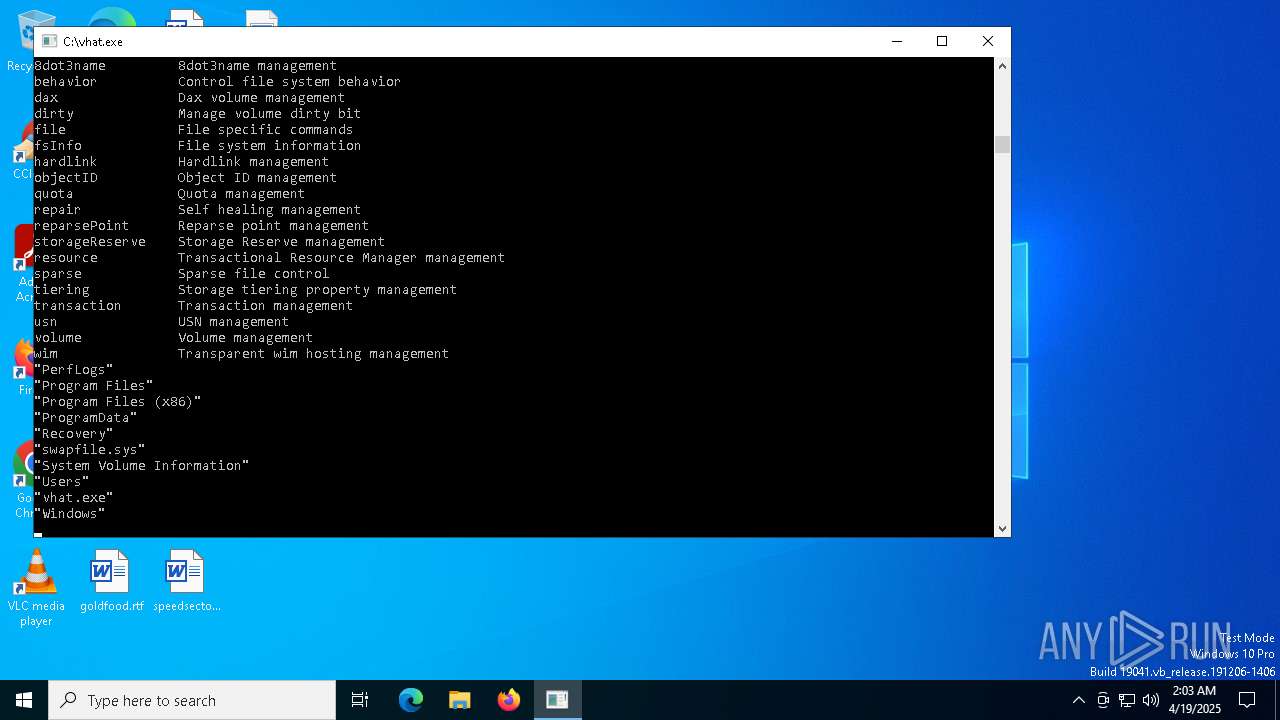
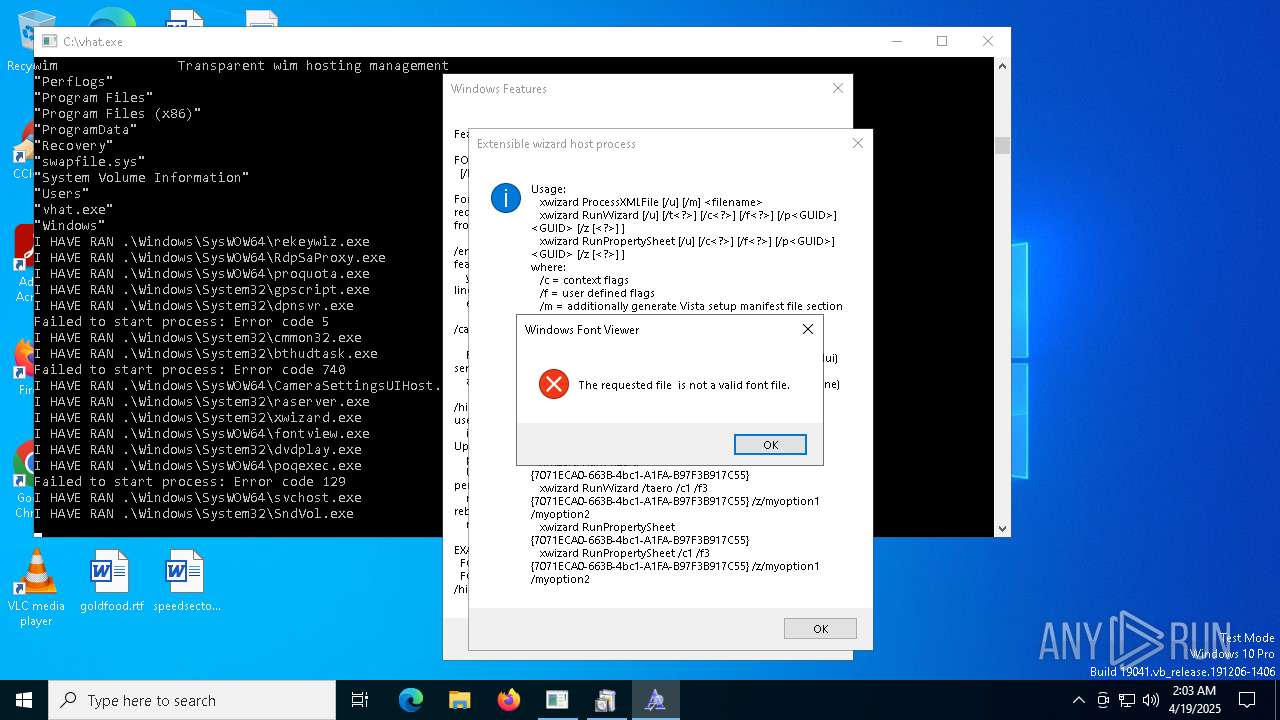
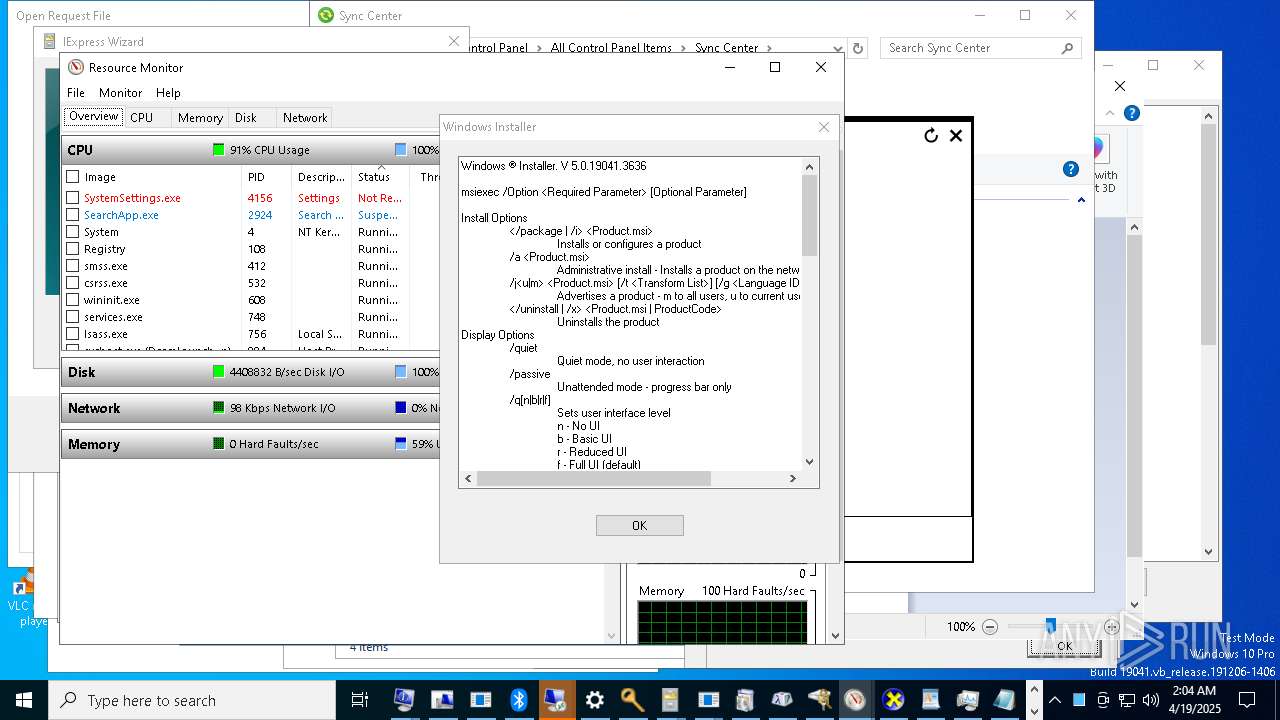
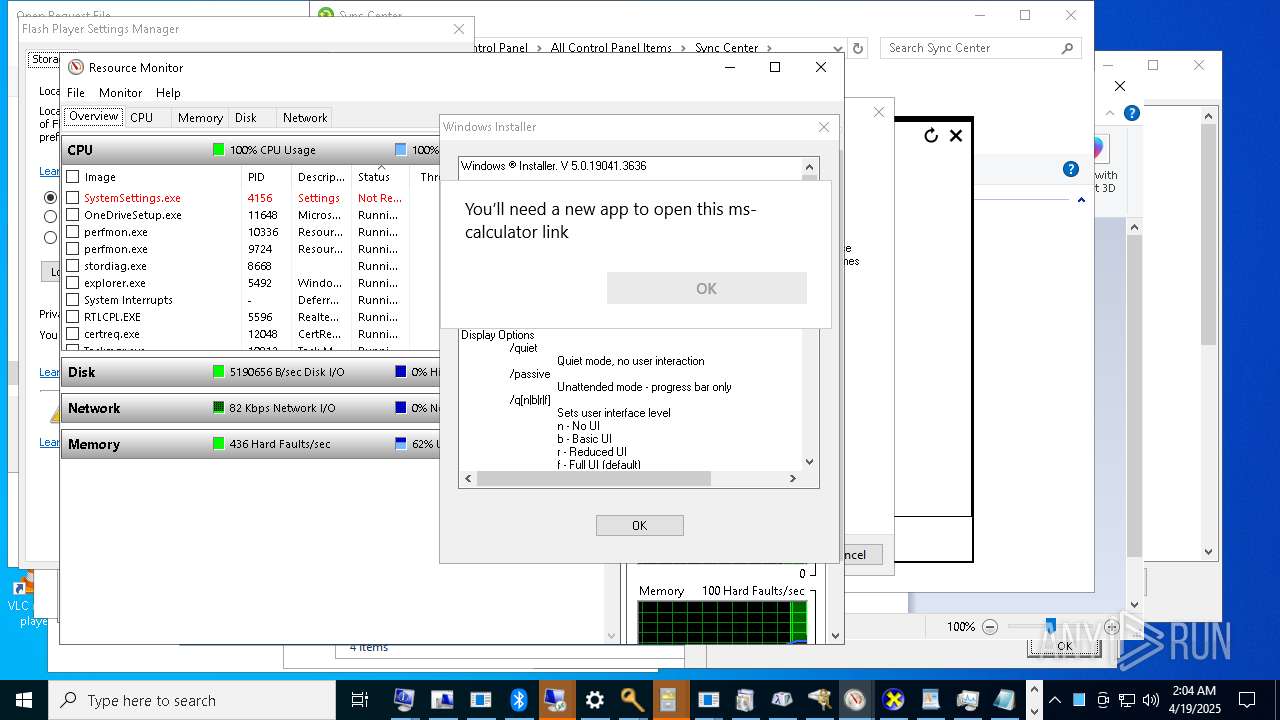
| File name: | vhat.exe |
| Full analysis: | https://app.any.run/tasks/e842ab4a-af9e-4e4a-ad85-67df5e6d3b62 |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2025, 02:03:37 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 4 sections |
| MD5: | 5FF75CA5795235EC29125BC6E2E0FC03 |
| SHA1: | 9421B8F5F85596930FD2D1B13B1A5EF502AC1863 |
| SHA256: | C9C4F06E5AFC509C4253345C323FC438C845ECAB0EF91BDDD52AF884E67F247E |
| SSDEEP: | 768:SQAm3cTxyWUucgFwTj9lIUDokoY3Em+mT4mIt:KMGgWNcdbREU3Em7e |
MALICIOUS
Antivirus name has been found in the command line (generic signature)
- sfc.exe (PID: 7824)
Registers / Runs the DLL via REGSVR32.EXE
- vhat.exe (PID: 1272)
SUSPICIOUS
Creates file in the systems drive root
- vhat.exe (PID: 1272)
- conhost.exe (PID: 7000)
- SndVol.exe (PID: 7472)
- compact.exe (PID: 9764)
- perfmon.exe (PID: 10336)
- Taskmgr.exe (PID: 10812)
- perfmon.exe (PID: 9724)
- RTLCPL.EXE (PID: 5596)
Windows service management via SC.EXE
- sc.exe (PID: 1660)
- sc.exe (PID: 5244)
Executes as Windows Service
- dllhost.exe (PID: 5800)
- msdtc.exe (PID: 7508)
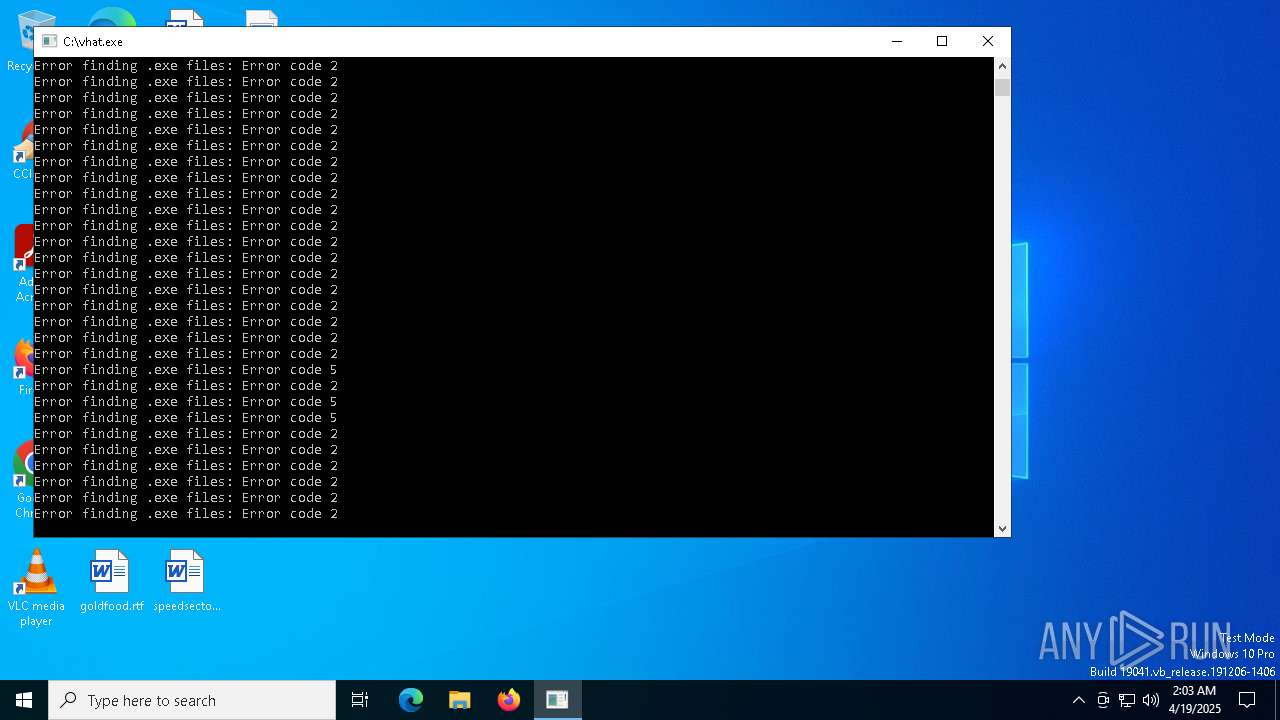
Searches and executes a command on selected files
- forfiles.exe (PID: 1188)
- forfiles.exe (PID: 9756)
Starts CMD.EXE for commands execution
- forfiles.exe (PID: 1188)
- forfiles.exe (PID: 9756)
Reads security settings of Internet Explorer
- wmplayer.exe (PID: 7436)
- GetHelp.exe (PID: 8252)
- perfmon.exe (PID: 5136)
- wmplayer.exe (PID: 10268)
- perfmon.exe (PID: 11356)
- FlashPlayerApp.exe (PID: 13300)
Uses ROUTE.EXE to obtain the routing table information
- vhat.exe (PID: 1272)
Executes application which crashes
- Windows.WARP.JITService.exe (PID: 7604)
- Windows.WARP.JITService.exe (PID: 8760)
- SystemSettings.exe (PID: 8048)
- WWAHost.exe (PID: 11020)
- PrintDialog.exe (PID: 5744)
- WWAHost.exe (PID: 8584)
Process copies executable file
- vhat.exe (PID: 1272)
Reads the history of recent RDP connections
- mstsc.exe (PID: 7596)
- mstsc.exe (PID: 7616)
- mstsc.exe (PID: 8052)
- mstsc.exe (PID: 8356)
Suspicious use of NETSH.EXE
- vhat.exe (PID: 1272)
Reads Internet Explorer settings
- IEChooser.exe (PID: 7248)
- IEChooser.exe (PID: 12388)
- mshta.exe (PID: 5132)
SQL CE related mutex has been found
- unregmp2.exe (PID: 7432)
Application launched itself
- msdt.exe (PID: 8424)
- OneDriveSetup.exe (PID: 2344)
Reads Microsoft Outlook installation path
- IEChooser.exe (PID: 7248)
- IEChooser.exe (PID: 12388)
- mshta.exe (PID: 5132)
Uses SYSTEMINFO.EXE to read the environment
- stordiag.exe (PID: 8668)
- vhat.exe (PID: 1272)
Query current time using 'w32tm.exe'
- vhat.exe (PID: 1272)
- w32tm.exe (PID: 2800)
- w32tm.exe (PID: 11064)
Process uses IPCONFIG to get network configuration information
- vhat.exe (PID: 1272)
Uses DRIVERQUERY.EXE to obtain a list of installed device drivers
- vhat.exe (PID: 1272)
Uses ICACLS.EXE to modify access control lists
- vhat.exe (PID: 1272)
Uses powercfg.exe to modify the power settings
- vhat.exe (PID: 1272)
Uses NSLOOKUP.EXE to check DNS info
- vhat.exe (PID: 1272)
Uses TASKKILL.EXE to kill process
- vhat.exe (PID: 1272)
Get information on the list of running processes
- vhat.exe (PID: 1272)
Using 'findstr.exe' to search for text patterns in files and output
- vhat.exe (PID: 1272)
The process checks if it is being run in the virtual environment
- perfmon.exe (PID: 10336)
- perfmon.exe (PID: 9724)
The system shut down or reboot
- vhat.exe (PID: 1272)
Starts another process probably with elevated privileges via RUNAS.EXE
- runas.exe (PID: 4784)
- runas.exe (PID: 11736)
Start notepad (likely ransomware note)
- vhat.exe (PID: 1272)
Uses ATTRIB.EXE to modify file attributes
- vhat.exe (PID: 1272)
Identifying current user with WHOAMI command
- vhat.exe (PID: 1272)
Sets XML DOM element text (SCRIPT)
- splwow64.exe (PID: 9380)
Uses TIMEOUT.EXE to delay execution
- vhat.exe (PID: 1272)
Uses WEVTUTIL.EXE to event management in Windows
- vhat.exe (PID: 1272)
Uses WMIC.EXE
- vhat.exe (PID: 1272)
Executable content was dropped or overwritten
- OneDriveSetup.exe (PID: 11648)
- RTLCPL.EXE (PID: 5596)
The process creates files with name similar to system file names
- OneDriveSetup.exe (PID: 11648)
The process drops C-runtime libraries
- OneDriveSetup.exe (PID: 11648)
INFO
Checks supported languages
- vhat.exe (PID: 1272)
- wmplayer.exe (PID: 7436)
- Windows.WARP.JITService.exe (PID: 7604)
- setup_wm.exe (PID: 7884)
- PresentationHost.exe (PID: 8048)
- GetHelp.exe (PID: 8252)
- extrac32.exe (PID: 8580)
- agentactivationruntimestarter.exe (PID: 8128)
- SystemSettings.exe (PID: 8048)
- tar.exe (PID: 2040)
- Windows.WARP.JITService.exe (PID: 8760)
- SOUNDMAN.EXE (PID: 9316)
- curl.exe (PID: 9896)
- Alcrmv64.exe (PID: 10100)
- extrac32.exe (PID: 10268)
- PSEXESVC.exe (PID: 10396)
- wordpad.exe (PID: 10564)
- BitLockerToGo.exe (PID: 10696)
- PrintDialog.exe (PID: 5744)
- perfmon.exe (PID: 5136)
- perfmon.exe (PID: 10336)
- wmplayer.exe (PID: 10268)
- curl.exe (PID: 9372)
- setup_wm.exe (PID: 4152)
- expand.exe (PID: 10068)
- PresentationHost.exe (PID: 11728)
- perfmon.exe (PID: 11356)
- perfmon.exe (PID: 9724)
- agentactivationruntimestarter.exe (PID: 11652)
- TrustedInstaller.exe (PID: 11912)
- RTLCPL.EXE (PID: 5596)
- FlashPlayerApp.exe (PID: 13300)
- TpmTool.exe (PID: 12864)
- tar.exe (PID: 12924)
- RTBK.EXE (PID: 12352)
- CPLUtl64.exe (PID: 12408)
Checks transactions between databases Windows and Oracle
- dllhost.exe (PID: 5800)
- msdtc.exe (PID: 7508)
Creates files in the program directory
- RMActivate_ssp.exe (PID: 5640)
- wermgr.exe (PID: 8504)
Disables trace logs
- cmmon32.exe (PID: 7248)
- cmdl32.exe (PID: 7928)
- rasdial.exe (PID: 7576)
- rasphone.exe (PID: 10384)
- cmstp.exe (PID: 7656)
Reads the computer name
- wmplayer.exe (PID: 7436)
- setup_wm.exe (PID: 7884)
- GetHelp.exe (PID: 8252)
- extrac32.exe (PID: 8580)
- agentactivationruntimestarter.exe (PID: 8128)
- SystemSettings.exe (PID: 8048)
- extrac32.exe (PID: 10268)
- PSEXESVC.exe (PID: 10396)
- BitLockerToGo.exe (PID: 10696)
- wordpad.exe (PID: 10564)
- perfmon.exe (PID: 5136)
- PrintDialog.exe (PID: 5744)
- perfmon.exe (PID: 10336)
- wmplayer.exe (PID: 10268)
- setup_wm.exe (PID: 4152)
- perfmon.exe (PID: 11356)
- perfmon.exe (PID: 9724)
- agentactivationruntimestarter.exe (PID: 11652)
- TrustedInstaller.exe (PID: 11912)
- FlashPlayerApp.exe (PID: 13300)
- RTLCPL.EXE (PID: 5596)
- RTBK.EXE (PID: 12352)
Process checks computer location settings
- wmplayer.exe (PID: 7436)
- setup_wm.exe (PID: 7884)
- perfmon.exe (PID: 5136)
- wmplayer.exe (PID: 10268)
- perfmon.exe (PID: 11356)
Create files in a temporary directory
- unregmp2.exe (PID: 7996)
- msdt.exe (PID: 8424)
- msdt.exe (PID: 8224)
- stordiag.exe (PID: 8668)
- OneDriveSetup.exe (PID: 2344)
- ddodiag.exe (PID: 5596)
- msdt.exe (PID: 11336)
- OneDriveSetup.exe (PID: 11648)
- OneDriveSetup.exe (PID: 12888)
- RTLCPL.EXE (PID: 5596)
Modifies the entries in the local IP routing table
- ROUTE.EXE (PID: 8124)
- ROUTE.EXE (PID: 12932)
Reads security settings of Internet Explorer
- unregmp2.exe (PID: 7996)
- mstsc.exe (PID: 7596)
- HelpPane.exe (PID: 8156)
- IEChooser.exe (PID: 7248)
- msdt.exe (PID: 8424)
- mstsc.exe (PID: 7616)
- RdpSaProxy.exe (PID: 516)
- mstsc.exe (PID: 8356)
- mstsc.exe (PID: 8052)
- TsWpfWrp.exe (PID: 8476)
- DpiScaling.exe (PID: 9652)
- explorer.exe (PID: 9816)
- RdpSaProxy.exe (PID: 8976)
- explorer.exe (PID: 9888)
- TsWpfWrp.exe (PID: 9648)
- write.exe (PID: 11232)
- cleanmgr.exe (PID: 11084)
- resmon.exe (PID: 10604)
- unregmp2.exe (PID: 10432)
- splwow64.exe (PID: 9380)
- OneDriveSetup.exe (PID: 2344)
- LaunchTM.exe (PID: 11164)
- explorer.exe (PID: 7708)
- stordiag.exe (PID: 8668)
- DpiScaling.exe (PID: 8480)
- explorer.exe (PID: 9668)
- resmon.exe (PID: 11324)
- Taskmgr.exe (PID: 10812)
- OneDriveSetup.exe (PID: 11648)
- certreq.exe (PID: 12048)
- calc.exe (PID: 10536)
- IEChooser.exe (PID: 12388)
- WMIC.exe (PID: 12780)
- OpenWith.exe (PID: 9096)
- WMIC.exe (PID: 12428)
- mshta.exe (PID: 5132)
Creates files or folders in the user directory
- wiaacmgr.exe (PID: 2420)
- unregmp2.exe (PID: 7432)
- WerFault.exe (PID: 1228)
- IEChooser.exe (PID: 7248)
- WerFault.exe (PID: 8536)
- WerFault.exe (PID: 9452)
- OneDriveSetup.exe (PID: 2344)
- WerFault.exe (PID: 11028)
- RMActivate.exe (PID: 11252)
- WerFault.exe (PID: 11180)
- WerFault.exe (PID: 10396)
- OneDriveSetup.exe (PID: 11648)
- Taskmgr.exe (PID: 10812)
- OneDriveSetup.exe (PID: 12888)
- IEChooser.exe (PID: 12388)
- FlashPlayerApp.exe (PID: 13300)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 7436)
Reads Environment values
- GetHelp.exe (PID: 8252)
Reads the software policy settings
- TsWpfWrp.exe (PID: 8476)
- TsWpfWrp.exe (PID: 9648)
- OneDriveSetup.exe (PID: 2344)
- stordiag.exe (PID: 8668)
- OneDriveSetup.exe (PID: 11648)
Checks proxy server information
- TsWpfWrp.exe (PID: 8476)
- TsWpfWrp.exe (PID: 9648)
Execution of CURL command
- vhat.exe (PID: 1272)
Failed to create an executable file in Windows directory
- fixmapi.exe (PID: 9756)
- fixmapi.exe (PID: 6736)
Uses BITSADMIN.EXE
- vhat.exe (PID: 1272)
Reads CPU info
- perfmon.exe (PID: 10336)
- perfmon.exe (PID: 9724)
Reads the time zone
- perfmon.exe (PID: 10336)
- runonce.exe (PID: 2152)
- perfmon.exe (PID: 9724)
- runonce.exe (PID: 12188)
The sample compiled with english language support
- OneDriveSetup.exe (PID: 11648)
- RTLCPL.EXE (PID: 5596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win16/32 Executable Delphi generic (34.1) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (32.9) |
| .exe | | | DOS Executable Generic (32.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:04:19 01:55:20+00:00 |
| ImageFileCharacteristics: | Executable, Bytes reversed lo, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.18 |
| CodeSize: | 29184 |
| InitializedDataSize: | 3584 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16a0 |
| OSVersion: | 1.11 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
Total processes
711
Monitored processes
551
Malicious processes
5
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | ".\Windows\SysWOW64\RdpSaProxy.exe" | C:\Windows\SysWOW64\RdpSaProxy.exe | — | vhat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: RDP Session Agent Proxy Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | ".\Windows\System32\clip.exe" | C:\Windows\SysWOW64\clip.exe | — | vhat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Clip - copies the data into clipboard Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | ".\Windows\System32\schtasks.exe" | C:\Windows\SysWOW64\schtasks.exe | — | vhat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | ".\Windows\HelpPane.exe" | C:\Windows\HelpPane.exe | — | vhat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Help and Support Exit code: 4294967295 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | ".\Windows\System32\RpcPing.exe" | C:\Windows\SysWOW64\RpcPing.exe | — | vhat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: RPC Ping Utility Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | ".\Windows\System32\SyncHost.exe" | C:\Windows\SysWOW64\SyncHost.exe | — | vhat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Sync Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 872 | ".\Windows\SysWOW64\perfmon.exe" | C:\Windows\SysWOW64\perfmon.exe | — | vhat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Resource and Performance Monitor Exit code: 3221226540 Version: 10.00 Modules
| |||||||||||||||
| 960 | ".\Windows\System32\w32tm.exe" | C:\Windows\System32\w32tm.exe | — | w32tm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Time Service Diagnostic Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | ".\Windows\System32\netbtugc.exe" | C:\Windows\SysWOW64\netbtugc.exe | — | vhat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NetBT Unattend Generic Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1004 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
87 891
Read events
87 557
Write events
275
Delete events
59
Modification events
| (PID) Process: | (5800) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Ole\Instrumentation |
| Operation: | write | Name: | InstrumentationLogFileDir |
Value: C:\WINDOWS\system32\com | |||
| (PID) Process: | (7248) cmmon32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\CMMON32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7248) cmmon32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\CMMON32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7248) cmmon32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\CMMON32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (7248) cmmon32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\CMMON32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (7248) cmmon32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\CMMON32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (7248) cmmon32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\CMMON32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (7248) cmmon32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\CMMON32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (7884) setup_wm.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\MediaPlayer\Preferences |
| Operation: | delete value | Name: | UsageTracking |
Value: | |||
| (PID) Process: | (7884) setup_wm.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\MediaPlayer\Preferences |
| Operation: | delete value | Name: | ForceUsageTracking |
Value: | |||
Executable files
98
Suspicious files
37
Text files
70
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1228 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_Windows.WARP.JIT_7f62154bdac86d6e50d9d95360b25359a157d2f_2f81cf5c_1ae02f15-d4c5-40fb-b516-80f491f8bad6\Report.wer | — | |
MD5:— | SHA256:— | |||
| 8536 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_Windows.WARP.JIT_7f62154bdac86d6e50d9d95360b25359a157d2f_2f81cf5c_7234155f-6cd3-4471-b4d5-13e1c11eb6db\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5640 | RMActivate_ssp.exe | C:\ProgramData\Microsoft\DRM\Server\S-1-5-21-1693682860-607145093-2874071422-1001\CERT-Machine.drm | binary | |
MD5:6B271CF4E71028D2B0AAB01574AC29CF | SHA256:9671F565369DB1B10706042A0B8498BCF7477FAEBF7B92041757489620362DA8 | |||
| 5640 | RMActivate_ssp.exe | C:\ProgramData\Microsoft\DRM\Server\S-1-5-21-1693682860-607145093-2874071422-1001\CERT-Machine-2048.drm | binary | |
MD5:727EFB3E87F7105E2648B7217BF45C3C | SHA256:C7E47DA8E01E1568B69043488A3981FD08BFDBC182F201EEEBE94B8EA233EA7E | |||
| 5800 | dllhost.exe | C:\Windows\Registration\{02D4B3F1-FD88-11D1-960D-00805FC79235}.{8A5722A3-207F-4F9E-9393-10E46600F2F9}.crmlog | binary | |
MD5:306A5E959D38BC962C6D24E5952B18F3 | SHA256:FA46832D1B9F12416FC3216A81BF5E251134137BBF65F3E8513A3C8E5FD4F0B0 | |||
| 7996 | unregmp2.exe | C:\Users\admin\AppData\Local\Temp\wmsetup.log | text | |
MD5:35517ABF005619BF37240AD13D2EDF33 | SHA256:1E7D1F769594CF7AE57B83A3C8FDE580F262F47084F2385A5FAB1D5B32AF1DDF | |||
| 7432 | unregmp2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.XML | text | |
MD5:5433EAB10C6B5C6D55B7CBD302426A39 | SHA256:23DBF7014E99E93AF5F2760F18EE1370274F06A453145C8D539B66D798DAD131 | |||
| 7432 | unregmp2.exe | C:\Users\admin\AppData\Local\Microsoft\Media Player\CurrentDatabase_400.wmdb | binary | |
MD5:79AEACC048DB9CA31E1BAF148FFC66C6 | SHA256:9974FC100ABF3300E5EBCAB88D7BA8F66158429E8EBB155F7118AECCC062FFF7 | |||
| 9452 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_SystemSettings.e_7b9fad3f749d9ab87e3cdc494a240af197021a_e3591d10_df64cd30-dafb-4b86-b9a3-427889d1bafc\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7432 | unregmp2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.DTD | xml | |
MD5:90BE2701C8112BEBC6BD58A7DE19846E | SHA256:644FBCDC20086E16D57F31C5BAD98BE68D02B1C061938D2F5F91CBE88C871FBF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
37
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.142.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.142.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 95.101.142.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 95.101.142.9:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.142.9:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
— | — | 95.101.142.9:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3812 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2196 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
3012 | dasHost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
2.100.168.192.in-addr.arpa |
| whitelisted |
158.240.127.40.in-addr.arpa |
| unknown |
9.142.101.95.in-addr.arpa |
| unknown |
250.255.255.239.in-addr.arpa |
| unknown |
252.0.0.224.in-addr.arpa |
| unknown |
3.0.0.0.1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.2.0.f.f.ip6.arpa |
| unknown |
b.f.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.2.0.f.f.ip6.arpa |
| unknown |