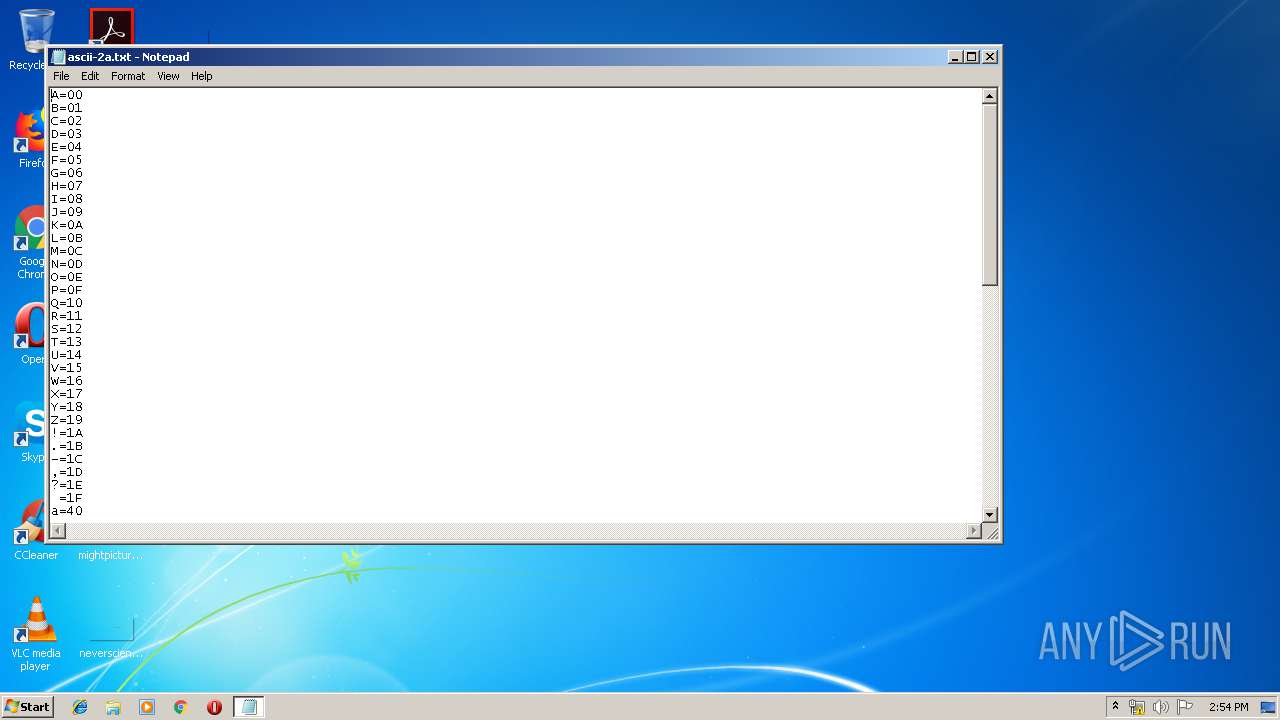
| File name: | ascii-2a.txt |
| Full analysis: | https://app.any.run/tasks/051fe0f4-2ccc-412a-b353-775c8ee5fd0e |
| Verdict: | Malicious activity |
| Analysis date: | June 16, 2019, 13:54:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ISO-8859 text, with CRLF line terminators |
| MD5: | CACA14E2CA992BF0F0878D52A035D123 |
| SHA1: | 965E96E2CD15C755173437A76D199A18FD1620A7 |
| SHA256: | C9C6D2A1BEF62C9331DFBBF8261D47E8342133657B2534FAE84DD33547DFD7DE |
| SSDEEP: | 12:sPHu91KlJynOhNyDCou+Ef0BR1Ge7K181VhyOhg:sPHu9UHyOX/rf0Pd97q |
MALICIOUS
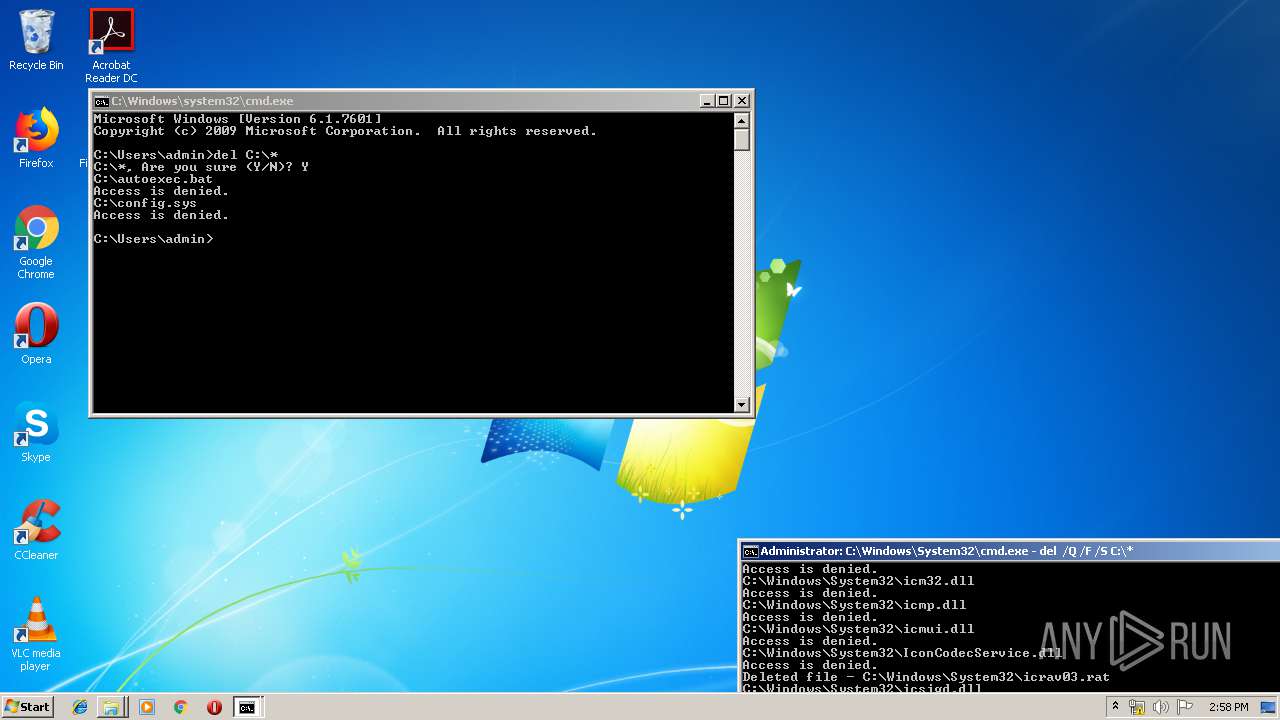
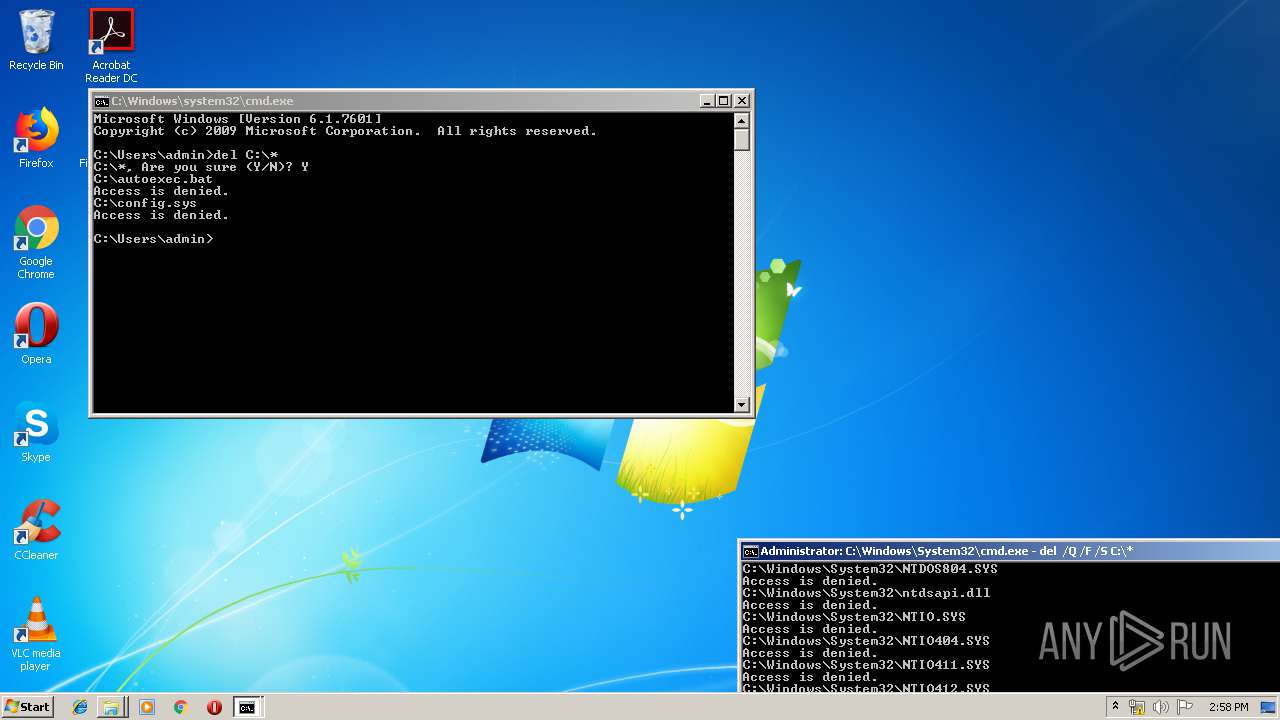
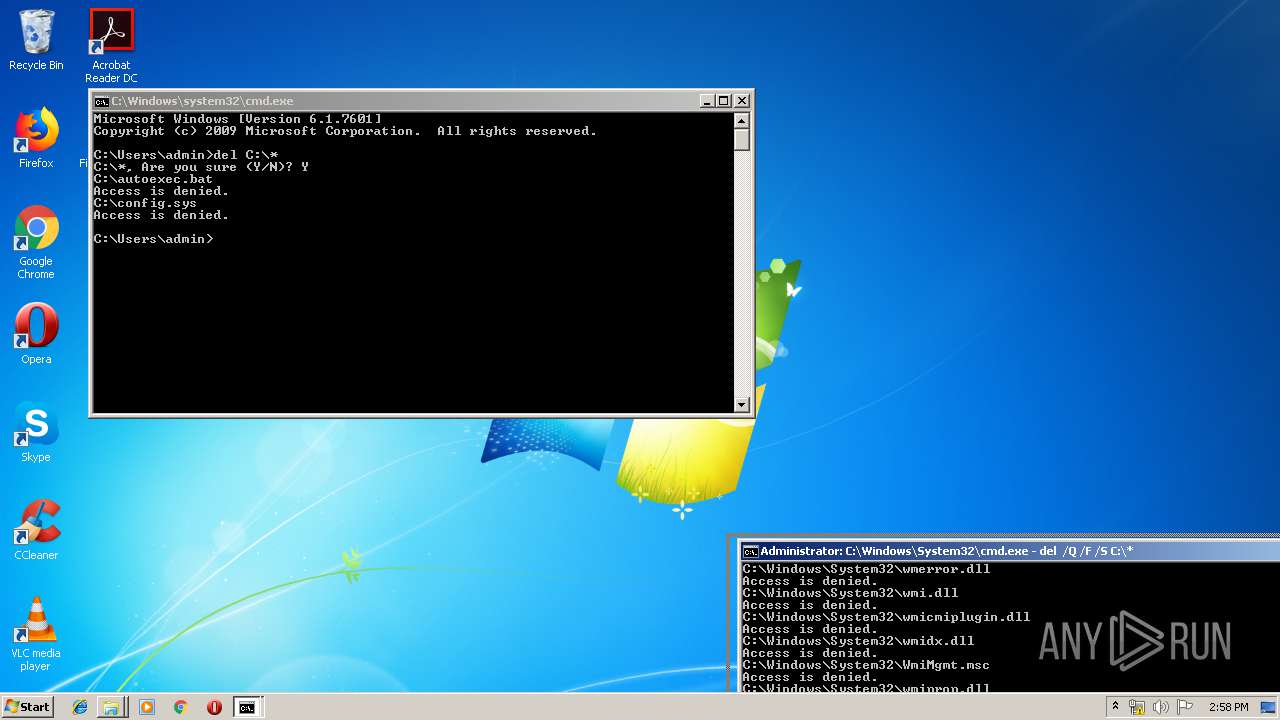
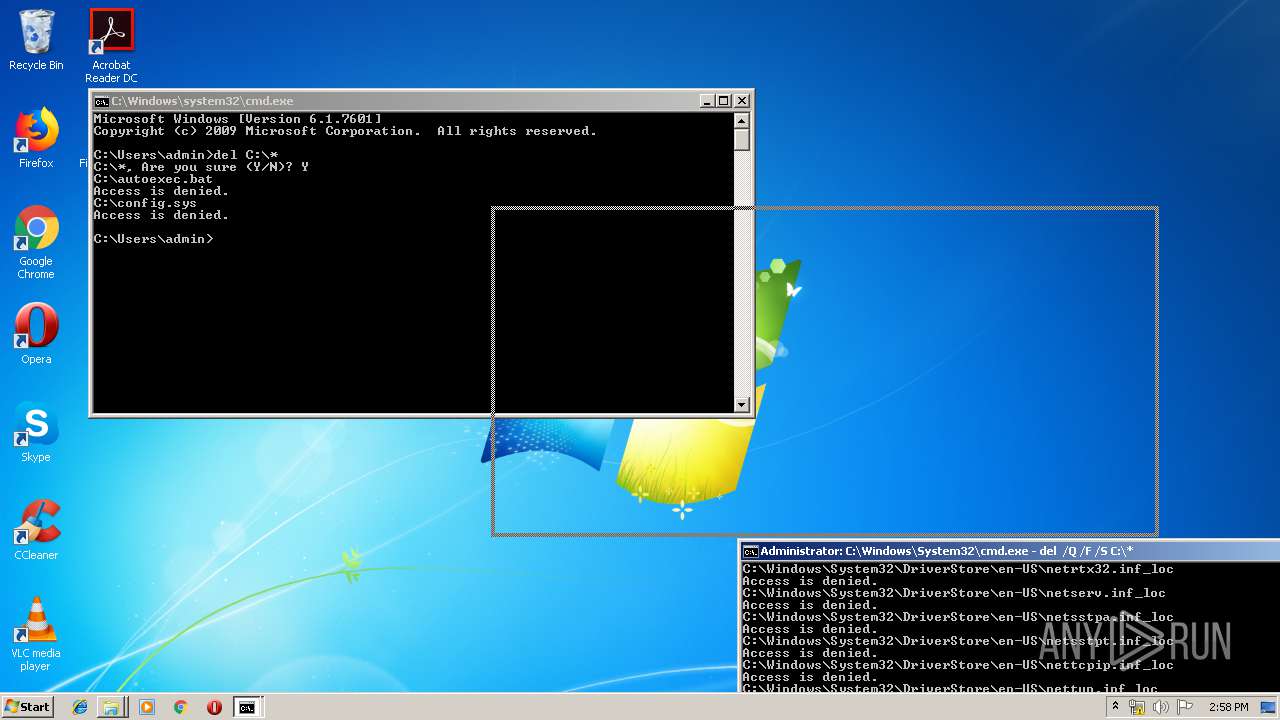
Actions looks like stealing of personal data
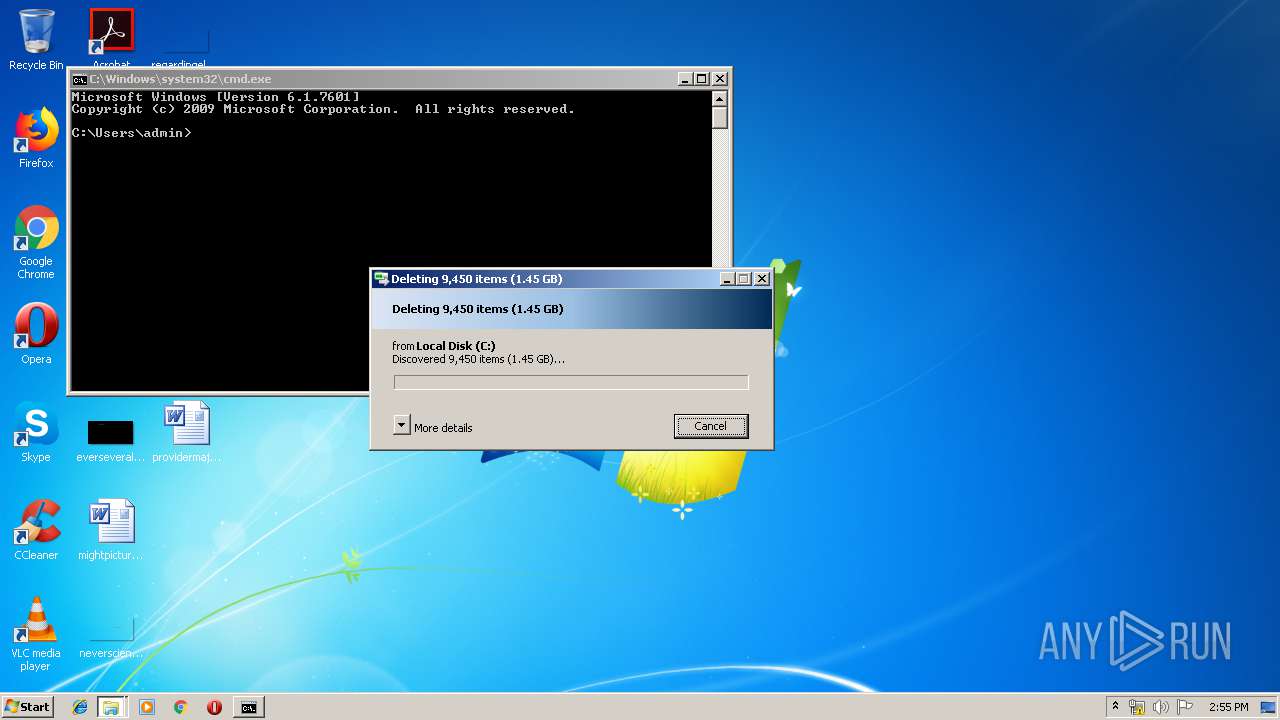
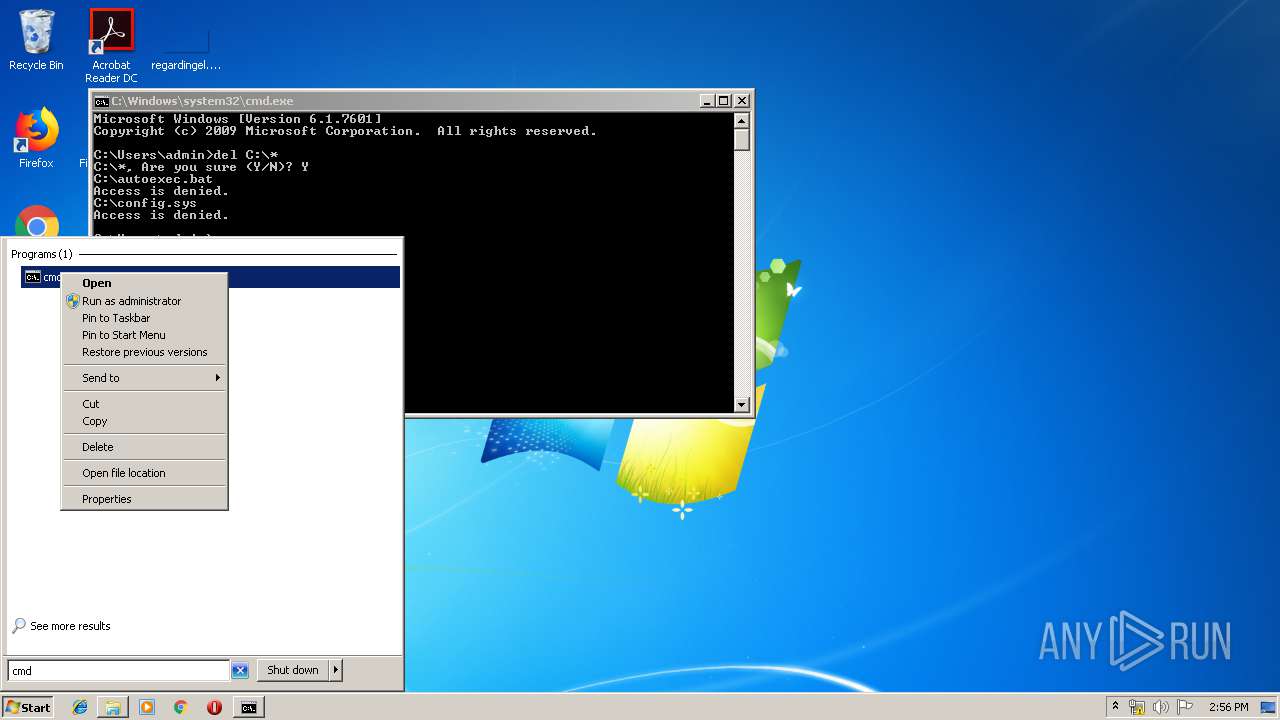
- cmd.exe (PID: 284)
SUSPICIOUS
Executed via COM
- DllHost.exe (PID: 3904)
- DllHost.exe (PID: 2976)
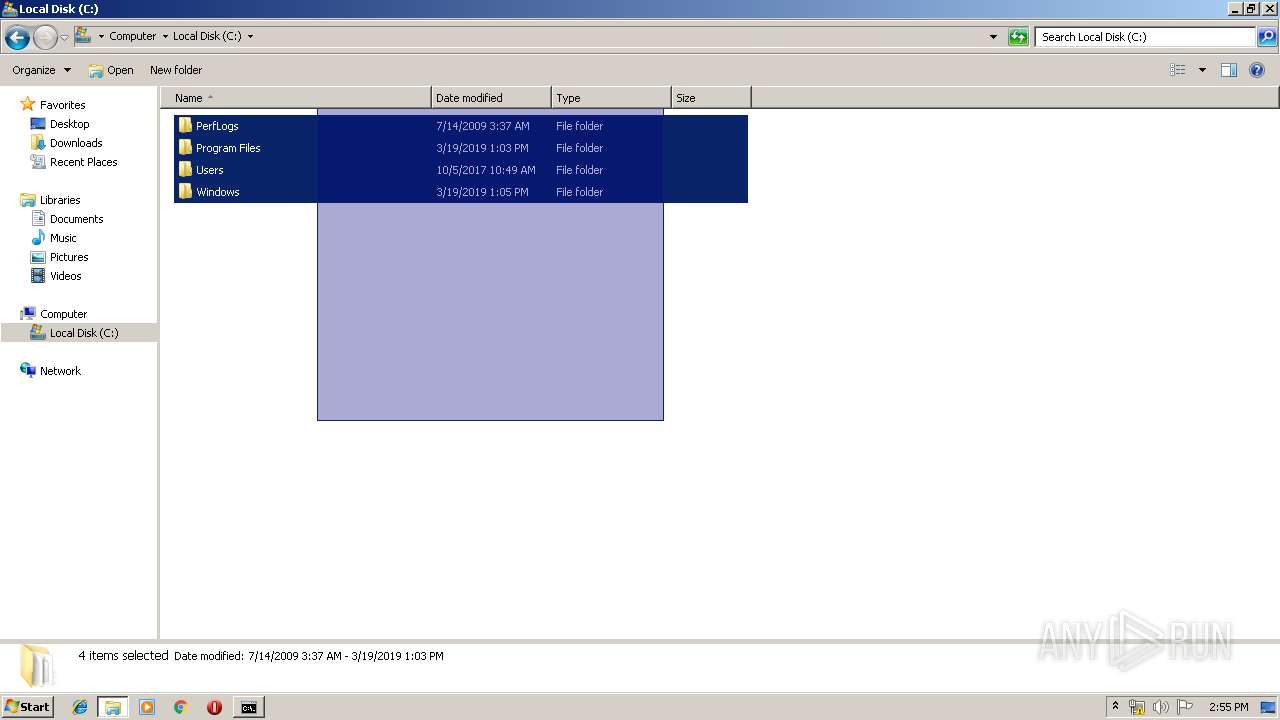
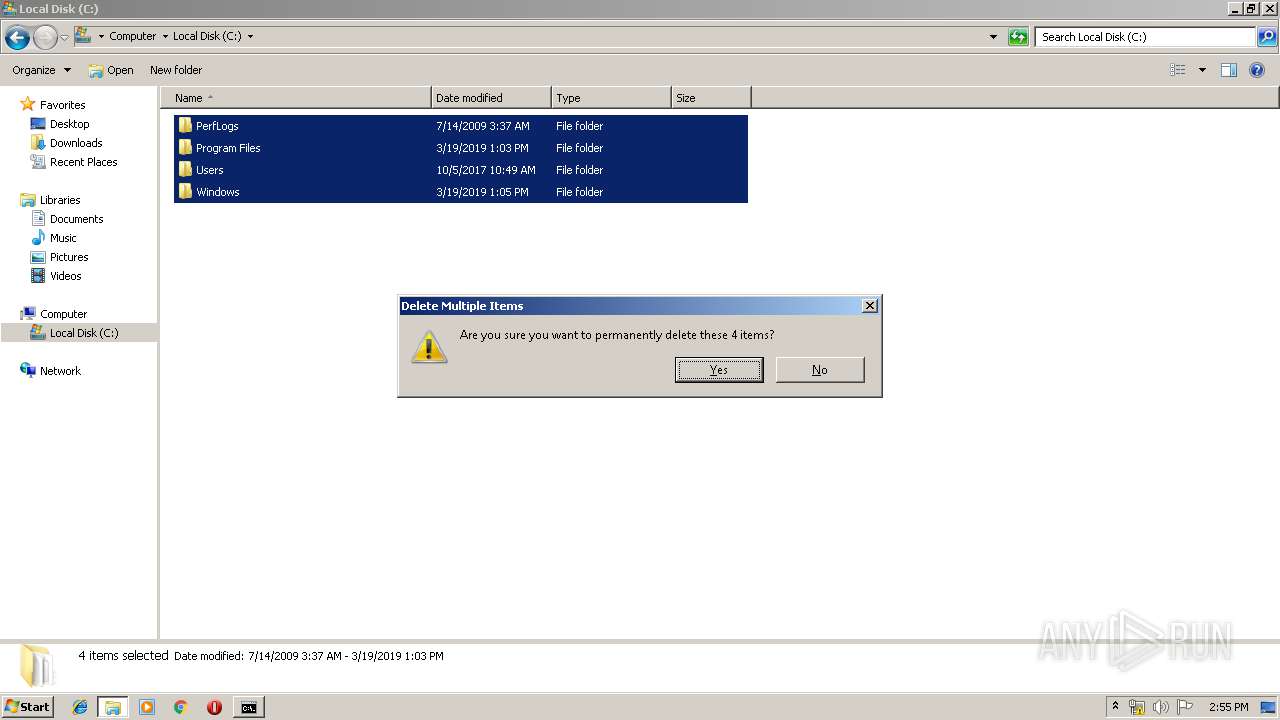
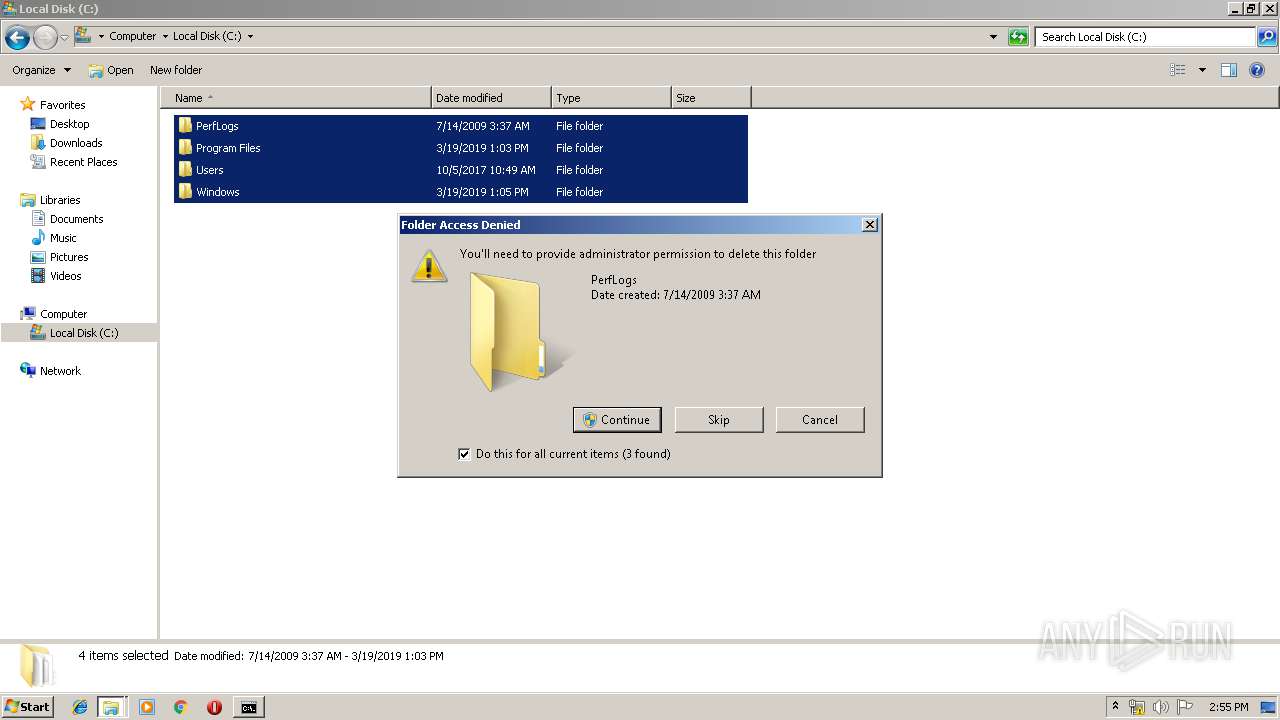
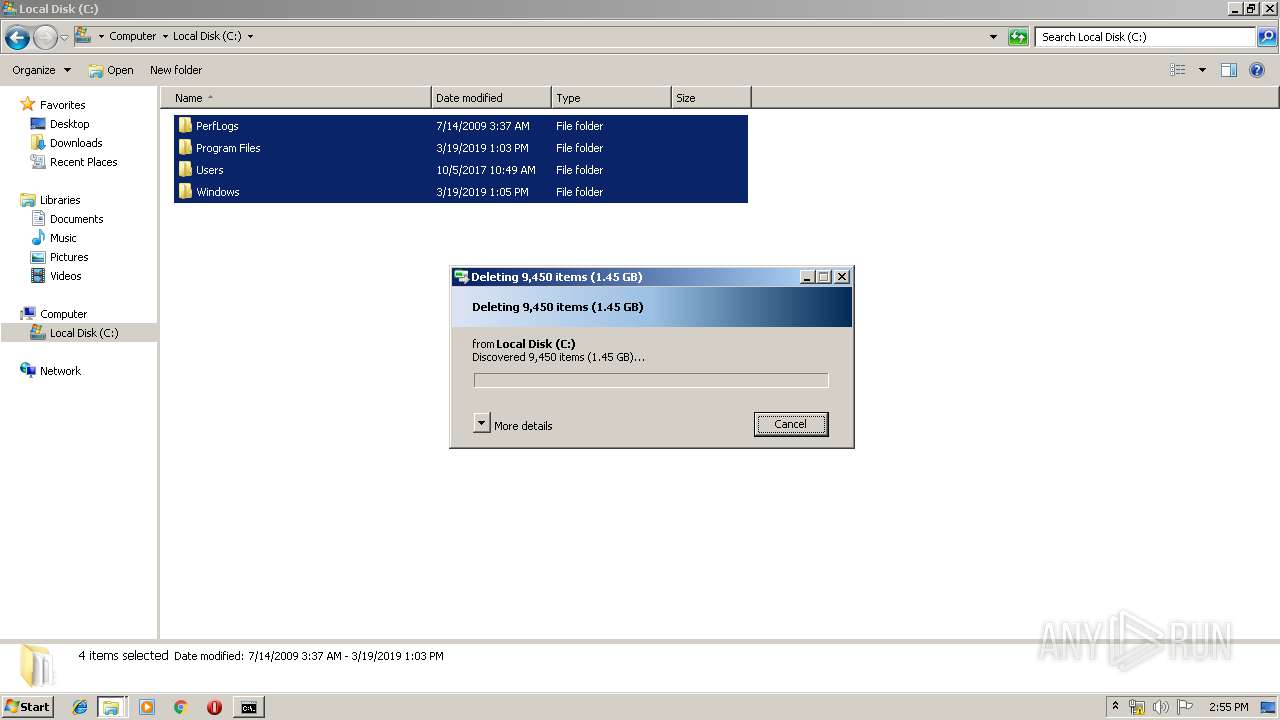
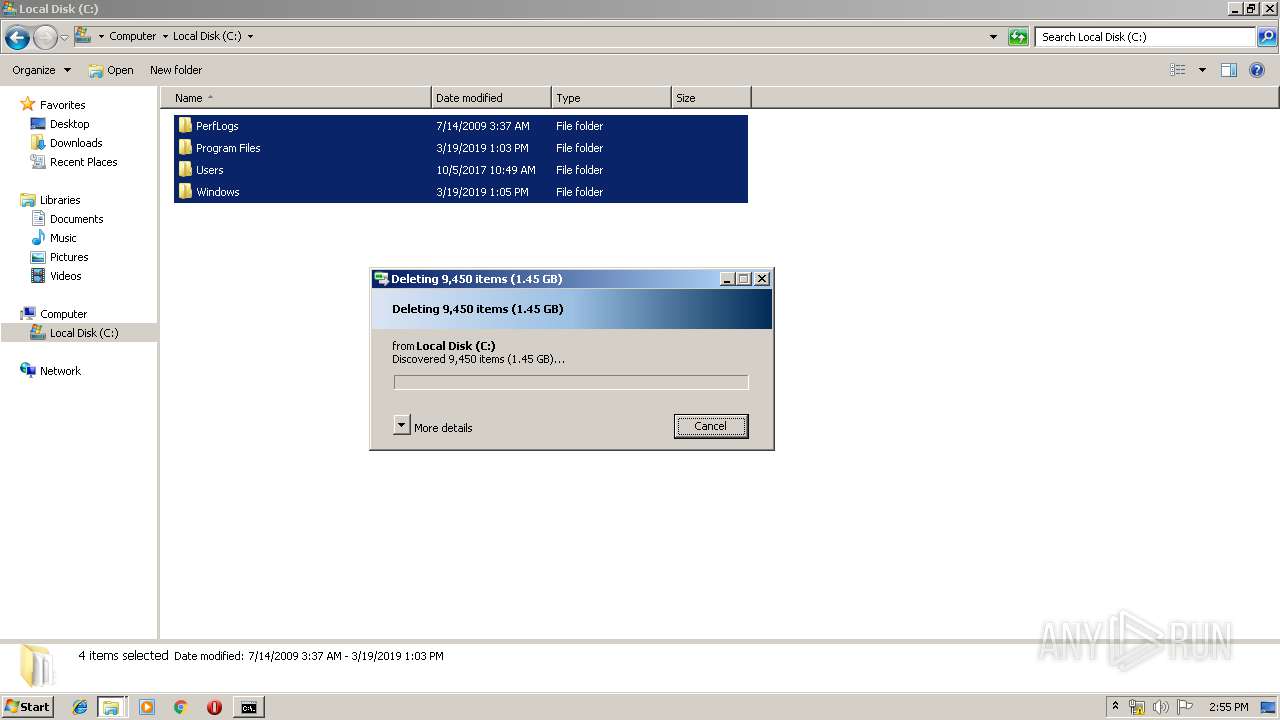
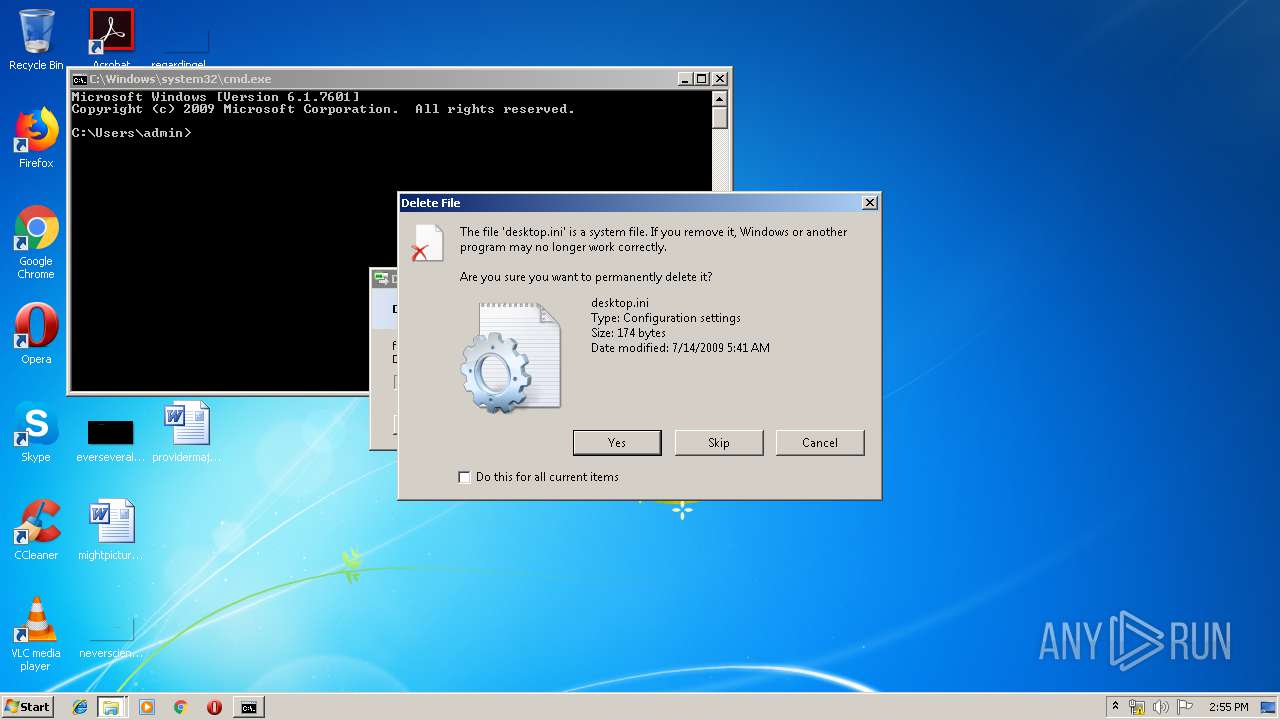
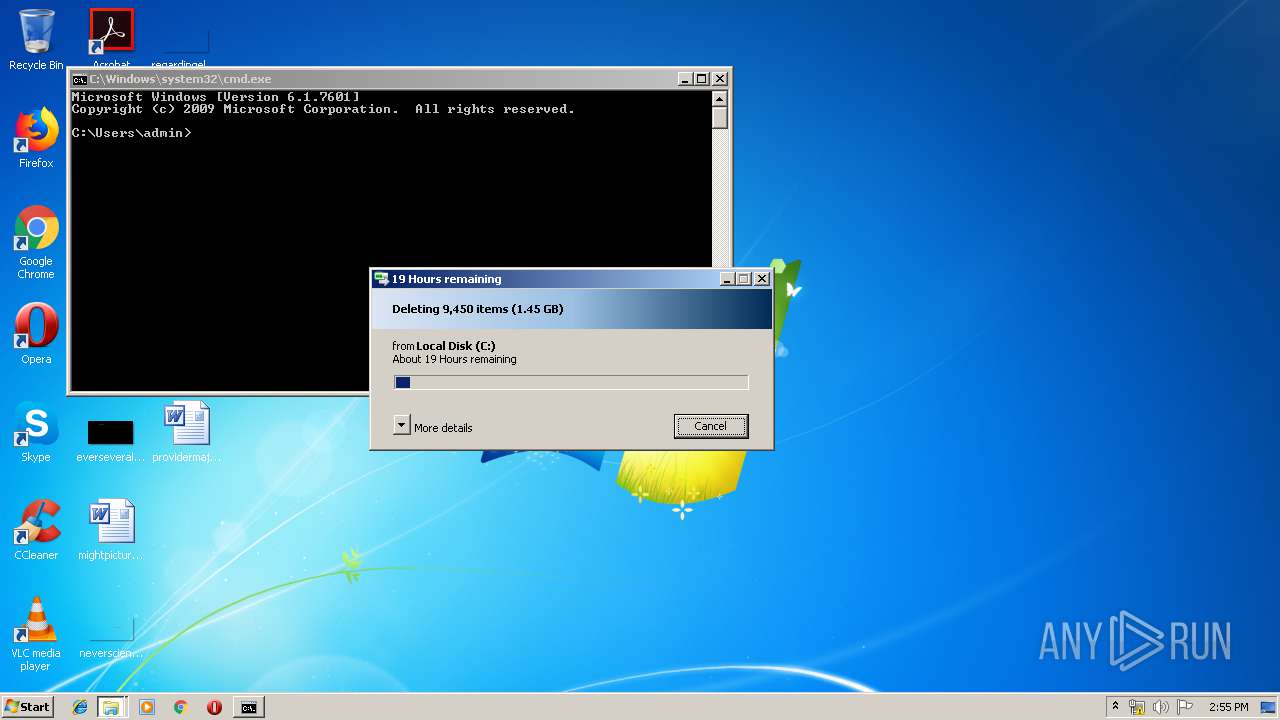
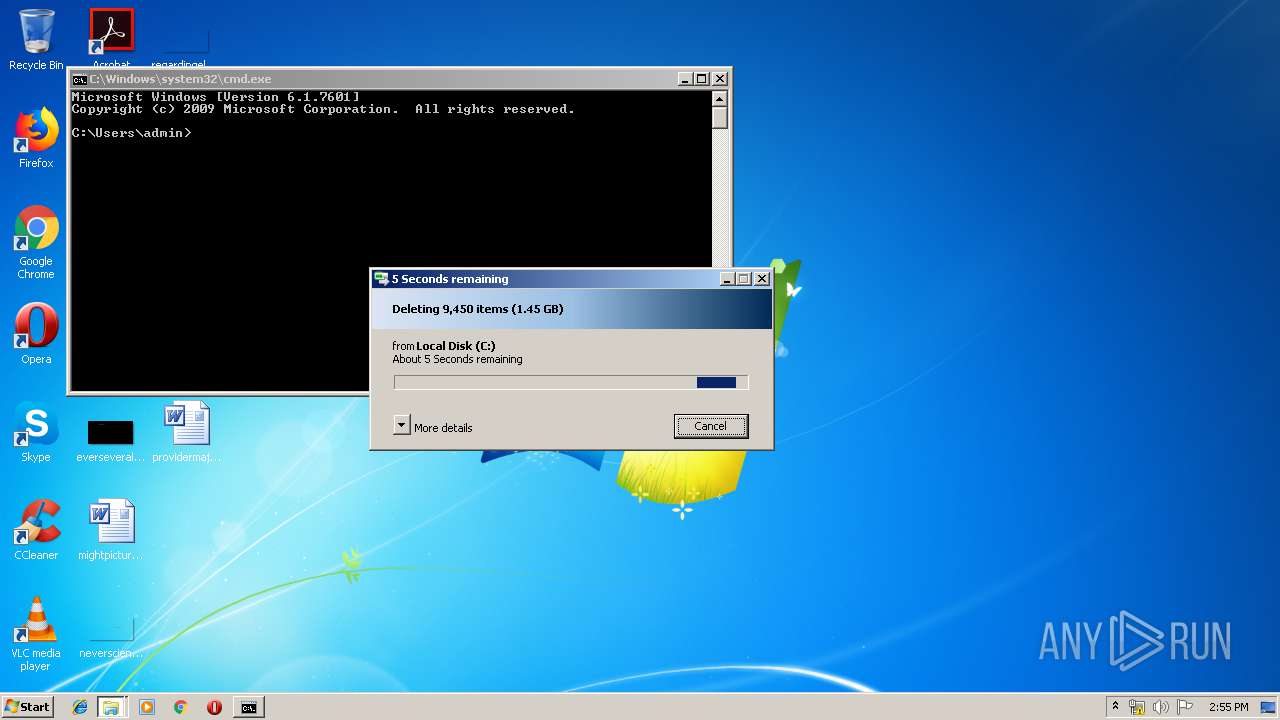
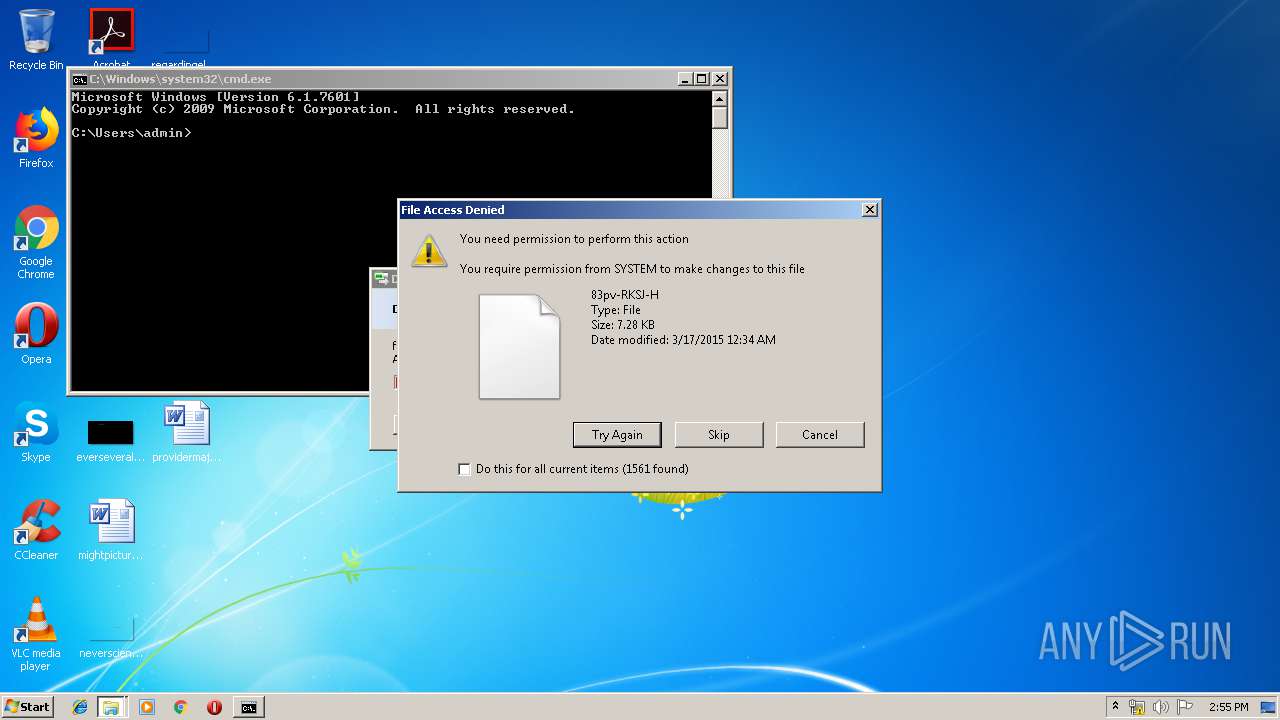
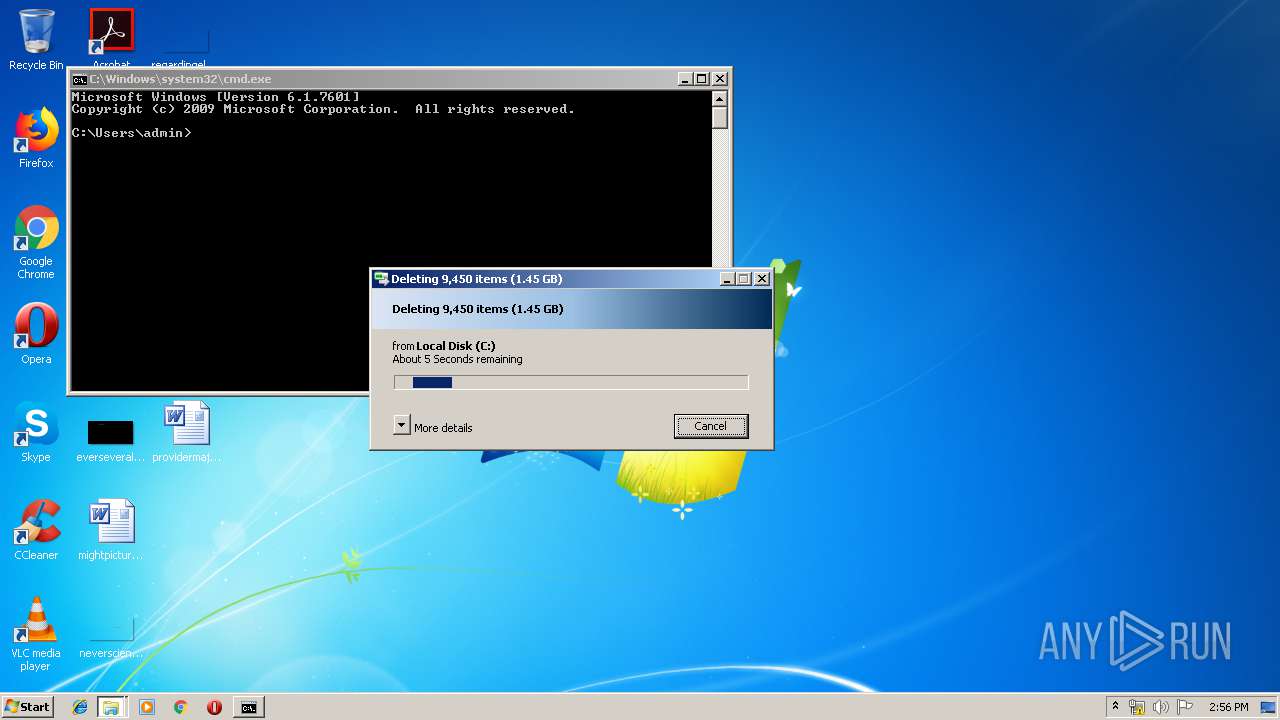
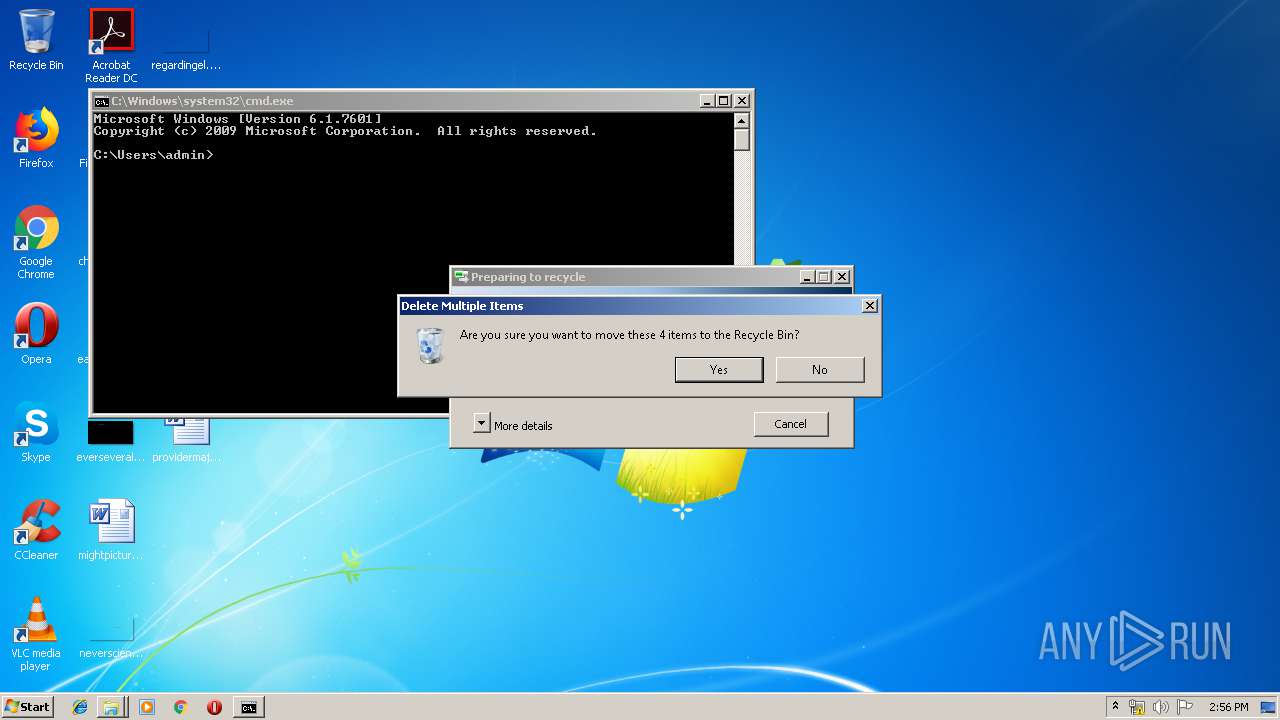
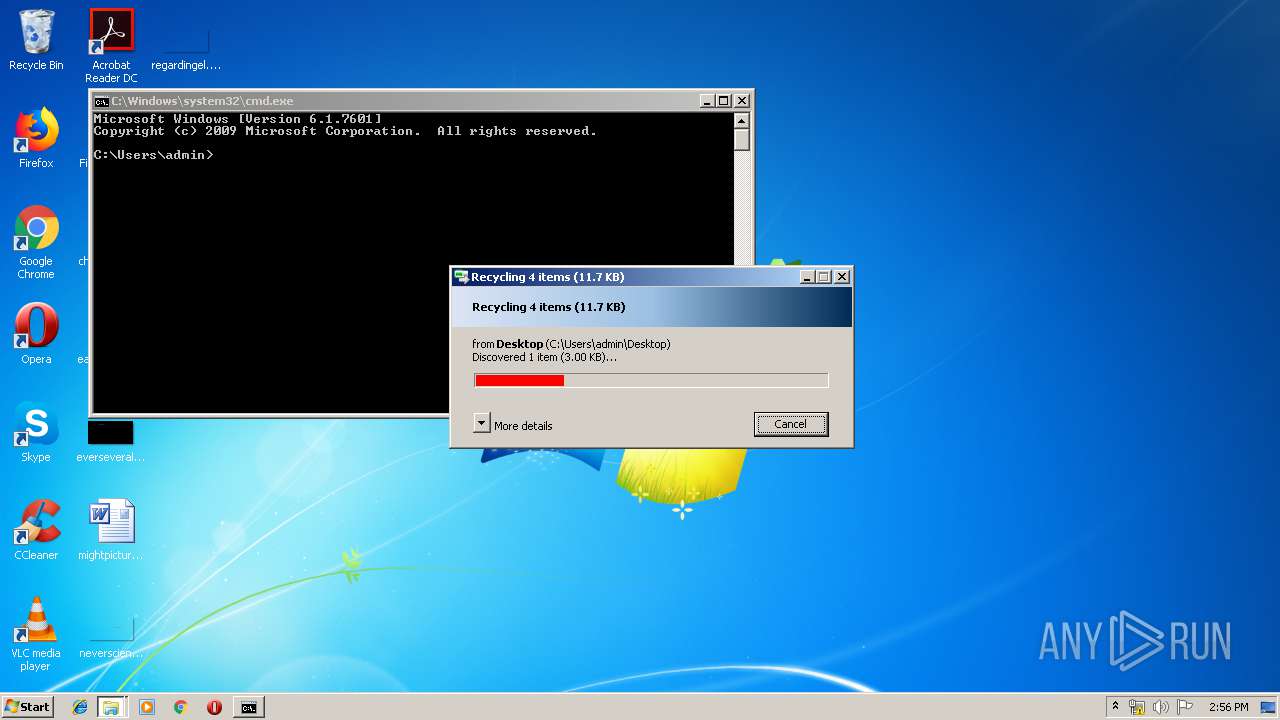
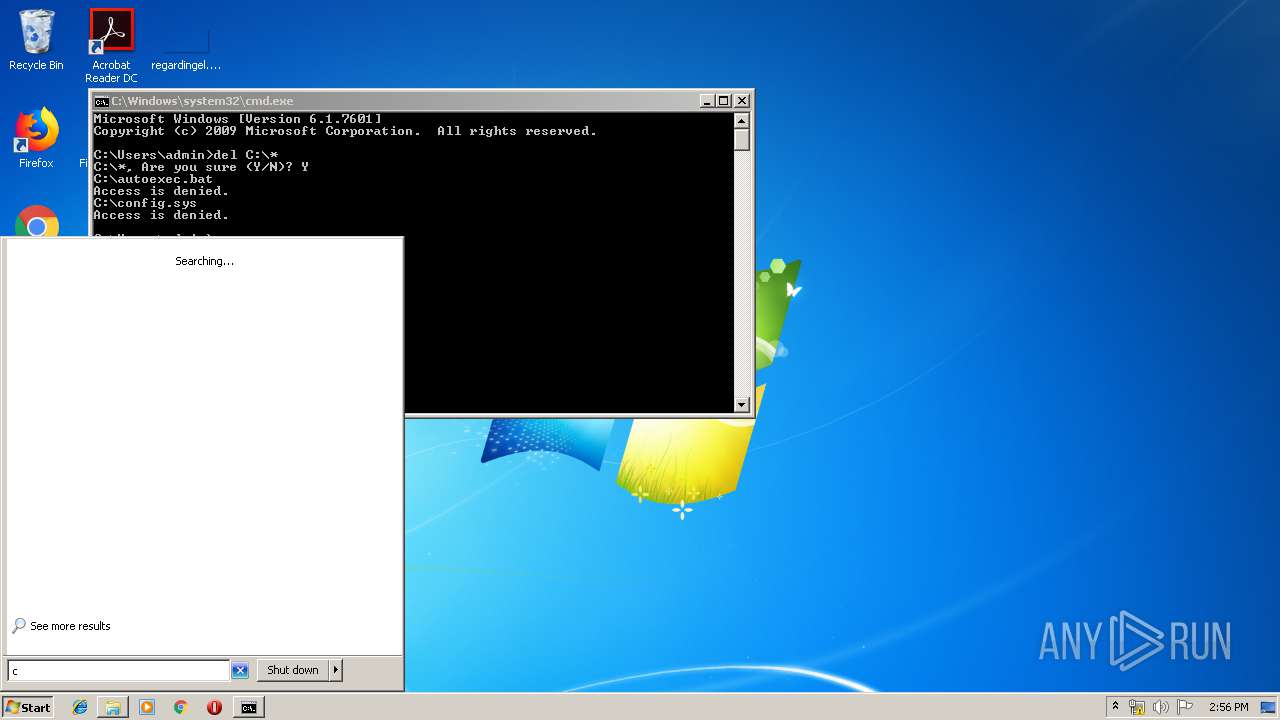
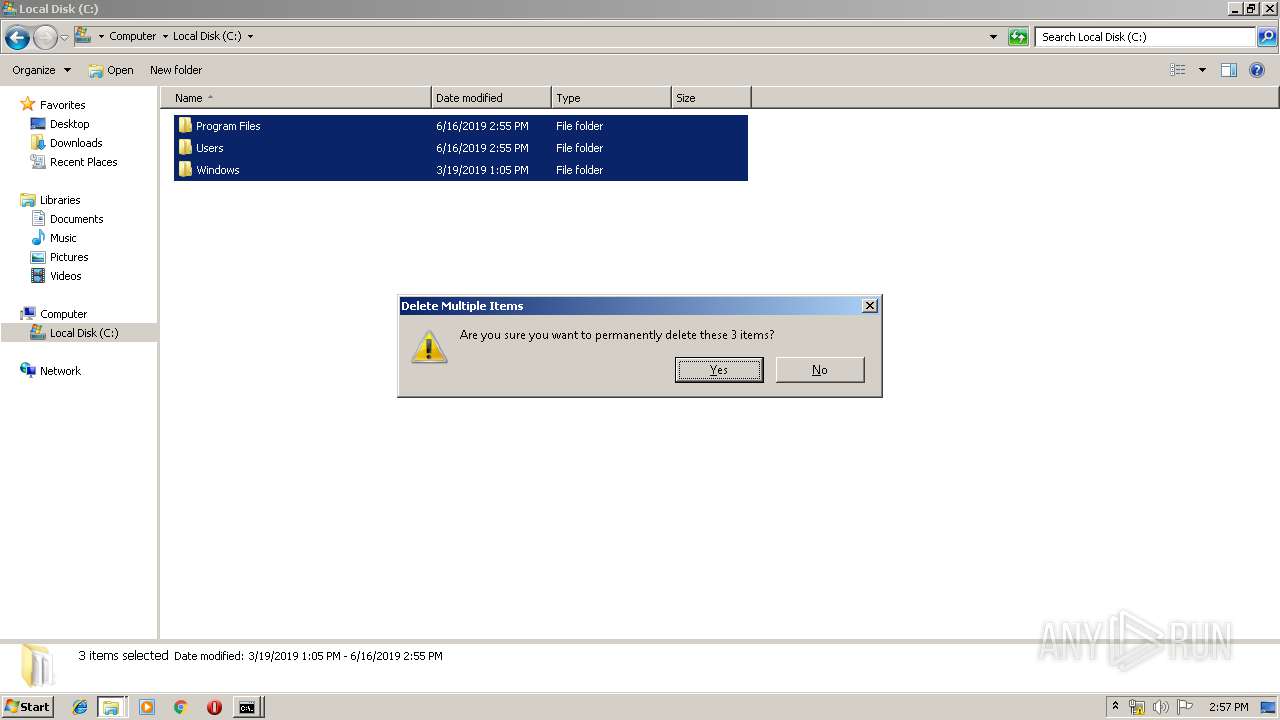
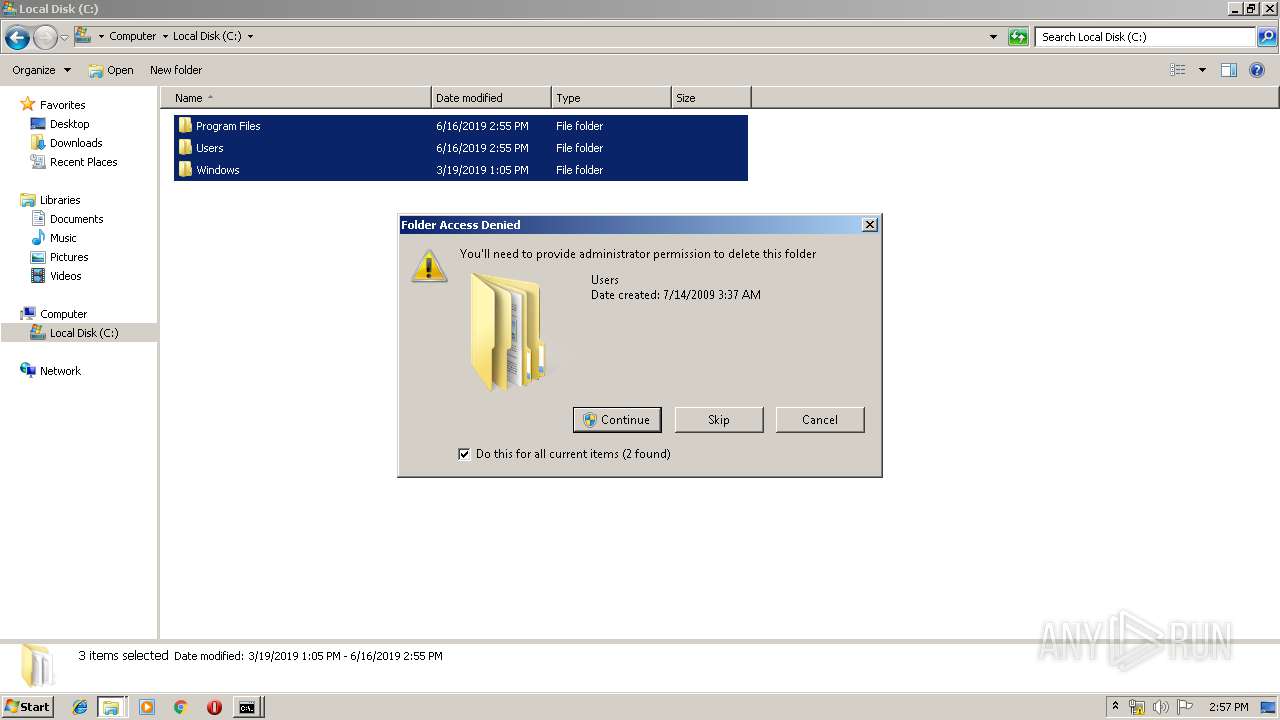
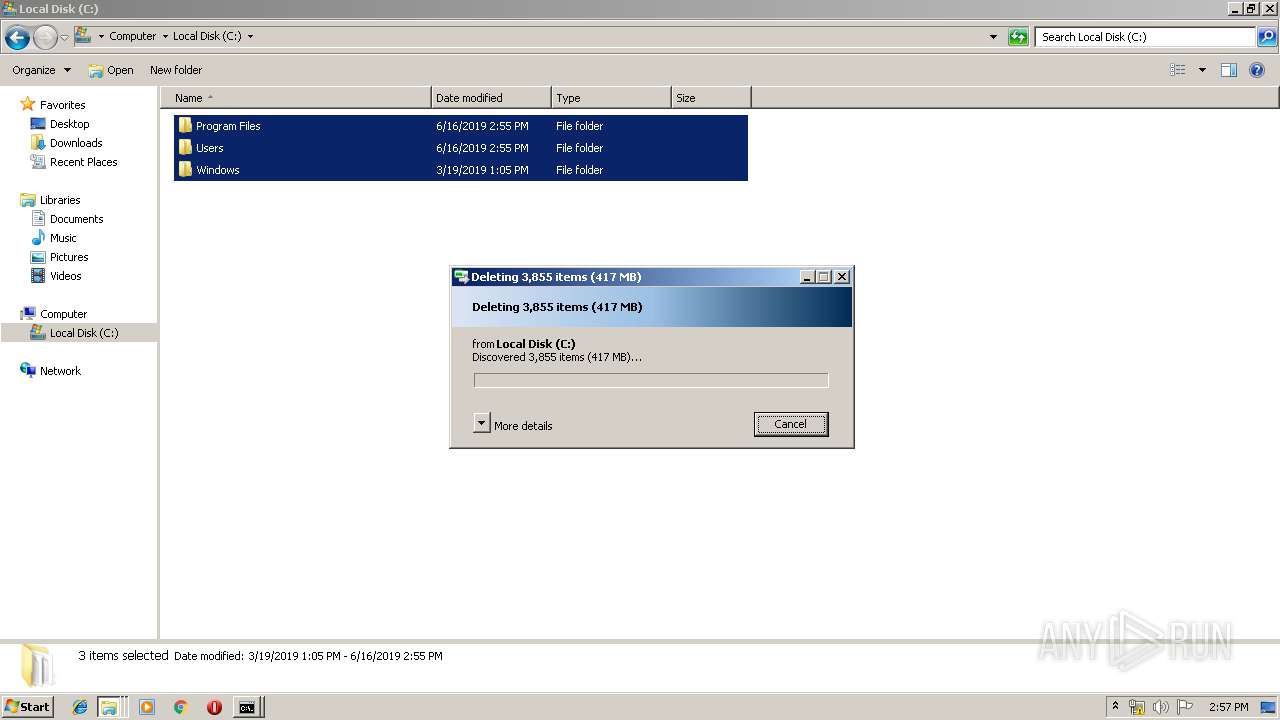
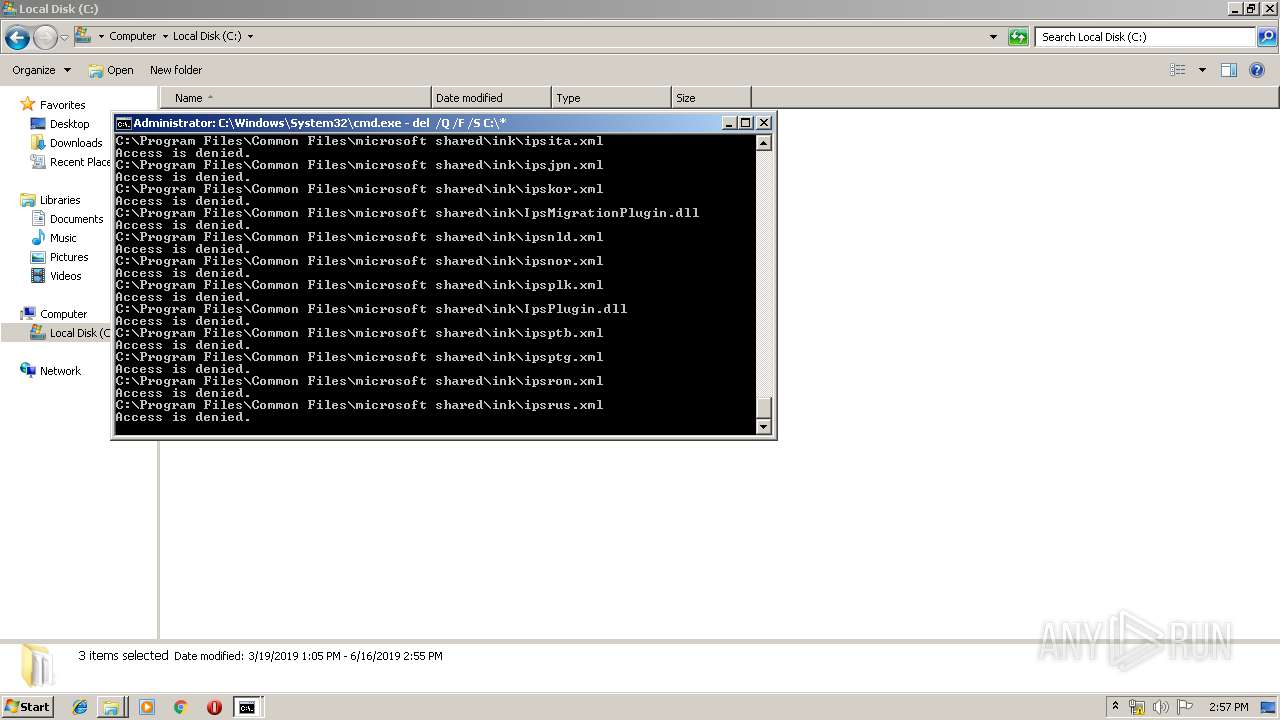
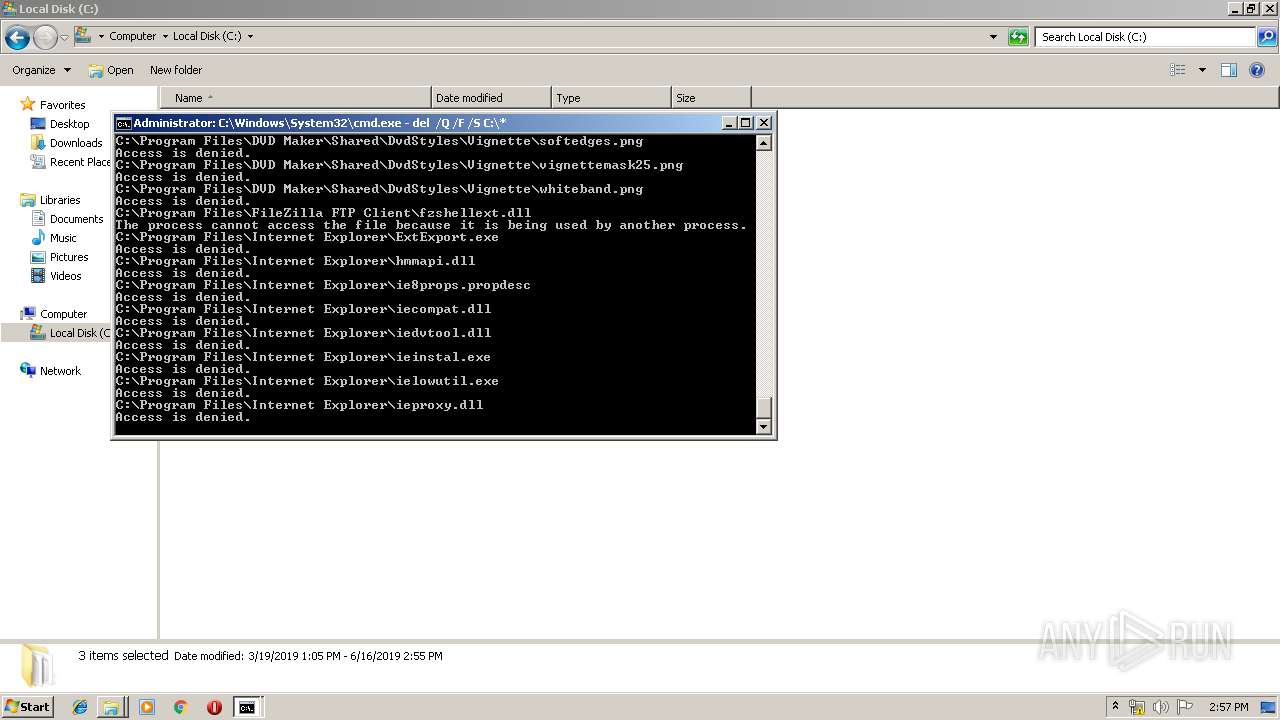
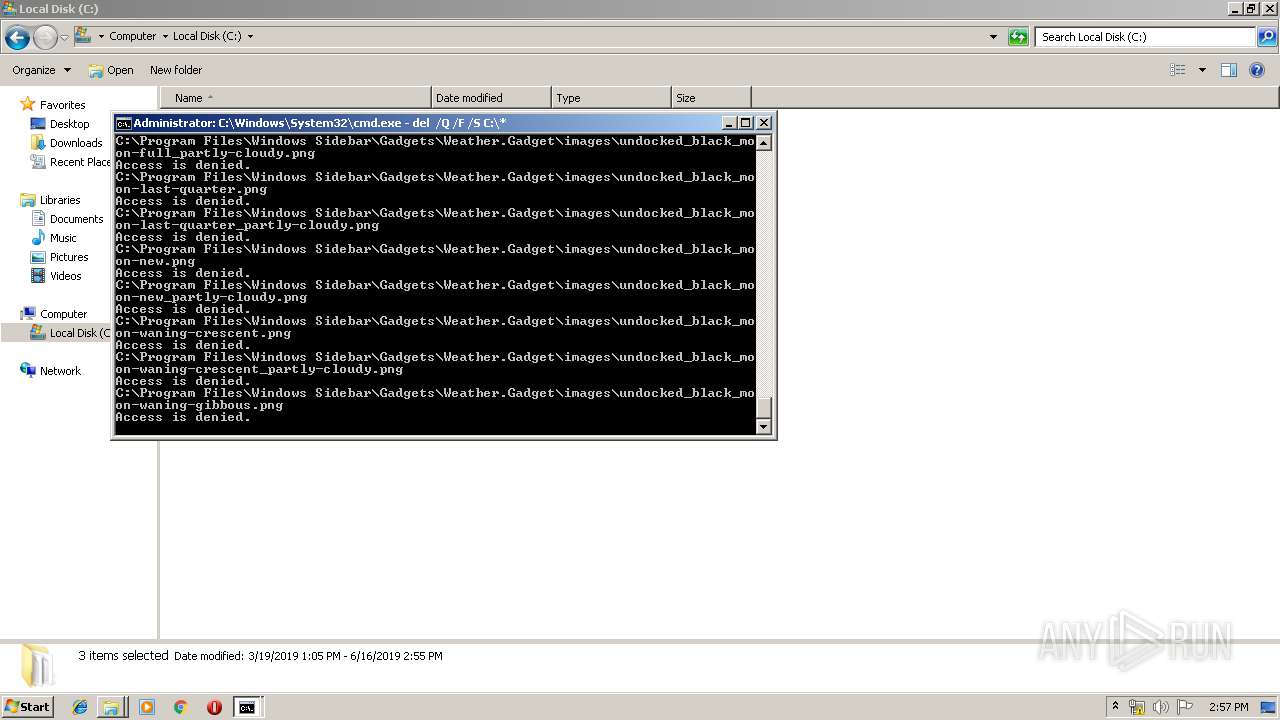
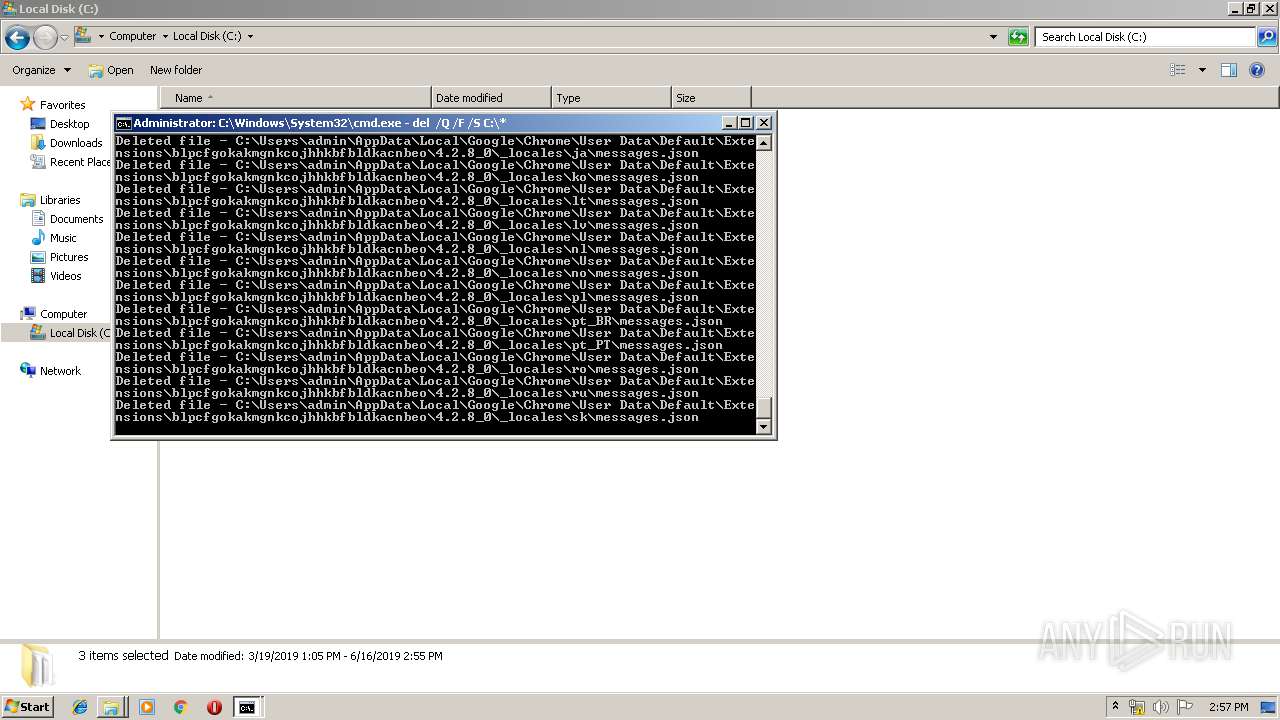
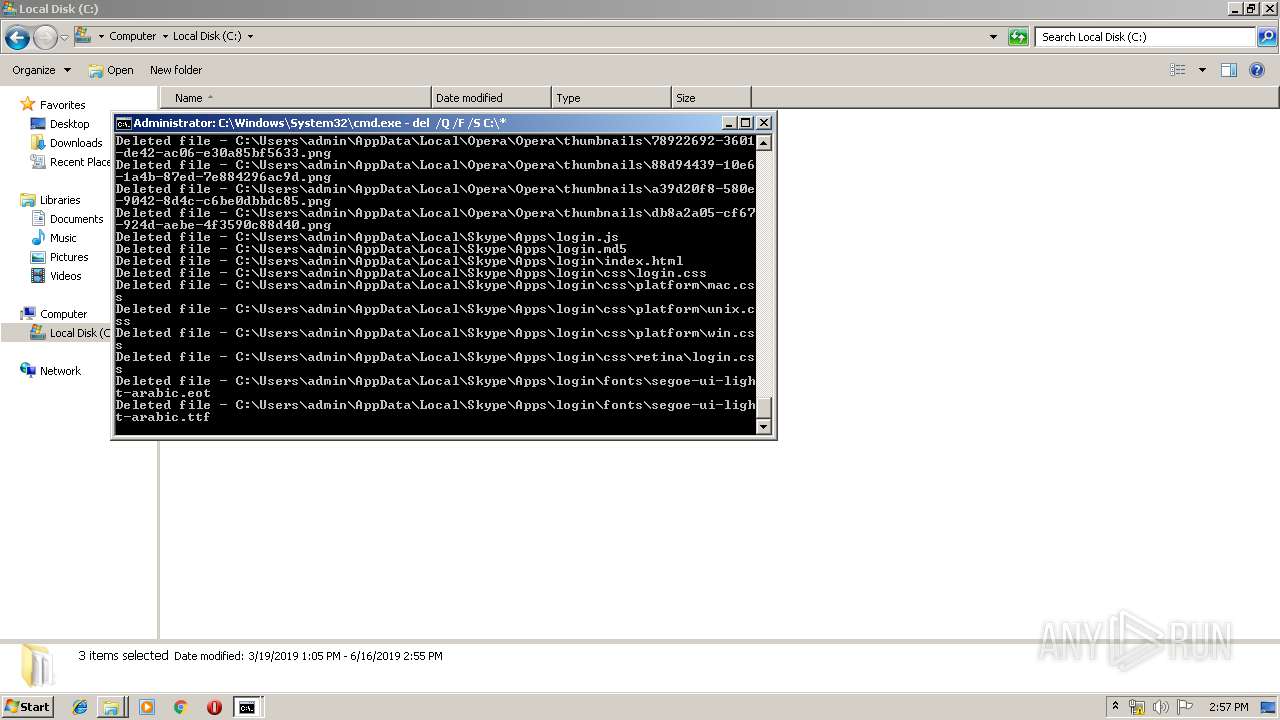
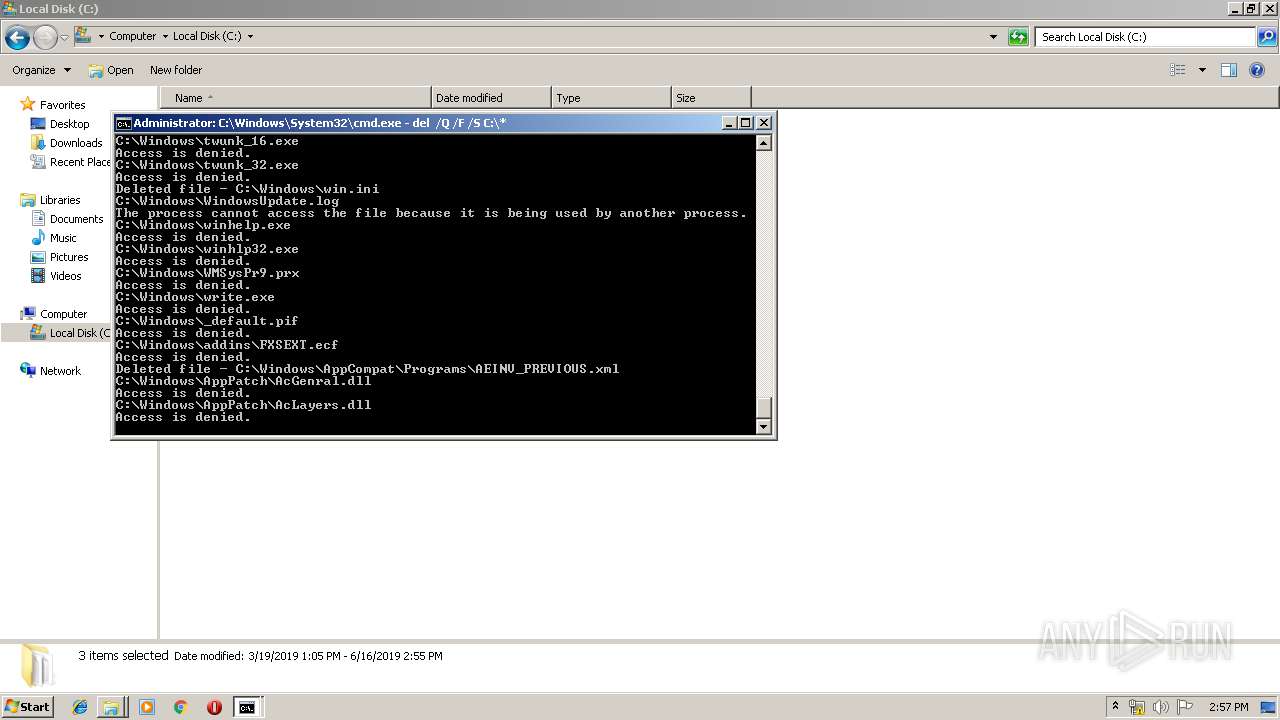
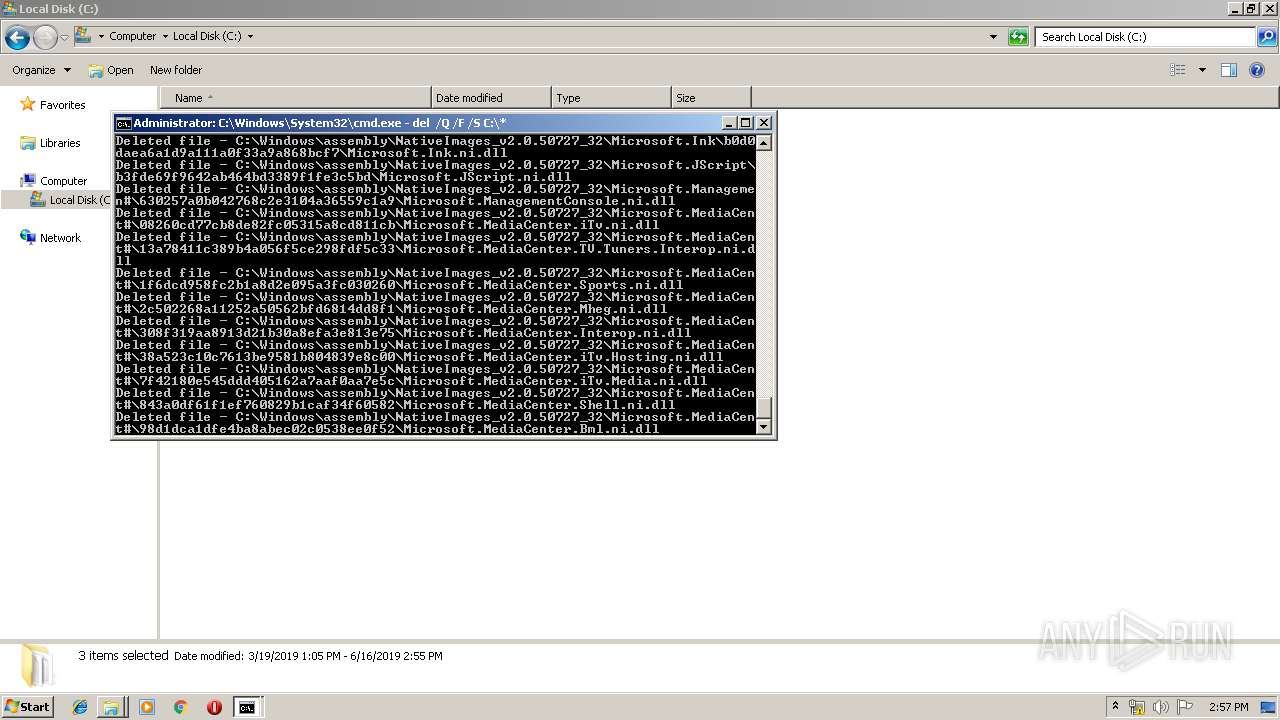
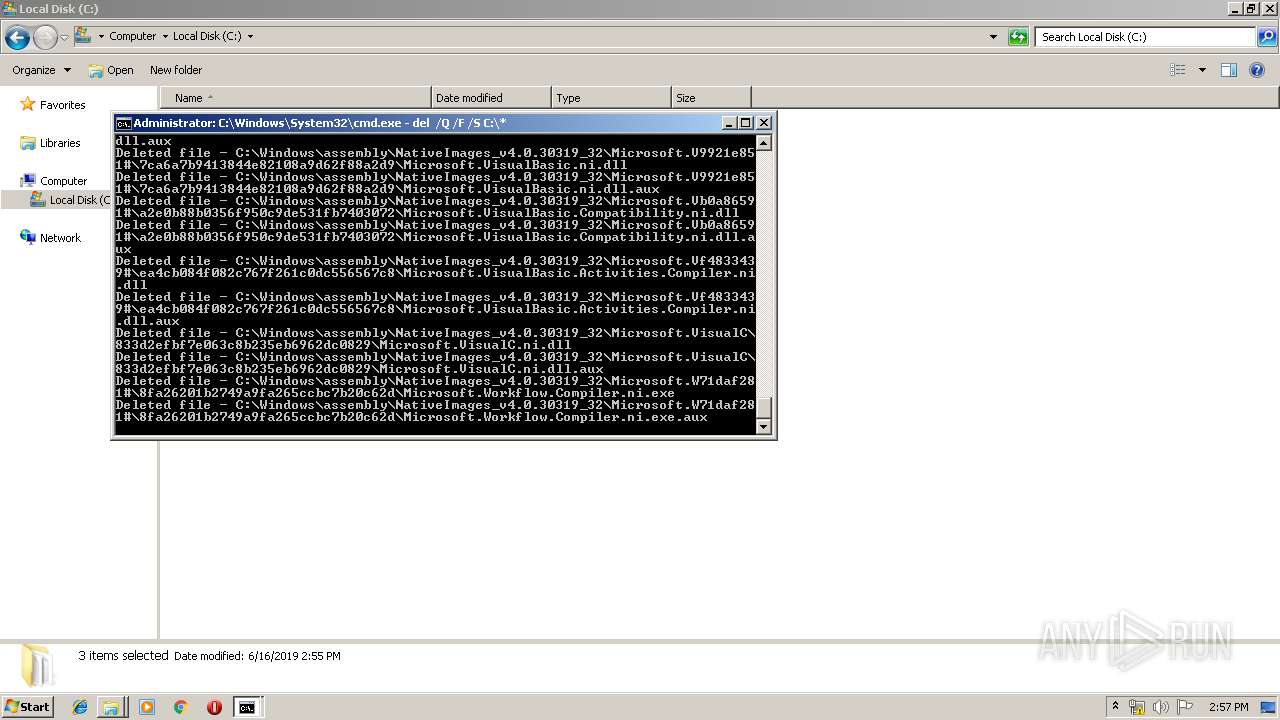
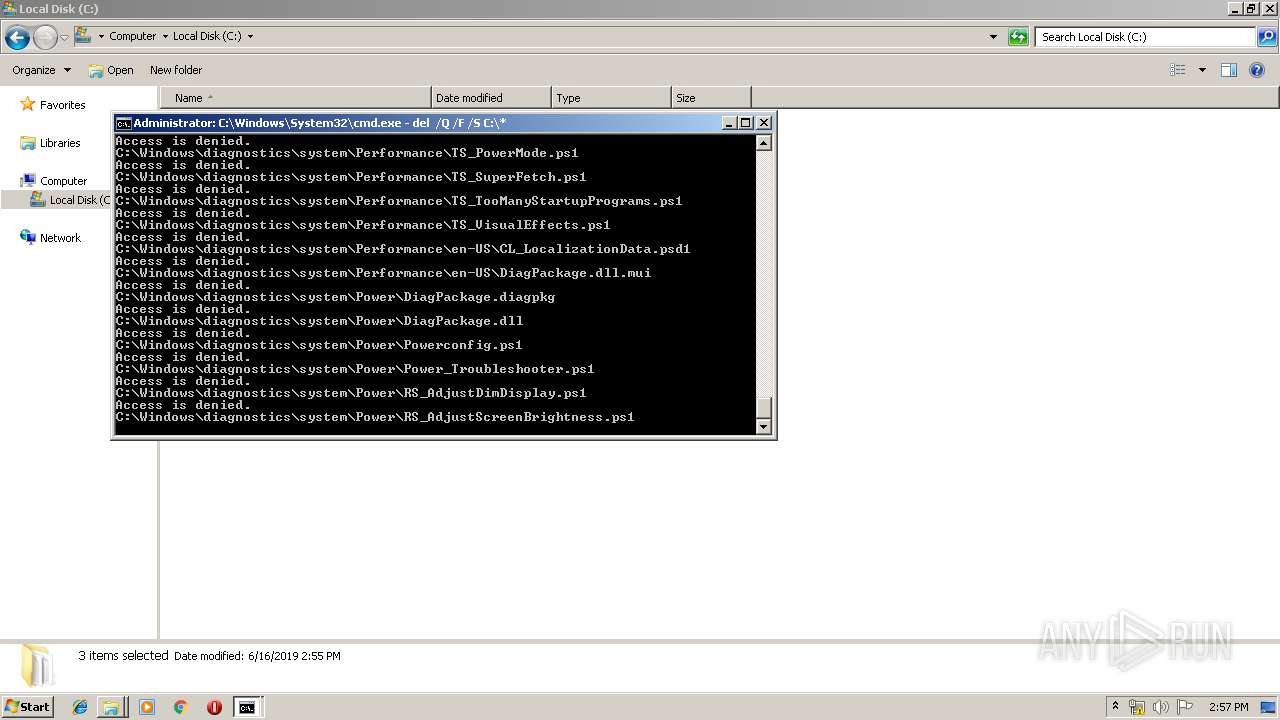
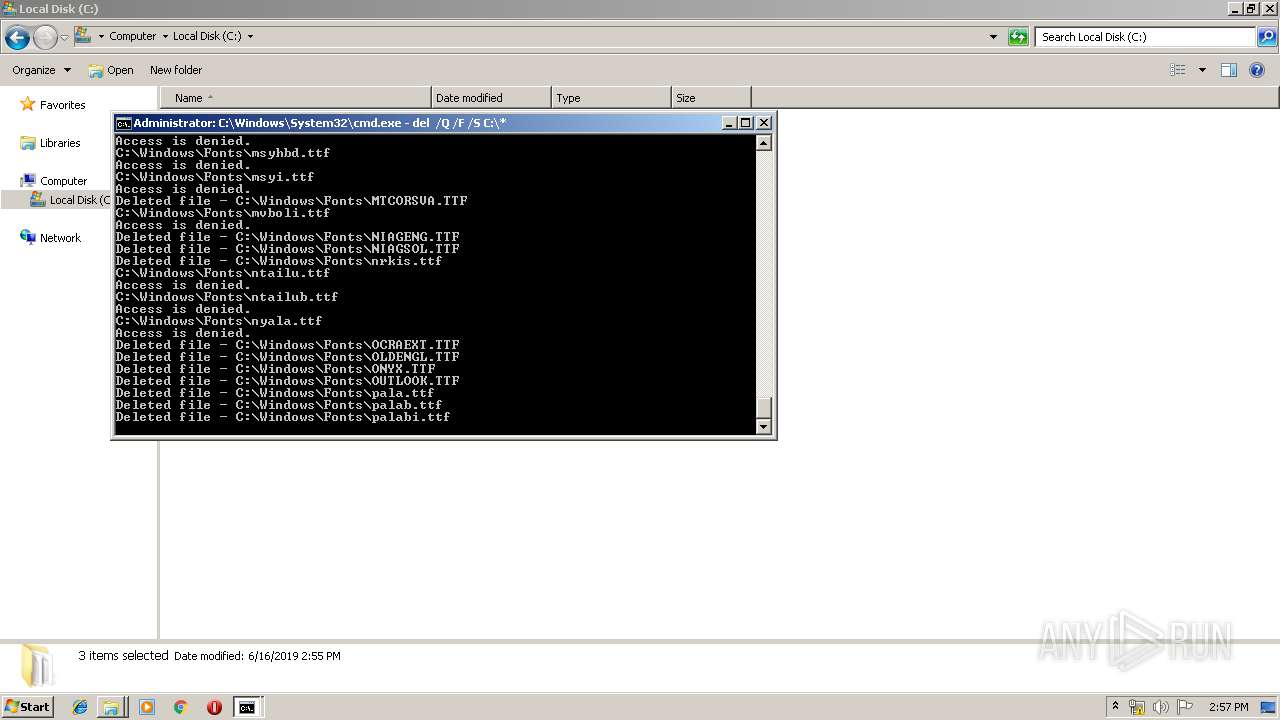
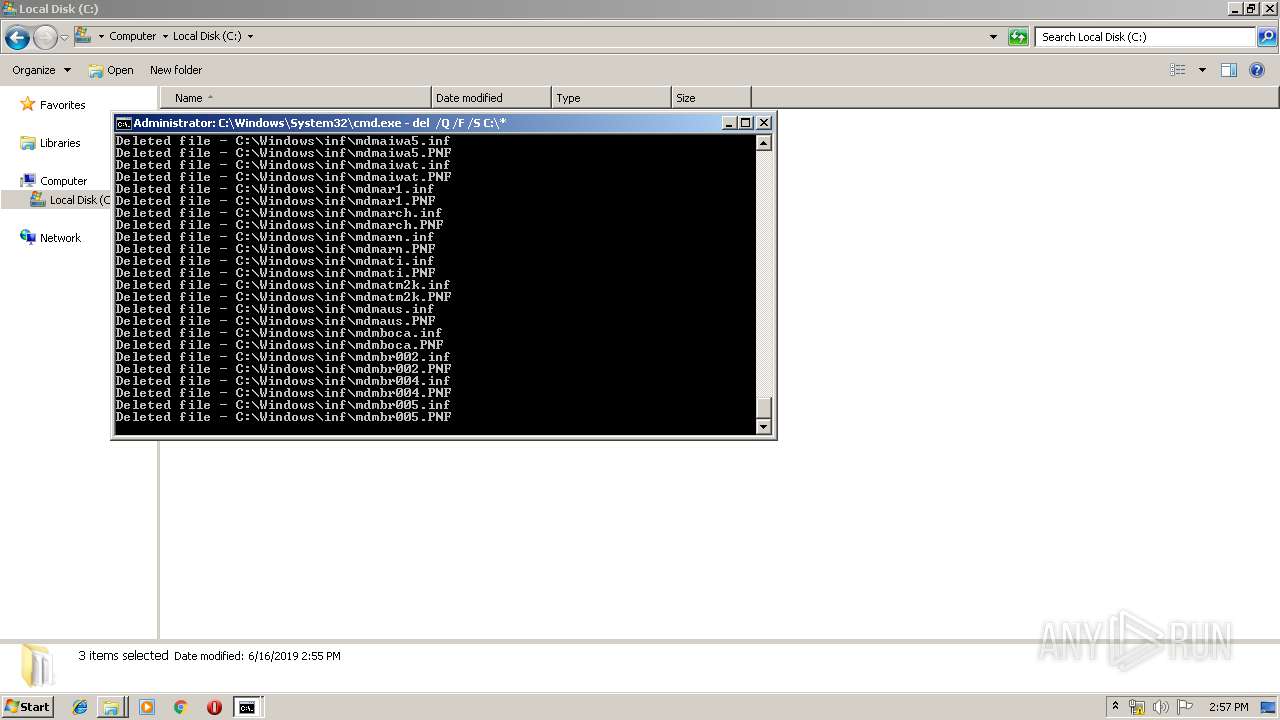
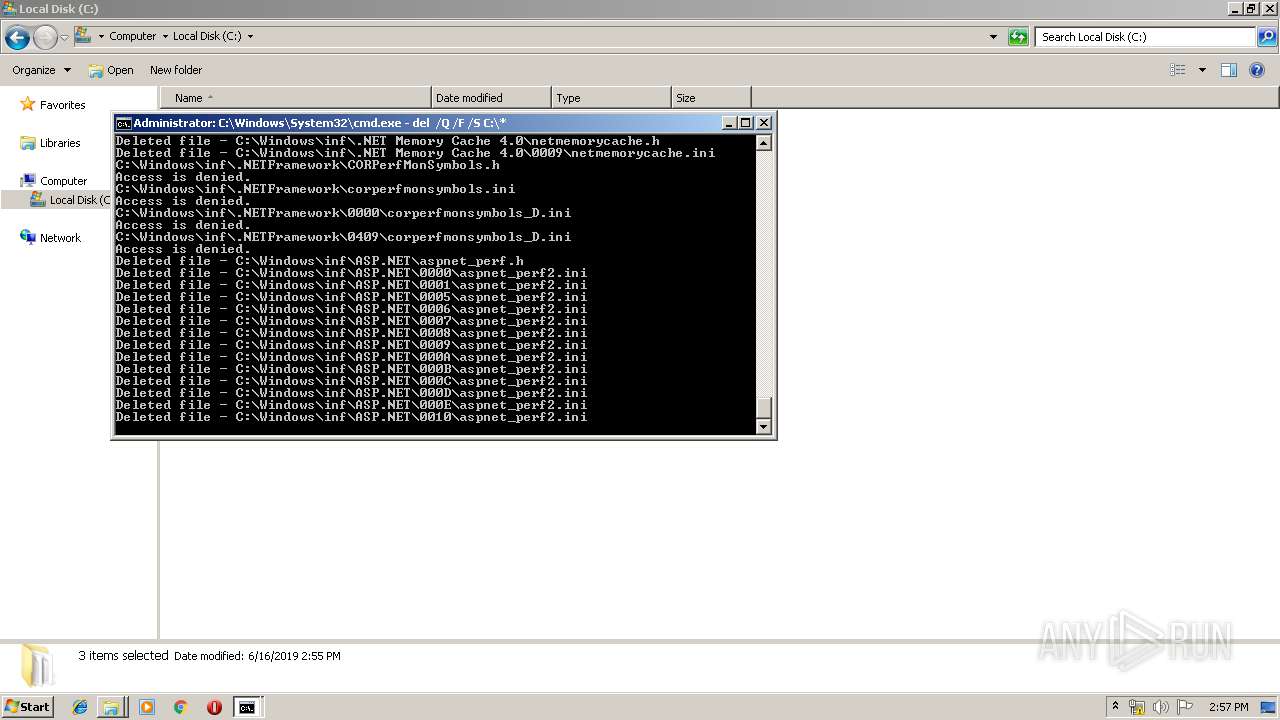
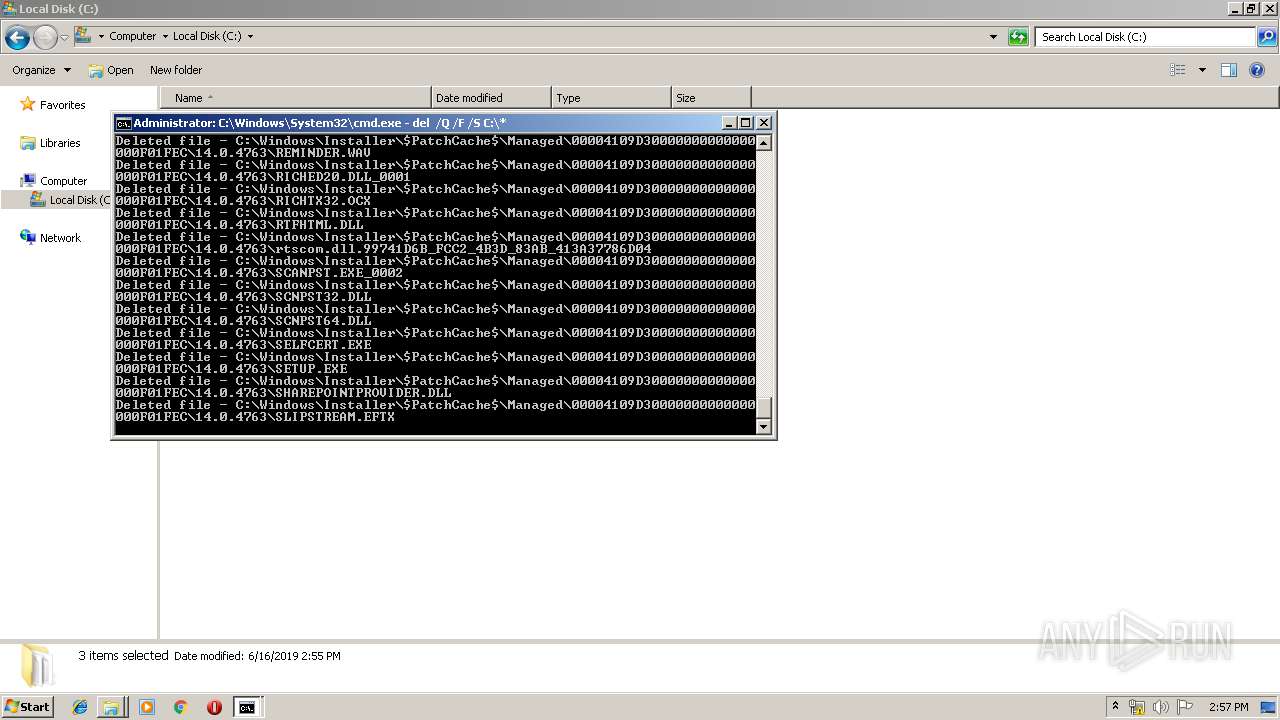
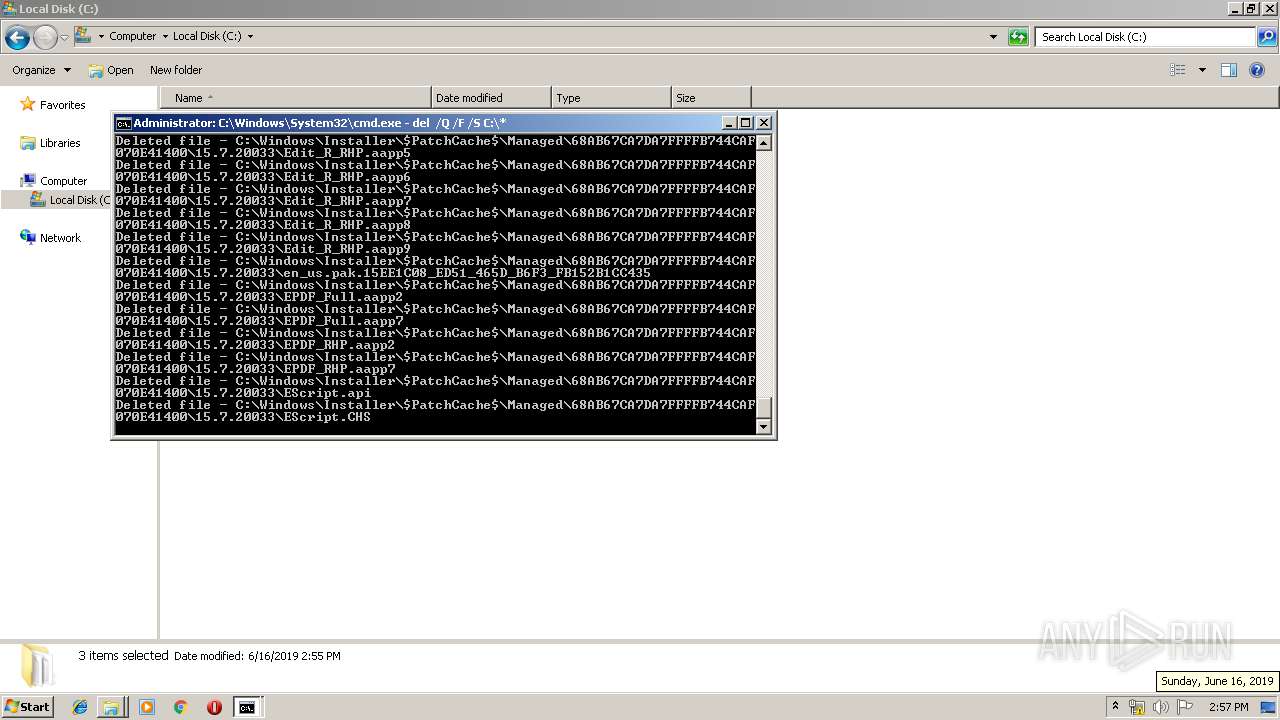
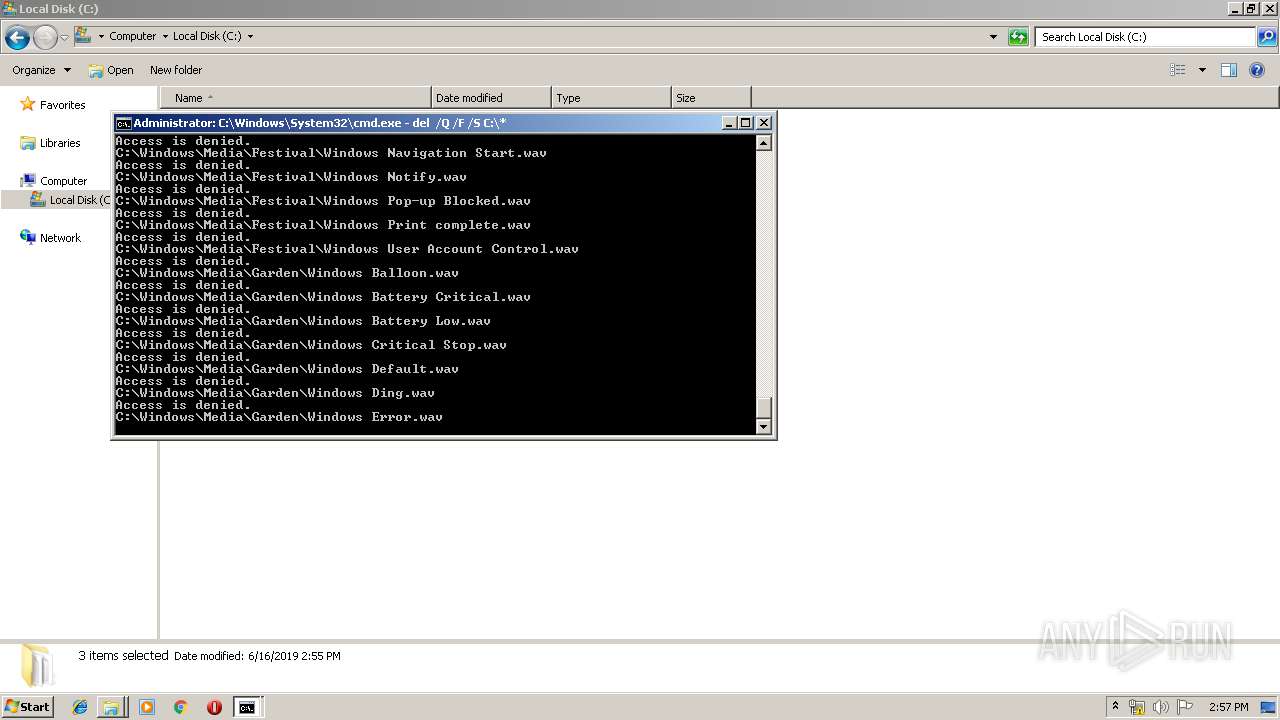
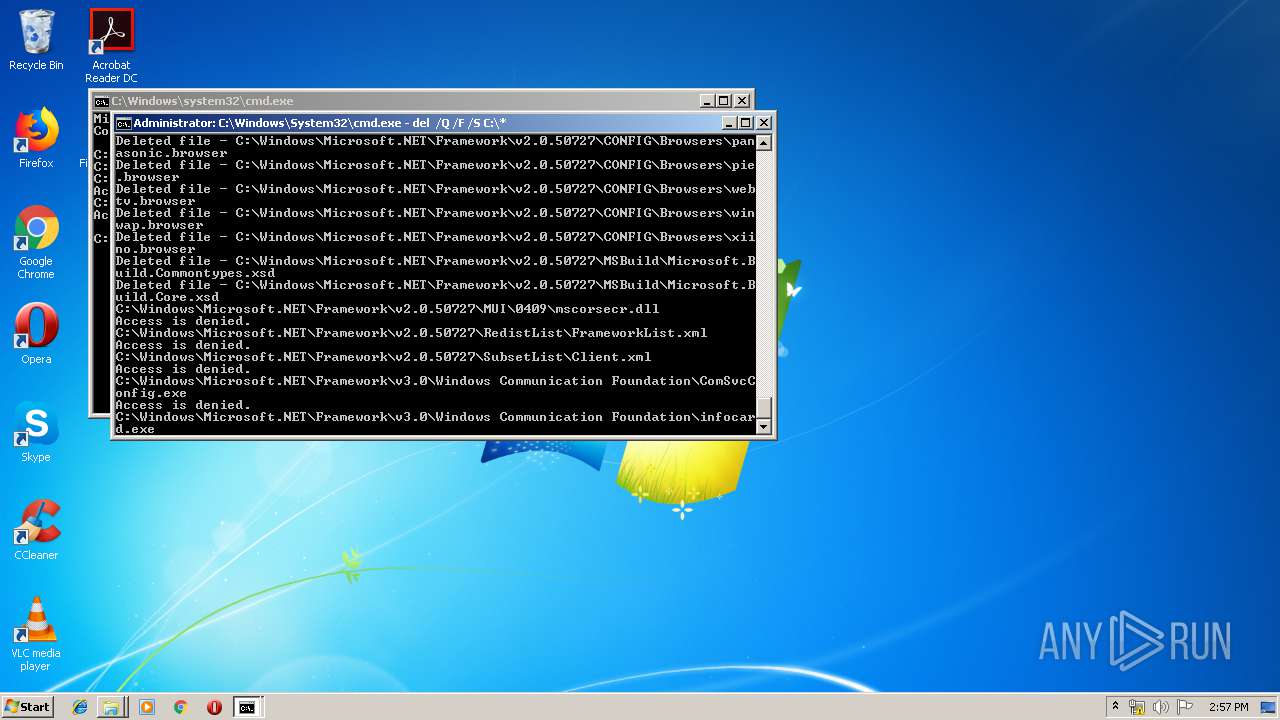
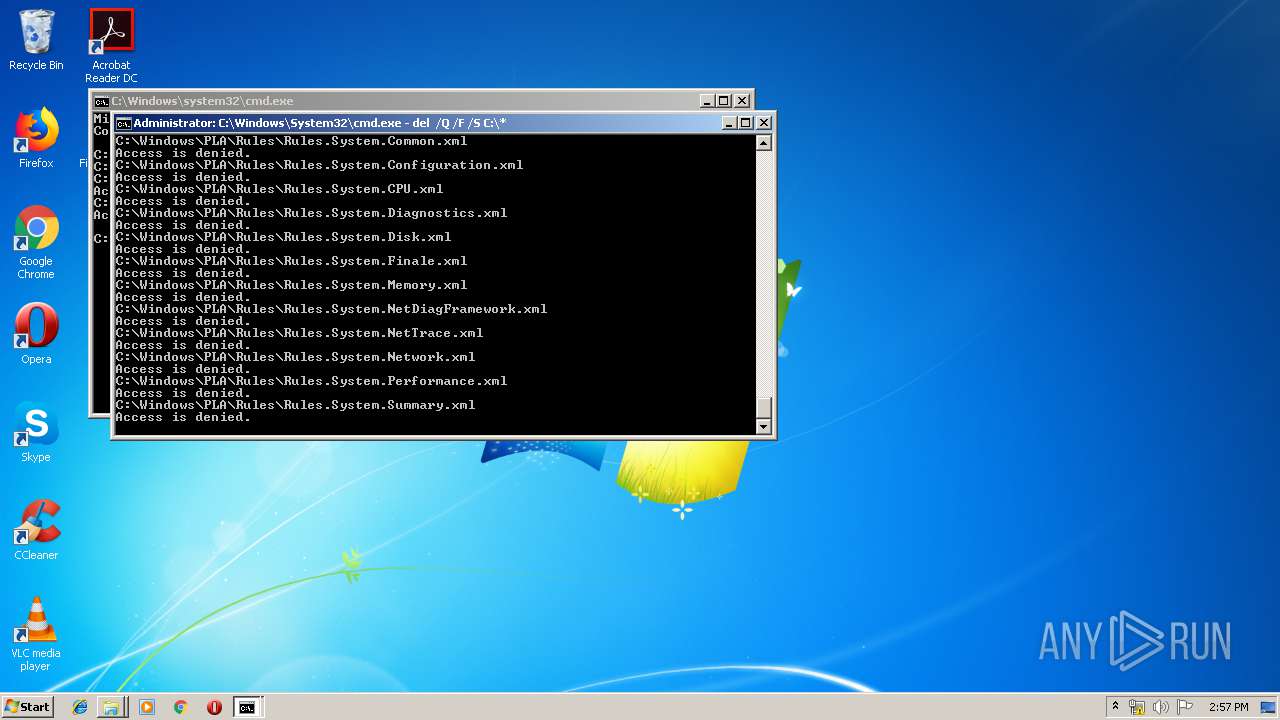
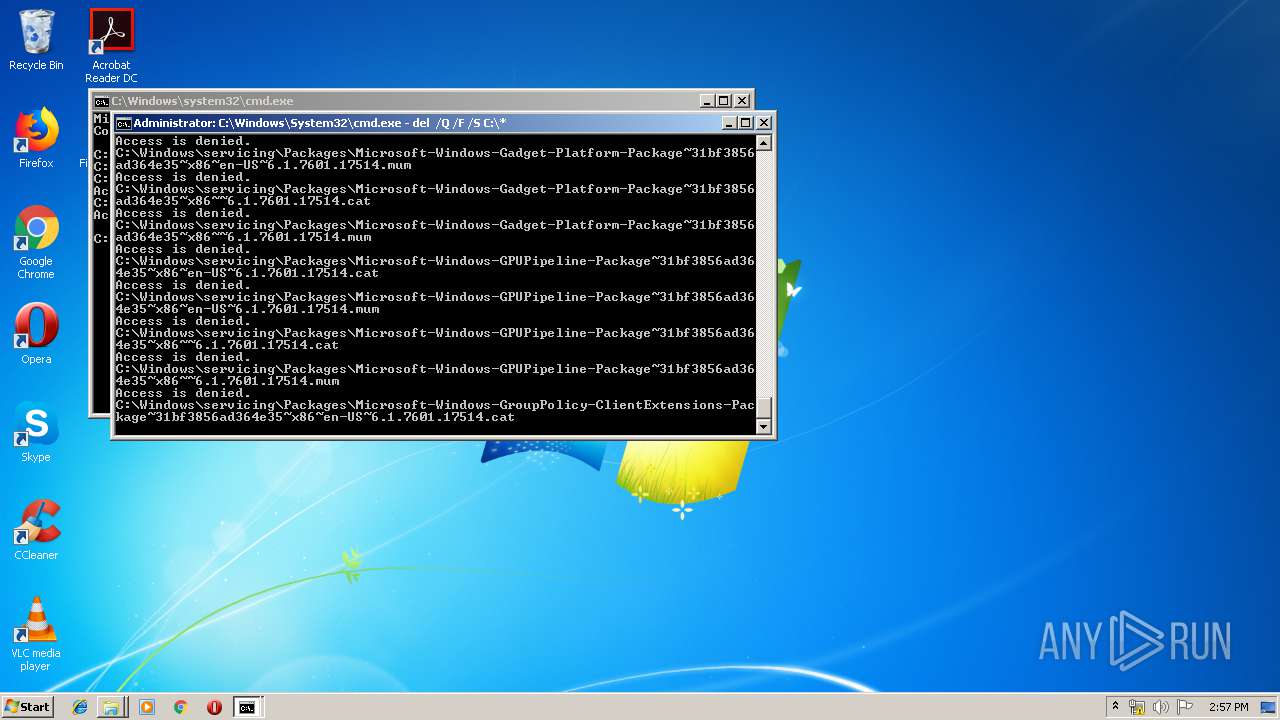
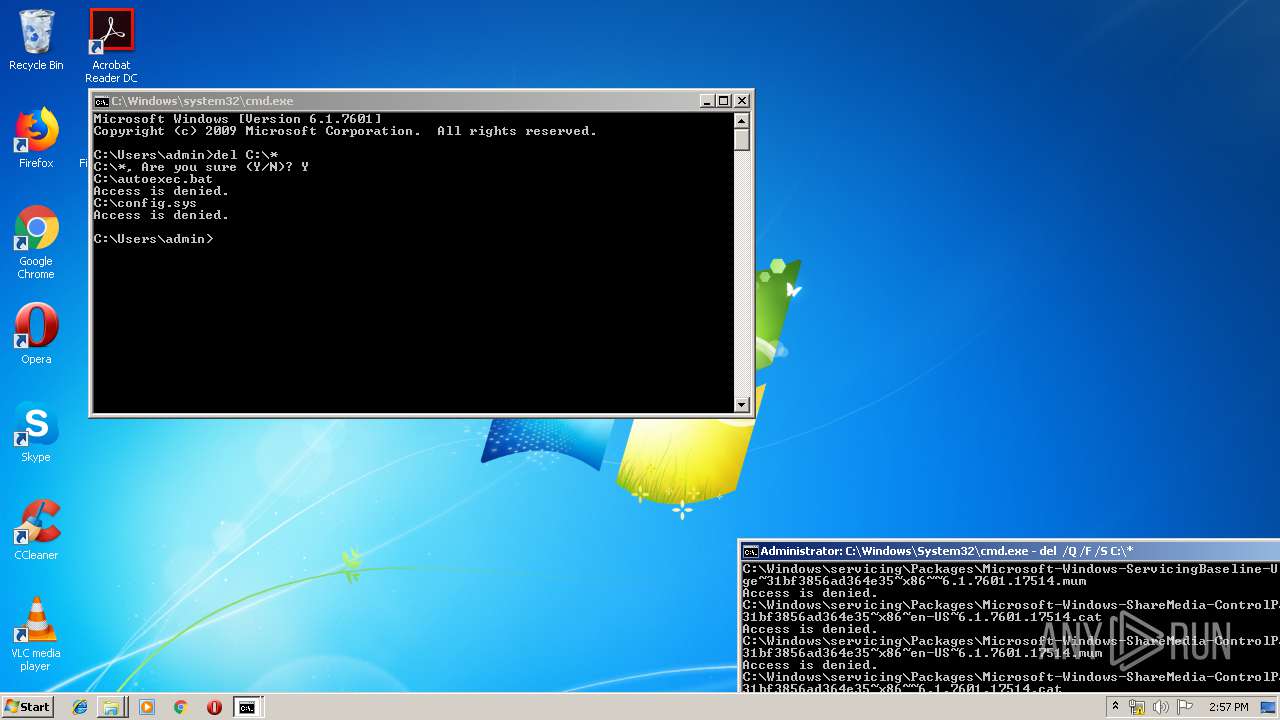
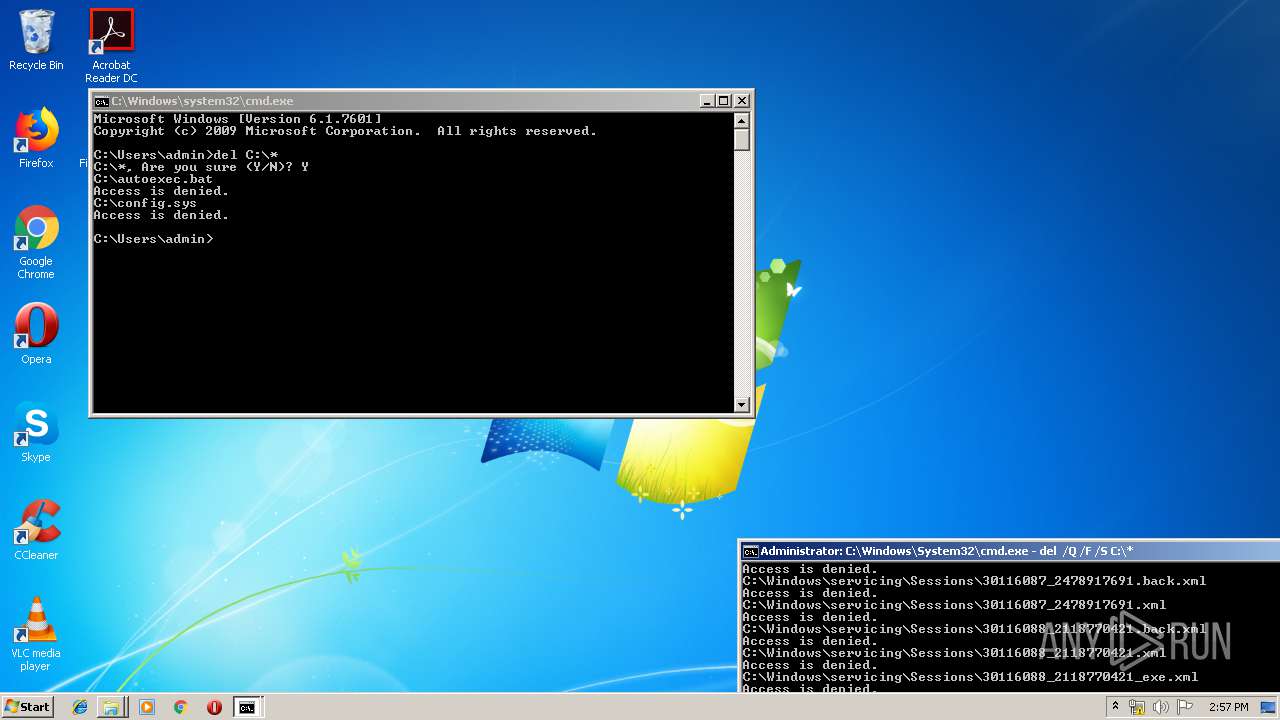
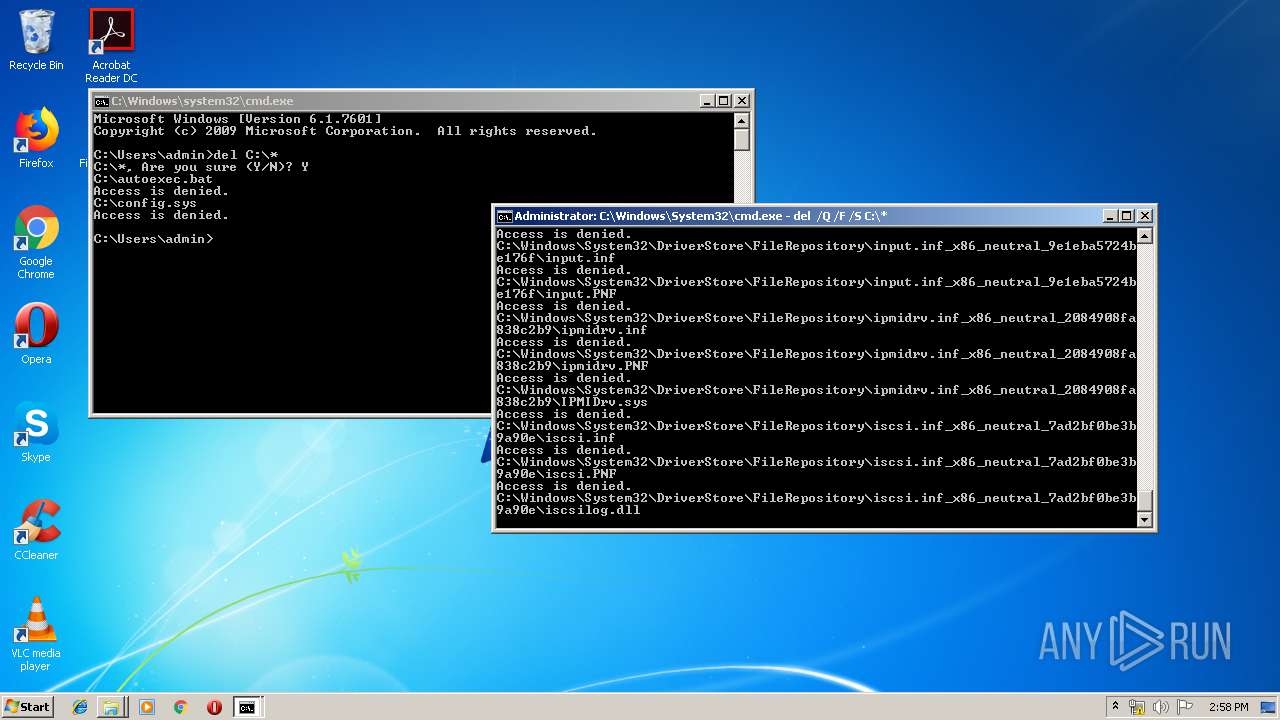
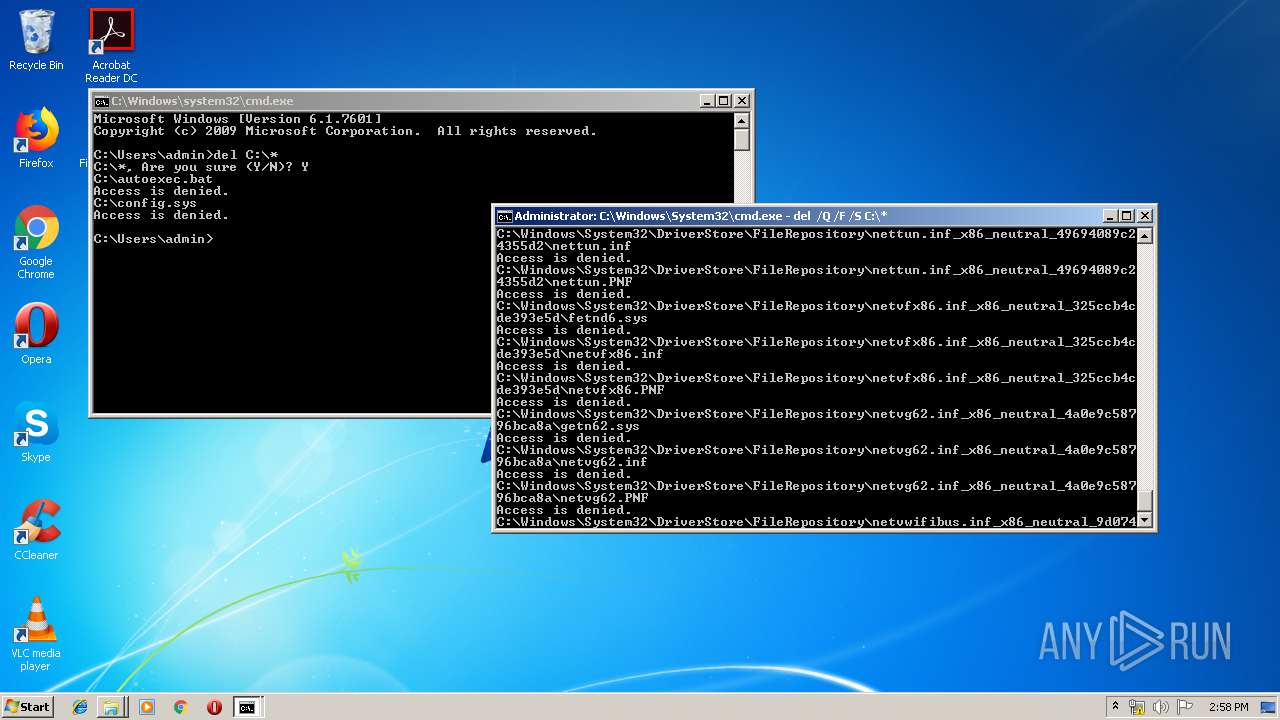
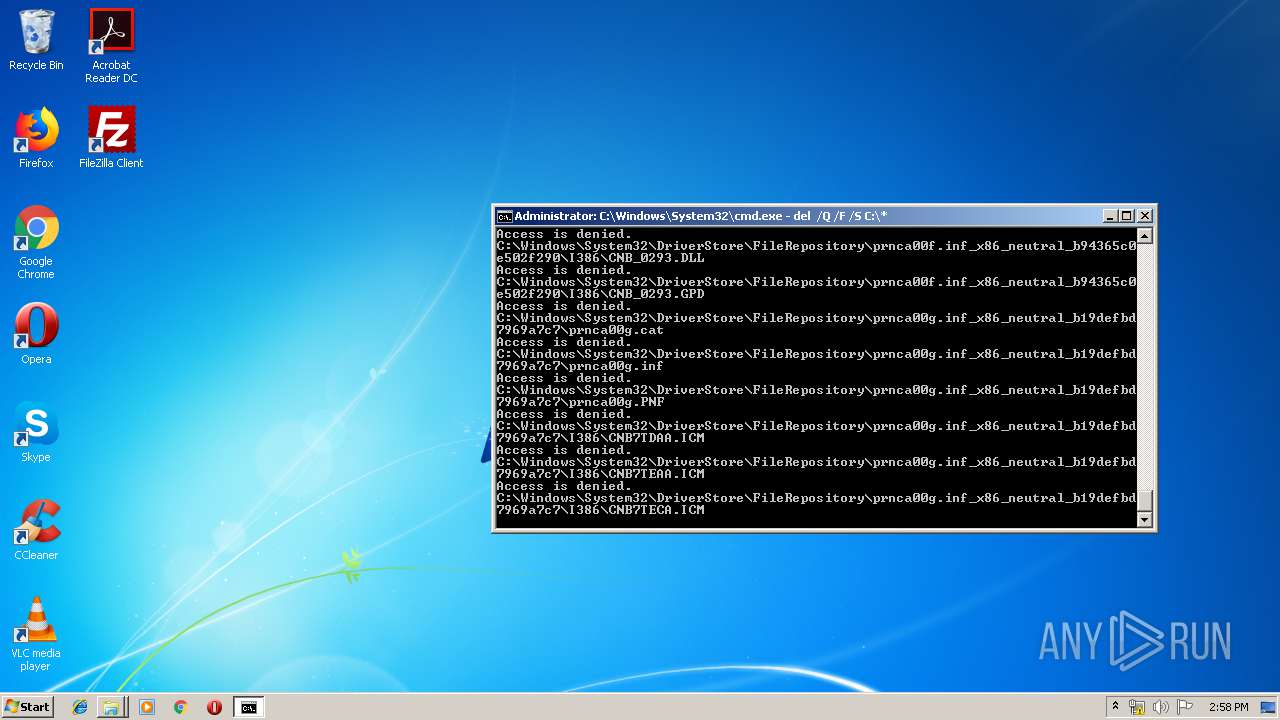
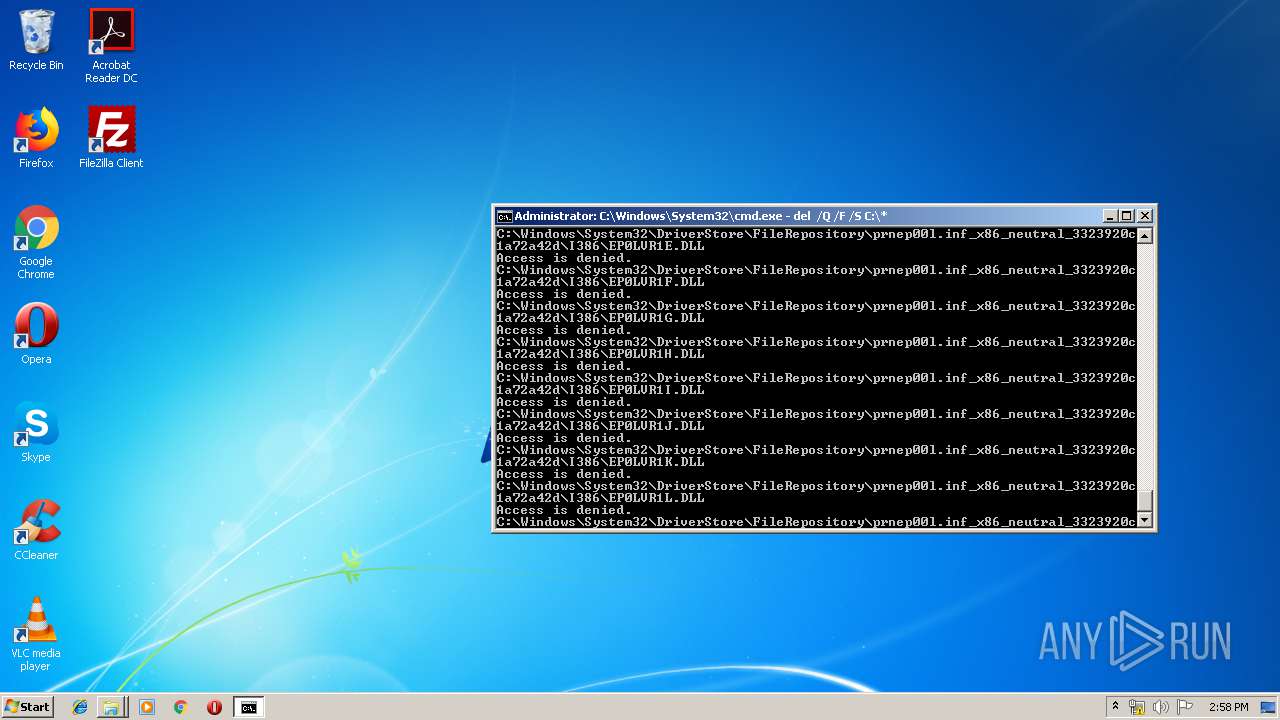
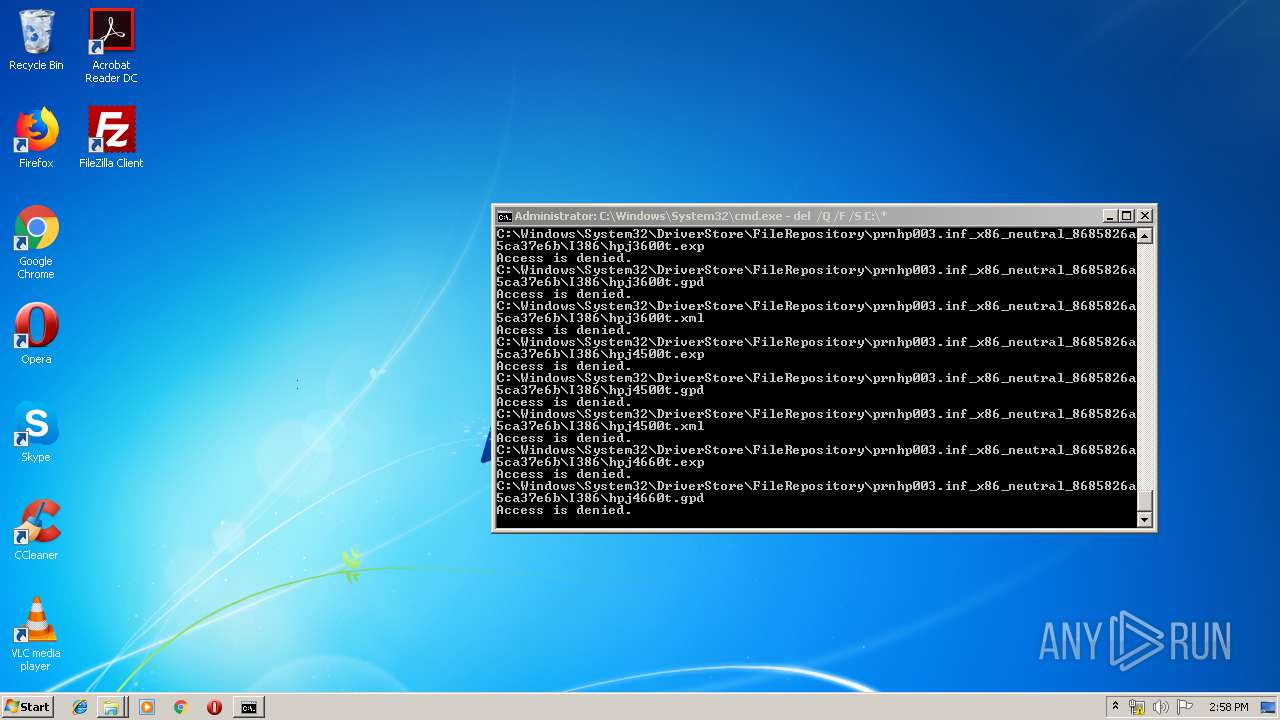
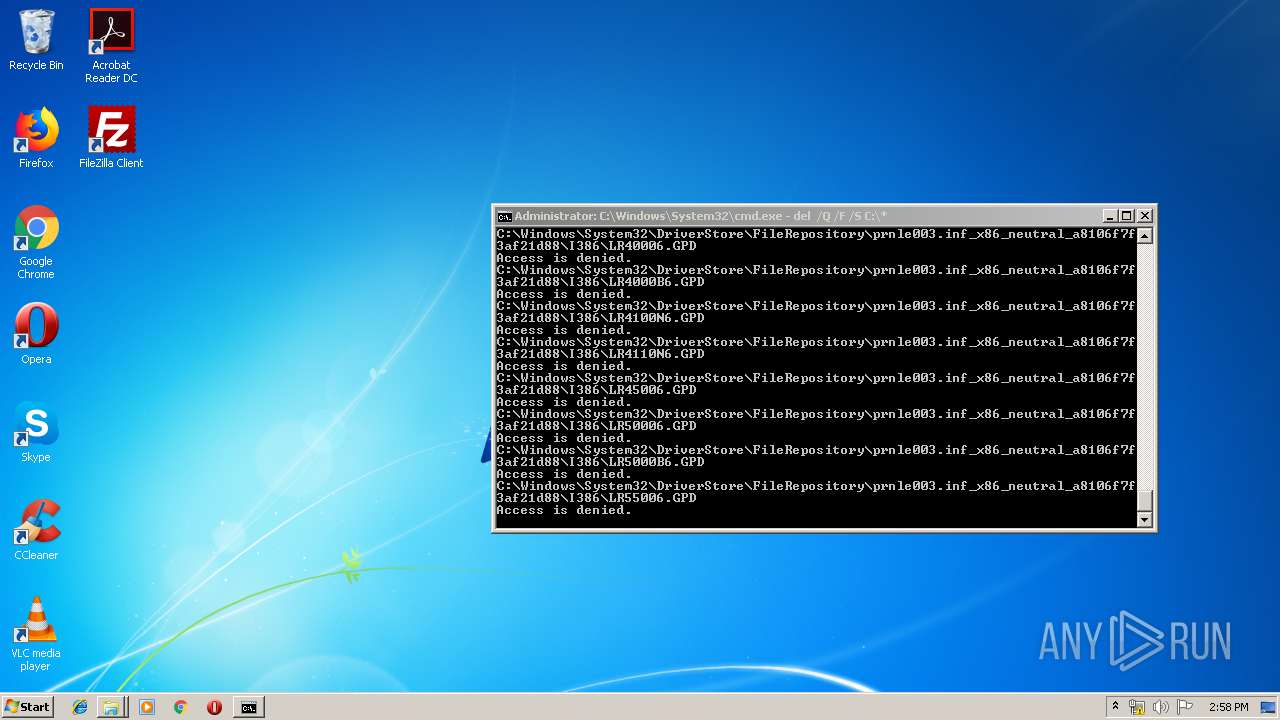
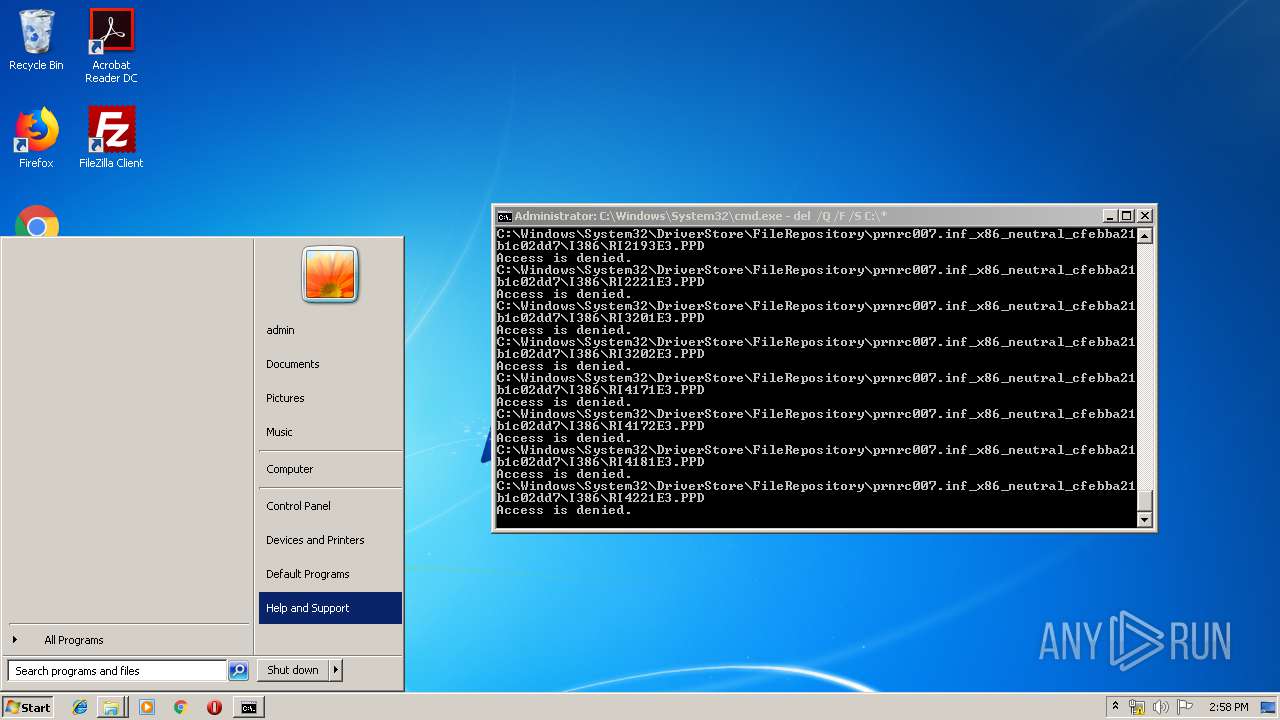
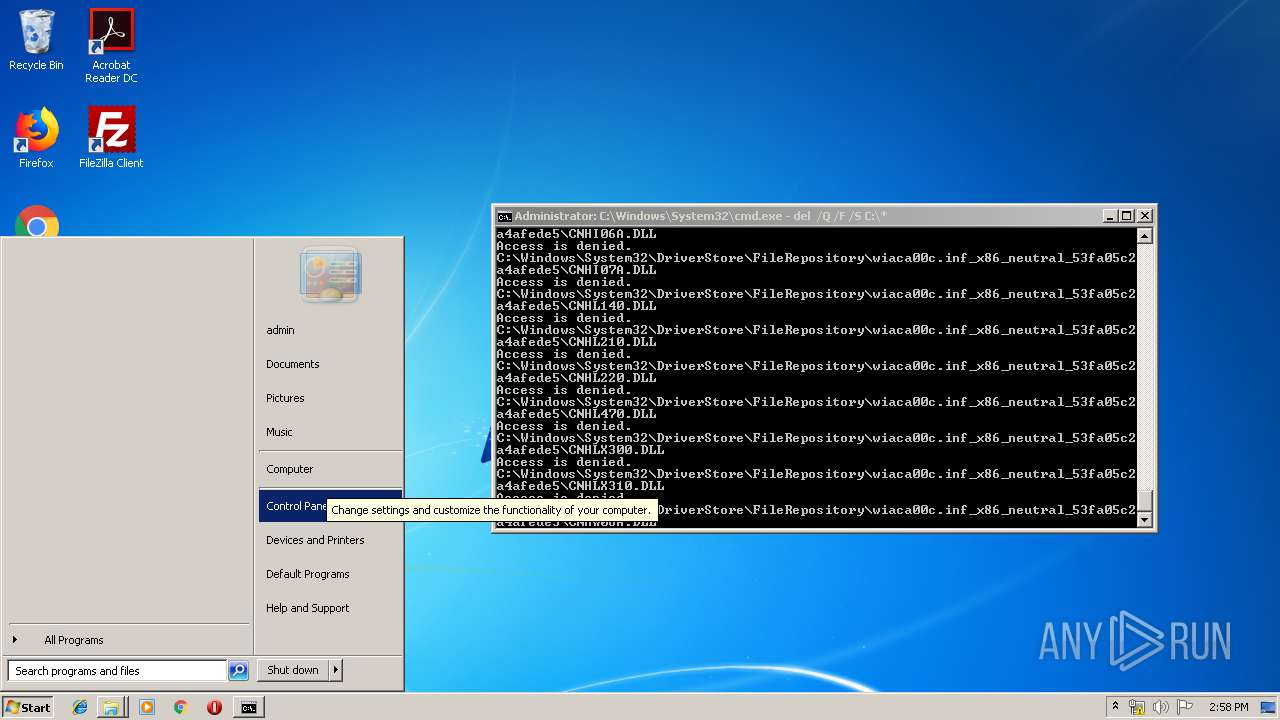
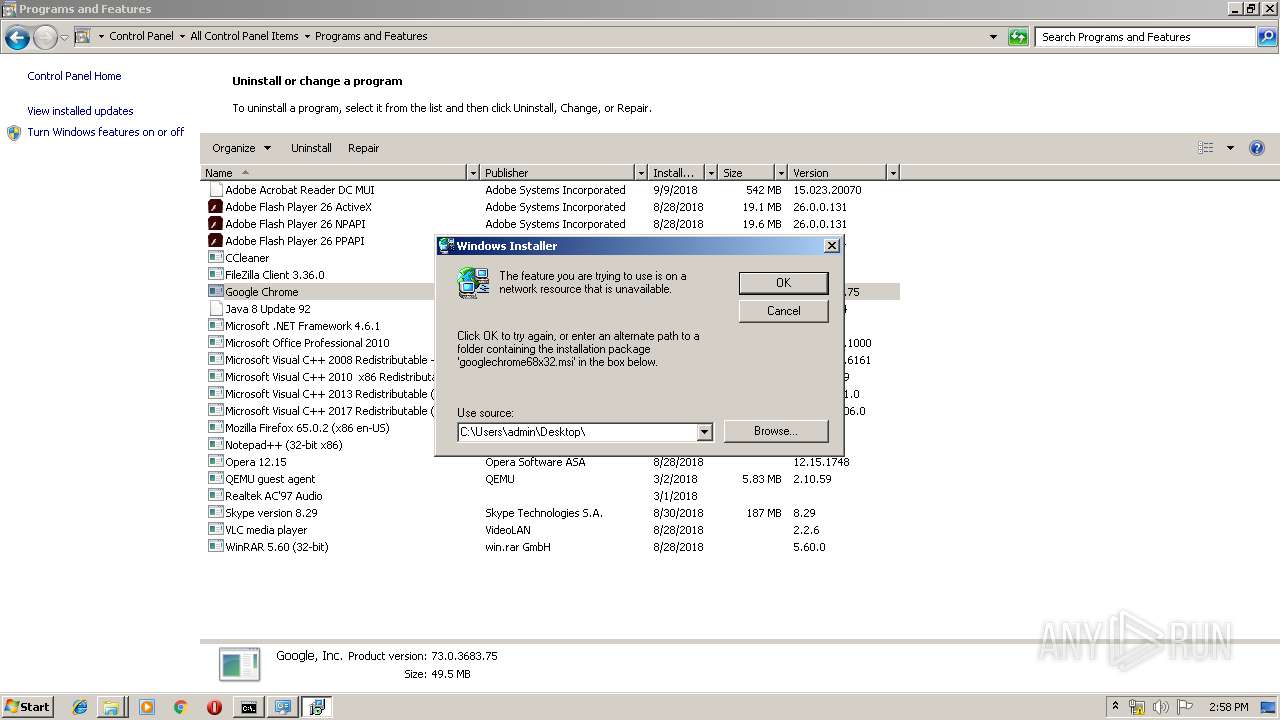
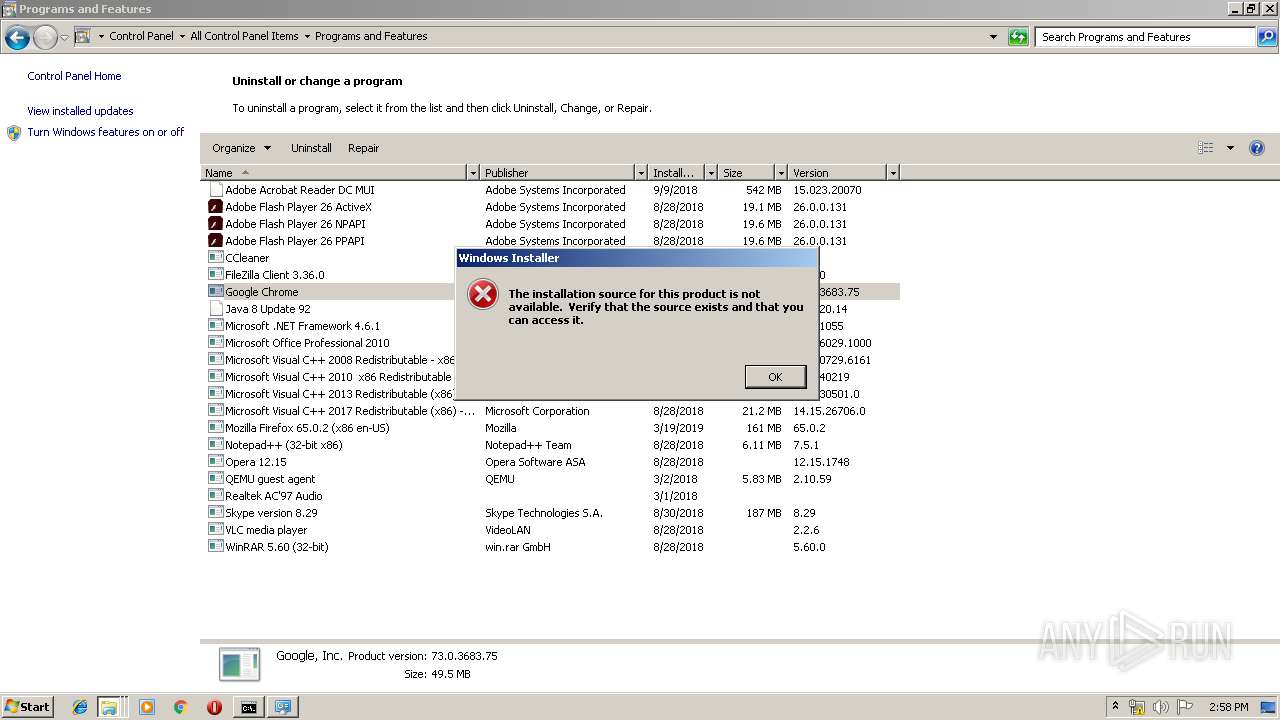
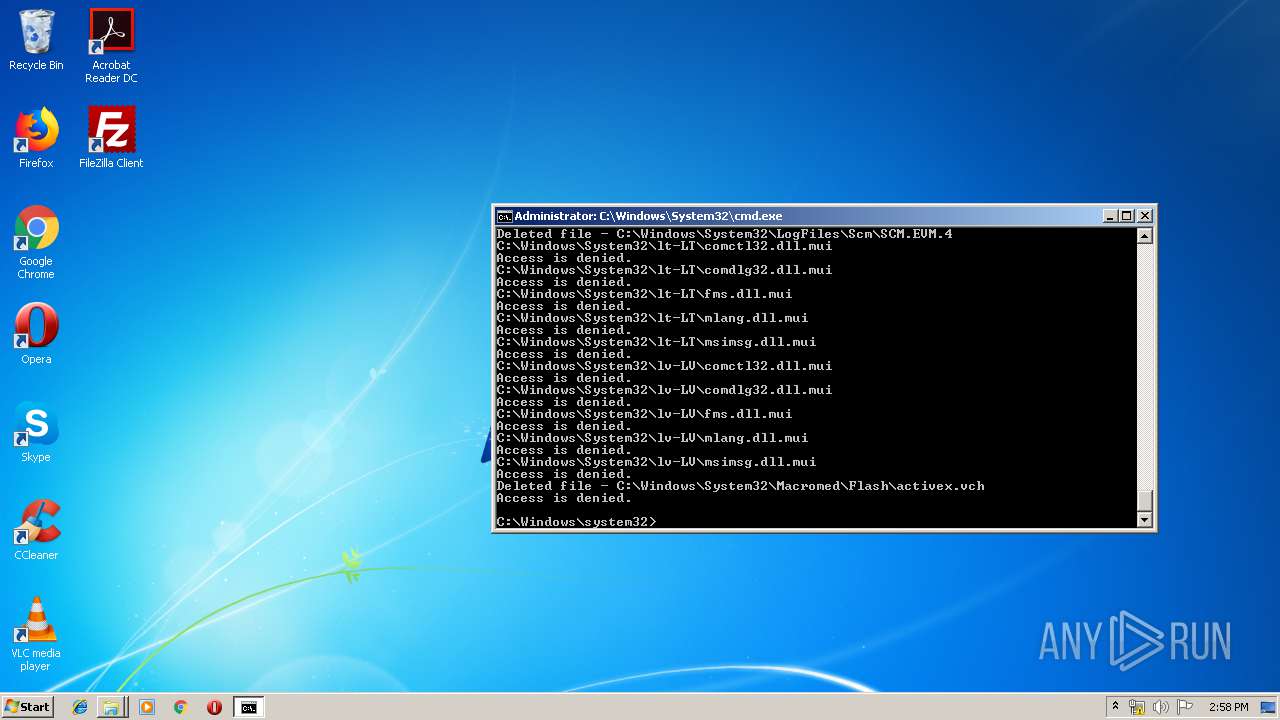
Removes files from Windows directory
- cmd.exe (PID: 284)
INFO
Manual execution by user
- cmd.exe (PID: 3720)
- explorer.exe (PID: 2532)
- cmd.exe (PID: 3420)
- cmd.exe (PID: 284)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
62
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2532 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2976 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3076 | explorer | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3132 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
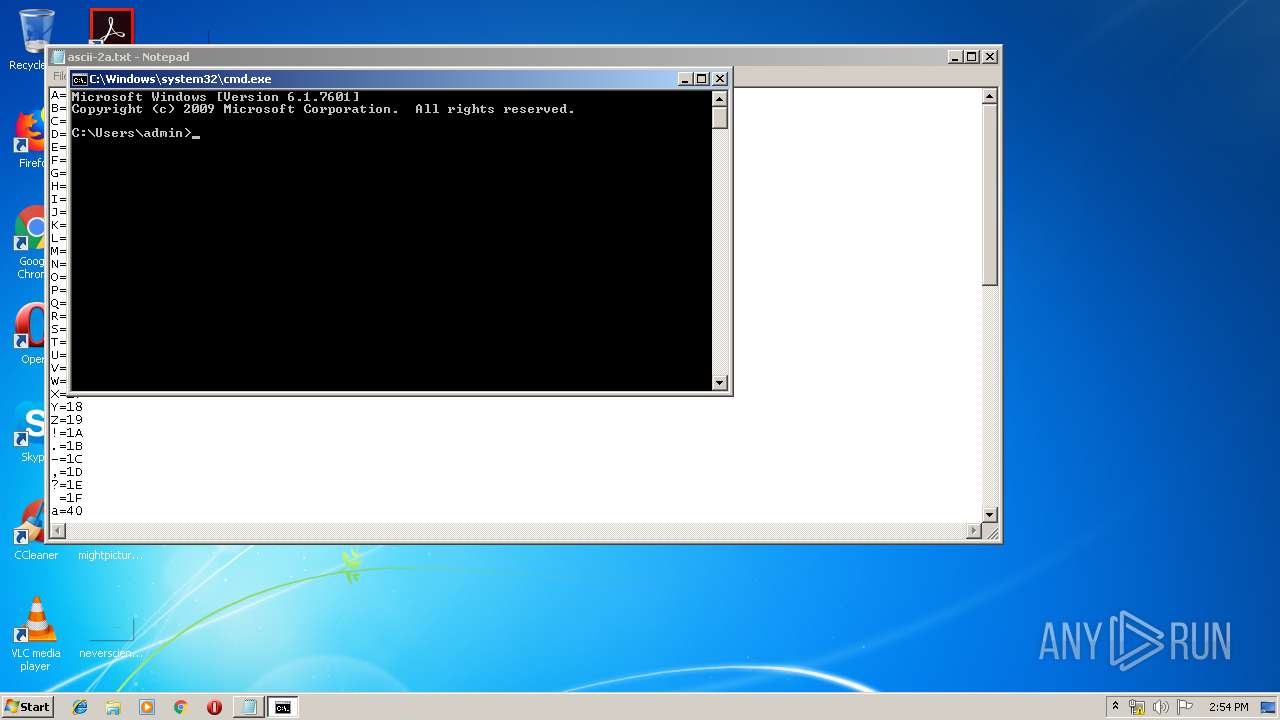
| 3288 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\ascii-2a.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3420 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3720 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3904 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
279
Read events
253
Write events
14
Delete events
12
Modification events
| (PID) Process: | (3288) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosX |
Value: 44 | |||
| (PID) Process: | (3288) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosY |
Value: 44 | |||
| (PID) Process: | (3288) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDX |
Value: 960 | |||
| (PID) Process: | (3288) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDY |
Value: 501 | |||
| (PID) Process: | (3904) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 400F00006BF8AC1A4B24D501 | |||
| (PID) Process: | (3904) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: B285DAE144D9DB1D9E9D86076FA651F4662CAC7D2FACF67E42F51EBBDA43BA23 | |||
| (PID) Process: | (3904) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3904) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
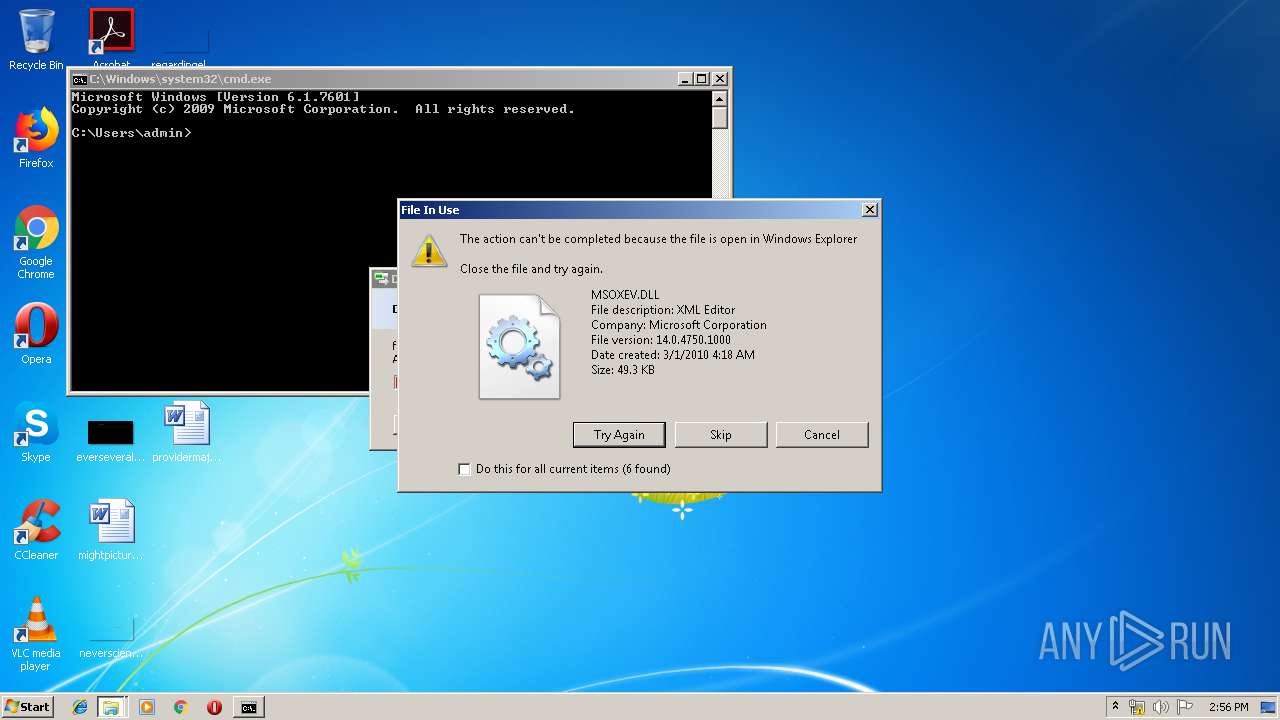
Value: C:\Program Files\Common Files\microsoft shared\OFFICE14\MSOXEV.DLL | |||
| (PID) Process: | (3904) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: FA2E057B3BD9169C52BEC828736D88D2E1D169D3A94CBA9825A13FB75A92BDE1 | |||
| (PID) Process: | (3904) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFilesHash |
Value: FA2E057B3BD9169C52BEC828736D88D2E1D169D3A94CBA9825A13FB75A92BDE1 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report