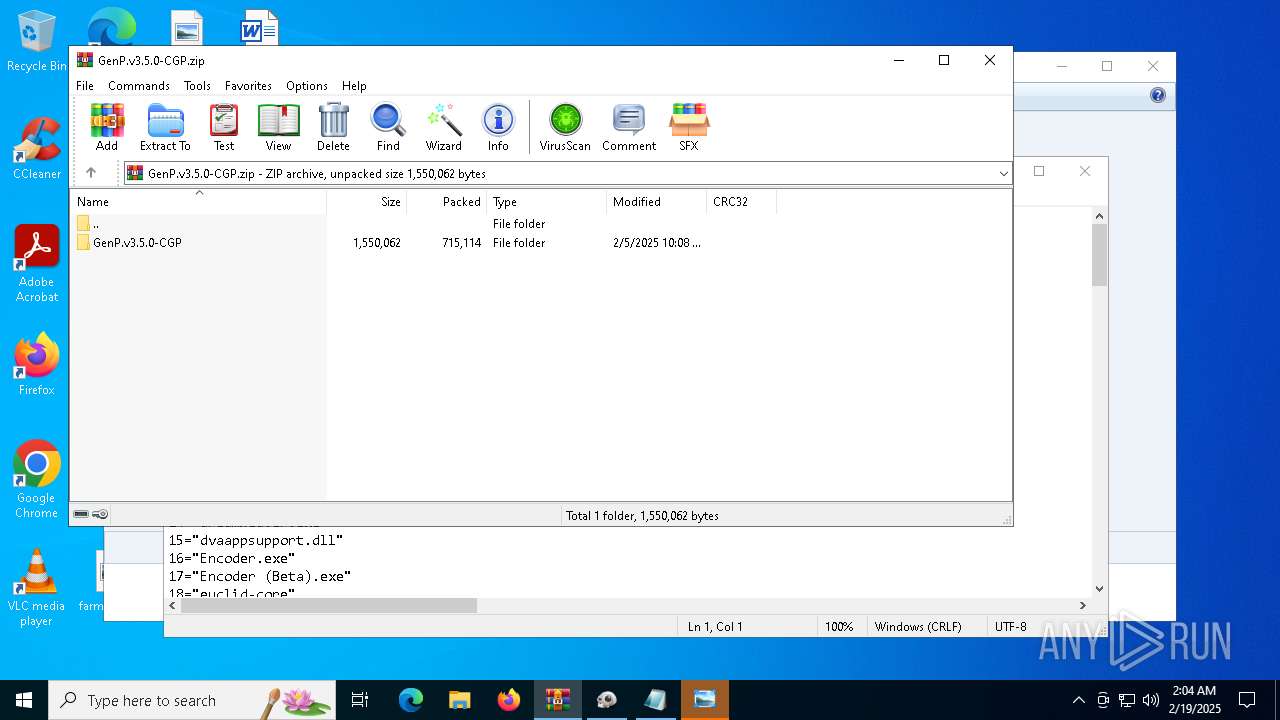
| File name: | GenP.v3.5.0-CGP.zip |
| Full analysis: | https://app.any.run/tasks/d2356c91-7f92-4820-9aad-b9c7b7ba8421 |
| Verdict: | Malicious activity |
| Analysis date: | February 19, 2025, 02:04:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 44A3093AFEF9BAE5C0B5856C36692AF7 |
| SHA1: | D5712662329A6E9FE3977574FA81490C3BFDCCAA |
| SHA256: | CA0AA3669485C241AF5166EDEA379B2A5474452B0D3F0951E0D5DB1CCB5616F4 |
| SSDEEP: | 24576:MEnzxX446LUlua9orG9cv3kuWdTBhv1Fmj2EmKXXVfnQ2AmiLtK5:MEnzxX446LUluU0G9cvkuWdTBhv1FmSO |
MALICIOUS
No malicious indicators.SUSPICIOUS
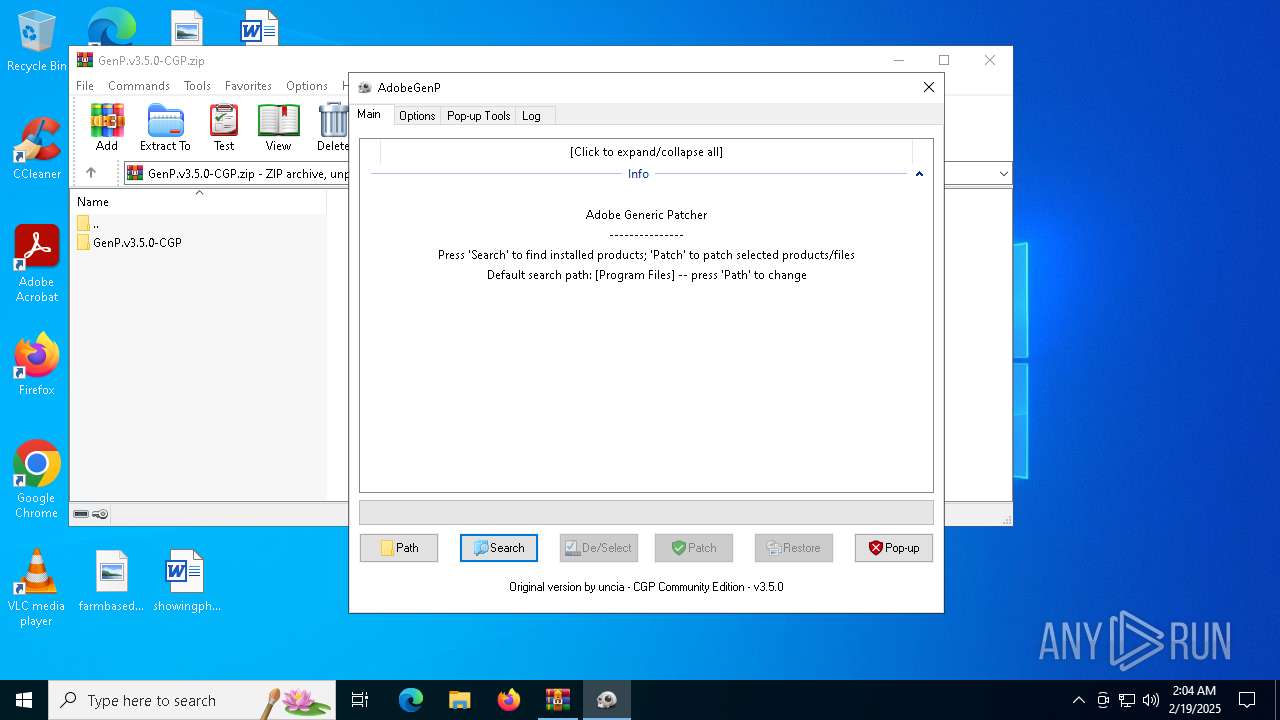
ADOBEGENP mutex has been found
- GenP 3.5.0.exe (PID: 2144)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4708)
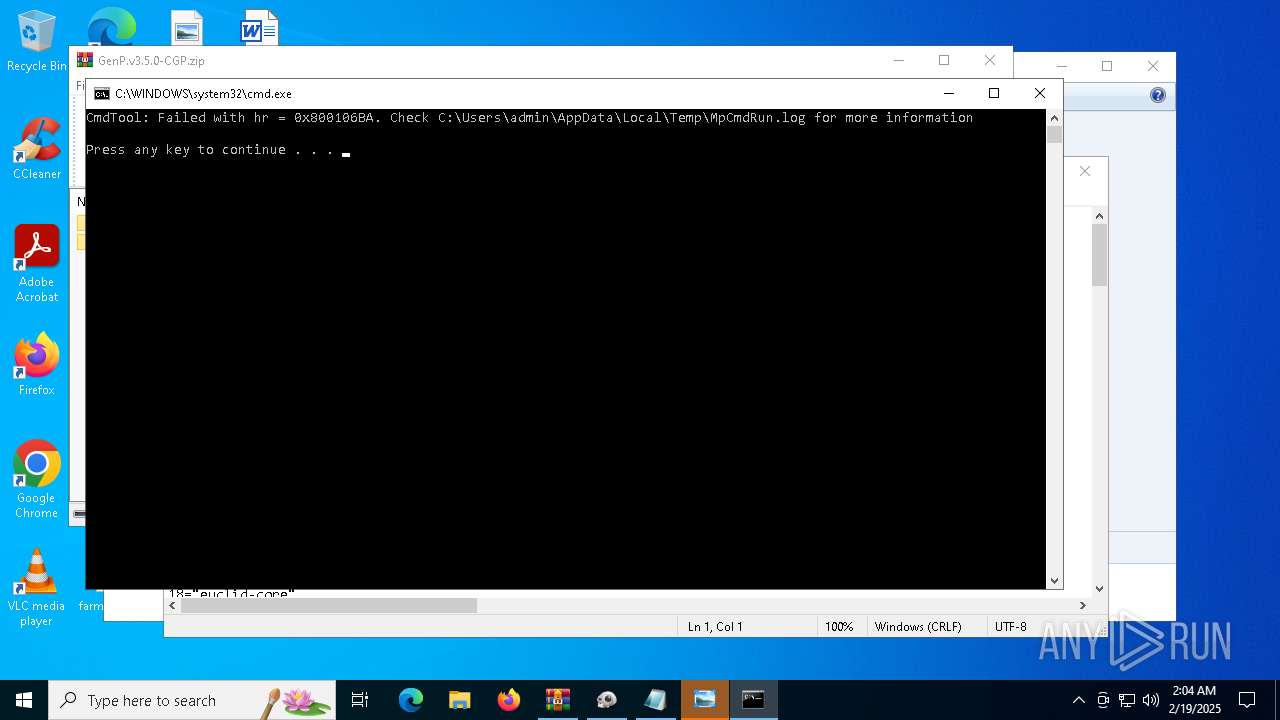
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 4708)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 4708)
There is functionality for taking screenshot (YARA)
- GenP 3.5.0.exe (PID: 2144)
INFO
Manual execution by a user
- GenP 3.5.0.exe (PID: 3420)
- GenP 3.5.0.exe (PID: 2144)
- notepad.exe (PID: 4672)
- OpenWith.exe (PID: 5244)
- rundll32.exe (PID: 4972)
Reads mouse settings
- GenP 3.5.0.exe (PID: 2144)
The sample compiled with english language support
- WinRAR.exe (PID: 4708)
Checks supported languages
- GenP 3.5.0.exe (PID: 2144)
- MpCmdRun.exe (PID: 5740)
Reads the computer name
- GenP 3.5.0.exe (PID: 2144)
- MpCmdRun.exe (PID: 5740)
Create files in a temporary directory
- GenP 3.5.0.exe (PID: 2144)
- MpCmdRun.exe (PID: 5740)
Reads security settings of Internet Explorer
- notepad.exe (PID: 4672)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 5244)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4708)
The process uses AutoIt
- GenP 3.5.0.exe (PID: 2144)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:02:05 21:08:38 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | GenP.v3.5.0-CGP/ |
Total processes
127
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 556 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2144 | "C:\Users\admin\Desktop\GenP 3.5.0.exe" | C:\Users\admin\Desktop\GenP 3.5.0.exe | explorer.exe | ||||||||||||
User: admin Company: AdobeGenp Integrity Level: HIGH Description: Adobe Generic Patcher Version: 3.5.0.0 Modules
| |||||||||||||||
| 3420 | "C:\Users\admin\Desktop\GenP 3.5.0.exe" | C:\Users\admin\Desktop\GenP 3.5.0.exe | — | explorer.exe | |||||||||||
User: admin Company: AdobeGenp Integrity Level: MEDIUM Description: Adobe Generic Patcher Exit code: 3221226540 Version: 3.5.0.0 Modules
| |||||||||||||||
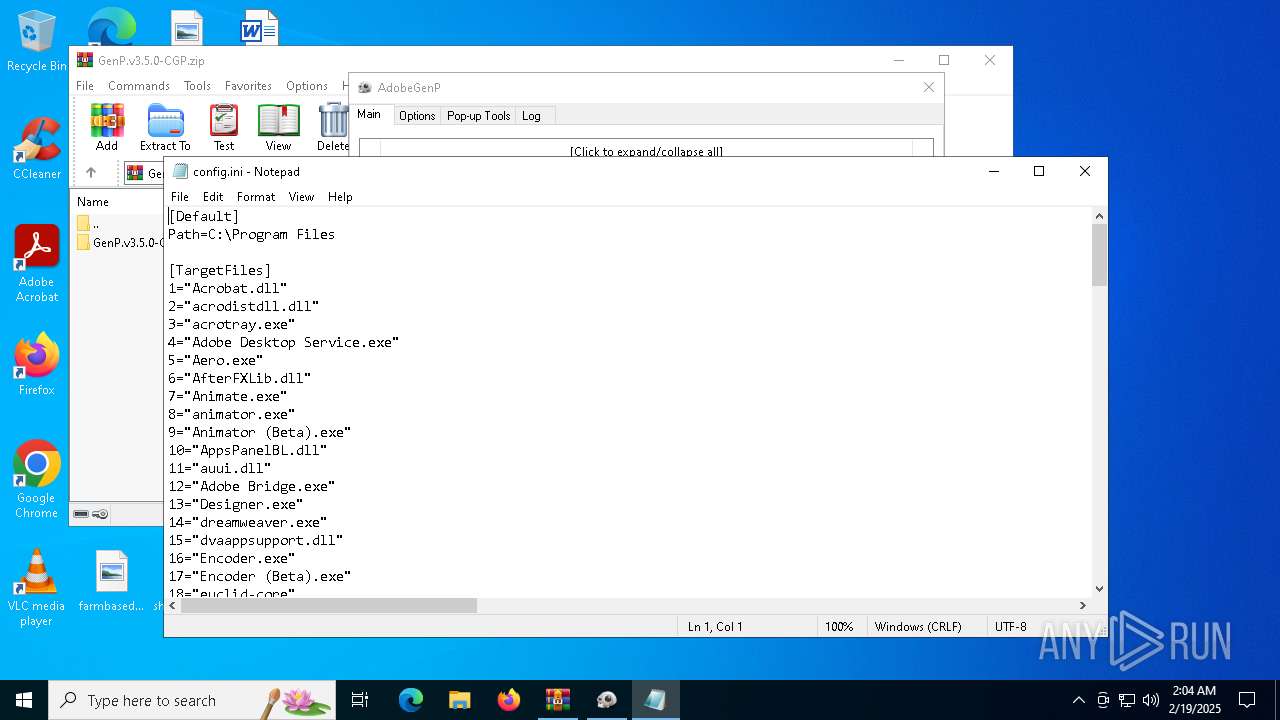
| 4672 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\config.ini | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4708 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\GenP.v3.5.0-CGP.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4972 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\Skull.ico | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
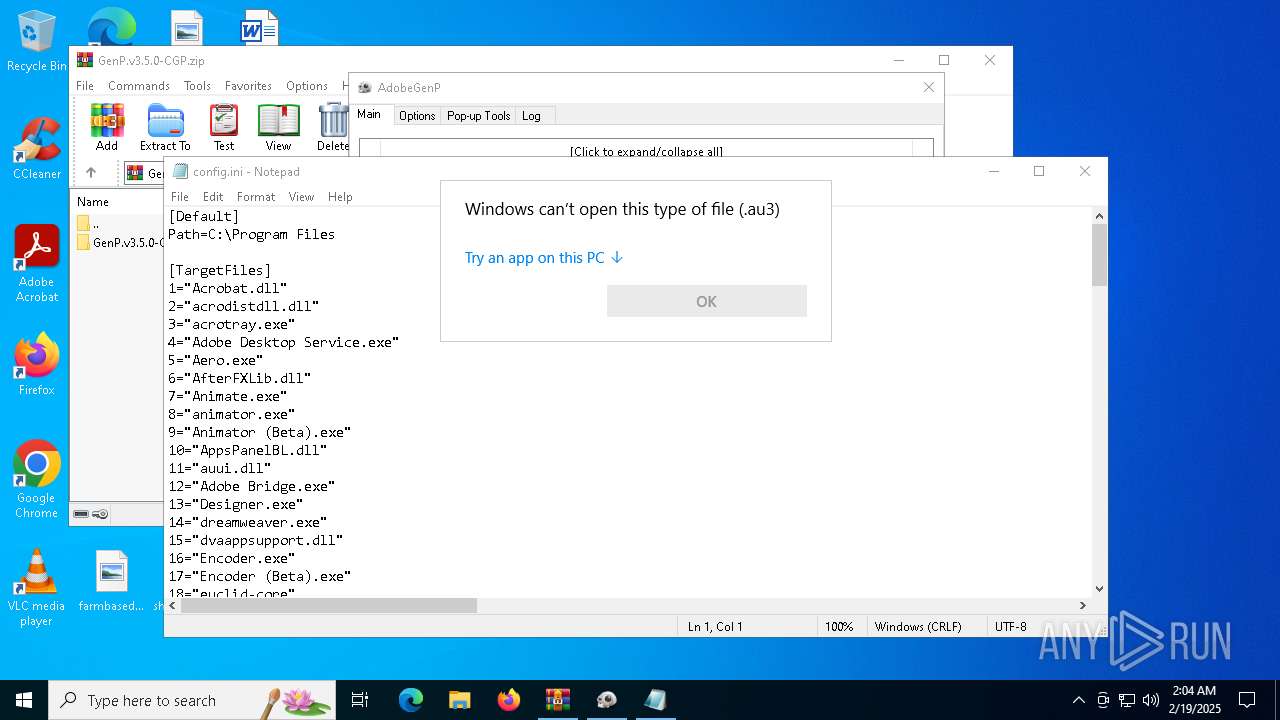
| 5244 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\AdobeGenP-3.5.0.au3 | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5740 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR4708.48496" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5864 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR4708.48496\Rar$Scan14652.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 856
Read events
2 847
Write events
9
Delete events
0
Modification events
| (PID) Process: | (4708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\GenP.v3.5.0-CGP.zip | |||
| (PID) Process: | (4708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
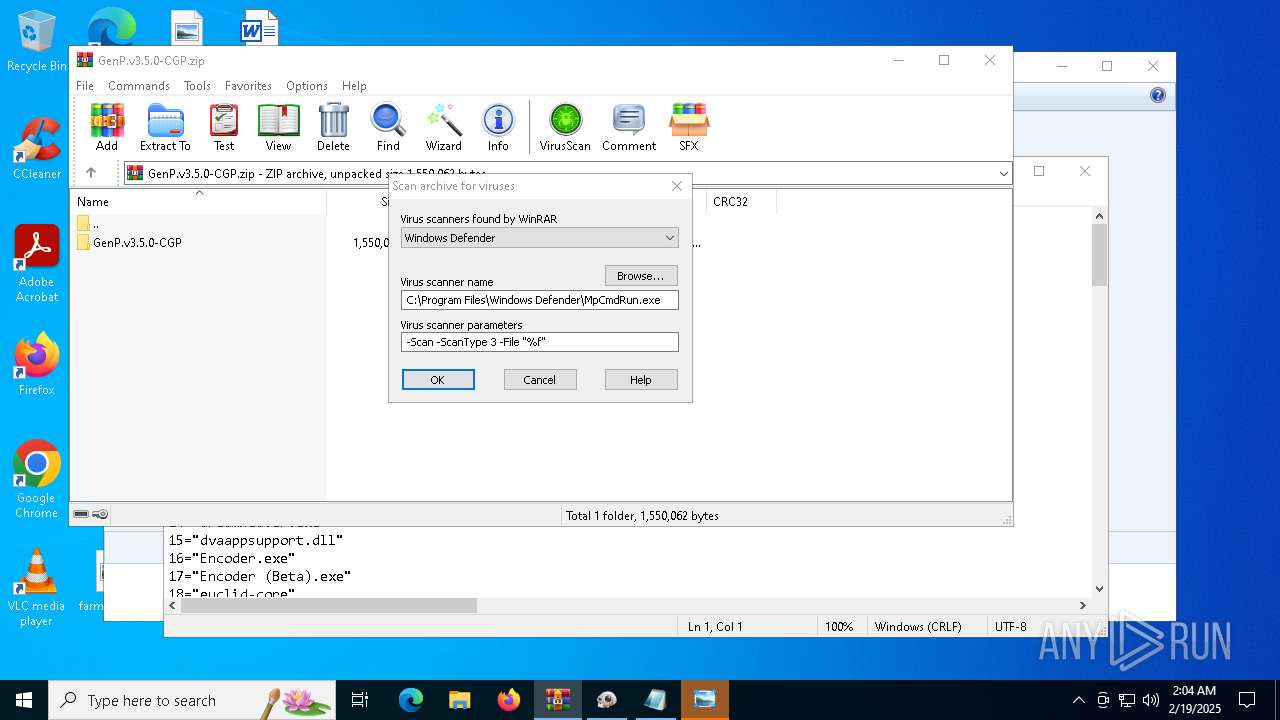
| (PID) Process: | (4708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
3
Suspicious files
2
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2144 | GenP 3.5.0.exe | C:\Users\admin\AppData\Local\Temp\aut740A.tmp | binary | |
MD5:4858736902FBC470F96AAEE483EFDFD2 | SHA256:D3569ED2DFD800B44D2F11303D522EDFB2BD1E094A7EC6E081913A552FB289E5 | |||
| 4708 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4708.48496\GenP.v3.5.0-CGP.zip\GenP.v3.5.0-CGP\GenP 3.5.0.exe | executable | |
MD5:362A9B5AB6C70AFF8C686FD35602E999 | SHA256:079E33038561CB759CA9EEBCB74C97C435593469509DFC90CC07A4CA80A2CCDC | |||
| 4708 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4708.48496\GenP.v3.5.0-CGP.zip\GenP.v3.5.0-CGP\Source Code\config.ini | text | |
MD5:3D6ACE120BB21EF7661F9BAA3A828BA0 | SHA256:0BC155DC39DD420893CE4228EAD4066D3C54A5CFE09C40AA3B6183FC0F4D68E6 | |||
| 2144 | GenP 3.5.0.exe | C:\Users\admin\Desktop\config.ini | text | |
MD5:3D6ACE120BB21EF7661F9BAA3A828BA0 | SHA256:0BC155DC39DD420893CE4228EAD4066D3C54A5CFE09C40AA3B6183FC0F4D68E6 | |||
| 4708 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4708.48496\GenP.v3.5.0-CGP.zip\GenP.v3.5.0-CGP\Source Code\AdobeGenP-3.5.0.au3 | text | |
MD5:4607B85345742B5F6913A88802C138D7 | SHA256:BDF51333C80779FBC4C71A3194AA28C6D756808BA7B50AEE868FB58BFCB94C19 | |||
| 4708 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4708.48496\GenP.v3.5.0-CGP.zip\GenP.v3.5.0-CGP\Source Code\Skull.ico | image | |
MD5:C37B537E533890560FE52664A7F1C1A0 | SHA256:1532311559D17CF7ECC0BE72FB47EC7D0EA086C414E2280566E0803133FD1D50 | |||
| 4708 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4708.48496\Rar$Scan14652.bat | text | |
MD5:83C013F4E4550F2DD0A25B5C0B95E020 | SHA256:C0C1A3D7AD5E34E5118CC31F0F9C697B334116B9339D9B614EEC6A4073EADAC7 | |||
| 5740 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | binary | |
MD5:C8C98229AAA259FFDBB16F89077B3865 | SHA256:B2BCB7EF2035F34A94CBA9CBAF2D96A6EABF049D39CC794AE024FB967590A25C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
19
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3984 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3984 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3984 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 92.123.104.32:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3984 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3984 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |