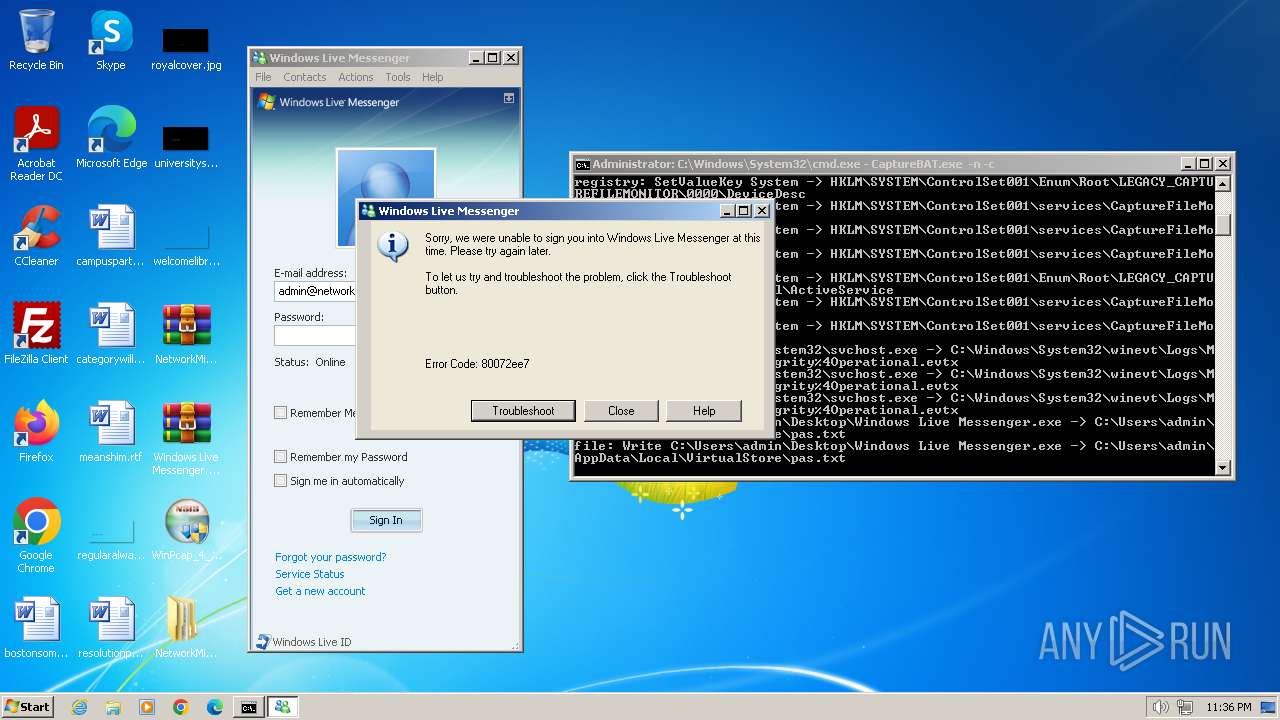
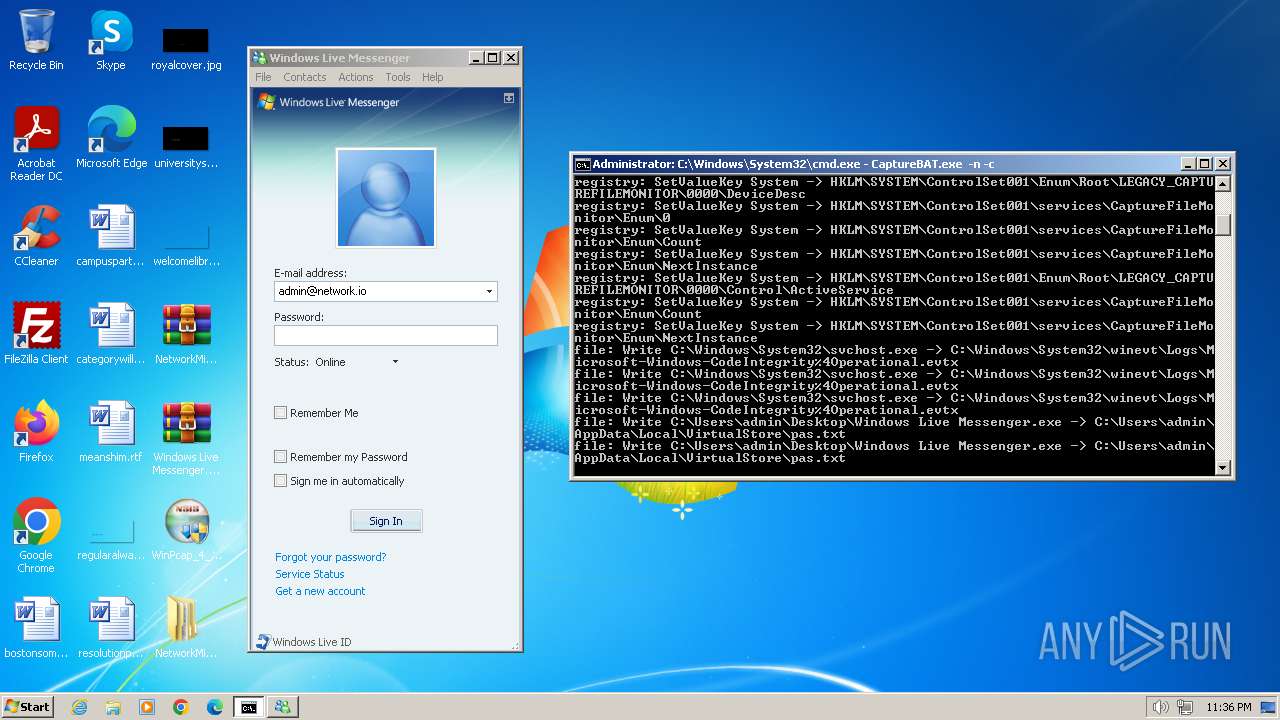
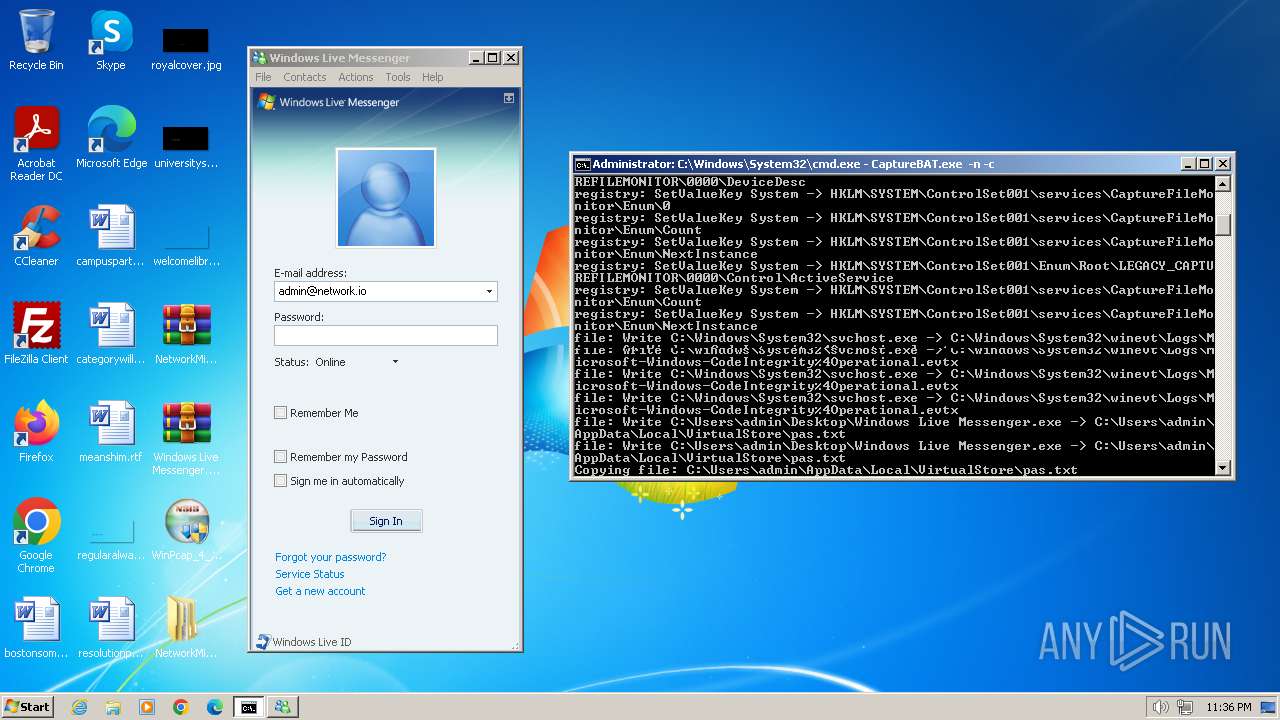
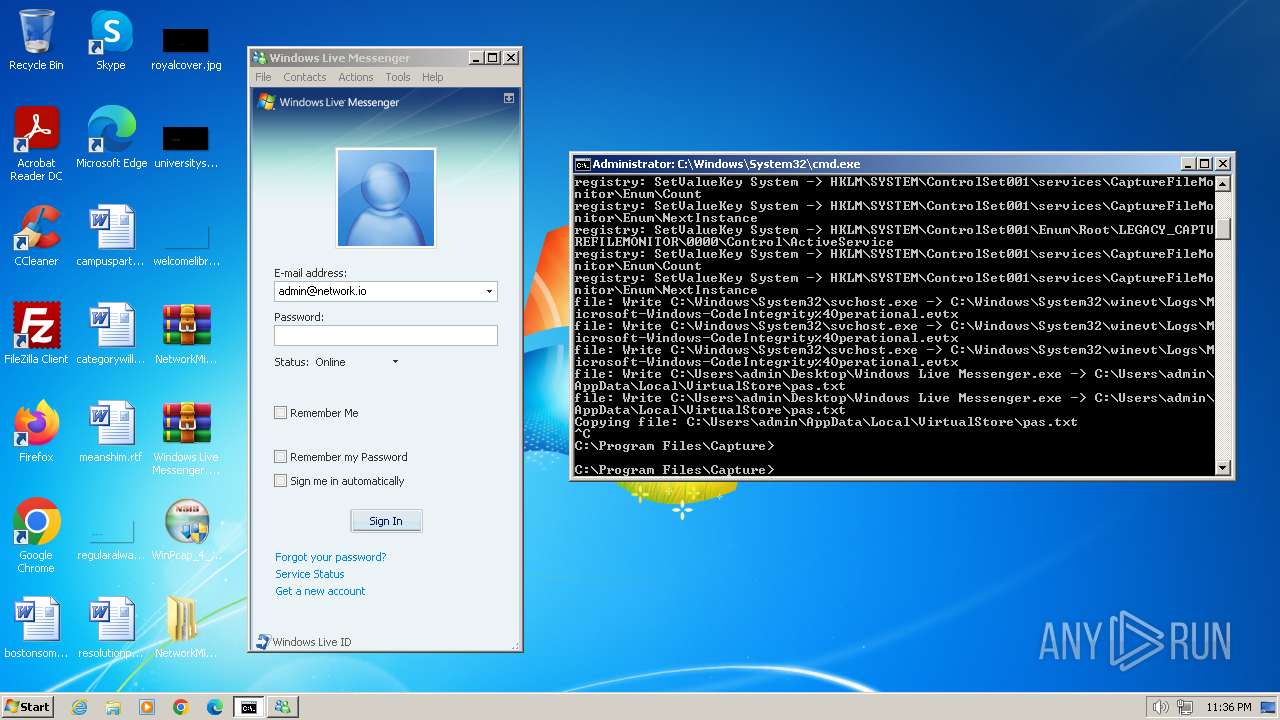
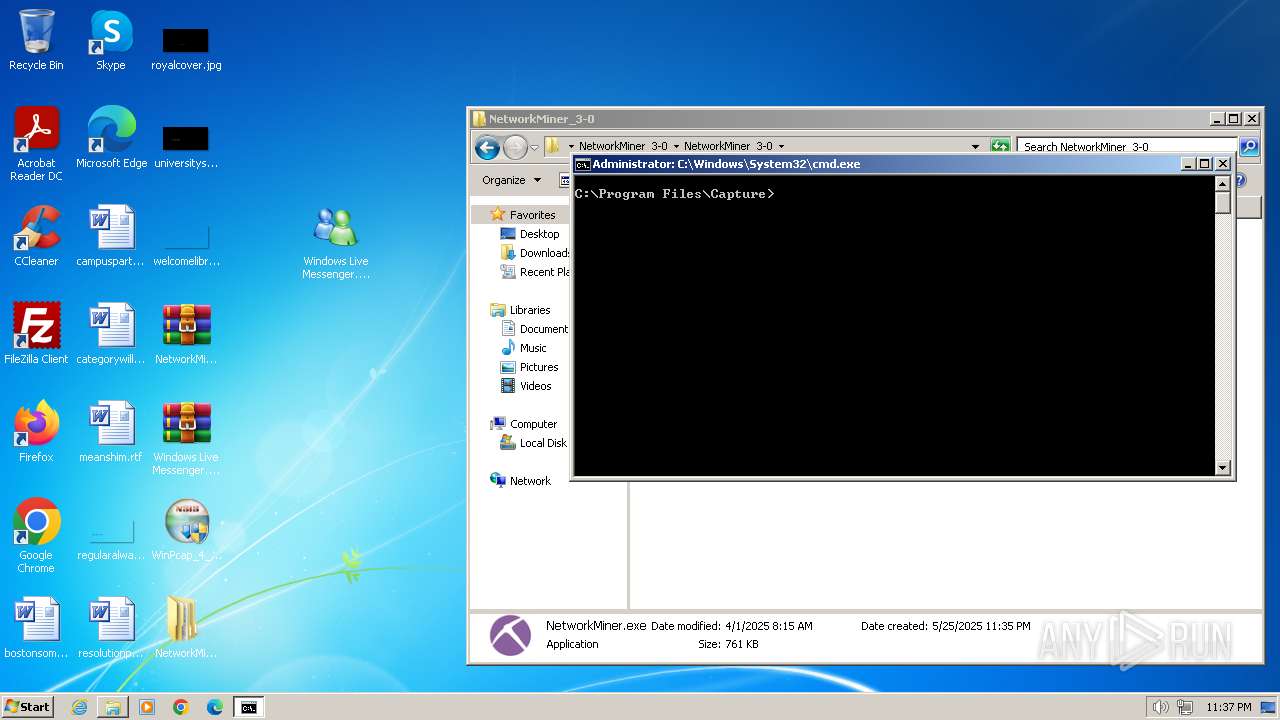
| File name: | CaptureBAT-Setup-2.0.0-5574.exe |
| Full analysis: | https://app.any.run/tasks/a2152eb5-f77f-444e-85f2-6565b5841bcb |
| Verdict: | Malicious activity |
| Analysis date: | May 25, 2025, 22:34:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | C1894E46FFE89BE6CA35729D9DAB6145 |
| SHA1: | C507C1FEA3C550DC32D4B0238DF47115AB4CD8DE |
| SHA256: | C91E50A921F07EB7CE510441761DAF38F3E4E6340CF9FAF67E660A3D13BD88E8 |
| SSDEEP: | 24576:B4cDmEFhnydPdXKdNtxqD8gXdP0zUlsFXZRRh6:B4cDmEFhydPdXKdNtxqD8gXdMzUls5Zg |
MALICIOUS
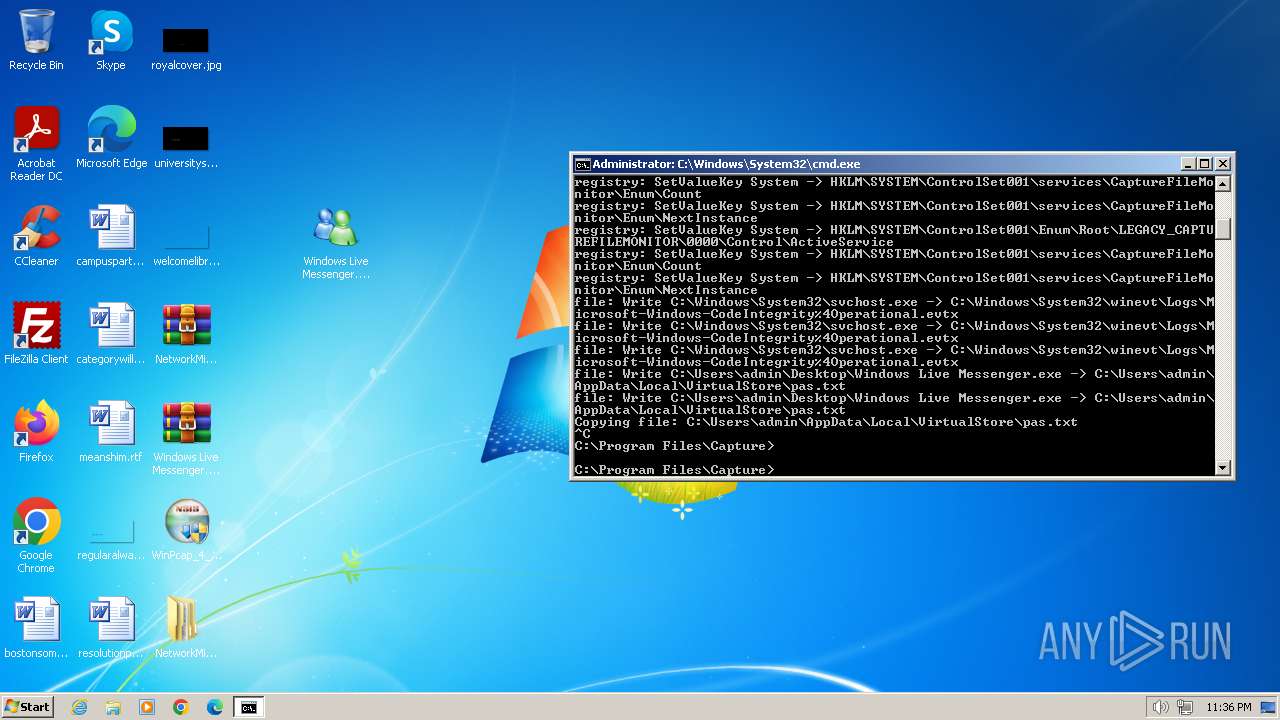
Changes the autorun value in the registry
- rundll32.exe (PID: 2304)
- rundll32.exe (PID: 1440)
Executing a file with an untrusted certificate
- WinPcap_4_1_3.exe (PID: 2492)
- WinPcap_4_1_3.exe (PID: 2368)
Starts NET.EXE for service management
- WinPcap_4_1_3.exe (PID: 2492)
- net.exe (PID: 2532)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1880)
Uses RUNDLL32.EXE to load library
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1880)
Executable content was dropped or overwritten
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1880)
- rundll32.exe (PID: 1440)
- WinPcap_4_1_3.exe (PID: 2492)
Reads the Internet Settings
- runonce.exe (PID: 3168)
- runonce.exe (PID: 3876)
- sipnotify.exe (PID: 1708)
- Windows Live Messenger.exe (PID: 3060)
- NetworkMiner.exe (PID: 2164)
There is functionality for taking screenshot (YARA)
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1880)
Drops a system driver (possible attempt to evade defenses)
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1880)
- rundll32.exe (PID: 1440)
- WinPcap_4_1_3.exe (PID: 2492)
Creates a software uninstall entry
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1880)
- WinPcap_4_1_3.exe (PID: 2492)
The process executes via Task Scheduler
- sipnotify.exe (PID: 1708)
- ctfmon.exe (PID: 1564)
Creates files in the driver directory
- WinPcap_4_1_3.exe (PID: 2492)
Malware-specific behavior (creating "System.dll" in Temp)
- WinPcap_4_1_3.exe (PID: 2492)
Creates or modifies Windows services
- WinPcap_4_1_3.exe (PID: 2492)
The process creates files with name similar to system file names
- WinPcap_4_1_3.exe (PID: 2492)
Reads settings of System Certificates
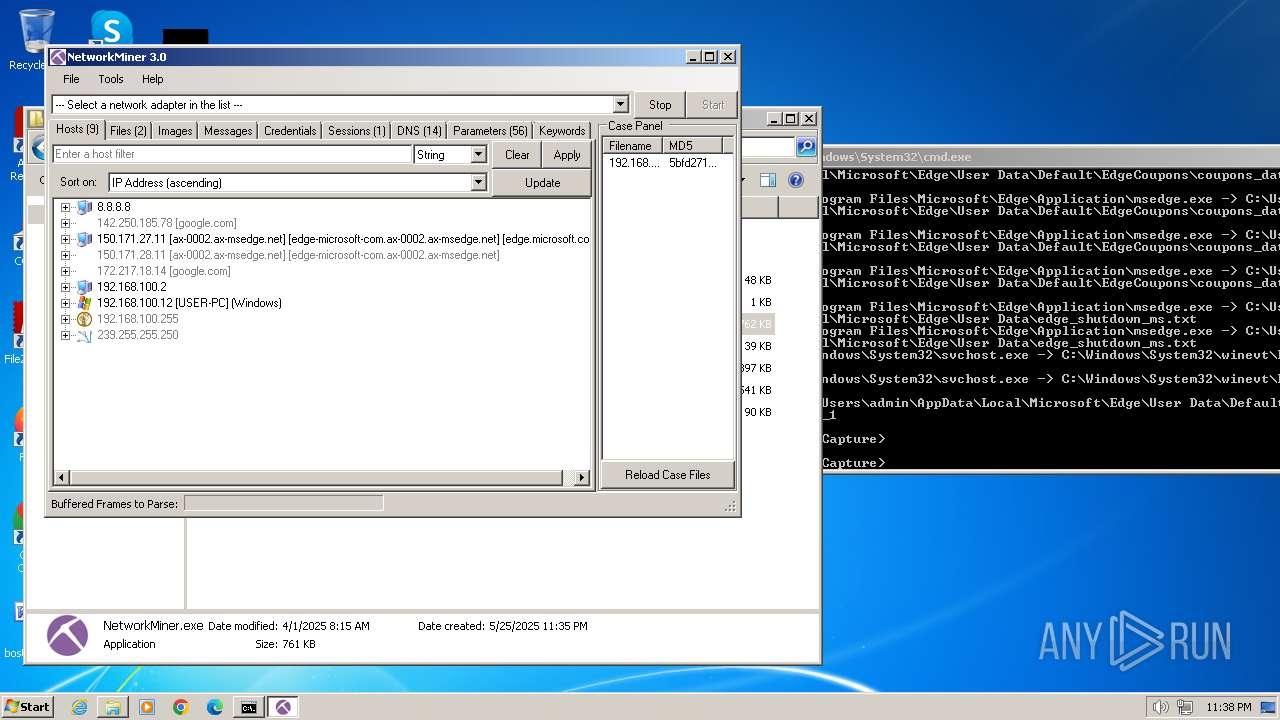
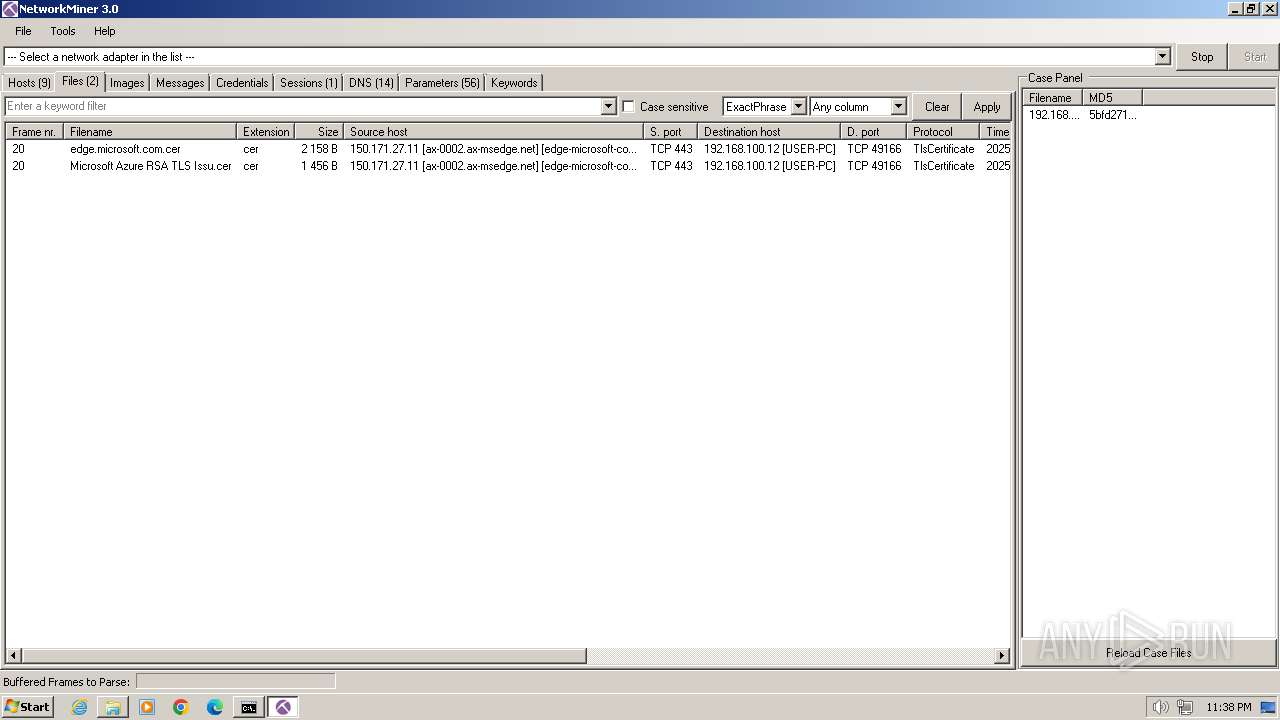
- NetworkMiner.exe (PID: 2164)
INFO
The sample compiled with english language support
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1880)
- WinRAR.exe (PID: 2672)
- WinPcap_4_1_3.exe (PID: 2492)
Reads security settings of Internet Explorer
- runonce.exe (PID: 3168)
- runonce.exe (PID: 3876)
Reads the time zone
- runonce.exe (PID: 3168)
- runonce.exe (PID: 3876)
Creates files in the driver directory
- rundll32.exe (PID: 1440)
Checks supported languages
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1880)
- IMEKLMG.EXE (PID: 1804)
- IMEKLMG.EXE (PID: 364)
- WinPcap_4_1_3.exe (PID: 2492)
- CaptureBAT.exe (PID: 3008)
- Windows Live Messenger.exe (PID: 3060)
- NetworkMiner.exe (PID: 2164)
Reads the computer name
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1880)
- IMEKLMG.EXE (PID: 1804)
- IMEKLMG.EXE (PID: 364)
- CaptureBAT.exe (PID: 3008)
- Windows Live Messenger.exe (PID: 3060)
- NetworkMiner.exe (PID: 2164)
- WinPcap_4_1_3.exe (PID: 2492)
Creates files in the program directory
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1880)
- WinPcap_4_1_3.exe (PID: 2492)
- CaptureBAT.exe (PID: 3008)
Manual execution by a user
- IMEKLMG.EXE (PID: 364)
- IMEKLMG.EXE (PID: 1804)
- WinPcap_4_1_3.exe (PID: 2492)
- WinPcap_4_1_3.exe (PID: 2368)
- WinRAR.exe (PID: 2604)
- WinRAR.exe (PID: 2672)
- cmd.exe (PID: 2968)
- Windows Live Messenger.exe (PID: 3060)
- NetworkMiner.exe (PID: 2164)
- Windows Live Messenger.exe (PID: 2892)
- NetworkMiner.exe (PID: 3424)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 364)
- IMEKLMG.EXE (PID: 1804)
Reads Environment values
- WinPcap_4_1_3.exe (PID: 2492)
- NetworkMiner.exe (PID: 2164)
Create files in a temporary directory
- WinPcap_4_1_3.exe (PID: 2492)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2604)
- WinRAR.exe (PID: 2672)
Creates files or folders in the user directory
- Windows Live Messenger.exe (PID: 3060)
- NetworkMiner.exe (PID: 2164)
Application launched itself
- msedge.exe (PID: 3152)
- msedge.exe (PID: 2900)
Reads the machine GUID from the registry
- NetworkMiner.exe (PID: 2164)
Disables trace logs
- NetworkMiner.exe (PID: 2164)
Reads the software policy settings
- NetworkMiner.exe (PID: 2164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:07:14 15:12:54+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 23552 |
| InitializedDataSize: | 164864 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30fb |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
143
Monitored processes
49
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 336 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1544 --field-trial-handle=1244,i,4618387542822858213,14132176267889730521,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 | ||||
| 364 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 | ||||
| 372 | "C:\Users\admin\AppData\Local\Temp\CaptureBAT-Setup-2.0.0-5574.exe" | C:\Users\admin\AppData\Local\Temp\CaptureBAT-Setup-2.0.0-5574.exe | — | explorer.exe |
User: admin Integrity Level: MEDIUM Exit code: 3221226540 | ||||
| 1440 | rundll32 setupapi.dll,InstallHinfSection DefaultInstall 0 C:\Program Files\Capture\FileMonitorInstallation.inf | C:\Windows\System32\rundll32.exe | CaptureBAT-Setup-2.0.0-5574.exe | |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 1564 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 1572 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1180 --field-trial-handle=1244,i,4618387542822858213,14132176267889730521,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 | ||||
| 1708 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) | ||||
| 1804 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 | ||||
| 1880 | "C:\Users\admin\AppData\Local\Temp\CaptureBAT-Setup-2.0.0-5574.exe" | C:\Users\admin\AppData\Local\Temp\CaptureBAT-Setup-2.0.0-5574.exe | explorer.exe | |
User: admin Integrity Level: HIGH Exit code: 2 | ||||
| 1996 | "C:\Windows\System32\grpconv.exe" -o | C:\Windows\System32\grpconv.exe | — | runonce.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
27
Suspicious files
98
Text files
130
Unknown types
0
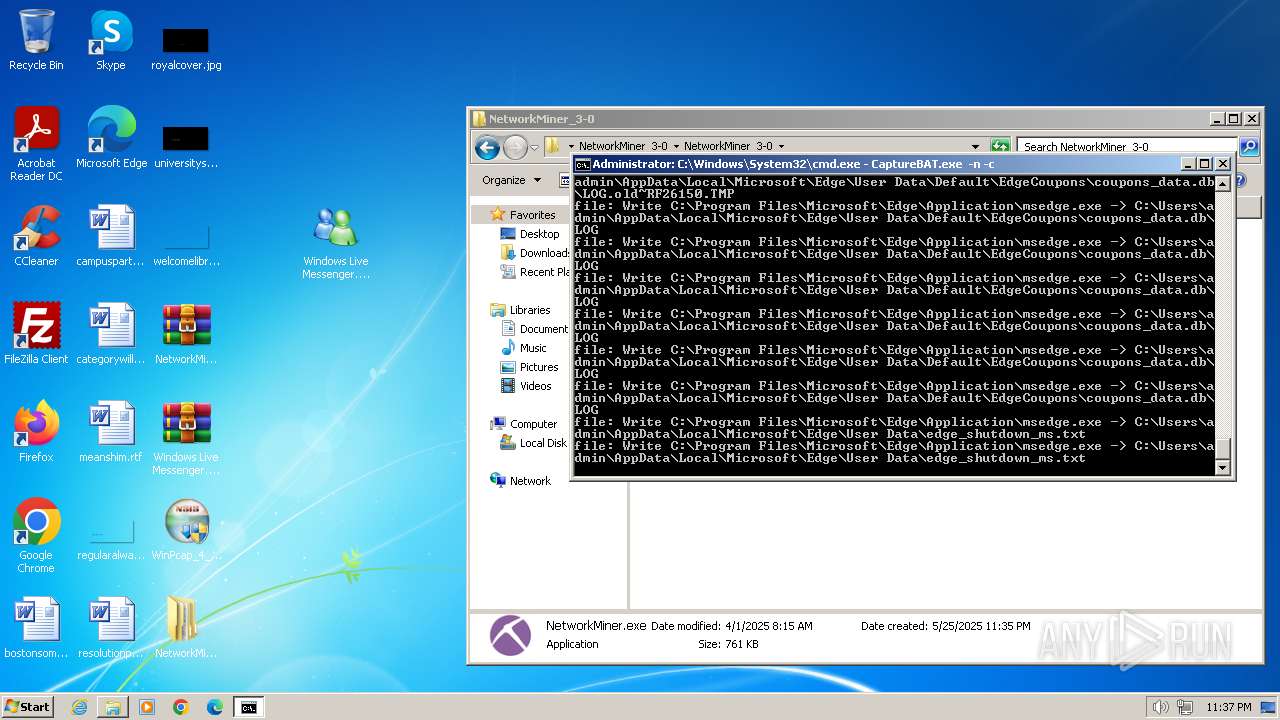
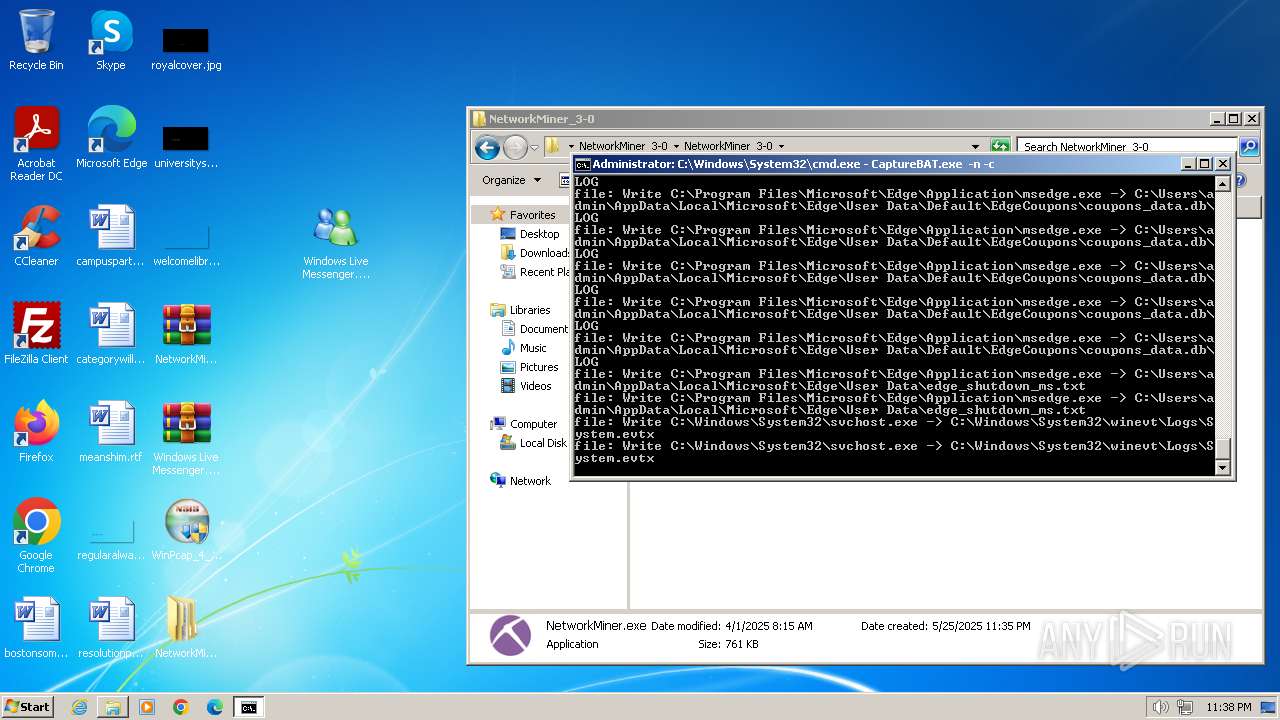
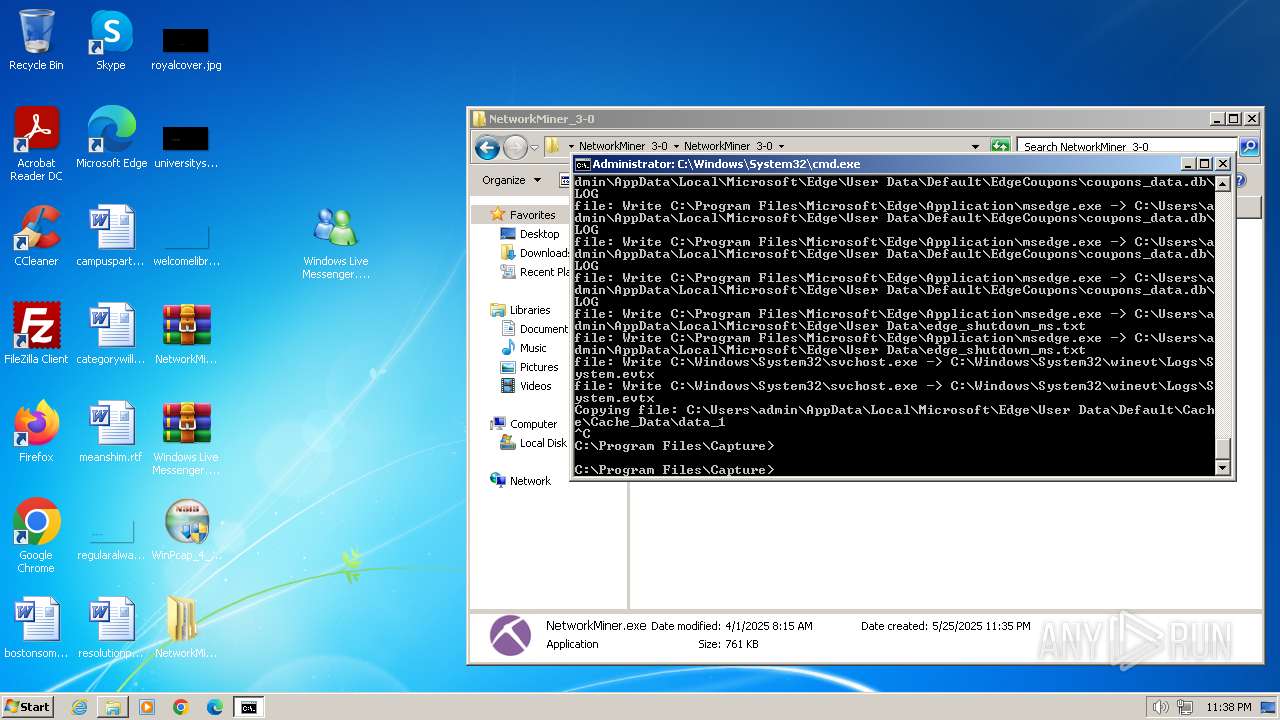
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1880 | CaptureBAT-Setup-2.0.0-5574.exe | C:\Program Files\Capture\7za.exe | executable | |
MD5:885E9EB42889CA547F4E3515DCDE5D3D | SHA256:B3A70D388488C34DD5C767692ECCC9EFFED36B8E7C1EE03ACE1BD27123A2E6D6 | |||
| 1880 | CaptureBAT-Setup-2.0.0-5574.exe | C:\Program Files\Capture\COPYING | text | |
MD5:751419260AA954499F7ABAABAA882BBE | SHA256:AB15FD526BD8DD18A9E77EBC139656BF4D33E97FC7238CD11BF60E2B9B8666C6 | |||
| 2304 | rundll32.exe | C:\Windows\inf\setupapi.app.log | text | |
MD5:CD749F2C8CD9AFF005ED522E34D9520E | SHA256:9F398F5D8DB471252403315327788D85F76810A0E9D9AC4C195F38CB67523366 | |||
| 1708 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\default.cab | compressed | |
MD5:340674F6A3D1562E28A011EC11E40D83 | SHA256:259880E2346D986ABEED46AA9C2917C53E969AAE6927F2CA0A2AD0967736DF98 | |||
| 1880 | CaptureBAT-Setup-2.0.0-5574.exe | C:\Program Files\Capture\FileMonitorInstallation.inf | binary | |
MD5:C2D8DFE752F2257DC12B983B82558566 | SHA256:219ABB4A859D8E62EFFC584BFE113D373C9FF471EA893B97449952E38C816270 | |||
| 1708 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\metadata.json | binary | |
MD5:253EDC8EC7674BD78293FF3B21866074 | SHA256:51C3A033F0160A30C1773F1E5A9CD01AB018B151EDA1BB64D0226B2437106A56 | |||
| 1880 | CaptureBAT-Setup-2.0.0-5574.exe | C:\Program Files\Capture\ProcessMonitor.exl | text | |
MD5:2EC9BE16BEEAC6AFAA115B2A9EEC5258 | SHA256:E91BB5871E840777B45691643105F6F015A9ADFF215EA7F82287148D451B71AE | |||
| 1880 | CaptureBAT-Setup-2.0.0-5574.exe | C:\Program Files\Capture\uninstall.exe | executable | |
MD5:D06A2E10BC637688F8A518640A181380 | SHA256:6EDE5A98855BD5694A363C9AF38FCD323208CFC88B9A0640ECE0F454BCB7889B | |||
| 1880 | CaptureBAT-Setup-2.0.0-5574.exe | C:\Program Files\Capture\CaptureFileMonitor.sys | executable | |
MD5:D70F8AFF620E1203C45680DC827A6B3E | SHA256:B2E6F2062B2F81CD0F3E1F2503F387AE824A84A8DD77ED55CF92DA03FDEEC130 | |||
| 3168 | runonce.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Explorer\ExplorerStartupLog_RunOnce.etl | binary | |
MD5:99A27E51DE23FC29B131FE125798C927 | SHA256:268E2E5FF2E47CC777A884327D933841E05C73E6AE522E65F2BC811FB892DDB5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
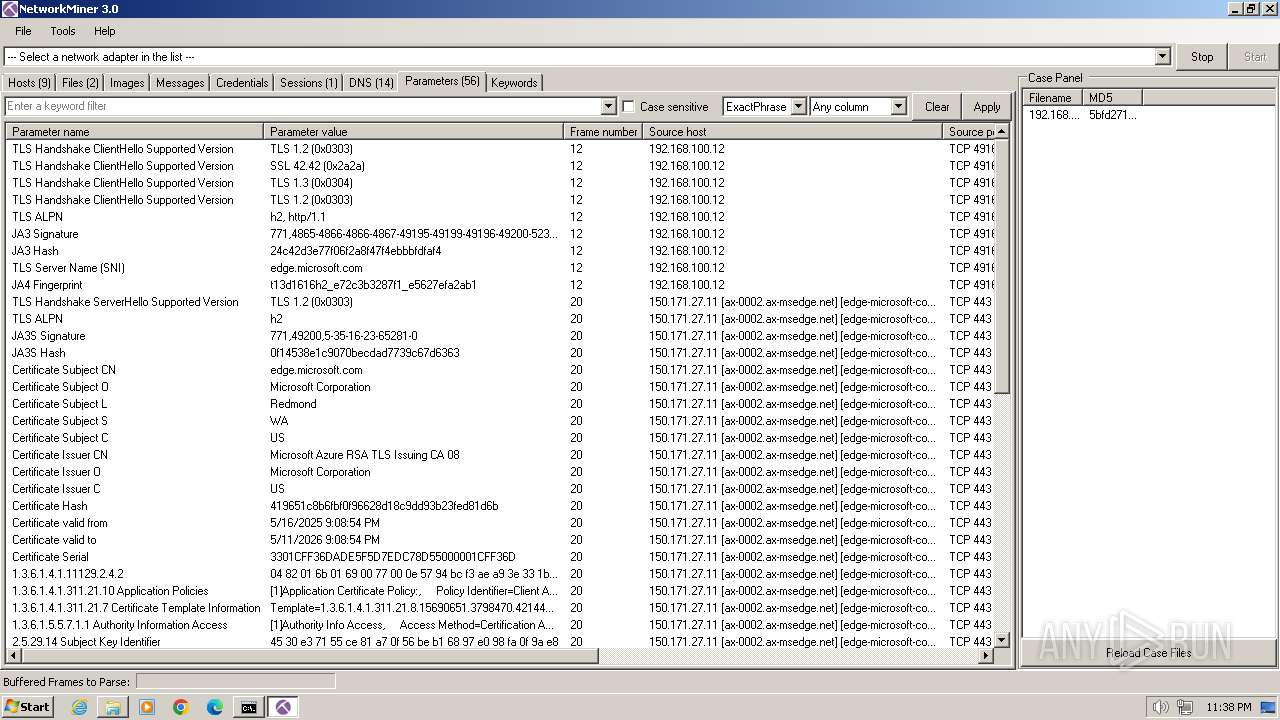
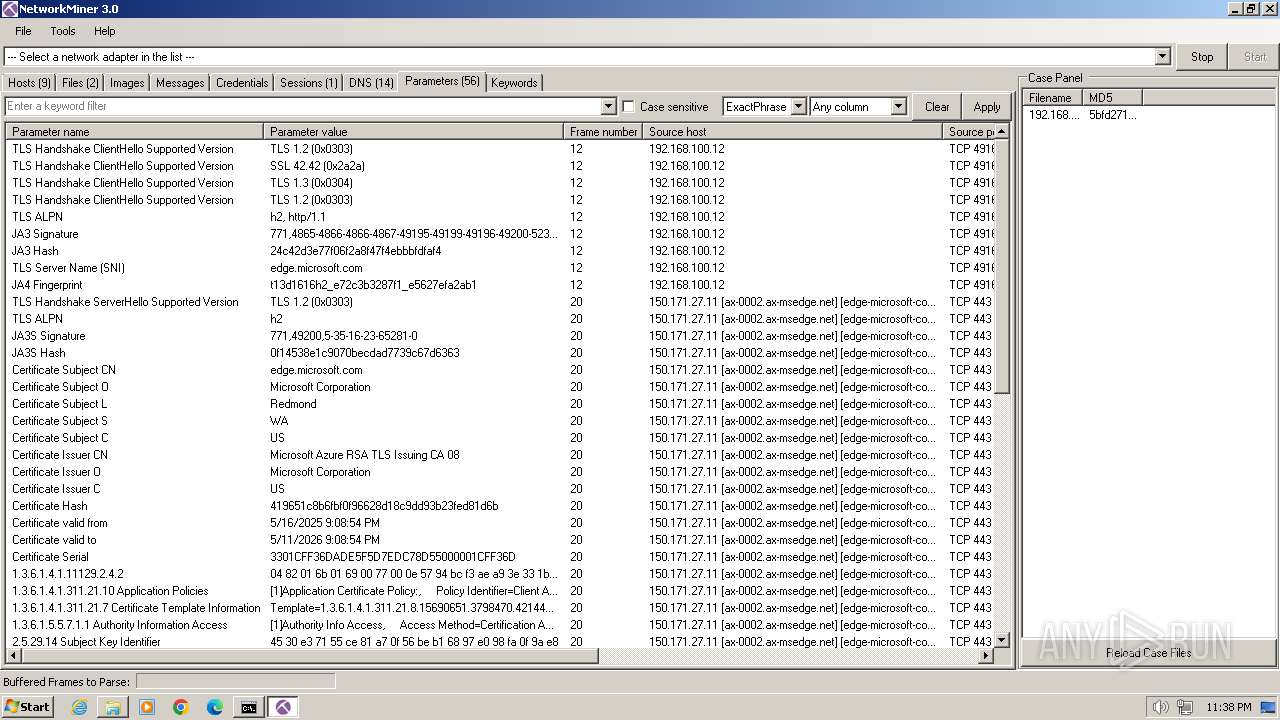
HTTP(S) requests
1
TCP/UDP connections
21
DNS requests
32
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1708 | sipnotify.exe | HEAD | 503 | 23.67.143.243:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133926897318590000 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
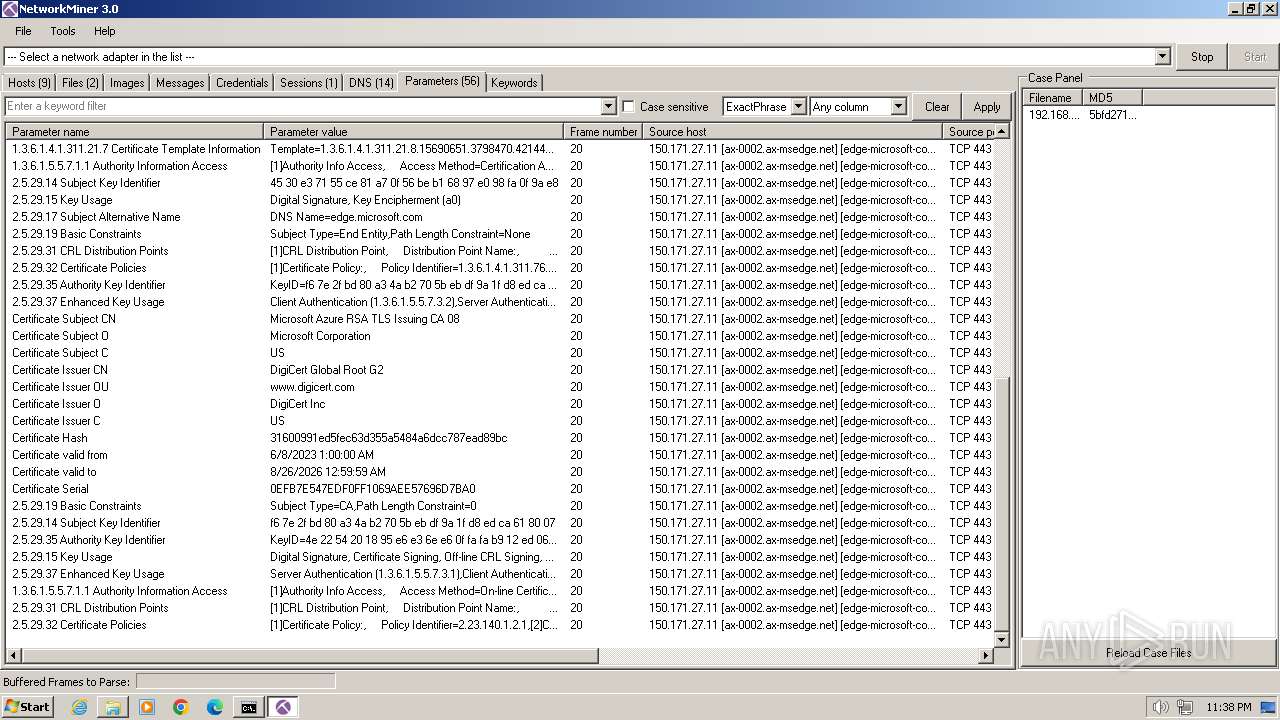
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1708 | sipnotify.exe | 23.67.143.243:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | DE | whitelisted |
1112 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
3152 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3336 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3336 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3152 | msedge.exe | 224.0.0.251:5353 | — | — | — | unknown |
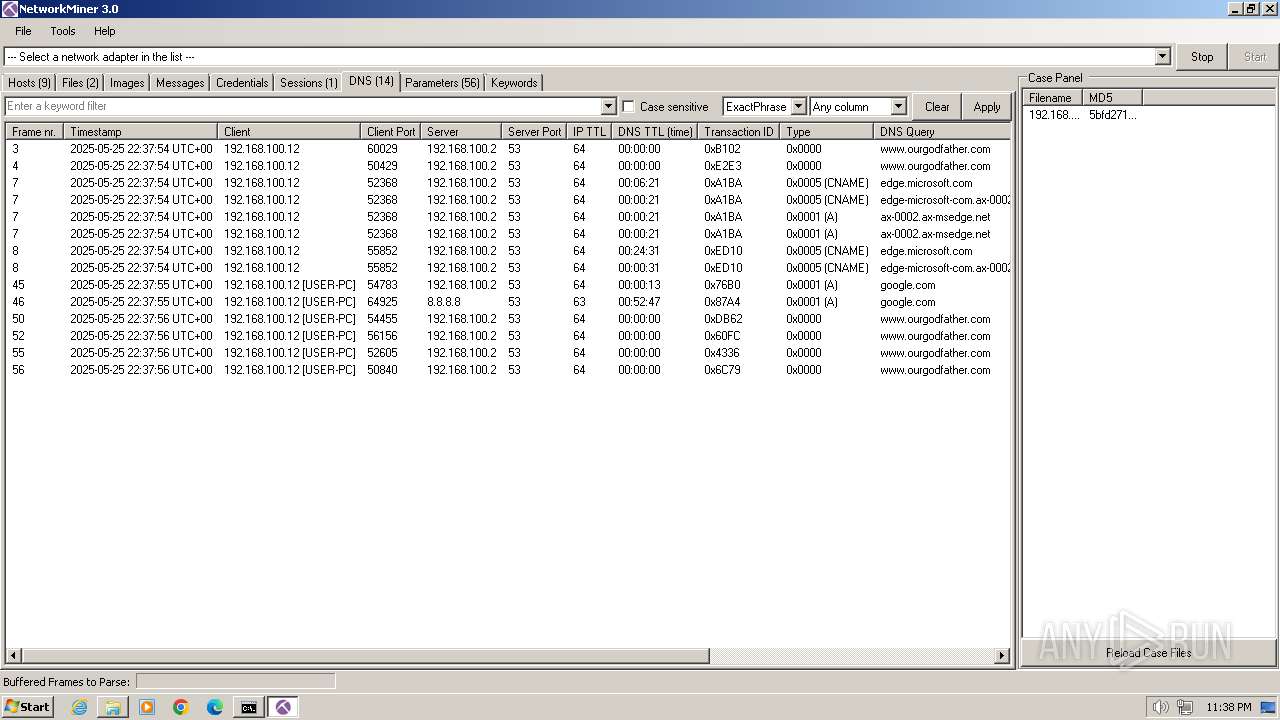
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
query.prod.cms.rt.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
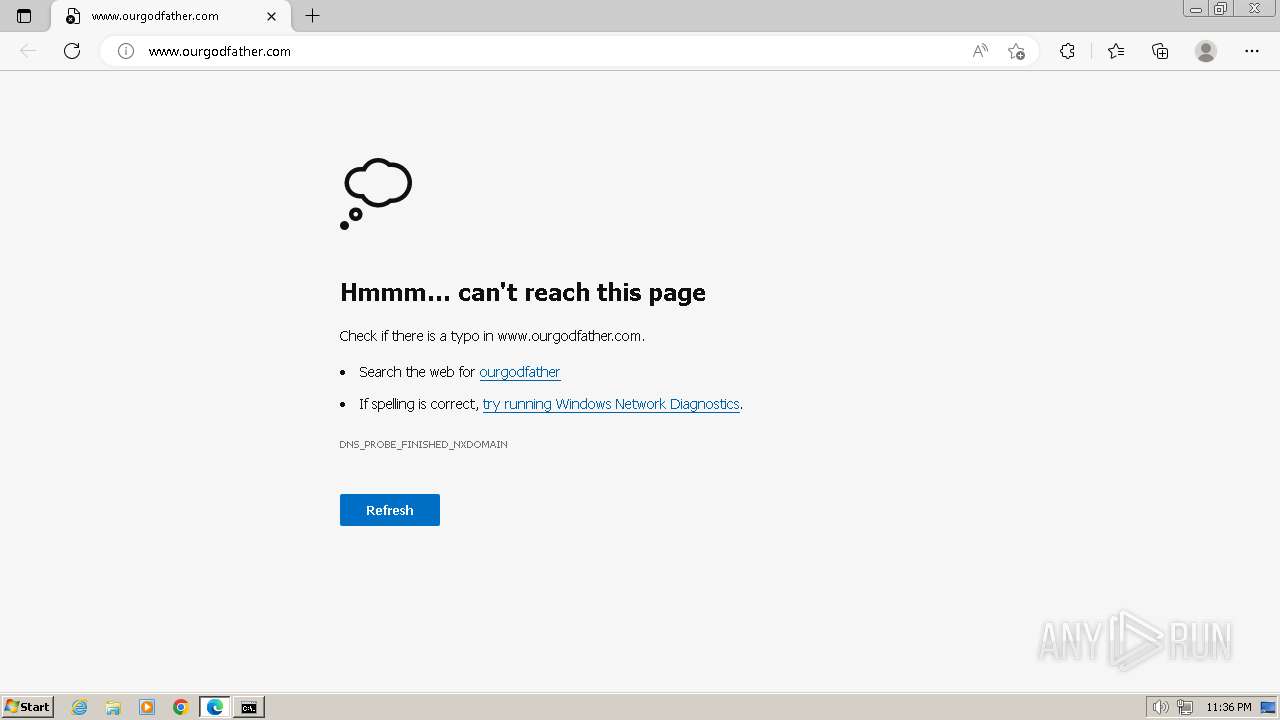
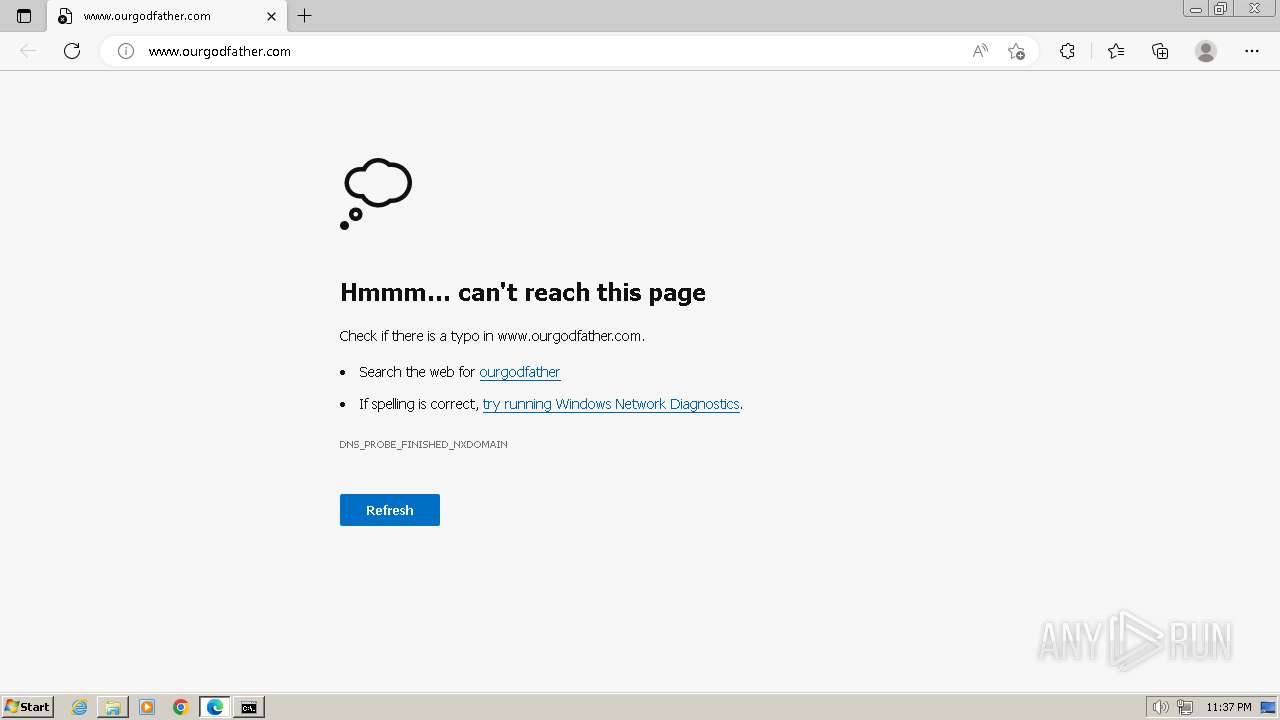
www.ourgodfather.com |
| unknown |
www.bing.com |
| whitelisted |
www.netresec.com |
| unknown |