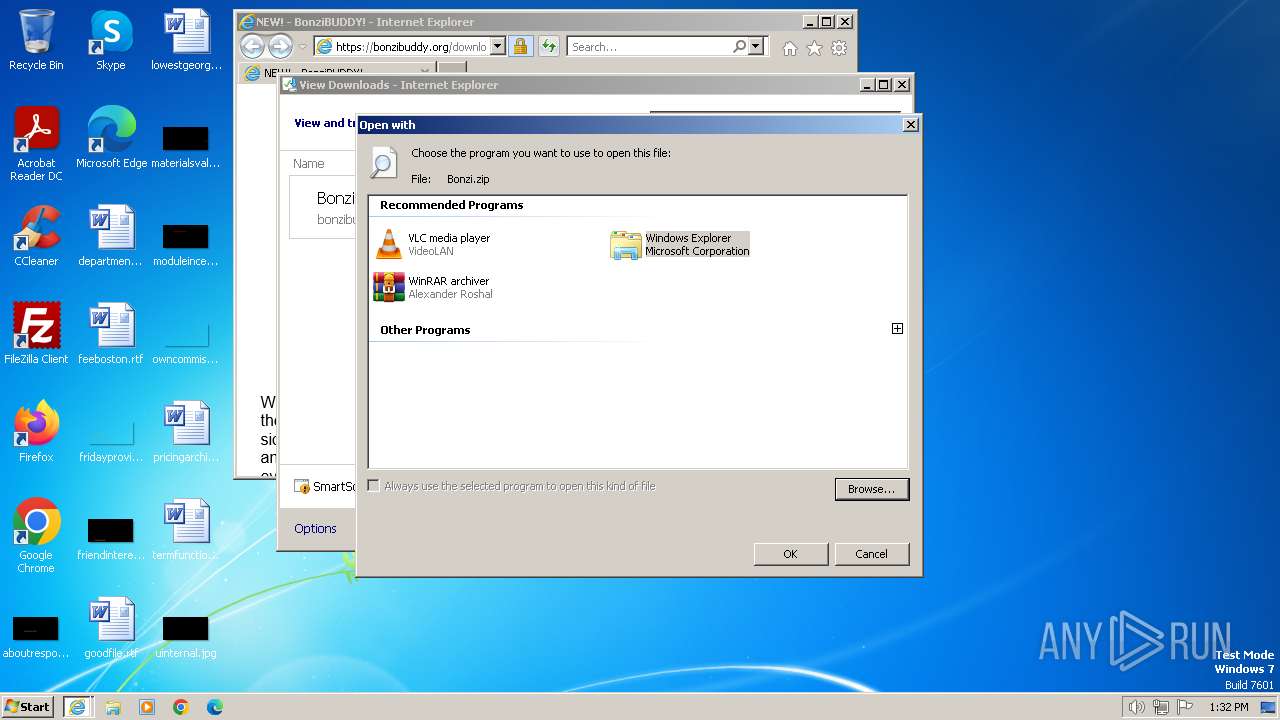
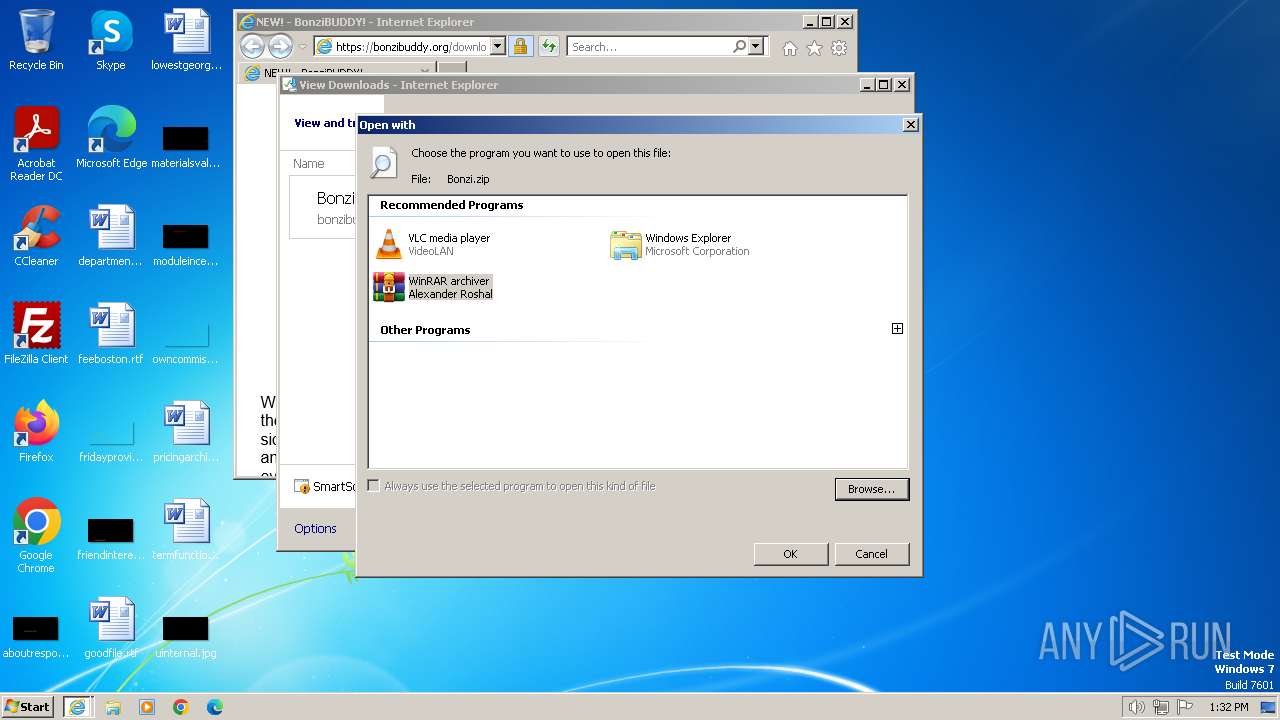
| URL: | https://bonzibuddy.org/download.html |
| Full analysis: | https://app.any.run/tasks/2d868e65-61ee-4f91-abf2-4d1bb25d8e63 |
| Verdict: | Malicious activity |
| Analysis date: | March 03, 2024, 13:30:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 8A56C620CE694BE321DD4B4ABEE33AC4 |
| SHA1: | 3856204BE8F661C8973766E2D67F40BCADD4E2FE |
| SHA256: | CA0C72BCBC2CFA4454EBE7DC9D70DE3A6AFE7205739FAF3AC2136C399C39DFC9 |
| SSDEEP: | 3:N89E3Q:296Q |
MALICIOUS
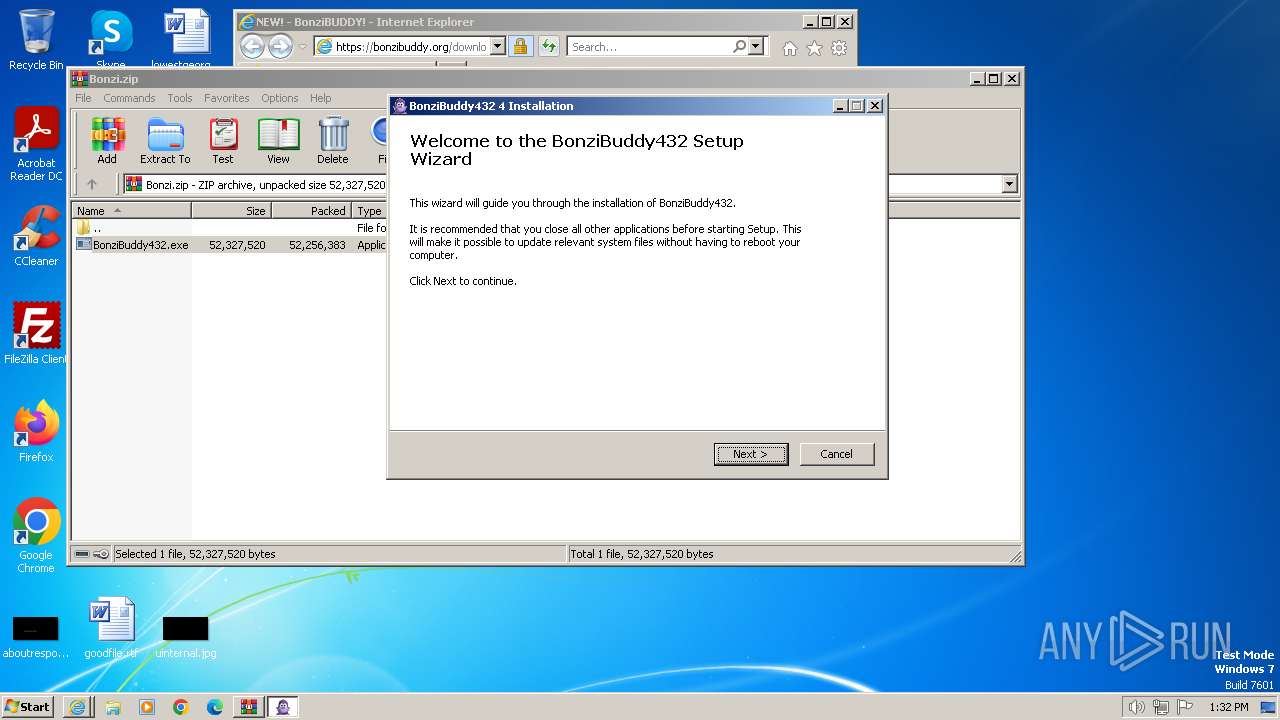
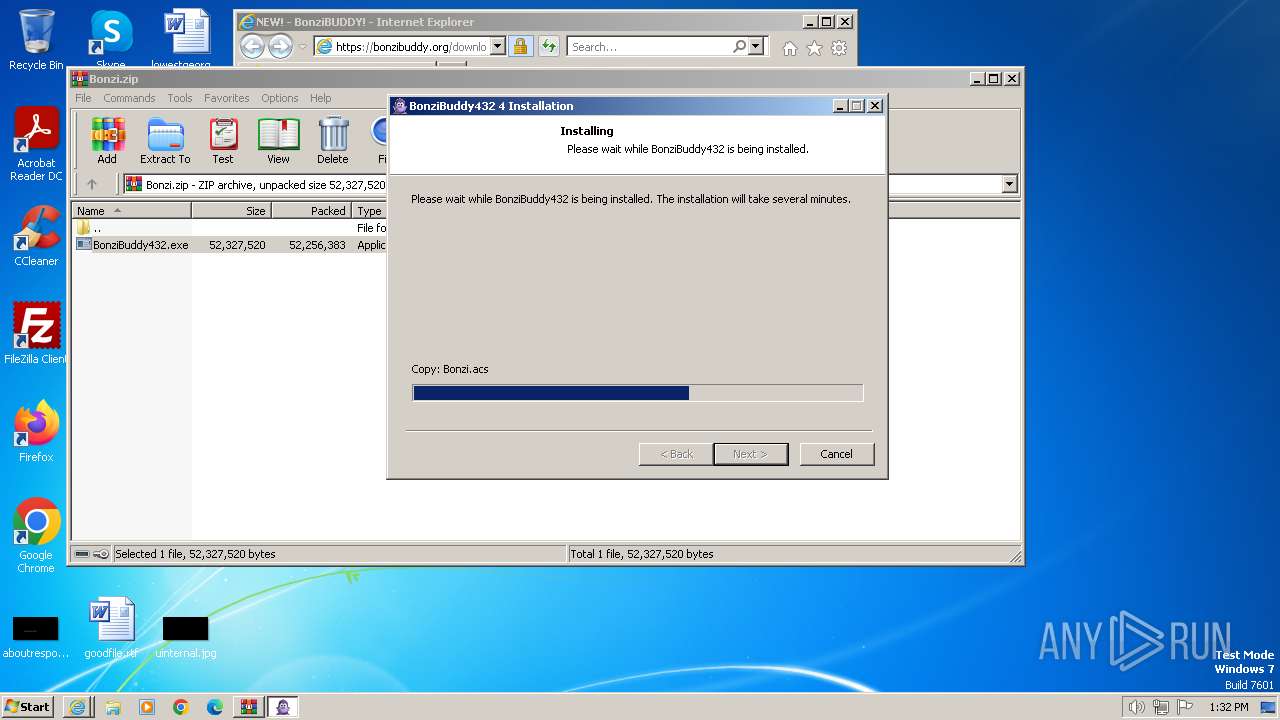
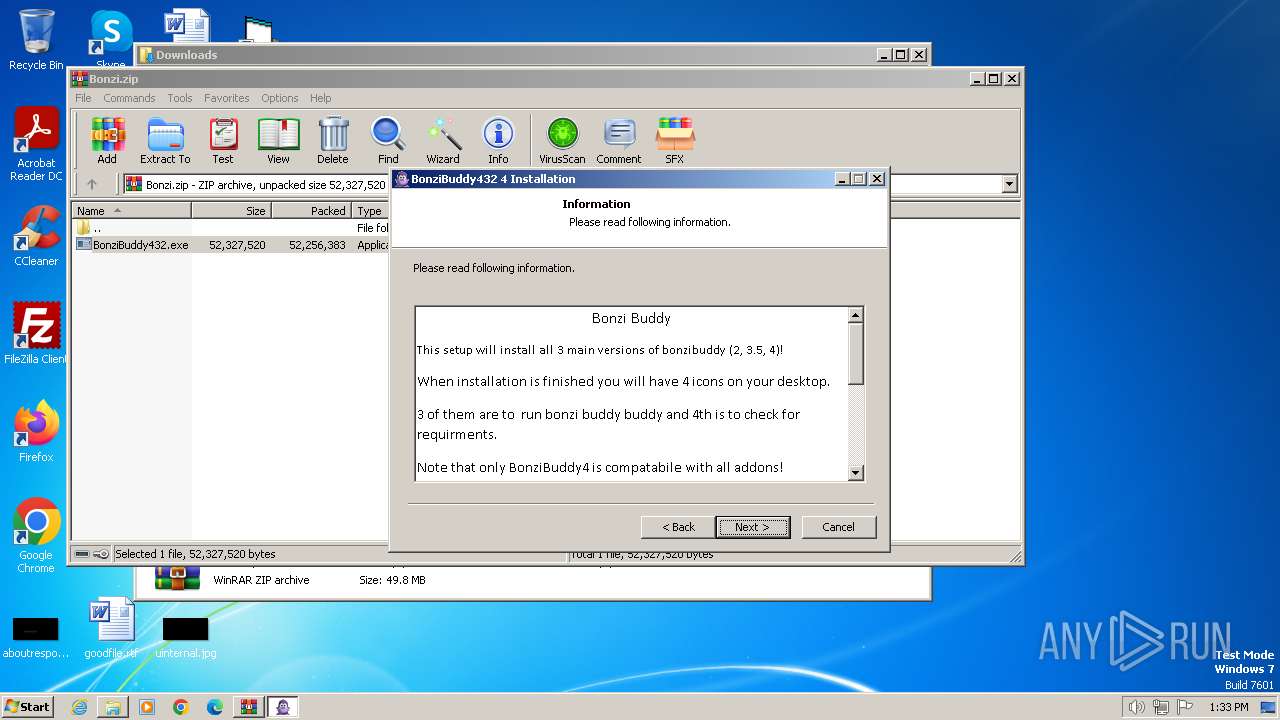
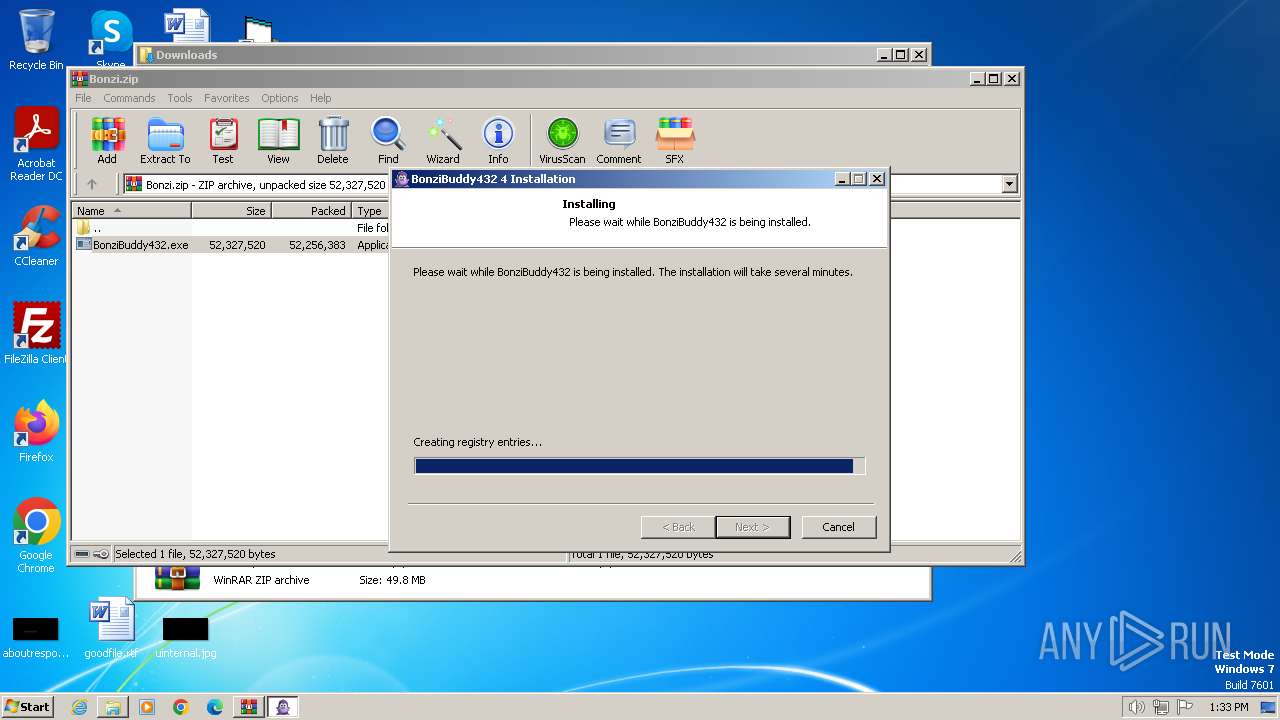
Drops the executable file immediately after the start
- BonziBuddy432.exe (PID: 680)
- MSAGENT.EXE (PID: 2468)
- tv_enua.exe (PID: 2992)
- BonziBuddy432.exe (PID: 3740)
Registers / Runs the DLL via REGSVR32.EXE
- MSAGENT.EXE (PID: 2468)
- tv_enua.exe (PID: 2992)
Creates a writable file in the system directory
- tv_enua.exe (PID: 2992)
Changes the autorun value in the registry
- tv_enua.exe (PID: 2992)
SUSPICIOUS
Reads the Internet Settings
- BonziBuddy432.exe (PID: 680)
- BonziBuddy432.exe (PID: 3740)
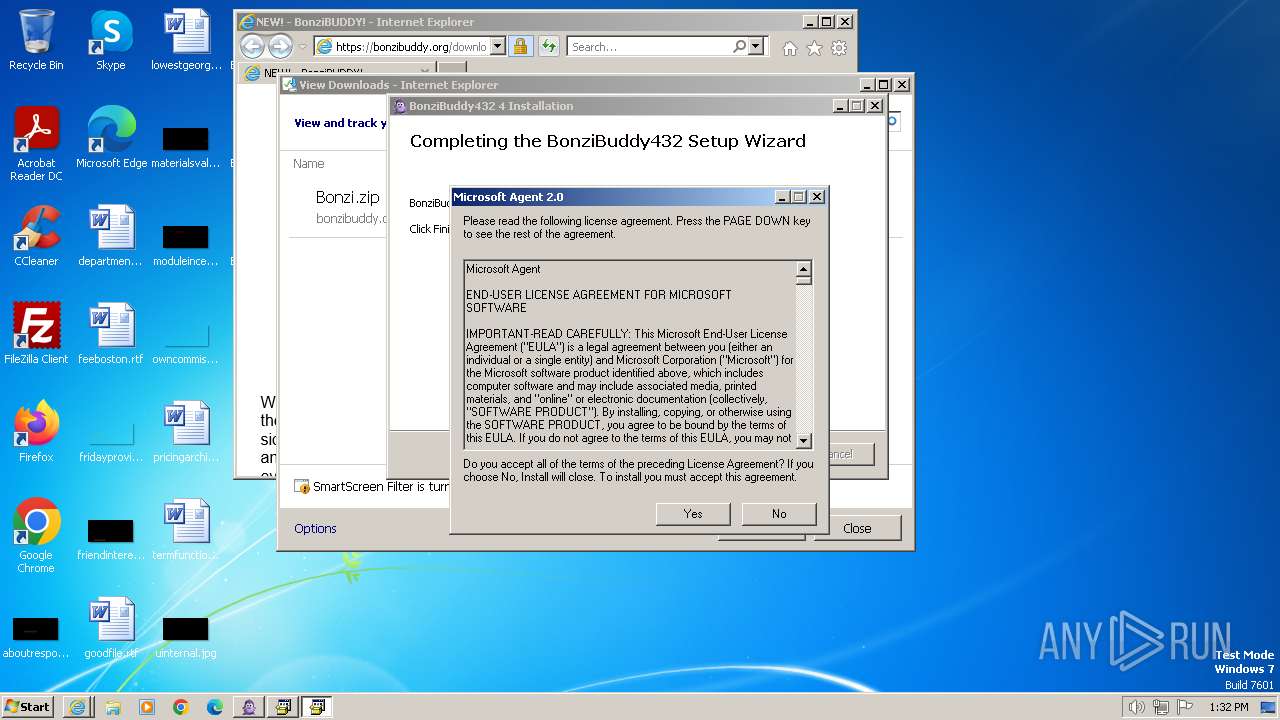
Reads security settings of Internet Explorer
- BonziBuddy432.exe (PID: 680)
- WinRAR.exe (PID: 2432)
- WinRAR.exe (PID: 2824)
- BonziBuddy432.exe (PID: 3740)
Executing commands from a ".bat" file
- BonziBuddy432.exe (PID: 680)
- BonziBuddy432.exe (PID: 3740)
Starts CMD.EXE for commands execution
- BonziBuddy432.exe (PID: 680)
- BonziBuddy432.exe (PID: 3740)
Executable content was dropped or overwritten
- MSAGENT.EXE (PID: 2468)
- tv_enua.exe (PID: 2992)
- BonziBuddy432.exe (PID: 3740)
- BonziBuddy432.exe (PID: 680)
Process drops legitimate windows executable
- MSAGENT.EXE (PID: 2468)
- tv_enua.exe (PID: 2992)
- BonziBuddy432.exe (PID: 3740)
- BonziBuddy432.exe (PID: 680)
Creates/Modifies COM task schedule object
- BonziBuddy432.exe (PID: 680)
- regsvr32.exe (PID: 3620)
- regsvr32.exe (PID: 2588)
- regsvr32.exe (PID: 2568)
- regsvr32.exe (PID: 2404)
- regsvr32.exe (PID: 124)
- regsvr32.exe (PID: 2396)
- regsvr32.exe (PID: 2376)
- regsvr32.exe (PID: 784)
- regsvr32.exe (PID: 948)
- BonziBuddy432.exe (PID: 3740)
Creates a software uninstall entry
- tv_enua.exe (PID: 2992)
- BonziBuddy432.exe (PID: 3740)
- BonziBuddy432.exe (PID: 680)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 2432)
- iexplore.exe (PID: 3700)
- WinRAR.exe (PID: 2824)
Application launched itself
- iexplore.exe (PID: 3700)
- msedge.exe (PID: 1548)
- msedge.exe (PID: 1168)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3700)
Reads the computer name
- BonziBuddy432.exe (PID: 680)
- MSAGENT.EXE (PID: 2468)
- tv_enua.exe (PID: 2992)
- BonziBuddy432.exe (PID: 3740)
Creates files or folders in the user directory
- BonziBuddy432.exe (PID: 680)
Reads mouse settings
- BonziBuddy432.exe (PID: 680)
- BonziBuddy432.exe (PID: 3740)
Checks supported languages
- BonziBuddy432.exe (PID: 680)
- tv_enua.exe (PID: 2992)
- MSAGENT.EXE (PID: 2468)
- AgentSvr.exe (PID: 2584)
- BonziBDY_4.EXE (PID: 3232)
- BonziBDY_35.EXE (PID: 3100)
- BonziBDY_2.EXE (PID: 2656)
- BonziBDY_35.EXE (PID: 3272)
- BonziBuddy432.exe (PID: 3740)
- BonziBDY_4.EXE (PID: 2516)
- BonziBDY_4.EXE (PID: 1216)
Create files in a temporary directory
- MSAGENT.EXE (PID: 2468)
- tv_enua.exe (PID: 2992)
- BonziBuddy432.exe (PID: 3740)
- BonziBuddy432.exe (PID: 680)
Manual execution by a user
- BonziBDY_35.EXE (PID: 3272)
- BonziBDY_35.EXE (PID: 3100)
- explorer.exe (PID: 3112)
- WinRAR.exe (PID: 2824)
- BonziBDY_4.EXE (PID: 3232)
- BonziBDY_2.EXE (PID: 2656)
- msedge.exe (PID: 1548)
- BonziBDY_4.EXE (PID: 2516)
- BonziBDY_4.EXE (PID: 1216)
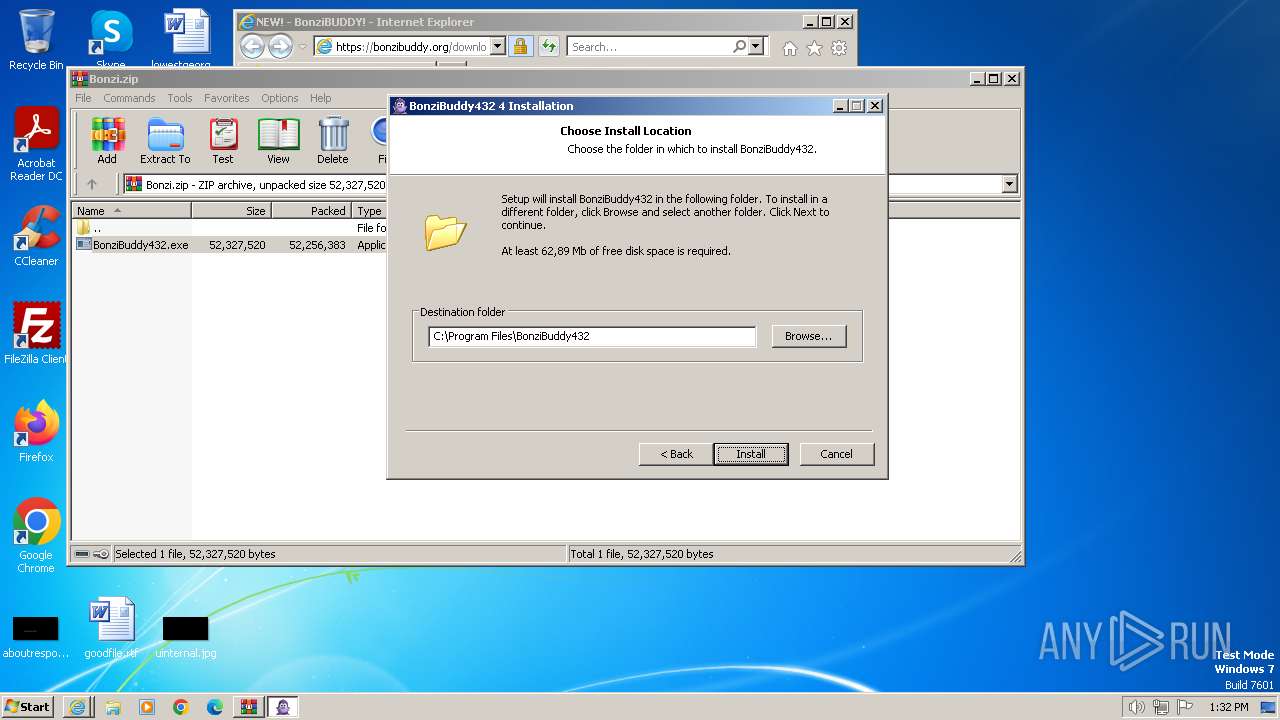
Creates files in the program directory
- BonziBuddy432.exe (PID: 3740)
- BonziBuddy432.exe (PID: 680)
Drops the executable file immediately after the start
- msedge.exe (PID: 1548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
103
Monitored processes
51
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | regsvr32 /s "C:\Windows\msagent\AgentPsh.dll" | C:\Windows\System32\regsvr32.exe | — | MSAGENT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 680 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2432.24278\BonziBuddy432.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2432.24278\BonziBuddy432.exe | WinRAR.exe | ||||||||||||
User: admin Company: Bonzi Software Integrity Level: HIGH Description: BonziBuddy432 4 Installation Exit code: 0 Version: 4 Modules
| |||||||||||||||
| 764 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3224 --field-trial-handle=1328,i,15454747248929799893,14660445874440435367,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 784 | regsvr32 /s C:\Windows\lhsp\tv\tv_enua.dll | C:\Windows\System32\regsvr32.exe | — | tv_enua.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 864 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x6bcdf598,0x6bcdf5a8,0x6bcdf5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 948 | regsvr32 /s C:\Windows\lhsp\tv\tvenuax.dll | C:\Windows\System32\regsvr32.exe | — | tv_enua.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
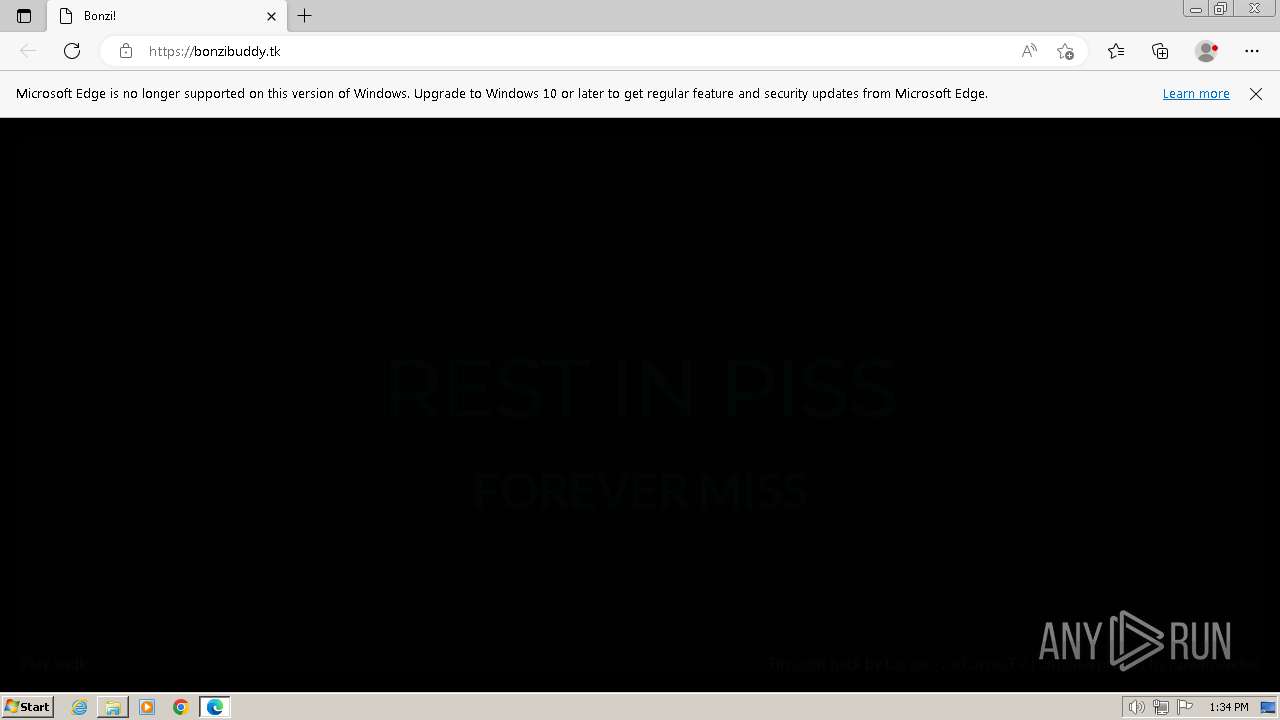
| 1168 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument http://bonzibuddy.tk/ | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | BonziBuddy432.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1216 | grpconv.exe -o | C:\Windows\System32\grpconv.exe | — | MSAGENT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1216 | "C:\Program Files\BonziBuddy432\BonziBDY_4.EXE" | C:\Program Files\BonziBuddy432\BonziBDY_4.EXE | — | explorer.exe | |||||||||||
User: admin Company: BONZI.COM Software Integrity Level: MEDIUM Description: BonziBUDDY, the intelligent, interactive traveling companion on the Internet. Exit code: 0 Version: 4.01.0009 Modules
| |||||||||||||||
| 1352 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2432.24278\BonziBuddy432.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2432.24278\BonziBuddy432.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Bonzi Software Integrity Level: MEDIUM Description: BonziBuddy432 4 Installation Exit code: 3221226540 Version: 4 Modules
| |||||||||||||||
Total events
45 029
Read events
43 668
Write events
906
Delete events
455
Modification events
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 128881616 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31092079 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 429042866 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31092079 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
117
Suspicious files
106
Text files
356
Unknown types
72
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:15B91BD6043D5C5BEB817B77FDC31432 | SHA256:04075B9196612538402646F9EE5A712C1599AD159B71B7A9F78B1D9E4B336A3B | |||
| 3700 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | der | |
MD5:1ECD3AFFD593047A1B3C250128289475 | SHA256:496284B831ACE71F9BEA6534037625F9063B71F2439840386B6DD76E0593D62D | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\bbvine[1].gif | image | |
MD5:C1F1DF26B445100C74EFF268CAA3112F | SHA256:58D0BF159A3DF8BBDE468999B349AE0DF54820936A4D5F089754B1DE54B8D260 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:9BEF185873AA6BA06147E57361248FA6 | SHA256:B08D3AE10FD689F52981F05F332F3FD1BCBC401D3FF73EE8235193694314E933 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\download[1].htm | html | |
MD5:CB08660747E3BFB38F6DE8492385ED1C | SHA256:CF69E6FCB6B15F8521CE78479503DA6F1ACA7C1D4E8BB4270A043098A66998F2 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\bbsearch[1].gif | image | |
MD5:2ABEBA1841F79D811756659B2AD47D93 | SHA256:8D10D0BED2F6814ABAF3AA81F01BA37B80490C682E04FB777DD266B9D8DF3BF0 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\download[1].gif | image | |
MD5:4B1C229D42D8604A214C6A6799AAA868 | SHA256:820701D14CAD06E81EB0FEC257AEB9A384CB55F8C9946F3D94FA7322043542E7 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:E3AA453A55638BCECC11958B116DC597 | SHA256:41F0A1B15DD35C2D25442B17BF16602CDADDBEA176765B01E8633B20C7EDD544 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:33D721987032531B4A7D0735AFED2327 | SHA256:E20793EF709140C343C36A31C4E3E6B0B54D779E378FFF55AF77E84D6A10180C | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E0802E4632F2005DDCC501E41C2958E5 | binary | |
MD5:A40D58604AD6755589C71851CAF8D492 | SHA256:6F63449E8286AC961AC94C34AFA574A187E6848A63096E36A0DFD295FC67A761 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
53
DNS requests
37
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2044 | iexplore.exe | GET | 304 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f78d505714a595e3 | unknown | — | — | unknown |
2044 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | binary | 1.42 Kb | unknown |
2044 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | binary | 2.18 Kb | unknown |
2044 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQDGWFyEtC08I%2B9RkZGiJTAP | unknown | binary | 472 b | unknown |
3700 | iexplore.exe | GET | 304 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?18014fff35250a83 | unknown | — | — | unknown |
3700 | iexplore.exe | GET | 304 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?70b4a85d87201c80 | unknown | — | — | unknown |
3700 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
2044 | iexplore.exe | GET | 301 | 198.187.29.31:80 | http://bonzibuddy.org/Bonzi.zip | unknown | html | 795 b | unknown |
1080 | svchost.exe | GET | 200 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?fc91d912a85a08d5 | unknown | compressed | 67.5 Kb | unknown |
3700 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2044 | iexplore.exe | 198.187.29.31:443 | bonzibuddy.org | NAMECHEAP-NET | US | unknown |
2044 | iexplore.exe | 87.248.205.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
2044 | iexplore.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
3700 | iexplore.exe | 198.187.29.31:443 | bonzibuddy.org | NAMECHEAP-NET | US | unknown |
3700 | iexplore.exe | 87.248.205.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
3700 | iexplore.exe | 2.19.193.83:443 | www.bing.com | Akamai International B.V. | TR | unknown |
3700 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bonzibuddy.org |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3516 | msedge.exe | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
3516 | msedge.exe | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
3516 | msedge.exe | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
3516 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
3516 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |