| File name: | bin.exe |
| Full analysis: | https://app.any.run/tasks/86ff66db-4615-4b7c-8880-10c159a5c19c |
| Verdict: | Malicious activity |
| Analysis date: | December 18, 2022, 16:31:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 6B33977ACF3E7D58B5E866D4732A2541 |
| SHA1: | AEA54FB39C45CE50EAD66E94B74268679A784D9E |
| SHA256: | C9D0DB6EC7A9ABE2915F825D15816E40ED6CA4FF51CE4166547C14BF9A9AA640 |
| SSDEEP: | 98304:tMzKLaV+TxFeT5EqRect9iKRViFtmSrepKIbed:tMz0aVMCi6aqm4SCpKIbed |
MALICIOUS
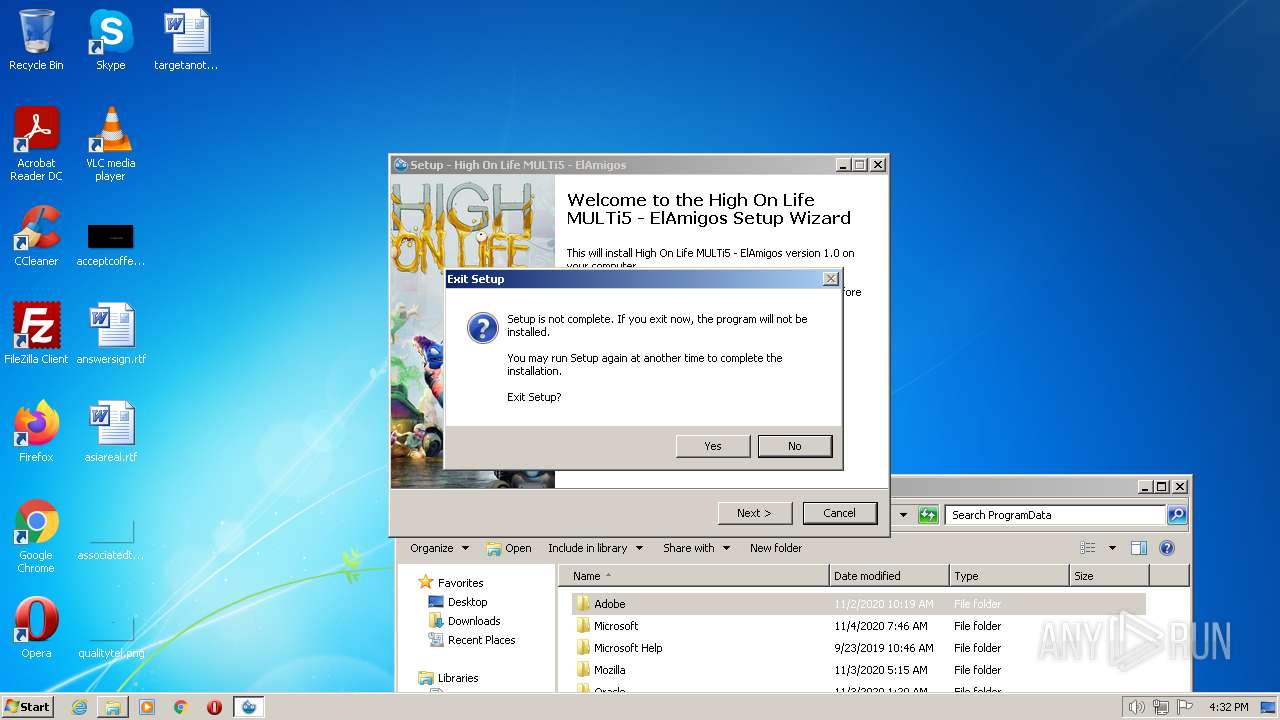
Drops the executable file immediately after the start
- bin.exe (PID: 856)
- bin.exe (PID: 3336)
- bin.tmp (PID: 2868)
SUSPICIOUS
Executable content was dropped or overwritten
- bin.exe (PID: 3336)
- bin.exe (PID: 856)
- bin.tmp (PID: 2868)
Reads the Windows owner or organization settings
- bin.tmp (PID: 2868)
Drops a file with too old compile date
- bin.tmp (PID: 2868)
INFO
Checks supported languages
- bin.exe (PID: 856)
- bin.tmp (PID: 2732)
- bin.tmp (PID: 2868)
- bin.exe (PID: 3336)
Reads the computer name
- bin.tmp (PID: 2732)
- bin.tmp (PID: 2868)
Application was dropped or rewritten from another process
- bin.tmp (PID: 2732)
- bin.tmp (PID: 2868)
Manual execution by a user
- explorer.exe (PID: 2852)
Drops a file that was compiled in debug mode
- bin.tmp (PID: 2868)
Loads dropped or rewritten executable
- bin.tmp (PID: 2868)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (57.2) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (18.2) |
| .exe | | | Win16/32 Executable Delphi generic (8.3) |
| .exe | | | Generic Win/DOS Executable (8) |
| .exe | | | DOS Executable Generic (8) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2014-Jul-09 07:58:13 |
| Detected languages: |
|
| Comments: | This installation was built with Inno Setup. |
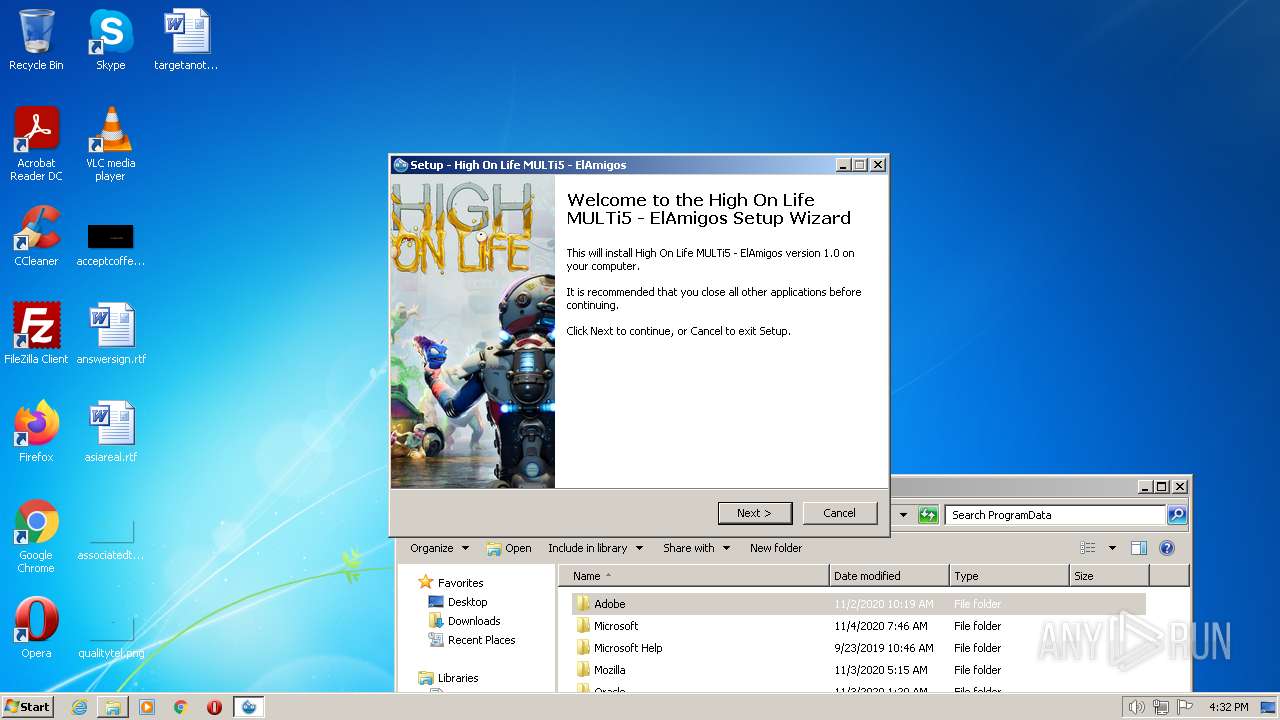
| CompanyName: | Squanch Games |
| FileDescription: | High On Life MULTi5 - ElAmigos Setup |
| FileVersion: | - |
| LegalCopyright: | - |
| ProductName: | High On Life MULTi5 - ElAmigos |
| ProductVersion: | 1.0 |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 80 |
| e_cp: | 2 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | 15 |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | 26 |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 256 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 8 |
| TimeDateStamp: | 2014-Jul-09 07:58:13 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 4096 | 61740 | 61952 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.39148 |
.itext | 69632 | 2884 | 3072 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.73207 |
.data | 73728 | 3208 | 3584 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.24631 |
.bss | 77824 | 22196 | 0 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.idata | 102400 | 3536 | 3584 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.97188 |
.tls | 106496 | 8 | 0 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.rdata | 110592 | 24 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0.204488 |
.rsrc | 114688 | 224532 | 224768 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.9501 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.48162 | 1128 | Latin 1 / Western European | English - United States | RT_ICON |
2 | 5.3564 | 2440 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 5.43591 | 4264 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 5.30909 | 9640 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 5.27106 | 16936 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 5.19066 | 38056 | Latin 1 / Western European | English - United States | RT_ICON |
7 | 5.16828 | 67624 | Latin 1 / Western European | English - United States | RT_ICON |
8 | 7.95904 | 43724 | Latin 1 / Western European | English - United States | RT_ICON |
4091 | 2.56031 | 104 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4092 | 3.25287 | 212 | Latin 1 / Western European | UNKNOWN | RT_STRING |
Imports
advapi32.dll |
advapi32.dll (#2) |
advapi32.dll (#3) |
comctl32.dll |
kernel32.dll |
kernel32.dll (#2) |
kernel32.dll (#3) |
kernel32.dll (#4) |
oleaut32.dll |
user32.dll |
Total processes
42
Monitored processes
5
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 856 | "C:\Users\admin\AppData\Local\Temp\bin.exe" | C:\Users\admin\AppData\Local\Temp\bin.exe | Explorer.EXE | ||||||||||||
User: admin Company: Squanch Games Integrity Level: MEDIUM Description: High On Life MULTi5 - ElAmigos Setup Exit code: 2 Version: Modules
| |||||||||||||||
| 2732 | "C:\Users\admin\AppData\Local\Temp\is-5VG5G.tmp\bin.tmp" /SL5="$50198,3055503,298496,C:\Users\admin\AppData\Local\Temp\bin.exe" | C:\Users\admin\AppData\Local\Temp\is-5VG5G.tmp\bin.tmp | — | bin.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 2 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2852 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2868 | "C:\Users\admin\AppData\Local\Temp\is-P73VC.tmp\bin.tmp" /SL5="$6019E,3055503,298496,C:\Users\admin\AppData\Local\Temp\bin.exe" /SPAWNWND=$501C8 /NOTIFYWND=$50198 | C:\Users\admin\AppData\Local\Temp\is-P73VC.tmp\bin.tmp | bin.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 2 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3336 | "C:\Users\admin\AppData\Local\Temp\bin.exe" /SPAWNWND=$501C8 /NOTIFYWND=$50198 | C:\Users\admin\AppData\Local\Temp\bin.exe | bin.tmp | ||||||||||||
User: admin Company: Squanch Games Integrity Level: HIGH Description: High On Life MULTi5 - ElAmigos Setup Exit code: 2 Version: Modules
| |||||||||||||||
Total events
1 650
Read events
1 636
Write events
6
Delete events
8
Modification events
| (PID) Process: | (2868) bin.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 340B0000B613343EFE12D901 | |||
| (PID) Process: | (2868) bin.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 344EA94A6865210D456CE09AAC4CA3583BF11E2C95DFDD4C696FEFF716AD9D9C | |||
| (PID) Process: | (2868) bin.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2868) bin.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2868) bin.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | SessionHash |
Value: 344EA94A6865210D456CE09AAC4CA3583BF11E2C95DFDD4C696FEFF716AD9D9C | |||
| (PID) Process: | (2868) bin.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Owner |
Value: 340B0000B613343EFE12D901 | |||
| (PID) Process: | (2868) bin.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
14
Suspicious files
0
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 856 | bin.exe | C:\Users\admin\AppData\Local\Temp\is-5VG5G.tmp\bin.tmp | executable | |
MD5:— | SHA256:— | |||
| 3336 | bin.exe | C:\Users\admin\AppData\Local\Temp\is-P73VC.tmp\bin.tmp | executable | |
MD5:— | SHA256:— | |||
| 2868 | bin.tmp | C:\Users\admin\AppData\Local\Temp\is-E7JG0.tmp\wintb.dll | executable | |
MD5:9436DF49E08C83BAD8DDC906478C2041 | SHA256:1910537AA95684142250CA0C7426A0B5F082E39F6FBDBDBA649AECB179541435 | |||
| 2868 | bin.tmp | C:\Users\admin\AppData\Local\Temp\is-E7JG0.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 2868 | bin.tmp | C:\Users\admin\AppData\Local\Temp\is-E7JG0.tmp\ISDone.dll | executable | |
MD5:4FEAFA8B5E8CDB349125C8AF0AC43974 | SHA256:BB8A0245DCC5C10A1C7181BAD509B65959855009A8105863EF14F2BB5B38AC71 | |||
| 2868 | bin.tmp | C:\Users\admin\AppData\Local\Temp\is-E7JG0.tmp\callbackctrl.dll | executable | |
MD5:F07E819BA2E46A897CFABF816D7557B2 | SHA256:68F42A7823ED7EE88A5C59020AC52D4BBCADF1036611E96E470D986C8FAA172D | |||
| 2868 | bin.tmp | C:\Users\admin\AppData\Local\Temp\is-E7JG0.tmp\_isetup\_iscrypt.dll | executable | |
MD5:A69559718AB506675E907FE49DEB71E9 | SHA256:2F6294F9AA09F59A574B5DCD33BE54E16B39377984F3D5658CDA44950FA0F8FC | |||
| 2868 | bin.tmp | C:\Users\admin\AppData\Local\Temp\is-E7JG0.tmp\1.ico | image | |
MD5:BCFD9F1E134DAB07B3D555F4078F1063 | SHA256:6FA58A4E79734E87057A92EFF2643BFAC9D4D92D7BC2ECB258BABE62239BA611 | |||
| 2868 | bin.tmp | C:\Users\admin\AppData\Local\Temp\is-E7JG0.tmp\3.ico | image | |
MD5:03623E728A8FF98BA17812B8AD1B00AB | SHA256:14BAE90A5AD2F623BBC0FB26FA31108F5340A120FDCA23A1608EC91C7EC8435D | |||
| 2868 | bin.tmp | C:\Users\admin\AppData\Local\Temp\is-E7JG0.tmp\2.ico | image | |
MD5:0EE990AF02BC758FD194844FFC1B66B1 | SHA256:34DD2954E50C46C600CC85C6AA6083813F995C6CAC0485498D3C172C13C51139 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report