| File name: | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.exe |
| Full analysis: | https://app.any.run/tasks/2b33078f-94b9-46da-a503-9292f4ef7dd2 |
| Verdict: | Malicious activity |
| Analysis date: | February 28, 2024, 07:33:06 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 5CA4FE497968B99C596EFF95E1AA9A4F |
| SHA1: | 776732DEFD9C4ABDF35871798AF4379BC925A879 |
| SHA256: | C9B51F852C0CB780BF1CA5BC137DF083AF9C9192188491D8AC1219EC30DE8795 |
| SSDEEP: | 196608:olmiLzc4+1hR+VscvbXnsM8pSOC77Xw+0RuHhr5gE1Nty8P1NqoJB:ymiLY4Mv+VDvbXn0cH7Xv0RS5gek8VJB |
MALICIOUS
Drops the executable file immediately after the start
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.exe (PID: 2696)
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 2460)
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.exe (PID: 6344)
Scans artifacts that could help determine the target
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 2460)
SUSPICIOUS
Executable content was dropped or overwritten
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.exe (PID: 2696)
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 2460)
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.exe (PID: 6344)
Reads security settings of Internet Explorer
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 5844)
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 2460)
Reads the Windows owner or organization settings
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 2460)
Reads the date of Windows installation
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 2460)
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 5844)
Uses TASKKILL.EXE to kill process
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 2460)
Checks Windows Trust Settings
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 2460)
INFO
Checks supported languages
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 5844)
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.exe (PID: 2696)
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 2460)
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.exe (PID: 6344)
Create files in a temporary directory
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.exe (PID: 2696)
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 2460)
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.exe (PID: 6344)
Reads the computer name
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 5844)
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 2460)
Process checks computer location settings
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 5844)
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 2460)
Creates files in the program directory
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 2460)
Reads the software policy settings
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 2460)
- slui.exe (PID: 2756)
Creates files or folders in the user directory
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 2460)
Checks proxy server information
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 2460)
- slui.exe (PID: 2756)
Reads the machine GUID from the registry
- c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp (PID: 2460)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:05:21 05:56:23+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741376 |
| InitializedDataSize: | 465920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.4389 |
| ProductVersionNumber: | 1.0.0.4389 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
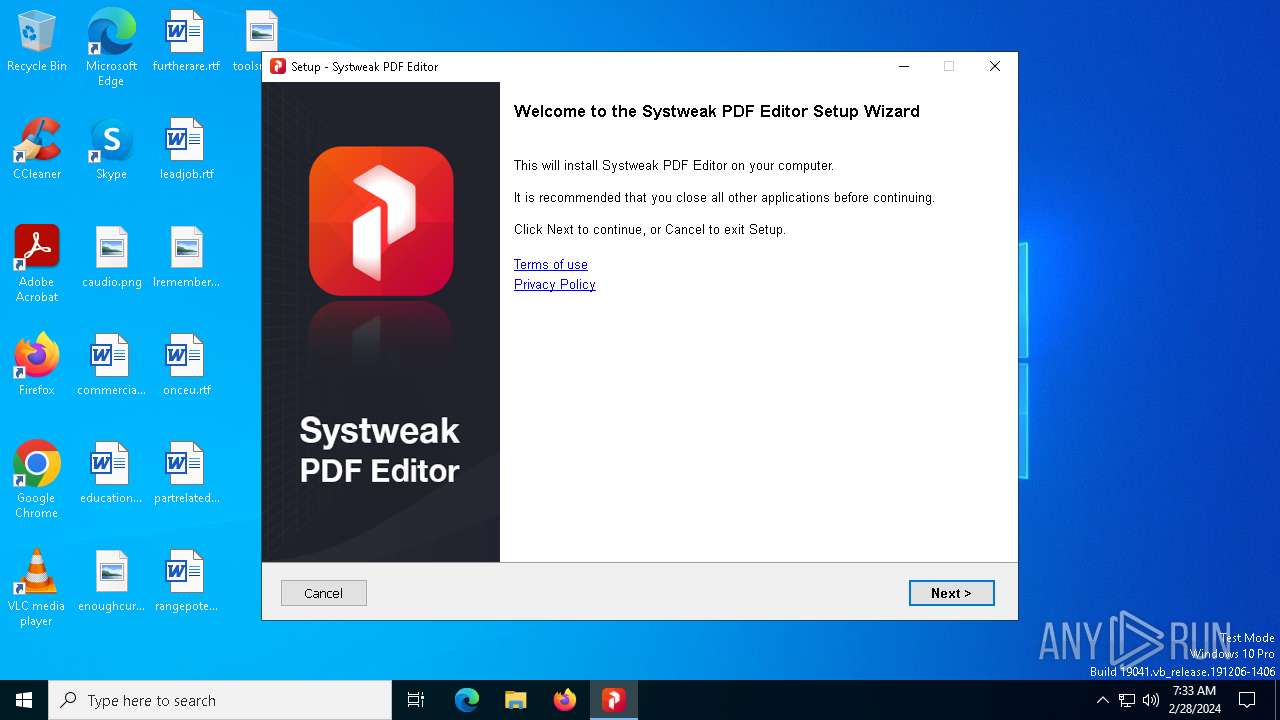
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Copyright © Systweak Software, 1999-2023 All rights reserved |
| FileDescription: | Systweak PDF Editor |
| FileVersion: | 1.0.0.4389 |
| LegalCopyright: | © Copyright © Systweak Software, 1999-2023 All rights reserved. |
| OriginalFileName: | spesetupg_.exe |
| ProductName: | Systweak PDF Editor |
| ProductVersion: | 1.0.0.4389 |
Total processes
145
Monitored processes
13
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 956 | "C:\Windows\System32\taskkill.exe" /f /im "spenotifier.exe" | C:\Windows\SysWOW64\taskkill.exe | — | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1820 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2460 | "C:\Users\admin\AppData\Local\Temp\is-RAP26.tmp\c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp" /SL5="$801C4,30277243,1208320,C:\Users\admin\AppData\Local\Temp\c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.exe" /SPAWNWND=$C01D4 /NOTIFYWND=$801C6 | C:\Users\admin\AppData\Local\Temp\is-RAP26.tmp\c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.exe | ||||||||||||
User: admin Company: Copyright © Systweak Software, 1999-2023 All rights reserved Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2696 | "C:\Users\admin\AppData\Local\Temp\c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.exe" | C:\Users\admin\AppData\Local\Temp\c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.exe | explorer.exe | ||||||||||||
User: admin Company: Copyright © Systweak Software, 1999-2023 All rights reserved Integrity Level: MEDIUM Description: Systweak PDF Editor Exit code: 0 Version: 1.0.0.4389 Modules
| |||||||||||||||
| 2756 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4060 | "C:\Windows\System32\taskkill.exe" /f /im "SystweakPdfEditor.exe" | C:\Windows\SysWOW64\taskkill.exe | — | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4188 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4276 | "C:\Windows\System32\taskkill.exe" /f /im "SystweakPdfEditor.exe" | C:\Windows\SysWOW64\taskkill.exe | — | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5808 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 185
Read events
7 162
Write events
23
Delete events
0
Modification events
| (PID) Process: | (2460) c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 9C0900000F78C279186ADA01 | |||
| (PID) Process: | (2460) c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 09E6D6714B998E53506A72F02FCA499EDC4F1E63B09EEDE33009A4D193D841C2 | |||
| (PID) Process: | (2460) c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2460) c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2460) c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2460) c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2460) c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2460) c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Systweak\Systweak PDF Editor |
| Operation: | write | Name: | AFTINSTS |
Value: 0 | |||
| (PID) Process: | (2460) c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Systweak\Systweak PDF Editor |
| Operation: | write | Name: | AFTINSTS |
Value: 0 | |||
| (PID) Process: | (2460) c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Systweak\Systweak PDF Editor |
| Operation: | write | Name: | IsNLBuild |
Value: 0 | |||
Executable files
11
Suspicious files
3
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2460 | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | C:\ProgramData\DownloadComponents\Aspose.PDF.dll | — | |
MD5:— | SHA256:— | |||
| 2460 | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | C:\Users\admin\AppData\Local\Temp\is-8AKMQ.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 2460 | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B039FEA45CB4CC4BBACFC013C7C55604_50D7940D5D3FEDD8634D83074C7A46A3 | binary | |
MD5:0371876D4A16DC90ABC371B12F1A0B53 | SHA256:3F9E7DF27722E24E6000E444BF22ADA1D93D47849D48680BA20D80379A7F79F6 | |||
| 2460 | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B039FEA45CB4CC4BBACFC013C7C55604_50D7940D5D3FEDD8634D83074C7A46A3 | binary | |
MD5:0B298333583A02C95599C23B9A39AB5B | SHA256:46BCA58FF2BC4A41C8AC069E68F193013CA0FA47C708E6AC558483C523D2B662 | |||
| 2460 | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | C:\Users\admin\AppData\Local\Temp\is-8AKMQ.tmp\idp.dll | executable | |
MD5:55C310C0319260D798757557AB3BF636 | SHA256:54E7E0AD32A22B775131A6288F083ED3286A9A436941377FC20F85DD9AD983ED | |||
| 2460 | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C73FF33095090306CEFC287683582EE9 | binary | |
MD5:62DB17D671C6644E94873FD18B05325F | SHA256:B8D6D94372D8C858CA27FC8717919829896747D3F9443EB8EE3315FAEEE52400 | |||
| 2460 | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C73FF33095090306CEFC287683582EE9 | binary | |
MD5:D8F5791DA661C9F23AF5BF70387486A7 | SHA256:907886D6F2BF82FCDE93C30BC85A17D113E8130F4B9262A4518A208D946A18C5 | |||
| 2460 | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | C:\Users\admin\AppData\Local\Temp\is-8AKMQ.tmp\isxdl.dll | executable | |
MD5:82201CD8F401F00000B7575B24B3AD0B | SHA256:9D64A934A4A12C61A33342151E674100E1EC0074D106612B1E81244234D93D67 | |||
| 2460 | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\gethash[1].txt | text | |
MD5:71908FAA32EDBE678E7C88D31E1E530B | SHA256:1C5FD4EB0A1A3C61A5456BA639C565C391B1B10B7680C51442967898760CF922 | |||
| 6344 | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.exe | C:\Users\admin\AppData\Local\Temp\is-RAP26.tmp\c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | executable | |
MD5:3363AB0DE7E93DAE505659BD91E0D033 | SHA256:CEAB57575E0200A7718FF184675CD79A41641D831FAAB3CBE19A87F60B1AF46F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
37
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2460 | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | GET | 404 | 5.79.122.22:80 | http://track.systweakpdfeditor.com/tempfile/1527470845 | unknown | html | 1.22 Kb | unknown |
2460 | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | GET | 200 | 104.18.21.226:80 | http://ocsp2.globalsign.com/rootr3/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCDQHuXyId%2FGI71DM6hVc%3D | unknown | binary | 1.40 Kb | unknown |
2460 | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | GET | 200 | 184.24.77.54:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgRWYtBEFSrniuoRl6ZT%2F2GQWQ%3D%3D | unknown | binary | 503 b | unknown |
6896 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.01 Kb | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1248 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
1608 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
4916 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.01 Kb | unknown |
2464 | svchost.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5928 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6896 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3848 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
2460 | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | 178.79.242.159:443 | cdn.systweak.com | LLNW | DE | unknown |
2460 | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | 104.18.21.226:80 | ocsp2.globalsign.com | CLOUDFLARENET | — | shared |
2460 | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | 157.245.131.96:443 | www.systweakpdfeditor.com | DIGITALOCEAN-ASN | US | unknown |
2460 | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | 184.24.77.54:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
2460 | c9b51f852c0cb780bf1ca5bc137df083af9c9192188491d8ac1219ec30de8795.tmp | 5.79.122.22:80 | track.systweakpdfeditor.com | LeaseWeb Netherlands B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.systweak.com |
| unknown |
ocsp2.globalsign.com |
| whitelisted |
www.systweakpdfeditor.com |
| unknown |
r3.o.lencr.org |
| shared |
track.systweakpdfeditor.com |
| unknown |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |