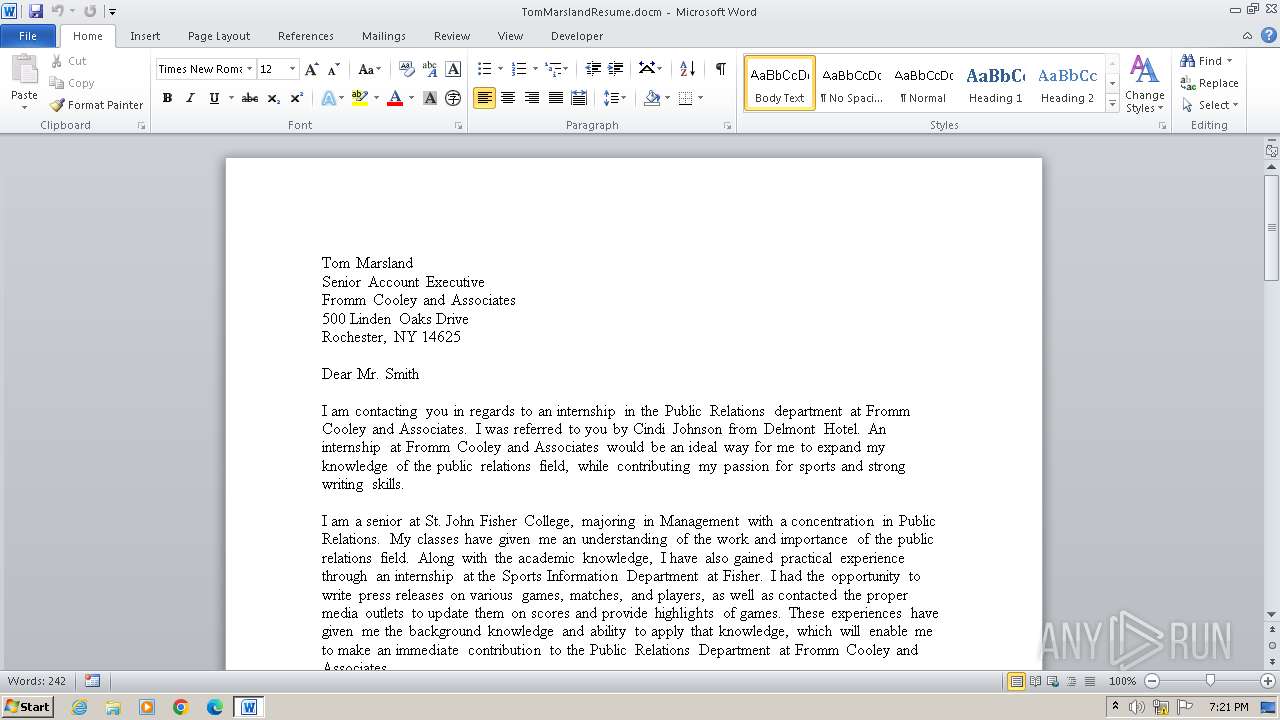
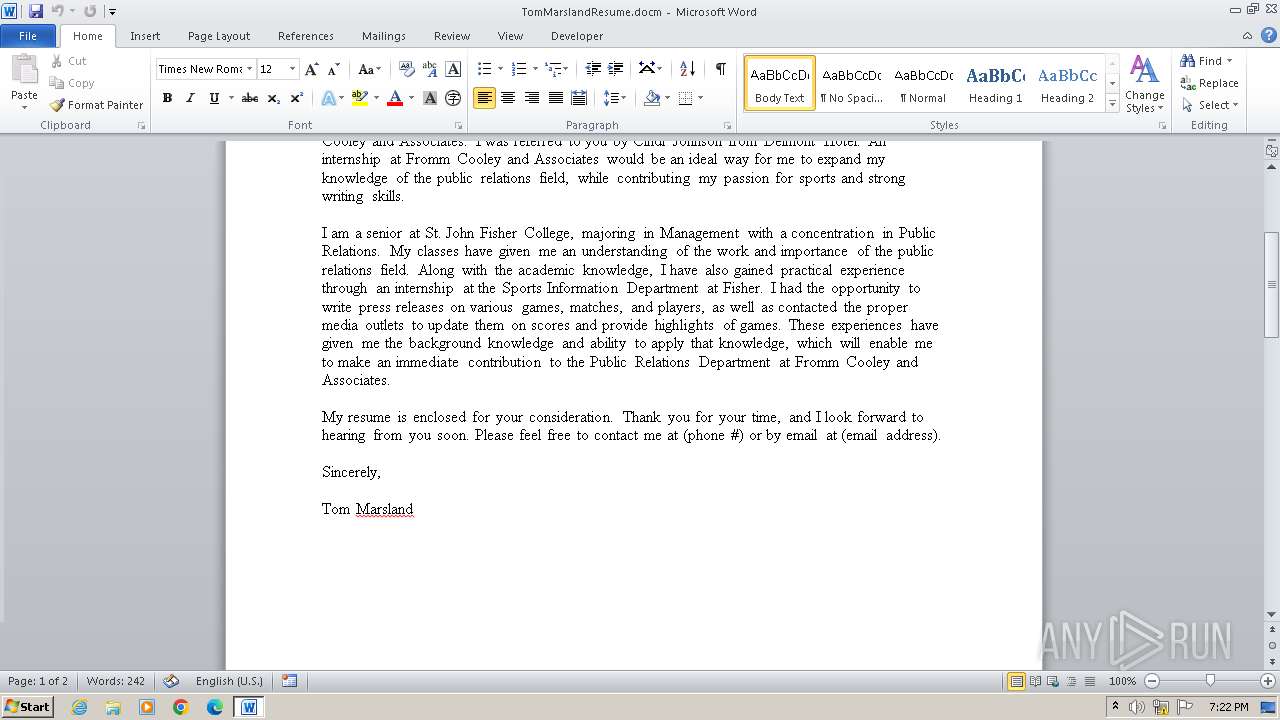
| File name: | TomMarslandResume.docm |
| Full analysis: | https://app.any.run/tasks/ef1e3b59-ad43-4aa2-892d-4394d8c55c54 |
| Verdict: | Malicious activity |
| Analysis date: | June 11, 2024, 18:20:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 9559A9EED09C11CBA30E4743CF7974CD |
| SHA1: | 52279F70194B2E4F89BDDE1F403B41194DFEC67D |
| SHA256: | C97A6B93B33D0DFC9685AAABC673756BC0329DE8D2F9F088CCE7C70B76C66489 |
| SSDEEP: | 384:UmA7zSZweORo0rhhFL/ulWsboTp0RBfk/VBCUNfde9I0ZkZY:UlWOxdhFLGlWsbm0bfW7nhIZkW |
MALICIOUS
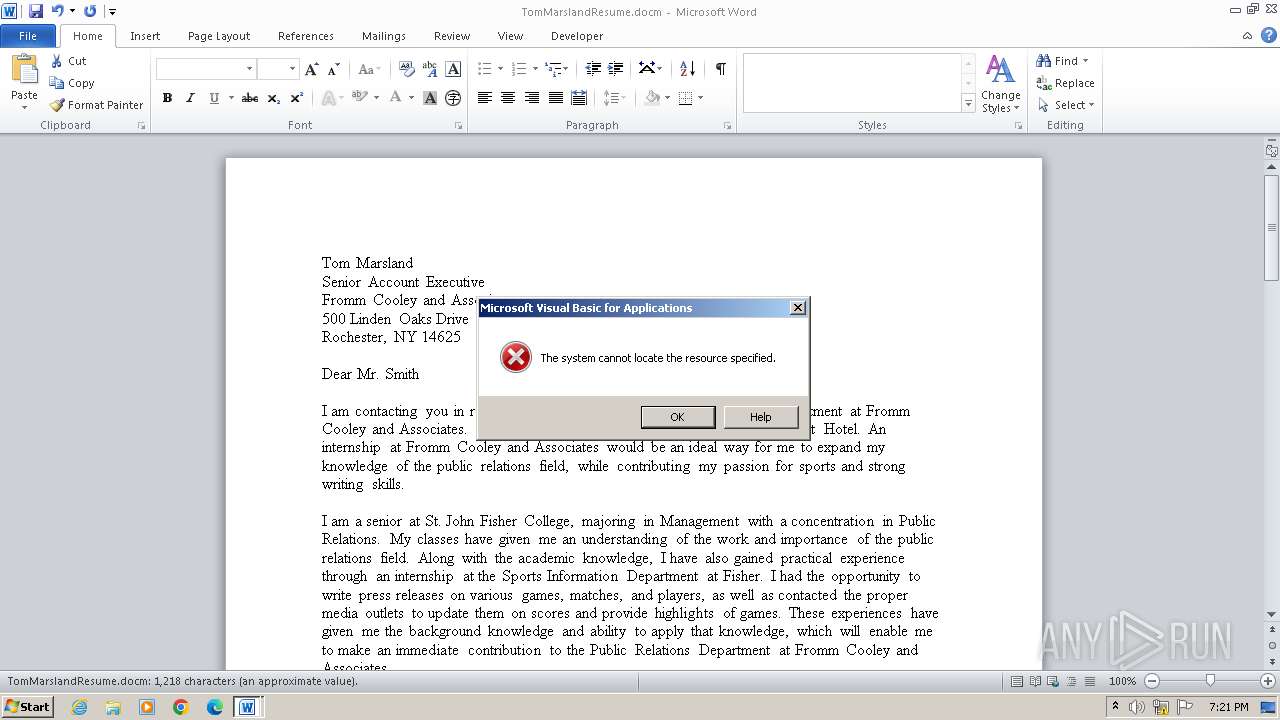
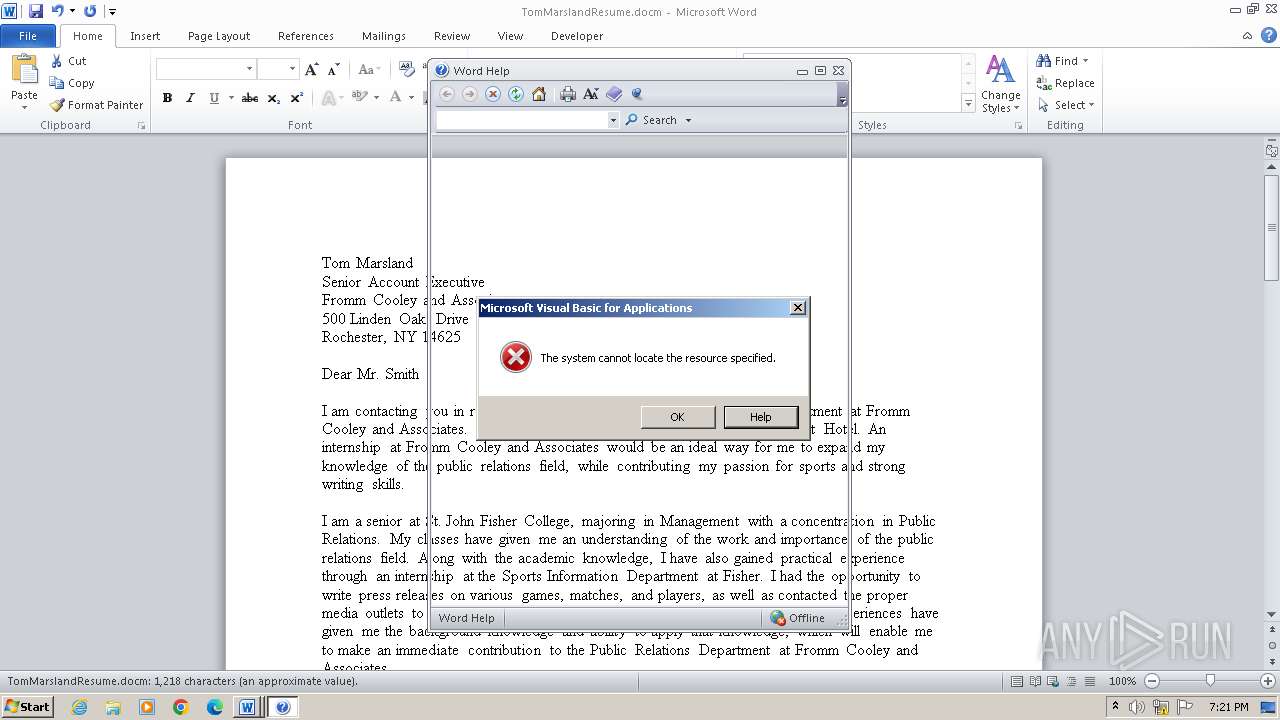
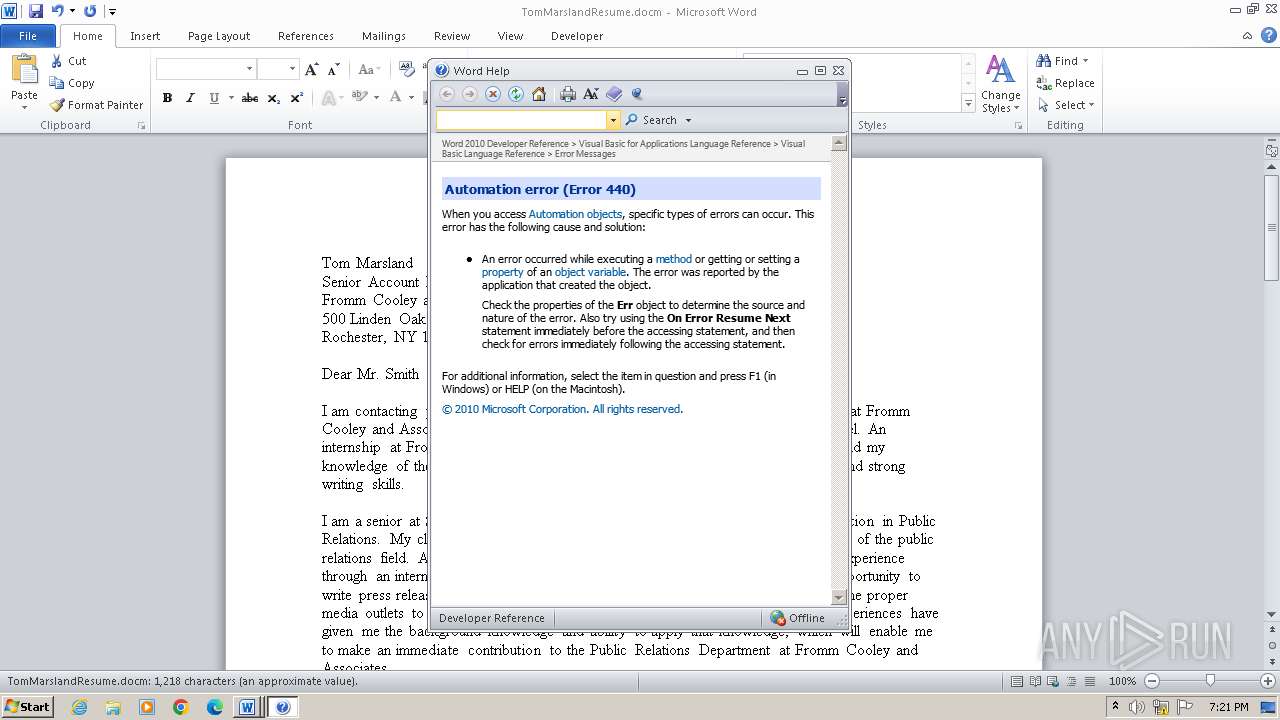
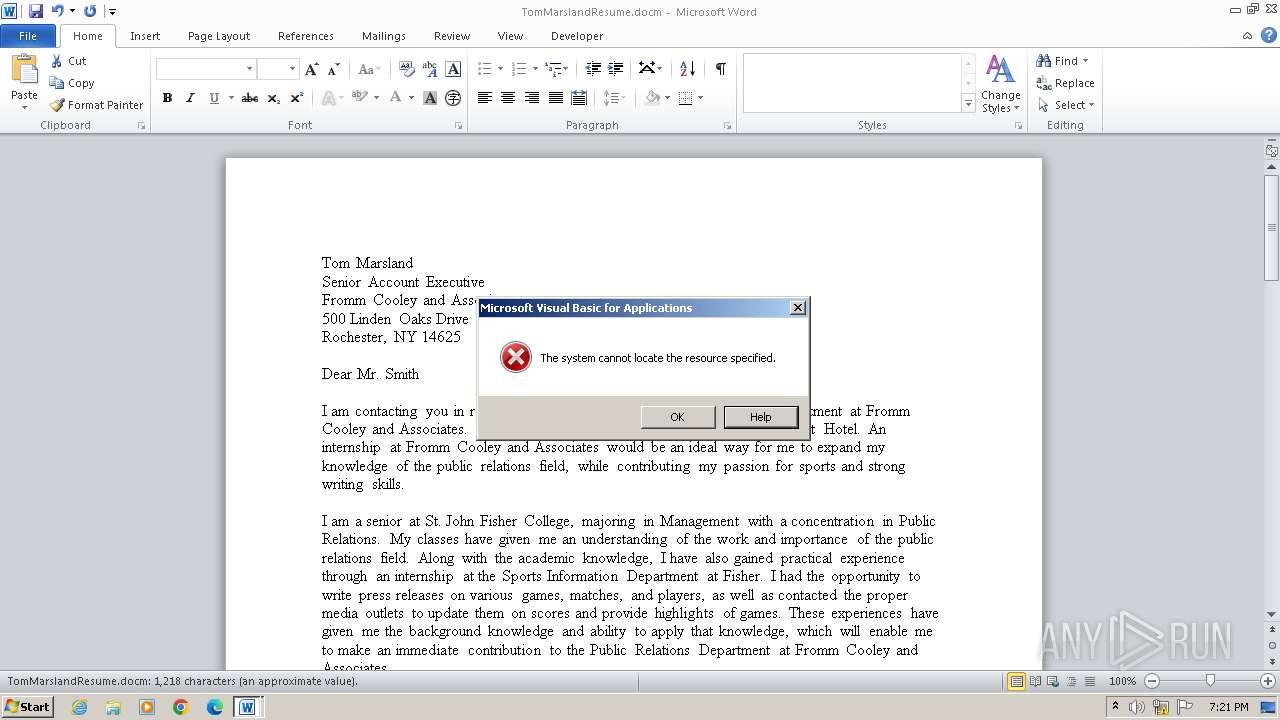
Creates internet connection object (SCRIPT)
- WINWORD.EXE (PID: 3972)
Sends HTTP request (SCRIPT)
- WINWORD.EXE (PID: 3972)
Opens an HTTP connection (SCRIPT)
- WINWORD.EXE (PID: 3972)
SUSPICIOUS
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- WINWORD.EXE (PID: 3972)
INFO
Reads Internet Explorer settings
- CLVIEW.EXE (PID: 2108)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x91fc8a0b |
| ZipCompressedSize: | 401 |
| ZipUncompressedSize: | 1586 |
| ZipFileName: | [Content_Types].xml |
XMP
| Creator: | cents |
|---|
XML
| LastModifiedBy: | Solanki, Chance Y Finance |
|---|---|
| RevisionNumber: | 12 |
| CreateDate: | 2022:07:04 00:29:00Z |
| ModifyDate: | 2023:01:16 06:22:00Z |
| Template: | Normal |
| TotalEditTime: | 3.1 hours |
| Pages: | 2 |
| Words: | 220 |
| Characters: | 1258 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 10 |
| Paragraphs: | 2 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Company: | ARGENTS |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 1476 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
35
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2108 | "C:\Program Files\Microsoft Office\Office14\CLVIEW.EXE" "WINWORD" "Microsoft Word" | C:\Program Files\Microsoft Office\Office14\CLVIEW.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Help Viewer Exit code: 0 Version: 14.0.6015.1000 Modules
| |||||||||||||||
| 3972 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n C:\Users\admin\AppData\Local\Temp\TomMarslandResume.docm | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
9 629
Read events
9 168
Write events
212
Delete events
249
Modification events
| (PID) Process: | (3972) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | *b? |
Value: 2A623F00840F0000010000000000000000000000 | |||
| (PID) Process: | (3972) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3972) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3972) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3972) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3972) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3972) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3972) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3972) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3972) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
106
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3972 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR3A7A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3972 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:D27D307C9620F0F2B78519B6F5CB7294 | SHA256:8A5E3EC0A17A150FA69946625208F77546C15E5247A4A318EE1F7ADA644FFCF5 | |||
| 3972 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\mso3F4E.tmp | image | |
MD5:ED3C1C40B68BA4F40DB15529D5443DEC | SHA256:039FE79B74E6D3D561E32D4AF570E6CA70DB6BB3718395BE2BF278B9E601279A | |||
| 2108 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMTEE89.tmp | binary | |
MD5:73E5F16AA352D7188E7266C6C20EAAF1 | SHA256:57408D0184C465A18379CAAF84030C6835B480BC644804F5670A02B985E84A0C | |||
| 2108 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMTEE8A.tmp | binary | |
MD5:4BE2AEDDA24E0539C95564B48CA9D8BA | SHA256:E4D153F74AC21D4212A83FE030EE7A407B5FDFE2D3A8145F3E826532BD796893 | |||
| 2108 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMTEE8B.tmp | binary | |
MD5:453FDB783008B8E22E87FF071A71860C | SHA256:58B421A26F4AF76DA1282FD12DE11F60C37E3EDD2067C4308BE874DE0D750F12 | |||
| 3972 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$mMarslandResume.docm | pgc | |
MD5:7394BAE1D2A0832A722F213319C7B309 | SHA256:A6BEE857756442152607A47F23176234F13CF25F78C10DC57C286C2D64655AA8 | |||
| 2108 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMTEE8C.tmp | binary | |
MD5:7E8B24EECB300B45B19F534EFF40AD54 | SHA256:DAA96DDB007D4387E35263890F76F3CE91EE276D6AE85B0BBF1D9BCB97FCF85B | |||
| 2108 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMTEEB0.tmp | binary | |
MD5:244F5BF7C311B71BACA300BFB020D6EA | SHA256:C48FF4E04C4F6FBA75600635FD7C57076FCF278F35C784FE12FDA0CF8F8B6AF8 | |||
| 2108 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMTEEE6.tmp | binary | |
MD5:453FDB783008B8E22E87FF071A71860C | SHA256:58B421A26F4AF76DA1282FD12DE11F60C37E3EDD2067C4308BE874DE0D750F12 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3972 | WINWORD.EXE | 9.53.99.47:80 | — | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |