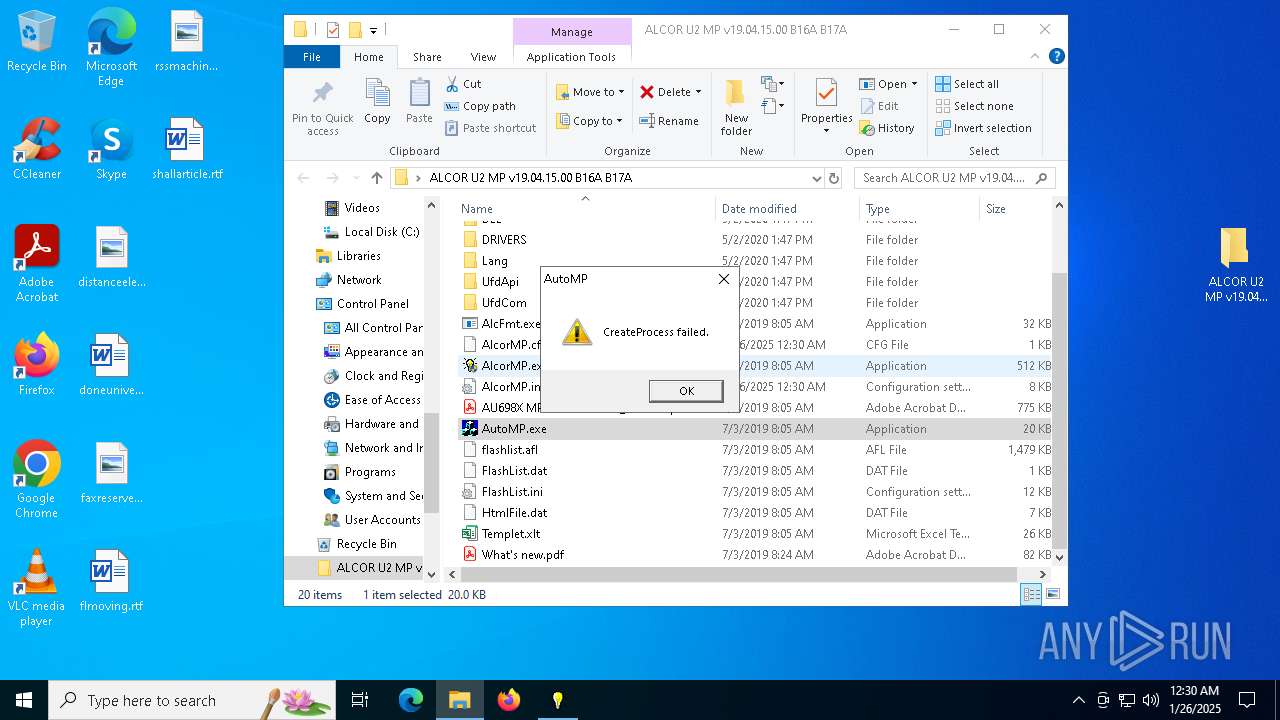
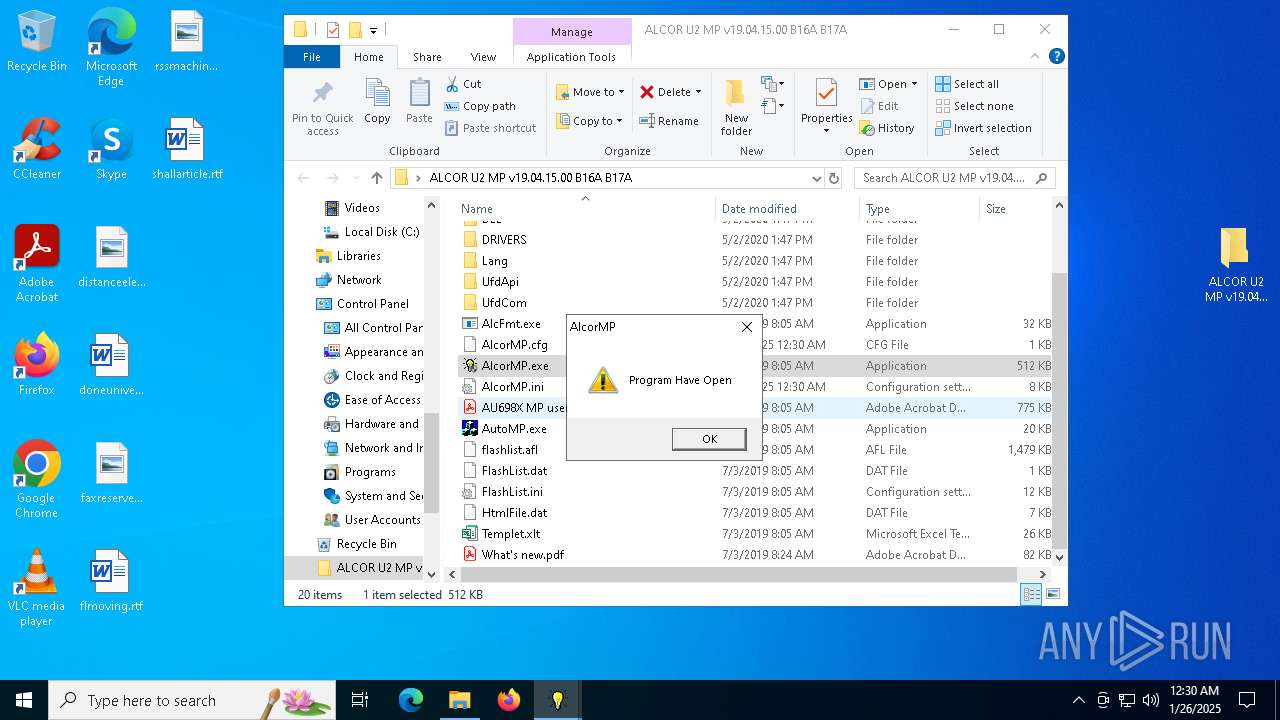
| download: | /files/file/1/download/alcor-u2-mp-v19041500-b16a-b17a_d08/ |
| Full analysis: | https://app.any.run/tasks/e9d890d4-4d3d-4bf0-955f-84bc0d345653 |
| Verdict: | Malicious activity |
| Analysis date: | January 26, 2025, 00:29:29 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
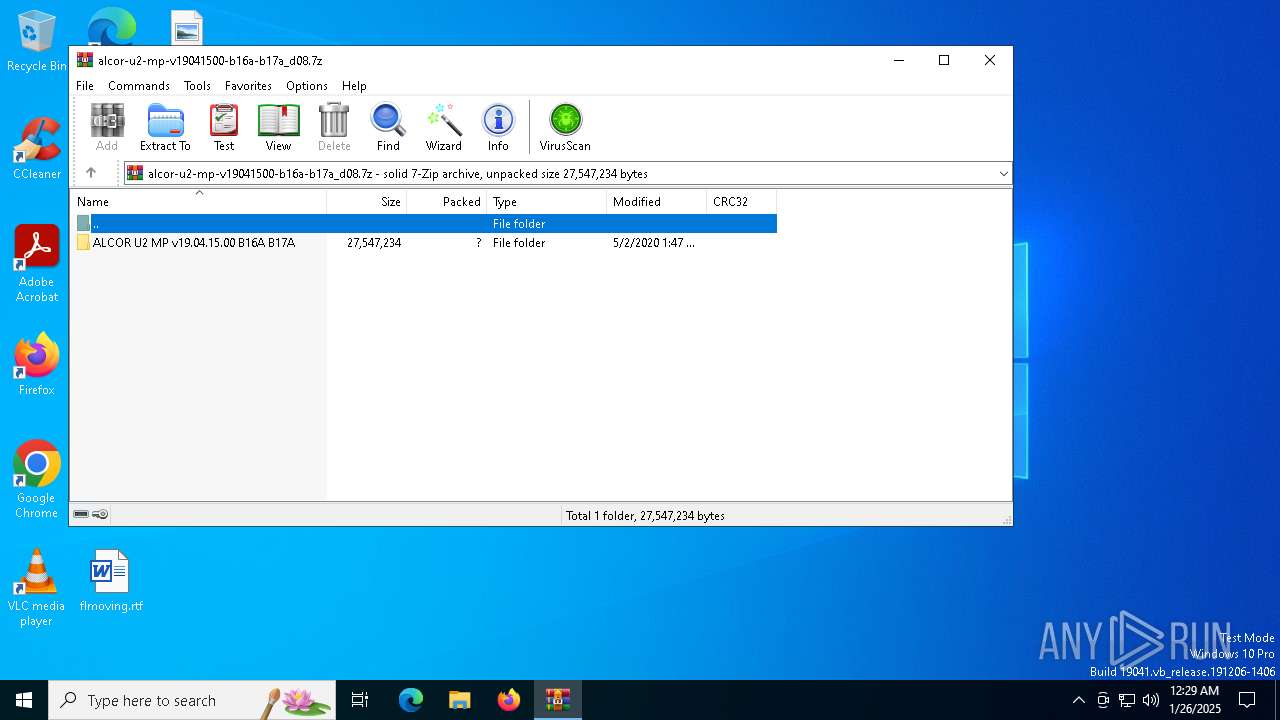
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | B6757AE95EA06BD563A27F4AABAD26DF |
| SHA1: | 4624B8652E8D40420953A614CCC943A26622991F |
| SHA256: | C9FF8EB52F005AEF6E89BDFF493ACF3EA0AC2984AD51794BB29C8B660754E625 |
| SSDEEP: | 98304:CPdR5jtMEMO60fuK0nLPF/UI7zntkFlcTBrpdy6XnMQMranc1E/X+91vp98GF+Ss:aCFw0tp9QtWNh |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5560)
SUSPICIOUS
Creates file in the systems drive root
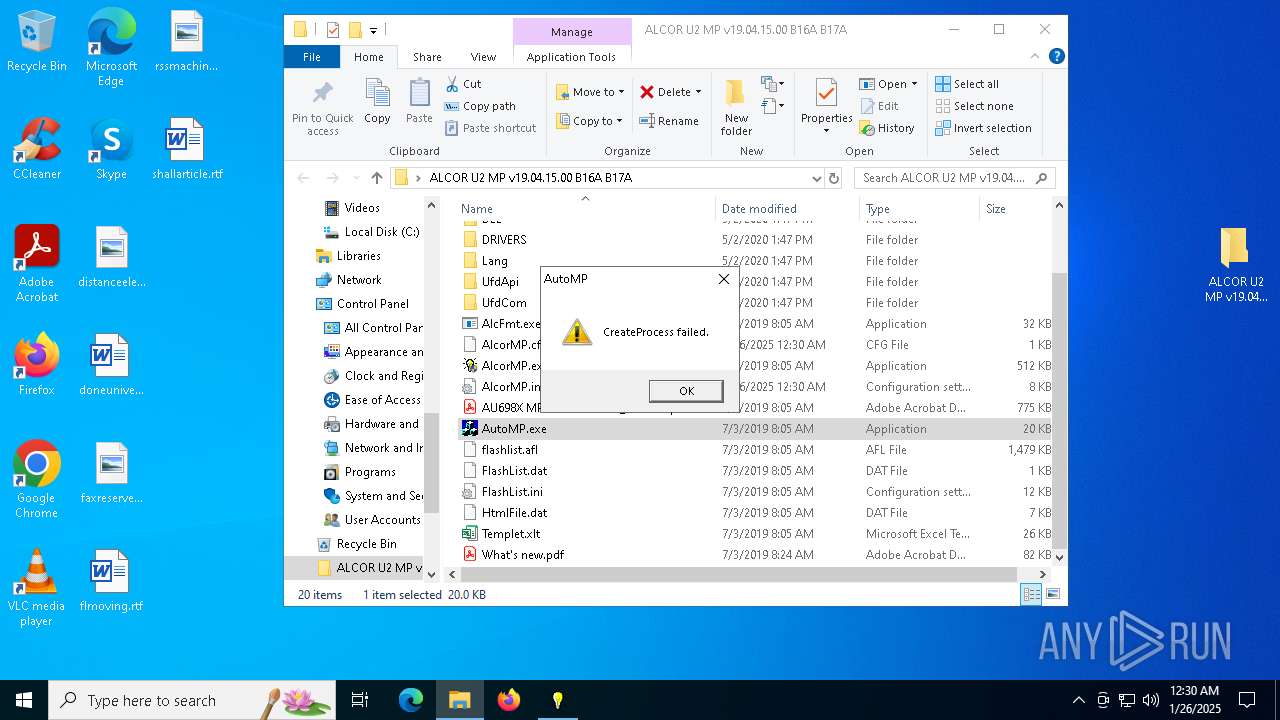
- AlcorMP.exe (PID: 2160)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 5560)
- LoadDrv.exe (PID: 5496)
Executable content was dropped or overwritten
- LoadDrv.exe (PID: 5496)
There is functionality for taking screenshot (YARA)
- AlcorMP.exe (PID: 2160)
Creates files in the driver directory
- LoadDrv.exe (PID: 5496)
INFO
The sample compiled with chinese language support
- WinRAR.exe (PID: 5560)
Reads security settings of Internet Explorer
- notepad.exe (PID: 1156)
Checks supported languages
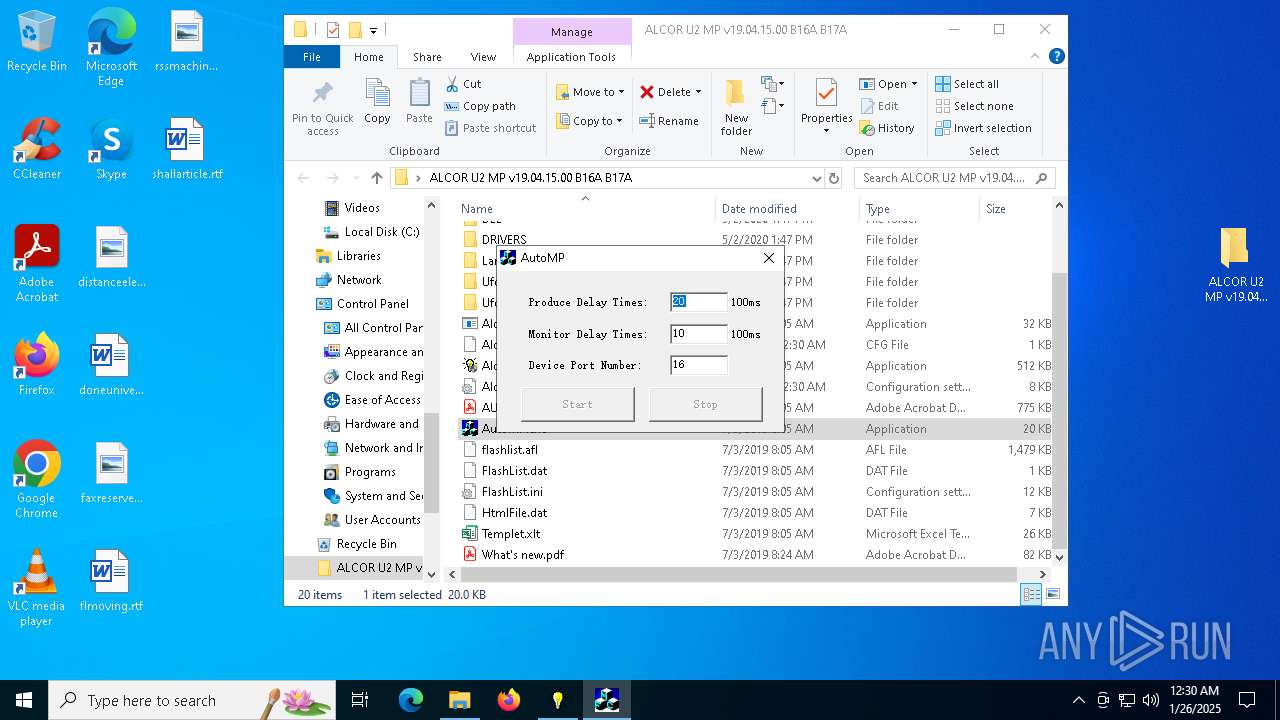
- AlcorMP.exe (PID: 2160)
- KillBaboon.exe (PID: 1356)
- DrvCovEx.exe (PID: 936)
- VerifyCat.exe (PID: 6072)
- LoadDrv.exe (PID: 624)
- LoadDrv.exe (PID: 5496)
- AlcFmt.exe (PID: 5592)
- AlcorMP.exe (PID: 3296)
- AutoMP.exe (PID: 3188)
- AlcFmt.exe (PID: 1852)
- KillBaboon.exe (PID: 5000)
- AutoMP.exe (PID: 4024)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5560)
The sample compiled with english language support
- WinRAR.exe (PID: 5560)
- LoadDrv.exe (PID: 5496)
Manual execution by a user
- notepad.exe (PID: 1156)
- AlcorMP.exe (PID: 1468)
- AutoMP.exe (PID: 4024)
- AlcFmt.exe (PID: 5592)
- AutoMP.exe (PID: 3188)
- AlcFmt.exe (PID: 1852)
- AlcorMP.exe (PID: 4672)
- AlcorMP.exe (PID: 3296)
- AlcorMP.exe (PID: 2160)
Reads the software policy settings
- VerifyCat.exe (PID: 6072)
Reads the computer name
- AlcorMP.exe (PID: 2160)
- LoadDrv.exe (PID: 5496)
- AutoMP.exe (PID: 4024)
- AutoMP.exe (PID: 3188)
- DrvCovEx.exe (PID: 936)
- AlcorMP.exe (PID: 3296)
Reads the machine GUID from the registry
- VerifyCat.exe (PID: 6072)
Create files in a temporary directory
- VerifyCat.exe (PID: 6072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2020:05:02 13:47:29+00:00 |
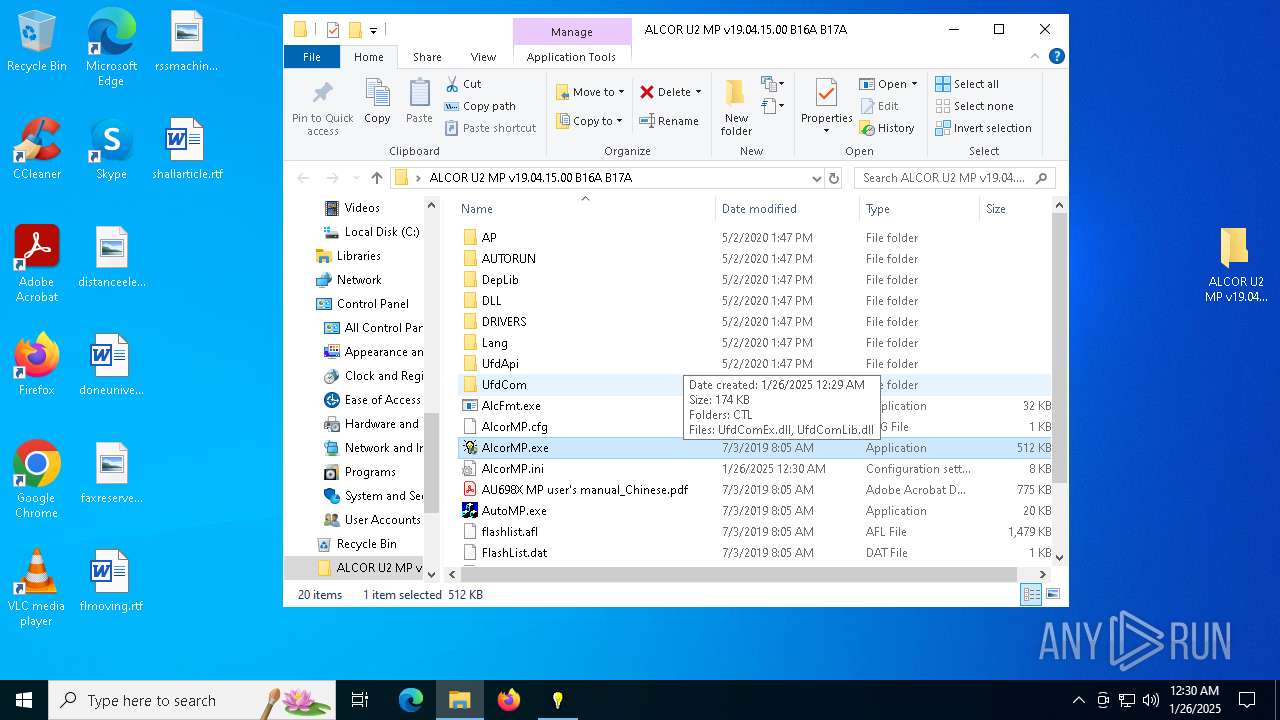
| ArchivedFileName: | ALCOR U2 MP v19.04.15.00 B16A B17A |
Total processes
143
Monitored processes
24
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 624 | "C:\Users\admin\Desktop\ALCOR U2 MP v19.04.15.00 B16A B17A\drivers\LoadDrv.exe" SetIgnoreHwID 058f6387 | C:\Users\admin\Desktop\ALCOR U2 MP v19.04.15.00 B16A B17A\DRIVERS\LoadDrv.exe | — | AlcorMP.exe | |||||||||||
User: admin Company: ALCOR Integrity Level: HIGH Description: LoadDrv Exit code: 0 Version: 1, 2, 0, 0 Modules
| |||||||||||||||
| 936 | C:\WINDOWS\system32\DrvCovEx.exe RegisterOnly DrvCovEx | C:\Windows\SysWOW64\DrvCovEx.exe | — | LoadDrv.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 1156 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\ALCOR U2 MP v19.04.15.00 B16A B17A\AlcorMP.ini | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1356 | "C:\Users\admin\Desktop\ALCOR U2 MP v19.04.15.00 B16A B17A\\DRIVERS\KillBaboon.exe" | C:\Users\admin\Desktop\ALCOR U2 MP v19.04.15.00 B16A B17A\DRIVERS\KillBaboon.exe | — | AlcorMP.exe | |||||||||||
User: admin Integrity Level: HIGH Description: KillBaboon Version: 1, 2, 0, 0 Modules
| |||||||||||||||
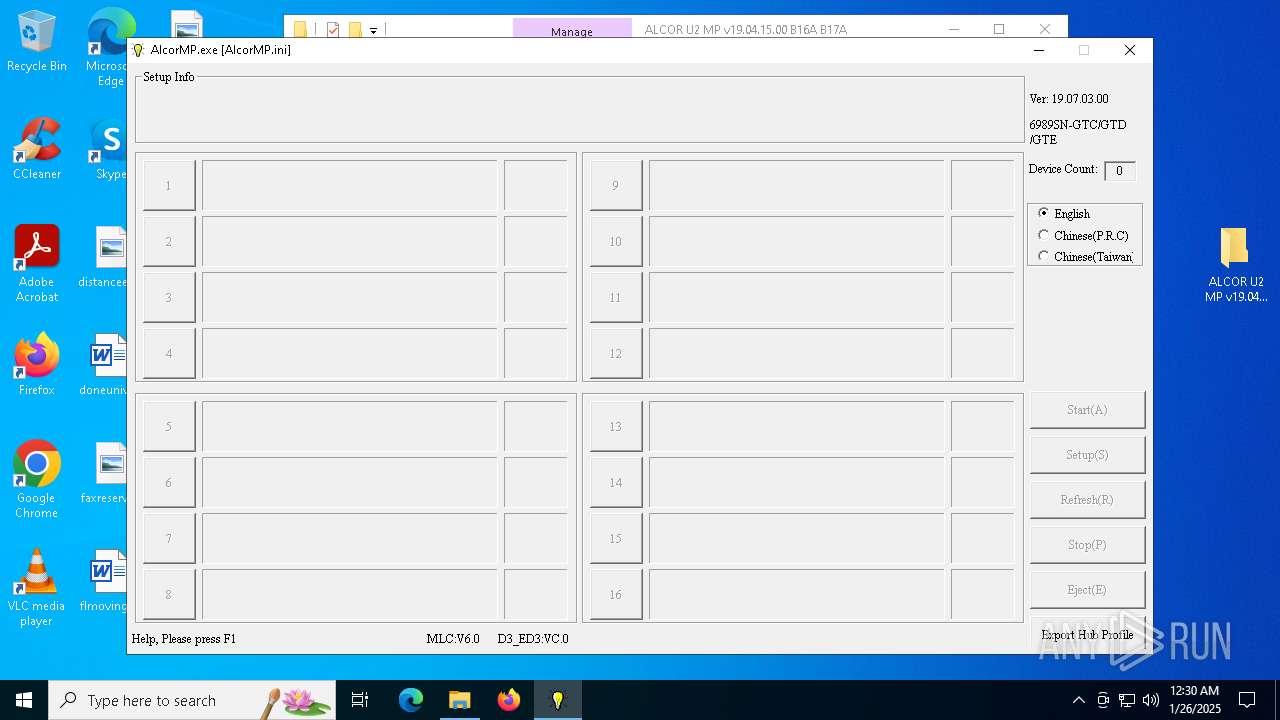
| 1468 | "C:\Users\admin\Desktop\ALCOR U2 MP v19.04.15.00 B16A B17A\AlcorMP.exe" | C:\Users\admin\Desktop\ALCOR U2 MP v19.04.15.00 B16A B17A\AlcorMP.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: MP Exit code: 3221226540 Version: 3, 1, 1, 33 Modules
| |||||||||||||||
| 1852 | "C:\Users\admin\Desktop\ALCOR U2 MP v19.04.15.00 B16A B17A\AlcFmt.exe" | C:\Users\admin\Desktop\ALCOR U2 MP v19.04.15.00 B16A B17A\AlcFmt.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2 Modules
| |||||||||||||||
| 2160 | "C:\Users\admin\Desktop\ALCOR U2 MP v19.04.15.00 B16A B17A\AlcorMP.exe" | C:\Users\admin\Desktop\ALCOR U2 MP v19.04.15.00 B16A B17A\AlcorMP.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: MP Version: 3, 1, 1, 33 Modules
| |||||||||||||||
| 3188 | "C:\Users\admin\Desktop\ALCOR U2 MP v19.04.15.00 B16A B17A\AutoMP.exe" | C:\Users\admin\Desktop\ALCOR U2 MP v19.04.15.00 B16A B17A\AutoMP.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: AutoMP Microsoft 基础类应用程序 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 3260 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | LoadDrv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3260 | "C:\Users\admin\Desktop\ALCOR U2 MP v19.04.15.00 B16A B17A\\AlcorMP.exe" -AT:0005048A | C:\Users\admin\Desktop\ALCOR U2 MP v19.04.15.00 B16A B17A\AlcorMP.exe | — | AutoMP.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: MP Exit code: 3221226540 Version: 3, 1, 1, 33 Modules
| |||||||||||||||
Total events
8 886
Read events
8 863
Write events
23
Delete events
0
Modification events
| (PID) Process: | (5560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\alcor-u2-mp-v19041500-b16a-b17a_d08.7z | |||
| (PID) Process: | (5560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (5560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
32
Suspicious files
13
Text files
267
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5560.19444\ALCOR U2 MP v19.04.15.00 B16A B17A\FlashList.dat | text | |
MD5:D211356E46C4B16FC7DC97F4DB38ABF3 | SHA256:56C0C0B4B4C91E0232C71C1D4321159784F416F0A2F78FCA6FC9A053A36CD112 | |||
| 5560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5560.19444\ALCOR U2 MP v19.04.15.00 B16A B17A\UfdApi\UfdApi_Gen\CTL\28\BIN\28_19_Hynix_3D.BIN | text | |
MD5:F261931CFDBCF398A82441DDDFE35631 | SHA256:B4B00AAFE2977211547F5AD739D8BC2C71F27EEEB6D901B02B38CD14FDF75C5A | |||
| 5560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5560.19444\ALCOR U2 MP v19.04.15.00 B16A B17A\UfdApi\UfdApi_Gen\CTL\28\BIN\28_18_N18_FP.BIN | text | |
MD5:A45F663909D184B7923B7D57C8B5D5A9 | SHA256:CFD4C07D56B6E9EAA3086B208B81C8866F5C593F5048117321CC9749CD0B36AA | |||
| 5560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5560.19444\ALCOR U2 MP v19.04.15.00 B16A B17A\AlcorMP.cfg | text | |
MD5:F4BA0B8C9057DE6C9E07AD45B03FCB9B | SHA256:374403C7A14667DD4321D58AED8B32102C84074ADEEB6943F385733C1F2CDE6D | |||
| 5560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5560.19444\ALCOR U2 MP v19.04.15.00 B16A B17A\AUTORUN\Reserve.img | binary | |
MD5:9F0B3CFC69D17A67B7B0AE7EA93BC57C | SHA256:3E4001500F6ECFC1AF63E8286DA31E17730457B03D0E5718A619C1FA0FAE33F7 | |||
| 5560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5560.19444\ALCOR U2 MP v19.04.15.00 B16A B17A\AUTORUN\9384.img | binary | |
MD5:08F9BCB981C3018B18AC8D7DFF51D822 | SHA256:7239FF04D41997F048CB6C9B42D2DEAC2D2B7AFCD7296B180AEB4B63C25D9ABB | |||
| 5560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5560.19444\ALCOR U2 MP v19.04.15.00 B16A B17A\DRIVERS\LoadDrv.ini | text | |
MD5:95504E1F50EBAE8191F368B59C4EA6B2 | SHA256:211C5431B56290B0317814F41B38105CBA04FAFB92705FD9AAD565B6B74CFBC9 | |||
| 5560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5560.19444\ALCOR U2 MP v19.04.15.00 B16A B17A\AlcorMP.ini | text | |
MD5:D5F6BC4865E865E788F5B6CCBBB55F39 | SHA256:0D9E4AB9514CA51925E3AF30C41661A34E0E7E90088280E6F36A1AD764C11A79 | |||
| 5560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5560.19444\ALCOR U2 MP v19.04.15.00 B16A B17A\UfdApi\UfdApi_Gen\CTL\28\BIN\28_17_16K_UCG256.BIN | text | |
MD5:4CF0BD5791DA6E569C55051A0054B58B | SHA256:B821F1EE25C17CC5ED0FE521AD392A67A1E19A5F5B52FF9DAB2C067C5F2C8611 | |||
| 5560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5560.19444\ALCOR U2 MP v19.04.15.00 B16A B17A\DRIVERS\CatSetting.ini | text | |
MD5:A5087171A86654CE35201CEB6653AF14 | SHA256:784F1CB69D7428425707DE38CC47E97BCB63D9682A622F92B4682D60291930A9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
23
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3976 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5208 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.206:49687 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
dns.msftncsi.com |
| whitelisted |