| File name: | c9daca7de1b623867aee943a1d508573841f2584ffa91aaaf09de2a883d2733f.exe |
| Full analysis: | https://app.any.run/tasks/d8a94f89-bd02-4a16-8dcf-6b72723e3432 |
| Verdict: | Malicious activity |
| Analysis date: | May 01, 2024, 09:25:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 7A506A2E92BC66A9F64C2333A815E97A |
| SHA1: | A123F6C070F4258C481CB0B6C2B5D1403463E2FA |
| SHA256: | C9DACA7DE1B623867AEE943A1D508573841F2584FFA91AAAF09DE2A883D2733F |
| SSDEEP: | 98304:W3njVY6OUdcAFccO//cirLLuaj06dT92azIXajHMtHM8gGIOBYADTeLhl6GC1tLt:W3Hvn5irnuaA6GaPj+VgGIOYSTeLXo |
MALICIOUS
Drops the executable file immediately after the start
- c9daca7de1b623867aee943a1d508573841f2584ffa91aaaf09de2a883d2733f.exe (PID: 5944)
Changes the autorun value in the registry
- c9daca7de1b623867aee943a1d508573841f2584ffa91aaaf09de2a883d2733f.exe (PID: 5944)
- cleaner.exe (PID: 5840)
Changes the login/logoff helper path in the registry
- c9daca7de1b623867aee943a1d508573841f2584ffa91aaaf09de2a883d2733f.exe (PID: 5944)
- cleaner.exe (PID: 5840)
SUSPICIOUS
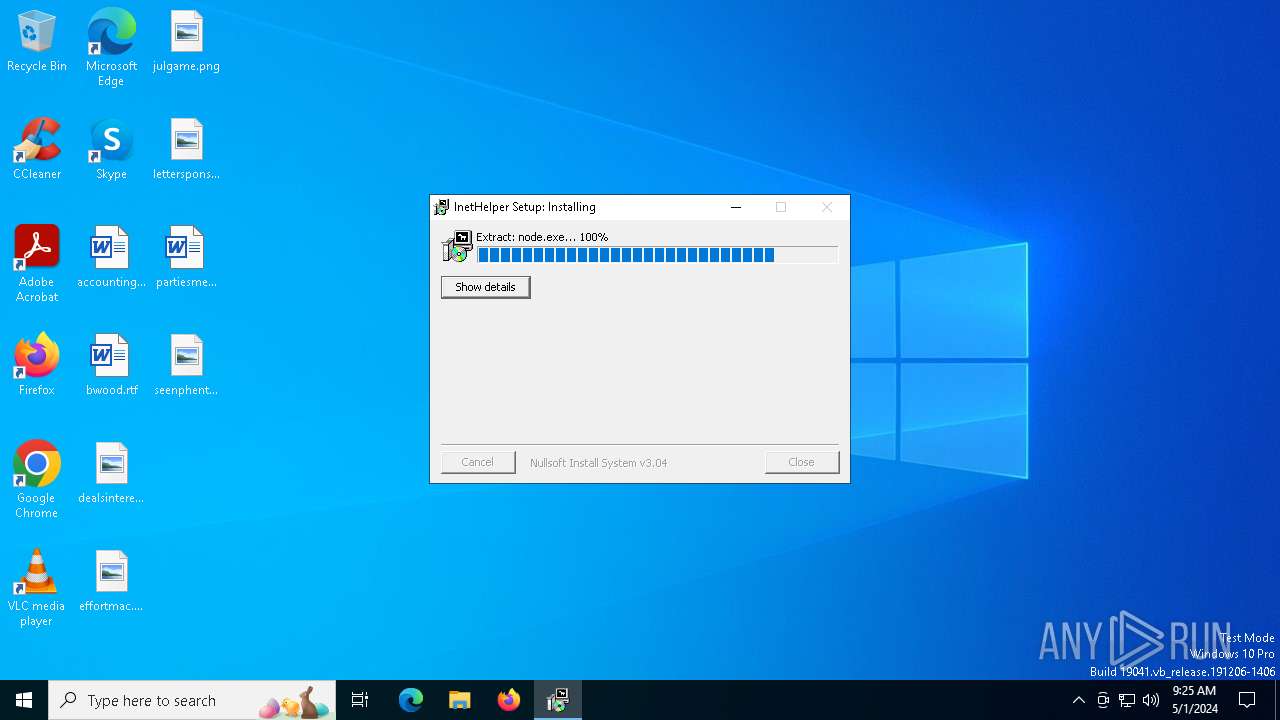
Node.exe was dropped
- c9daca7de1b623867aee943a1d508573841f2584ffa91aaaf09de2a883d2733f.exe (PID: 5944)
Executable content was dropped or overwritten
- c9daca7de1b623867aee943a1d508573841f2584ffa91aaaf09de2a883d2733f.exe (PID: 5944)
Executes script using NodeJS
- node.exe (PID: 4924)
Potential Corporate Privacy Violation
- node.exe (PID: 4924)
Connects to unusual port
- node.exe (PID: 4924)
Uses WMIC.EXE
- node.exe (PID: 4924)
Uses WMIC.EXE to obtain network information
- node.exe (PID: 4924)
INFO
Creates files or folders in the user directory
- c9daca7de1b623867aee943a1d508573841f2584ffa91aaaf09de2a883d2733f.exe (PID: 5944)
- cleaner.exe (PID: 5840)
Checks supported languages
- c9daca7de1b623867aee943a1d508573841f2584ffa91aaaf09de2a883d2733f.exe (PID: 5944)
- cleaner.exe (PID: 5840)
- node.exe (PID: 4924)
Reads the computer name
- c9daca7de1b623867aee943a1d508573841f2584ffa91aaaf09de2a883d2733f.exe (PID: 5944)
- node.exe (PID: 4924)
Create files in a temporary directory
- c9daca7de1b623867aee943a1d508573841f2584ffa91aaaf09de2a883d2733f.exe (PID: 5944)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 308)
- WMIC.exe (PID: 3396)
- WMIC.exe (PID: 5936)
- WMIC.exe (PID: 3724)
- WMIC.exe (PID: 4124)
- WMIC.exe (PID: 1184)
- WMIC.exe (PID: 5076)
- WMIC.exe (PID: 1204)
- WMIC.exe (PID: 4704)
- WMIC.exe (PID: 1712)
- WMIC.exe (PID: 2764)
- WMIC.exe (PID: 4060)
- WMIC.exe (PID: 3724)
- WMIC.exe (PID: 4944)
- WMIC.exe (PID: 4928)
- WMIC.exe (PID: 5380)
Reads Environment values
- node.exe (PID: 4924)
Reads the software policy settings
- slui.exe (PID: 4124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:15 22:26:01+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 428544 |
| UninitializedDataSize: | 16384 |
| EntryPoint: | 0x34a5 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
163
Monitored processes
39
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 308 | wmic path Win32_NetworkAdapter where Index=10 get NetConnectionID,MACAddress /format:table | C:\Windows\SysWOW64\wbem\WMIC.exe | — | node.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 324 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 400 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe -Embedding | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 19.043.0304.0013 Modules
| |||||||||||||||
| 1184 | wmic path Win32_NetworkAdapterConfiguration where IPEnabled=true get DefaultIPGateway,GatewayCostMetric,IPConnectionMetric,Index /format:table | C:\Windows\SysWOW64\wbem\WMIC.exe | — | node.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | wmic path Win32_NetworkAdapter where Index=10 get NetConnectionID,MACAddress /format:table | C:\Windows\SysWOW64\wbem\WMIC.exe | — | node.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1712 | wmic path Win32_NetworkAdapterConfiguration where IPEnabled=true get DefaultIPGateway,GatewayCostMetric,IPConnectionMetric,Index /format:table | C:\Windows\SysWOW64\wbem\WMIC.exe | — | node.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 103
Read events
10 098
Write events
5
Delete events
0
Modification events
| (PID) Process: | (5944) c9daca7de1b623867aee943a1d508573841f2584ffa91aaaf09de2a883d2733f.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Shell |
Value: explorer.exe,"C:\Users\admin\AppData\Local\Microsoft\Windows\InetHelper\cleaner.exe" | |||
| (PID) Process: | (5944) c9daca7de1b623867aee943a1d508573841f2584ffa91aaaf09de2a883d2733f.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | InetHelper |
Value: "C:\Users\admin\AppData\Local\Microsoft\Windows\InetHelper\cleaner.exe" | |||
| (PID) Process: | (5840) cleaner.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Shell |
Value: explorer.exe,"C:\Users\admin\AppData\Local\Microsoft\Windows\InetHelper\cleaner.exe" | |||
| (PID) Process: | (5840) cleaner.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | InetHelper |
Value: "C:\Users\admin\AppData\Local\Microsoft\Windows\InetHelper\cleaner.exe" | |||
| (PID) Process: | (4768) slui.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\sppcomapi.dll,-3200 |
Value: Software Licensing | |||
Executable files
2
Suspicious files
3
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5944 | c9daca7de1b623867aee943a1d508573841f2584ffa91aaaf09de2a883d2733f.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\InetHelper.status | — | |
MD5:— | SHA256:— | |||
| 5944 | c9daca7de1b623867aee943a1d508573841f2584ffa91aaaf09de2a883d2733f.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\InetHelper\vp | — | |
MD5:— | SHA256:— | |||
| 5944 | c9daca7de1b623867aee943a1d508573841f2584ffa91aaaf09de2a883d2733f.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\InetHelper\node.exe | executable | |
MD5:5F40521D2E1082FE1C734610C4A83911 | SHA256:79AC7AE94231A392D27F303418E305A60C4194DBBE143C5DEFFC977C7B2E7A78 | |||
| 5944 | c9daca7de1b623867aee943a1d508573841f2584ffa91aaaf09de2a883d2733f.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\InetHelper\service.js | binary | |
MD5:42FB0FA52C2E0BBBDF379C1ABA97D12E | SHA256:3DB6FFA48CAE2DBDC68F9BF5EE75BA5B7ABD4F923C5FC6741477916957909071 | |||
| 624 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2024-05-01.0926.624.1.aodl | binary | |
MD5:28DCA2FF4B34B5A52A2E59DF202A6ED3 | SHA256:33BACCB7296F1ED1F995FC77A23049F261CF391AC0388F9E8DD161F8C17B7F94 | |||
| 624 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2024-05-01.0926.624.1.odl | binary | |
MD5:8E5315C47BBE65C442CE8919B282DE25 | SHA256:0053E7E8CC9F870CCFED384E357397C0301EF58B7BEDBDFC875DEE600119CAF0 | |||
| 5944 | c9daca7de1b623867aee943a1d508573841f2584ffa91aaaf09de2a883d2733f.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\InetHelper\cleaner.exe | executable | |
MD5:E9DED10DFF258F6522FE9079ED3319CA | SHA256:EA1D61984EDE5908E0840E91A71BB127EFD62D836C1F76702B426FD79B57F780 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
54
DNS requests
23
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4924 | node.exe | GET | 101 | 57.129.16.154:6101 | http://register.nflxso.ca:6101/strvn | unknown | — | — | unknown |
5576 | svchost.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
4924 | node.exe | GET | 301 | 104.21.1.239:80 | http://files.nflxso.ca/downloads/winapp/latest-version.txt | unknown | — | — | unknown |
4680 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
6036 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
528 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
1744 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
1744 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4364 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5576 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
928 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5140 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4924 | node.exe | 57.129.16.154:6101 | register.nflxso.ca | — | FR | unknown |
4924 | node.exe | 104.21.1.239:80 | files.nflxso.ca | CLOUDFLARENET | — | unknown |
5576 | svchost.exe | 104.119.109.218:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
4924 | node.exe | 104.21.1.239:443 | files.nflxso.ca | CLOUDFLARENET | — | unknown |
4680 | SearchApp.exe | 2.23.209.185:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
register.nflxso.ca |
| malicious |
settings-win.data.microsoft.com |
| whitelisted |
files.nflxso.ca |
| unknown |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4924 | node.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Websocket to External Network |
1 ETPRO signatures available at the full report