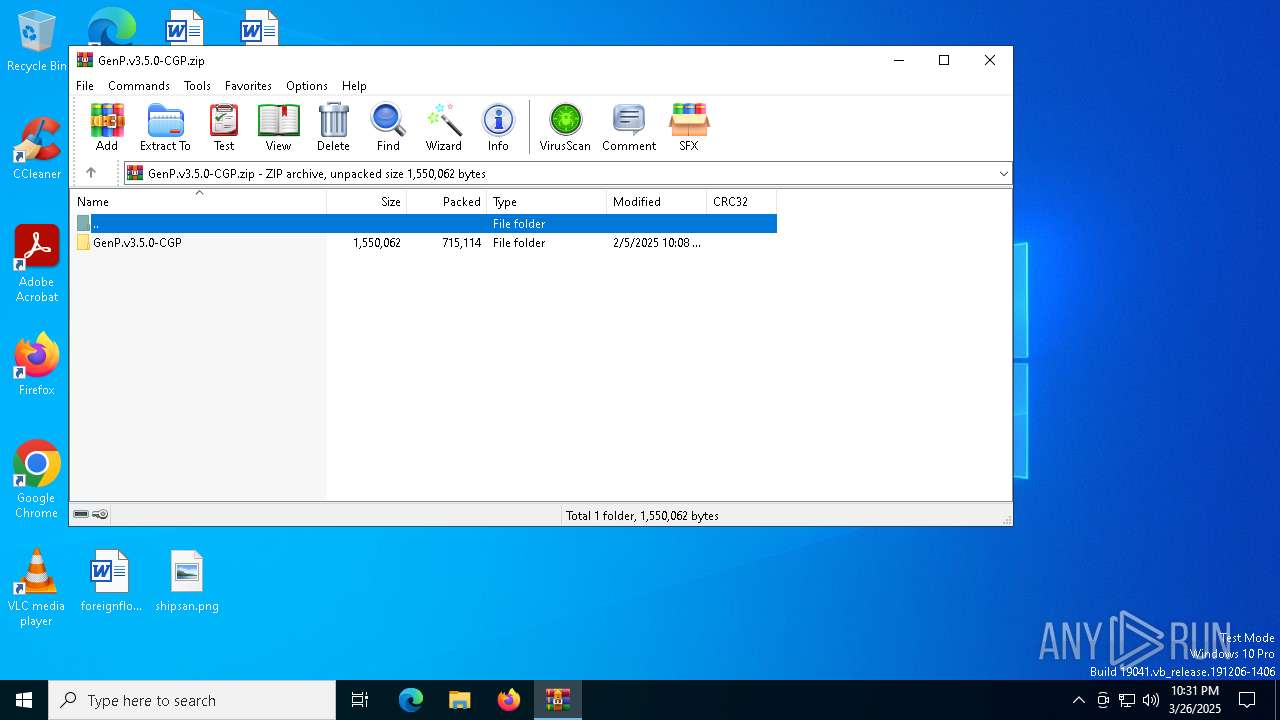
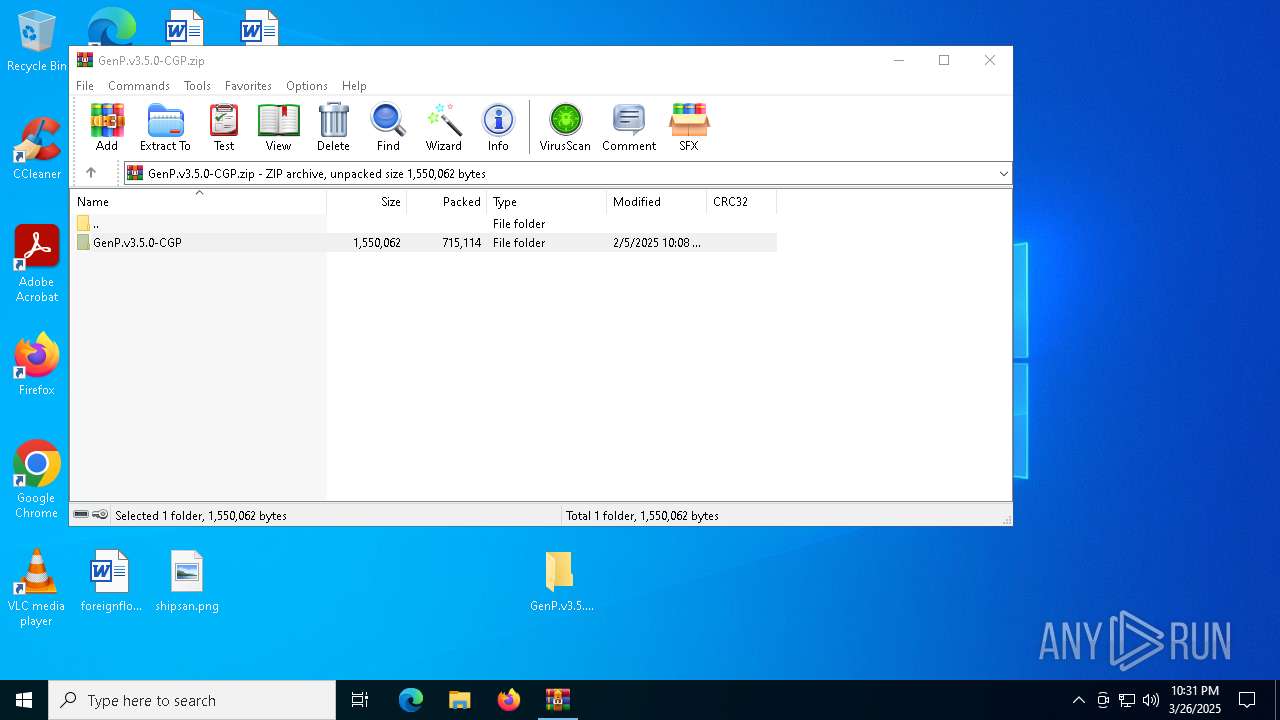
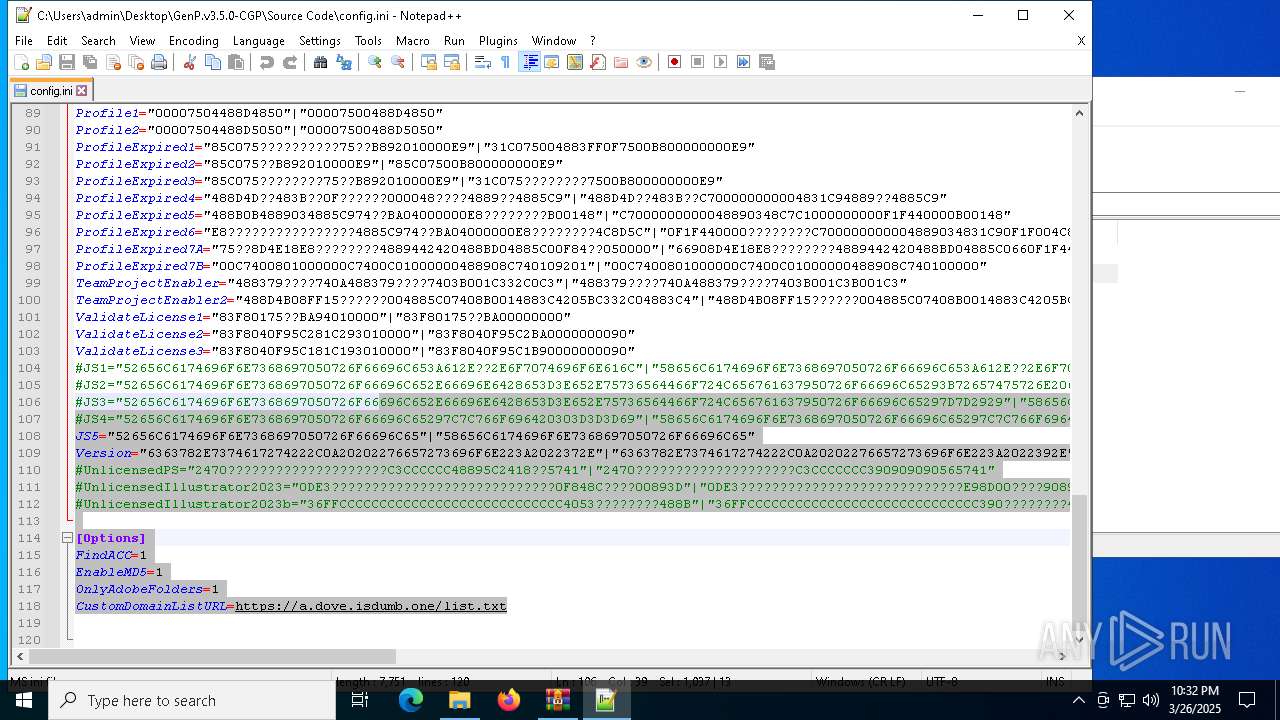
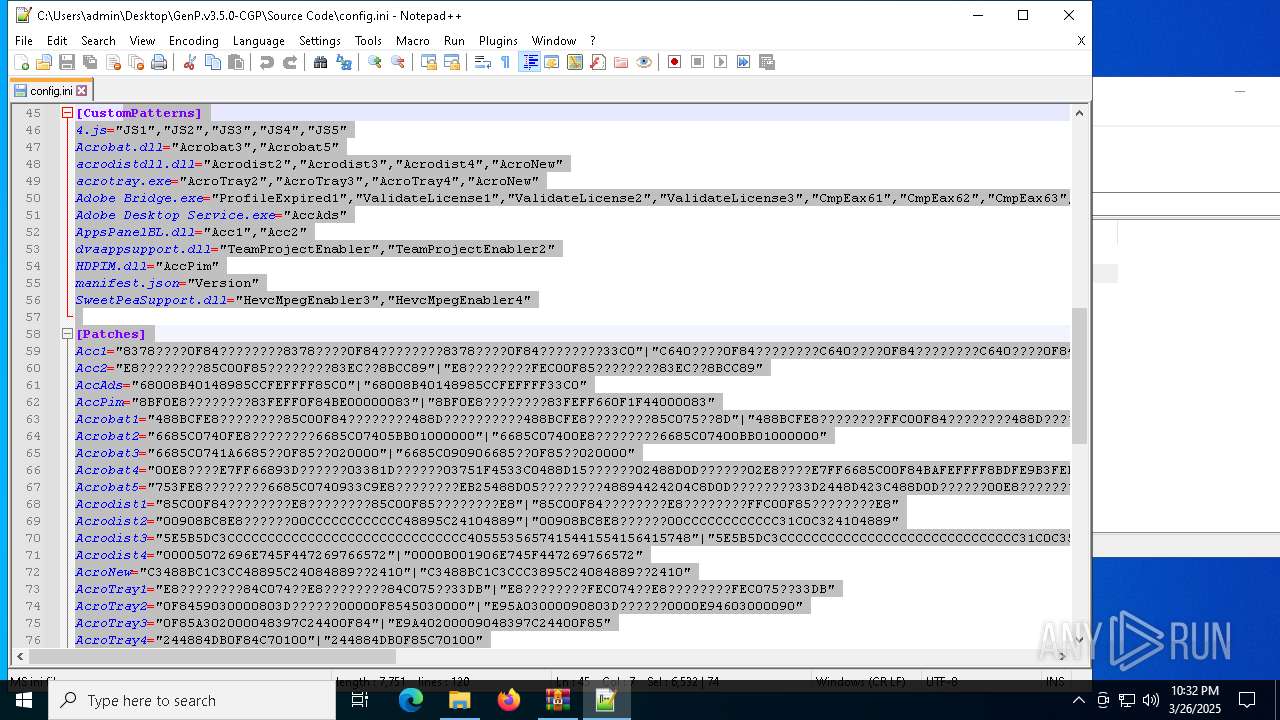
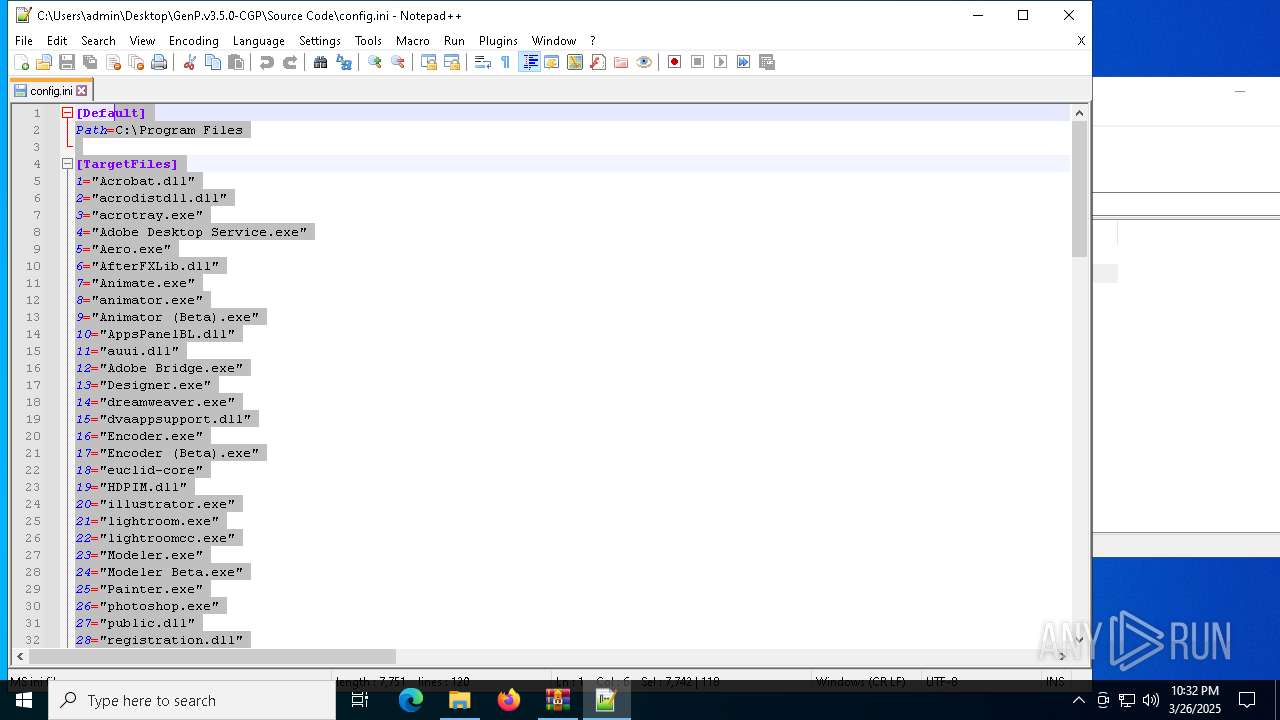
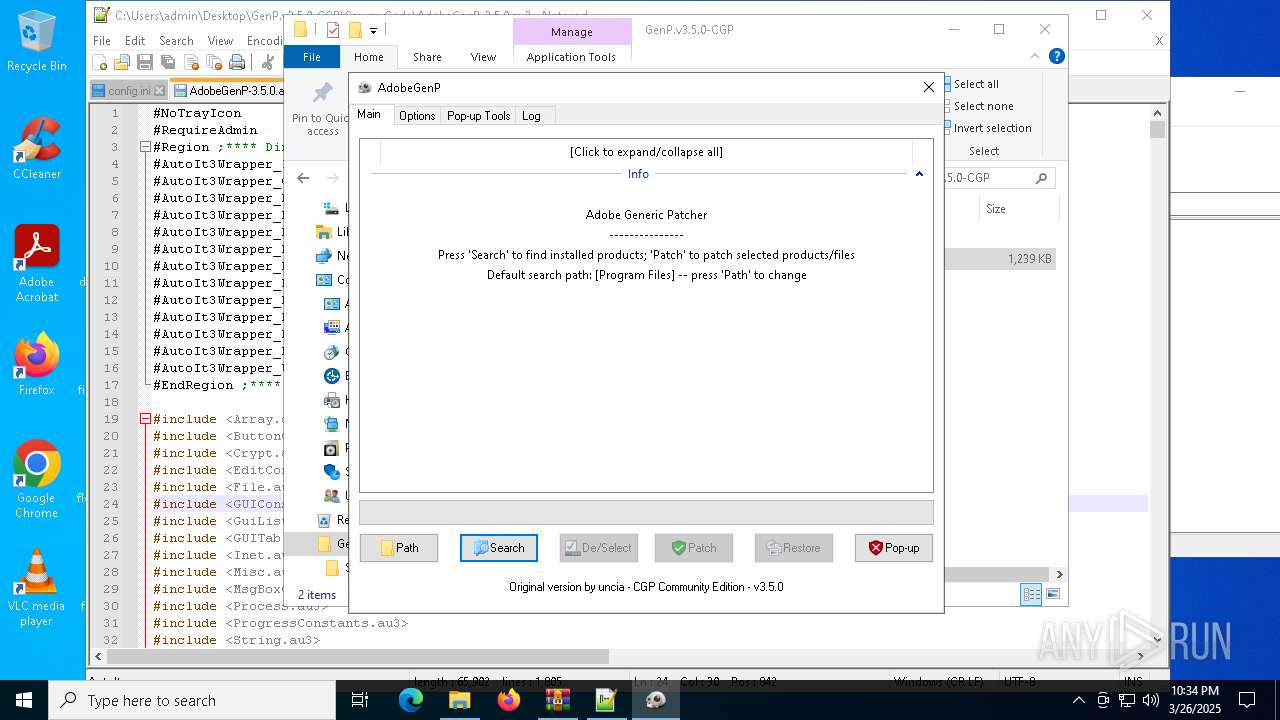
| File name: | GenP.v3.5.0-CGP.zip |
| Full analysis: | https://app.any.run/tasks/f2265ddc-69bf-4852-91c2-1cbe2ec267b1 |
| Verdict: | Malicious activity |
| Analysis date: | March 26, 2025, 22:31:17 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 44A3093AFEF9BAE5C0B5856C36692AF7 |
| SHA1: | D5712662329A6E9FE3977574FA81490C3BFDCCAA |
| SHA256: | CA0AA3669485C241AF5166EDEA379B2A5474452B0D3F0951E0D5DB1CCB5616F4 |
| SSDEEP: | 24576:MEnzxX446LUlua9orG9cv3kuWdTBhv1Fmj2EmKXXVfnQ2AmiLtK5:MEnzxX446LUluU0G9cvkuWdTBhv1FmSO |
MALICIOUS
No malicious indicators.SUSPICIOUS
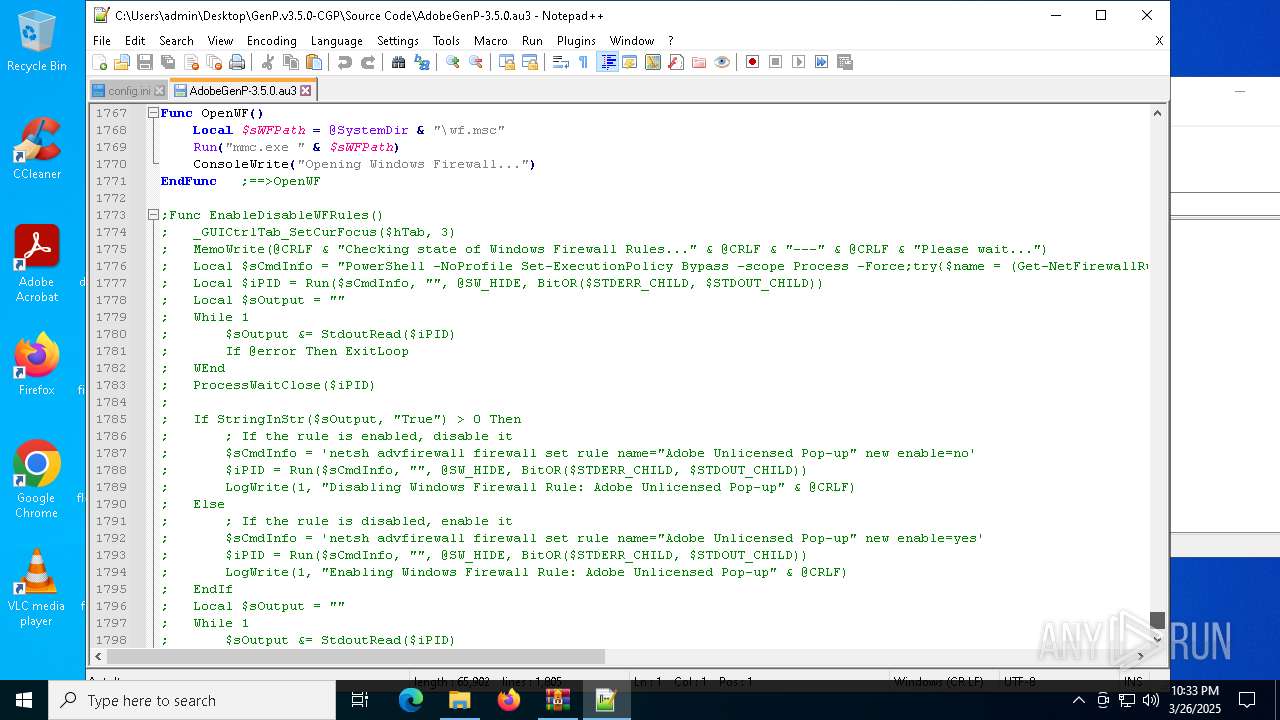
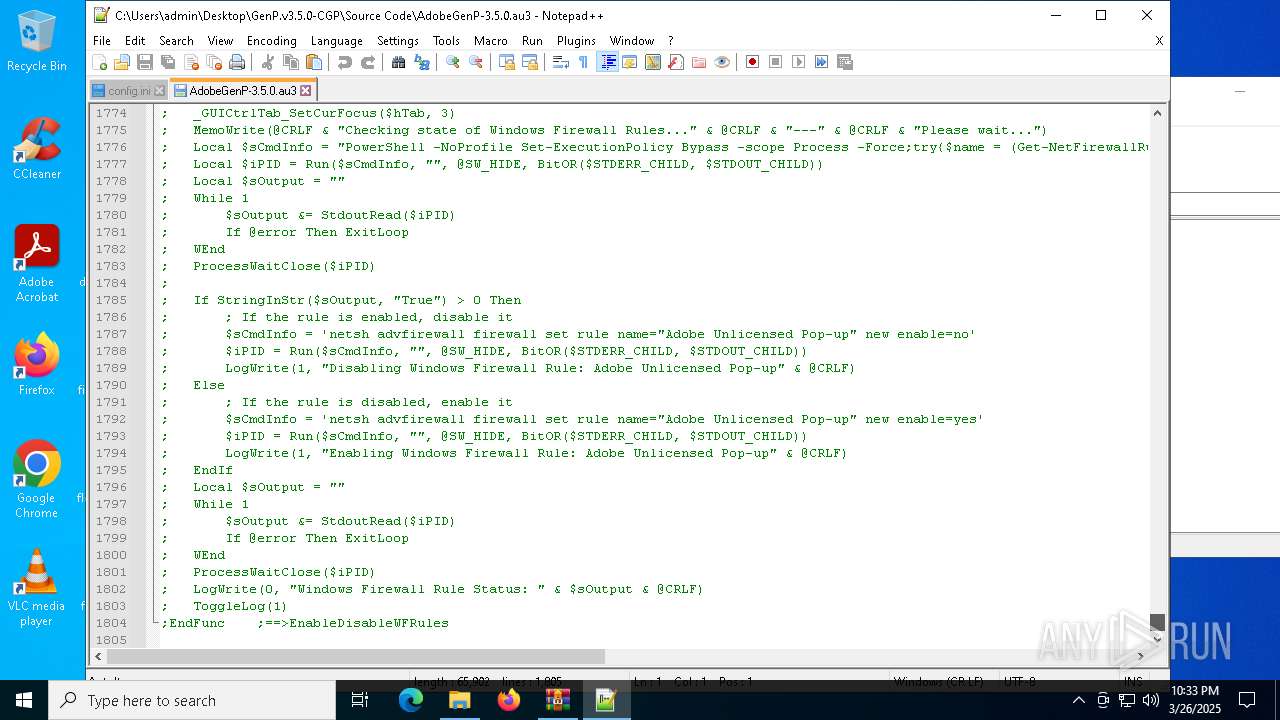
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 7596)
- GenP 3.5.0.exe (PID: 7200)
ADOBEGENP mutex has been found
- GenP 3.5.0.exe (PID: 7200)
Creates files in the driver directory
- GenP 3.5.0.exe (PID: 7200)
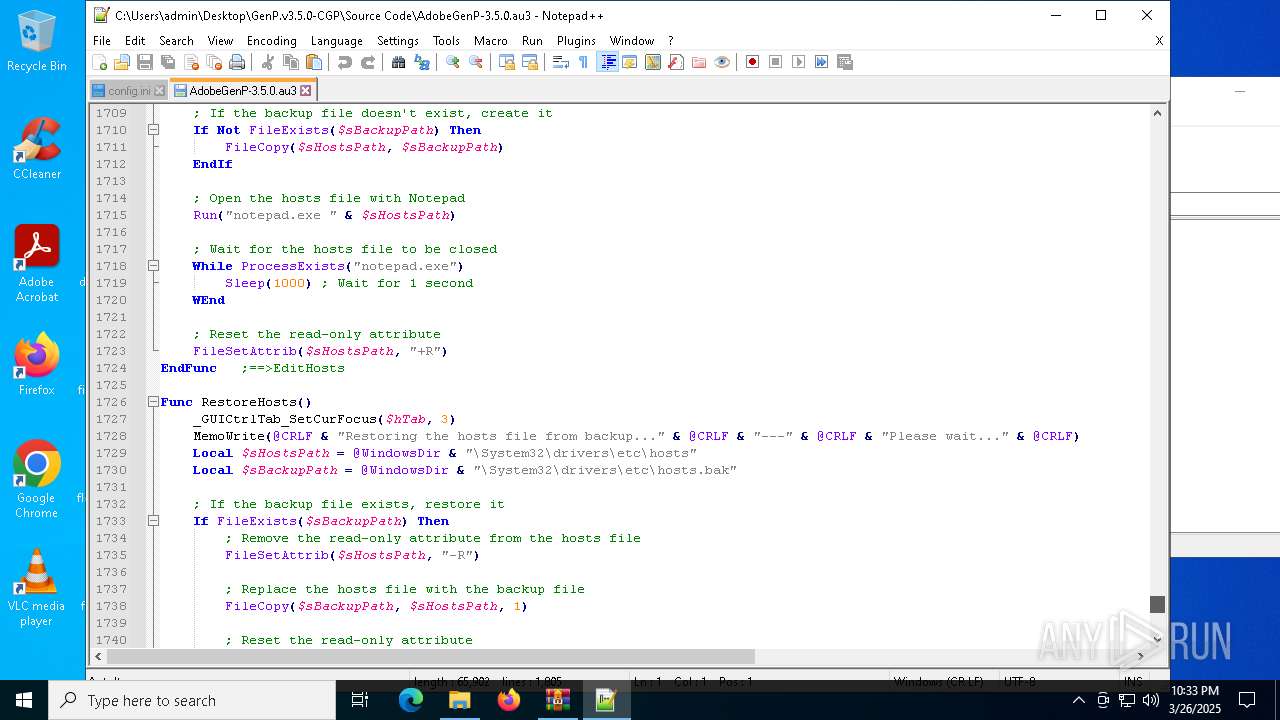
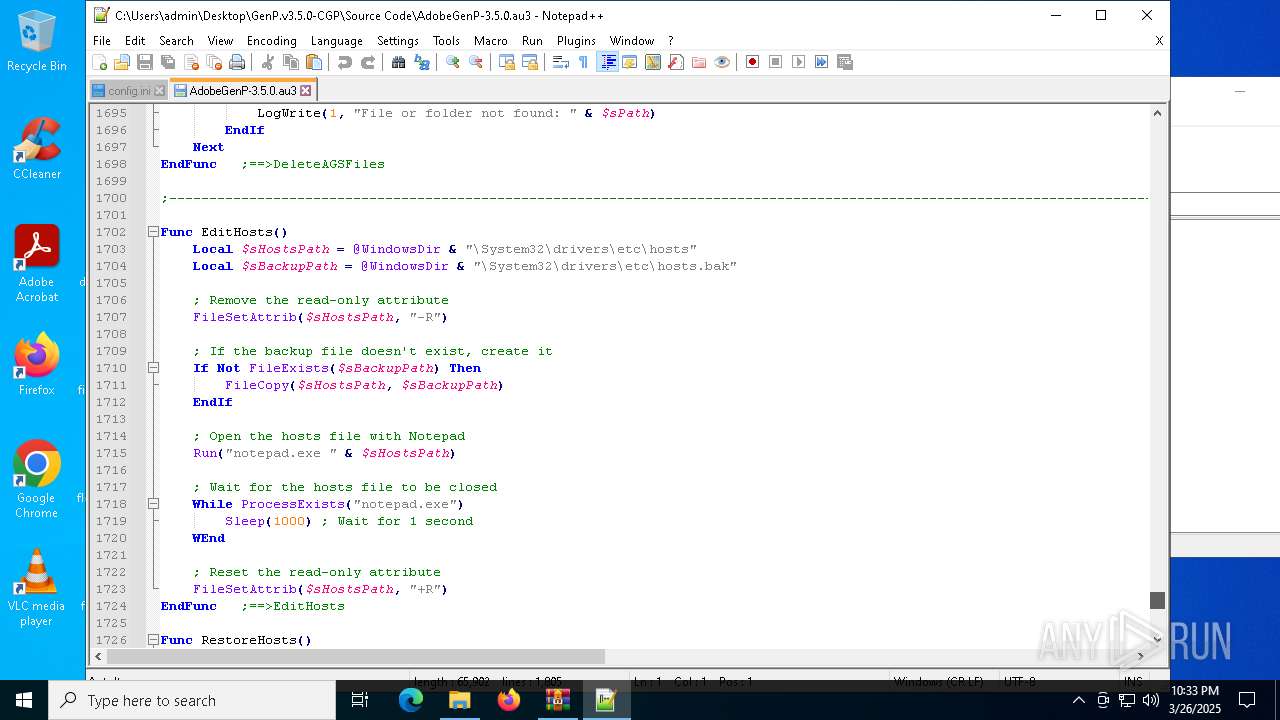
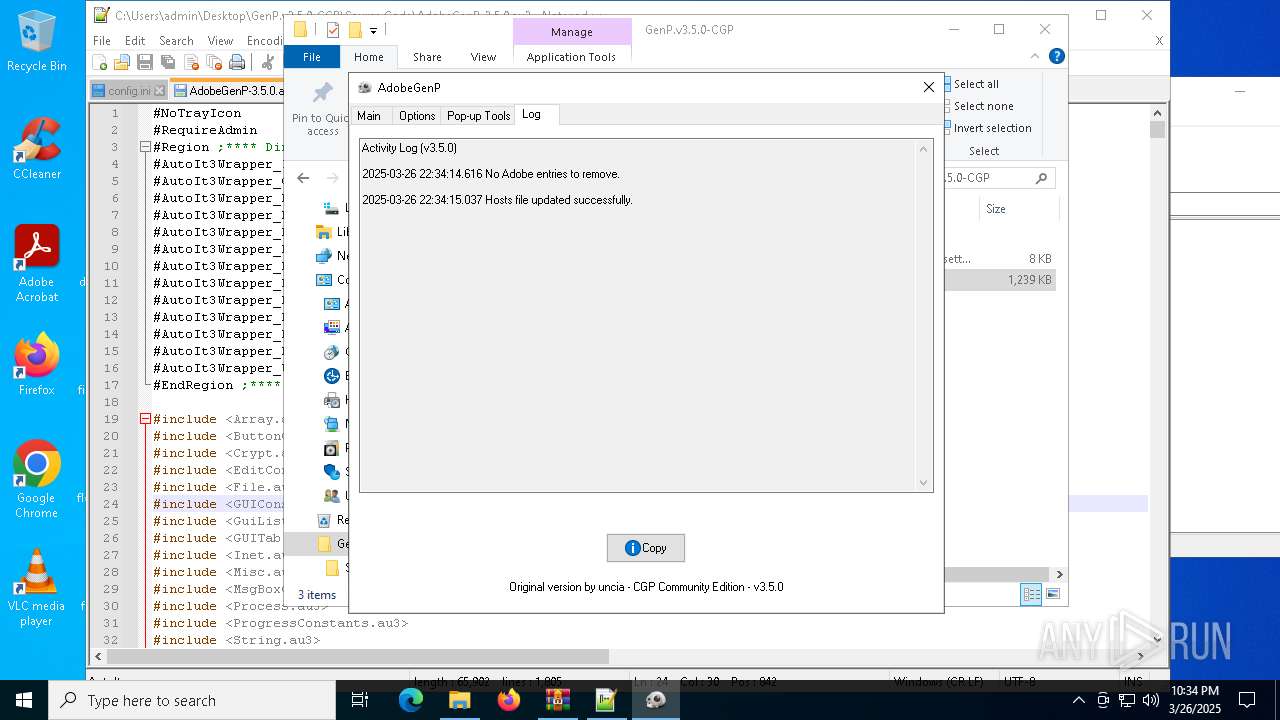
Modifies hosts file to alter network resolution
- GenP 3.5.0.exe (PID: 7200)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6620)
The sample compiled with english language support
- WinRAR.exe (PID: 6620)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 8012)
- BackgroundTransferHost.exe (PID: 5608)
- BackgroundTransferHost.exe (PID: 5376)
- BackgroundTransferHost.exe (PID: 7152)
- BackgroundTransferHost.exe (PID: 7860)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 7152)
- slui.exe (PID: 4892)
- GenP 3.5.0.exe (PID: 7200)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 7152)
- GenP 3.5.0.exe (PID: 7200)
Manual execution by a user
- notepad++.exe (PID: 7976)
- notepad++.exe (PID: 728)
- Acrobat.exe (PID: 7988)
- mspaint.exe (PID: 2416)
- GenP 3.5.0.exe (PID: 2104)
- GenP 3.5.0.exe (PID: 7200)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 7152)
- slui.exe (PID: 7280)
- slui.exe (PID: 4892)
- GenP 3.5.0.exe (PID: 7200)
Reads the computer name
- ShellExperienceHost.exe (PID: 7596)
- GenP 3.5.0.exe (PID: 7200)
Checks supported languages
- ShellExperienceHost.exe (PID: 7596)
- GenP 3.5.0.exe (PID: 7200)
Application launched itself
- Acrobat.exe (PID: 7988)
- AcroCEF.exe (PID: 4008)
Reads mouse settings
- GenP 3.5.0.exe (PID: 7200)
Create files in a temporary directory
- GenP 3.5.0.exe (PID: 7200)
Reads the machine GUID from the registry
- GenP 3.5.0.exe (PID: 7200)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:02:05 21:08:38 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | GenP.v3.5.0-CGP/ |
Total processes
168
Monitored processes
26
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=disabled --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2776 --field-trial-handle=1612,i,9889157825286202544,14998914645617567717,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
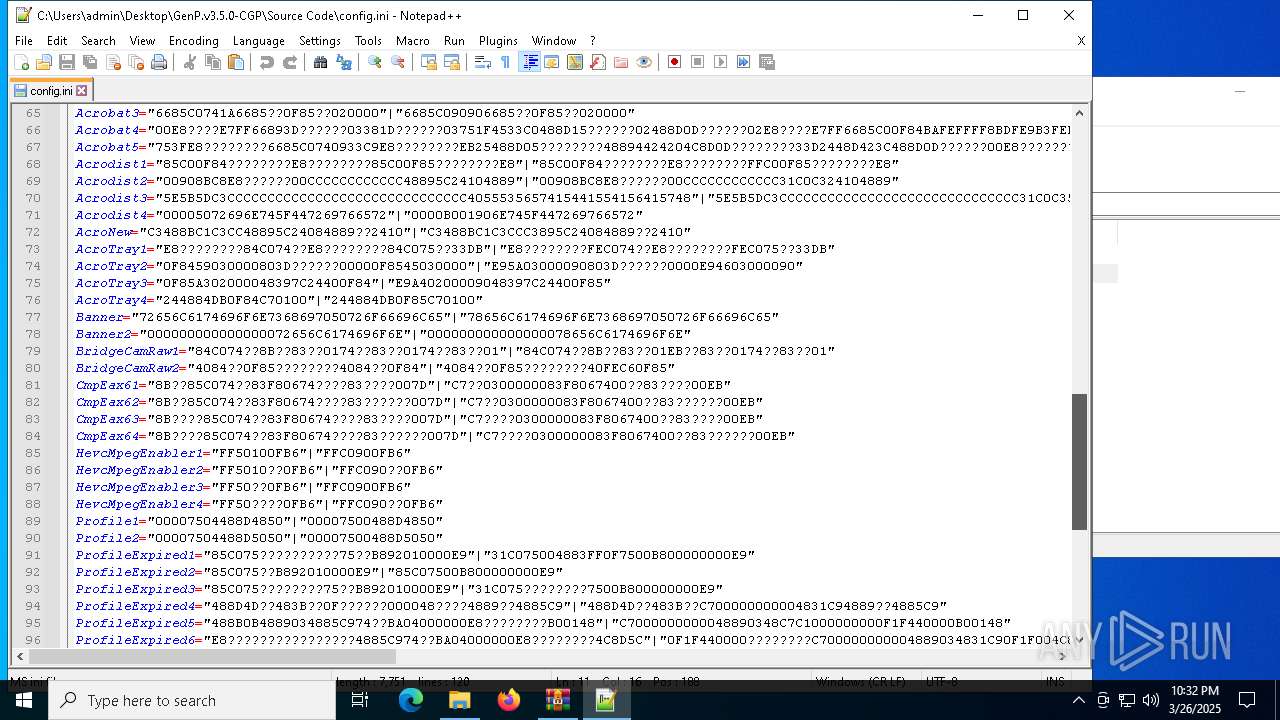
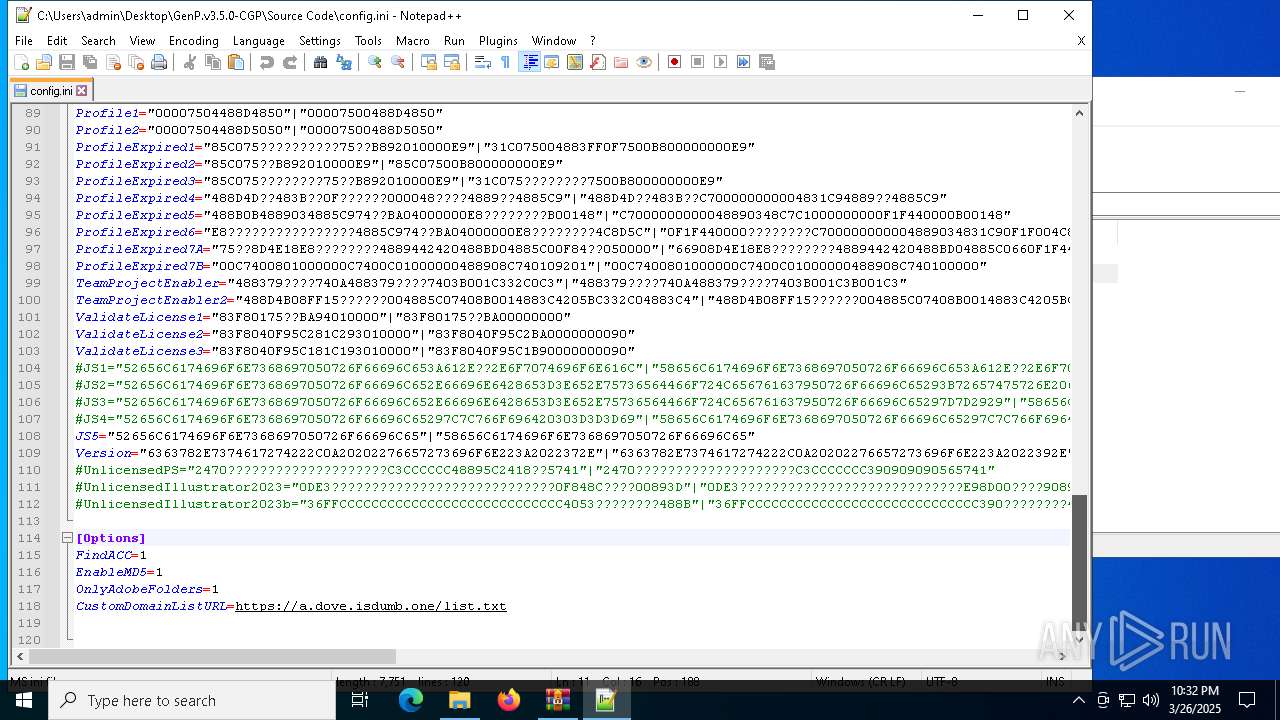
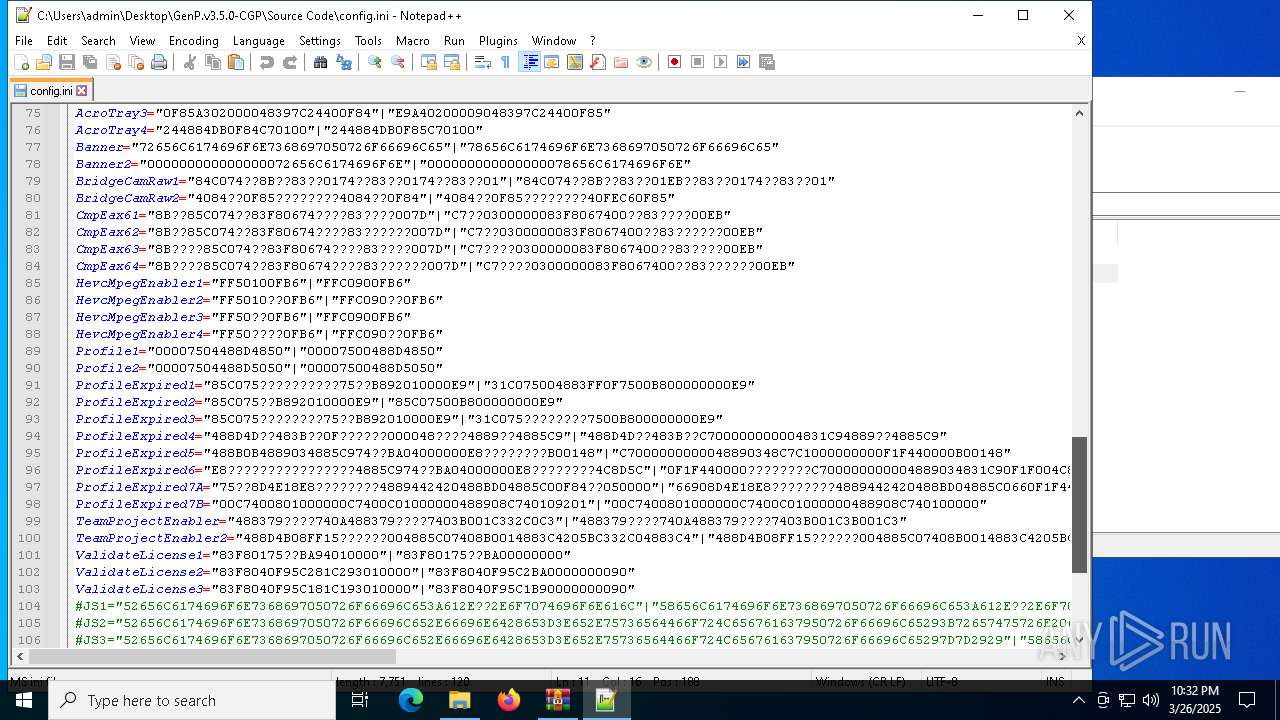
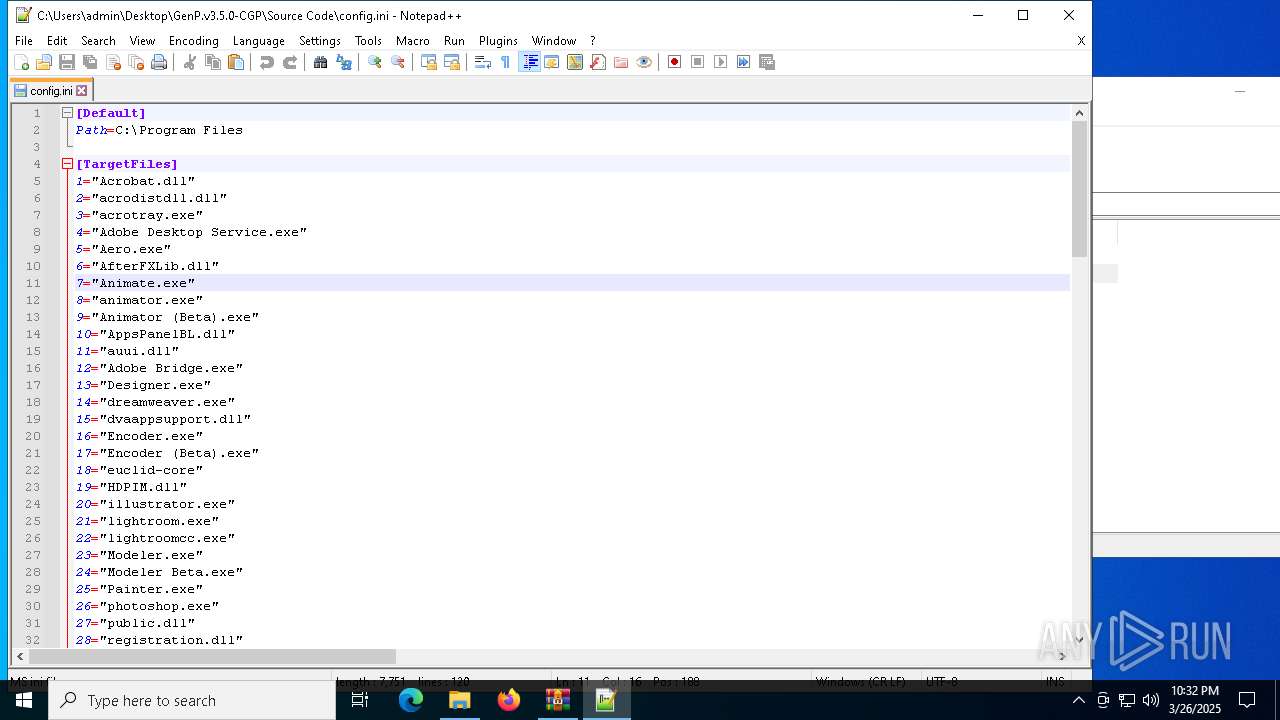
| 728 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\GenP.v3.5.0-CGP\Source Code\AdobeGenP-3.5.0.au3" | C:\Program Files\Notepad++\notepad++.exe | — | explorer.exe | |||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 1348 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Exit code: 1 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2104 | "C:\Users\admin\Desktop\GenP.v3.5.0-CGP\GenP 3.5.0.exe" | C:\Users\admin\Desktop\GenP.v3.5.0-CGP\GenP 3.5.0.exe | — | explorer.exe | |||||||||||
User: admin Company: AdobeGenp Integrity Level: MEDIUM Description: Adobe Generic Patcher Exit code: 3221226540 Version: 3.5.0.0 Modules
| |||||||||||||||
| 2416 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\GenP.v3.5.0-CGP\Source Code\Skull.ico" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4008 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 4892 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5344 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=1788 --field-trial-handle=1612,i,9889157825286202544,14998914645617567717,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 5376 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5608 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 904
Read events
16 686
Write events
205
Delete events
13
Modification events
| (PID) Process: | (6620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\GenP.v3.5.0-CGP.zip | |||
| (PID) Process: | (6620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (8012) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (8012) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
3
Suspicious files
100
Text files
22
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7152 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\f7a0ff47-2348-4c6a-a2ca-46d75808cd34.down_data | — | |
MD5:— | SHA256:— | |||
| 7152 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:FA6095A37891A45F775E9A21DDAA863A | SHA256:9D7DF71A8C9E60562B699363C26409853C04962CEA5482CD56835B600A7CFA7C | |||
| 6620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6620.9726\GenP.v3.5.0-CGP\Source Code\Skull.ico | image | |
MD5:C37B537E533890560FE52664A7F1C1A0 | SHA256:1532311559D17CF7ECC0BE72FB47EC7D0EA086C414E2280566E0803133FD1D50 | |||
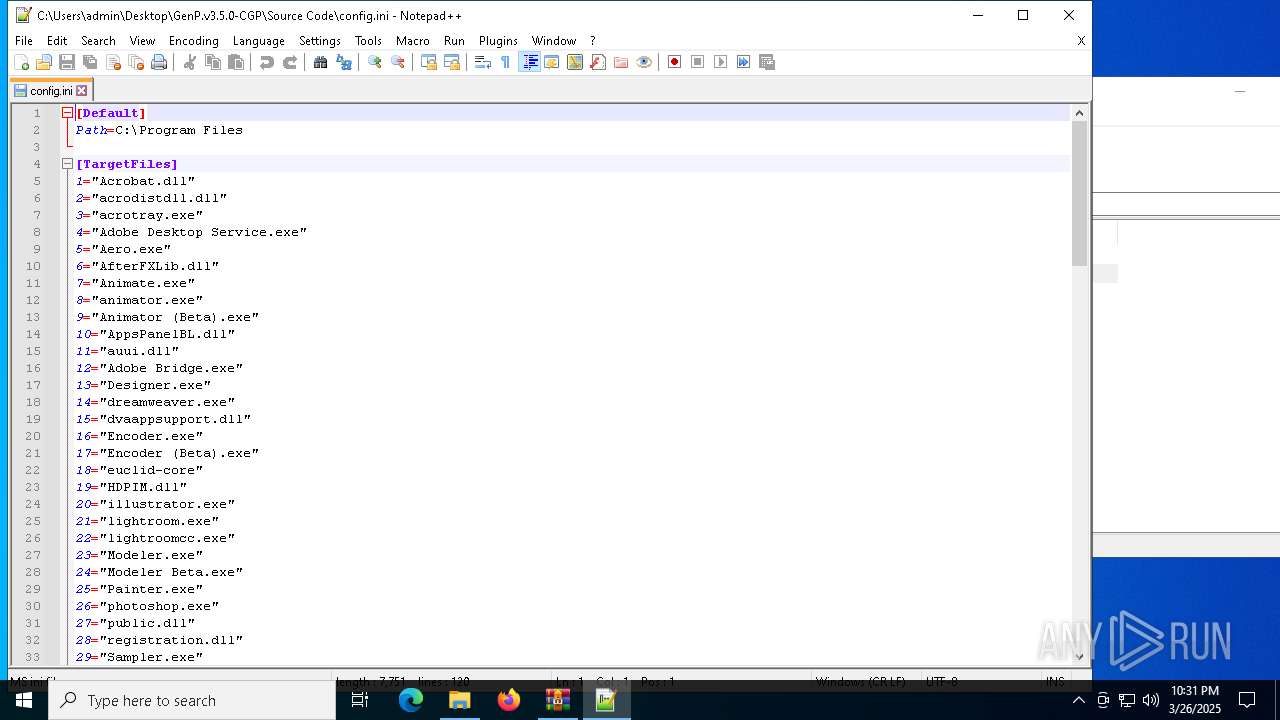
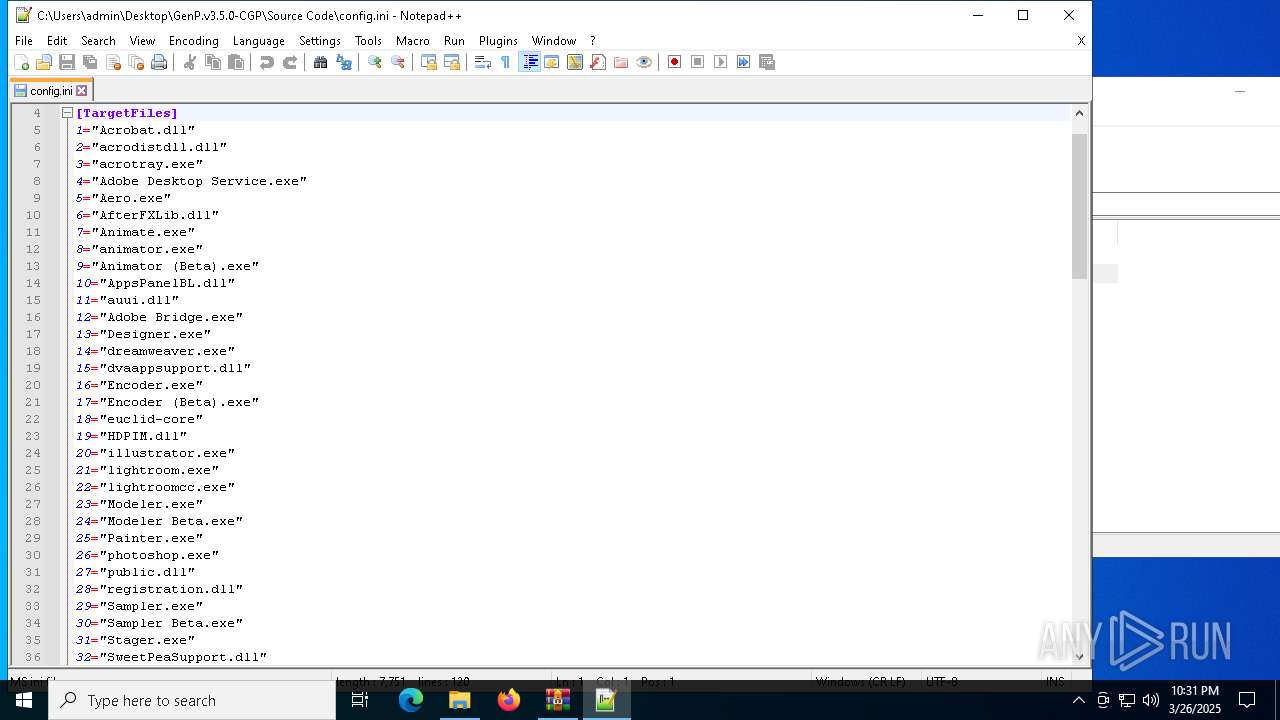
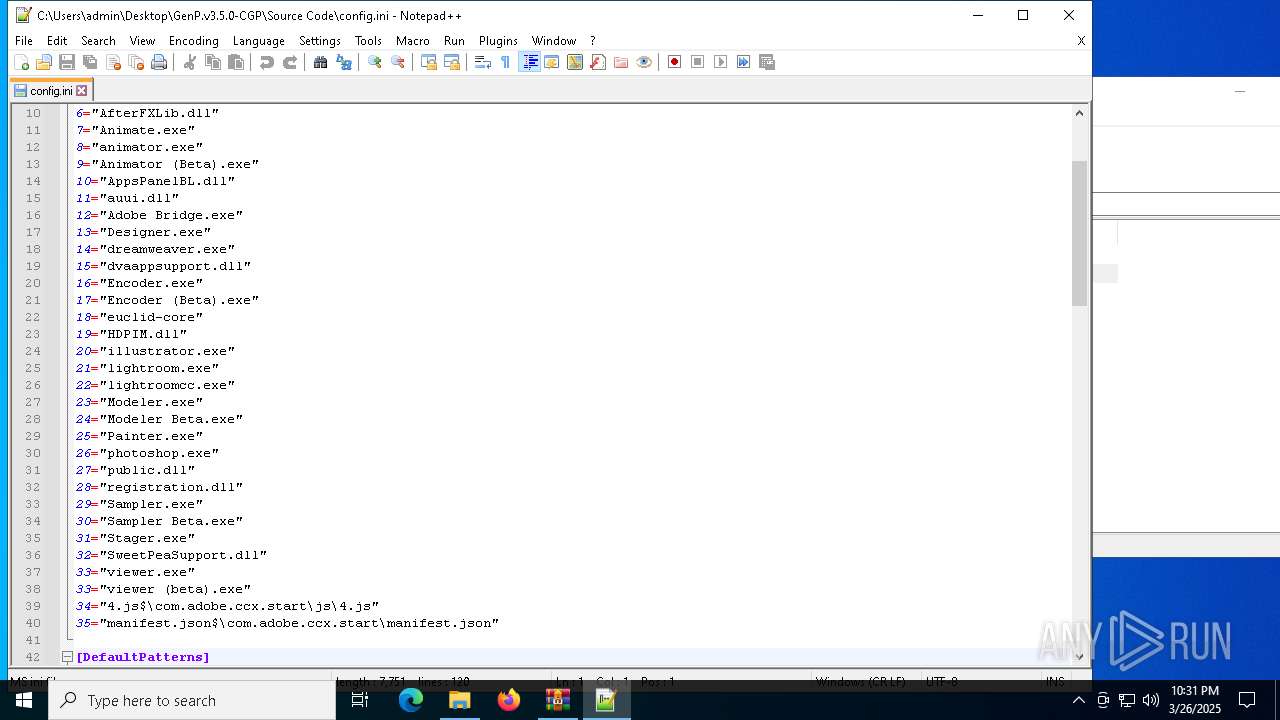
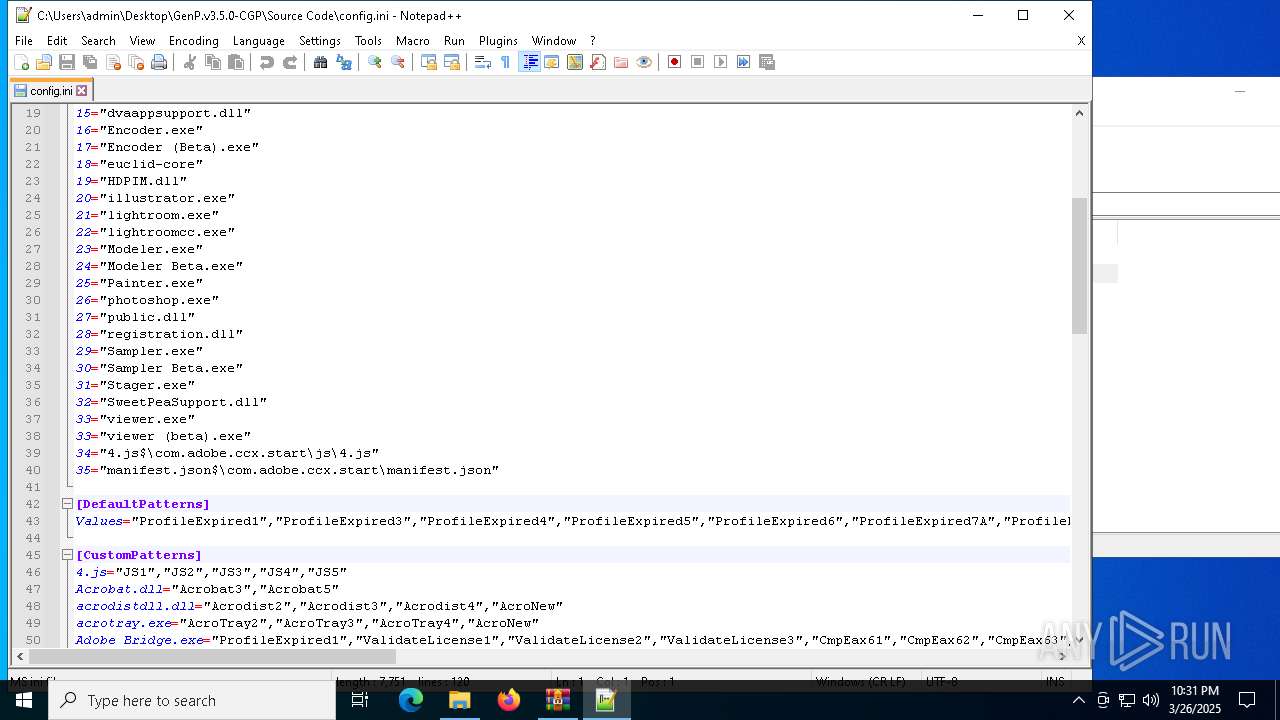
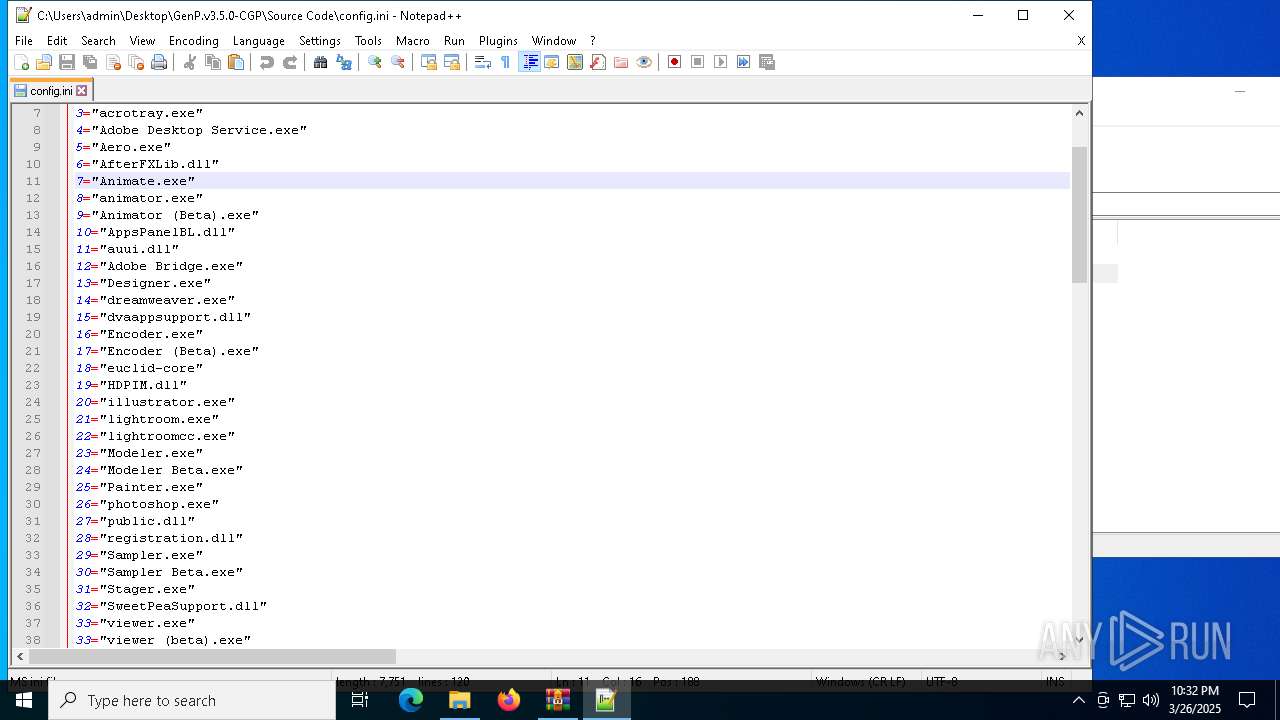
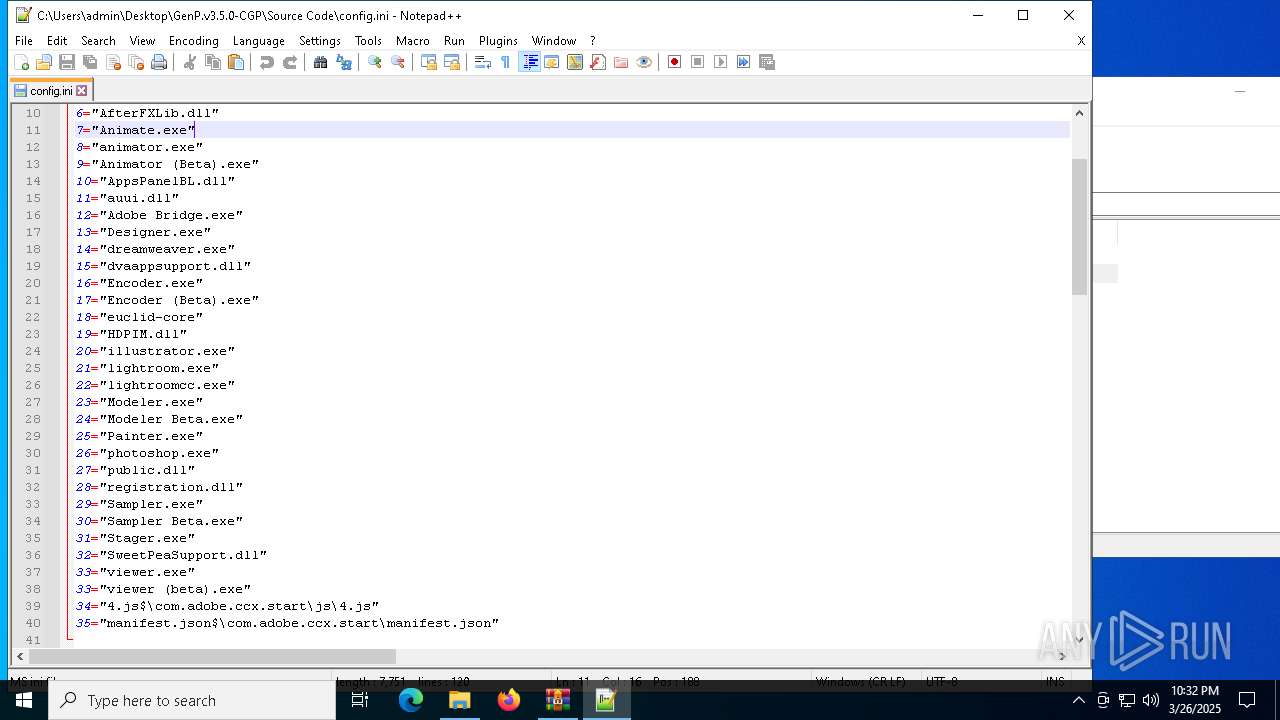
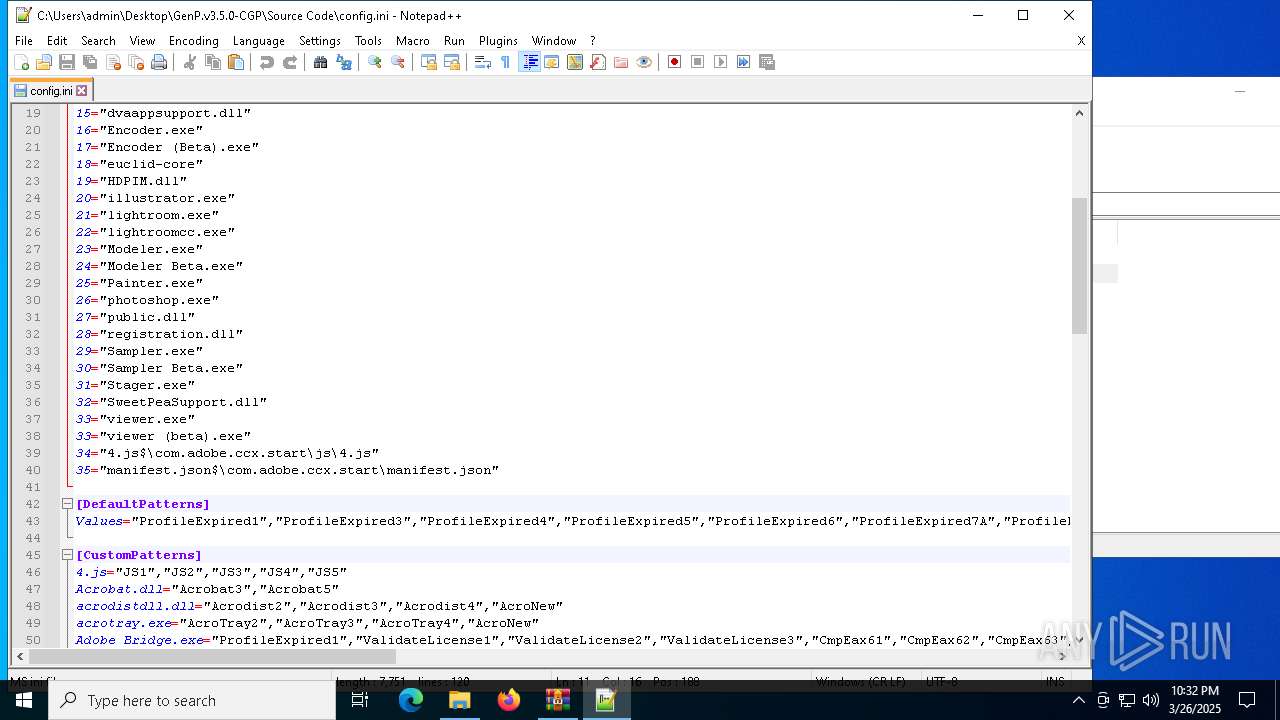
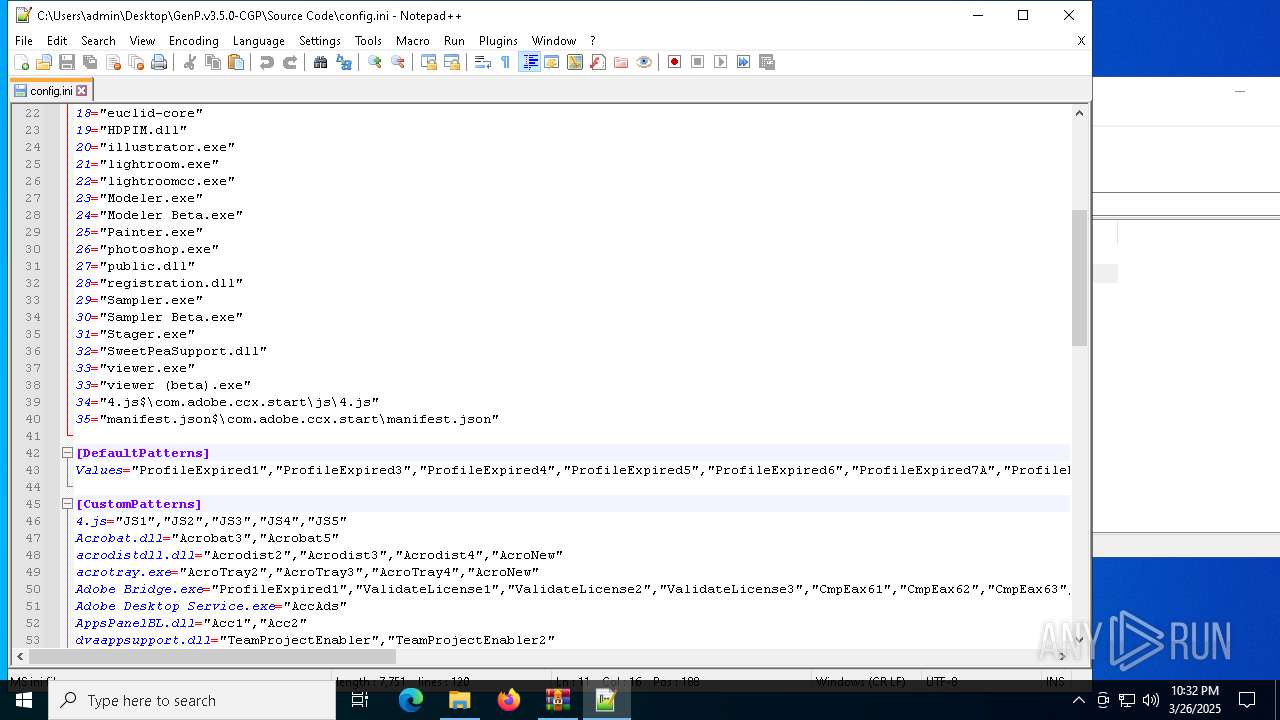
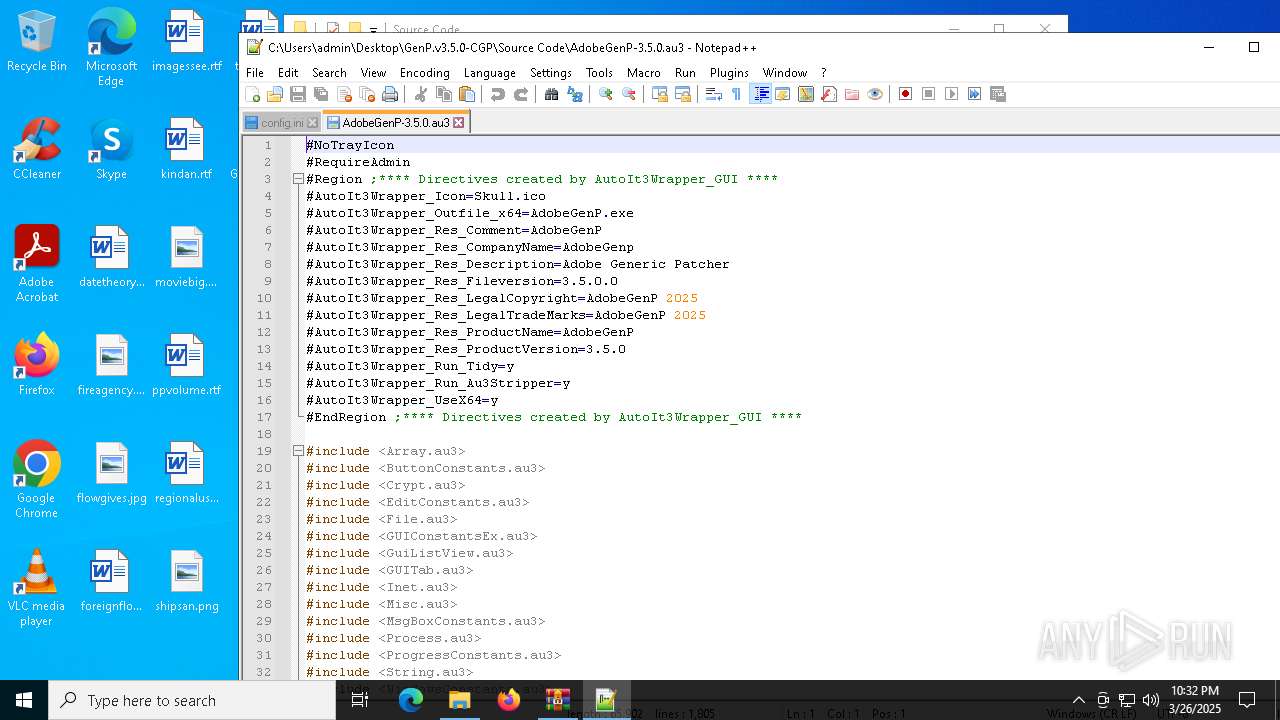
| 6620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6620.9726\GenP.v3.5.0-CGP\Source Code\AdobeGenP-3.5.0.au3 | text | |
MD5:4607B85345742B5F6913A88802C138D7 | SHA256:BDF51333C80779FBC4C71A3194AA28C6D756808BA7B50AEE868FB58BFCB94C19 | |||
| 7152 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\f7a0ff47-2348-4c6a-a2ca-46d75808cd34.8c9ae897-240b-472c-b331-7a85fd71d589.down_meta | binary | |
MD5:CCDD13E01539CE3EC642D94737AC80E7 | SHA256:C20A13CD9FA4B8A34965BCD454ABE69CC65367060F7CA27C77C3EEE04B1FE70F | |||
| 7152 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\15e03727-2e16-4a29-af8c-a1ec564e5e1d.up_meta_secure | binary | |
MD5:EC496BEB2AD19377BA0218DA430F0E06 | SHA256:90B531E27A6B914E4CD147977866C5C14BA2E7E9456BF98BEFE5E613724E3E77 | |||
| 7976 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\stylers.xml | xml | |
MD5:312281C4126FA897EF21A7E8CCB8D495 | SHA256:53B4BE3ED1CFD712E53542B30CFE30C5DB35CC48BE7C57727DFEC26C9E882E90 | |||
| 7152 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\15e03727-2e16-4a29-af8c-a1ec564e5e1d.8c9ae897-240b-472c-b331-7a85fd71d589.down_meta | binary | |
MD5:CCDD13E01539CE3EC642D94737AC80E7 | SHA256:C20A13CD9FA4B8A34965BCD454ABE69CC65367060F7CA27C77C3EEE04B1FE70F | |||
| 7976 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:FE22EC5755BC98988F9656F73B2E6FB8 | SHA256:F972C425CE176E960F6347F1CA2F64A8CE2B95A375C33A03E57538052BA0624D | |||
| 7976 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\plugins\config\converter.ini | text | |
MD5:F70F579156C93B097E656CABA577A5C9 | SHA256:B926498A19CA95DC28964B7336E5847107DD3C0F52C85195C135D9DD6CA402D4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
29
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7336 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7152 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7996 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7996 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7200 | GenP 3.5.0.exe | GET | 200 | 216.58.206.35:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
7200 | GenP 3.5.0.exe | GET | 200 | 216.58.206.35:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
7336 | backgroundTaskHost.exe | 20.199.58.43:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7336 | backgroundTaskHost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
7152 | BackgroundTransferHost.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
7152 | BackgroundTransferHost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |