| File name: | laragon.exe |
| Full analysis: | https://app.any.run/tasks/ca956bee-784c-4333-9108-a10d9573b7bb |
| Verdict: | Malicious activity |
| Analysis date: | December 29, 2024, 10:36:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 9 sections |
| MD5: | 7CDF508F8BDA389910A9FDB51889BE3A |
| SHA1: | 30A074B111290D000A22A92F1783ADD9BFB1DBE2 |
| SHA256: | C98CED9E6D035738EB8025ECF96EC028E2F9C09210F0EA204C5D64BDD9712E56 |
| SSDEEP: | 98304:krEhZQcx2VxV+/5eXbjS6sWd0ChRzknU:yS6sW |
MALICIOUS
Executing a file with an untrusted certificate
- curl.exe (PID: 2252)
- curl.exe (PID: 1744)
SUSPICIOUS
Starts CMD.EXE for commands execution
- laragon.exe (PID: 1932)
INFO
Create files in a temporary directory
- laragon.exe (PID: 1932)
Reads the computer name
- laragon.exe (PID: 1932)
- curl.exe (PID: 1744)
- wmpnscfg.exe (PID: 2276)
- curl.exe (PID: 2252)
Reads the machine GUID from the registry
- laragon.exe (PID: 1932)
The sample compiled with english language support
- laragon.exe (PID: 1932)
Checks supported languages
- laragon.exe (PID: 1932)
- curl.exe (PID: 2252)
- curl.exe (PID: 1744)
- wmpnscfg.exe (PID: 2276)
Manual execution by a user
- wmpnscfg.exe (PID: 2276)
Execution of CURL command
- laragon.exe (PID: 1932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (80.2) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (8.4) |
| .exe | | | Win16/32 Executable Delphi generic (3.8) |
| .exe | | | Generic Win/DOS Executable (3.7) |
| .exe | | | DOS Executable Generic (3.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:12:17 18:55:24+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 1528832 |
| InitializedDataSize: | 659456 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x176d94 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.0.0.5 |
| ProductVersionNumber: | 7.0.0.5 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Le Ngoc Khoa |
| FileDescription: | Laragon - The Dev Environment for Entrepreneurs |
| FileVersion: | 7.0.0.5 |
| InternalName: | - |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| ProductName: | Laragon |
| ProductVersion: | 7 |
| Comments: | - |
Total processes
41
Monitored processes
5
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | cmd.exe /C C:\Users\admin\AppData\Local\Temp\bin\laragon\utils\curl.exe -L "https://raw.githubusercontent.com/leokhoa/laragon/master/usr/packages.conf" -o C:\Users\admin\AppData\Local\Temp\tmp\packages.conf.tmp | C:\Windows\System32\cmd.exe | — | laragon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
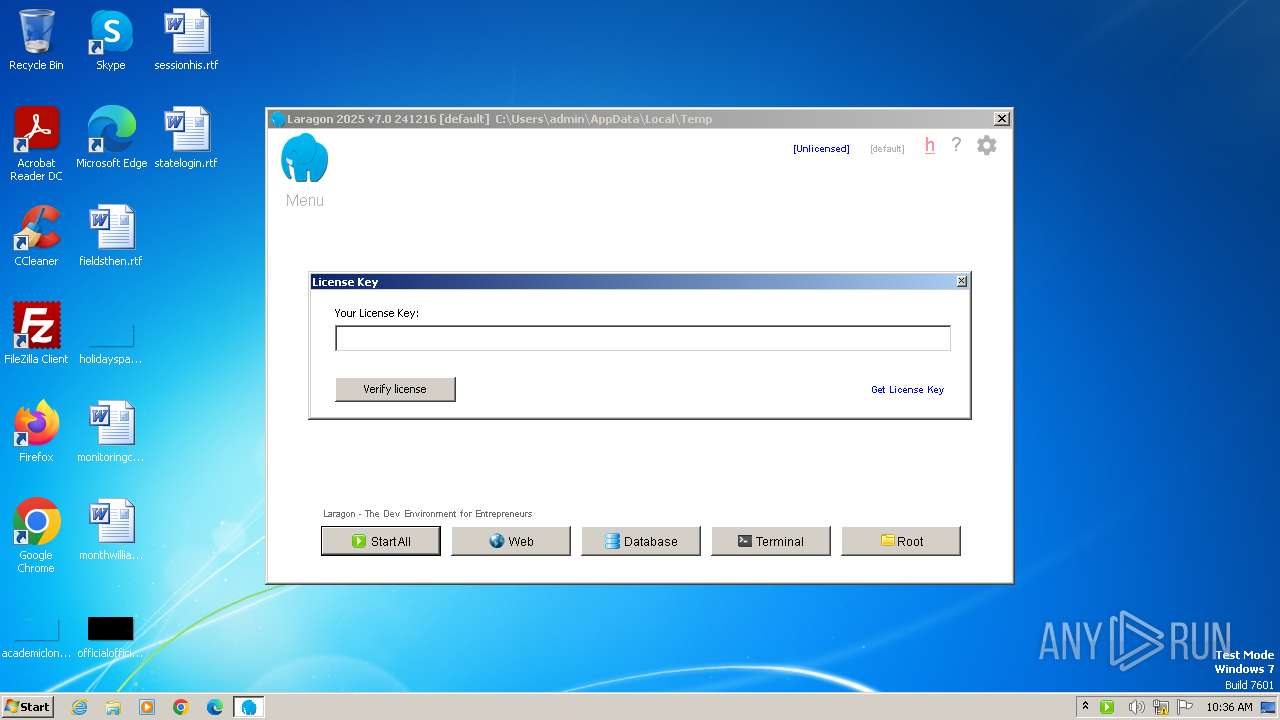
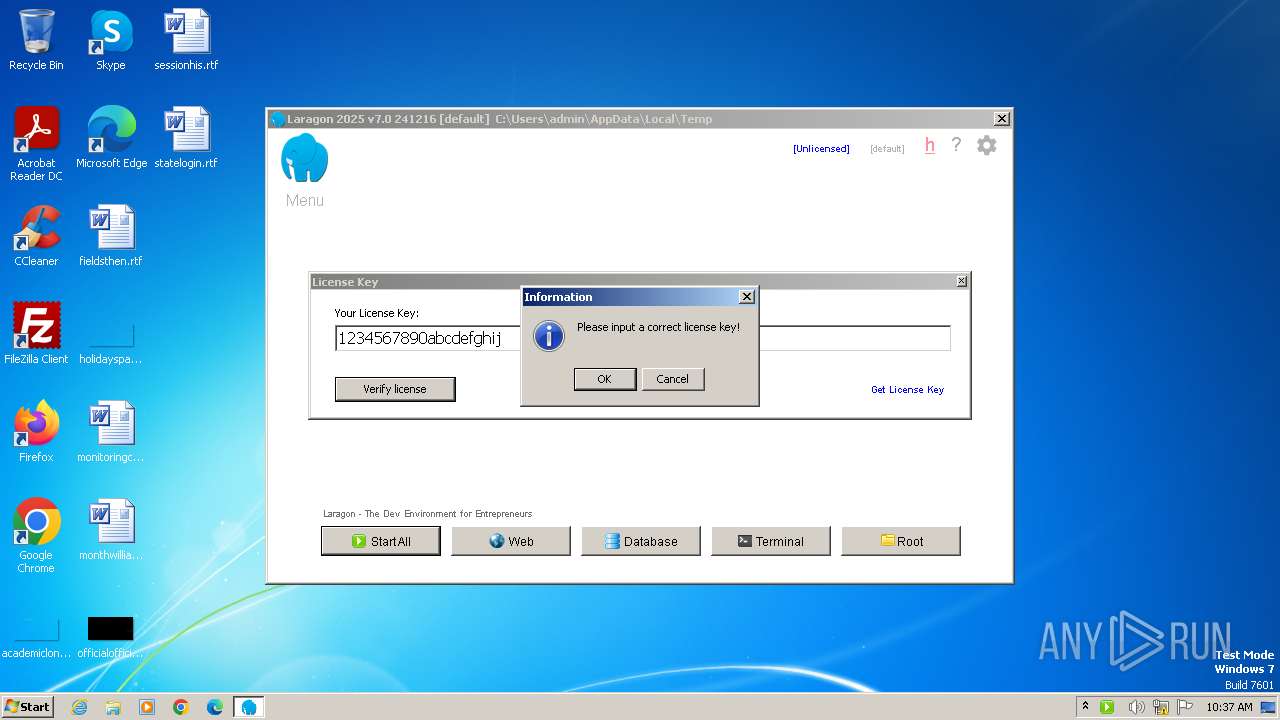
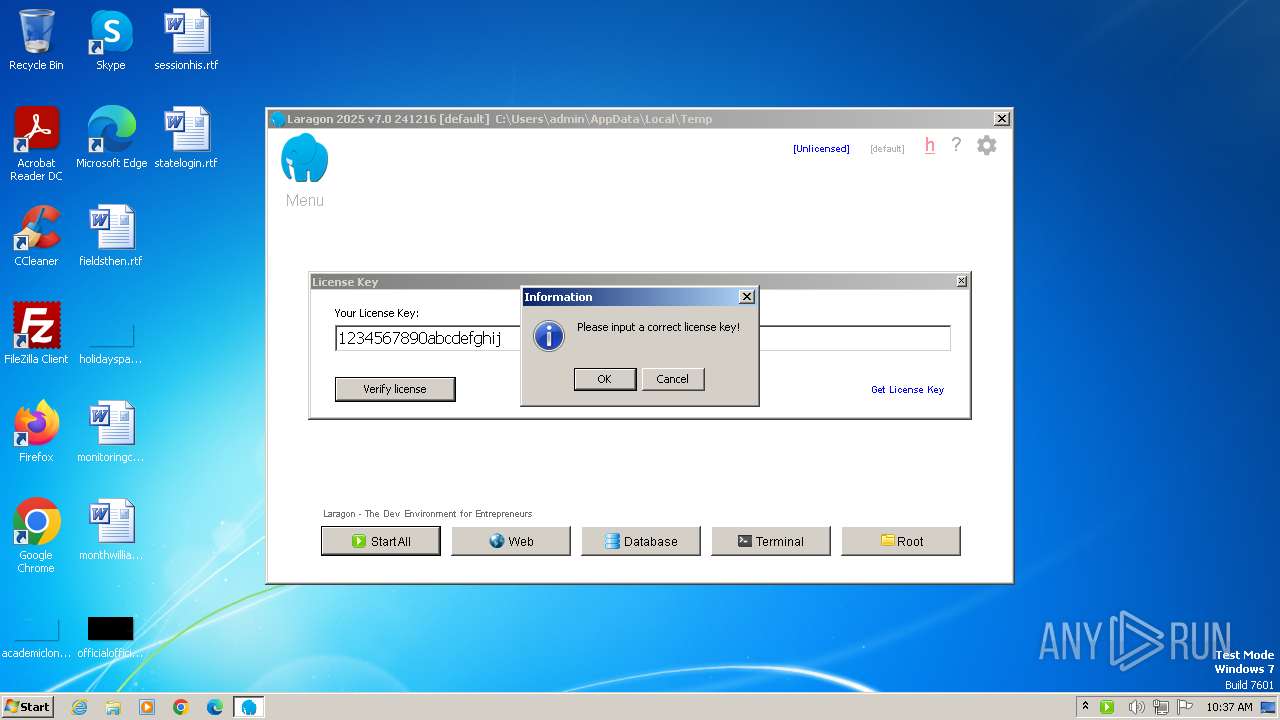
| 1744 | curl -sS -H "Authorization: Bearer UBiAJEh9Bs3Aq0reR3GMK3znxF933mmtU/taklQ3hqk=" "https://api.laragon.org/v1/licenses/activate" --data "{\"license_key\": \"1234567890abcdefghij\", \"instance_name\": \"8E830DDC-316F-45DE-AA50-3C0C7208C821\"}" | C:\Windows\System32\curl.exe | laragon.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 0 Version: 8.5.0 Modules
| |||||||||||||||
| 1932 | "C:\Users\admin\AppData\Local\Temp\laragon.exe" | C:\Users\admin\AppData\Local\Temp\laragon.exe | — | explorer.exe | |||||||||||
User: admin Company: Le Ngoc Khoa Integrity Level: MEDIUM Description: Laragon - The Dev Environment for Entrepreneurs Version: 7.0.0.5 Modules
| |||||||||||||||
| 2252 | curl -sS -H "Authorization: Bearer UBiAJEh9Bs3Aq0reR3GMK3znxF933mmtU/taklQ3hqk=" "https://api.laragon.org/v1/licenses/activate" --data "{\"license_key\": \"1234567890abcdefghij\", \"instance_name\": \"8E830DDC-316F-45DE-AA50-3C0C7208C821\"}" | C:\Windows\System32\curl.exe | laragon.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 0 Version: 8.5.0 Modules
| |||||||||||||||
| 2276 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
878
Read events
878
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1932 | laragon.exe | C:\Users\admin\AppData\Local\Temp\bin\laragon\laragon.cmd | text | |
MD5:632821DCAB4CA1A98524F758DA2146AF | SHA256:5396C2DA01ECAF3AC154A903CDE33482DB3984384D935D5ADF000FB44F9FDD61 | |||
| 1932 | laragon.exe | C:\Users\admin\AppData\Local\Temp\usr\user.cmd | text | |
MD5:BE39C8A1C134CBDD17C6E45F619AA334 | SHA256:CD3F25E2D9FCB114160C794CBEA712DBE94527C1C3E7D237AF5390920F5E3B94 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
7
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1108 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2252 | curl.exe | 172.67.140.61:443 | api.laragon.org | CLOUDFLARENET | US | whitelisted |
1744 | curl.exe | 172.67.140.61:443 | api.laragon.org | CLOUDFLARENET | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
api.laragon.org |
| whitelisted |