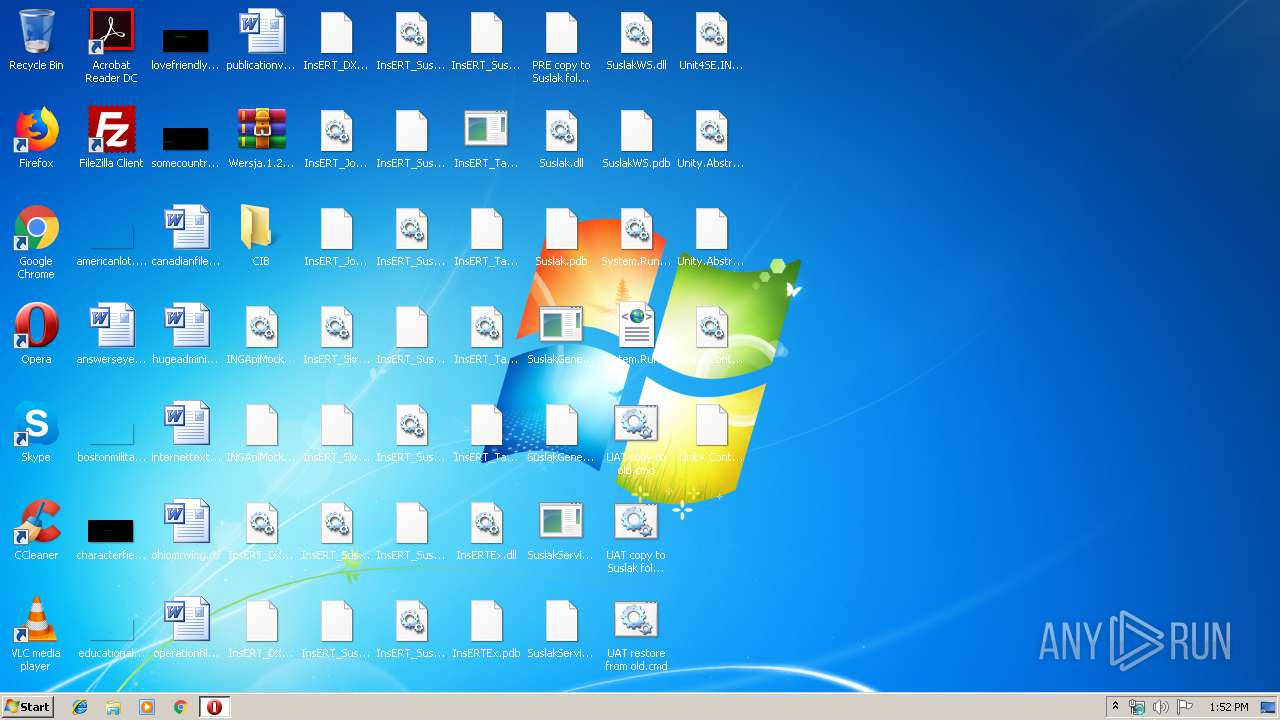
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1708)
Application was dropped or rewritten from another process
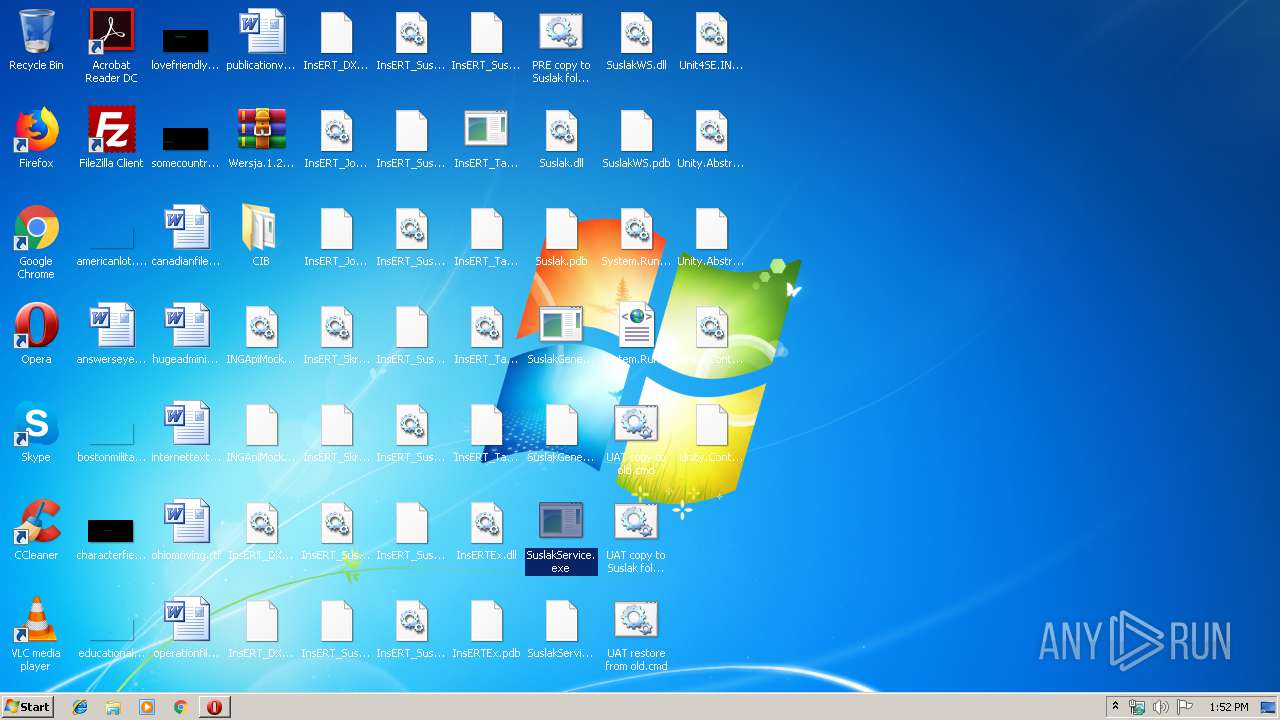
- SuslakService.exe (PID: 3648)
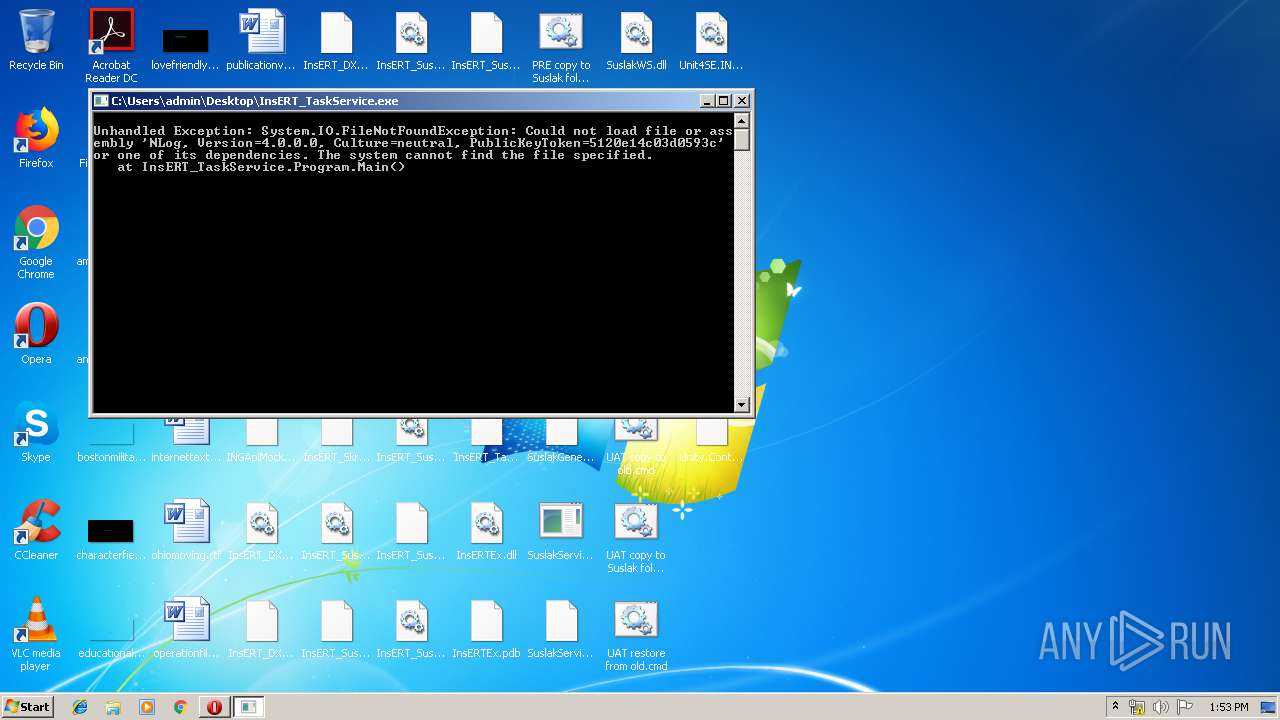
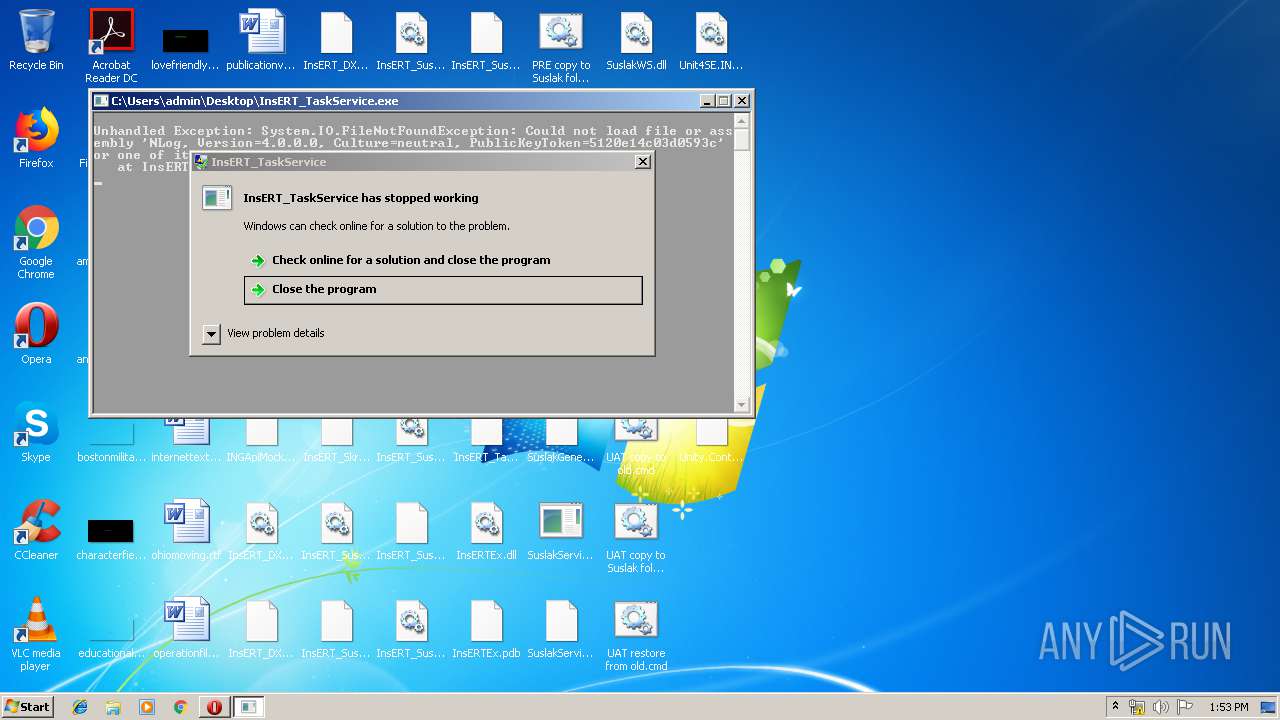
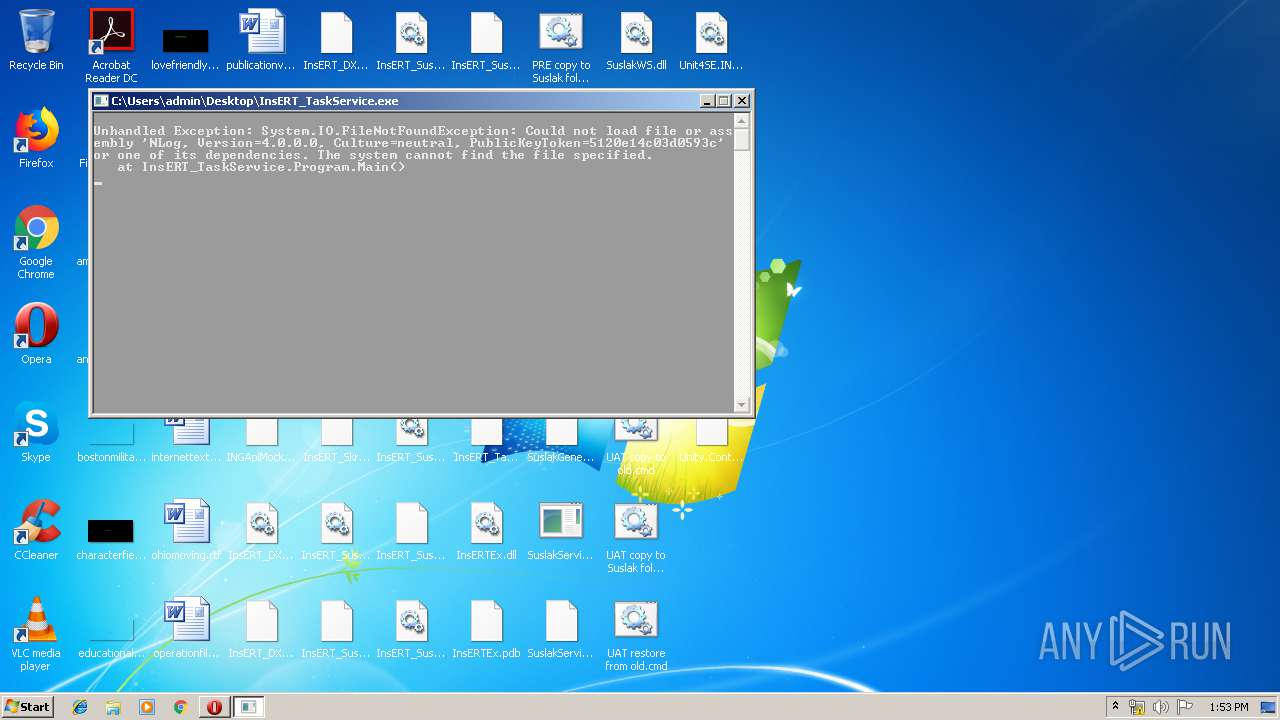
- InsERT_TaskService.exe (PID: 2420)
- SuslakGeneratorPodmiotowService.exe (PID: 3920)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2876)
INFO
Creates files in the user directory
- opera.exe (PID: 2904)
Manual execution by user
- WinRAR.exe (PID: 2876)
- SuslakGeneratorPodmiotowService.exe (PID: 3920)
- SuslakService.exe (PID: 3648)
- InsERT_TaskService.exe (PID: 2420)
Dropped object may contain Bitcoin addresses
- opera.exe (PID: 2904)
Reads Internet Cache Settings
- opera.exe (PID: 2904)
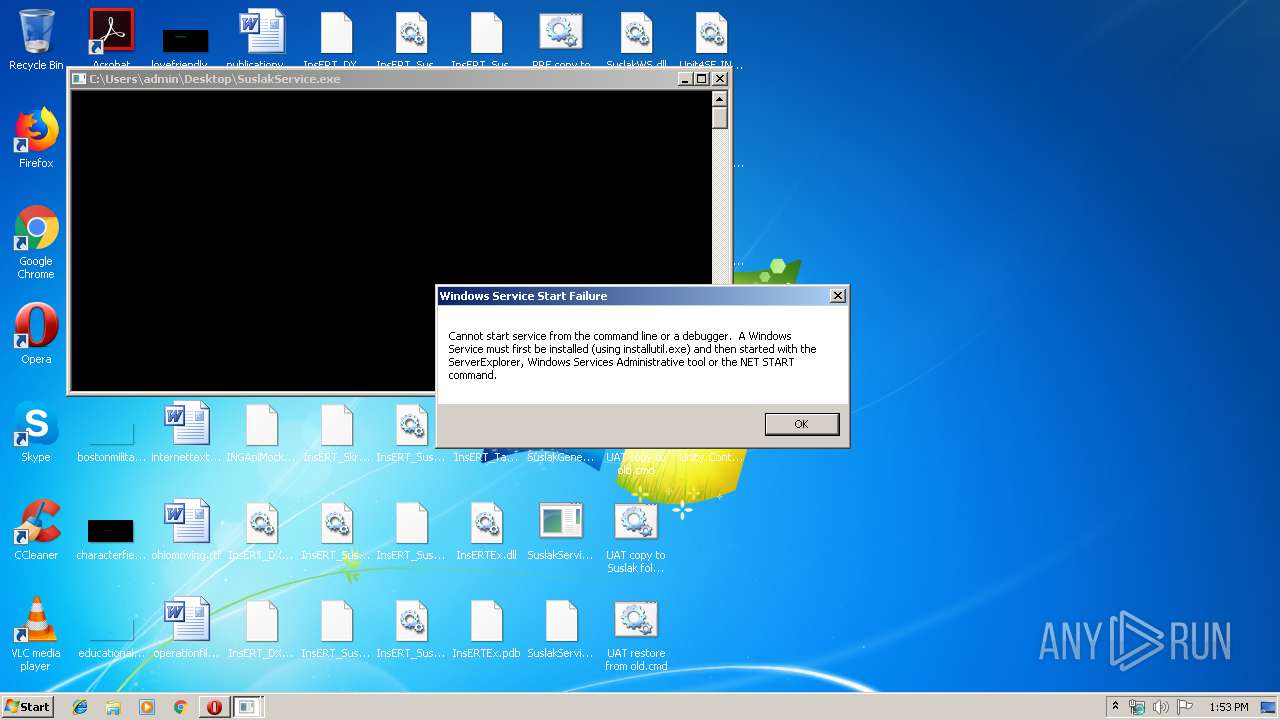
Application was crashed
- InsERT_TaskService.exe (PID: 2420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
44
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1708 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\Desktop\InsERT_TaskService.exe" | C:\Users\admin\Desktop\InsERT_TaskService.exe | explorer.exe | ||||||||||||
User: admin Company: InsERT S.A. Integrity Level: MEDIUM Description: InsERT_TaskService Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
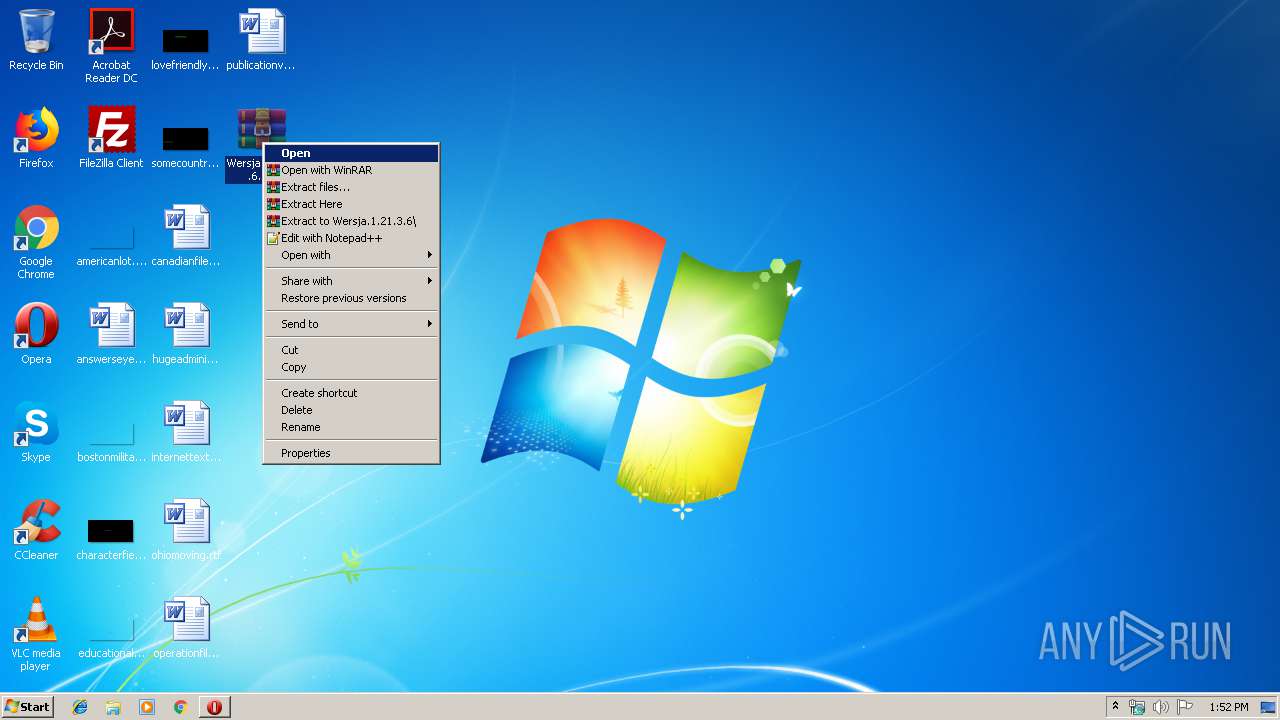
| 2876 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Wersja.1.21.3.6.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2904 | "C:\Program Files\Opera\opera.exe" http://link.ins.pl/.mxr1ouq0/Wersja.1.21.3.6.zip | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 3648 | "C:\Users\admin\Desktop\SuslakService.exe" | C:\Users\admin\Desktop\SuslakService.exe | — | explorer.exe | |||||||||||
User: admin Company: InsERT S.A. Integrity Level: MEDIUM Description: SuslakService Exit code: 0 Version: 1.11.9.1 Modules
| |||||||||||||||
| 3920 | "C:\Users\admin\Desktop\SuslakGeneratorPodmiotowService.exe" | C:\Users\admin\Desktop\SuslakGeneratorPodmiotowService.exe | — | explorer.exe | |||||||||||
User: admin Company: InsERT Integrity Level: MEDIUM Description: SuslakGeneratorPodmiotowService Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 081
Read events
938
Write events
141
Delete events
2
Modification events
| (PID) Process: | (2904) opera.exe | Key: | HKEY_CURRENT_USER\Software\Opera Software |
| Operation: | write | Name: | Last CommandLine v2 |
Value: C:\Program Files\Opera\opera.exe http://link.ins.pl/.mxr1ouq0/Wersja.1.21.3.6.zip | |||
| (PID) Process: | (2904) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2904) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2904) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0200000001000000000000000700000006000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2904) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (2904) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (2904) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (2904) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (2904) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (2904) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | FFlags |
Value: 1092616257 | |||
Executable files
29
Suspicious files
24
Text files
18
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2904 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr4148.tmp | — | |
MD5:— | SHA256:— | |||
| 2904 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr4159.tmp | — | |
MD5:— | SHA256:— | |||
| 2904 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr41B8.tmp | — | |
MD5:— | SHA256:— | |||
| 2904 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\E67NNFT4DTVN9YR89XWE.temp | — | |
MD5:— | SHA256:— | |||
| 2904 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\tasks.xml | xml | |
MD5:— | SHA256:— | |||
| 2904 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opssl6.dat | binary | |
MD5:— | SHA256:— | |||
| 2904 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\g_0000\opr00001.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2904 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16ec093b8f51508f.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2904 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00002.tmp | xml | |
MD5:— | SHA256:— | |||
| 2904 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16ec093b8f51508f.customDestinations-ms~RF154c93.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
8
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2904 | opera.exe | GET | — | 195.116.205.43:80 | http://link.ins.pl/.mxr1ouq0/Wersja.1.21.3.6.zip | PL | — | — | suspicious |
2904 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 528 b | whitelisted |
2904 | opera.exe | GET | 400 | 185.26.182.94:80 | http://sitecheck2.opera.com/?host=link.ins.pl&hdn=vGjwzn/GZbO1yaL72JmDJA== | unknown | html | 150 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2904 | opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
2904 | opera.exe | 185.26.182.94:443 | certs.opera.com | Opera Software AS | — | whitelisted |
2904 | opera.exe | 195.116.205.43:80 | link.ins.pl | Orange Polska Spolka Akcyjna | PL | suspicious |
2904 | opera.exe | 185.26.182.94:80 | certs.opera.com | Opera Software AS | — | whitelisted |
2904 | opera.exe | 93.184.220.29:80 | crl4.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
link.ins.pl |
| suspicious |
certs.opera.com |
| whitelisted |
sitecheck2.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |