| download: | postsending-1.25.0.exe |
| Full analysis: | https://app.any.run/tasks/1154b50b-589a-431b-b8a5-5c2036e4f8e8 |
| Verdict: | Malicious activity |
| Analysis date: | April 14, 2019, 15:40:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 51F42F7A5556DE606B8A13DF4E6AEB4C |
| SHA1: | 1DFD7E84BC0228D9BA9D76AA85473DCF3680B6F4 |
| SHA256: | CA0627A2BD764BA9AF680D0D1F2A66B61BB580E9888056835D195172C259F34D |
| SSDEEP: | 196608:3Wr71tcAVB5vG5p1g4H/JAkmy+oUoffzgz225yLQsO9:3Wlt9Ip19/JAvQf8ayyLM9 |
MALICIOUS
Loads dropped or rewritten executable
- postsending-1.25.0.exe (PID: 3740)
- postsending.exe (PID: 2888)
- svchost.exe (PID: 848)
Application was dropped or rewritten from another process
- postsending.exe (PID: 2888)
- vdjobman.dll (PID: 2612)
SUSPICIOUS
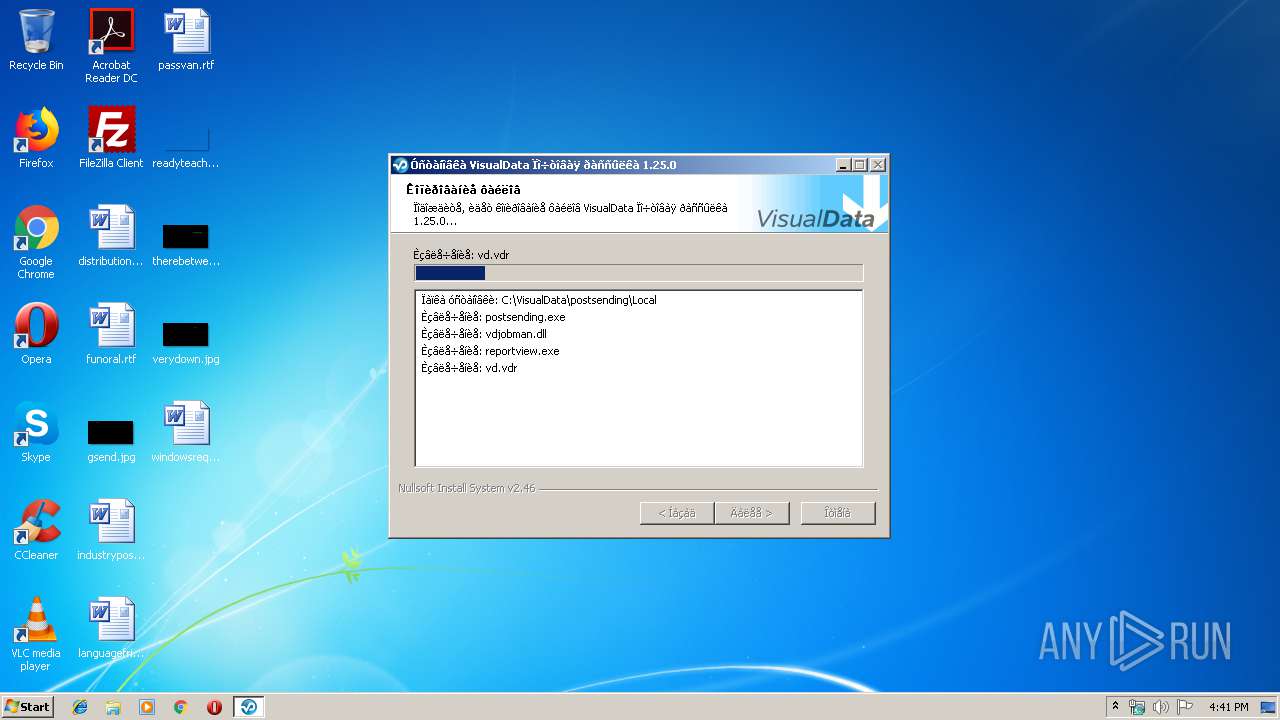
Creates files in the program directory
- postsending-1.25.0.exe (PID: 3740)
Executable content was dropped or overwritten
- postsending-1.25.0.exe (PID: 3740)
Starts application with an unusual extension
- postsending.exe (PID: 2888)
Creates a software uninstall entry
- postsending-1.25.0.exe (PID: 3740)
INFO
Dropped object may contain Bitcoin addresses
- postsending-1.25.0.exe (PID: 3740)
- postsending.exe (PID: 2888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:12:05 23:50:46+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 23552 |
| InitializedDataSize: | 119808 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x323c |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 05-Dec-2009 22:50:46 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 05-Dec-2009 22:50:46 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00005A5A | 0x00005C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.4177 |
.rdata | 0x00007000 | 0x00001190 | 0x00001200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.18163 |
.data | 0x00009000 | 0x0001AF98 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.70903 |
.ndata | 0x00024000 | 0x0000A000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x0002E000 | 0x00007858 | 0x00007A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.91231 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.10394 | 533 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 4.88159 | 4264 | UNKNOWN | English - United States | RT_ICON |
3 | 5.88009 | 2216 | UNKNOWN | English - United States | RT_ICON |
4 | 5.50206 | 1384 | UNKNOWN | English - United States | RT_ICON |
5 | 5.47465 | 1128 | UNKNOWN | English - United States | RT_ICON |
102 | 2.71813 | 180 | UNKNOWN | English - United States | RT_DIALOG |
103 | 2.63539 | 76 | UNKNOWN | English - United States | RT_GROUP_ICON |
104 | 2.70992 | 344 | UNKNOWN | English - United States | RT_DIALOG |
105 | 2.68372 | 512 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.91148 | 248 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
ole32.dll |
Total processes
38
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2612 | C:\VisualData\postsending\Local\vdjobman.dll 616 628 2888 | C:\VisualData\postsending\Local\vdjobman.dll | — | postsending.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
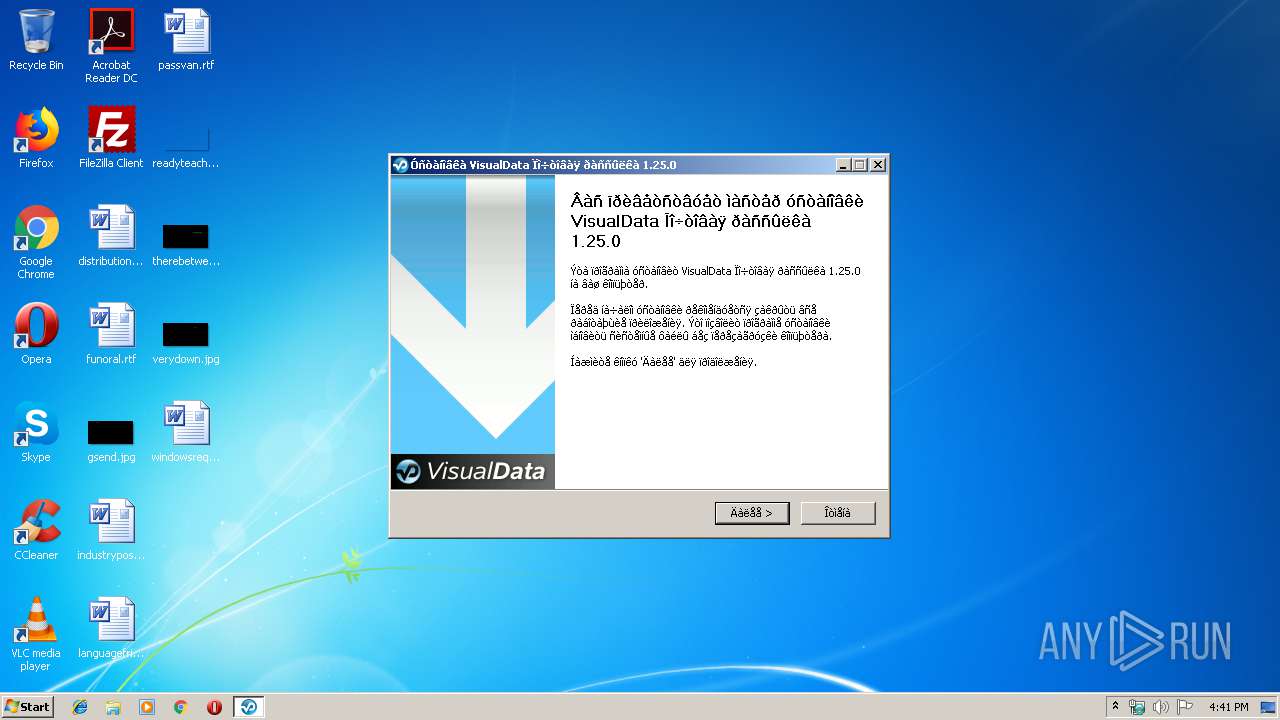
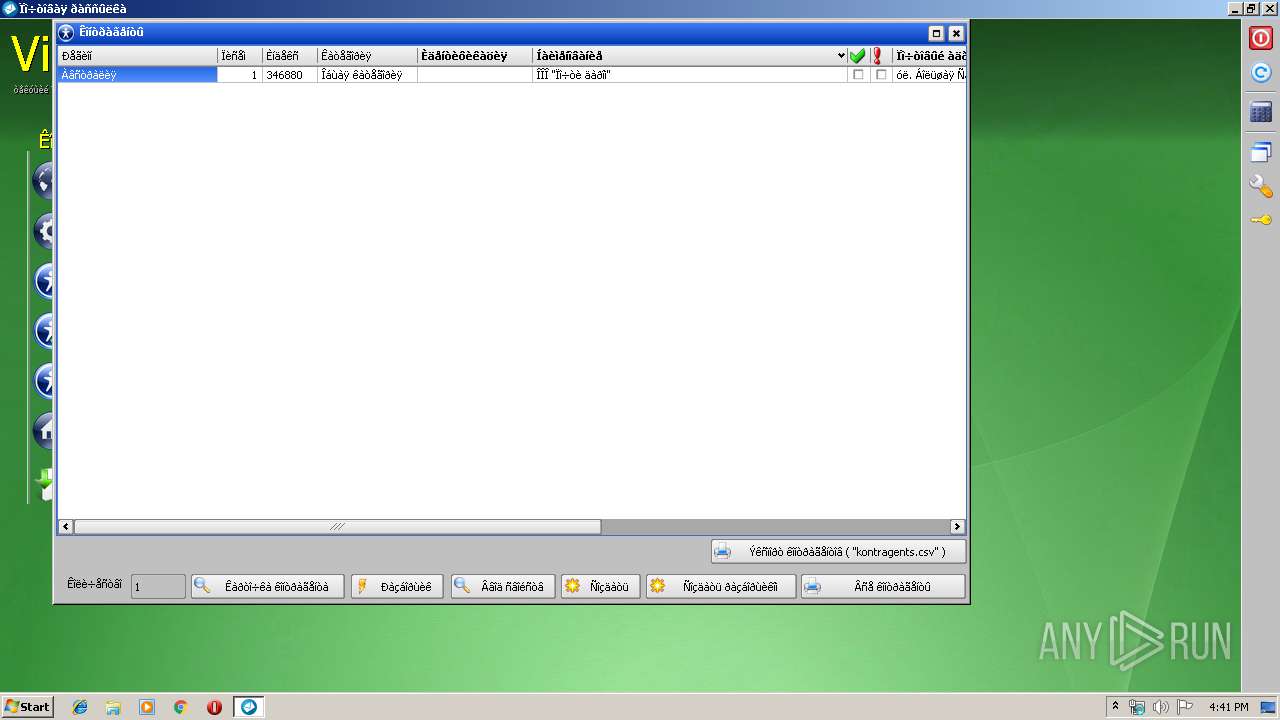
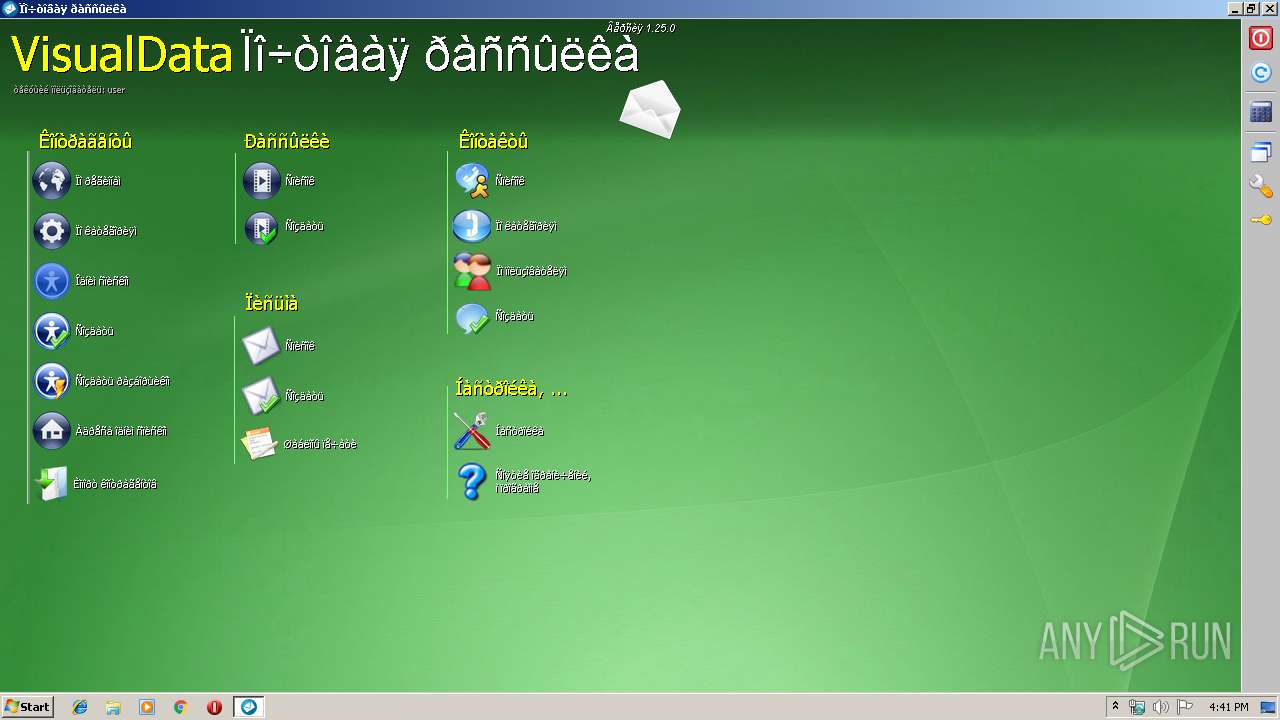
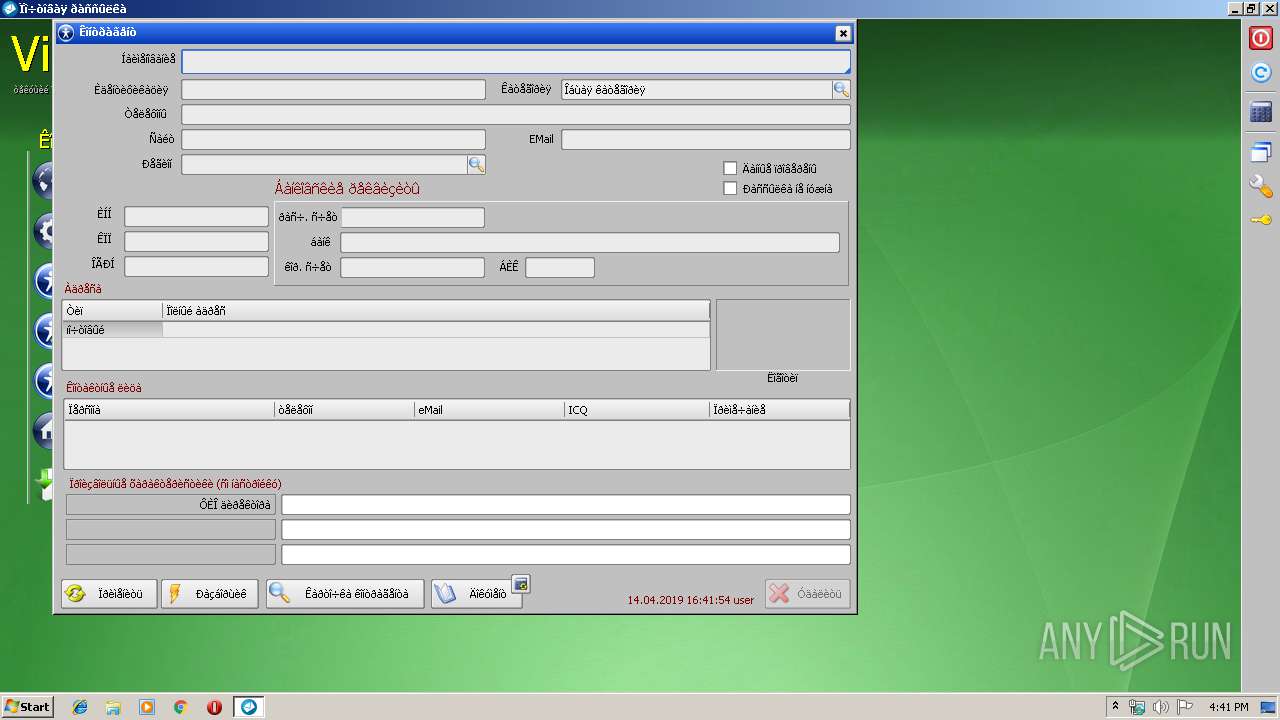
| 2888 | "C:\VisualData\postsending\Local\postsending.exe" | C:\VisualData\postsending\Local\postsending.exe | explorer.exe | ||||||||||||
User: admin Company: VisualData.ru Integrity Level: MEDIUM Description: Движок Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3232 | "C:\Users\admin\AppData\Local\Temp\postsending-1.25.0.exe" | C:\Users\admin\AppData\Local\Temp\postsending-1.25.0.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3740 | "C:\Users\admin\AppData\Local\Temp\postsending-1.25.0.exe" | C:\Users\admin\AppData\Local\Temp\postsending-1.25.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
406
Read events
394
Write events
12
Delete events
0
Modification events
| (PID) Process: | (3740) postsending-1.25.0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\postsending.exe |
| Operation: | write | Name: | |
Value: C:\VisualData\postsending\visualdata.exe | |||
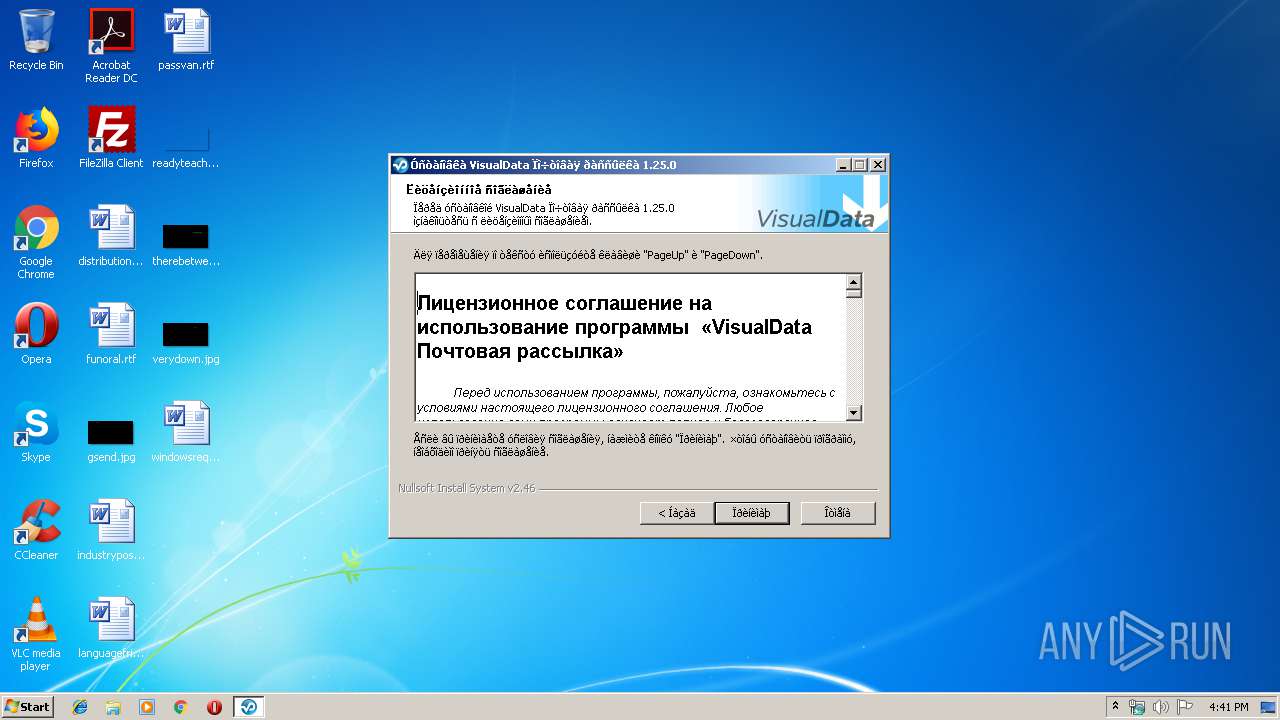
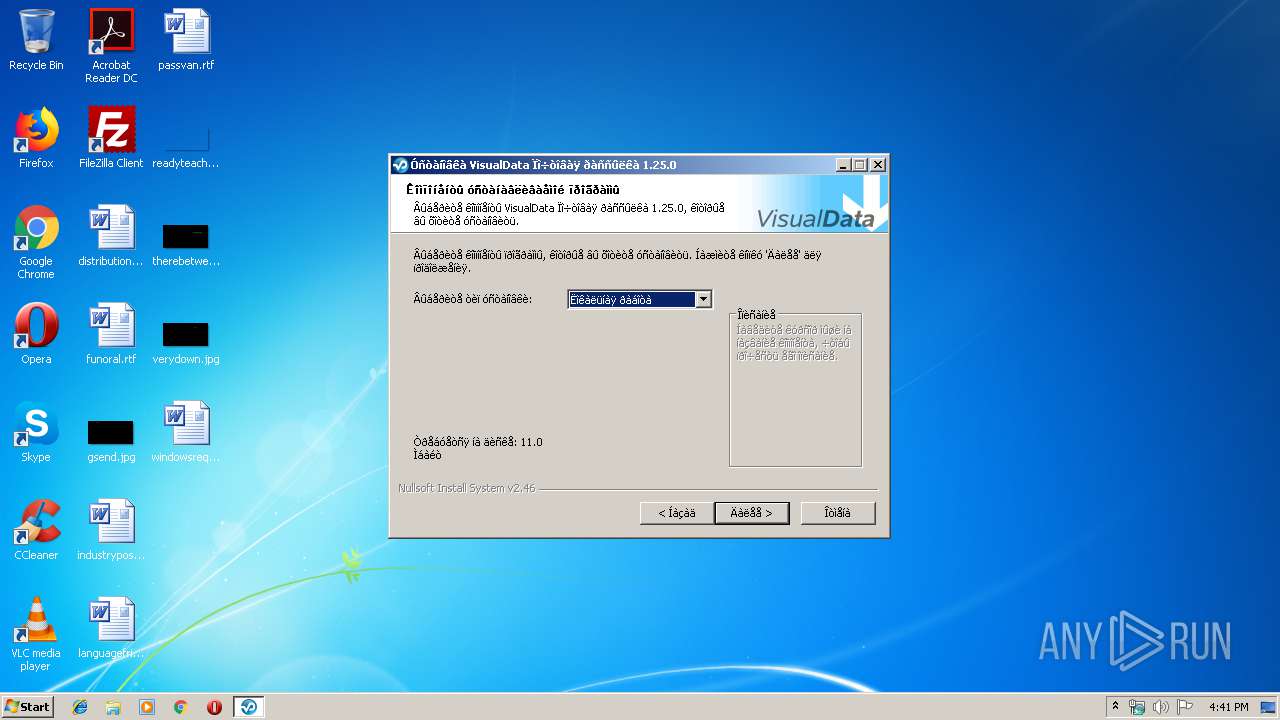
| (PID) Process: | (3740) postsending-1.25.0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\VisualData Ïî÷òîâàÿ ðàññûëêà-1.25.0 |
| Operation: | write | Name: | DisplayName |
Value: VisualData Ïî÷òîâàÿ ðàññûëêà 1.25.0 | |||
| (PID) Process: | (3740) postsending-1.25.0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\VisualData Ïî÷òîâàÿ ðàññûëêà-1.25.0 |
| Operation: | write | Name: | UninstallString |
Value: C:\VisualData\postsending\uninst.exe | |||
| (PID) Process: | (3740) postsending-1.25.0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\VisualData Ïî÷òîâàÿ ðàññûëêà-1.25.0 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\VisualData\postsending\post-icon.ico | |||
| (PID) Process: | (3740) postsending-1.25.0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\VisualData Ïî÷òîâàÿ ðàññûëêà-1.25.0 |
| Operation: | write | Name: | DisplayVersion |
Value: 1.25.0 | |||
| (PID) Process: | (3740) postsending-1.25.0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\VisualData Ïî÷òîâàÿ ðàññûëêà-1.25.0 |
| Operation: | write | Name: | URLInfoAbout |
Value: http://www.visualdata.ru | |||
| (PID) Process: | (3740) postsending-1.25.0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\VisualData Ïî÷òîâàÿ ðàññûëêà-1.25.0 |
| Operation: | write | Name: | HelpLink |
Value: http://www.visualdata.ru | |||
| (PID) Process: | (3740) postsending-1.25.0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\VisualData Ïî÷òîâàÿ ðàññûëêà-1.25.0 |
| Operation: | write | Name: | Publisher |
Value: VisualData | |||
| (PID) Process: | (3740) postsending-1.25.0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\VisualData Ïî÷òîâàÿ ðàññûëêà-1.25.0 |
| Operation: | write | Name: | Contact |
Value: òåë/ôàêñ.: 8 (863) 239-92-54 | |||
| (PID) Process: | (3740) postsending-1.25.0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\VisualData Ïî÷òîâàÿ ðàññûëêà-1.25.0 |
| Operation: | write | Name: | InstallLocation |
Value: C:\VisualData\postsending | |||
Executable files
8
Suspicious files
64
Text files
83
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3740 | postsending-1.25.0.exe | C:\Users\admin\AppData\Local\Temp\nse1514.tmp\ioSpecial.ini | text | |
MD5:— | SHA256:— | |||
| 3740 | postsending-1.25.0.exe | C:\Users\admin\AppData\Local\Temp\nse1514.tmp\modern-wizard.bmp | image | |
MD5:— | SHA256:— | |||
| 3740 | postsending-1.25.0.exe | C:\Users\admin\AppData\Local\Temp\nse1514.tmp\modern-header.bmp | image | |
MD5:— | SHA256:— | |||
| 848 | svchost.exe | C:\Windows\appcompat\programs\RecentFileCache.bcf | txt | |
MD5:— | SHA256:— | |||
| 3740 | postsending-1.25.0.exe | C:\VisualData\postsending\Local\mm.dll | executable | |
MD5:— | SHA256:— | |||
| 3740 | postsending-1.25.0.exe | C:\Users\admin\AppData\Local\Temp\nse1514.tmp\InstallOptions.dll | executable | |
MD5:325B008AEC81E5AAA57096F05D4212B5 | SHA256:C9CD5C9609E70005926AE5171726A4142FFBCCCC771D307EFCD195DAFC1E6B4B | |||
| 3740 | postsending-1.25.0.exe | C:\VisualData\postsending\Local\extimg.vdr | dbf | |
MD5:— | SHA256:— | |||
| 3740 | postsending-1.25.0.exe | C:\VisualData\postsending\Local\log.dll | executable | |
MD5:— | SHA256:— | |||
| 3740 | postsending-1.25.0.exe | C:\VisualData\postsending\Local\vd.vdr | dbf | |
MD5:— | SHA256:— | |||
| 3740 | postsending-1.25.0.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\VisualData Ïî÷òîâàÿ ðàññûëêà\VisualData Ïî÷òîâàÿ ðàññûëêà.lnk | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report