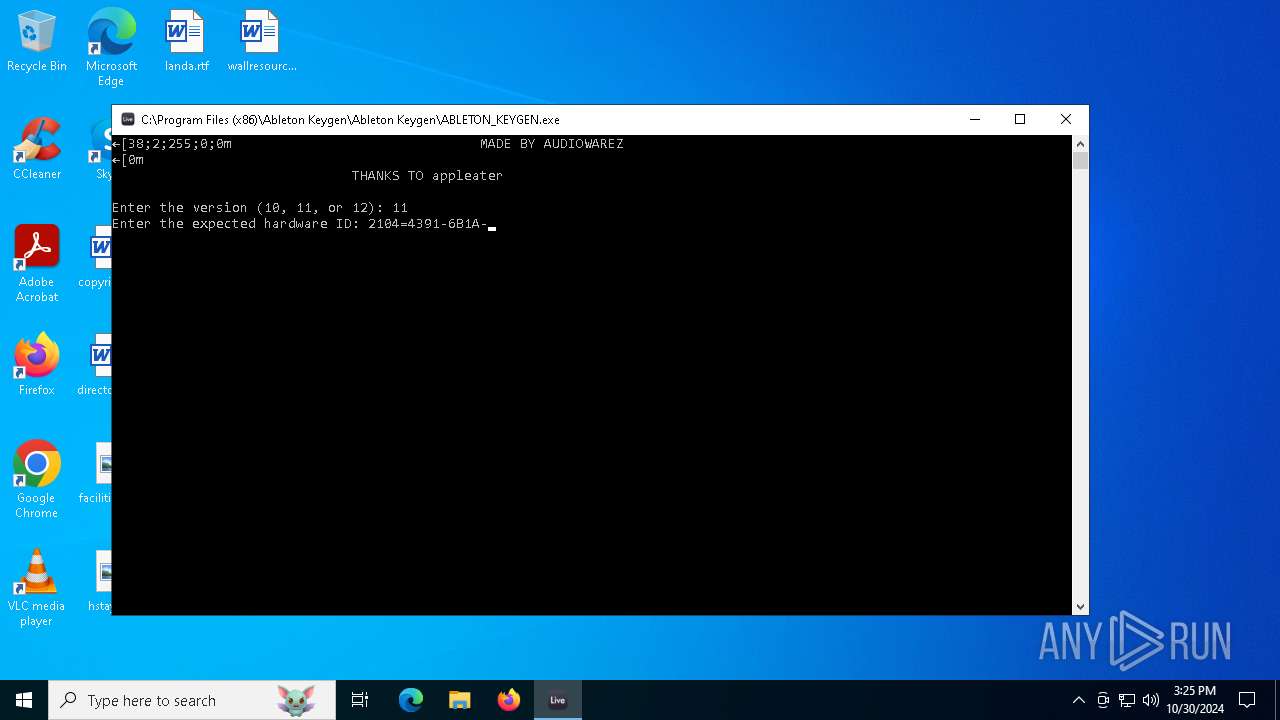
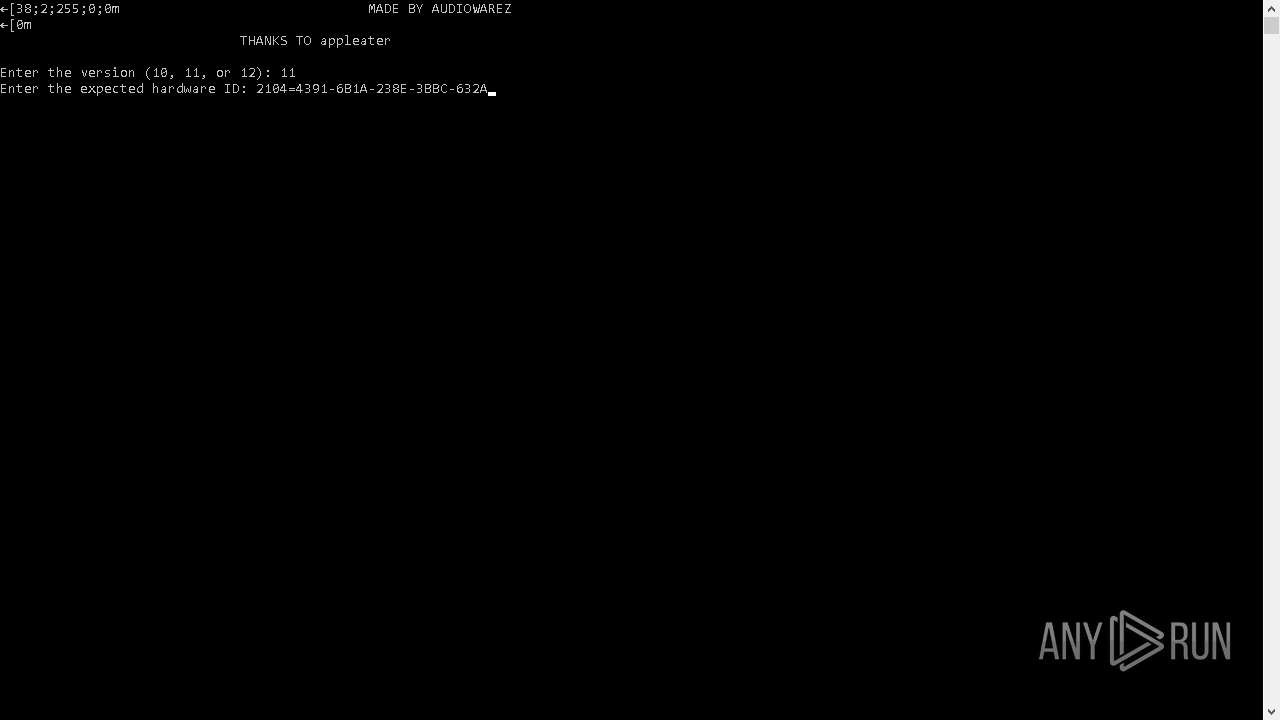
| File name: | ABLETON_KEYGEN.exe |
| Full analysis: | https://app.any.run/tasks/d220e896-b86d-4c0e-bc24-e02d41ffc6dc |
| Verdict: | Malicious activity |
| Analysis date: | October 30, 2024, 15:22:49 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 4E712BA13B32ECBA50B7A2F0044DAFDC |
| SHA1: | 48643261204D95F16376D449966151EAF7FD4334 |
| SHA256: | C92EEFAD26C98741A630CF1F615596E218ED85503AA3552341EF13AF69024BD0 |
| SSDEEP: | 98304:L+fgP3xqRyA5XxvvPjjhFl/Kg4x5YbdkwDgRy+SalI6Ft/jG/ZgsX97WfIq0MVYj:enmeKRXQB+uDg2Iko5SefvEW1Qr3L |
MALICIOUS
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 4680)
Adds extension to the Windows Defender exclusion list
- cmd.exe (PID: 4680)
SUSPICIOUS
Process drops legitimate windows executable
- ABLETON_KEYGEN.exe (PID: 5160)
- ABLETON_KEYGEN.exe (PID: 1768)
Creates or modifies Windows services
- ABLETON_KEYGEN.exe (PID: 5160)
Drops a system driver (possible attempt to evade defenses)
- ABLETON_KEYGEN.exe (PID: 5160)
Executing commands from a ".bat" file
- ABLETON_KEYGEN.exe (PID: 5160)
Creates a software uninstall entry
- ABLETON_KEYGEN.exe (PID: 5160)
Executable content was dropped or overwritten
- ABLETON_KEYGEN.exe (PID: 5160)
- ABLETON_KEYGEN.exe (PID: 1768)
Reads security settings of Internet Explorer
- ABLETON_KEYGEN.exe (PID: 5160)
Process drops python dynamic module
- ABLETON_KEYGEN.exe (PID: 1768)
Application launched itself
- ABLETON_KEYGEN.exe (PID: 1768)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 4680)
Starts CMD.EXE for commands execution
- ABLETON_KEYGEN.exe (PID: 5160)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4680)
Script adds exclusion extension to Windows Defender
- cmd.exe (PID: 4680)
Loads Python modules
- ABLETON_KEYGEN.exe (PID: 5792)
The process drops C-runtime libraries
- ABLETON_KEYGEN.exe (PID: 1768)
INFO
Create files in a temporary directory
- ABLETON_KEYGEN.exe (PID: 5160)
- ABLETON_KEYGEN.exe (PID: 1768)
Checks supported languages
- ABLETON_KEYGEN.exe (PID: 5160)
- ABLETON_KEYGEN.exe (PID: 1768)
- ABLETON_KEYGEN.exe (PID: 5792)
Reads the computer name
- ABLETON_KEYGEN.exe (PID: 5160)
- ABLETON_KEYGEN.exe (PID: 1768)
Creates files in the program directory
- ABLETON_KEYGEN.exe (PID: 5160)
The process uses the downloaded file
- ABLETON_KEYGEN.exe (PID: 5160)
- powershell.exe (PID: 2272)
Process checks computer location settings
- ABLETON_KEYGEN.exe (PID: 5160)
PyInstaller has been detected (YARA)
- ABLETON_KEYGEN.exe (PID: 5792)
- ABLETON_KEYGEN.exe (PID: 1768)
Application based on Rust
- ABLETON_KEYGEN.exe (PID: 5792)
Reads the machine GUID from the registry
- ABLETON_KEYGEN.exe (PID: 5792)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (49.2) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (16.2) |
| .scr | | | Windows screen saver (14.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.5) |
| .exe | | | Win32 Executable (generic) (5.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 148992 |
| InitializedDataSize: | 27648 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x25468 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | - |
| CompanyName: | Ableton Keygen |
| FileDescription: | Ableton Keygen 1.0 Installation |
| FileVersion: | 1.0 |
| LegalCopyright: | Ableton Keygen |
Total processes
133
Monitored processes
13
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1344 | "C:\Users\admin\AppData\Local\Temp\ABLETON_KEYGEN.exe" | C:\Users\admin\AppData\Local\Temp\ABLETON_KEYGEN.exe | — | explorer.exe | |||||||||||
User: admin Company: Ableton Keygen Integrity Level: MEDIUM Description: Ableton Keygen 1.0 Installation Exit code: 3221226540 Version: 1.0 Modules
| |||||||||||||||
| 1768 | "C:\Program Files (x86)\Ableton Keygen\Ableton Keygen\ABLETON_KEYGEN.exe" | C:\Program Files (x86)\Ableton Keygen\Ableton Keygen\ABLETON_KEYGEN.exe | ABLETON_KEYGEN.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2272 | powershell.exe Add-MpPreference -ExclusionPath C:\Windows\WinS | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4556 | powershell.exe Add-MpPreference -ExclusionExtension ".sys" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4680 | C:\WINDOWS\system32\cmd.exe /c ""C:\Windows\WinS\wd.bat" " | C:\Windows\SysWOW64\cmd.exe | — | ABLETON_KEYGEN.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5160 | "C:\Users\admin\AppData\Local\Temp\ABLETON_KEYGEN.exe" | C:\Users\admin\AppData\Local\Temp\ABLETON_KEYGEN.exe | explorer.exe | ||||||||||||
User: admin Company: Ableton Keygen Integrity Level: HIGH Description: Ableton Keygen 1.0 Installation Exit code: 0 Version: 1.0 Modules
| |||||||||||||||
| 5792 | "C:\Program Files (x86)\Ableton Keygen\Ableton Keygen\ABLETON_KEYGEN.exe" | C:\Program Files (x86)\Ableton Keygen\Ableton Keygen\ABLETON_KEYGEN.exe | ABLETON_KEYGEN.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6348 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6412 | powershell.exe Add-MpPreference -ExclusionExtension ".exe" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7044 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ABLETON_KEYGEN.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
31 576
Read events
31 514
Write events
62
Delete events
0
Modification events
| (PID) Process: | (5160) ABLETON_KEYGEN.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | Type |
Value: 16 | |||
| (PID) Process: | (5160) ABLETON_KEYGEN.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | Start |
Value: 2 | |||
| (PID) Process: | (5160) ABLETON_KEYGEN.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | ErrorControl |
Value: 1 | |||
| (PID) Process: | (5160) ABLETON_KEYGEN.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | ImagePath |
Value: C:\Windows\WinS\wmpnetwk.exe | |||
| (PID) Process: | (5160) ABLETON_KEYGEN.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | Description |
Value: WMI Providers | |||
| (PID) Process: | (5160) ABLETON_KEYGEN.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | DisplayName |
Value: WMIs | |||
| (PID) Process: | (5160) ABLETON_KEYGEN.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | ObjectName |
Value: LocalSystem | |||
| (PID) Process: | (5160) ABLETON_KEYGEN.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | DelayedAutostart |
Value: 0 | |||
| (PID) Process: | (5160) ABLETON_KEYGEN.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | FailureActionsOnNonCrashFailures |
Value: 1 | |||
| (PID) Process: | (5160) ABLETON_KEYGEN.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | FailureActions |
Value: 00000000000000000000000003000000140000000100000060EA00000100000060EA00000100000060EA0000 | |||
Executable files
17
Suspicious files
4
Text files
33
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5160 | ABLETON_KEYGEN.exe | C:\Users\admin\AppData\Local\Temp\$inst\temp_0.tmp | — | |
MD5:— | SHA256:— | |||
| 1768 | ABLETON_KEYGEN.exe | C:\Users\admin\AppData\Local\Temp\_MEI17682\_bz2.pyd | executable | |
MD5:A4B636201605067B676CC43784AE5570 | SHA256:F178E29921C04FB68CC08B1E5D1181E5DF8CE1DE38A968778E27990F4A69973C | |||
| 1768 | ABLETON_KEYGEN.exe | C:\Users\admin\AppData\Local\Temp\_MEI17682\base_library.zip | compressed | |
MD5:D588EC43695A4571E2BCB17C183A767A | SHA256:1036B9A6A53021902D4563FA968F48041CB99F0E9650C3D6EBB7B1129F07CB70 | |||
| 1768 | ABLETON_KEYGEN.exe | C:\Users\admin\AppData\Local\Temp\_MEI17682\cryptography-41.0.3.dist-info\LICENSE.BSD | text | |
MD5:5AE30BA4123BC4F2FA49AA0B0DCE887B | SHA256:602C4C7482DE6479DD2E9793CDA275E5E63D773DACD1ECA689232AB7008FB4FB | |||
| 5160 | ABLETON_KEYGEN.exe | C:\Windows\WinS\wd.bat | text | |
MD5:479988FE0741BA53D6682562377FBEE6 | SHA256:490C8EF0D7AA7DAA4255FF0792E4BA8D5EDAD5E2F8AB032DA1AC77019A207146 | |||
| 1768 | ABLETON_KEYGEN.exe | C:\Users\admin\AppData\Local\Temp\_MEI17682\cryptography-41.0.3.dist-info\LICENSE | text | |
MD5:8C3617DB4FB6FAE01F1D253AB91511E4 | SHA256:3E0C7C091A948B82533BA98FD7CBB40432D6F1A9ACBF85F5922D2F99A93AE6BB | |||
| 1768 | ABLETON_KEYGEN.exe | C:\Users\admin\AppData\Local\Temp\_MEI17682\_cffi_backend.cp310-win_amd64.pyd | executable | |
MD5:6F1B90884343F717C5DC14F94EF5ACEA | SHA256:2093E7E4F5359B38F0819BDEF8314FDA332A1427F22E09AFC416E1EDD5910FE1 | |||
| 5160 | ABLETON_KEYGEN.exe | C:\Users\admin\AppData\Local\Temp\$inst\2.tmp | compressed | |
MD5:8708699D2C73BED30A0A08D80F96D6D7 | SHA256:A32E0A83001D2C5D41649063217923DAC167809CAB50EC5784078E41C9EC0F0F | |||
| 1768 | ABLETON_KEYGEN.exe | C:\Users\admin\AppData\Local\Temp\_MEI17682\cryptography-41.0.3.dist-info\METADATA | text | |
MD5:5FD999CE35D911A5B8024F8B37325743 | SHA256:B73BBFE161BE8116A983104049C67260C1DF4DC87A55906B08C2BAE258C0AA3B | |||
| 1768 | ABLETON_KEYGEN.exe | C:\Users\admin\AppData\Local\Temp\_MEI17682\VCRUNTIME140.dll | executable | |
MD5:F12681A472B9DD04A812E16096514974 | SHA256:D66C3B47091CEB3F8D3CC165A43D285AE919211A0C0FCB74491EE574D8D464F8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
42
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3764 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1500 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.23.209.176:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.32.185.131:80 | www.microsoft.com | AKAMAI-AS | BR | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3764 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |