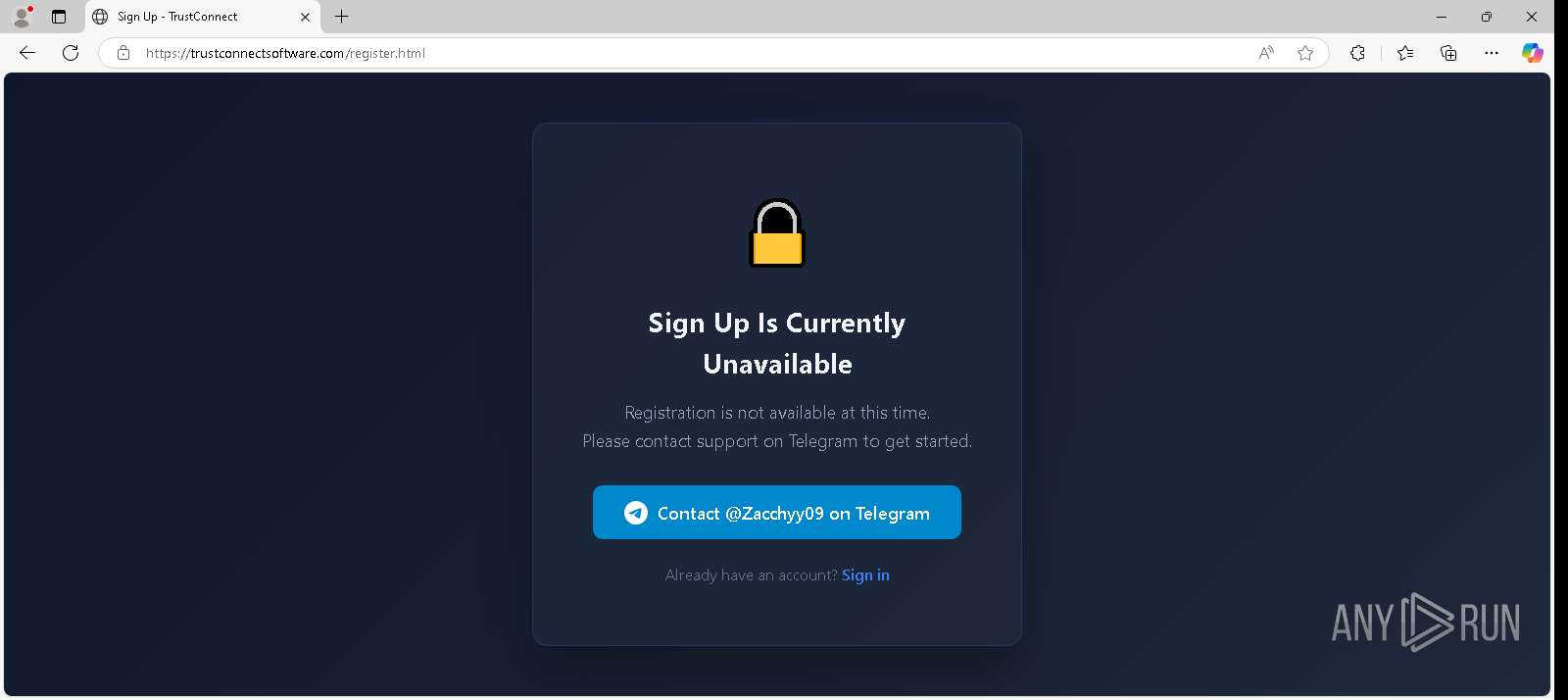
| URL: | trustconnectsoftware.com |
| Full analysis: | https://app.any.run/tasks/81ce0bac-eda1-4c22-b477-825d883ce426 |
| Verdict: | Malicious activity |
| Analysis date: | February 13, 2026, 22:22:19 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 59BB6799E0B47933CCF36FFBAA5E26E3 |
| SHA1: | 5569428EF1738C6751A41A7EED08623FE59F9F3E |
| SHA256: | C99D0971C04AE6CA207F8EBD7E5CC1F23A5C938D47A36296993EE32F21F1FC65 |
| SSDEEP: | 3:q8D0BI:hT |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
170
Monitored processes
1
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 6612 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --webtransport-developer-mode --string-annotations --always-read-main-dll --field-trial-handle=2268,i,4483529040041015744,4079588458005810556,262144 --variations-seed-version --mojo-platform-channel-handle=2612 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
3
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6612 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000b5 | text | |
MD5:5294DAF2F5DDEA3BF4D24C5447475AFF | SHA256:83671031D409FAFA1657F0B299BC4AFA7055C44CC222C1F332FE2FA2FB3F3F52 | |||
| 6612 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000b8 | compressed | |
MD5:14E39BE019DA848A73DA7658165674CB | SHA256:39595A1806156CFCADF3CC4E20C5C3F3EEC721386A0551790A15F025BA9402BD | |||
| 6612 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000b6 | compressed | |
MD5:F3AD19FDBD15A27B32A4D25E49CC266E | SHA256:3A657EDDEC2905CE29950E37A3CC78C6839AFC858FE26A89490A1502BE032D13 | |||
| 6612 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\Network Persistent State | text | |
MD5:F054A7D6E382DF24018FE84986B710A2 | SHA256:4E5235C6B40BCE6C5FD0554D554FCDB38E8016DCDDFA9CAB63103407CAF8DAEB | |||
| 6612 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\22618865-2baa-4a02-9061-137812be9d5a.tmp | text | |
MD5:F054A7D6E382DF24018FE84986B710A2 | SHA256:4E5235C6B40BCE6C5FD0554D554FCDB38E8016DCDDFA9CAB63103407CAF8DAEB | |||
| 6612 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\Network Persistent State~RF147e08.TMP | text | |
MD5:8CA6AC4CD0D4F8B2EA5A9FC6FD4311D7 | SHA256:EE810A451AEA499C3D6F89EDB840ED025DF0937874485A211A3BB39F915F4EA0 | |||
| 6612 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000b7 | compressed | |
MD5:CB803A43F1FD3C541F619F8AD1A97948 | SHA256:B7822481DBE290B28CE433843C7C3F283DEF927EE6BD1610196DE71FCD9BC152 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
67
TCP/UDP connections
67
DNS requests
50
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6244 | svchost.exe | HEAD | 200 | 23.222.48.173:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | whitelisted |
5336 | MoUsoCoreWorker.exe | GET | 304 | 51.124.78.146:443 | https://settings-win.data.microsoft.com/settings/v3.0/wsd/muse?ProcessorClockSpeed=3593&FlightIds=&UpdateOfferedDays=344&BranchReadinessLevel=CB&OEMManufacturerName=DELL&IsCloudDomainJoined=0&ProcessorIdentifier=AMD64%20Family%206%20Model%2014%20Stepping%203&sku=48&ActivationChannel=Retail&AttrDataVer=188&IsMDMEnrolled=0&ProcessorCores=4&ProcessorModel=Intel%28R%29%20Core%28TM%29%20i5-6400%20CPU%20%40%202.70GHz&TotalPhysicalRAM=4096&PrimaryDiskType=4294967295&FlightingBranchName=&ChassisTypeId=1&OEMModelNumber=DELL&SystemVolumeTotalCapacity=260246&sampleId=95271487&deviceClass=Windows.Desktop&App=muse&DisableDualScan=0&AppVer=10.0&OEMSubModel=J5CR&locale=en-US&IsAlwaysOnAlwaysConnectedCapable=0&ms=0&DefaultUserRegion=244&osVer=10.0.19045.4046.amd64fre.vb_release.191206-1406&os=windows&deviceId=s%3ABAD99146-31D3-4EC6-A1A4-BE76F32BA5D4&DeferQualityUpdatePeriodInDays=0&ring=Retail&DeferFeatureUpdatePeriodInDays=30 | unknown | — | — | whitelisted |
5532 | RUXIMICS.exe | GET | 304 | 51.124.78.146:443 | https://settings-win.data.microsoft.com/settings/v3.0/WSD/RUXIM?os=Windows&osVer=10.0.19045.4046.amd64fre.vb_release.191206-1406&sku=48&deviceClass=Windows.Desktop&locale=en-US&deviceId=s:BAD99146-31D3-4EC6-A1A4-BE76F32BA5D4&sampleId=s:95271487&appVer=10.0.19041.3623&OSVersionFull=10.0.19045.4046.amd64fre.vb_release.191206-1406&FlightRing=Retail&AttrDataVer=188&App=RUXIM&AppVer=&DeviceFamily=Windows.Desktop | unknown | — | — | whitelisted |
— | — | POST | 200 | 150.171.27.11:443 | https://edge.microsoft.com/componentupdater/api/v1/update | unknown | binary | 1.57 Kb | unknown |
6612 | msedge.exe | GET | 403 | 185.160.60.100:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/550117a4-8c0f-4d0d-8ff8-7c3caccb0e8a?P1=1757972498&P2=404&P3=2&P4=SosfgGvPP%2bqG%2fKPFOnStRp0ebgR4wibSifLIFAVozbIX%2fohzlu3OKFqIl2l0qzX%2bohjhEGOVS0QtuGPmE2Wd%2bQ%3d%3d | unknown | — | — | whitelisted |
— | — | HEAD | 200 | 23.222.48.173:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | — |
7544 | svchost.exe | GET | 200 | 2.21.23.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | — | 178.128.69.245:443 | https://trustconnectsoftware.com/ | unknown | — | — | — |
5532 | RUXIMICS.exe | GET | 200 | 2.21.23.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1072 | svchost.exe | GET | 200 | 2.21.23.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
7544 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1072 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5532 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5336 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3720 | msedge.exe | 224.0.0.251:5353 | — | — | — | whitelisted |
6612 | msedge.exe | 185.160.60.100:80 | msedge.b.tlu.dl.delivery.mp.microsoft.com | GCORE | LU | whitelisted |
6612 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6612 | msedge.exe | 2.16.106.200:443 | www.bing.com | AKAMAI-ASN1 | NL | whitelisted |
6244 | svchost.exe | 23.222.48.173:443 | fs.microsoft.com | AKAMAI-AS | US | whitelisted |
7544 | svchost.exe | 2.21.23.19:80 | crl.microsoft.com | AKAMAI-ASN1 | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
msedge.b.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
trustconnectsoftware.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
xpaywalletcdn.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6612 | msedge.exe | A Network Trojan was detected | ET MALWARE TrustConnect RAT CnC Domain in DNS Lookup (trustconnectsoftware .com) |
6612 | msedge.exe | A Network Trojan was detected | ET MALWARE TrustConnect RAT CnC Domain in DNS Lookup (trustconnectsoftware .com) |
6612 | msedge.exe | A Network Trojan was detected | ET MALWARE TrustConnect RAT CnC Domain in DNS Lookup (trustconnectsoftware .com) |
6612 | msedge.exe | A Network Trojan was detected | ET MALWARE TrustConnect RAT CnC Domain in DNS Lookup (trustconnectsoftware .com) |
6612 | msedge.exe | A Network Trojan was detected | ET MALWARE TrustConnect RAT CnC Domain in DNS Lookup (trustconnectsoftware .com) |
6612 | msedge.exe | A Network Trojan was detected | ET MALWARE TrustConnect RAT CnC Domain in DNS Lookup (trustconnectsoftware .com) |
6612 | msedge.exe | A Network Trojan was detected | ET MALWARE TrustConnect RAT CnC Domain in DNS Lookup (trustconnectsoftware .com) |
6612 | msedge.exe | A Network Trojan was detected | ET MALWARE TrustConnect RAT CnC Domain in DNS Lookup (trustconnectsoftware .com) |
6612 | msedge.exe | A Network Trojan was detected | ET MALWARE Observed TrustConnect RAT Domain (trustconnectsoftware .com in TLS SNI) |
7544 | svchost.exe | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |