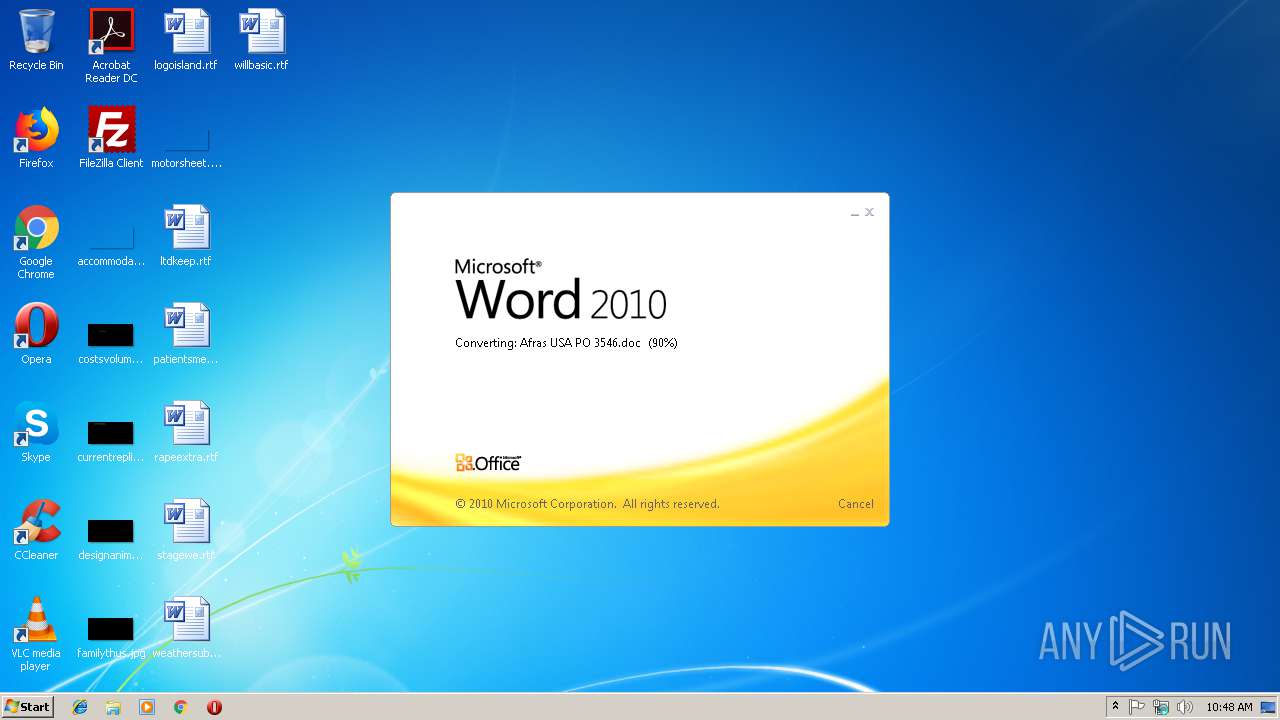
| File name: | Afras USA PO 3546.doc |
| Full analysis: | https://app.any.run/tasks/ed86d197-bc20-479c-b298-84082b550413 |
| Verdict: | Malicious activity |
| Analysis date: | January 23, 2019, 10:48:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, version 1, unknown character set |
| MD5: | 112BB054B7BD80238EC5AE7E01D37CEB |
| SHA1: | 538F41BA7210B1966DB66DC645ADF5DCF13C3A65 |
| SHA256: | C9C61C6065A6F545557FBEF5DBFC7223022259C5F8419A74CBFAF742BFCE6FFD |
| SSDEEP: | 12288:zPPZ5ha1mi0UNOtrH9uA8hE47nJF/xNXqKIopHE79LS+4a1PpF84Ji6mE1S+0luT:zPLha1mi0U6rH9T8B7PEUk79LS+4OPpf |
MALICIOUS
Runs app for hidden code execution
- cmd.exe (PID: 2612)
- cmd.exe (PID: 3952)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2880)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 2880)
Application was dropped or rewritten from another process
- saver.scr (PID: 3796)
- Saver.SCR (PID: 2608)
- Host.exe (PID: 3108)
SUSPICIOUS
Uses TASKKILL.EXE to kill Office Apps
- cmd.exe (PID: 2632)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2612)
- cmd.exe (PID: 2360)
- cmd.exe (PID: 3952)
- cmd.exe (PID: 2632)
Executes scripts
- cmd.exe (PID: 2632)
Executable content was dropped or overwritten
- cscript.exe (PID: 2232)
- Saver.SCR (PID: 2608)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2632)
- cmd.exe (PID: 2364)
- cmd.exe (PID: 3096)
- cmd.exe (PID: 1760)
- cmd.exe (PID: 3204)
- cmd.exe (PID: 3548)
- cmd.exe (PID: 3172)
Application launched itself
- cmd.exe (PID: 2632)
- saver.scr (PID: 3796)
Starts application with an unusual extension
- cmd.exe (PID: 2632)
- saver.scr (PID: 3796)
Creates files in the user directory
- Saver.SCR (PID: 2608)
Starts itself from another location
- Saver.SCR (PID: 2608)
INFO
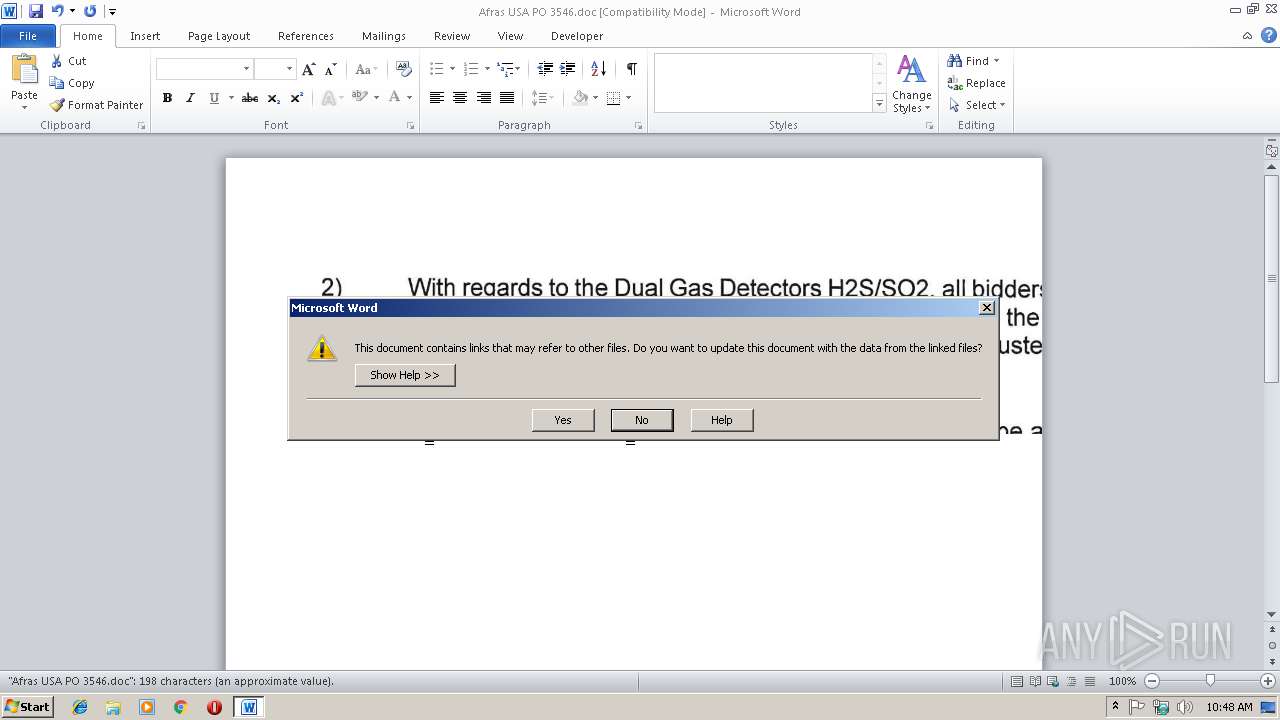
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2880)
Creates files in the user directory
- WINWORD.EXE (PID: 2880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
Total processes
70
Monitored processes
39
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1760 | C:\Windows\system32\cmd.exe /c REG QUERY "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\13.0\Word\File MRU" /v "Item 1" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2232 | cscript //nologo "C:\Users\admin\AppData\Local\Temp\_.vbs" | C:\Windows\system32\cscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2264 | REG QUERY "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\11.0\Word\File MRU" /v "Item 1" | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2324 | REG QUERY "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\15.0\Word\File MRU" /v "Item 1" | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2348 | REG QUERY "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\13.0\Word\File MRU" /v "Item 1" | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2360 | CmD | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2364 | C:\Windows\system32\cmd.exe /c REG QUERY "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\11.0\Word\File MRU" /v "Item 1" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2544 | TIMEOUT /T 1 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2608 | "C:\Users\admin\AppData\Local\temp\Saver.SCR" | C:\Users\admin\AppData\Local\temp\Saver.SCR | saver.scr | ||||||||||||
User: admin Company: American Express Company Integrity Level: MEDIUM Description: ISAPI filter module Exit code: 0 Version: 11.11.12.4 Modules
| |||||||||||||||
| 2612 | "C:\Windows\System32\cmd.exe" /C CmD < "C:\Users\admin\AppData\Local\Temp\ufFm.cMD" | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 481
Read events
1 448
Write events
30
Delete events
3
Modification events
| (PID) Process: | (2880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 9$ |
Value: 397F2400400B0000010000000000000000000000 | |||
| (PID) Process: | (2880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2880) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1312227358 | |||
| (PID) Process: | (2880) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1312227472 | |||
| (PID) Process: | (2880) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1312227473 | |||
| (PID) Process: | (2880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 400B0000B067EE3909B3D40100000000 | |||
| (PID) Process: | (2880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | -a$ |
Value: 2D612400400B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | -a$ |
Value: 2D612400400B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
4
Text files
13
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2880 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR9BB9.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2880 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\itnqknf5.cmd | text | |
MD5:— | SHA256:— | |||
| 2880 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$ras USA PO 3546.doc | pgc | |
MD5:— | SHA256:— | |||
| 2880 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2632 | cmd.exe | C:\Users\admin\AppData\Local\Temp\_.vbs | text | |
MD5:— | SHA256:— | |||
| 2880 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\a.ScT | xml | |
MD5:— | SHA256:— | |||
| 2880 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\itn.zip | compressed | |
MD5:— | SHA256:— | |||
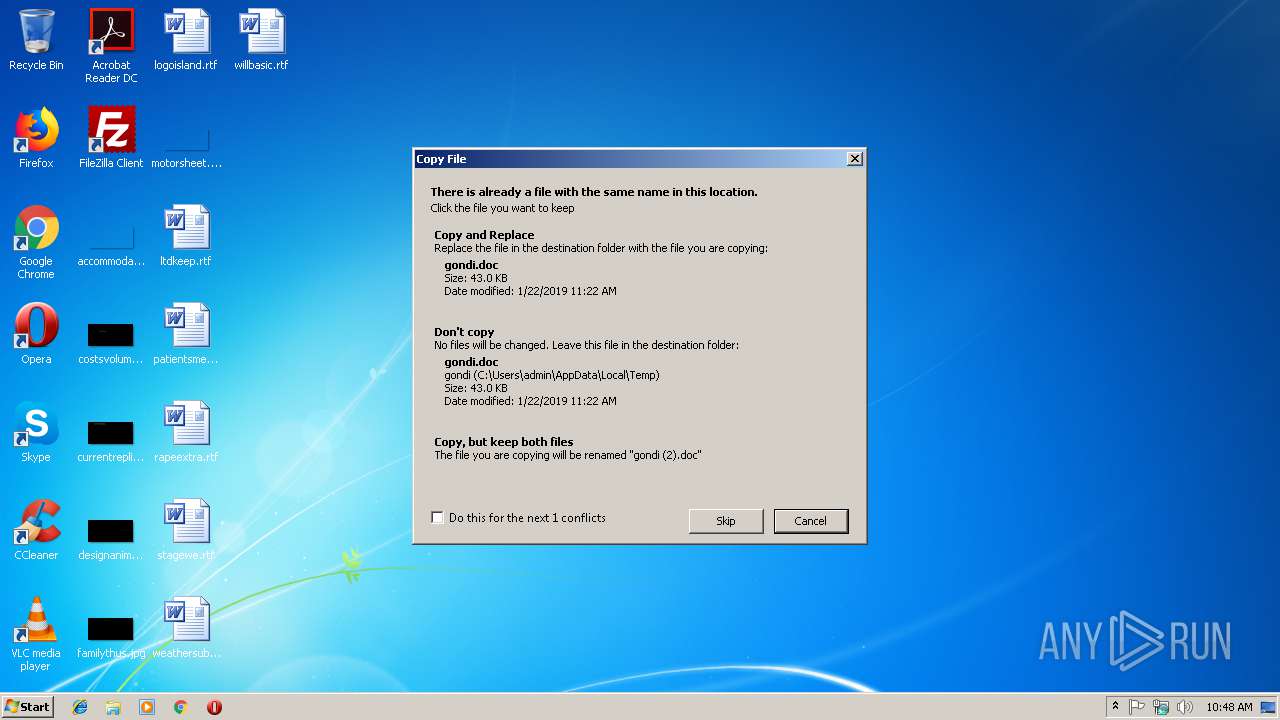
| 2232 | cscript.exe | C:\Users\admin\AppData\Local\Temp\gondi.doc | document | |
MD5:— | SHA256:— | |||
| 2232 | cscript.exe | C:\Users\admin\AppData\Local\Temp\saver.scr | executable | |
MD5:— | SHA256:— | |||
| 2880 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{4E0FCACC-C084-47EE-9E79-E7B760733F9B}.tmp | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report