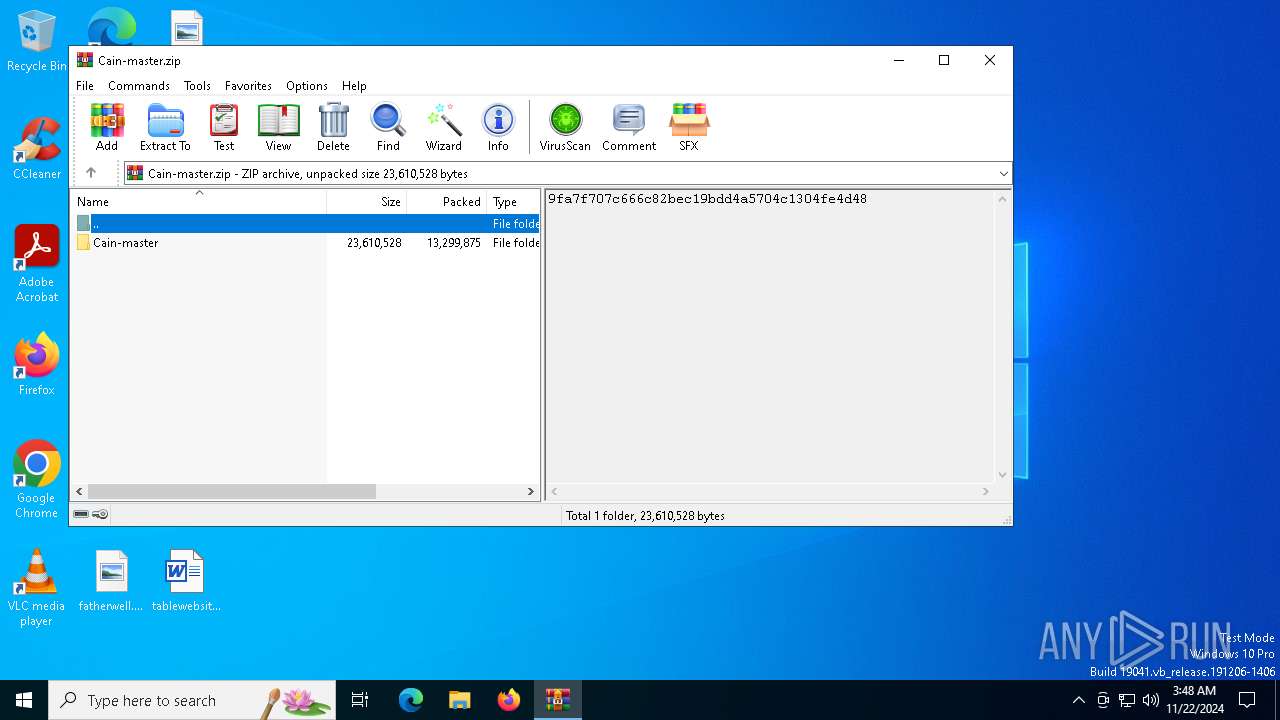
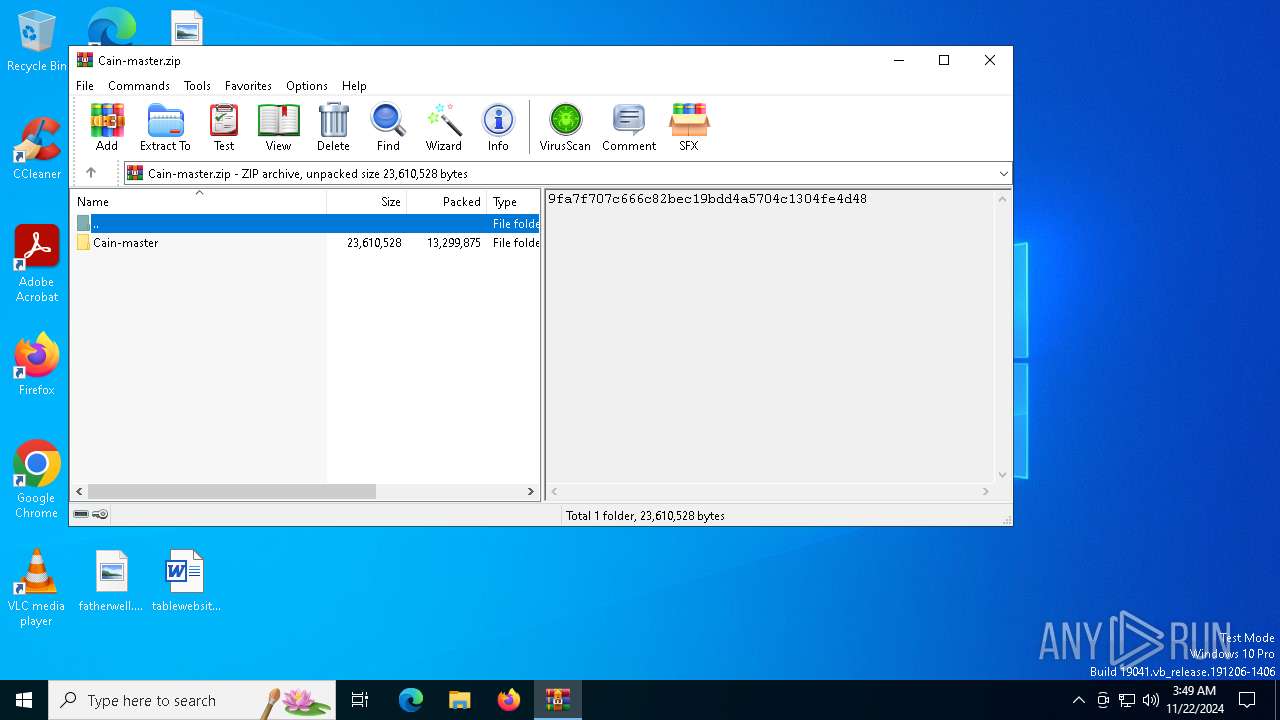
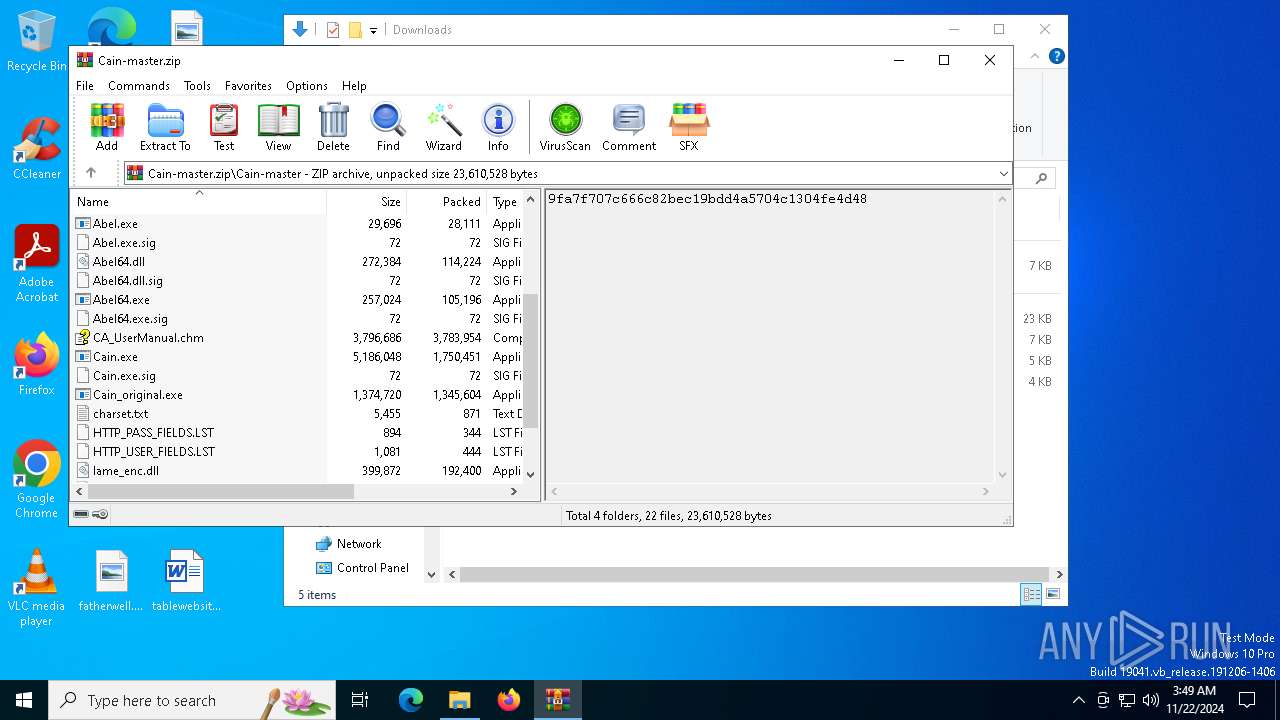
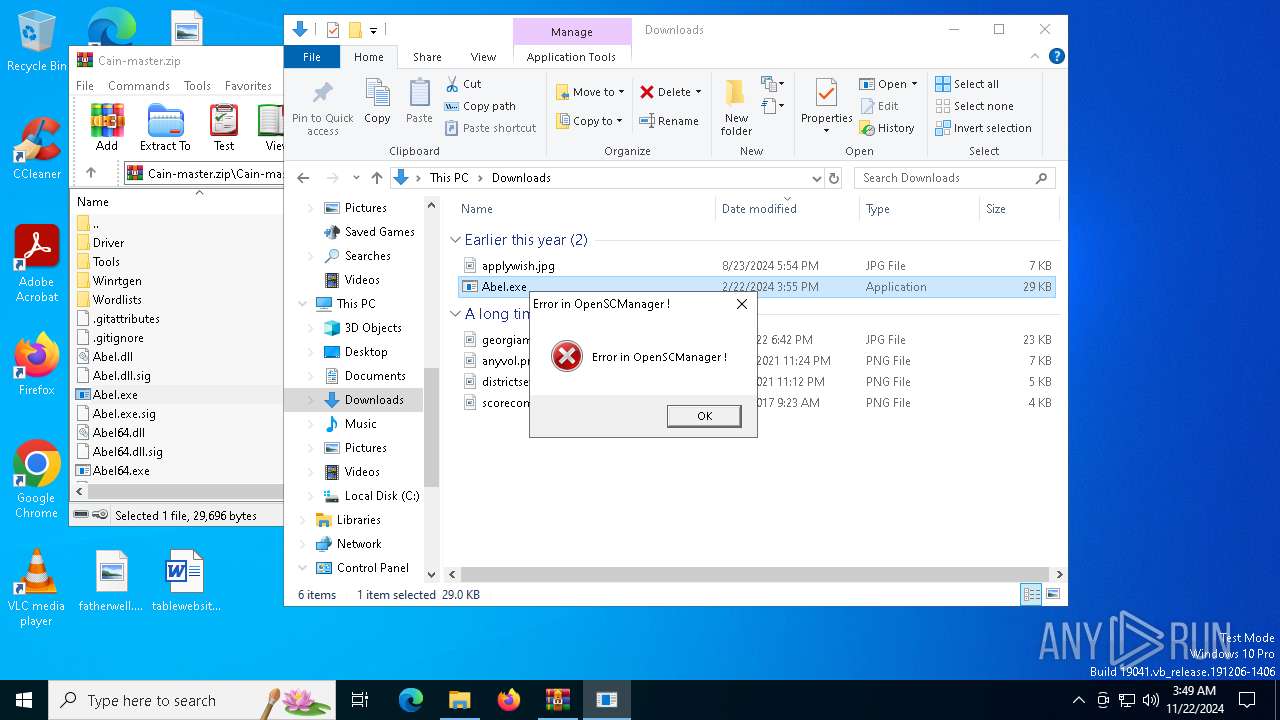
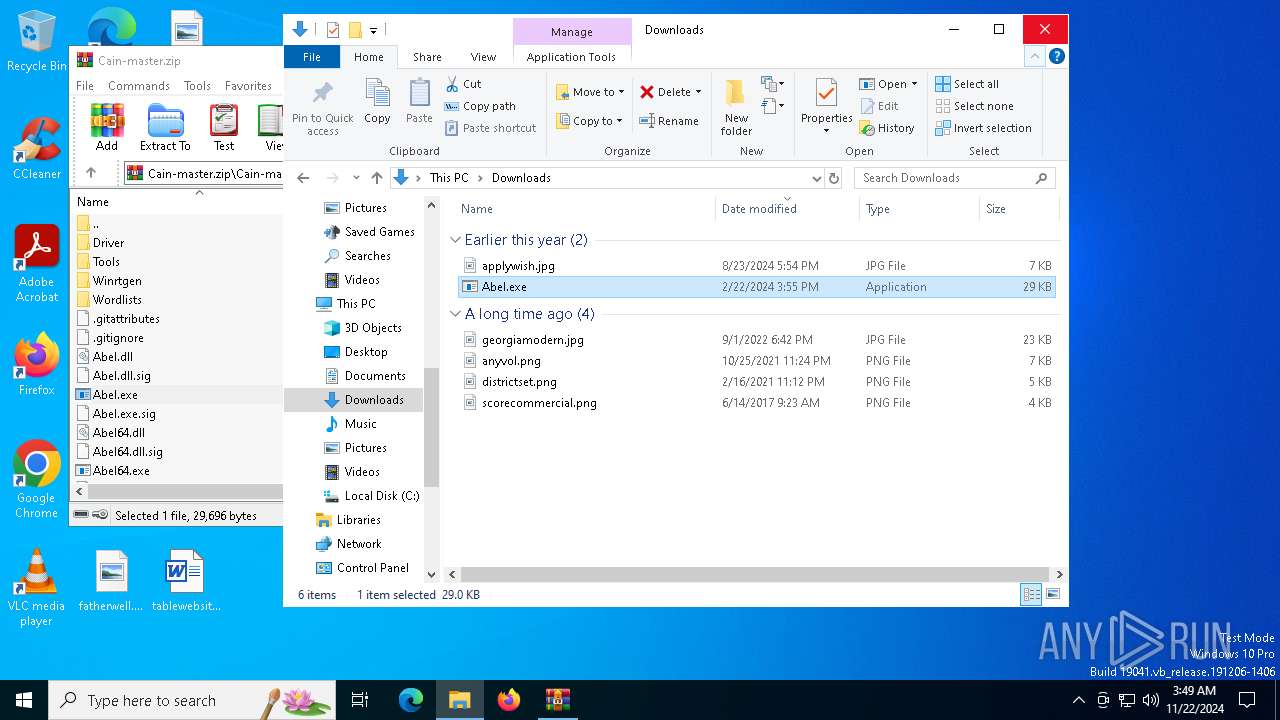
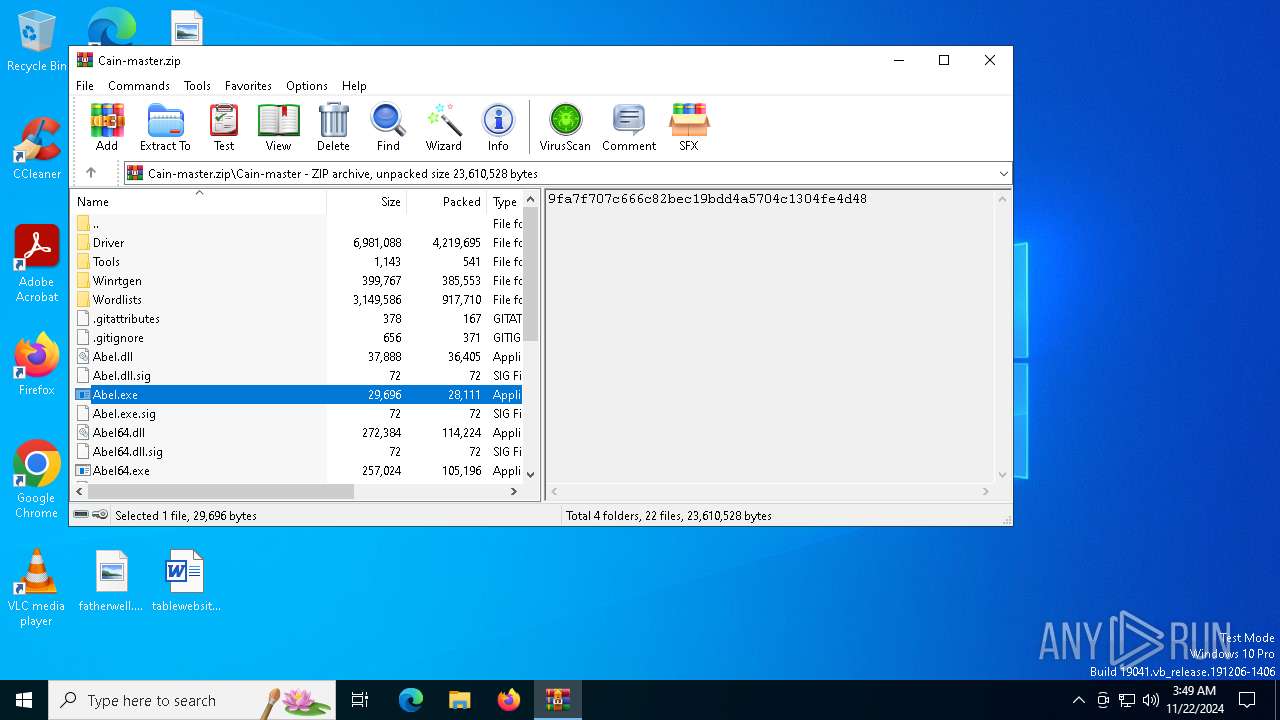
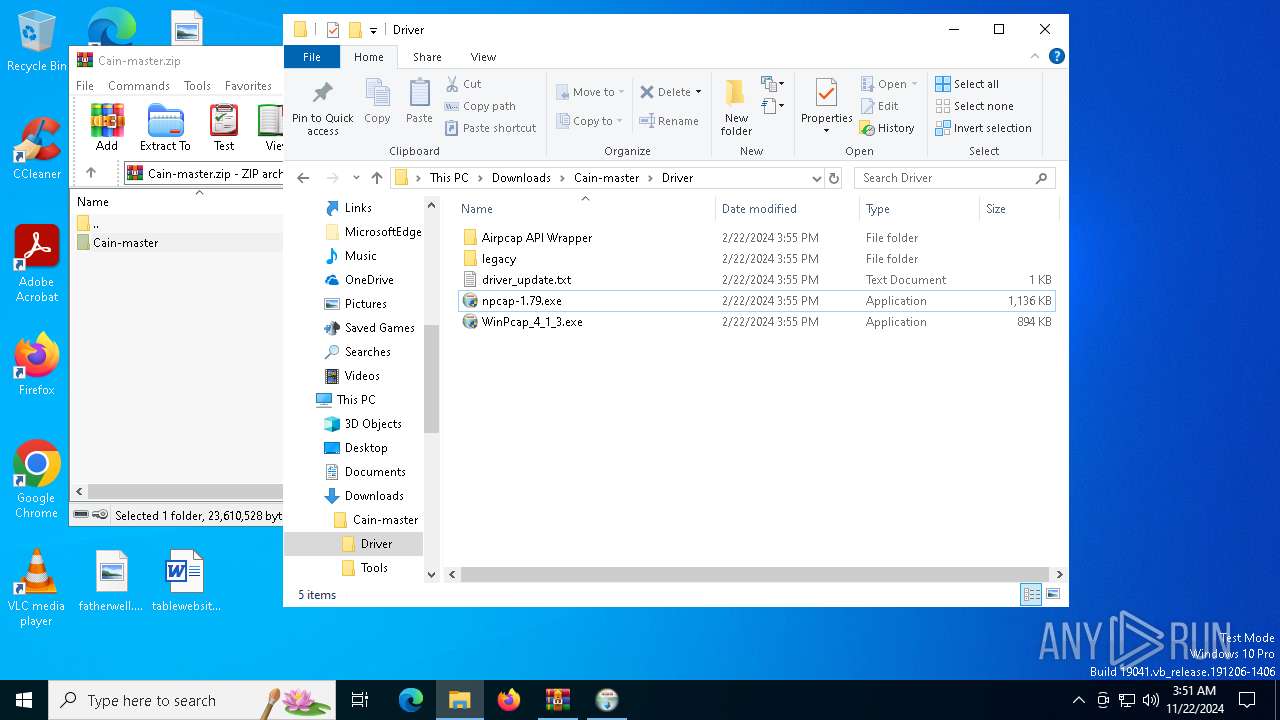
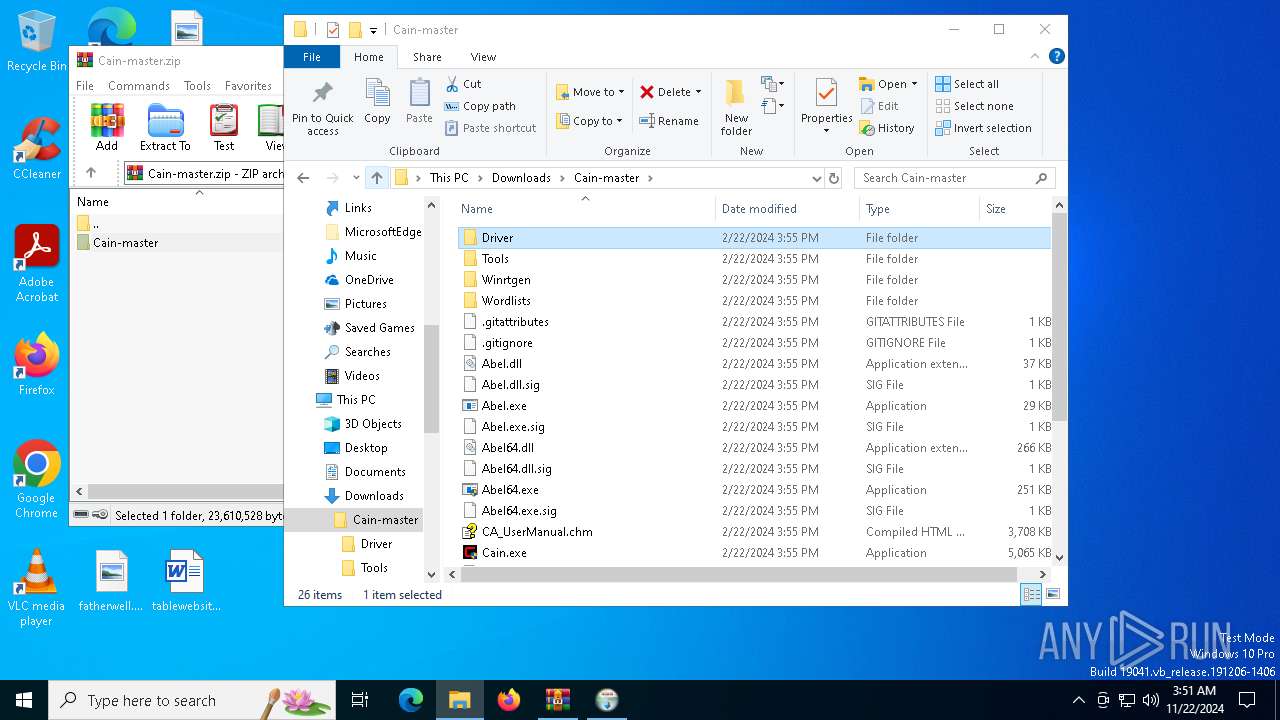
| File name: | Cain-master.zip |
| Full analysis: | https://app.any.run/tasks/de0bd9f6-fb13-45f8-8adc-2e863808d974 |
| Verdict: | Malicious activity |
| Analysis date: | November 22, 2024, 03:48:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 7C5F70C97E1C8CB4CC0C8542604DDB70 |
| SHA1: | 92839216E7788F42F03DC3EC04F3B4AD6F522C0D |
| SHA256: | C9F07641920AEE056010E1522C386CC6227B62265297584F133F9D7E43703DF5 |
| SSDEEP: | 98304:WiJd7L6/T7RngHqbEcY5ZquVhQKNERcsWxkb995mkTHftvMRxaZfybPbbrWGu9N3:d5E+BGeSdlXK/aV9RA0hhFySRvl5LN |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 4444)
- powershell.exe (PID: 6252)
- powershell.exe (PID: 5564)
- powershell.exe (PID: 6476)
- powershell.exe (PID: 6324)
- powershell.exe (PID: 968)
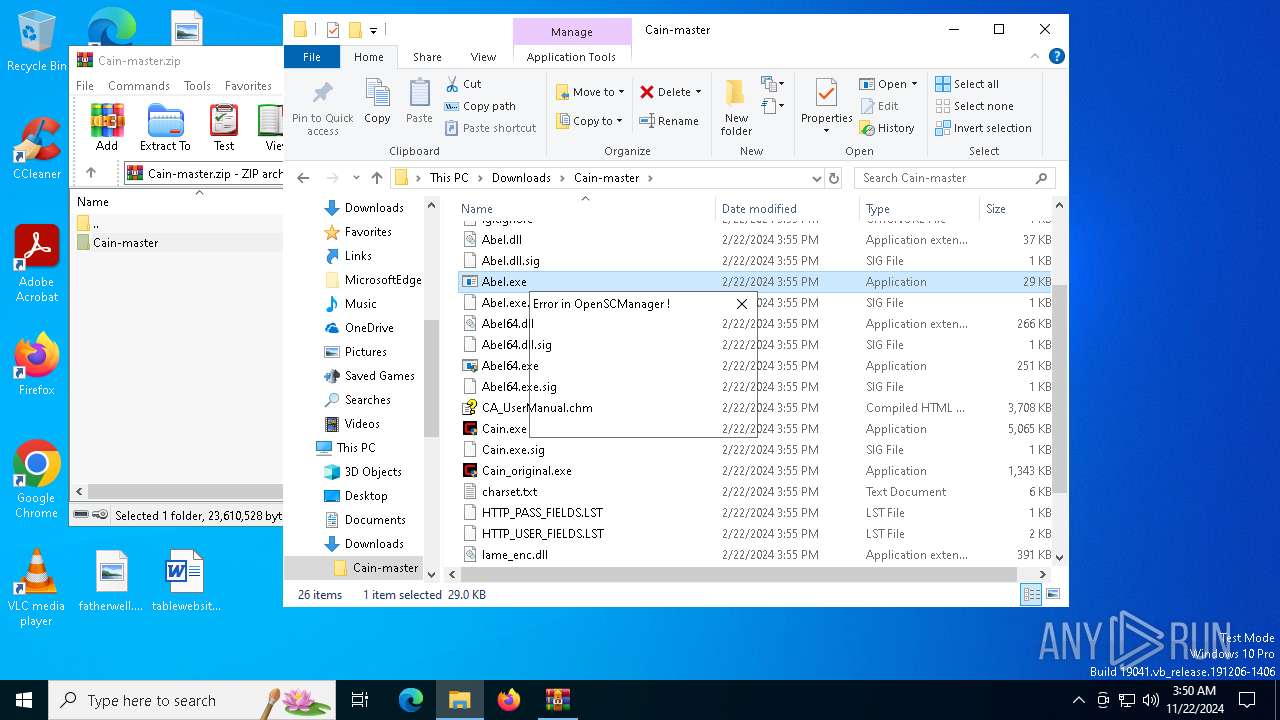
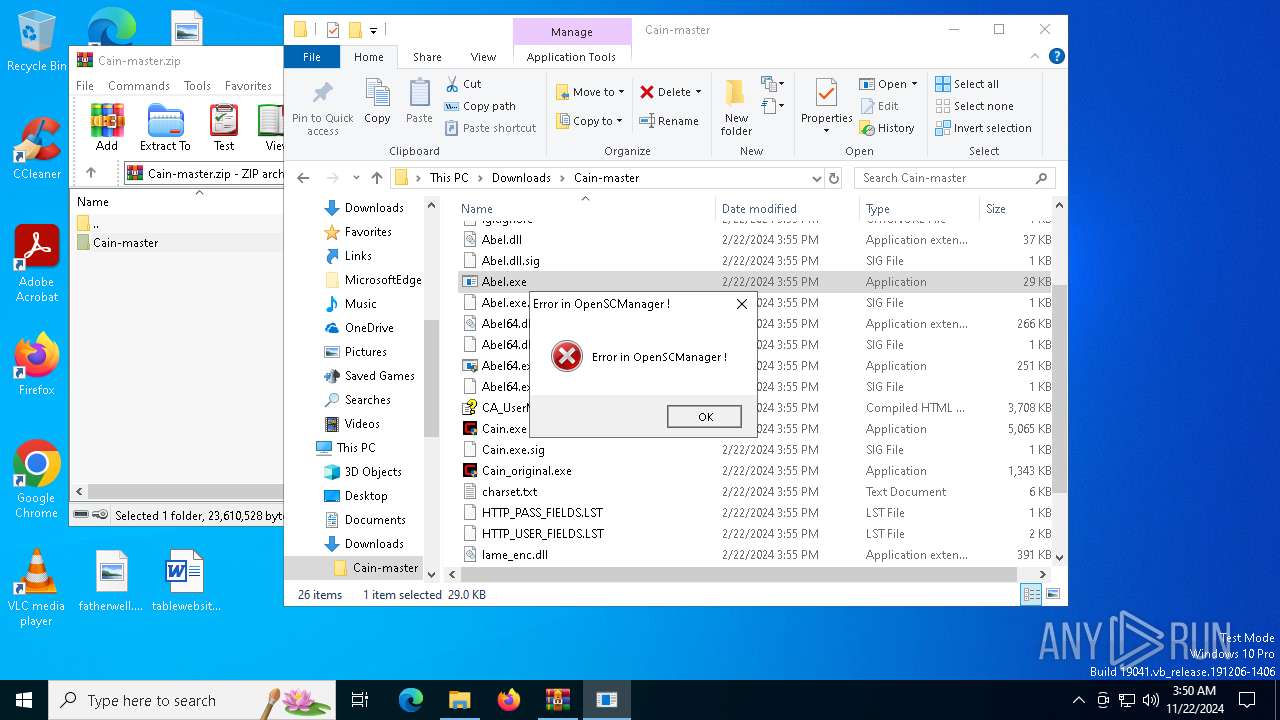
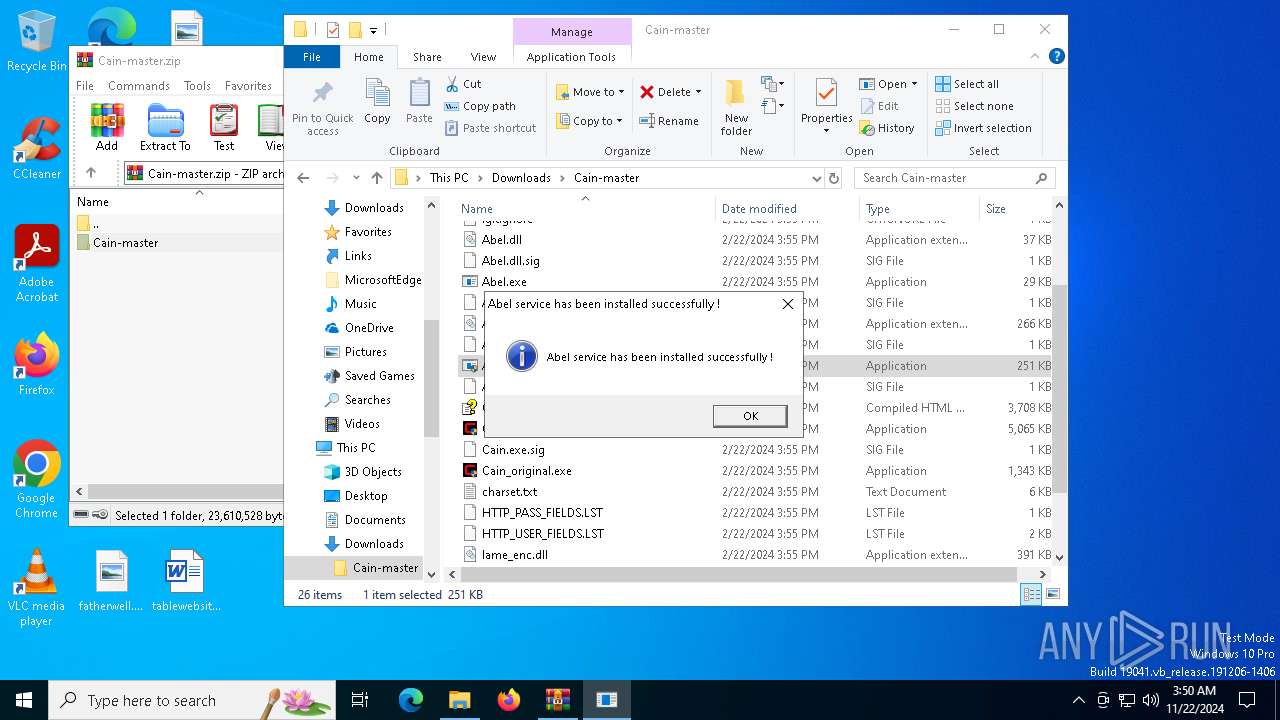
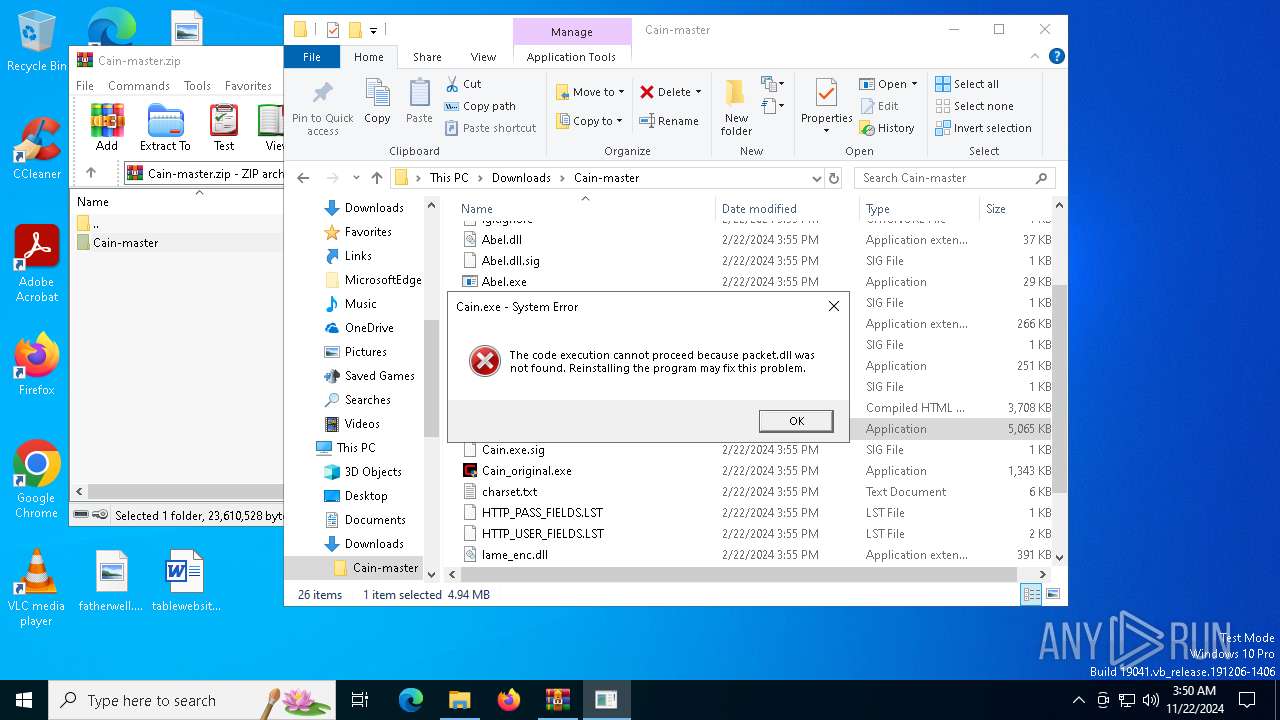
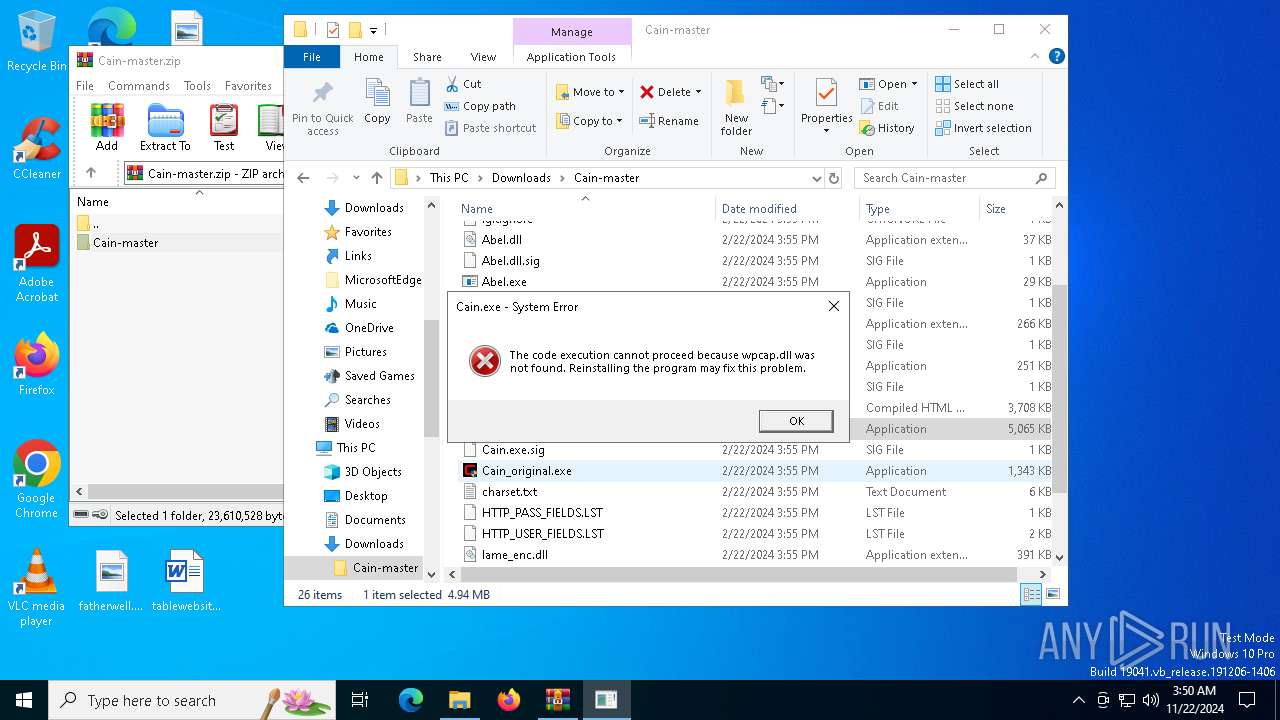
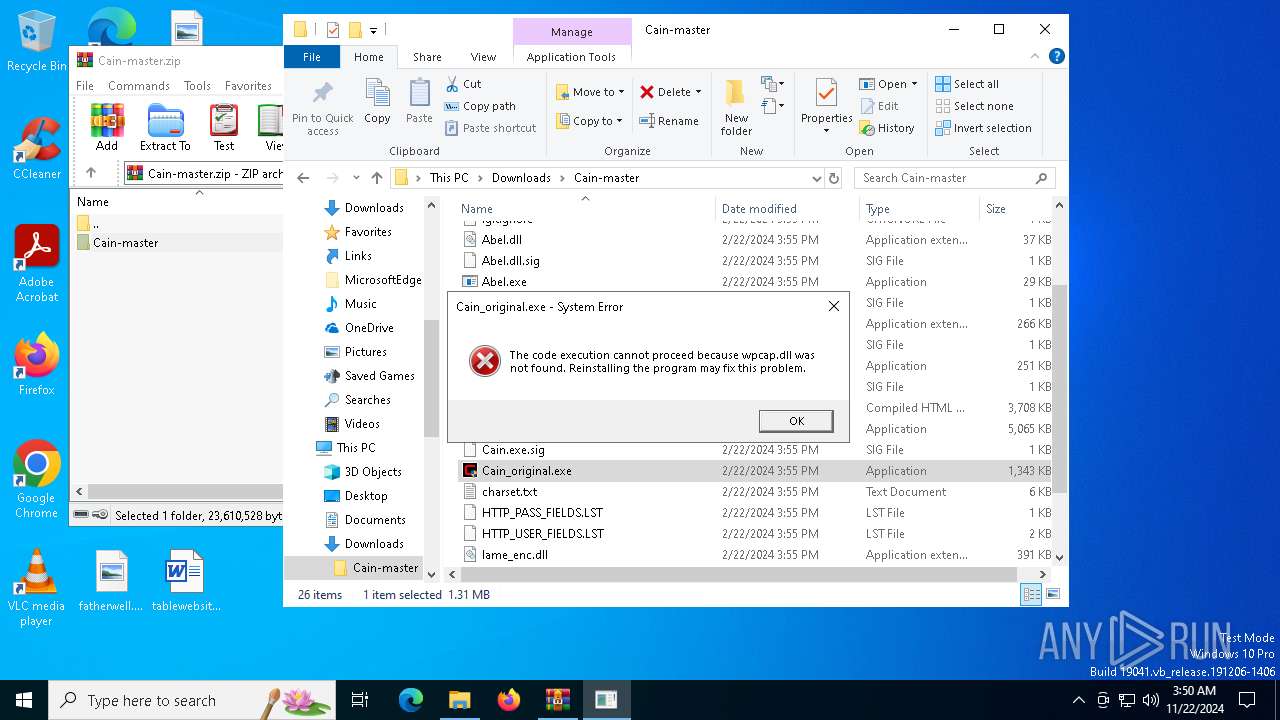
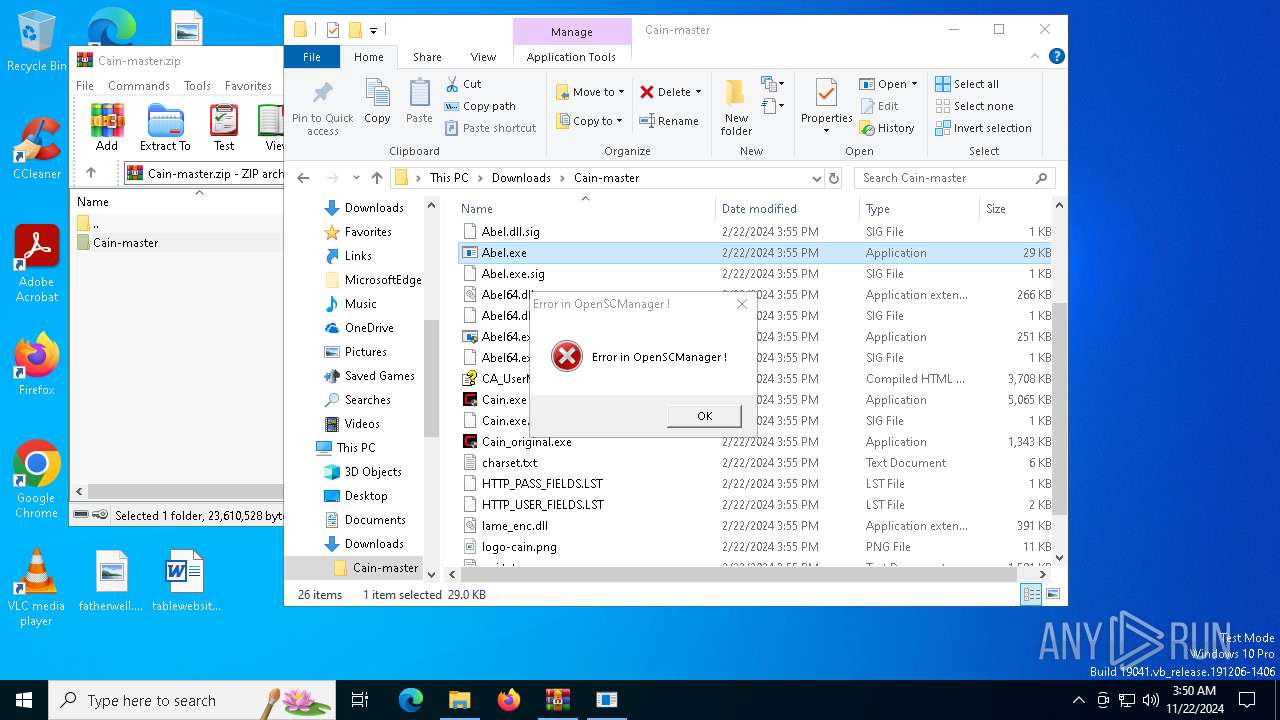
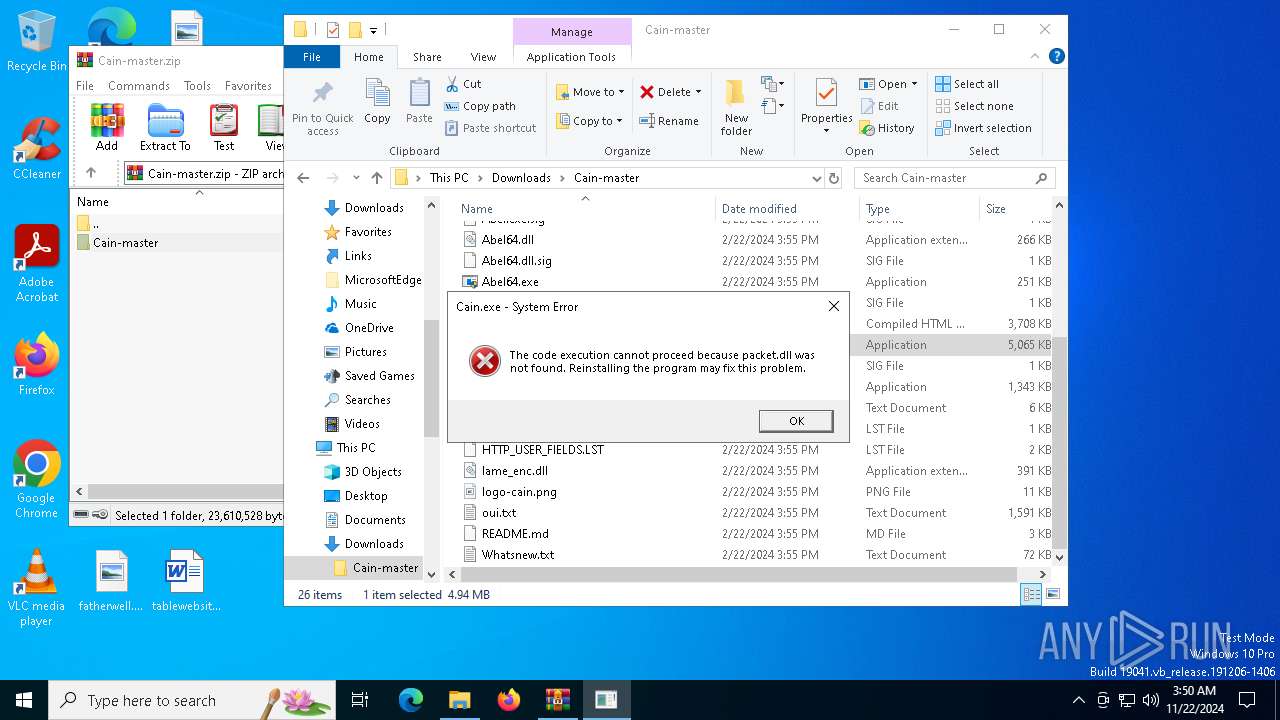
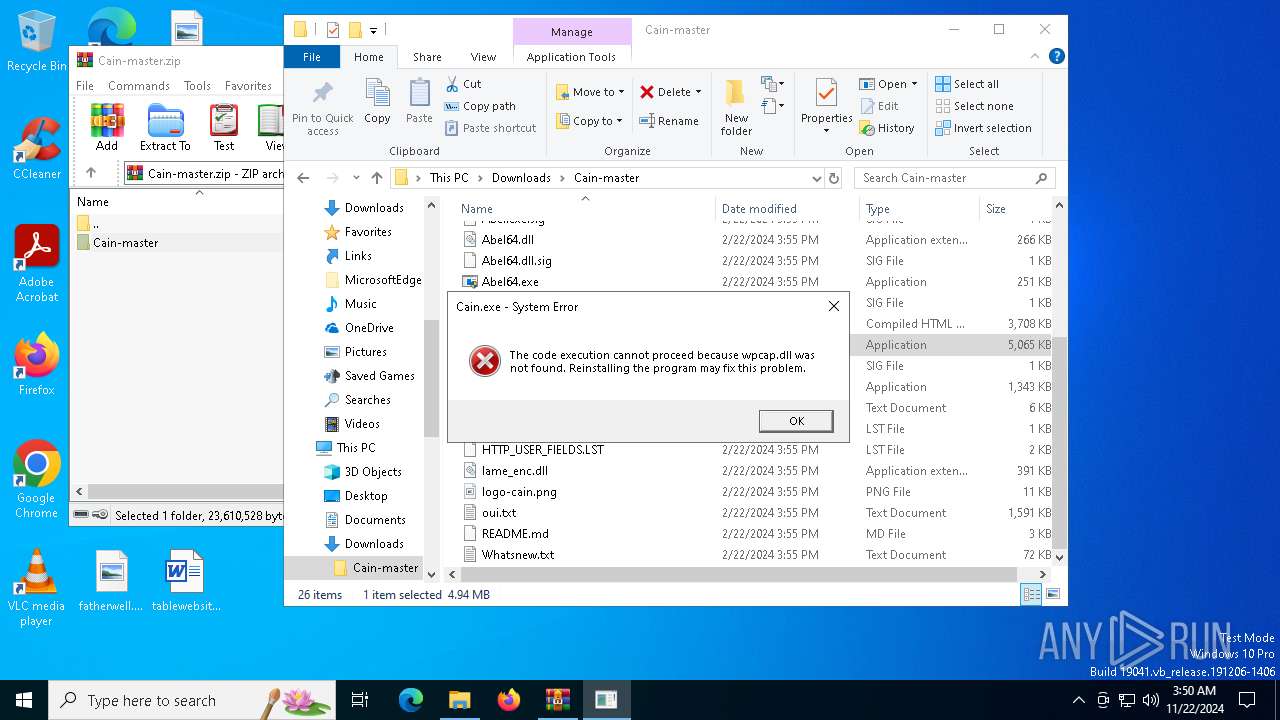
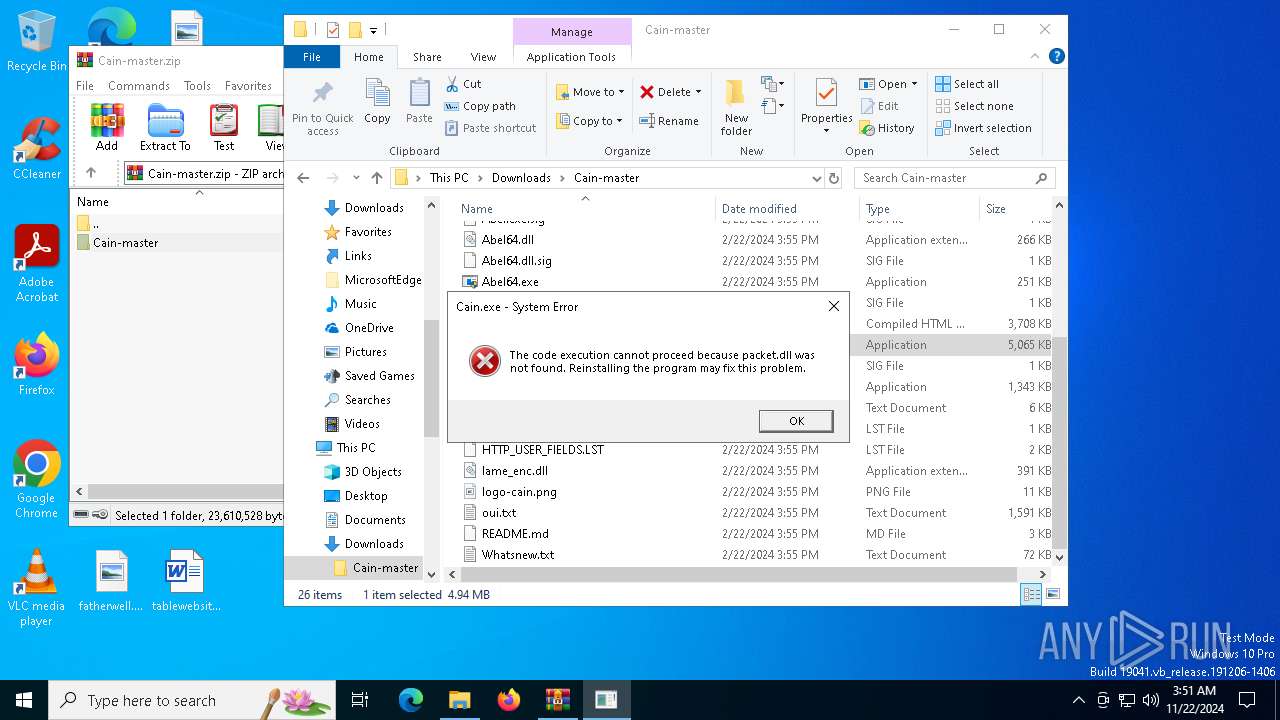
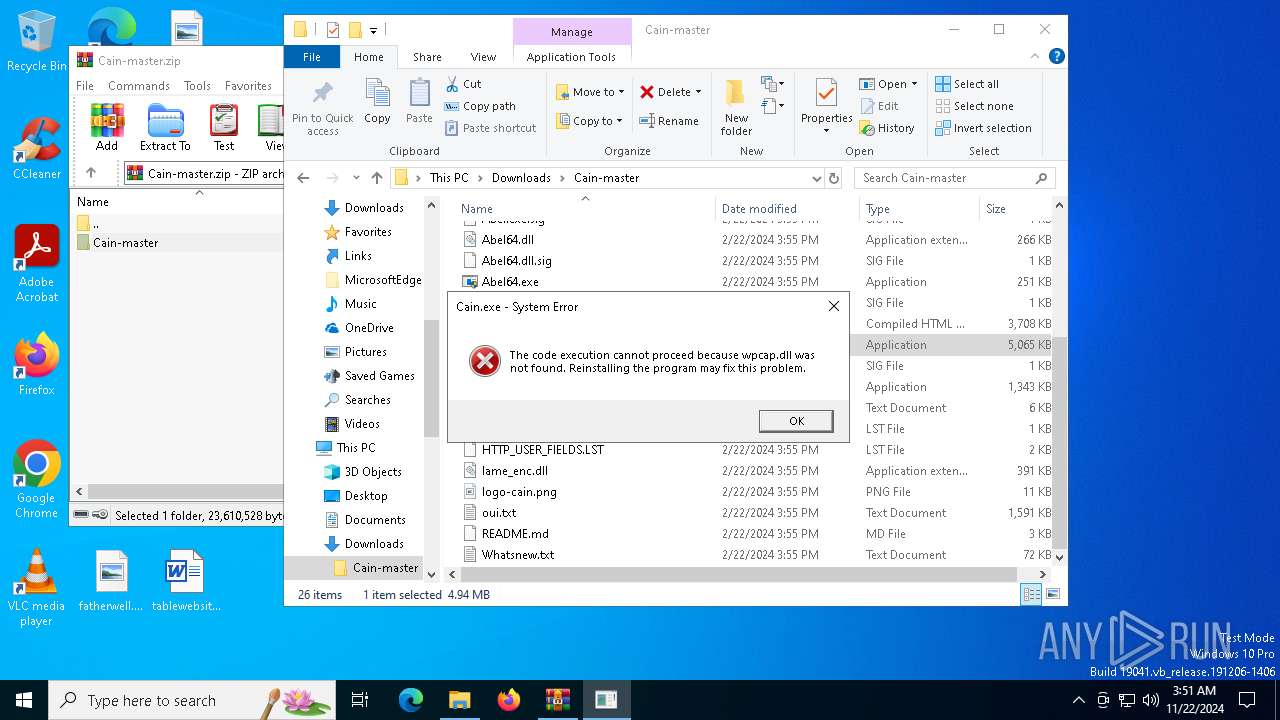
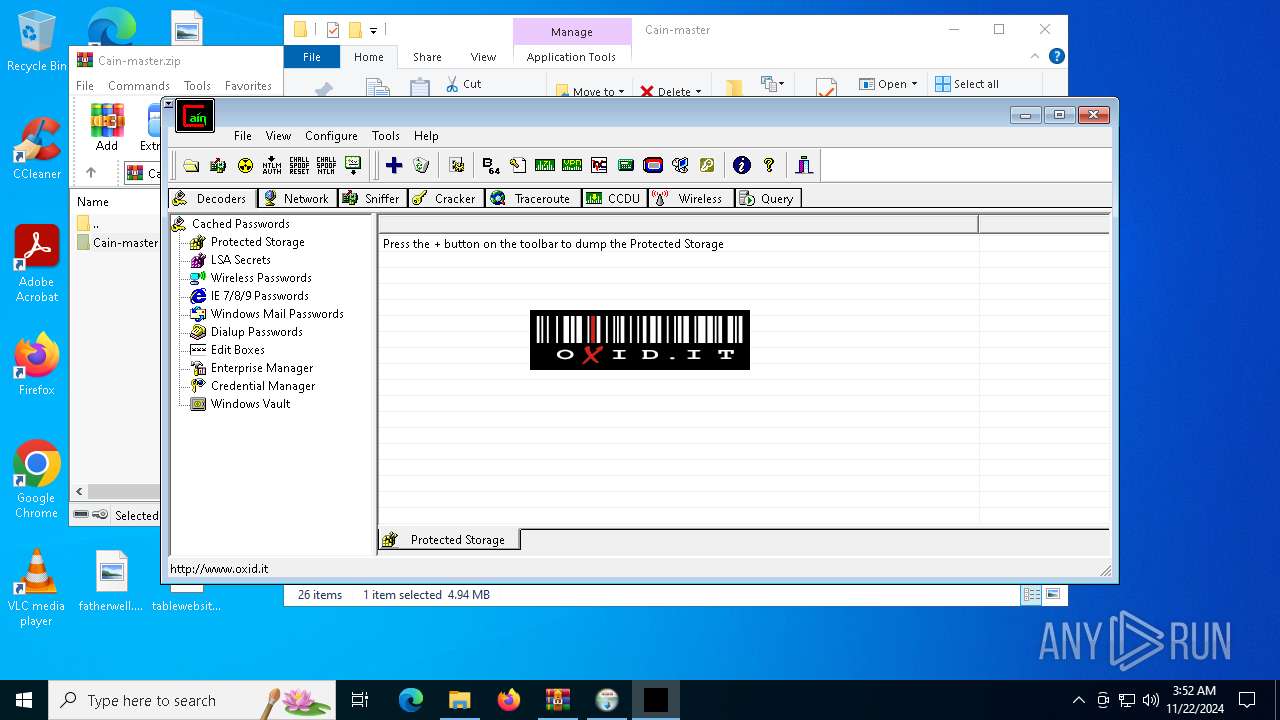
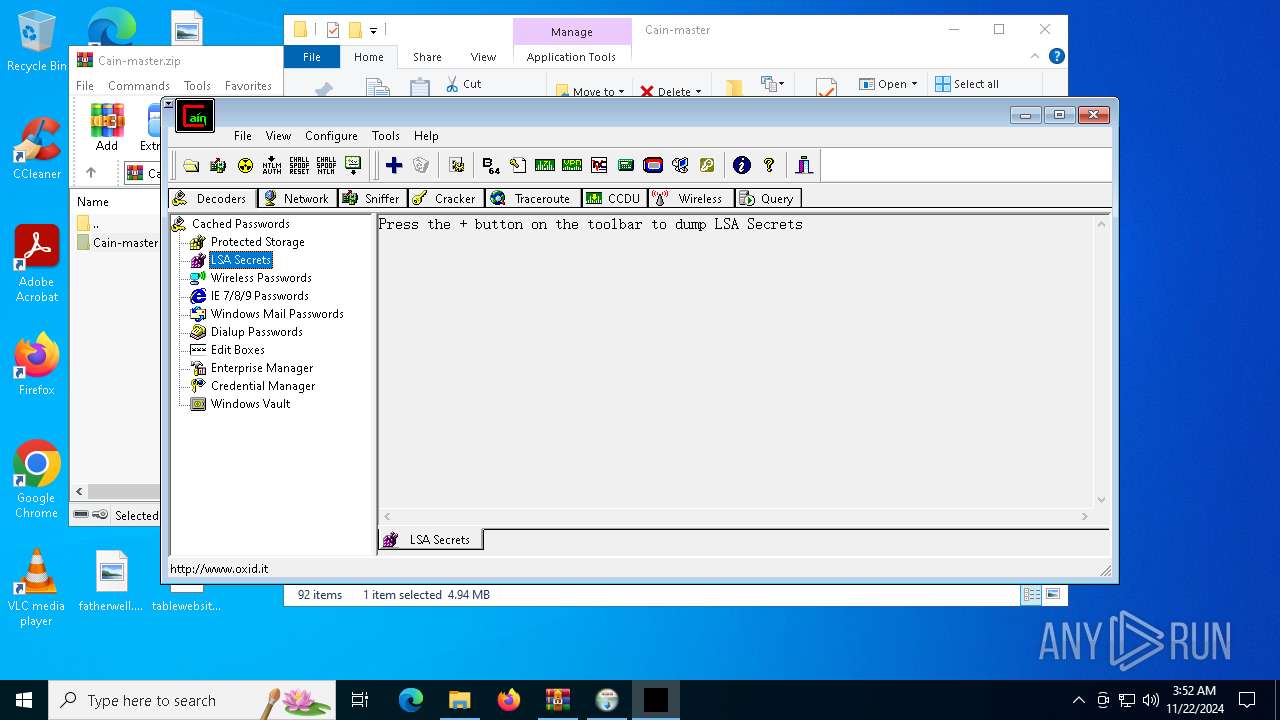
MIMIKATZ has been detected (YARA)
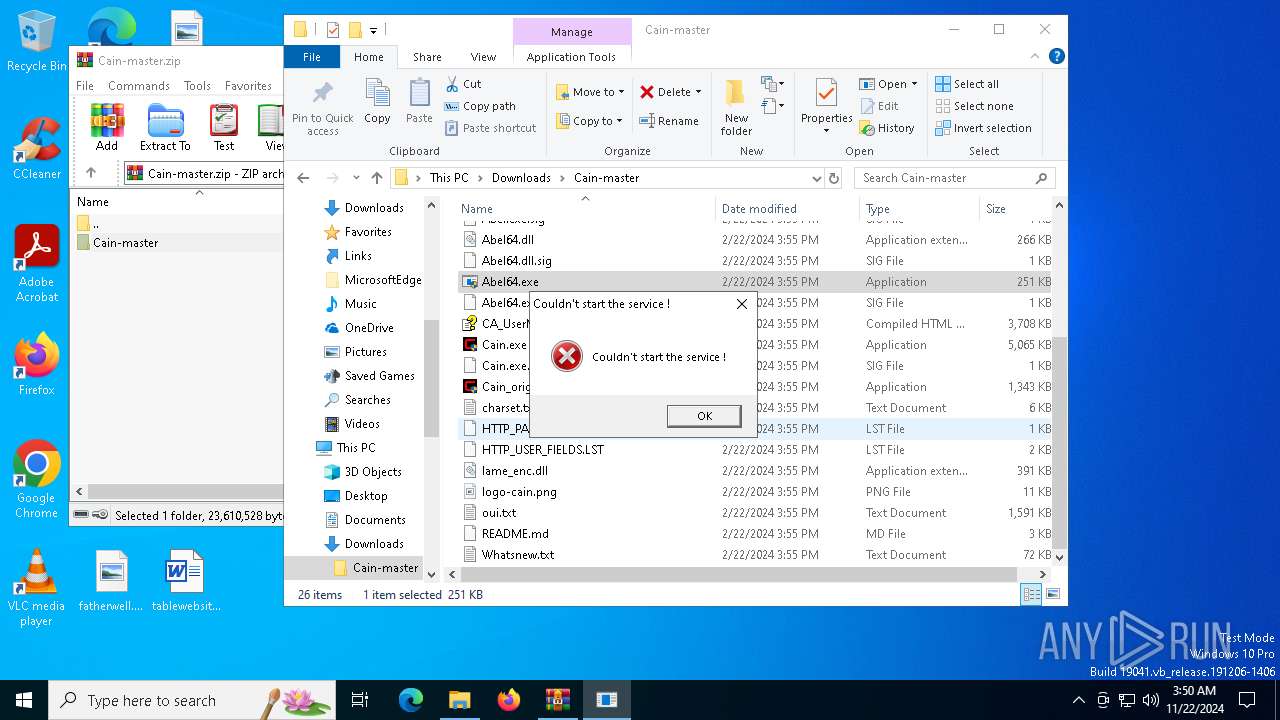
- Cain.exe (PID: 5936)
SUSPICIOUS
The process drops C-runtime libraries
- WinRAR.exe (PID: 3912)
Process drops legitimate windows executable
- WinRAR.exe (PID: 3912)
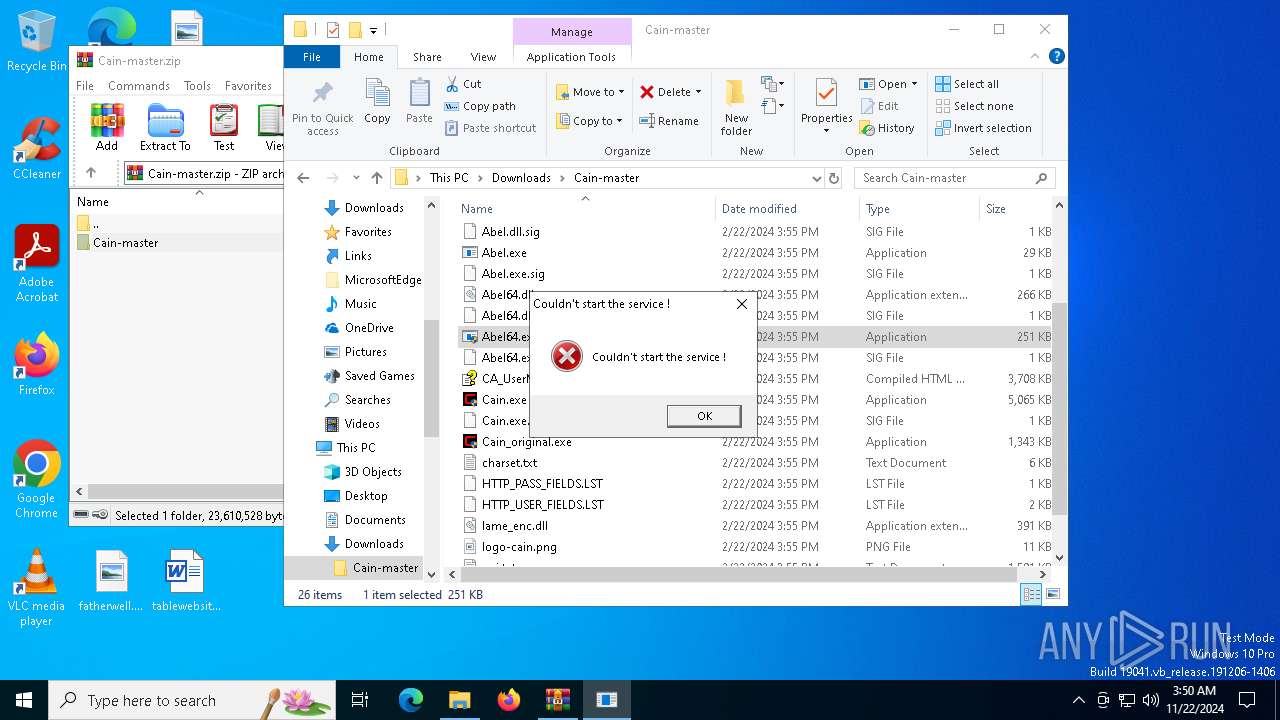
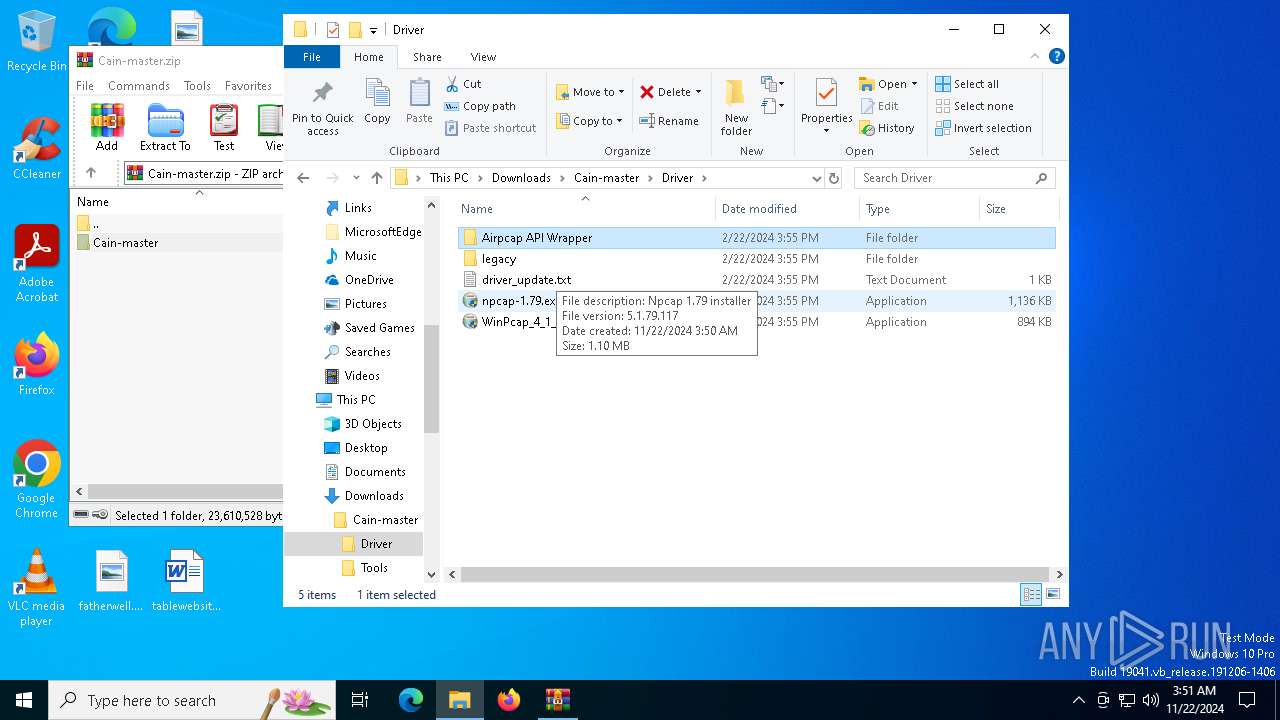
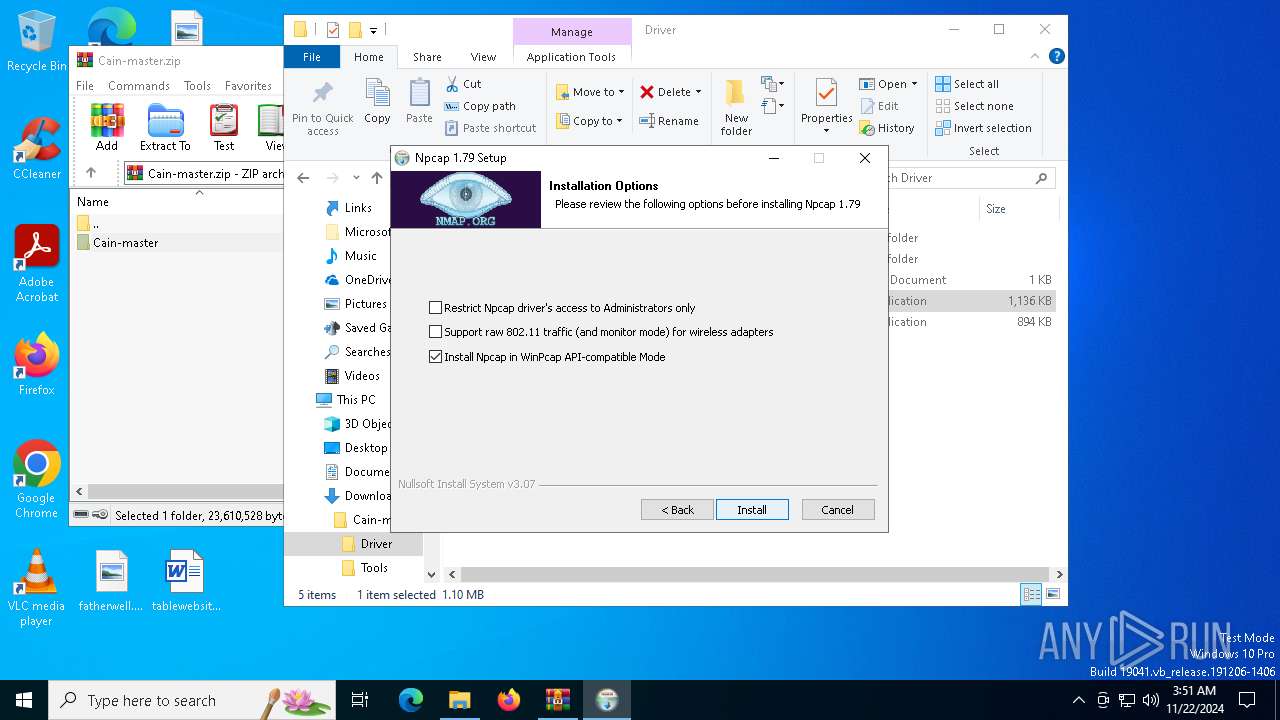
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 3912)
- npcap-1.79.exe (PID: 5100)
- drvinst.exe (PID: 7132)
- NPFInstall.exe (PID: 6956)
The process bypasses the loading of PowerShell profile settings
- npcap-1.79.exe (PID: 5100)
Starts POWERSHELL.EXE for commands execution
- npcap-1.79.exe (PID: 5100)
Malware-specific behavior (creating "System.dll" in Temp)
- npcap-1.79.exe (PID: 5100)
Executable content was dropped or overwritten
- npcap-1.79.exe (PID: 5100)
- drvinst.exe (PID: 7132)
- NPFInstall.exe (PID: 6956)
The process hide an interactive prompt from the user
- npcap-1.79.exe (PID: 5100)
Removes files via Powershell
- powershell.exe (PID: 6252)
- powershell.exe (PID: 6476)
INFO
Manual execution by a user
- Abel.exe (PID: 6424)
- Cain.exe (PID: 6564)
- Abel.exe (PID: 6276)
- Cain.exe (PID: 6612)
- Abel64.exe (PID: 6516)
- Abel64.exe (PID: 6468)
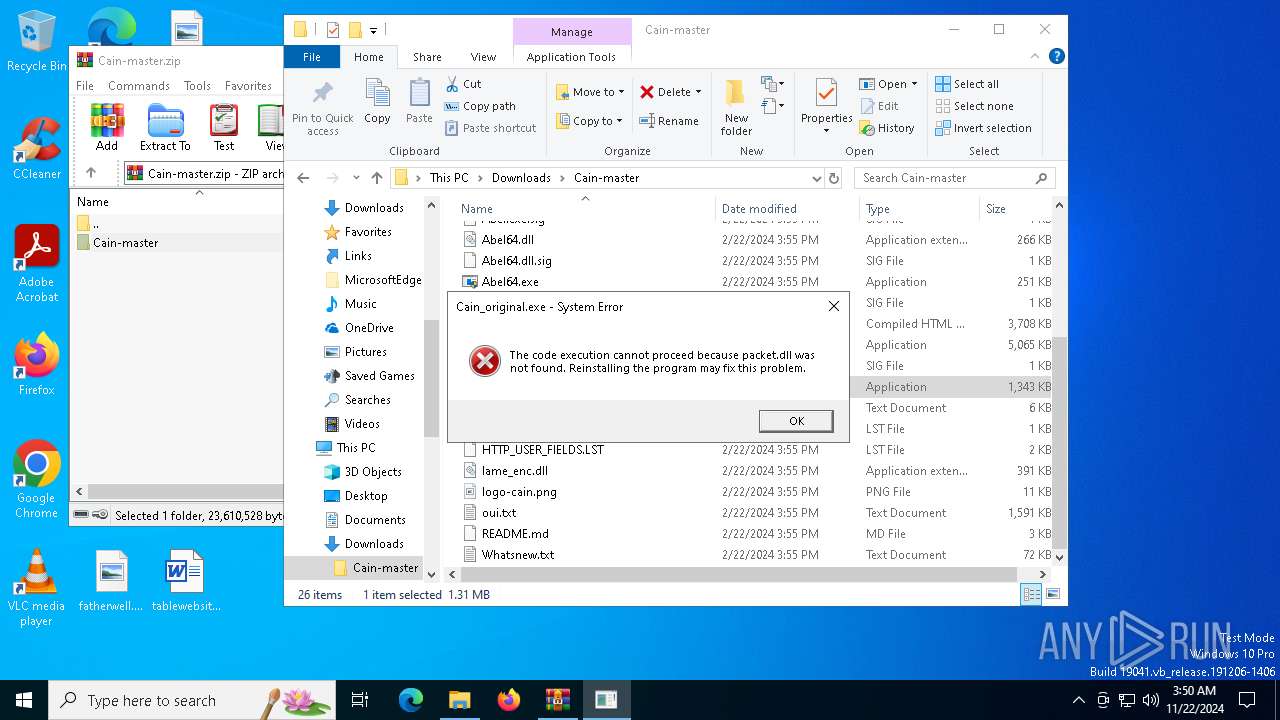
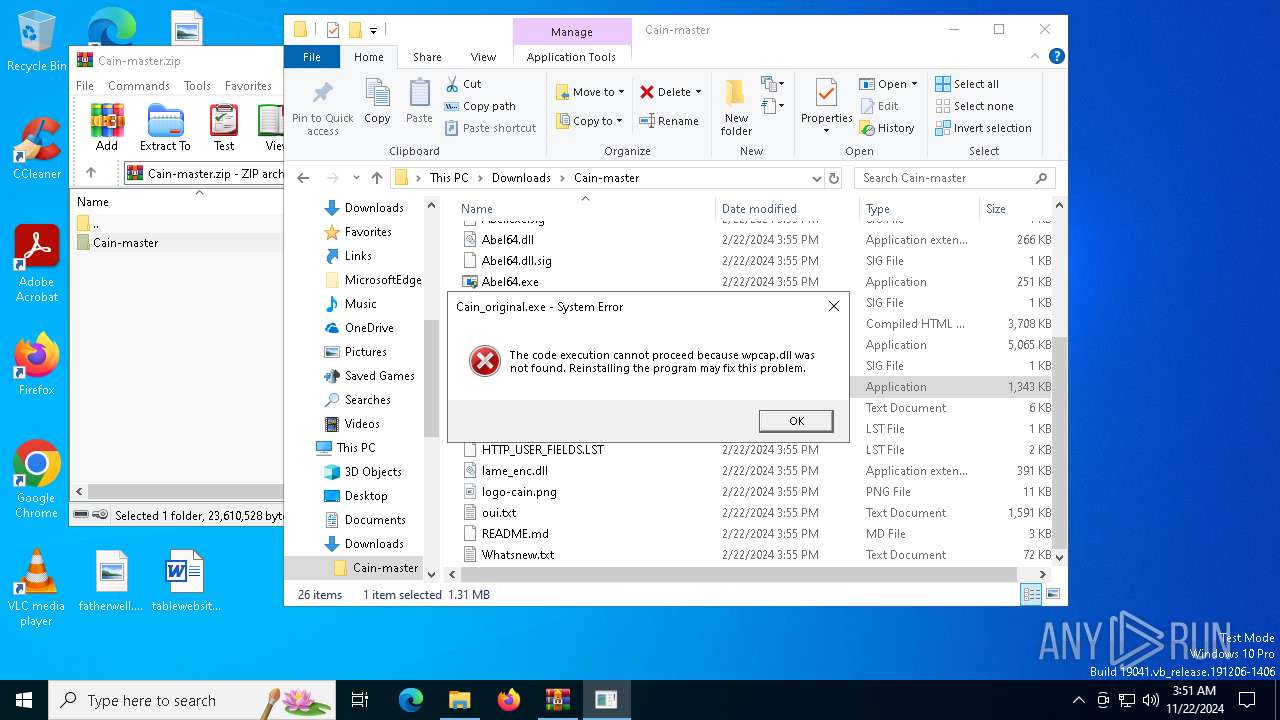
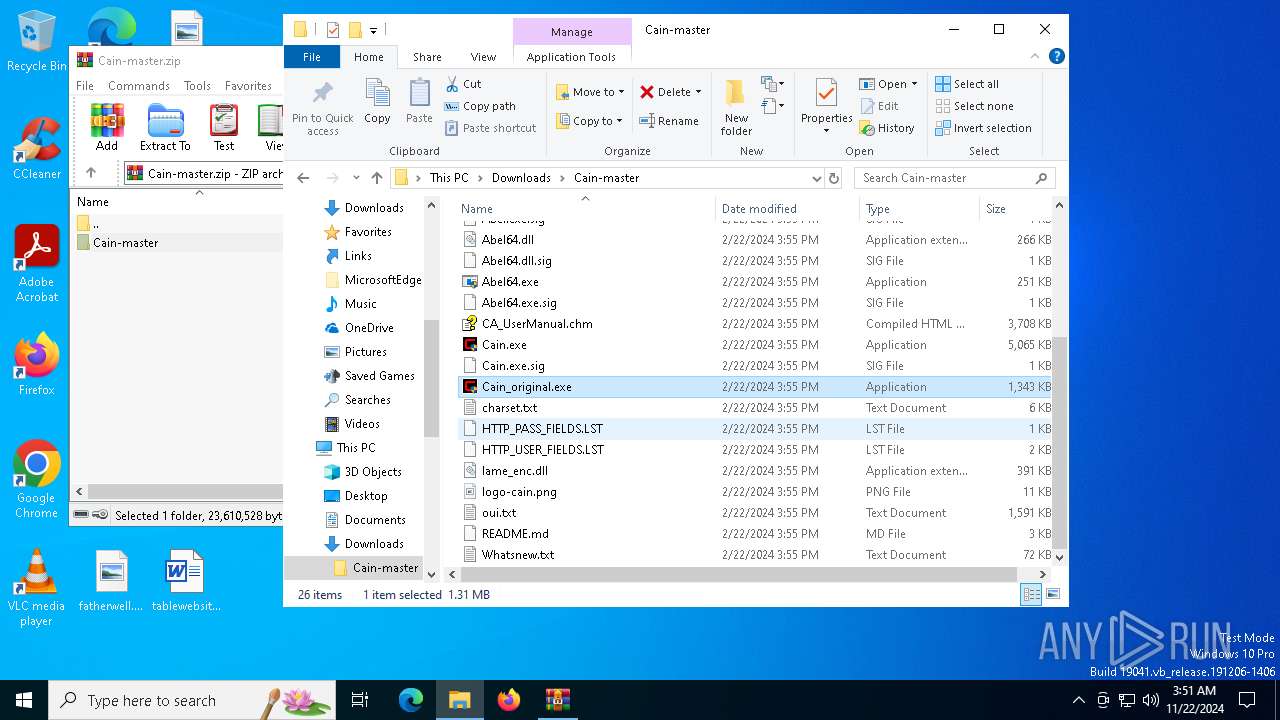
- Cain_original.exe (PID: 6692)
- Cain_original.exe (PID: 6740)
- notepad.exe (PID: 6652)
- Abel.exe (PID: 6772)
- Abel64.exe (PID: 6856)
- Abel64.exe (PID: 6808)
- Cain.exe (PID: 6896)
- Cain.exe (PID: 6944)
- Cain_original.exe (PID: 7028)
- Cain_original.exe (PID: 7076)
- Cain.exe (PID: 7108)
- Cain.exe (PID: 7156)
- npcap-1.79.exe (PID: 5100)
- npcap-1.79.exe (PID: 6156)
- Cain.exe (PID: 5936)
- Winrtgen.exe (PID: 3700)
- Winrtgen.exe (PID: 3524)
- Cain.exe (PID: 6276)
The process uses the downloaded file
- WinRAR.exe (PID: 3912)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3912)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:02:22 07:55:42 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Cain-master/ |
Total processes
190
Monitored processes
63
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | powershell.exe -NoProfile -WindowStyle Hidden -NonInteractive -Command "ScheduledTasks\Register-ScheduledTask -Force -TaskName 'npcapwatchdog' -Description 'Ensure Npcap service is configured to start at boot' -Action (ScheduledTasks\New-ScheduledTaskAction -Execute 'C:\Program Files\Npcap\CheckStatus.bat') -Principal (ScheduledTasks\New-ScheduledTaskPrincipal -UserId 'SYSTEM' -LogonType ServiceAccount) -Trigger (ScheduledTasks\New-ScheduledTaskTrigger -AtStartup) -Settings (ScheduledTasks\New-ScheduledTaskSettingsSet -AllowStartIfOnBatteries -Compatibility Win8)" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | npcap-1.79.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1140 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1472 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3524 | "C:\WINDOWS\system32\certutil.exe" -verifystore Root 0563b8630d62d75abbc8ab1e4bdfb5a899b24d43 | C:\Windows\SysWOW64\certutil.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 2148073489 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
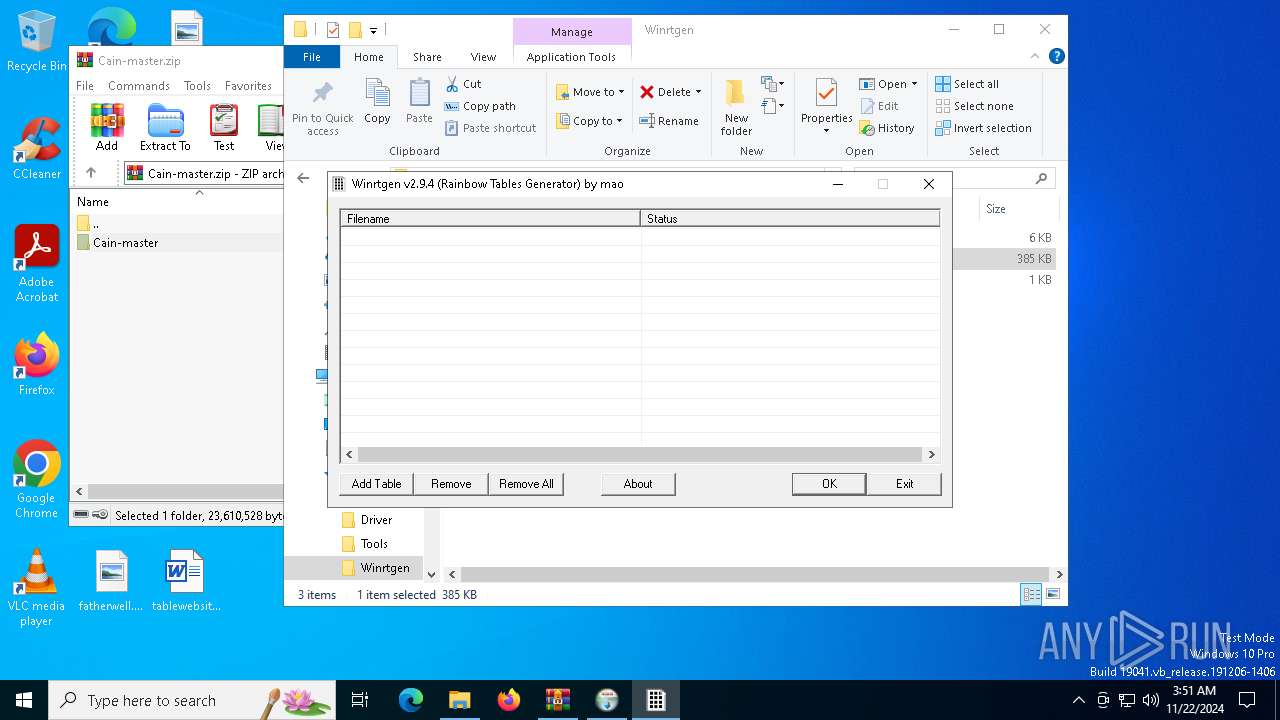
| 3524 | "C:\Users\admin\Downloads\Cain-master\Winrtgen\Winrtgen.exe" | C:\Users\admin\Downloads\Cain-master\Winrtgen\Winrtgen.exe | explorer.exe | ||||||||||||
User: admin Company: oxid.it Integrity Level: HIGH Description: Rainbow Tables Generator Exit code: 0 Version: 2, 9, 0, 4 | |||||||||||||||
| 3700 | "C:\Users\admin\Downloads\Cain-master\Winrtgen\Winrtgen.exe" | C:\Users\admin\Downloads\Cain-master\Winrtgen\Winrtgen.exe | — | explorer.exe | |||||||||||
User: admin Company: oxid.it Integrity Level: MEDIUM Description: Rainbow Tables Generator Exit code: 3221226540 Version: 2, 9, 0, 4 | |||||||||||||||
| 3912 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Cain-master.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4340 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | NPFInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4444 | powershell.exe -NoProfile -WindowStyle Hidden -NonInteractive -Command "Get-ChildItem Cert:\LocalMachine\Root | Where-Object {$_.Thumbprint -eq '0563b8630d62d75abbc8ab1e4bdfb5a899b24d43'} | Sort-Object -Descending -Property FriendlyName | Select-Object -Skip 1 | Remove-Item" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | npcap-1.79.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
49 647
Read events
49 544
Write events
69
Delete events
34
Modification events
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Cain-master.zip | |||
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
103
Suspicious files
39
Text files
73
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Cain-master\Cain-master\.gitattributes | text | |
MD5:01C2BA45B8CE4CB9D870B39204AAE551 | SHA256:BDBD68B106767972511720C3034130C2FFC1862C5ABC29BFE110BF82C5137383 | |||
| 3912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Cain-master\Cain-master\Abel64.dll | executable | |
MD5:DC0670DC01C6C8FDCD9AD95194FA723E | SHA256:6139689FC078EBCE7BEA5143BAE4F6D89344AE2FA3B6266A7C783F3A2FD2FD16 | |||
| 3912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Cain-master\Cain-master\.gitignore | text | |
MD5:94AF9B08018A807E6873053159ADC477 | SHA256:9687E9DDEF87E01683265A3AF7C501FDCFD5279281CA6B0D499EC7B251B23946 | |||
| 3912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Cain-master\Cain-master\Driver\Airpcap API Wrapper\Driver\msvcp110_32.dll | executable | |
MD5:3E29914113EC4B968BA5EB1F6D194A0A | SHA256:C8D5572CA8D7624871188F0ACABC3AE60D4C5A4F6782D952B9038DE3BC28B39A | |||
| 3912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Cain-master\Cain-master\Cain.exe | executable | |
MD5:D5EDB284374796EF5BA3DE00D90C43DF | SHA256:A0B918730CFA2804EF34E2DAE028DF3961DDA2DD267AA1130FC1A8430BE96355 | |||
| 3912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Cain-master\Cain-master\Abel64.exe.sig | fli | |
MD5:0DF87ED399A9CC3FB169025B957362E0 | SHA256:8338A27A9B1F7D4EF40C4213DDC75641BCF7B00B3C1E2415C7E5409BC7C6B214 | |||
| 3912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Cain-master\Cain-master\Abel.exe | executable | |
MD5:ECBCBDE87B9837F89600F8F14F6A4914 | SHA256:A709F37B3A50608F2E9830F92EA25DA04BFA4F34D2EFECFD061DE9F29AF02427 | |||
| 3912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Cain-master\Cain-master\Abel.dll | executable | |
MD5:D7E4B380C5AFB4BCB5DA9B458D51685A | SHA256:C0EB5900760FA6F9CCF4257E5DFC40BFC8852342874EE8E7B6E5271C52ADA53F | |||
| 3912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Cain-master\Cain-master\CA_UserManual.chm | binary | |
MD5:C904361FBFD53714F8FF3B0ACF4EE476 | SHA256:9B71D0ED2A74B105AE3C8017FB5FE03124FC65539C867719A7062B964CD030B7 | |||
| 3912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Cain-master\Cain-master\Cain.exe.sig | fli | |
MD5:559FBE2DF522745619FA9AB9A7BA1A95 | SHA256:553EB386A04BB234E6331A14C8FF9355CFD414D6B8C52F28AF7B85A03D8373AD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
34
DNS requests
11
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3976 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4932 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 104.126.37.128:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |