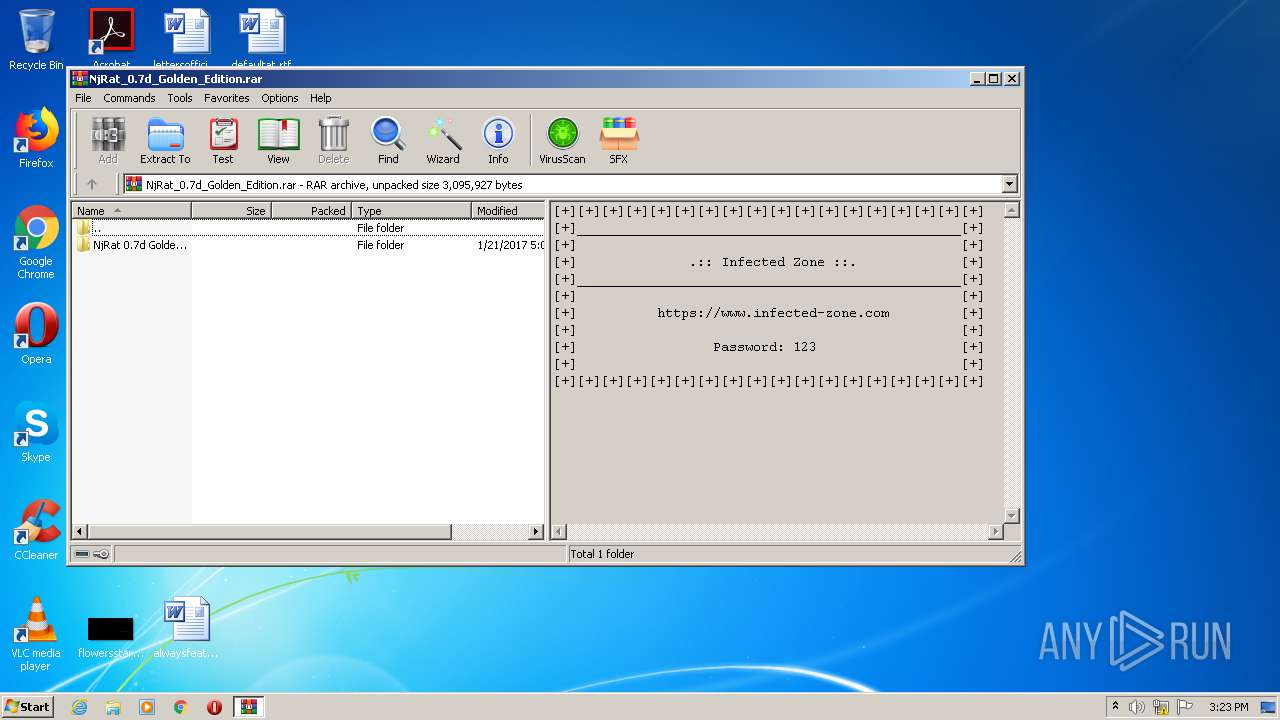
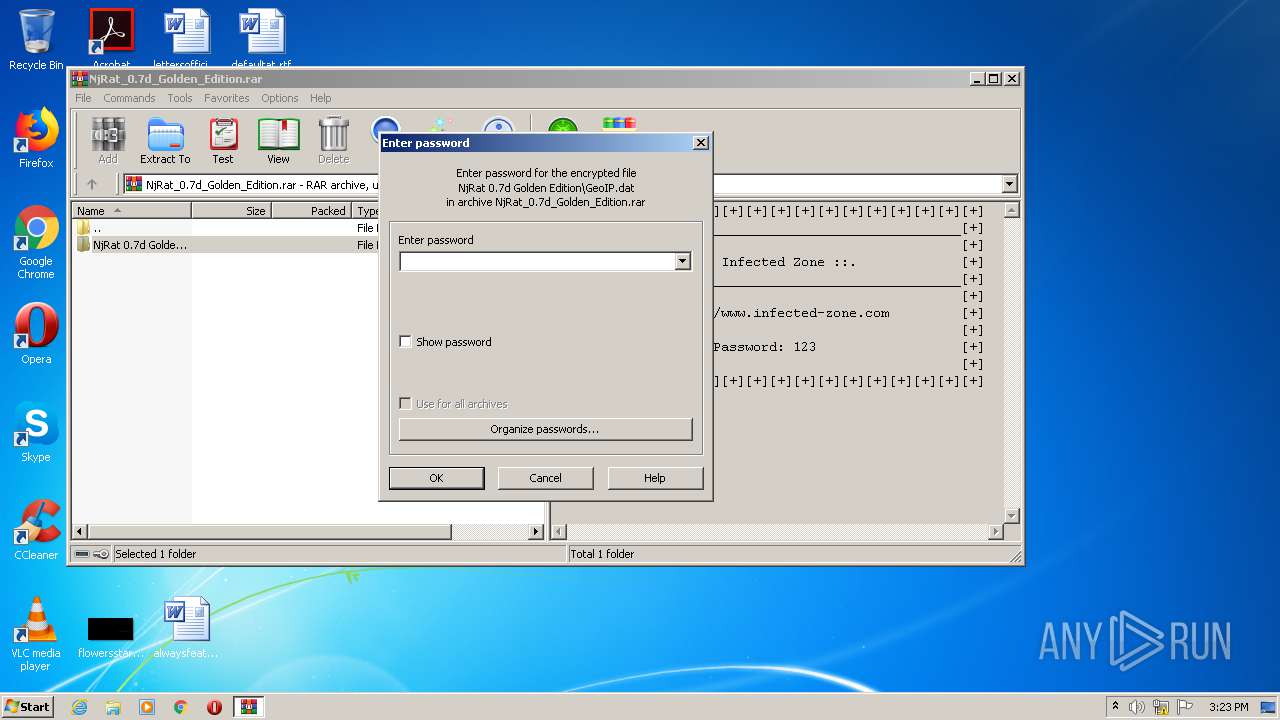
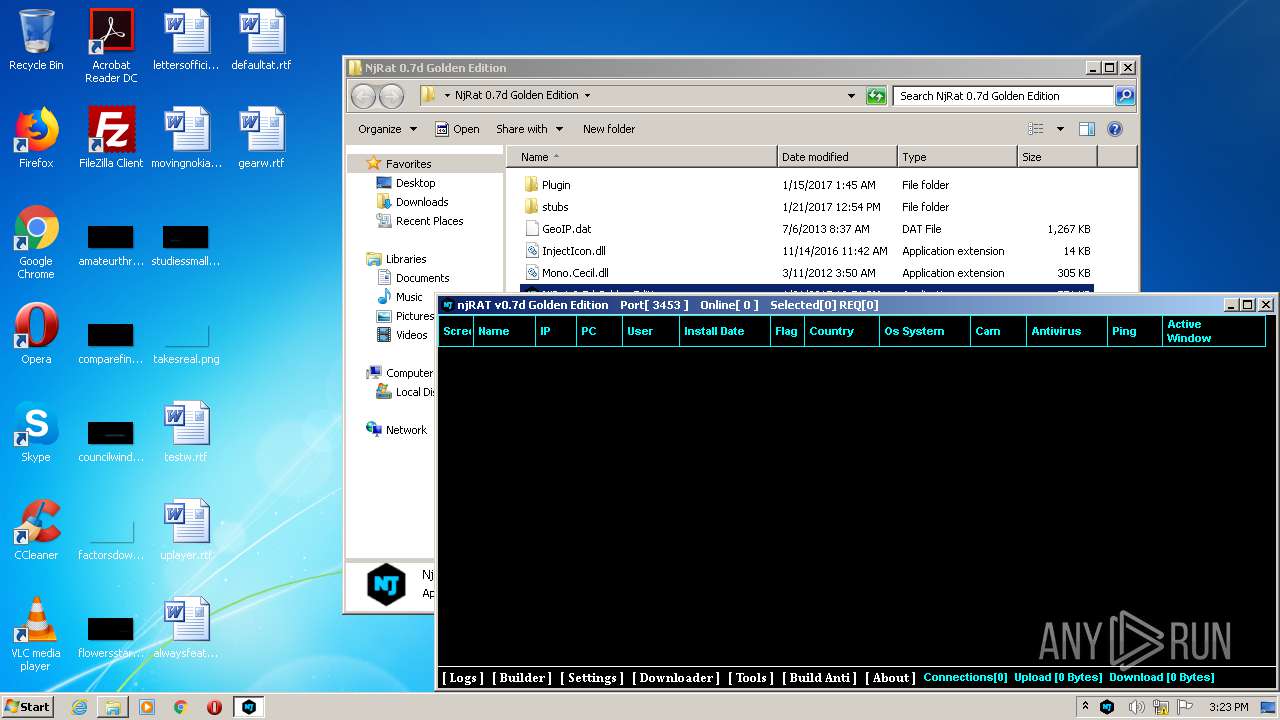
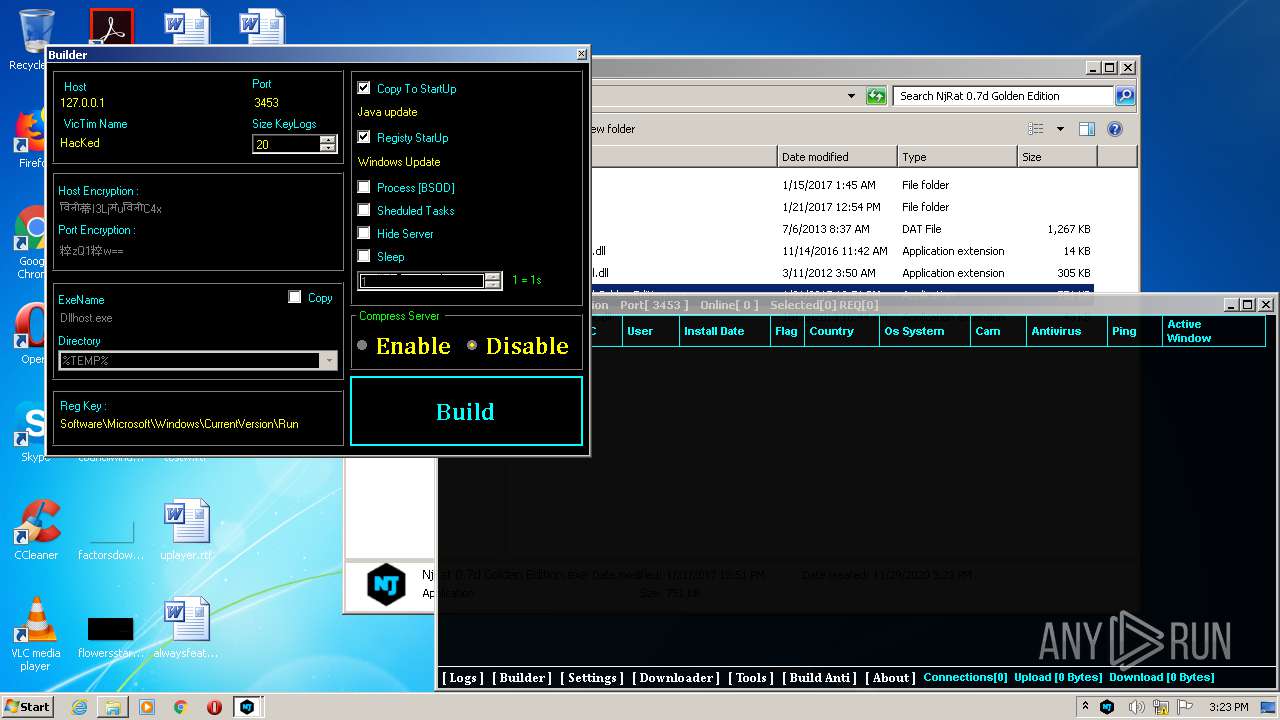
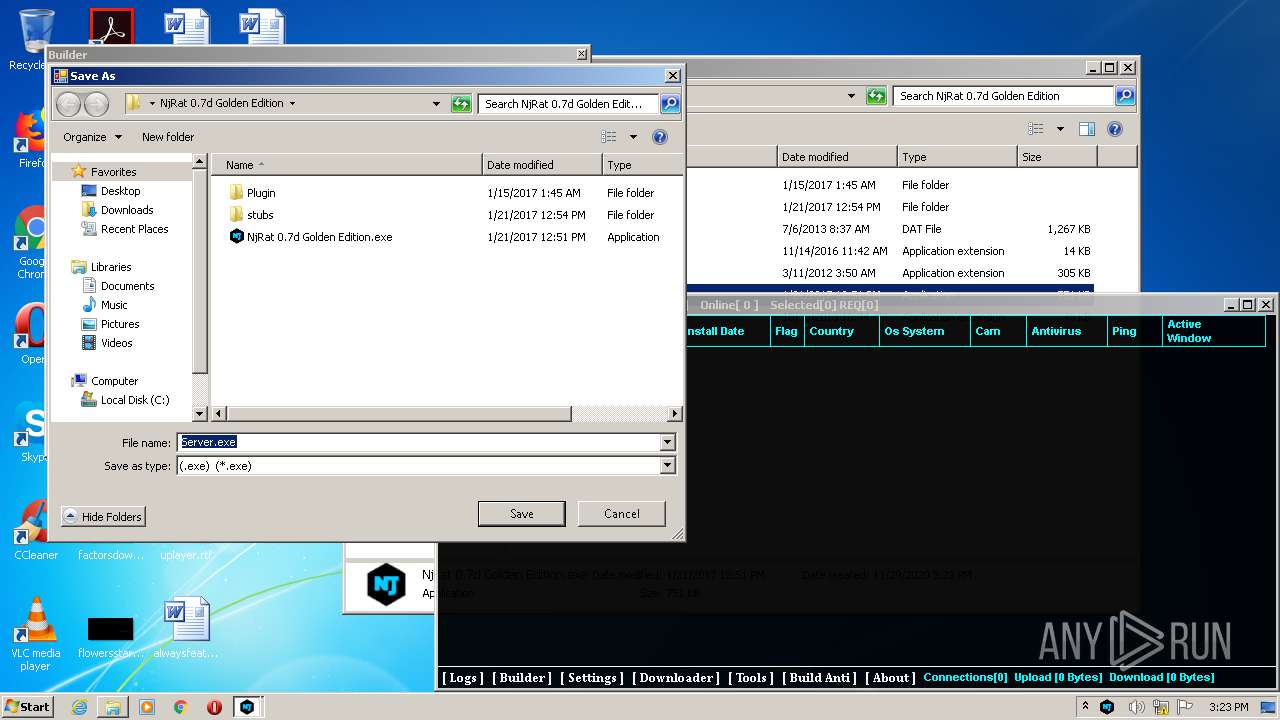
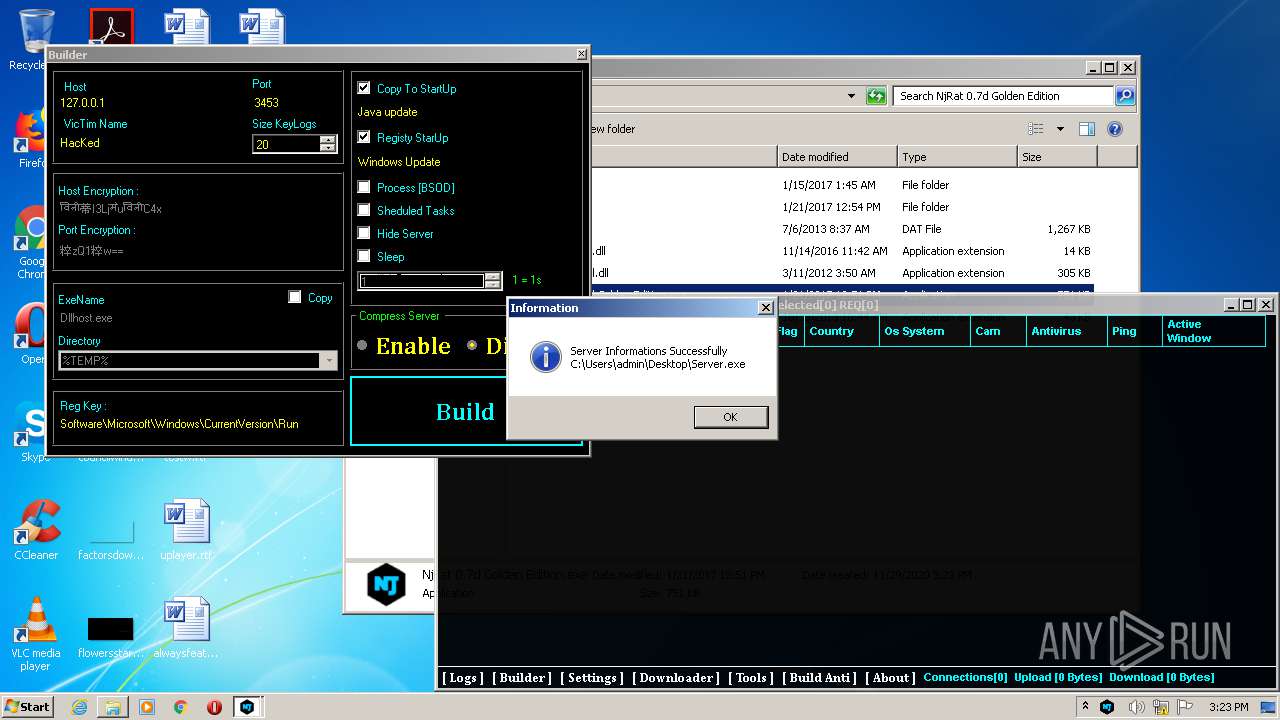
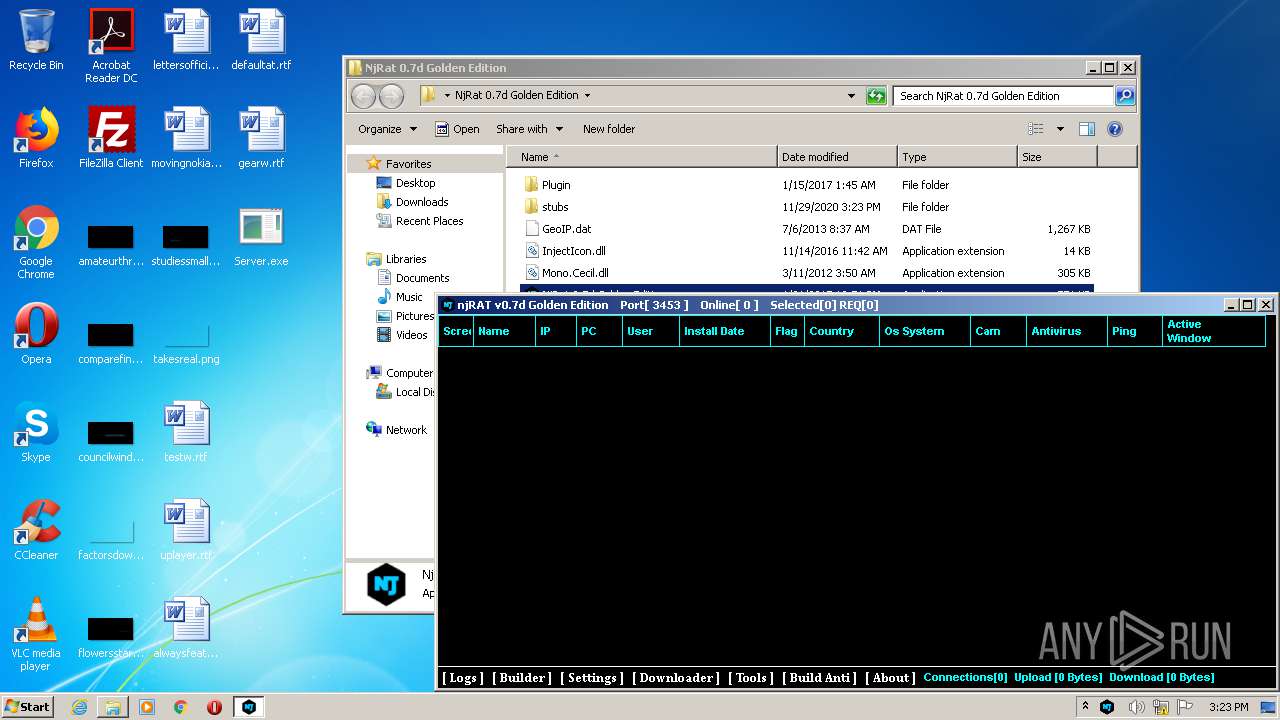
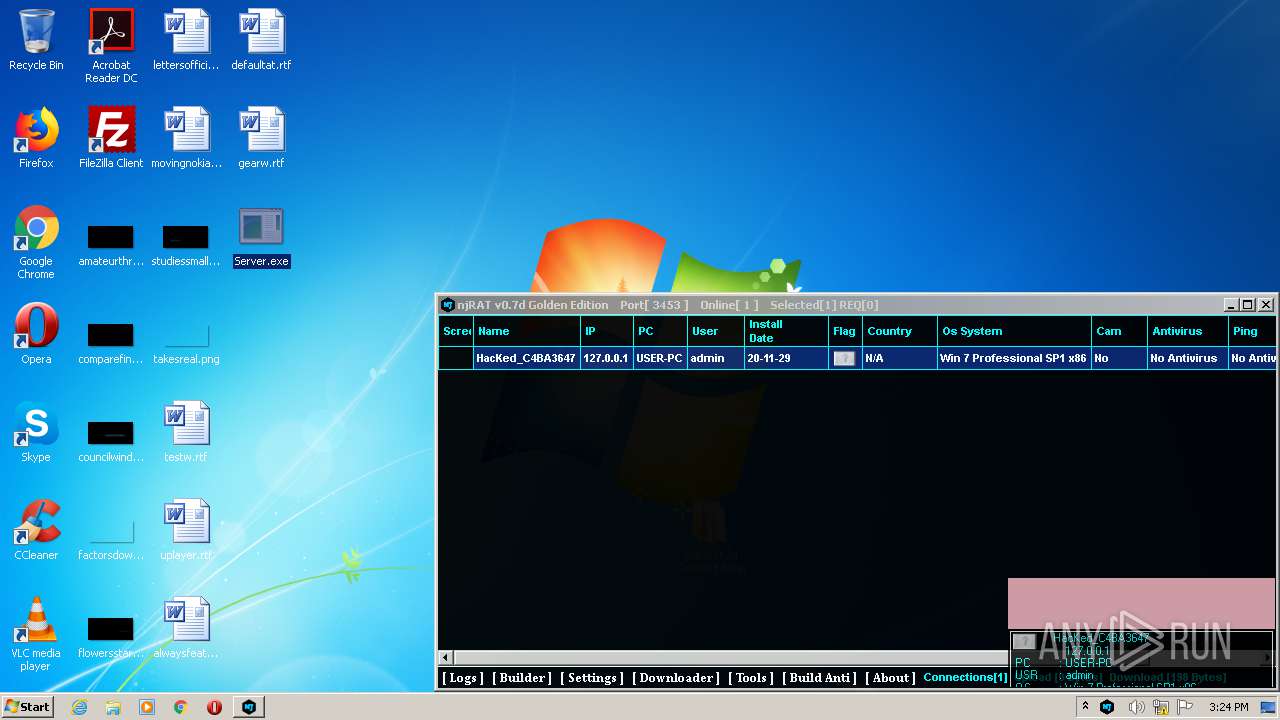
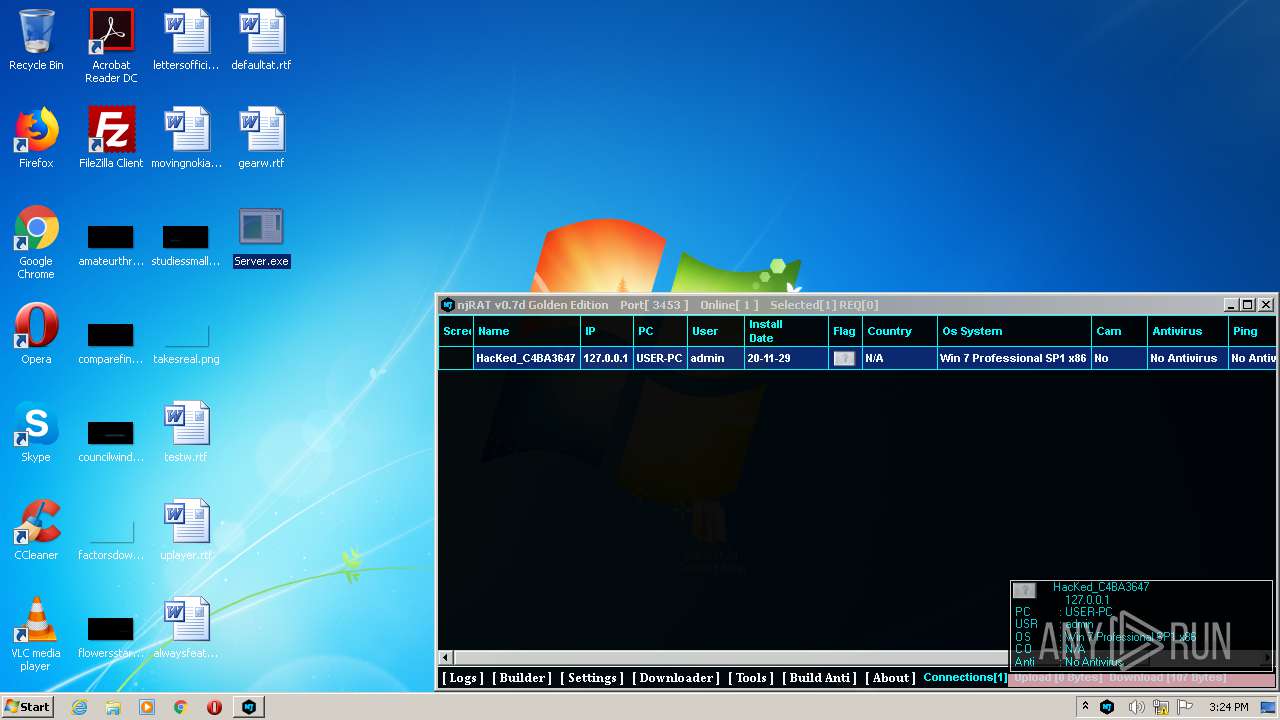
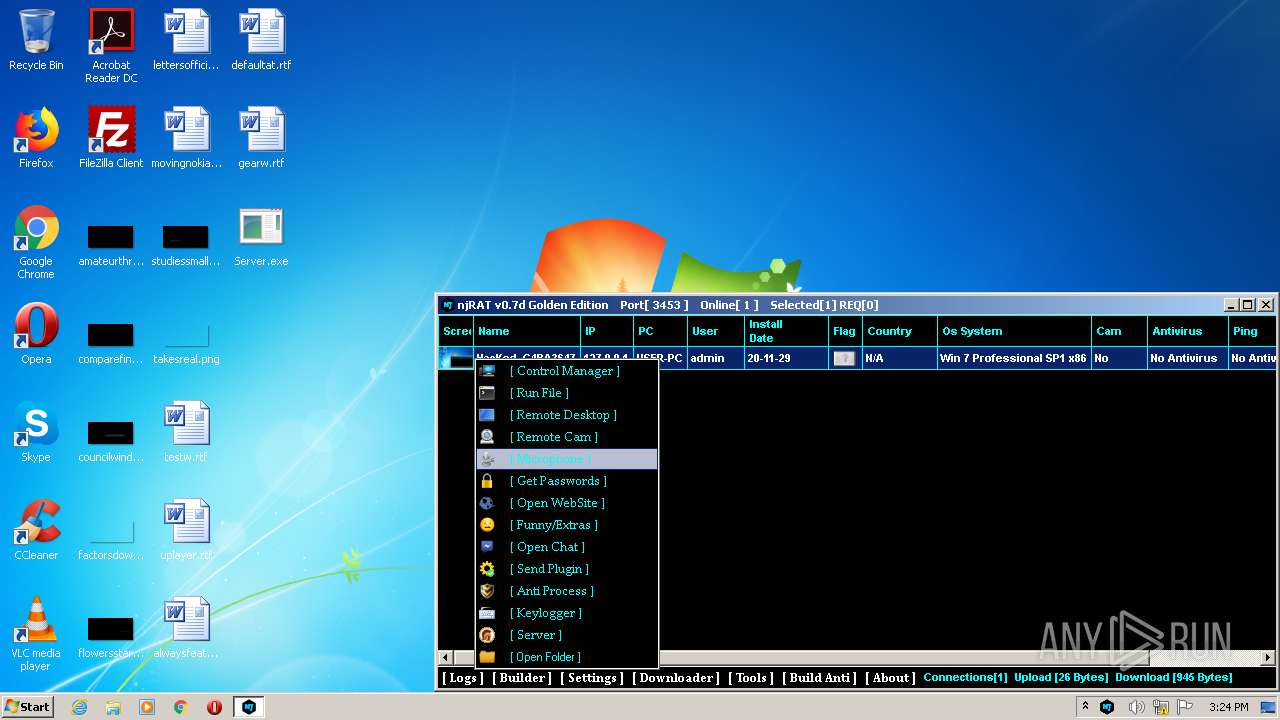
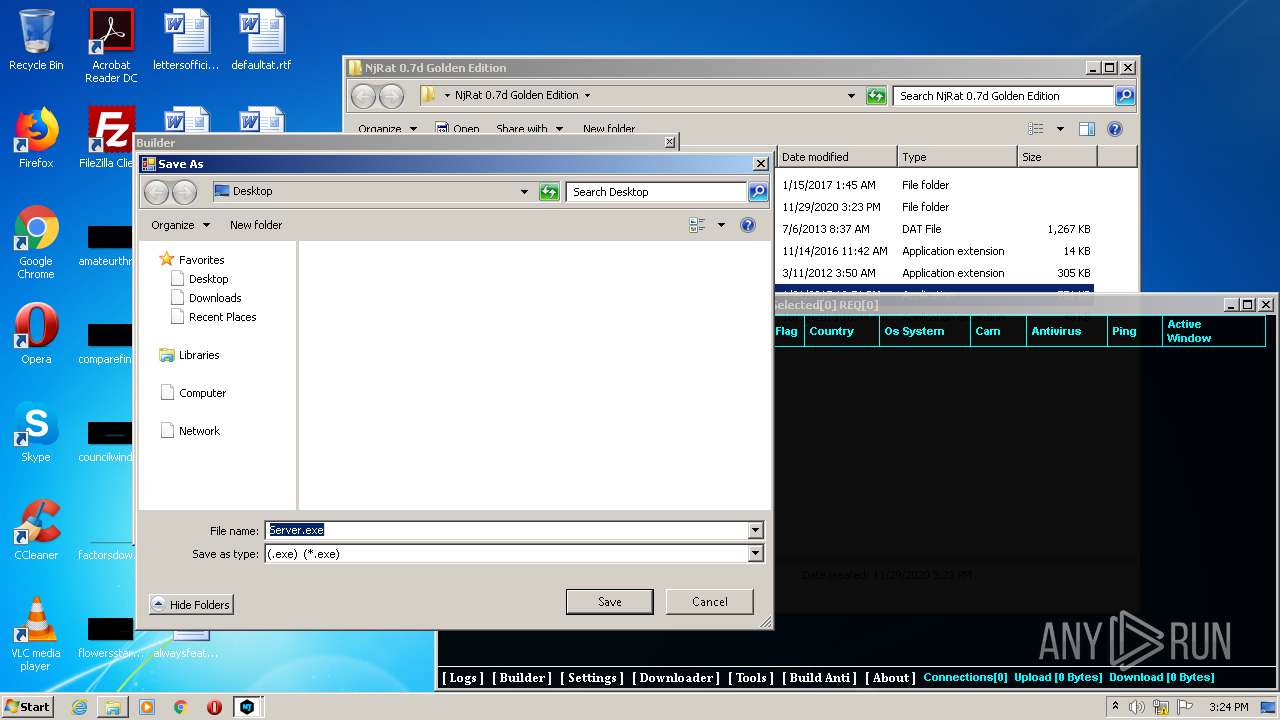
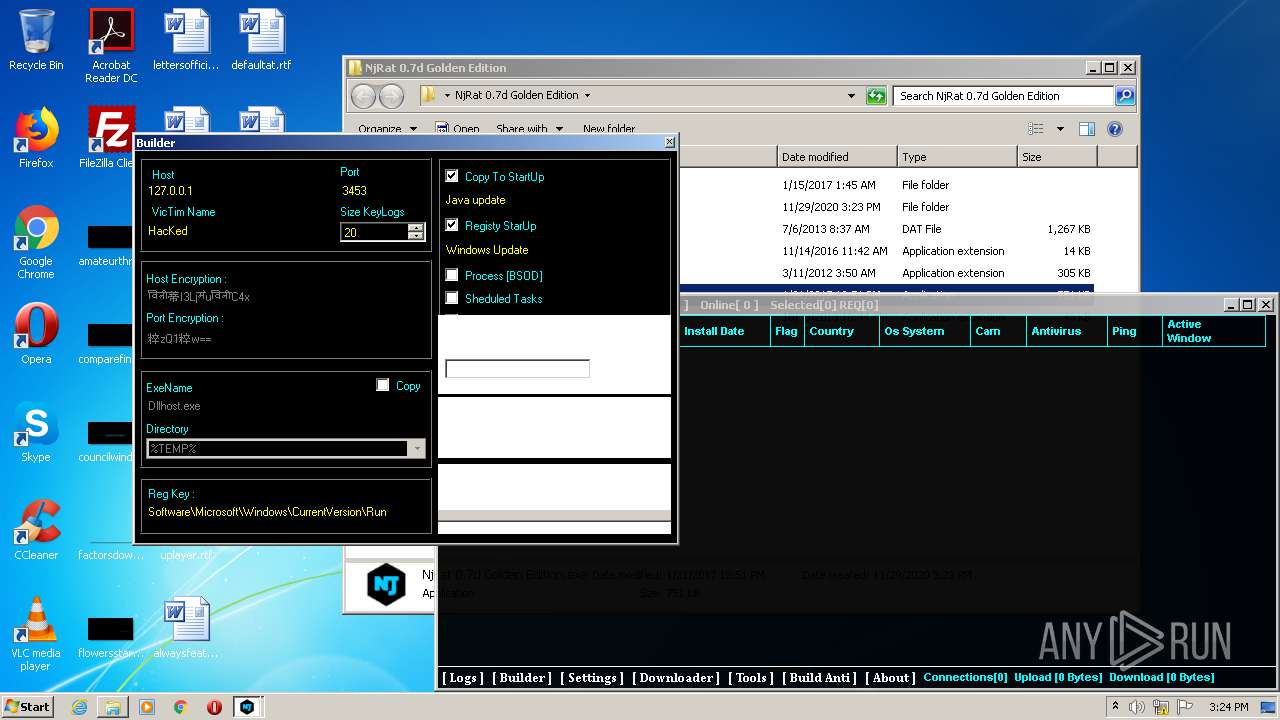
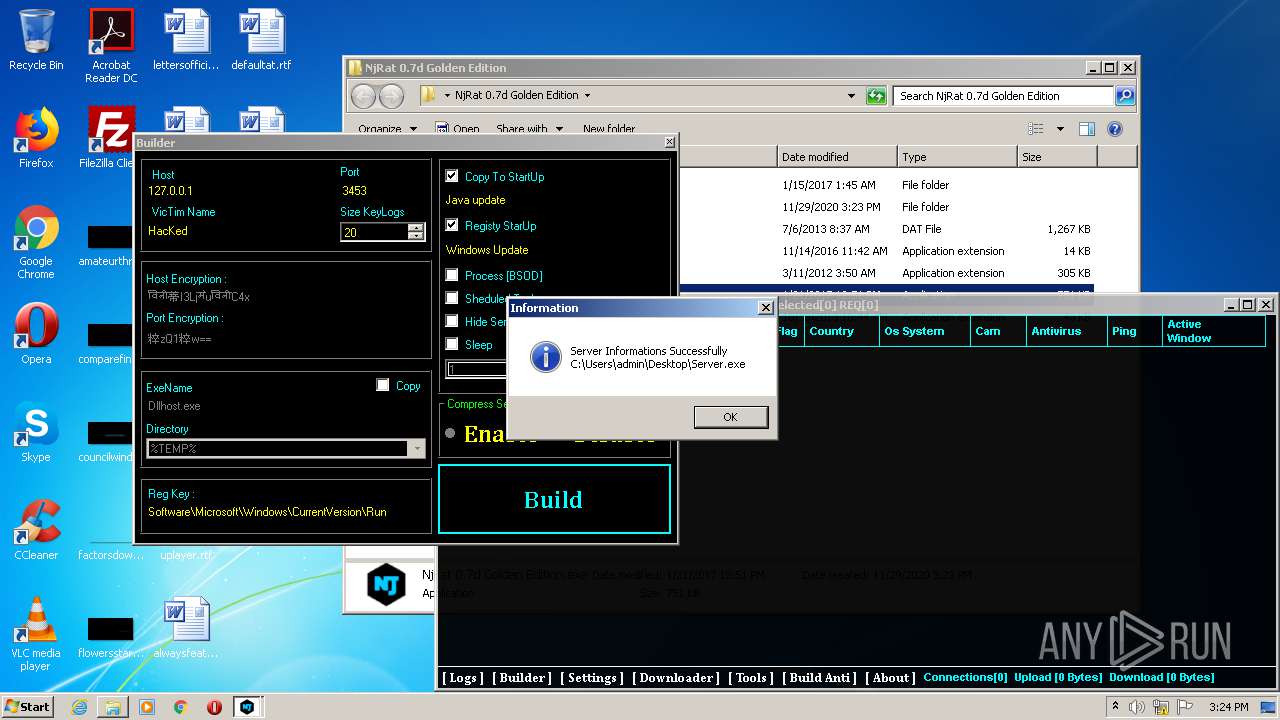
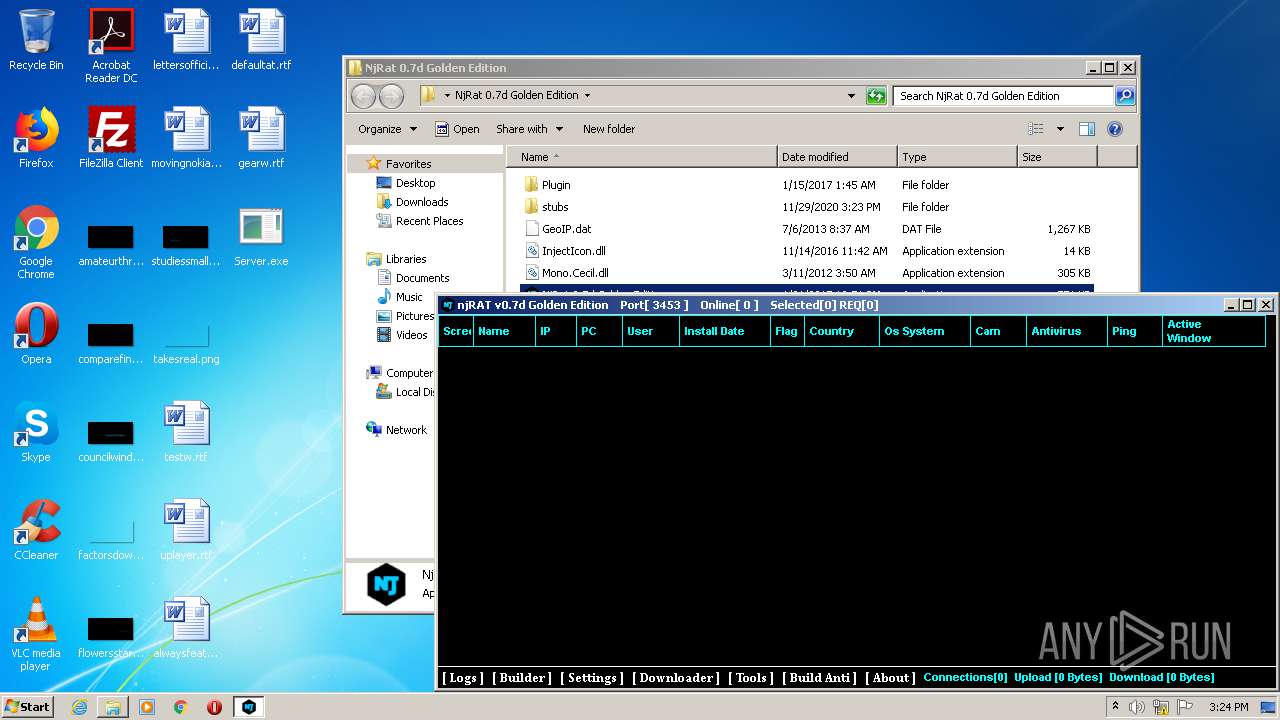
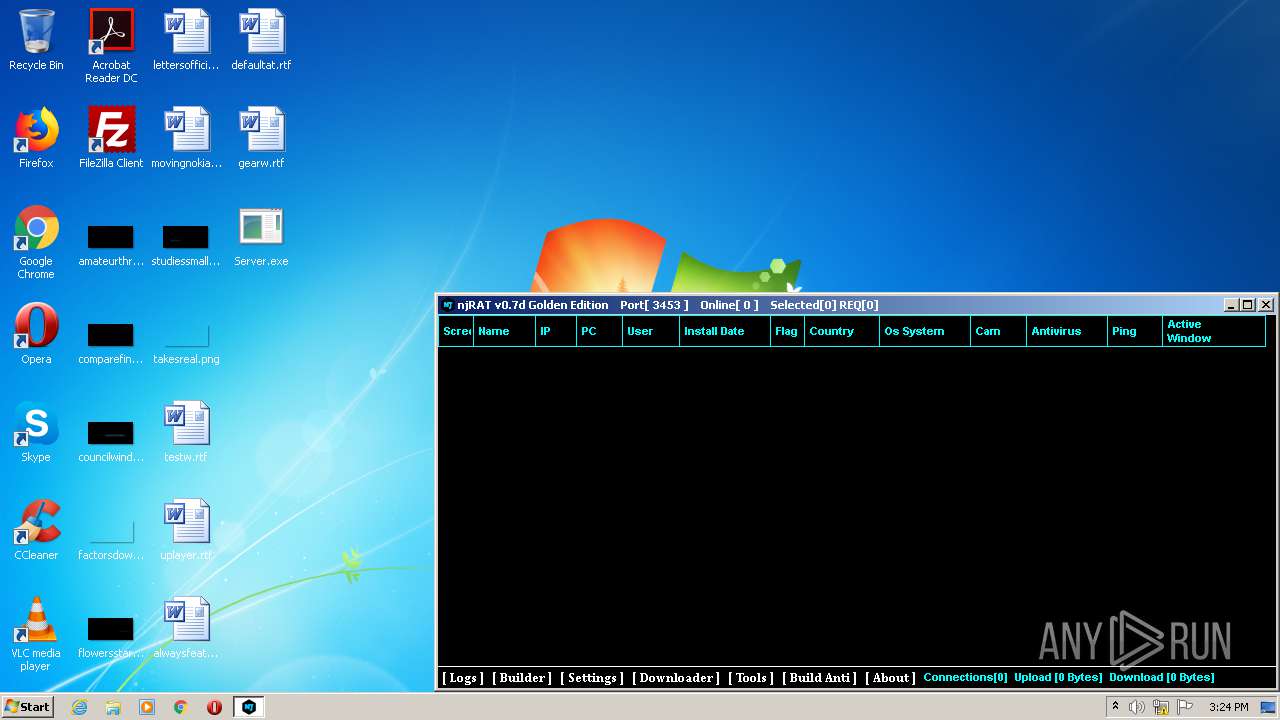
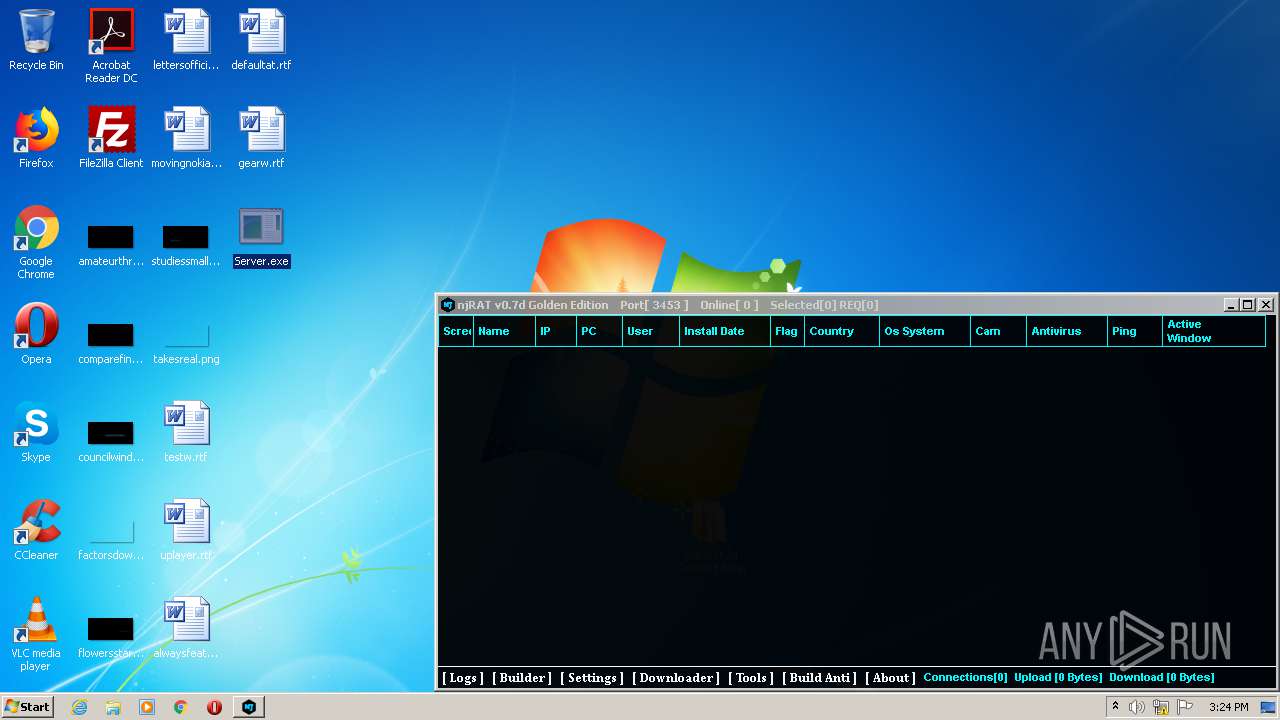
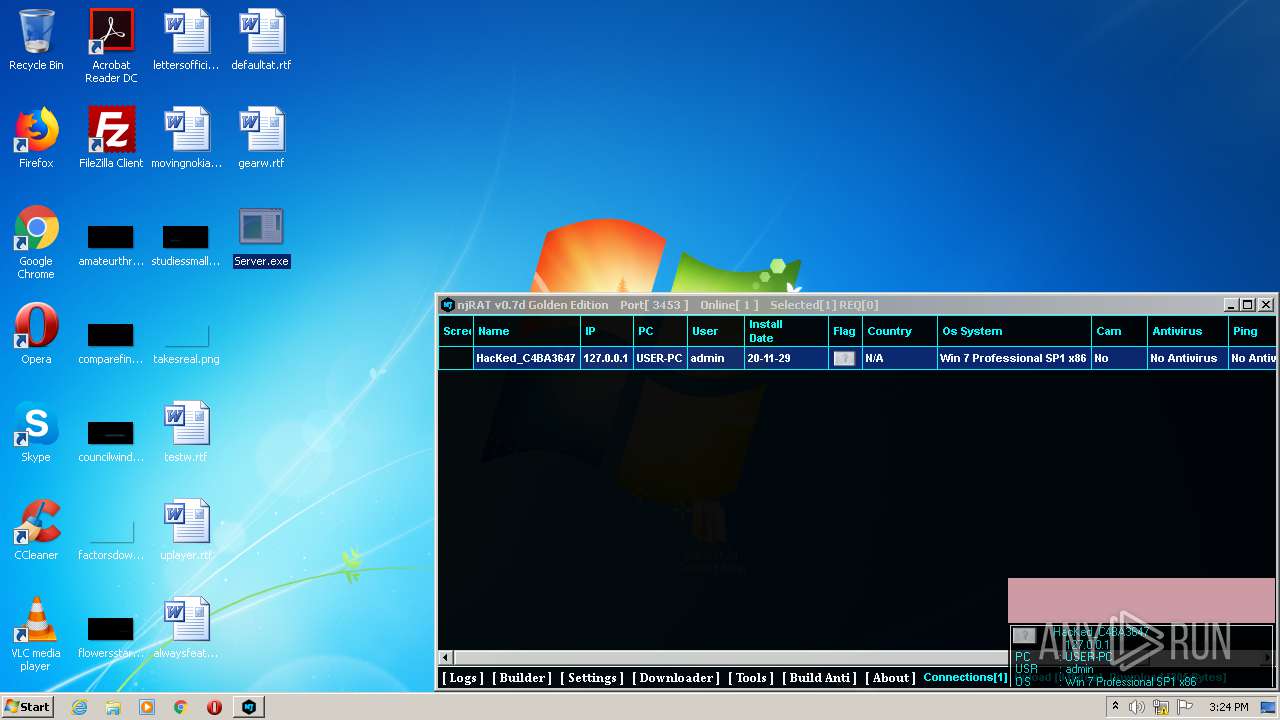
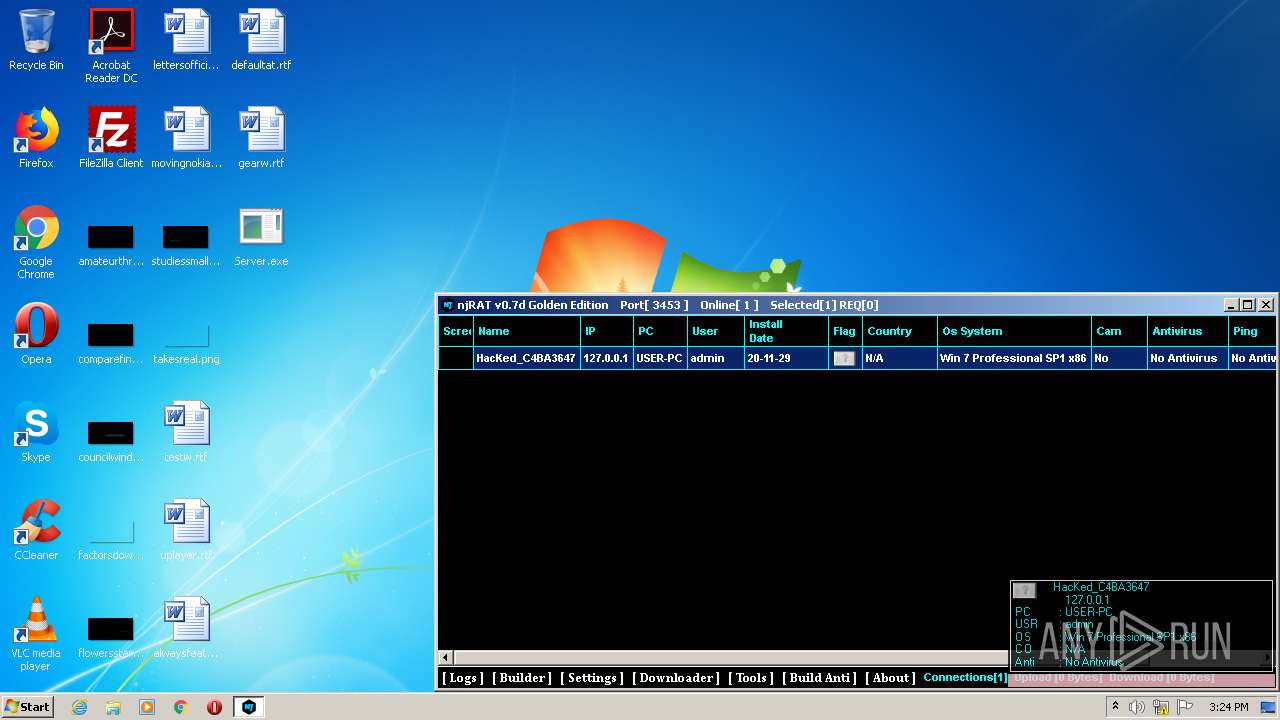
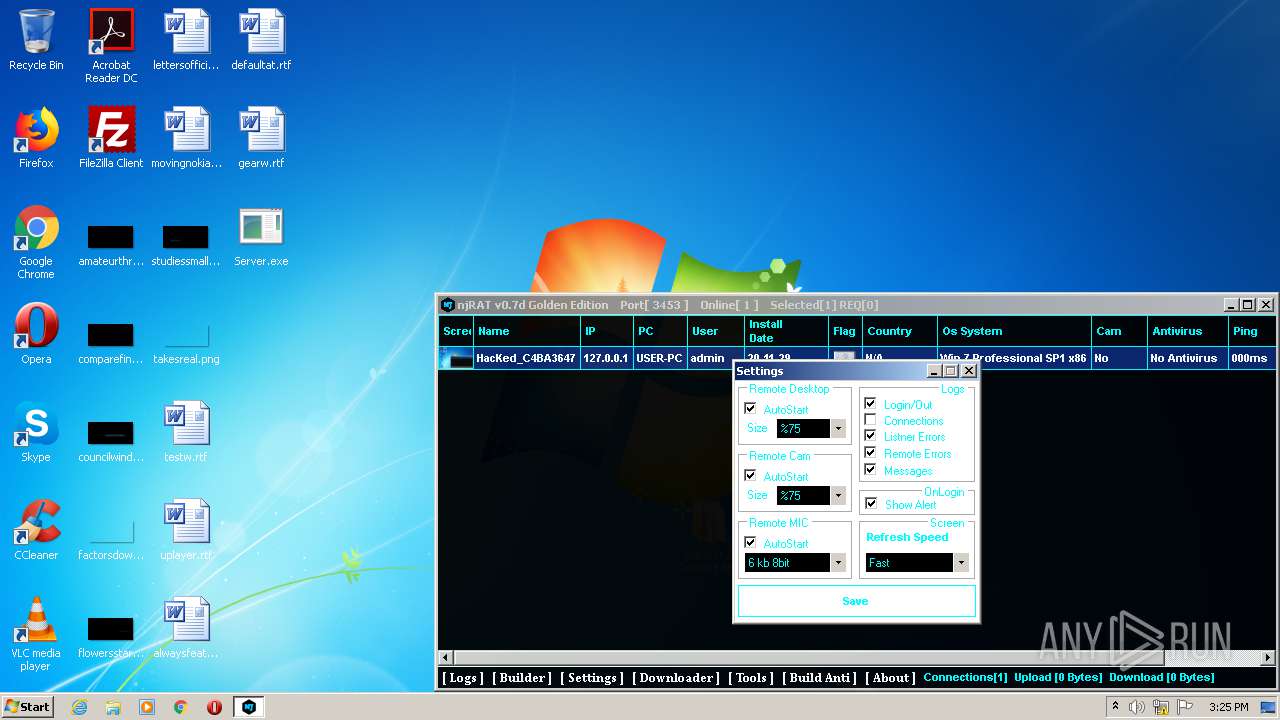
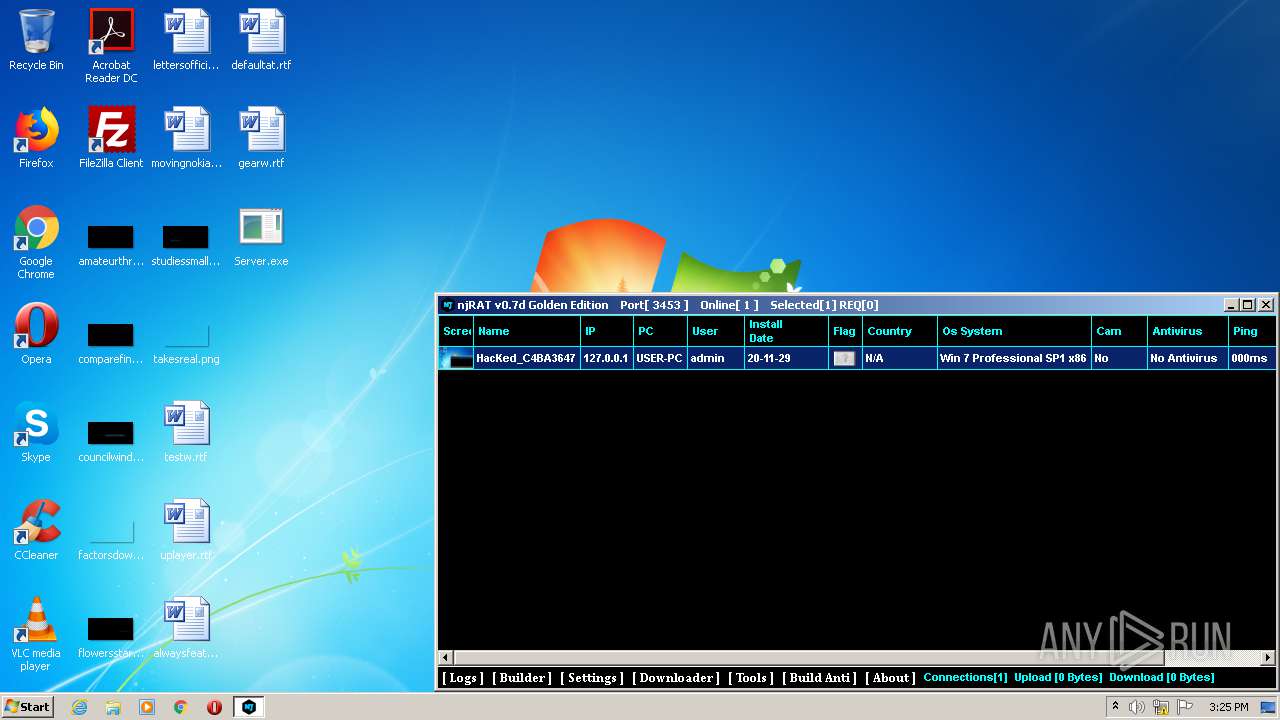
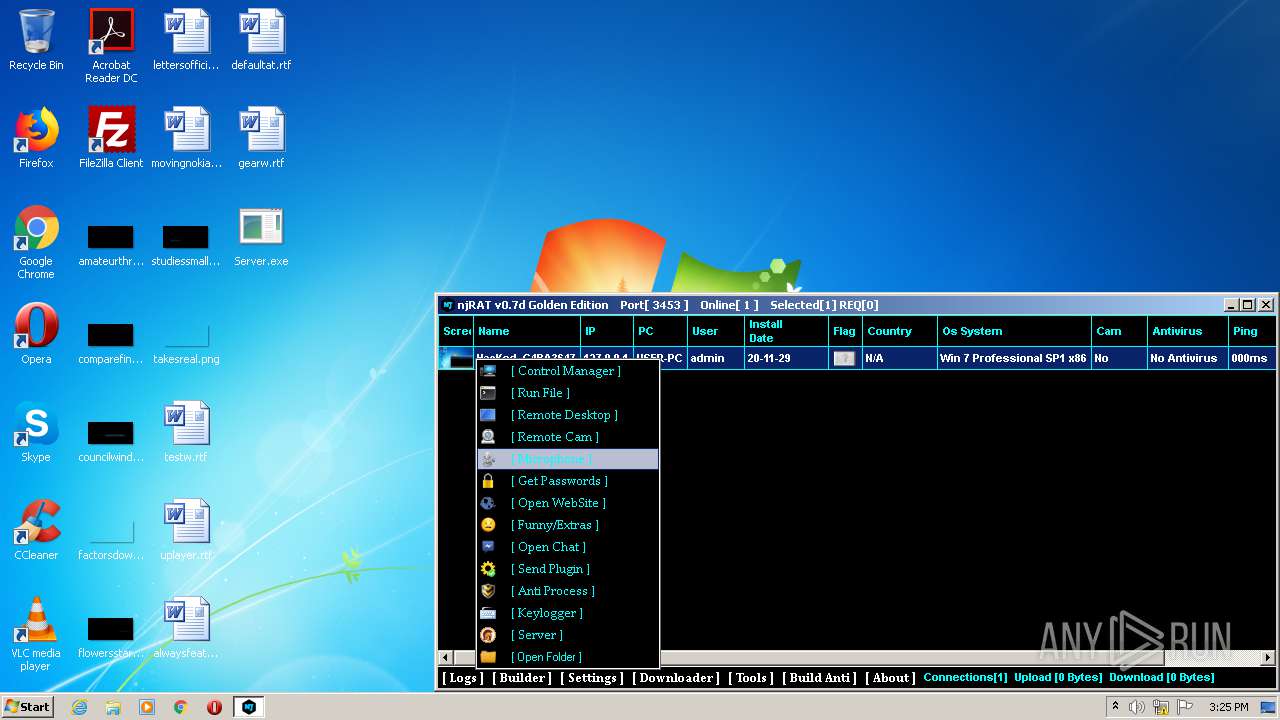
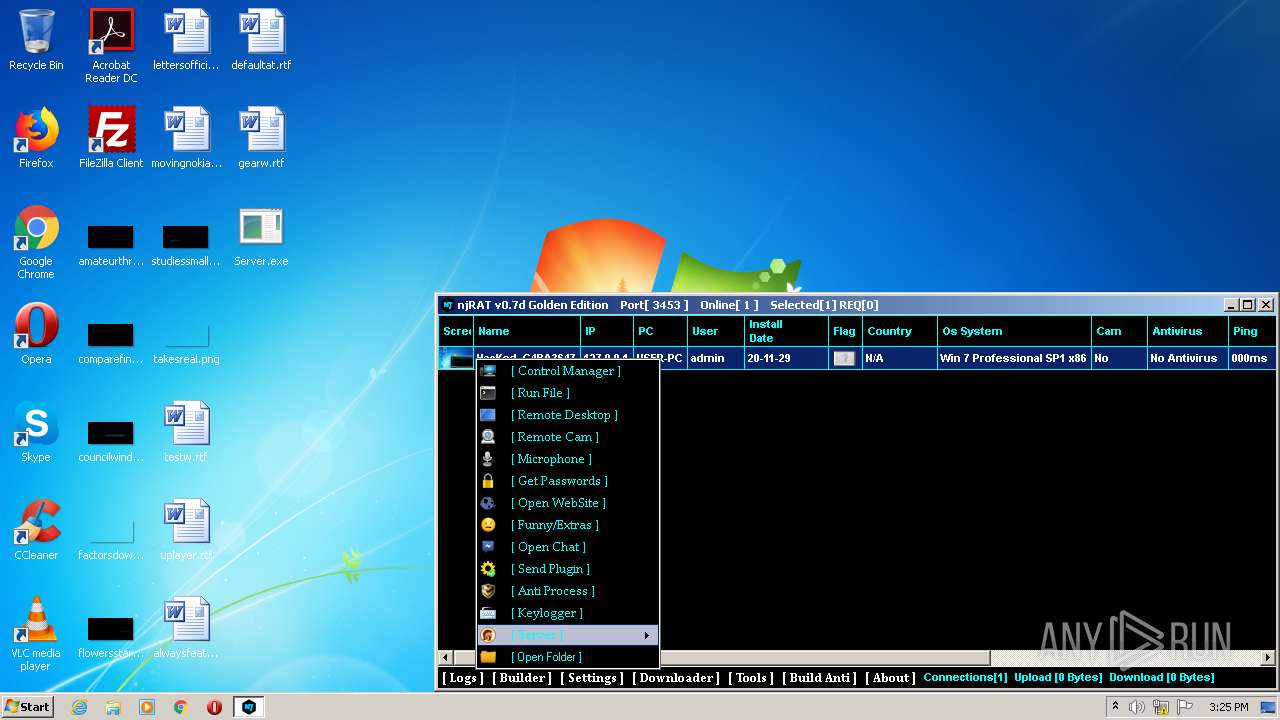
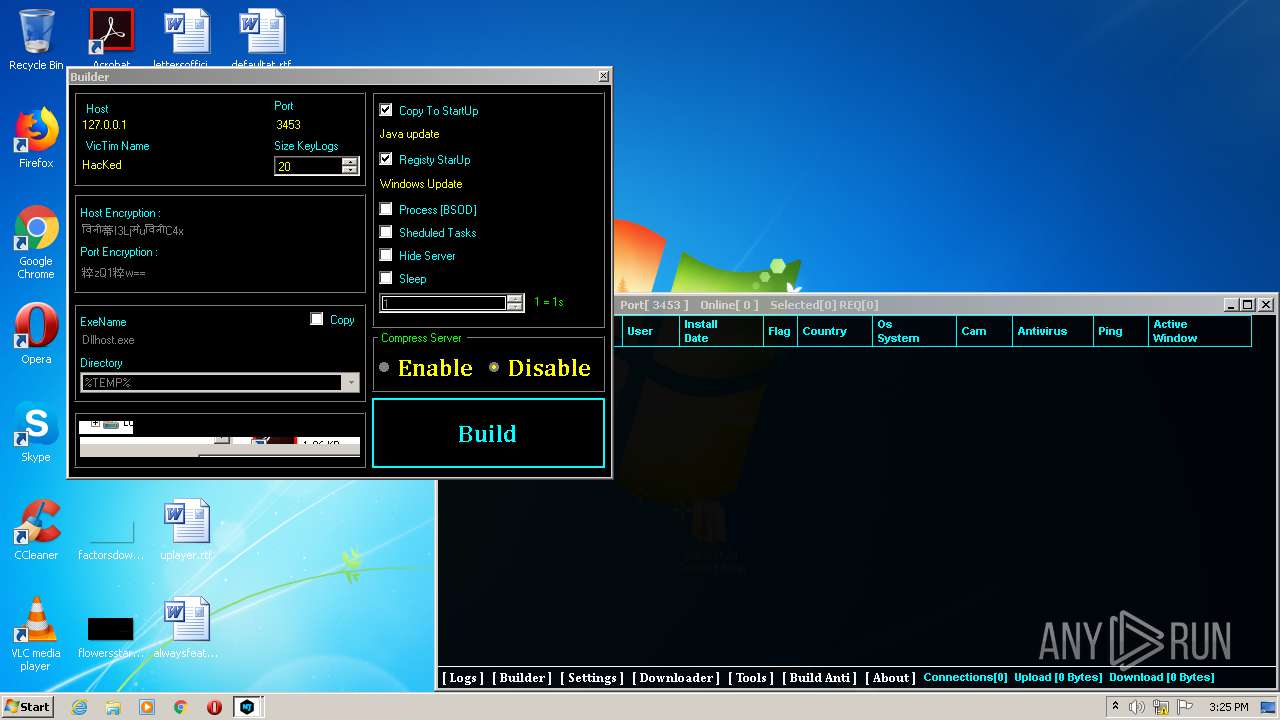
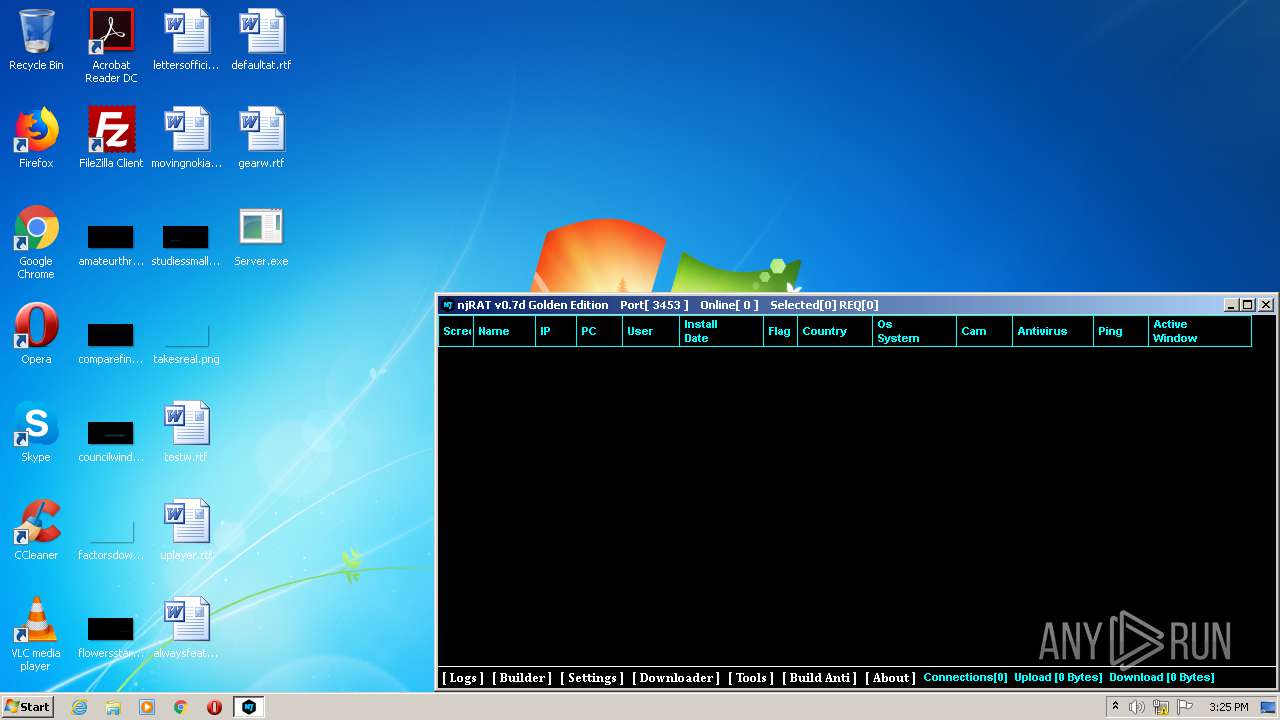
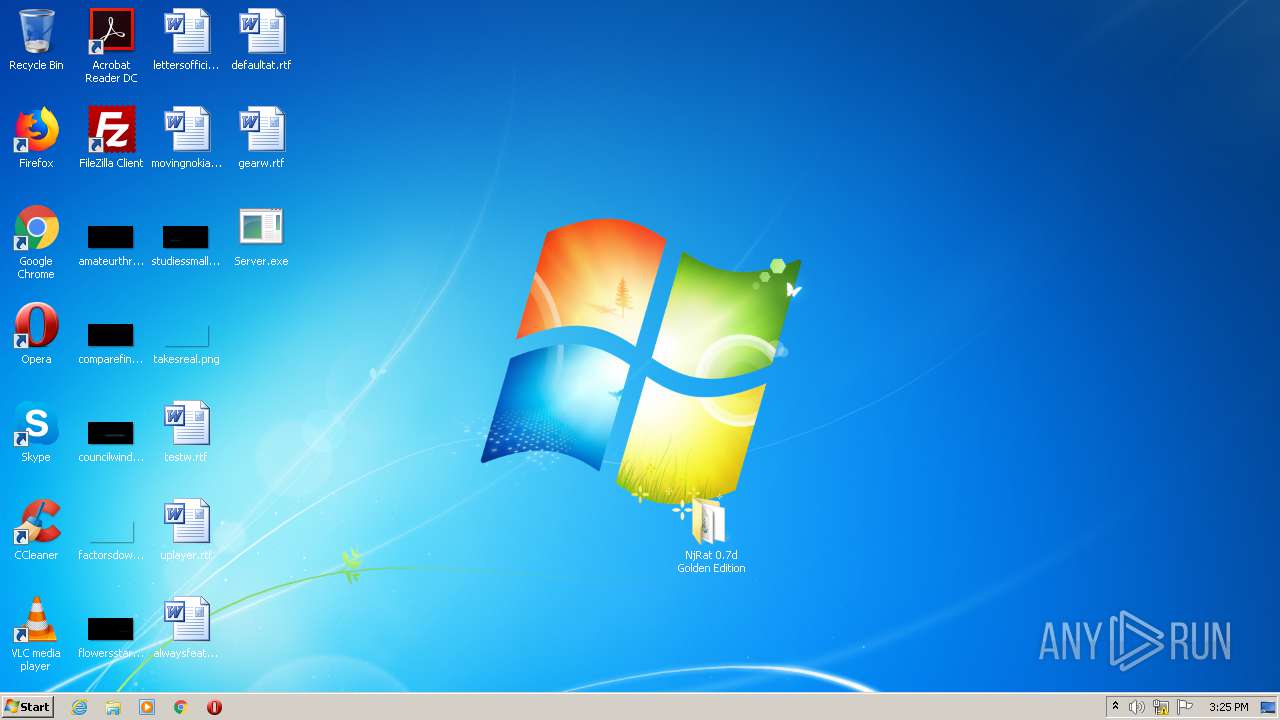
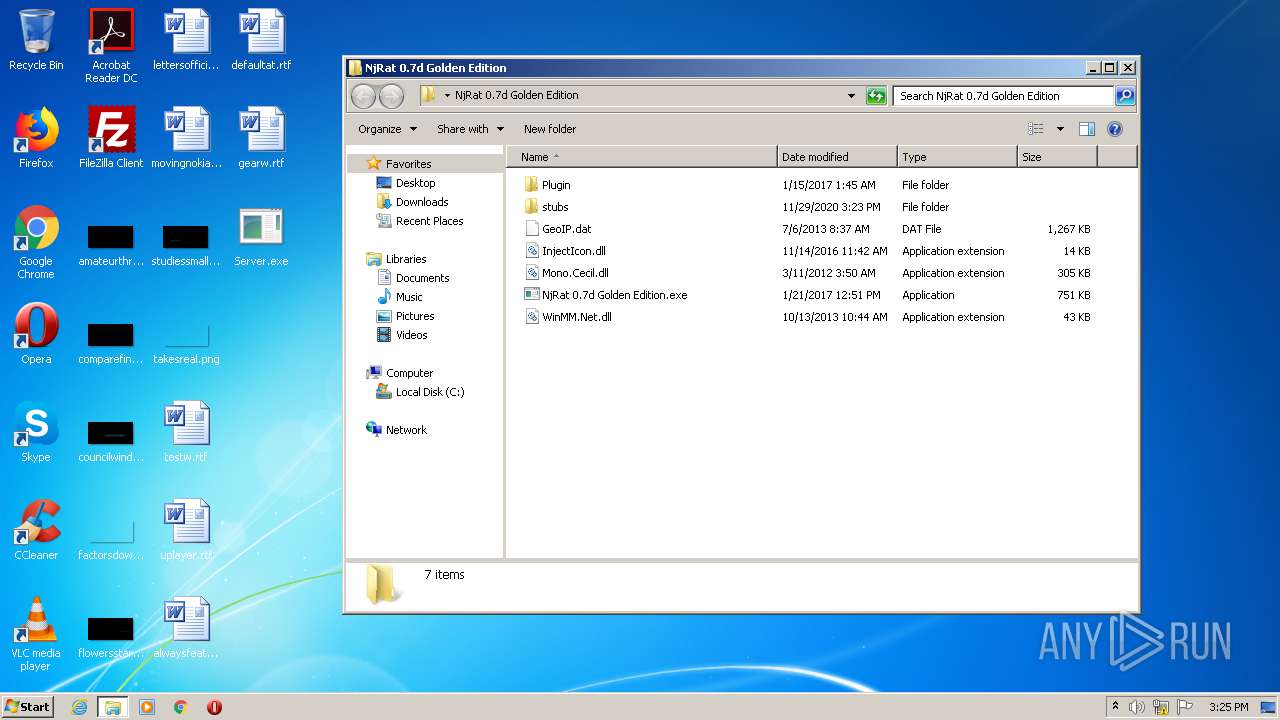
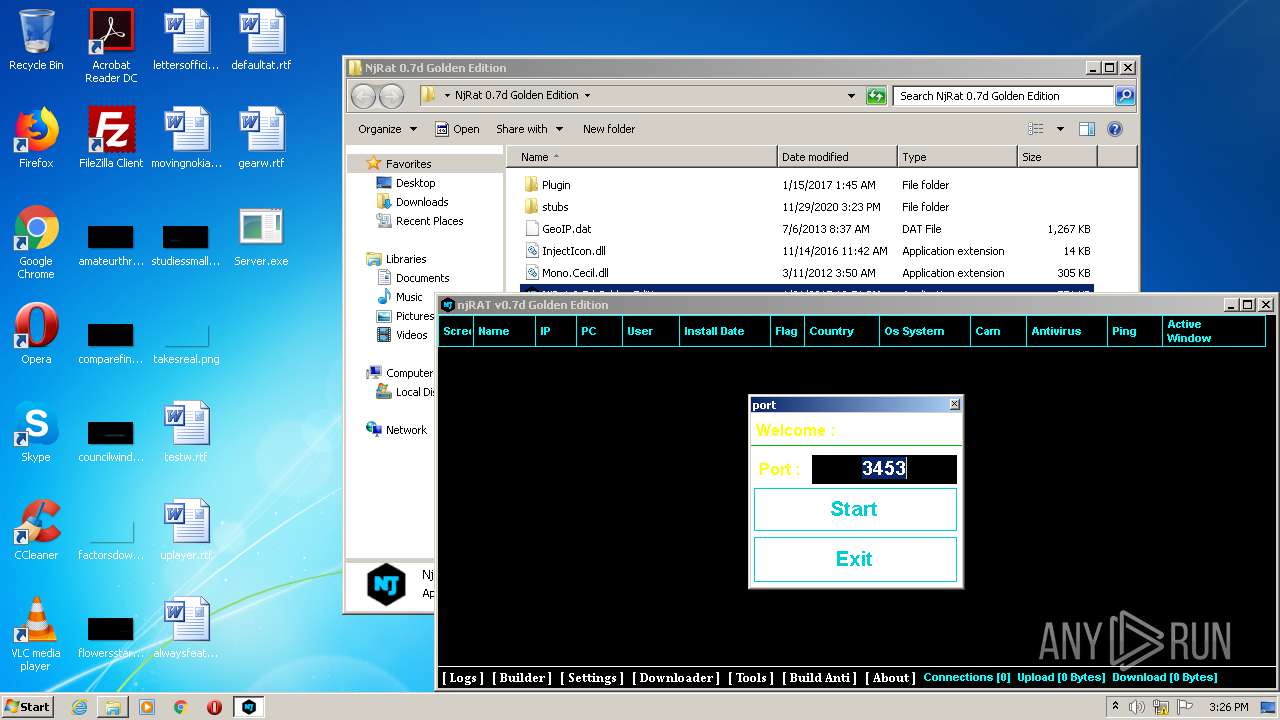
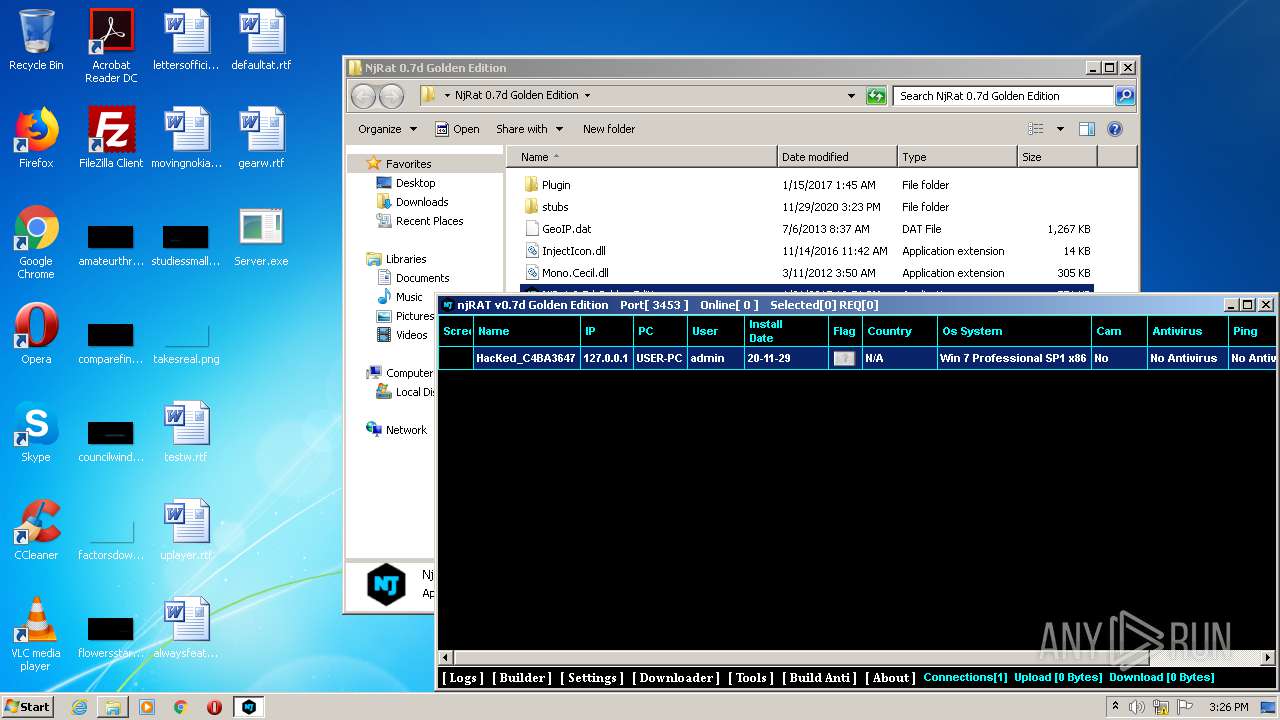
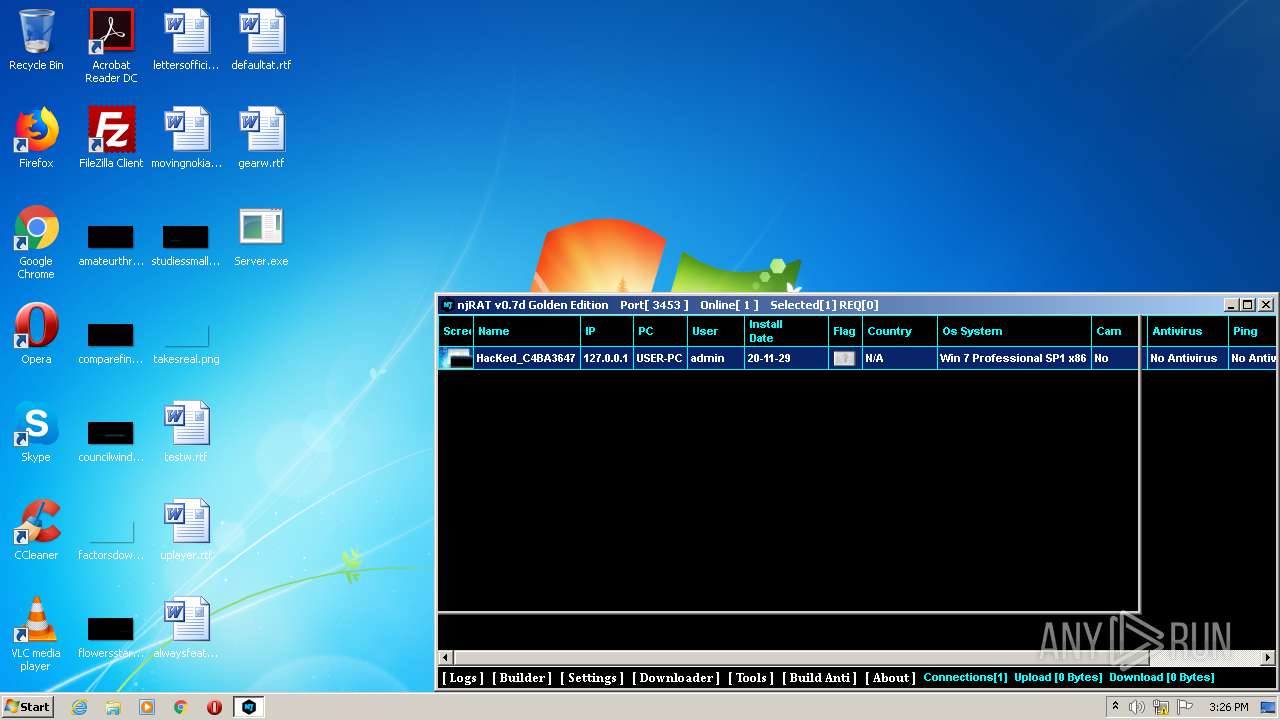
| File name: | NjRat_0.7d_Golden_Edition.rar |
| Full analysis: | https://app.any.run/tasks/9c8f52fe-51f7-4806-91b5-4a096a206c68 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2020, 15:22:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | C9CDD2A79133EA91595C3FCDFABC7A77 |
| SHA1: | 5E4868B15D942390F5887D2C5BB4525AF6A57A38 |
| SHA256: | C921F5E1616EAF2EDE3CE97D316FCA8CED1D741E3A65F4B23CE9F12103FC6765 |
| SSDEEP: | 49152:gmvGePTZ09B+Rw6BGpYE4RhfeB5R4XAwNuqfL:H10hVpyhfeBMQwcIL |
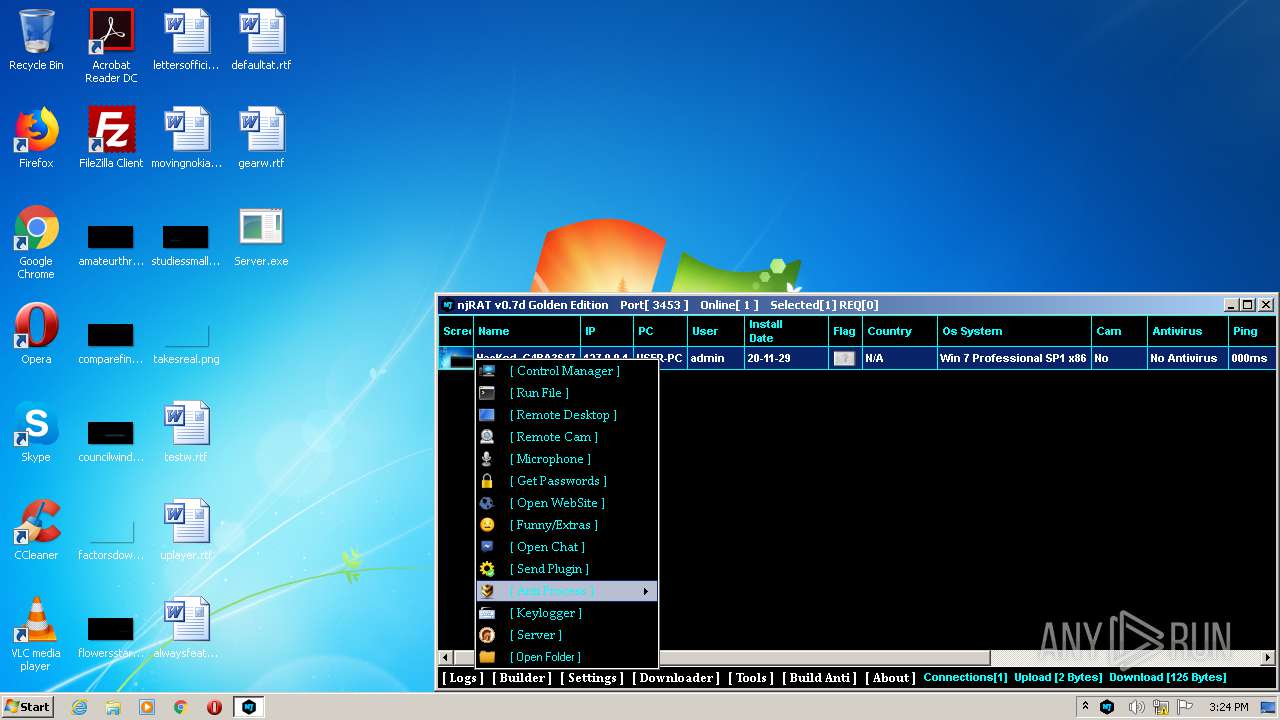
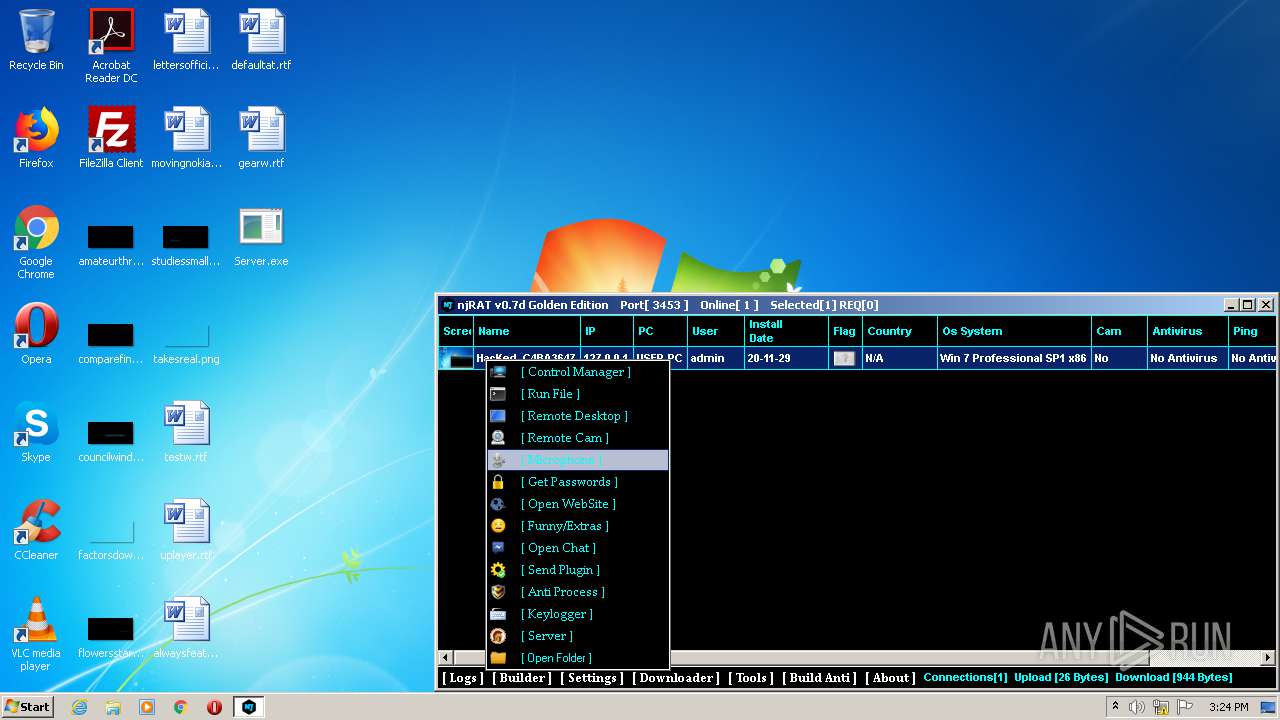
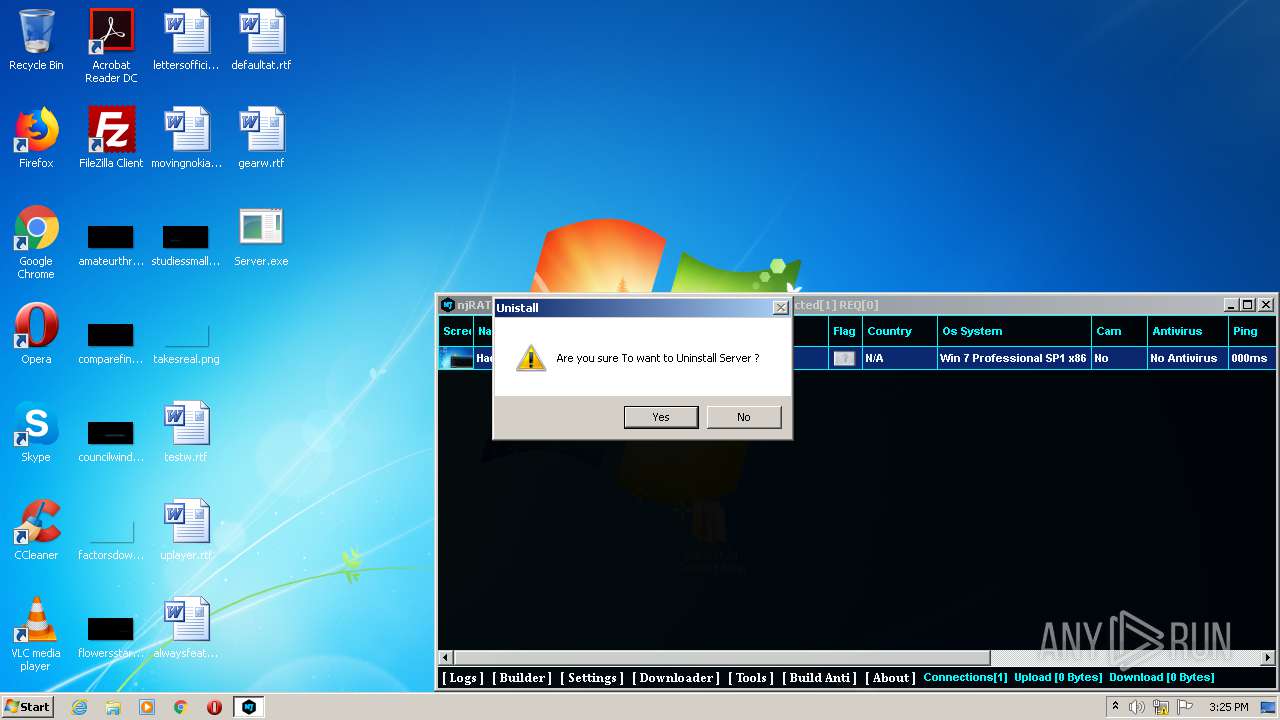
MALICIOUS
Application was dropped or rewritten from another process
- Server.exe (PID: 1872)
- Server.exe (PID: 3048)
- Server.exe (PID: 2564)
- Server.exe (PID: 3264)
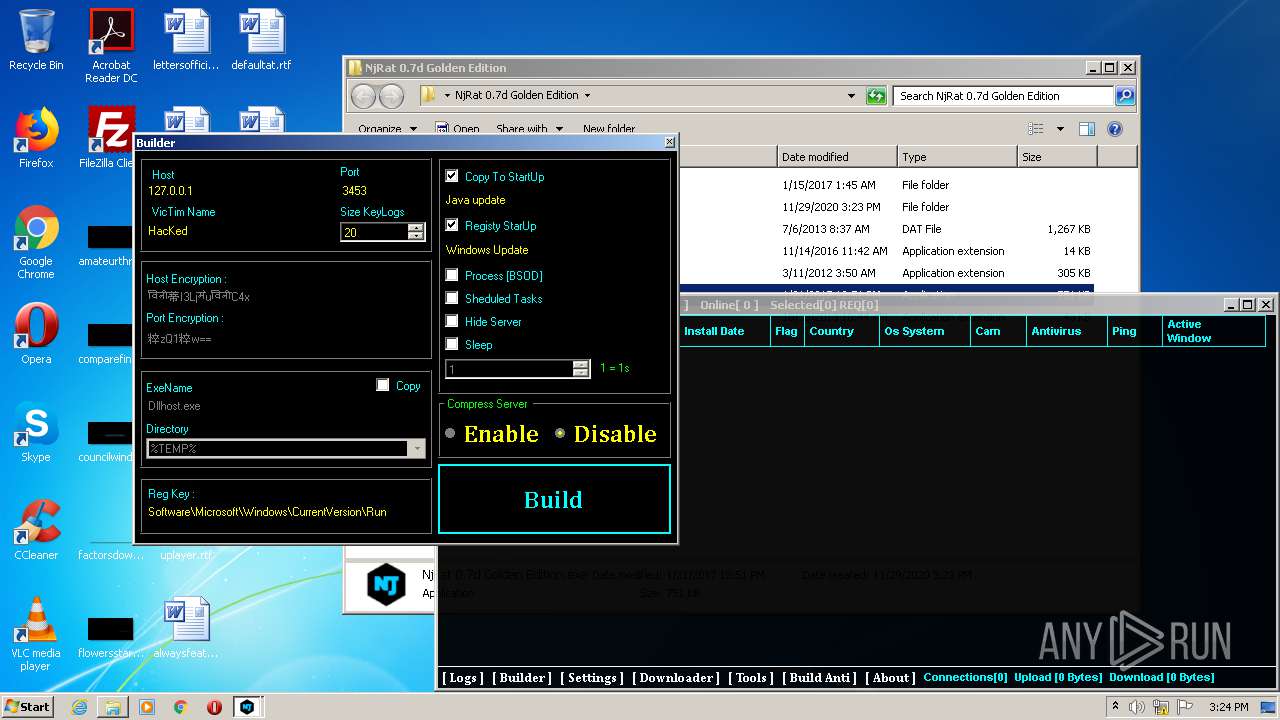
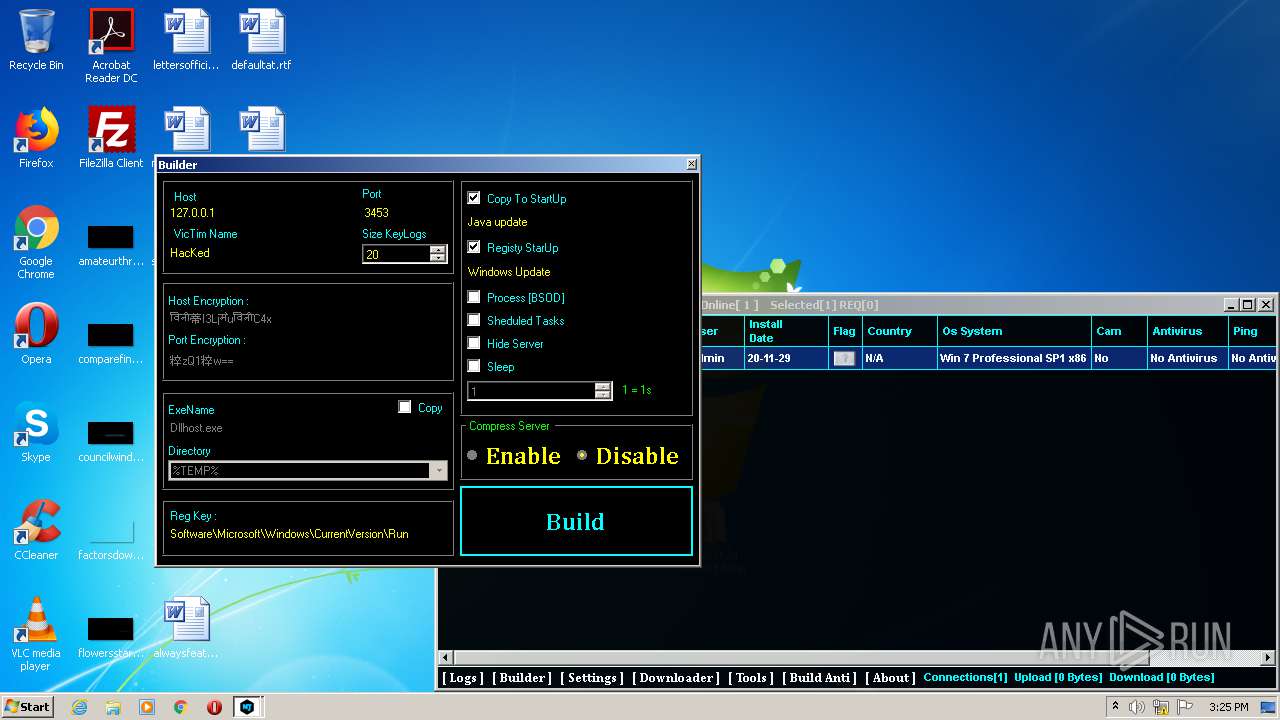
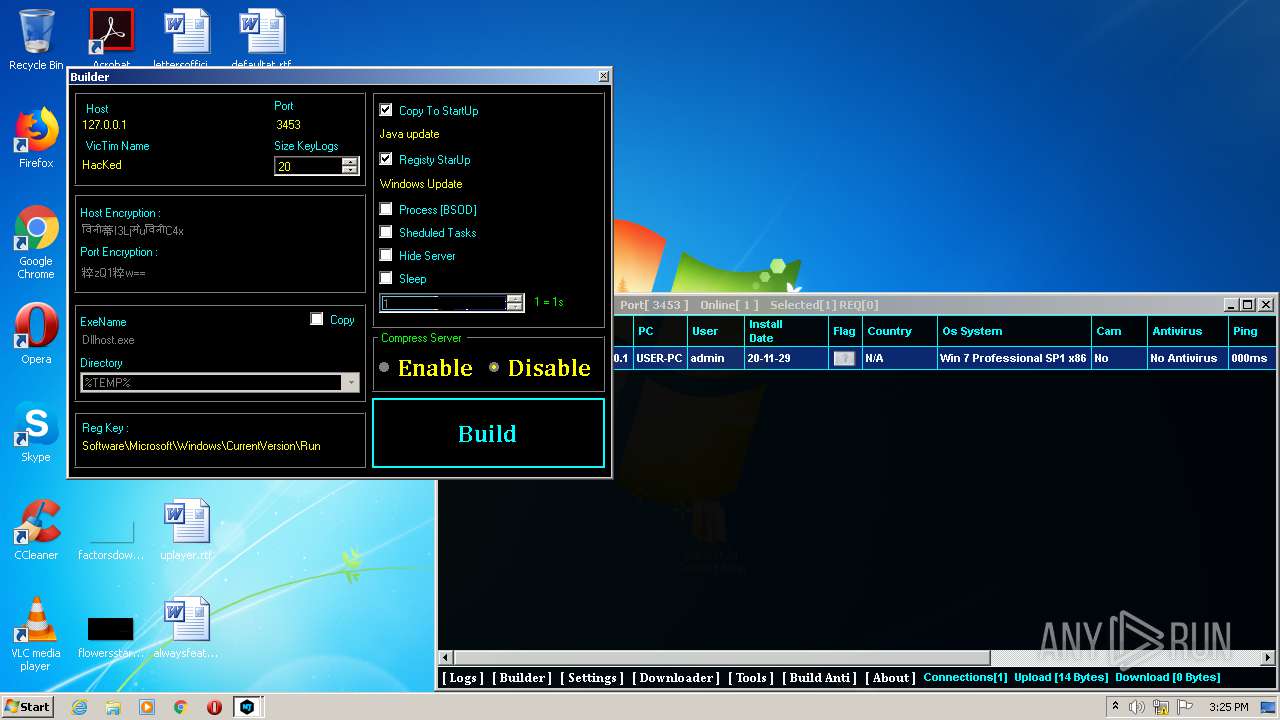
Changes the autorun value in the registry
- Server.exe (PID: 1872)
- Server.exe (PID: 3048)
- Server.exe (PID: 2564)
Writes to a start menu file
- Server.exe (PID: 1872)
- Server.exe (PID: 2564)
- Server.exe (PID: 3048)
SUSPICIOUS
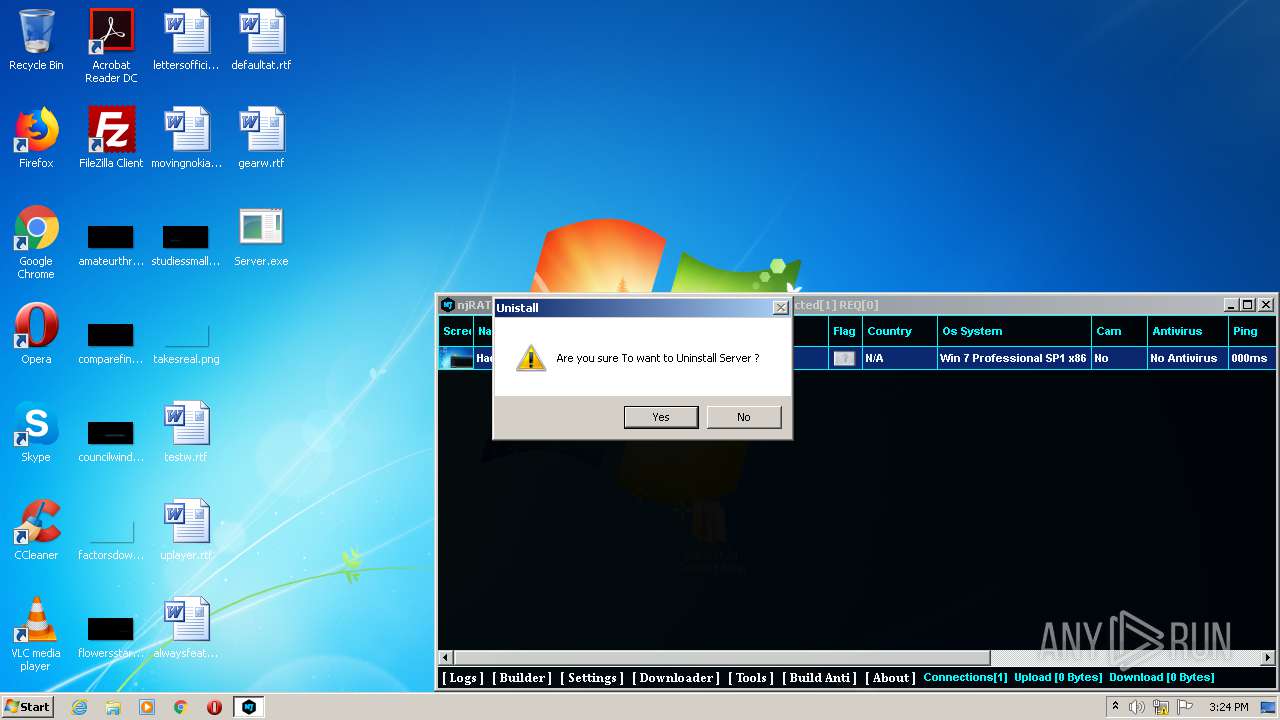
Starts CMD.EXE for self-deleting
- Server.exe (PID: 3048)
- Server.exe (PID: 1872)
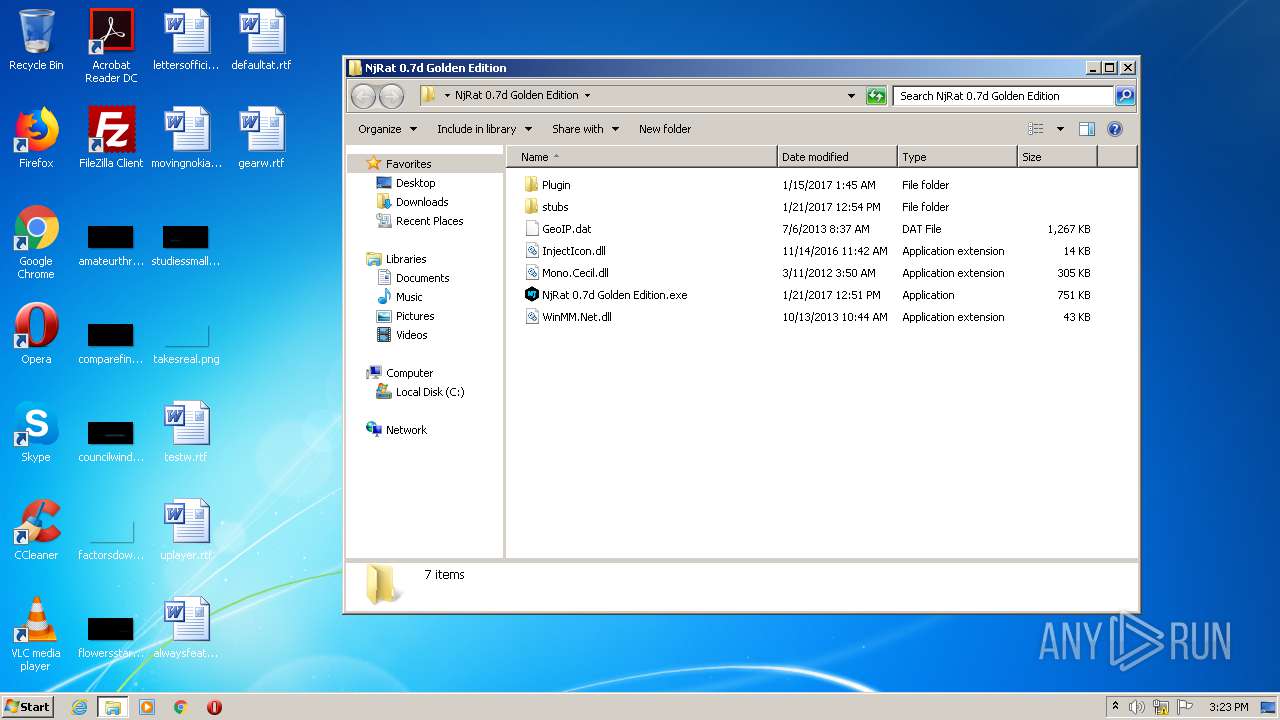
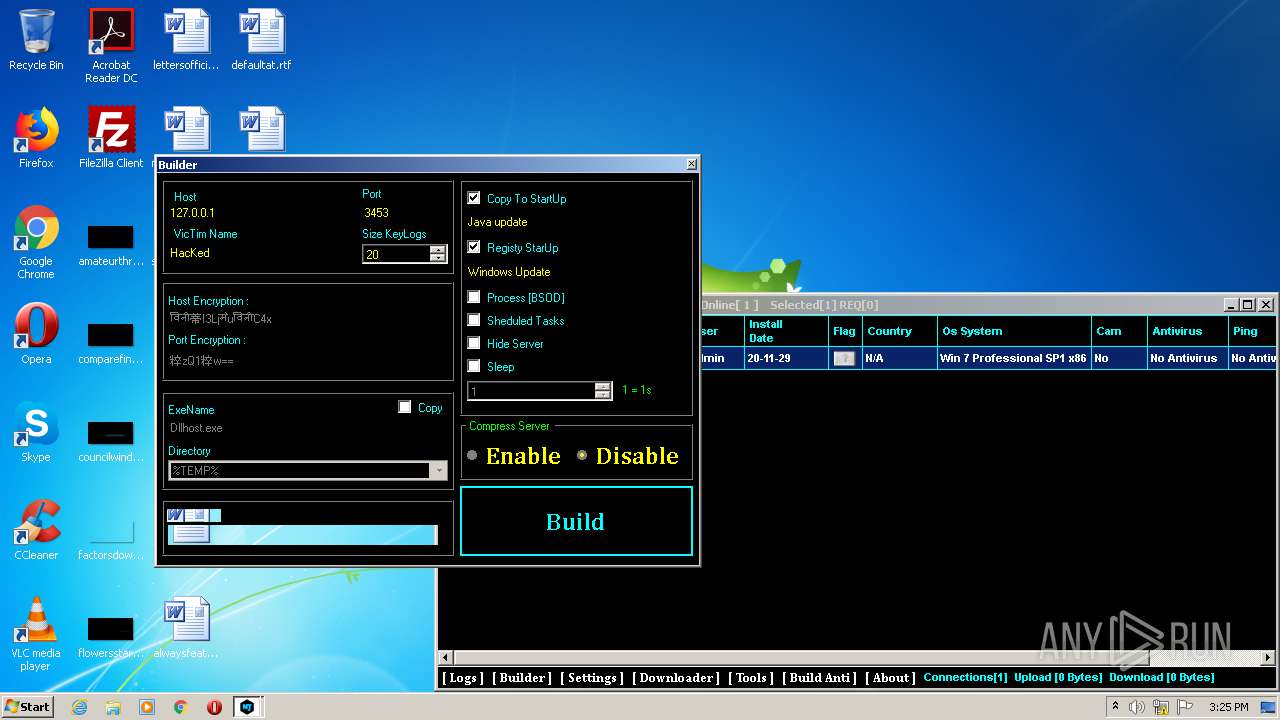
Executable content was dropped or overwritten
- NjRat 0.7d Golden Edition.exe (PID: 3588)
- Server.exe (PID: 1872)
- NjRat 0.7d Golden Edition.exe (PID: 4064)
- Server.exe (PID: 2564)
- Server.exe (PID: 3048)
Starts CMD.EXE for commands execution
- Server.exe (PID: 3048)
- Server.exe (PID: 1872)
Drops a file with a compile date too recent
- NjRat 0.7d Golden Edition.exe (PID: 3588)
- Server.exe (PID: 1872)
- NjRat 0.7d Golden Edition.exe (PID: 4064)
- Server.exe (PID: 2564)
- Server.exe (PID: 3048)
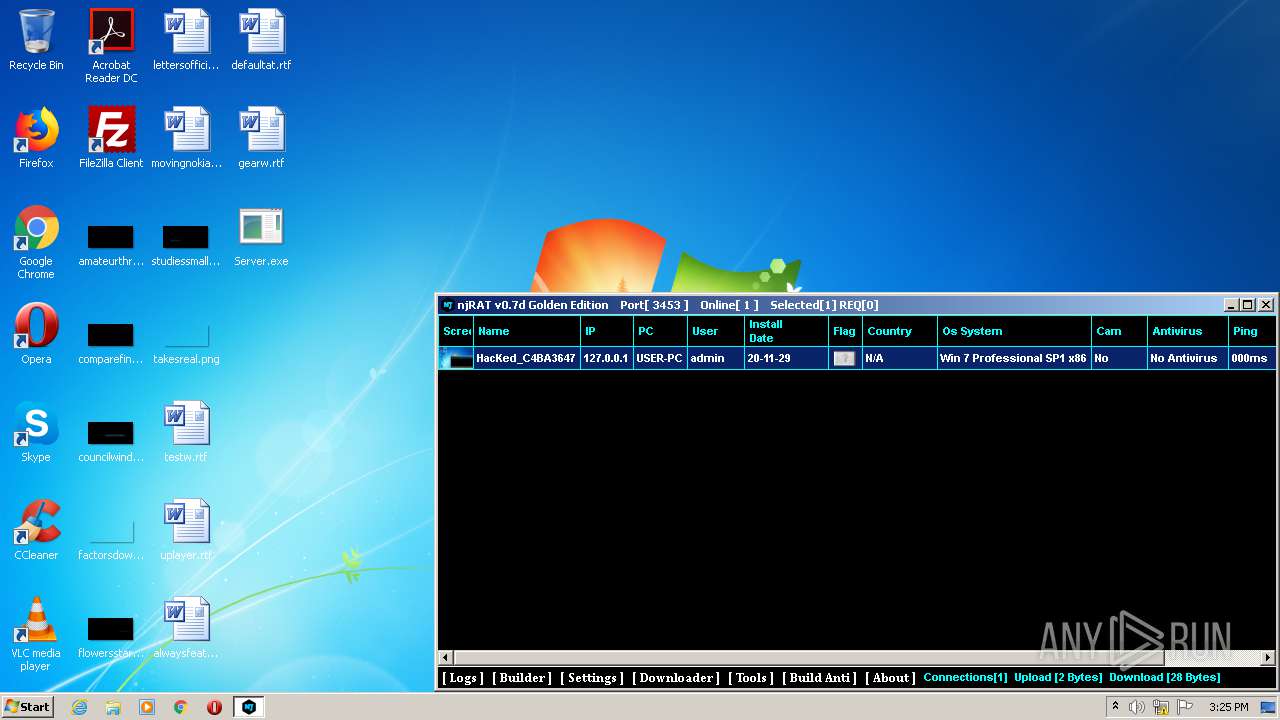
Creates files in the user directory
- Server.exe (PID: 3048)
INFO
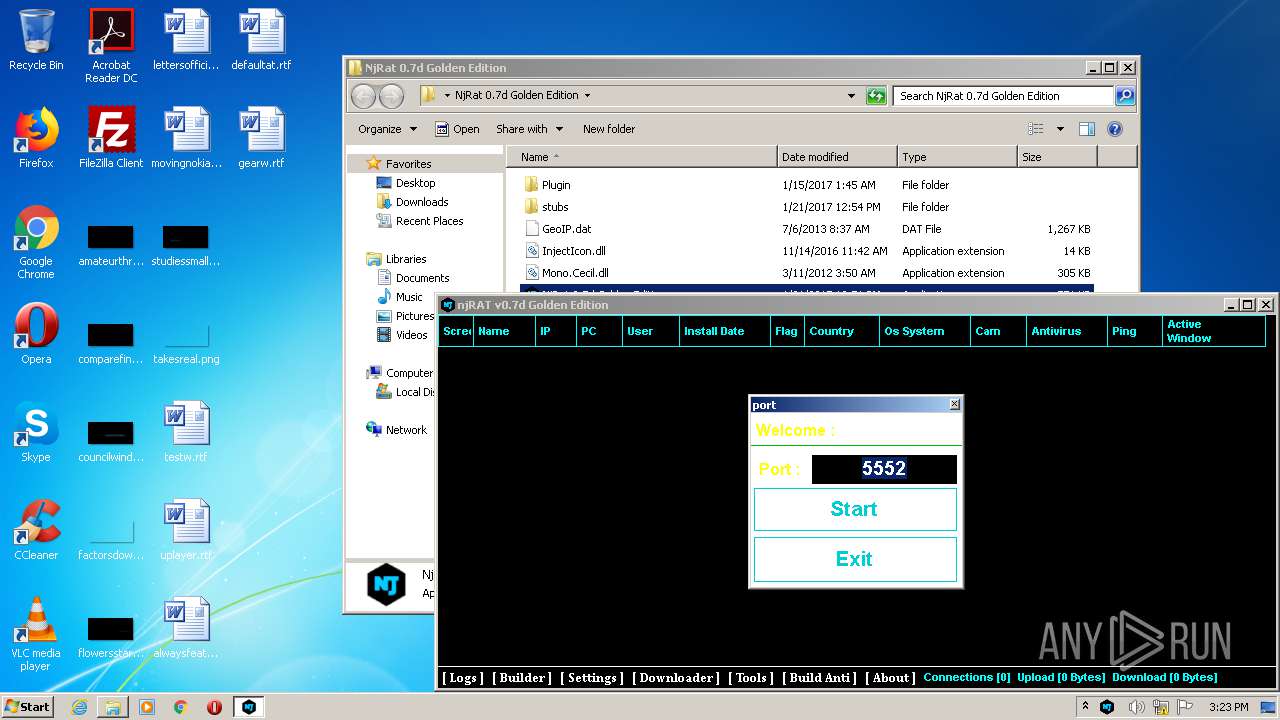
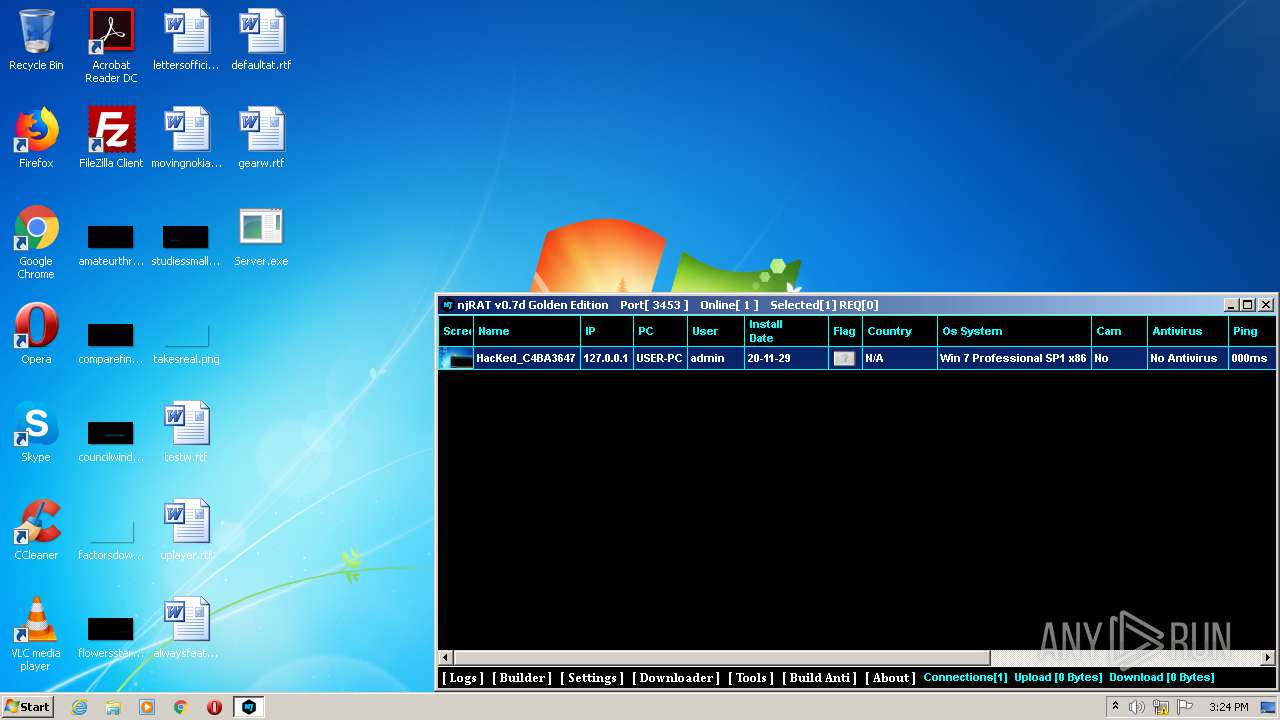
Manual execution by user
- NjRat 0.7d Golden Edition.exe (PID: 4064)
- Server.exe (PID: 1872)
- NjRat 0.7d Golden Edition.exe (PID: 3588)
- Server.exe (PID: 3048)
- Server.exe (PID: 2564)
- Server.exe (PID: 3264)
- NjRat 0.7d Golden Edition.exe (PID: 1600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
54
Monitored processes
12
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 340 | ping 0 -n 2 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1352 | ping 0 -n 2 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
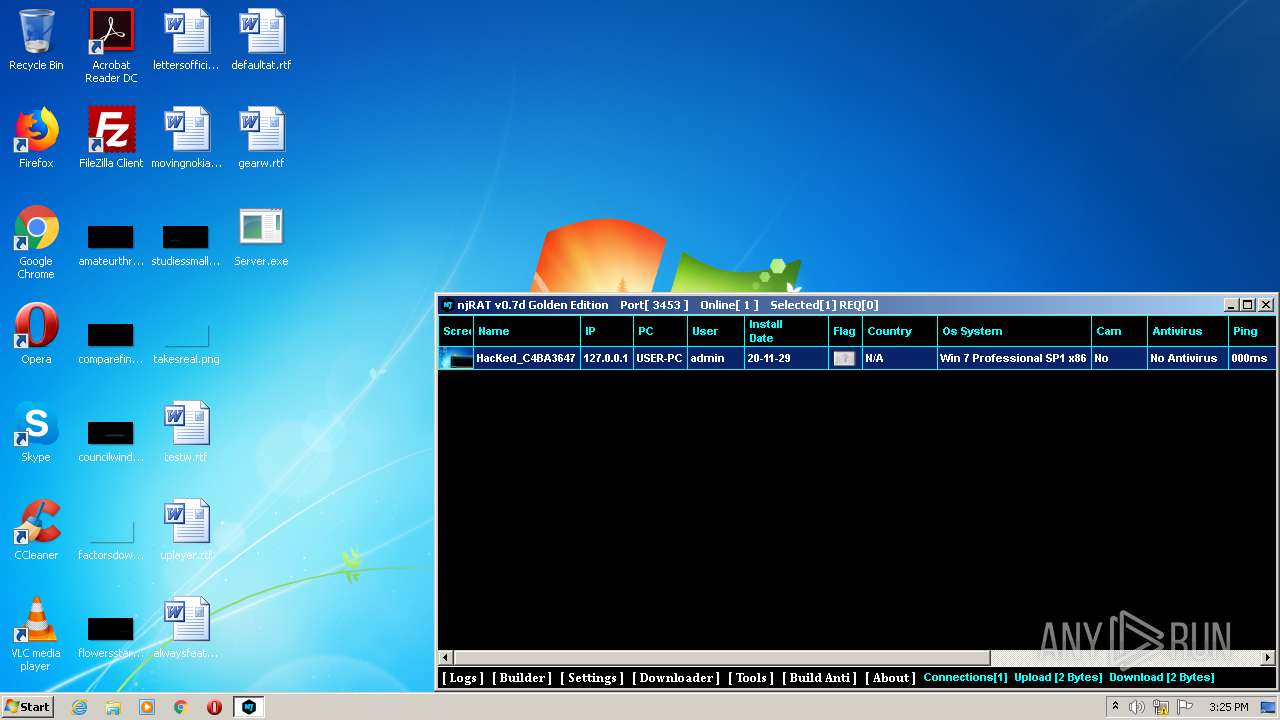
| 1600 | "C:\Users\admin\Desktop\NjRat 0.7d Golden Edition\NjRat 0.7d Golden Edition.exe" | C:\Users\admin\Desktop\NjRat 0.7d Golden Edition\NjRat 0.7d Golden Edition.exe | — | explorer.exe | |||||||||||
User: admin Company: Njrat 0.7d Golden Edition Integrity Level: MEDIUM Description: Njrat 0.7d Golden Edition Exit code: 3221225547 Version: 7.1.0.0 Modules
| |||||||||||||||
| 1872 | "C:\Users\admin\Desktop\Server.exe" | C:\Users\admin\Desktop\Server.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2316 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\NjRat_0.7d_Golden_Edition.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2564 | "C:\Users\admin\Desktop\Server.exe" | C:\Users\admin\Desktop\Server.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2592 | cmd.exe /c ping 0 -n 2 & del "C:\Users\admin\Desktop\Server.exe" | C:\Windows\system32\cmd.exe | — | Server.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3012 | cmd.exe /c ping 0 -n 2 & del "C:\Users\admin\Desktop\Server.exe" | C:\Windows\system32\cmd.exe | — | Server.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3048 | "C:\Users\admin\Desktop\Server.exe" | C:\Users\admin\Desktop\Server.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3264 | "C:\Users\admin\Desktop\Server.exe" | C:\Users\admin\Desktop\Server.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
2 128
Read events
1 709
Write events
402
Delete events
17
Modification events
| (PID) Process: | (2316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2316) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\NjRat_0.7d_Golden_Edition.rar | |||
| (PID) Process: | (2316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
6
Suspicious files
0
Text files
28
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2316.21871\NjRat 0.7d Golden Edition\GeoIP.dat | — | |
MD5:— | SHA256:— | |||
| 2316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2316.21871\NjRat 0.7d Golden Edition\InjectIcon.dll | — | |
MD5:— | SHA256:— | |||
| 2316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2316.21871\NjRat 0.7d Golden Edition\Mono.Cecil.dll | — | |
MD5:— | SHA256:— | |||
| 2316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2316.21871\NjRat 0.7d Golden Edition\NjRat 0.7d Golden Edition.exe | — | |
MD5:— | SHA256:— | |||
| 2316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2316.21871\NjRat 0.7d Golden Edition\Plugin\AntiProcess.dll | — | |
MD5:— | SHA256:— | |||
| 2316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2316.21871\NjRat 0.7d Golden Edition\Plugin\cam.dll | — | |
MD5:— | SHA256:— | |||
| 2316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2316.21871\NjRat 0.7d Golden Edition\Plugin\ch.dll | — | |
MD5:— | SHA256:— | |||
| 2316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2316.21871\NjRat 0.7d Golden Edition\Plugin\mic.dll | — | |
MD5:— | SHA256:— | |||
| 2316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2316.21871\NjRat 0.7d Golden Edition\Plugin\plg.dll | — | |
MD5:— | SHA256:— | |||
| 2316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2316.21871\NjRat 0.7d Golden Edition\Plugin\pw.dll | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report