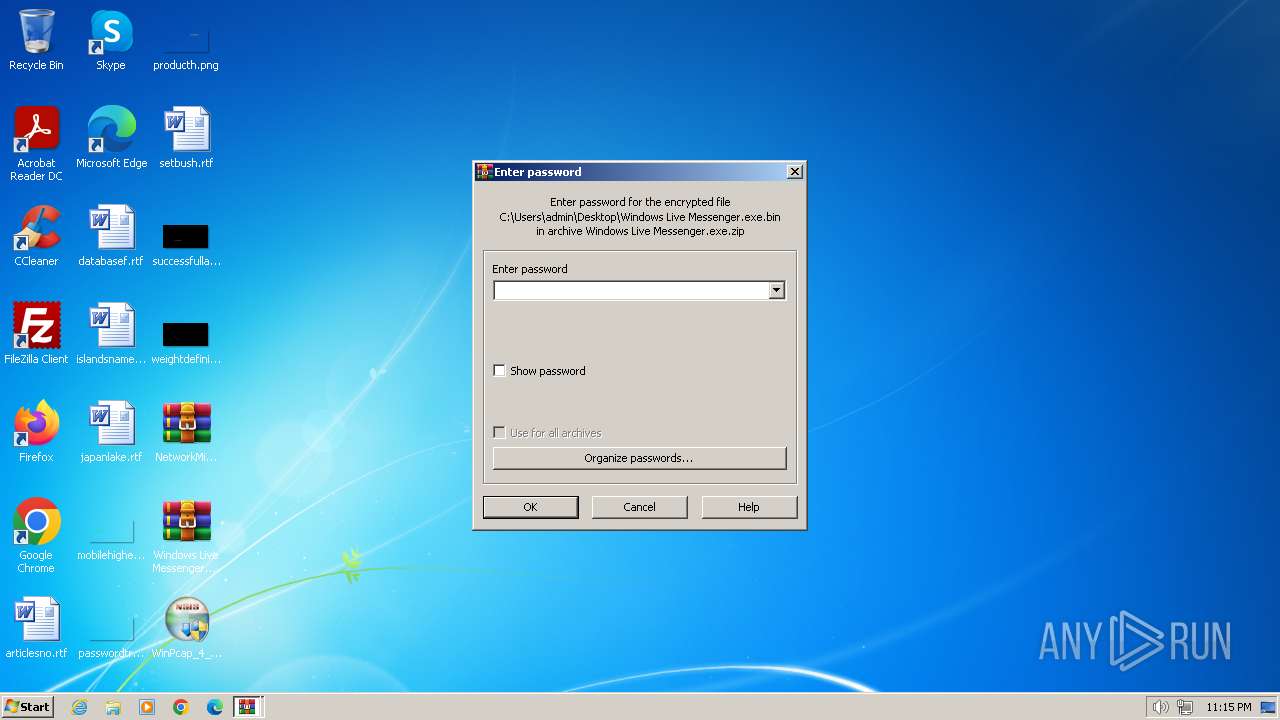
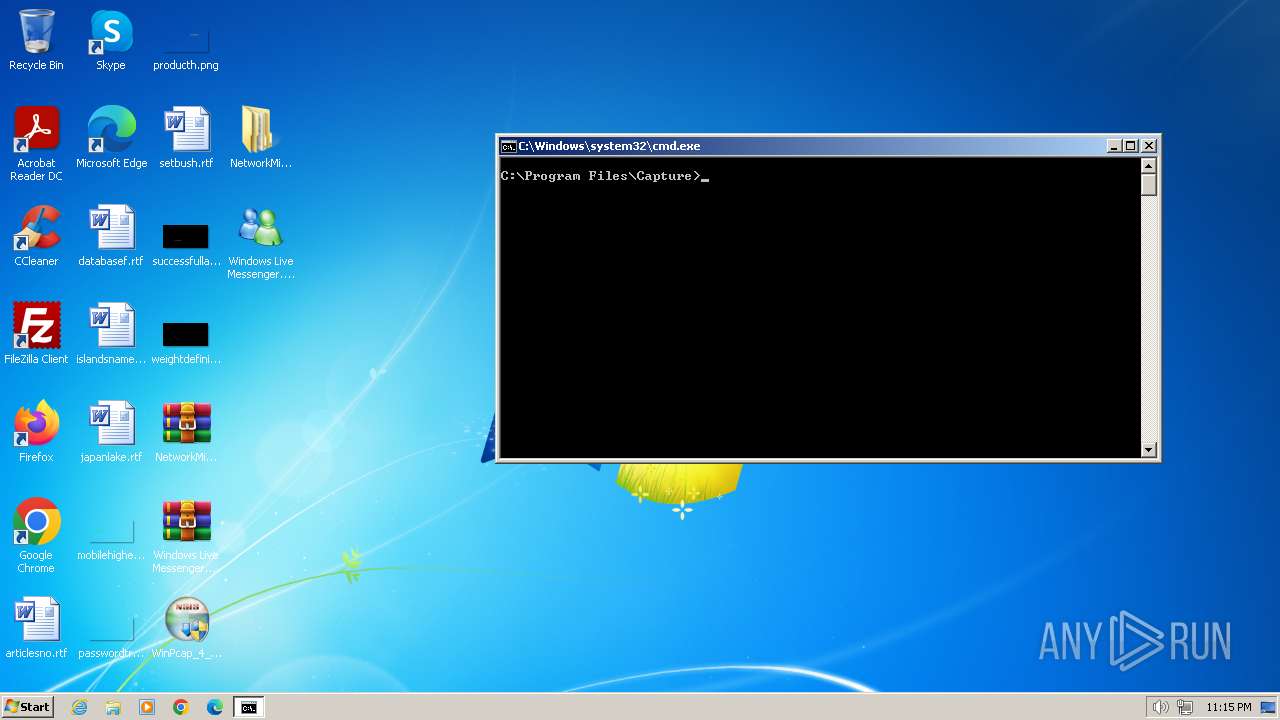
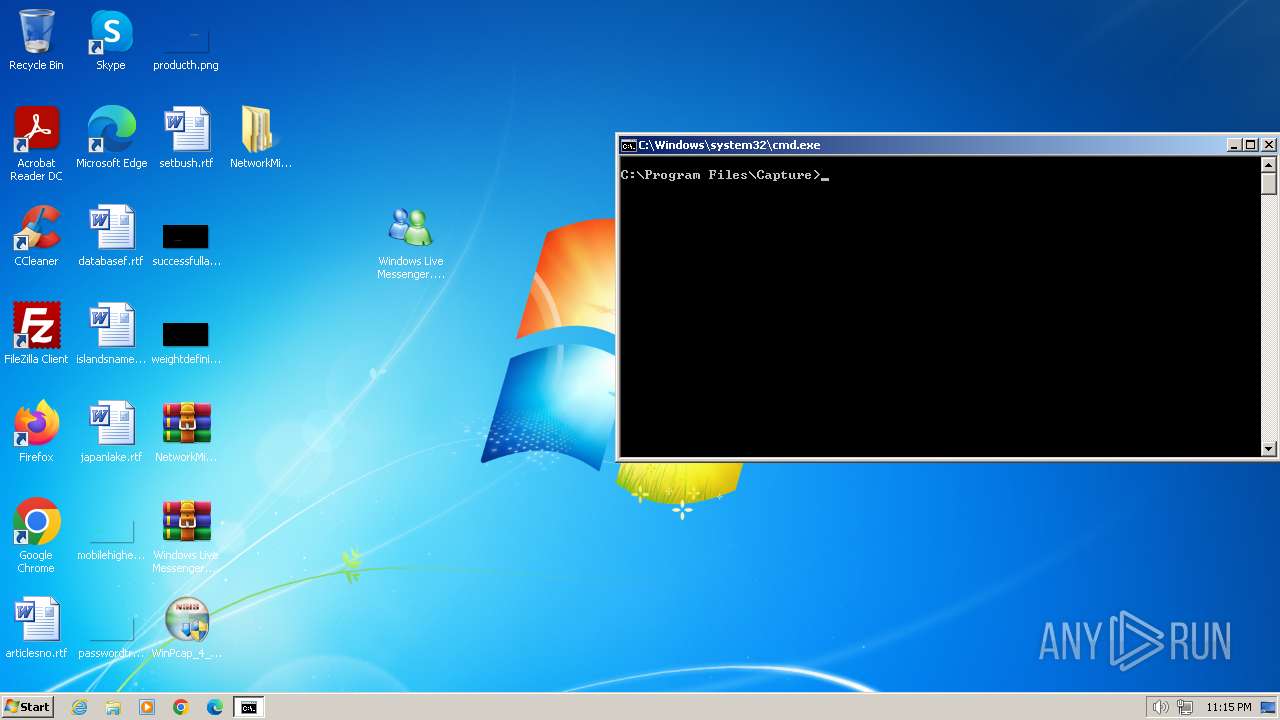
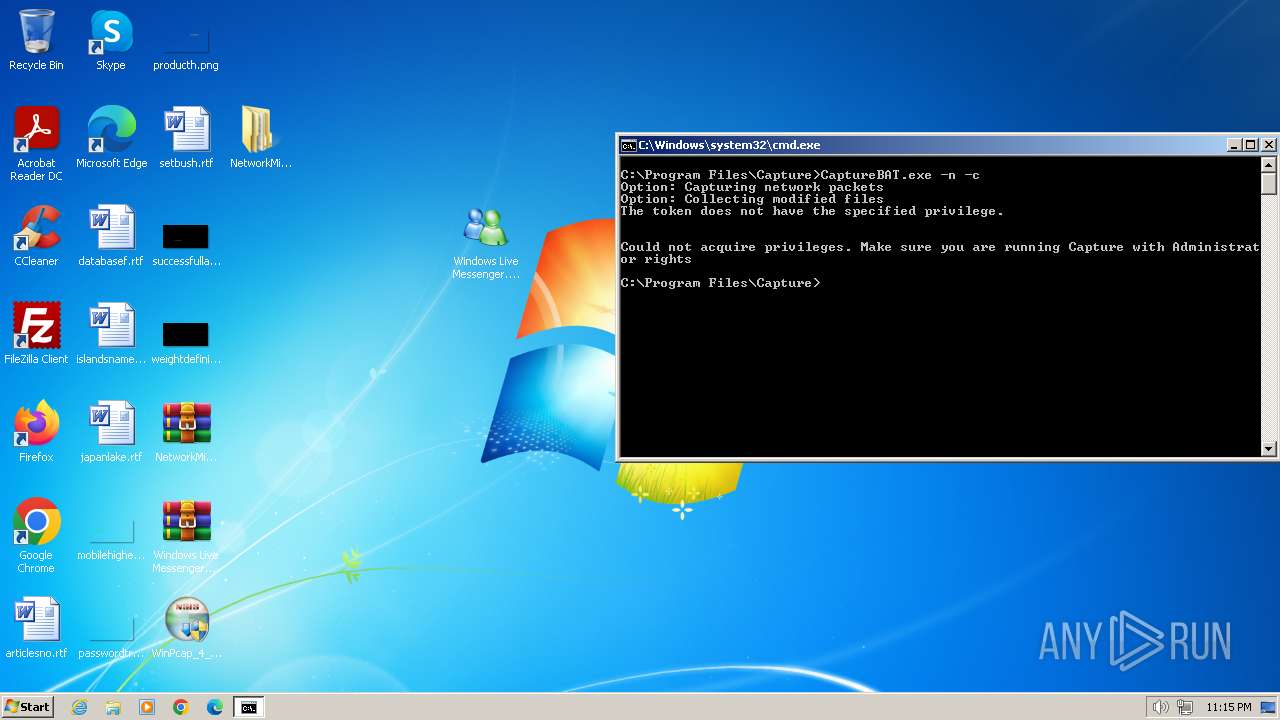
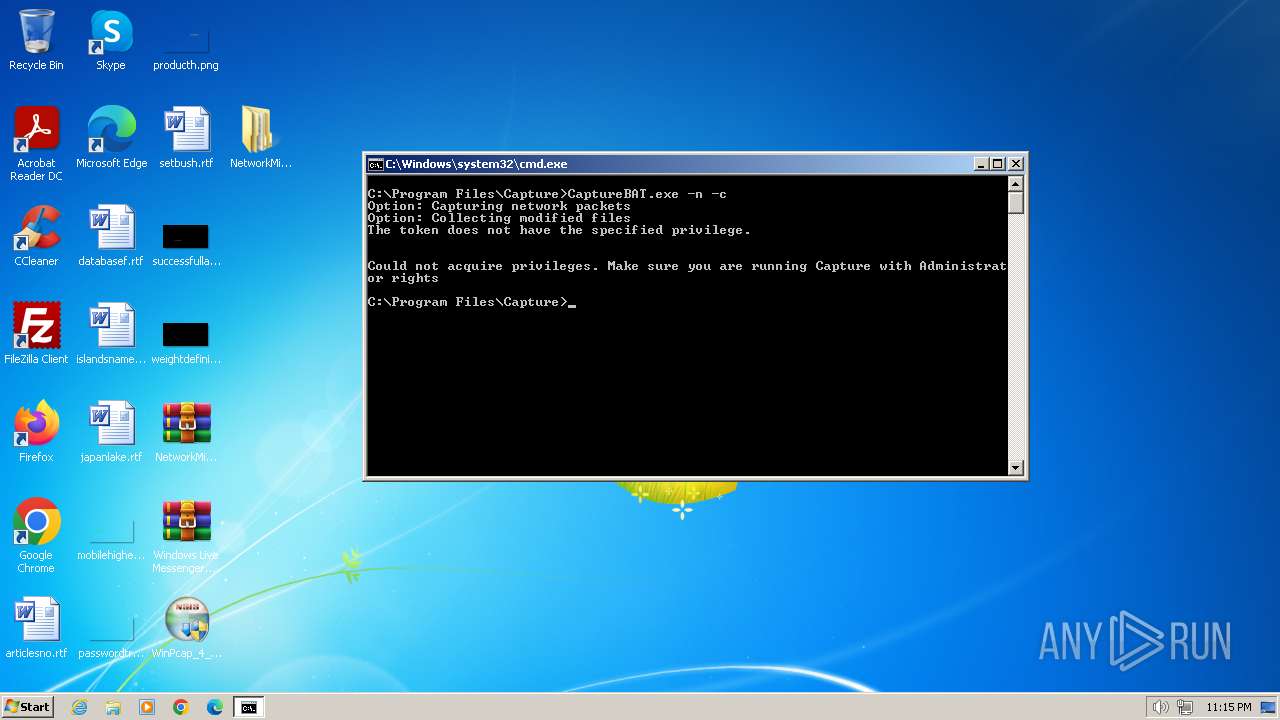
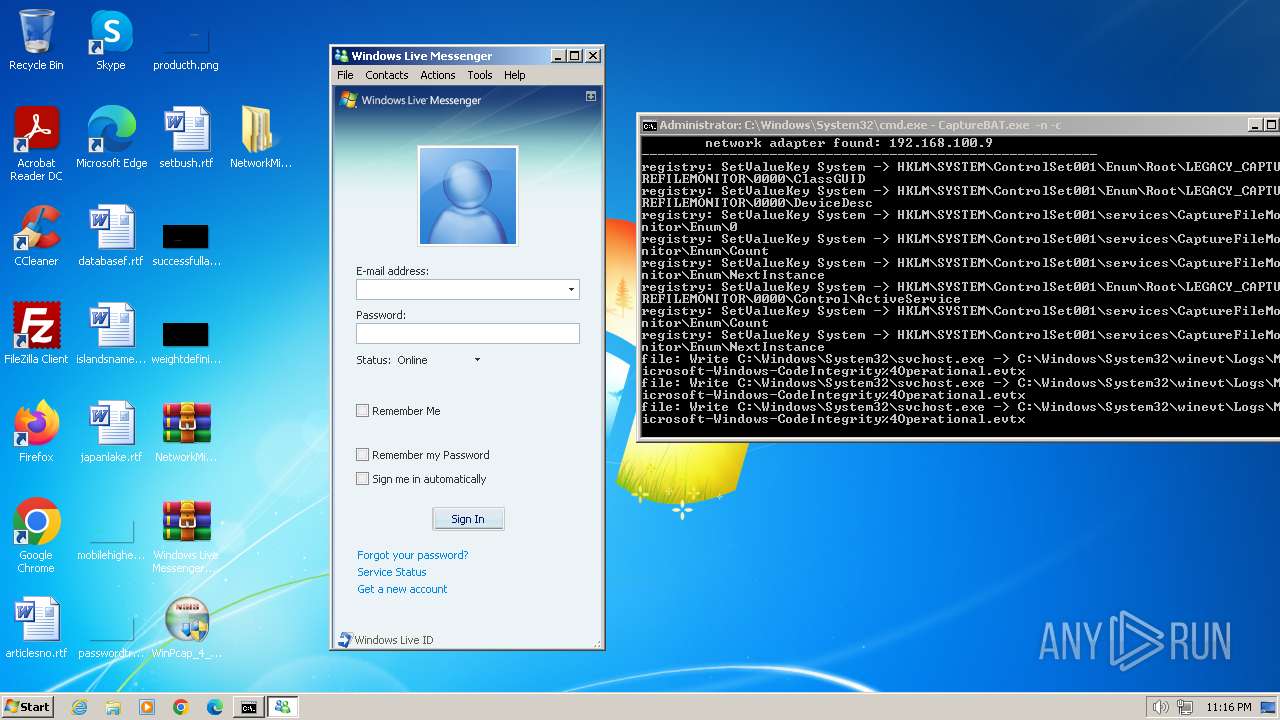
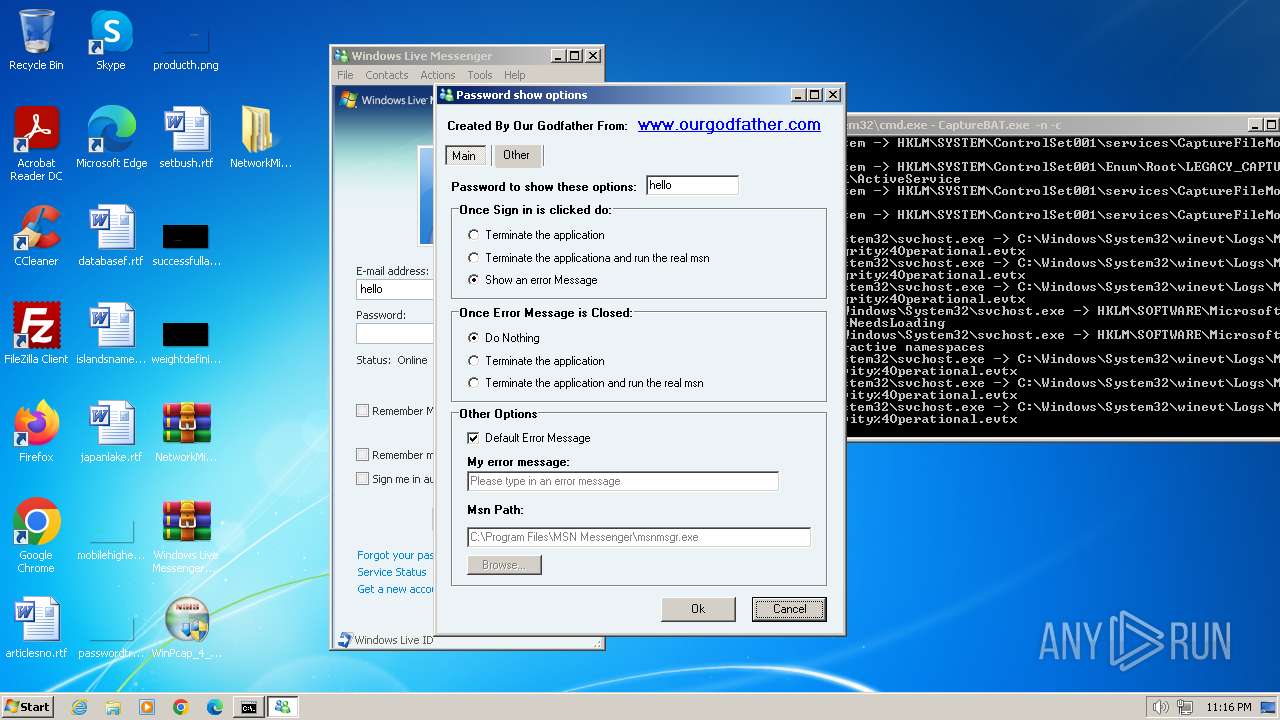
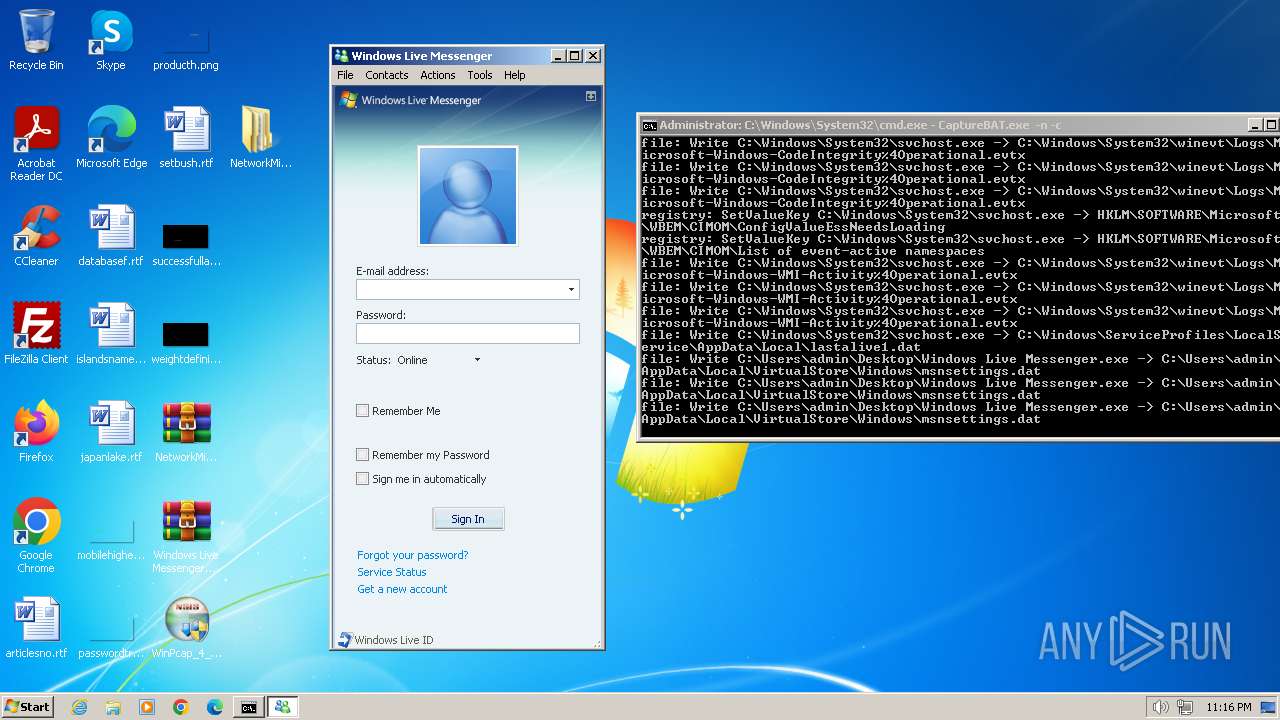
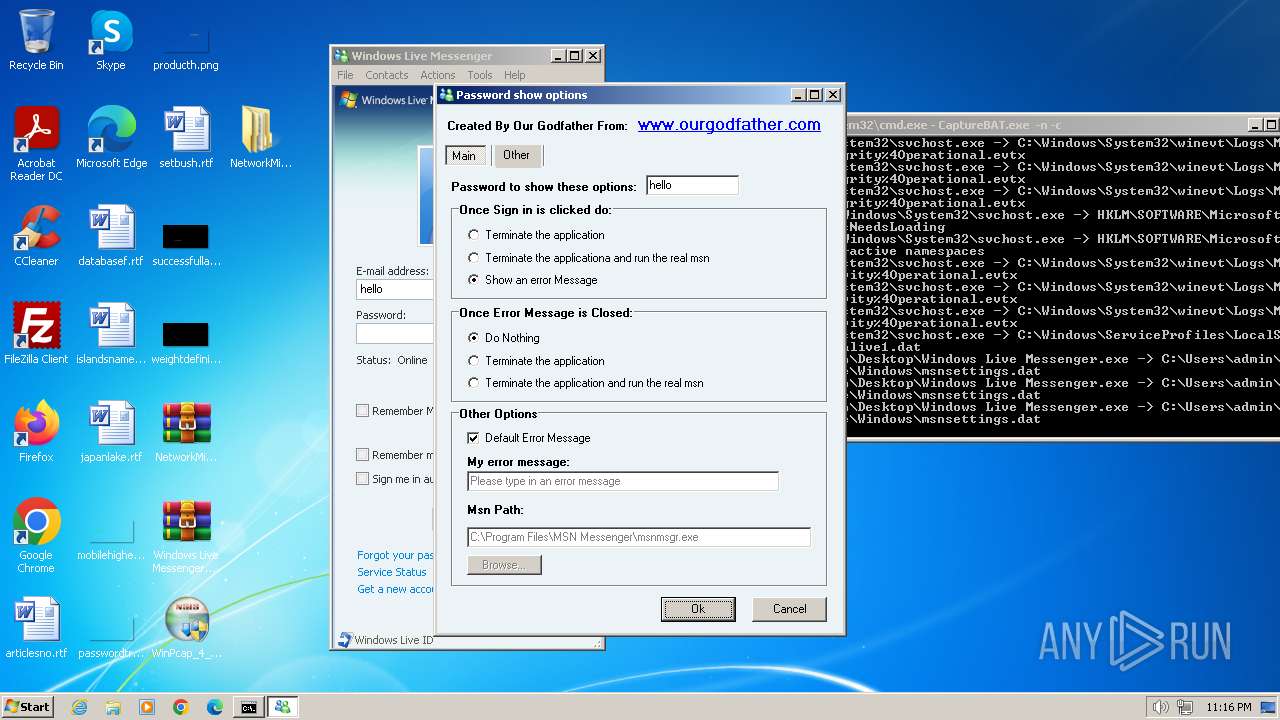
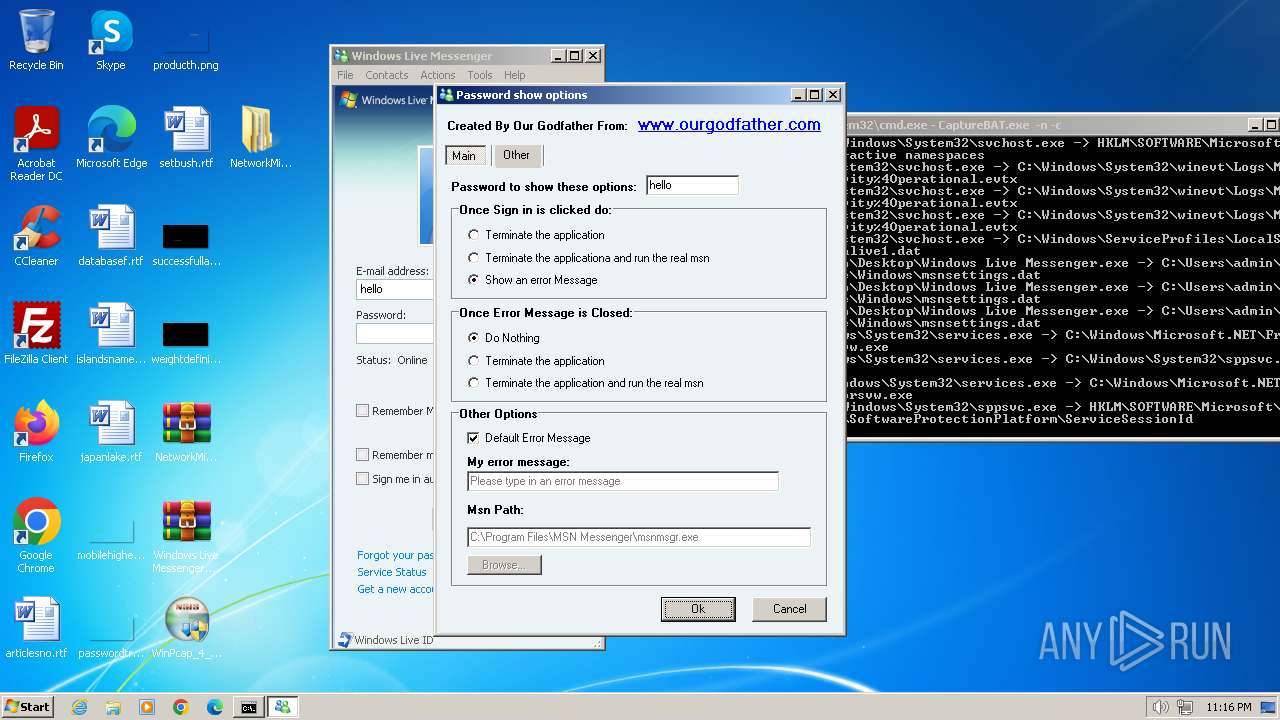
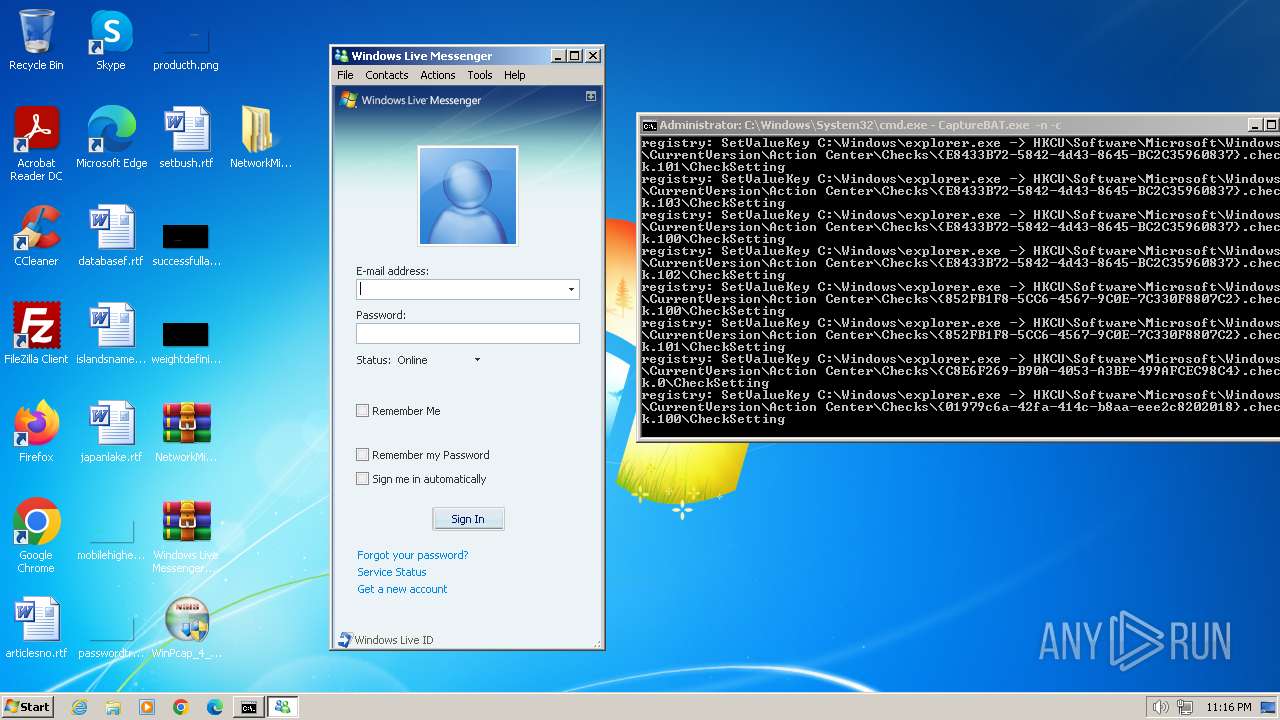
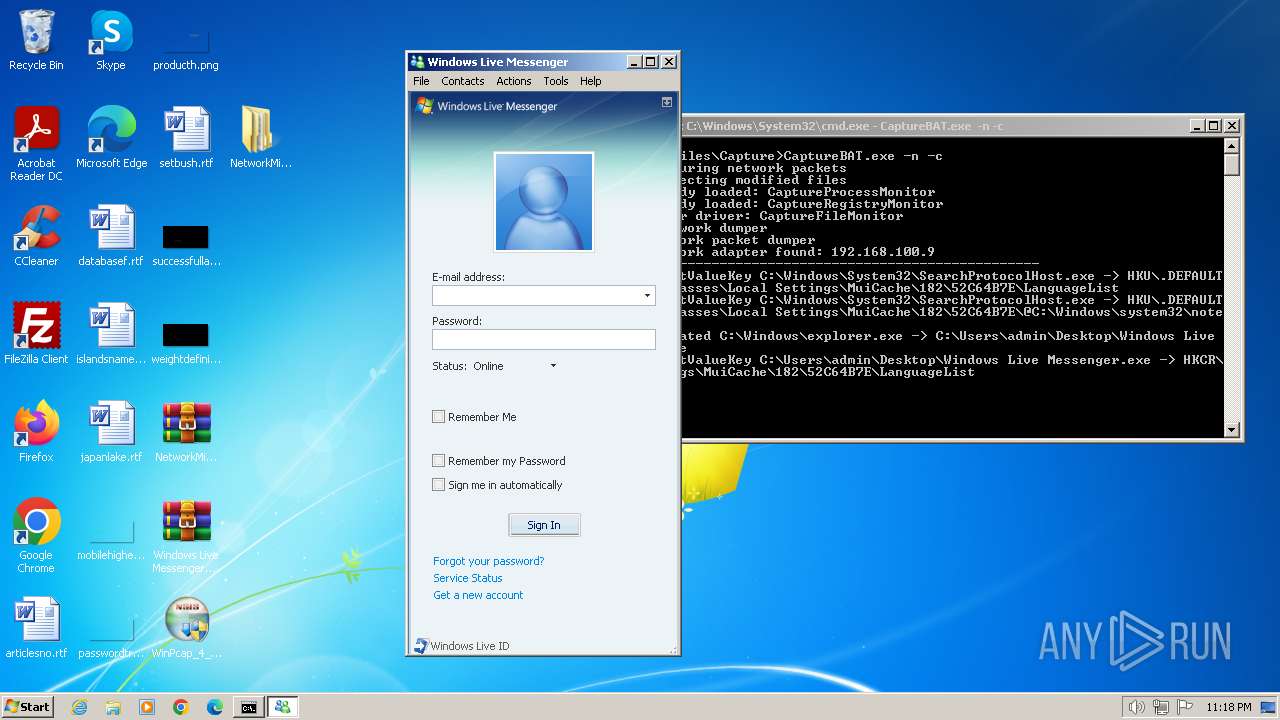
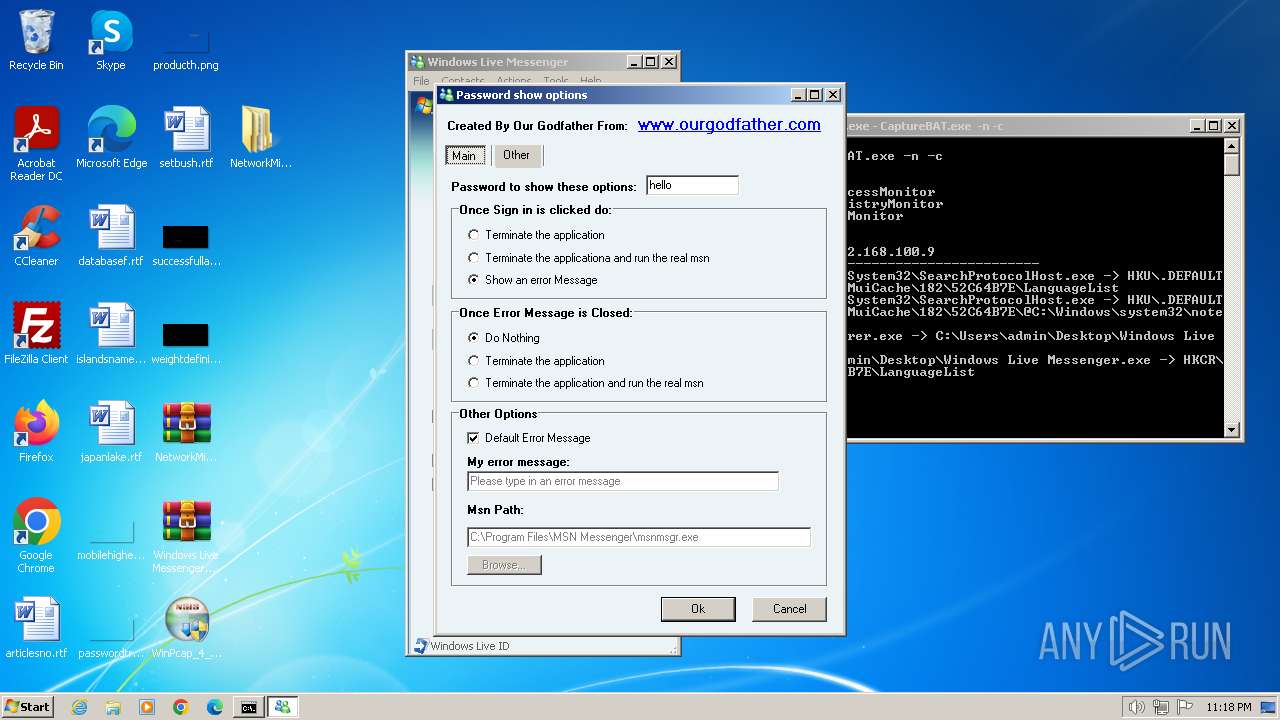
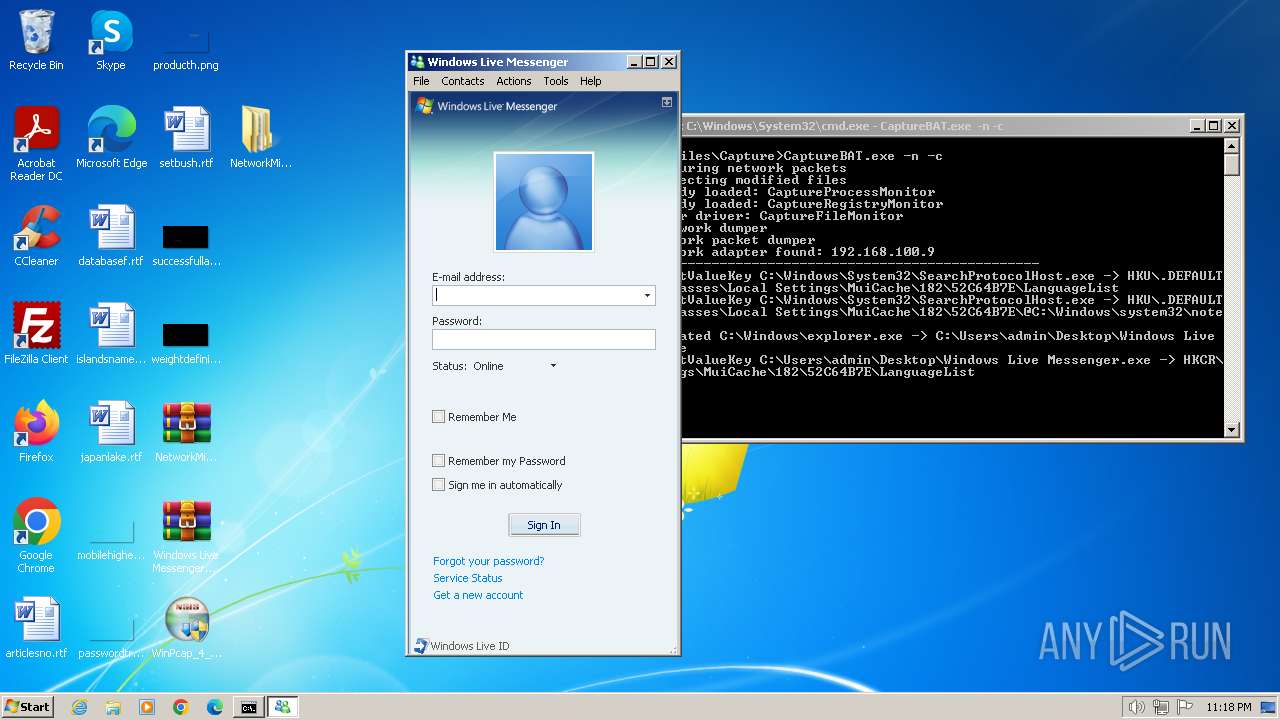
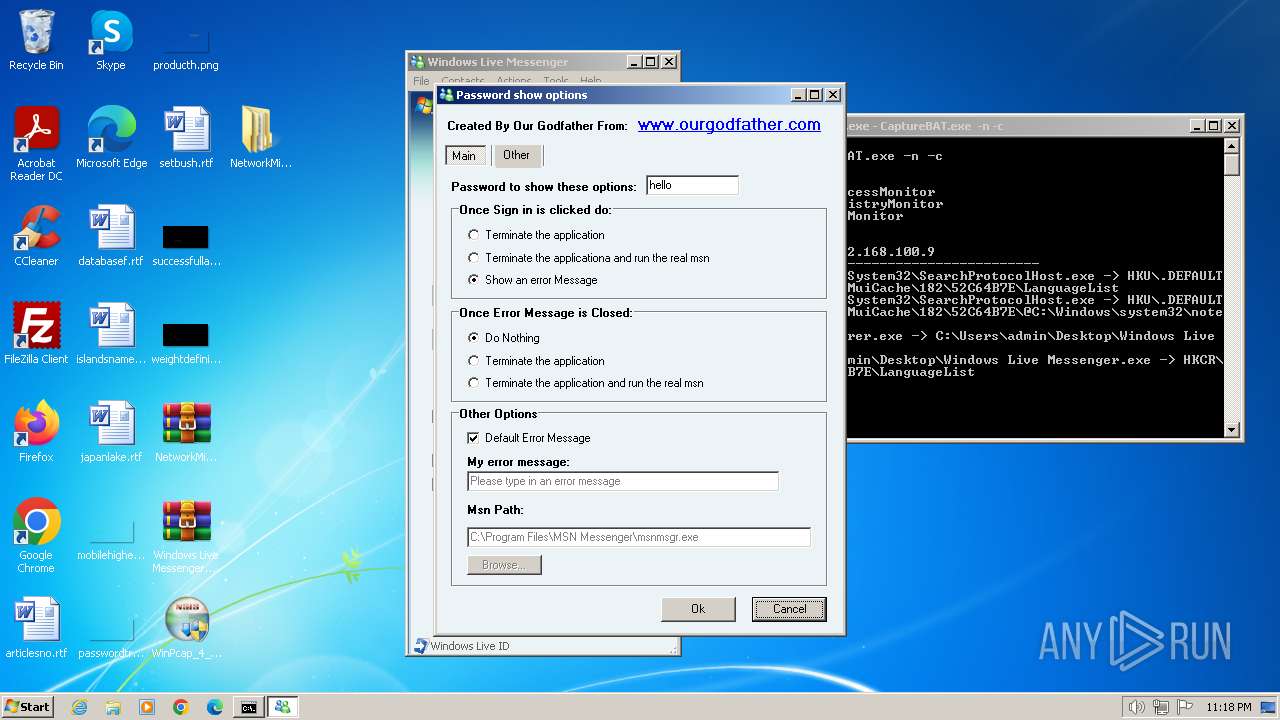
| File name: | CaptureBAT-Setup-2.0.0-5574.exe |
| Full analysis: | https://app.any.run/tasks/774478f5-a070-46b9-973f-73e1e98b09a4 |
| Verdict: | Malicious activity |
| Analysis date: | May 25, 2025, 22:14:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | C1894E46FFE89BE6CA35729D9DAB6145 |
| SHA1: | C507C1FEA3C550DC32D4B0238DF47115AB4CD8DE |
| SHA256: | C91E50A921F07EB7CE510441761DAF38F3E4E6340CF9FAF67E660A3D13BD88E8 |
| SSDEEP: | 24576:B4cDmEFhnydPdXKdNtxqD8gXdP0zUlsFXZRRh6:B4cDmEFhydPdXKdNtxqD8gXdMzUls5Zg |
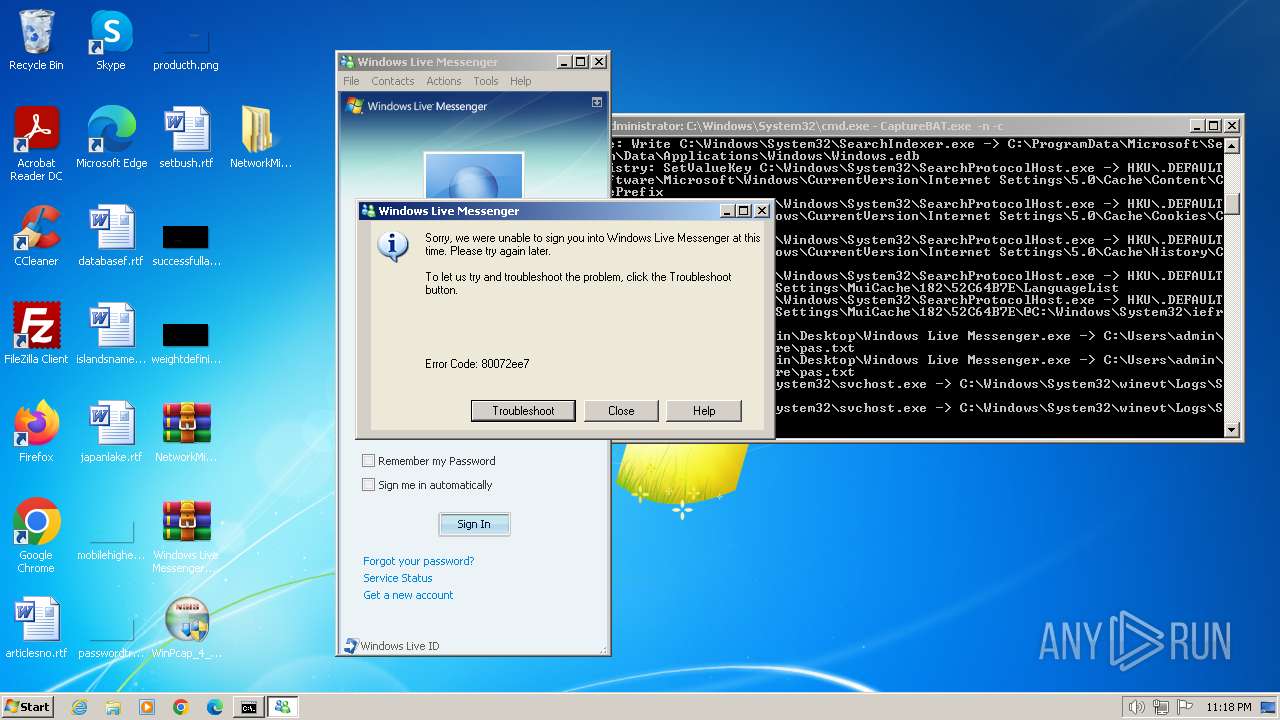
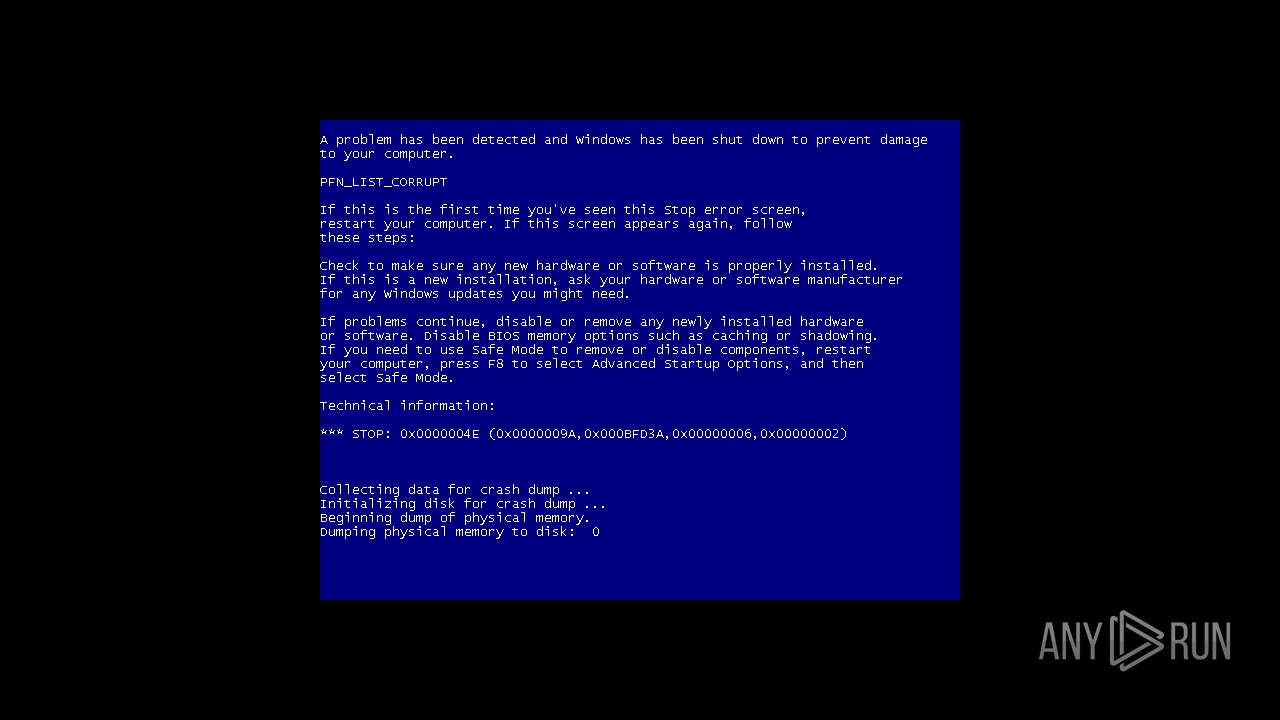
MALICIOUS
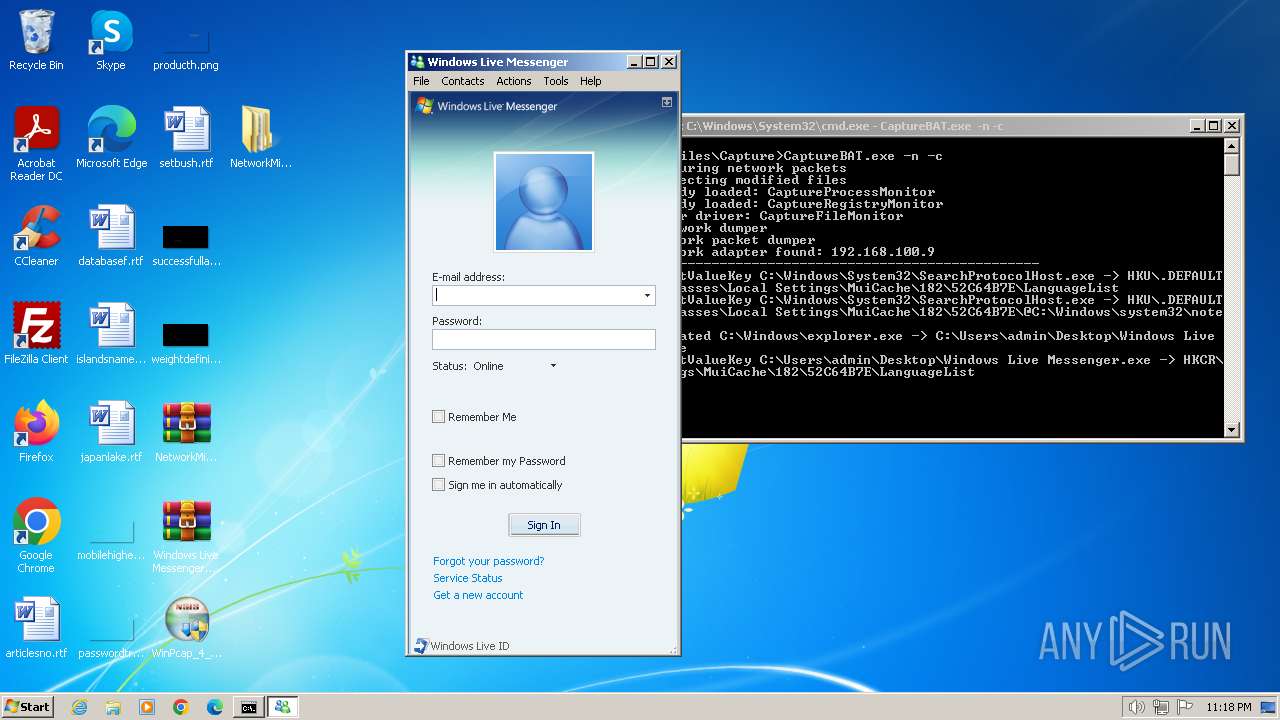
Changes the autorun value in the registry
- rundll32.exe (PID: 1844)
- rundll32.exe (PID: 3432)
Executing a file with an untrusted certificate
- WinPcap_4_1_3.exe (PID: 2624)
- WinPcap_4_1_3.exe (PID: 2512)
Starts NET.EXE for service management
- WinPcap_4_1_3.exe (PID: 2624)
- net.exe (PID: 2668)
SUSPICIOUS
Executable content was dropped or overwritten
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1032)
- rundll32.exe (PID: 3432)
- WinPcap_4_1_3.exe (PID: 2624)
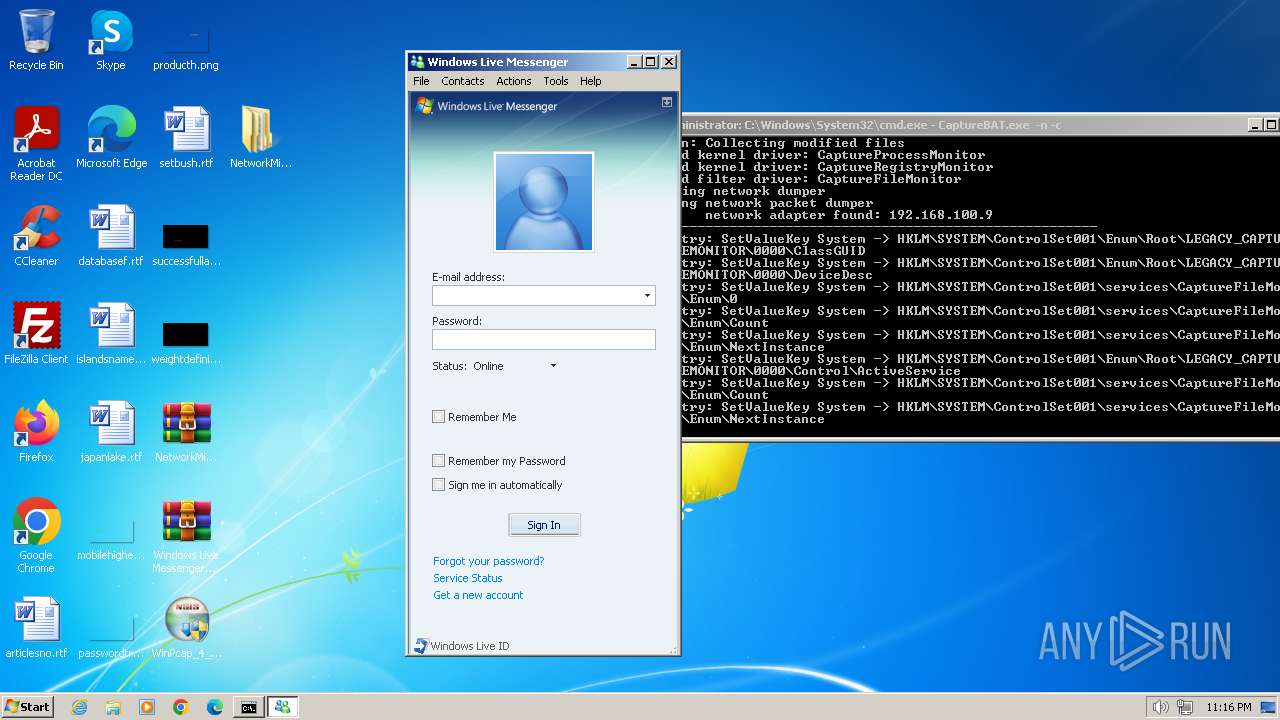
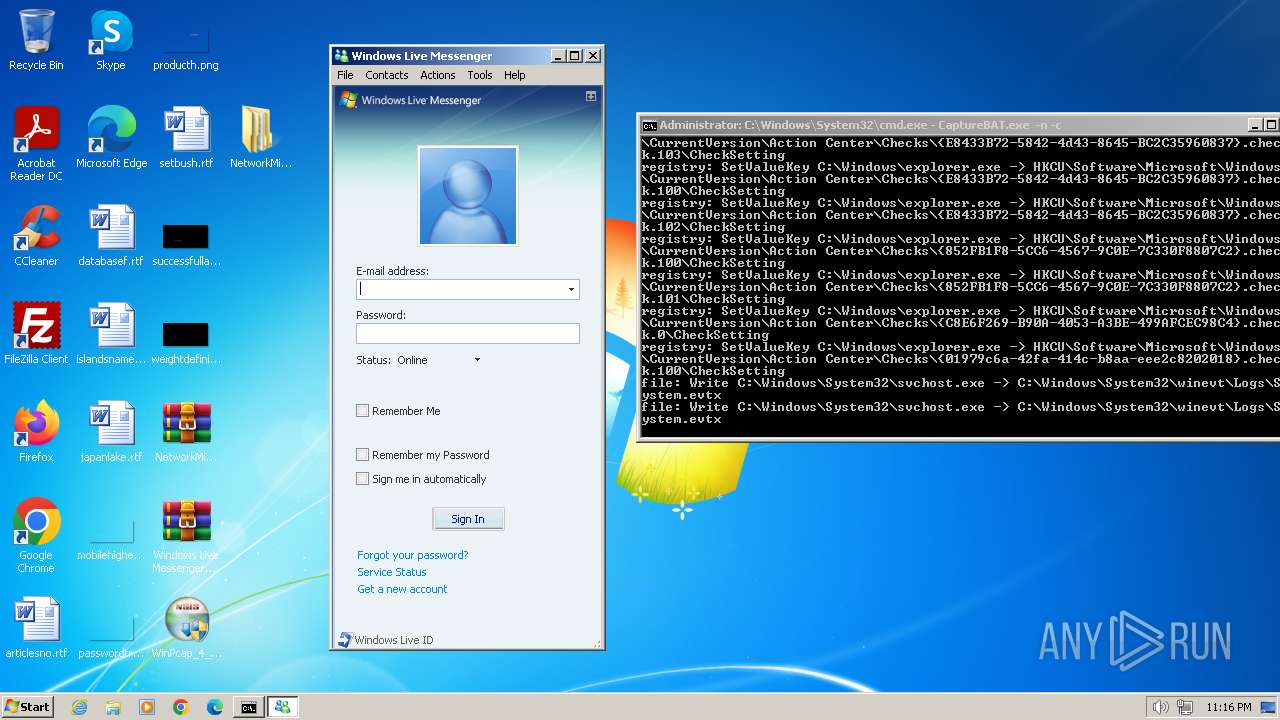
Drops a system driver (possible attempt to evade defenses)
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1032)
- rundll32.exe (PID: 3432)
- WinPcap_4_1_3.exe (PID: 2624)
Drops 7-zip archiver for unpacking
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1032)
Reads the Internet Settings
- runonce.exe (PID: 2948)
- sipnotify.exe (PID: 1664)
- runonce.exe (PID: 2916)
Uses RUNDLL32.EXE to load library
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1032)
The process executes via Task Scheduler
- ctfmon.exe (PID: 148)
- sipnotify.exe (PID: 1664)
Creates a software uninstall entry
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1032)
- WinPcap_4_1_3.exe (PID: 2624)
The process creates files with name similar to system file names
- WinPcap_4_1_3.exe (PID: 2624)
Creates or modifies Windows services
- WinPcap_4_1_3.exe (PID: 2624)
Creates files in the driver directory
- WinPcap_4_1_3.exe (PID: 2624)
Malware-specific behavior (creating "System.dll" in Temp)
- WinPcap_4_1_3.exe (PID: 2624)
INFO
Reads the computer name
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1032)
- IMEKLMG.EXE (PID: 1196)
- IMEKLMG.EXE (PID: 284)
- WinPcap_4_1_3.exe (PID: 2624)
- CaptureBAT.exe (PID: 3188)
- CaptureBAT.exe (PID: 3468)
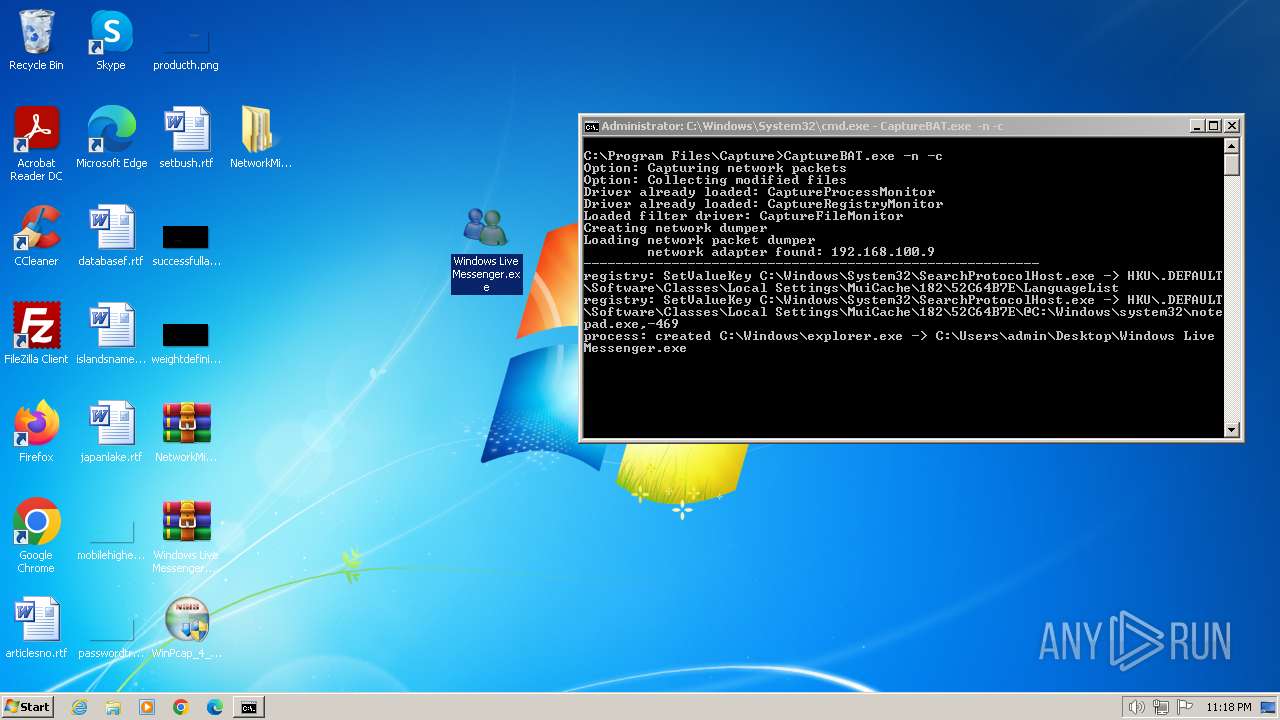
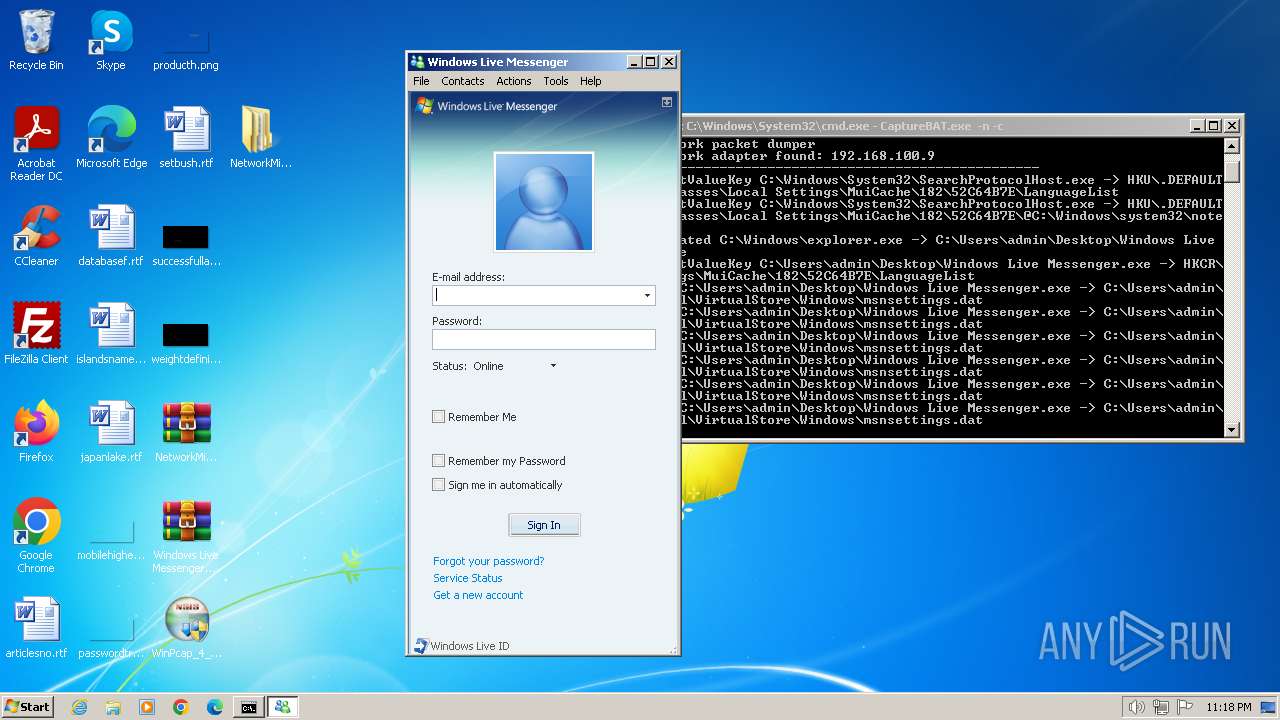
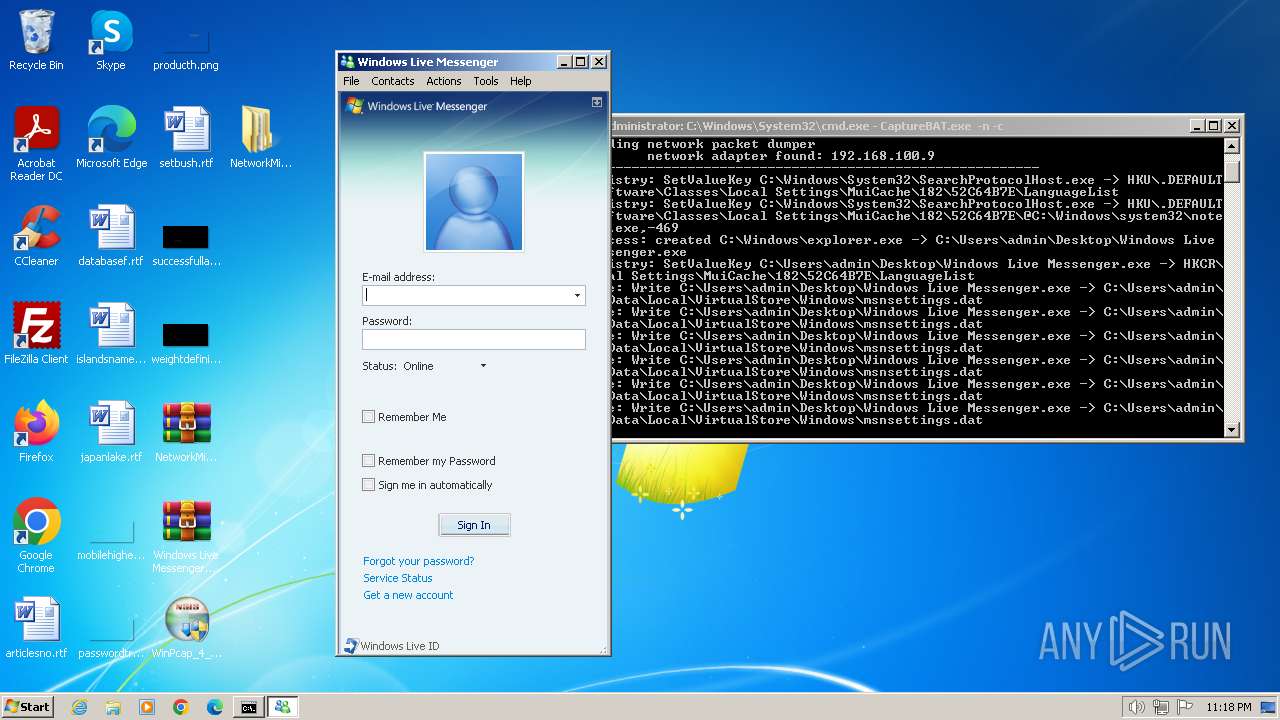
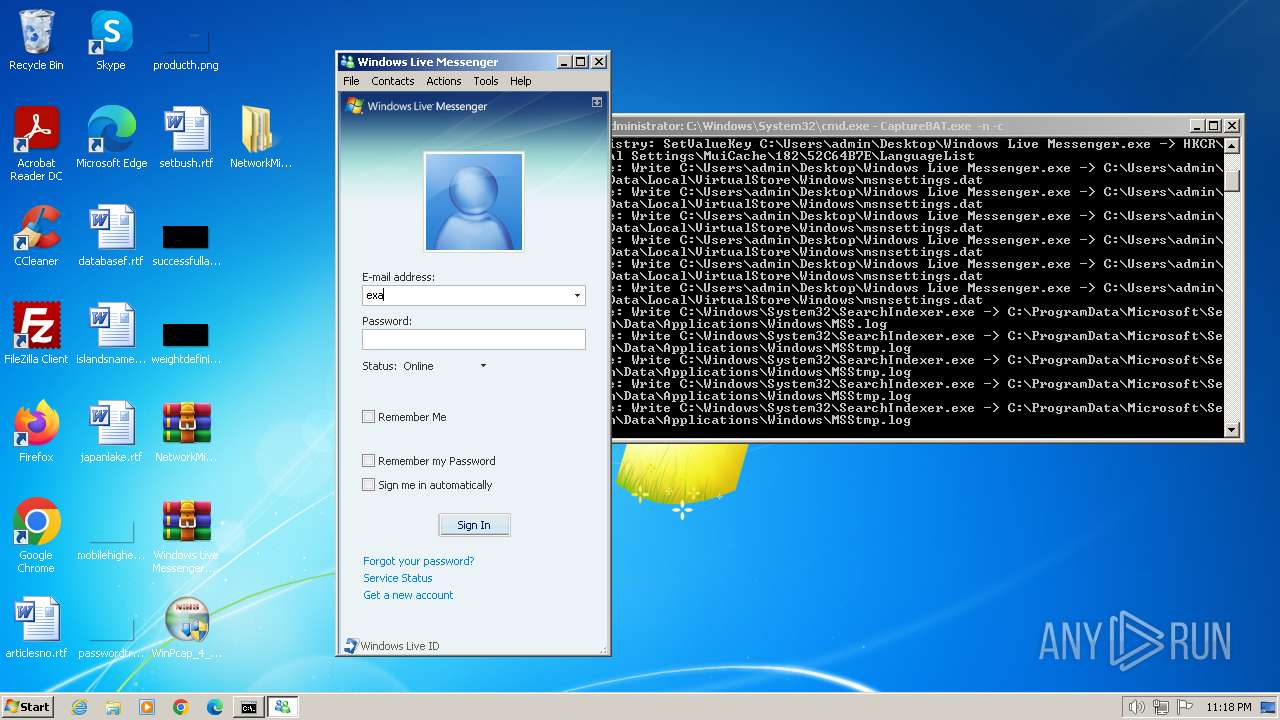
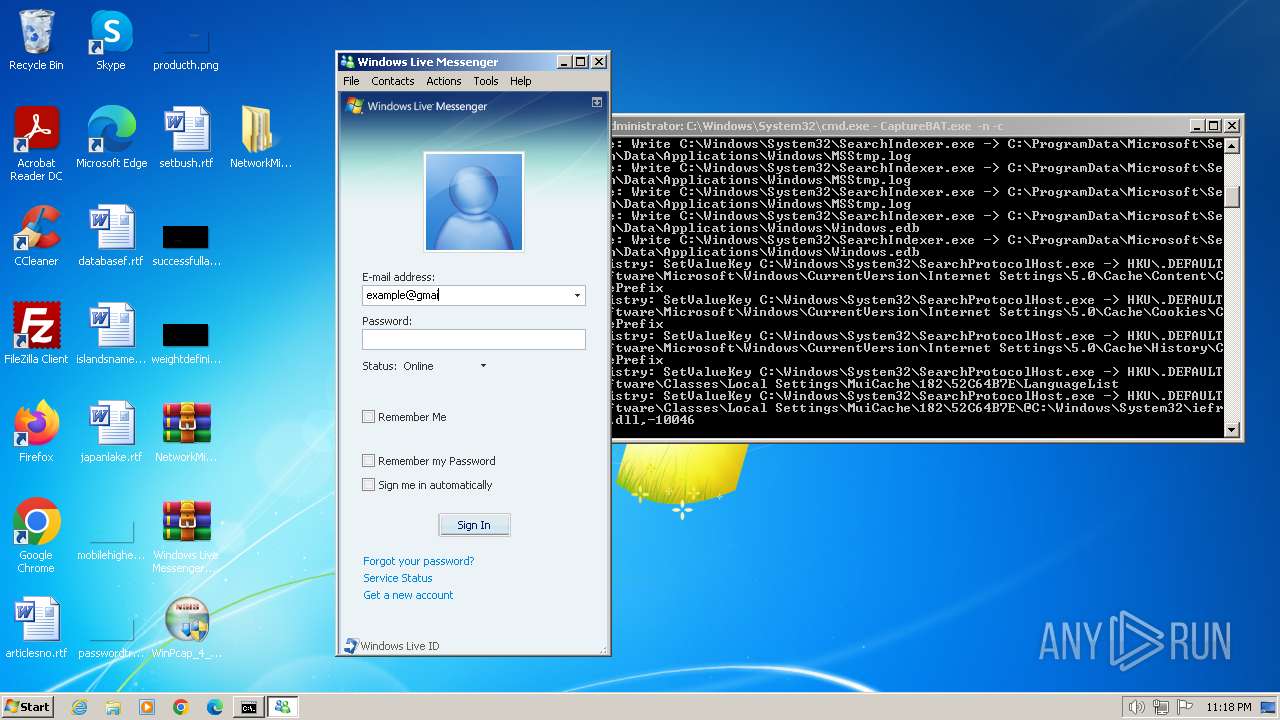
- Windows Live Messenger.exe (PID: 3488)
Checks supported languages
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1032)
- IMEKLMG.EXE (PID: 1196)
- IMEKLMG.EXE (PID: 284)
- WinPcap_4_1_3.exe (PID: 2624)
- CaptureBAT.exe (PID: 3188)
- Windows Live Messenger.exe (PID: 3488)
- CaptureBAT.exe (PID: 3468)
The sample compiled with english language support
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1032)
- WinRAR.exe (PID: 2740)
- WinPcap_4_1_3.exe (PID: 2624)
Creates files in the program directory
- CaptureBAT-Setup-2.0.0-5574.exe (PID: 1032)
- WinPcap_4_1_3.exe (PID: 2624)
- CaptureBAT.exe (PID: 3468)
Reads the time zone
- runonce.exe (PID: 2948)
- runonce.exe (PID: 2916)
Reads security settings of Internet Explorer
- runonce.exe (PID: 2948)
- runonce.exe (PID: 2916)
Creates files in the driver directory
- rundll32.exe (PID: 3432)
Manual execution by a user
- IMEKLMG.EXE (PID: 1196)
- IMEKLMG.EXE (PID: 284)
- WinPcap_4_1_3.exe (PID: 2512)
- WinPcap_4_1_3.exe (PID: 2624)
- WinRAR.exe (PID: 2740)
- cmd.exe (PID: 3152)
- cmd.exe (PID: 3352)
- Windows Live Messenger.exe (PID: 3488)
- explorer.exe (PID: 3816)
- explorer.exe (PID: 2872)
- Windows Live Messenger.exe (PID: 3524)
- WinRAR.exe (PID: 2808)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 1196)
- IMEKLMG.EXE (PID: 284)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2740)
- WinRAR.exe (PID: 2808)
Reads Environment values
- WinPcap_4_1_3.exe (PID: 2624)
Create files in a temporary directory
- WinPcap_4_1_3.exe (PID: 2624)
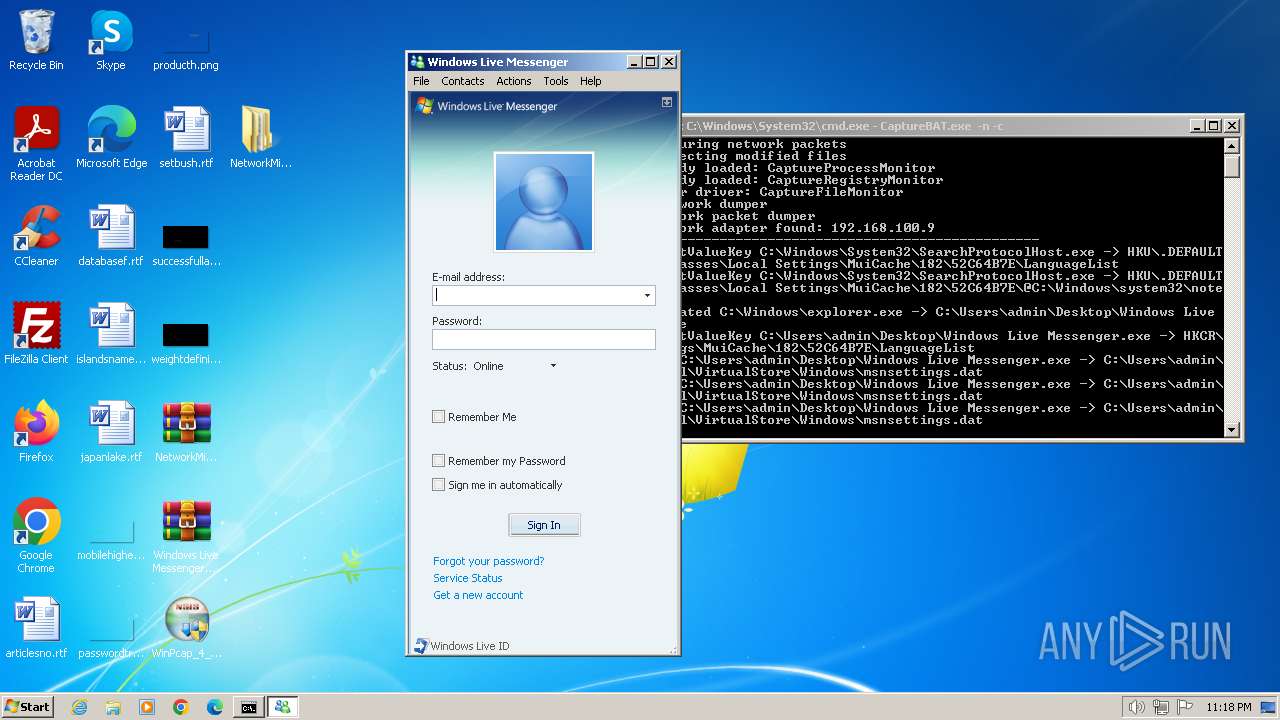
Creates files or folders in the user directory
- Windows Live Messenger.exe (PID: 3488)
Application launched itself
- msedge.exe (PID: 3840)
- msedge.exe (PID: 2944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:07:14 15:12:54+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 23552 |
| InitializedDataSize: | 164864 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30fb |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
148
Monitored processes
49
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2228 --field-trial-handle=1364,i,4757277213912052210,9538758312286477840,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 148 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 284 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 296 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2248 --field-trial-handle=1264,i,6931158795865381614,17222685257975757594,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 324 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1432 --field-trial-handle=1264,i,6931158795865381614,17222685257975757594,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 348 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2236 --field-trial-handle=1364,i,4757277213912052210,9538758312286477840,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 548 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1676 --field-trial-handle=1264,i,6931158795865381614,17222685257975757594,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1000 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1440 --field-trial-handle=1364,i,4757277213912052210,9538758312286477840,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
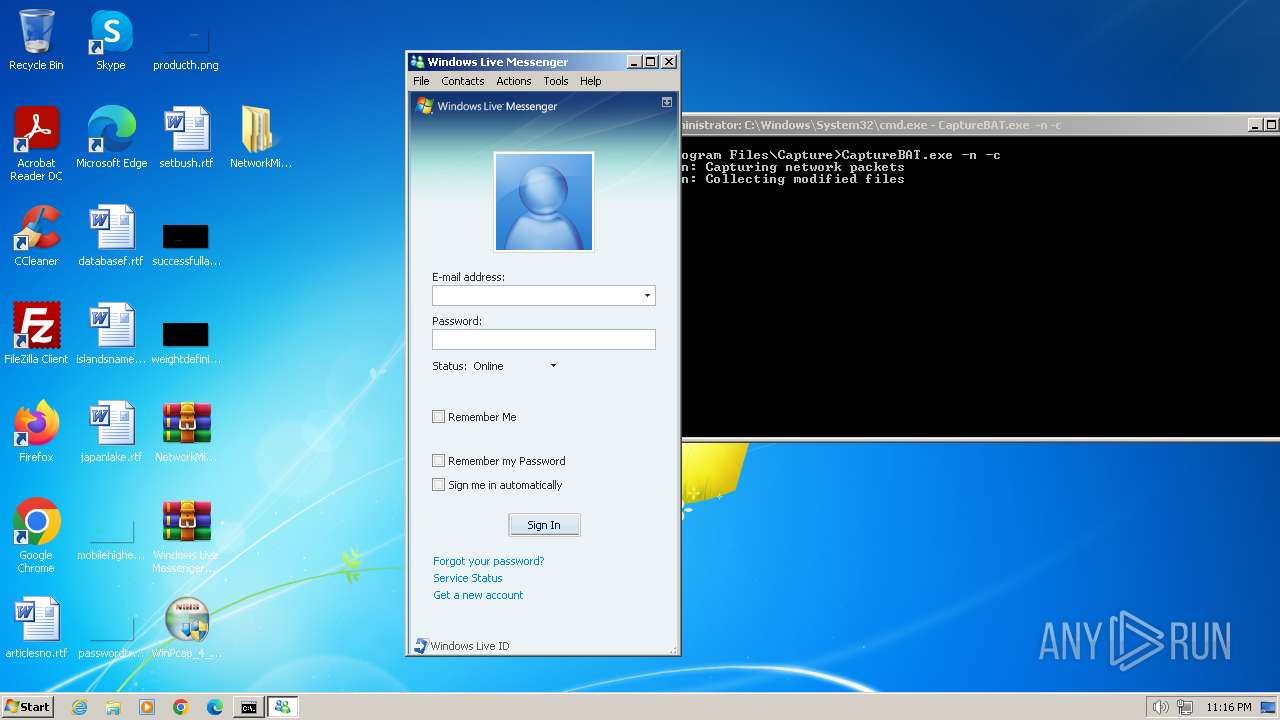
| 1012 | CaptureBAT.exe -n -c | C:\Program Files\Capture\CaptureBAT.exe | — | cmd.exe | |||||||||||
User: admin Company: Victoria University of Wellington and the New Zealand Honeynet Project Integrity Level: HIGH Description: Capture Version: 2.0.0 Modules
| |||||||||||||||
| 1032 | "C:\Users\admin\AppData\Local\Temp\CaptureBAT-Setup-2.0.0-5574.exe" | C:\Users\admin\AppData\Local\Temp\CaptureBAT-Setup-2.0.0-5574.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 2 Modules
| |||||||||||||||
Total events
10 975
Read events
10 872
Write events
95
Delete events
8
Modification events
| (PID) Process: | (2948) runonce.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | GrpConv |
Value: grpconv -o | |||
| (PID) Process: | (2948) runonce.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2948) runonce.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2948) runonce.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2948) runonce.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1844) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 118 | |||
| (PID) Process: | (2916) runonce.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | GrpConv |
Value: grpconv -o | |||
| (PID) Process: | (3432) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 119 | |||
| (PID) Process: | (1844) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | GrpConv |
Value: grpconv -o | |||
| (PID) Process: | (3432) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\GroupOrderList |
| Operation: | write | Name: | FSFilter Activity Monitor |
Value: 020000000100000002000000 | |||
Executable files
27
Suspicious files
69
Text files
123
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1032 | CaptureBAT-Setup-2.0.0-5574.exe | C:\Program Files\Capture\7za.exe | executable | |
MD5:885E9EB42889CA547F4E3515DCDE5D3D | SHA256:B3A70D388488C34DD5C767692ECCC9EFFED36B8E7C1EE03ACE1BD27123A2E6D6 | |||
| 1032 | CaptureBAT-Setup-2.0.0-5574.exe | C:\Program Files\Capture\CaptureRegistryMonitor.sys | executable | |
MD5:BFB27AE3985A7D4A50DF860A7D6E331C | SHA256:629CA2CB005FB282DCA8B61DA76A90E73B900B949E8D0EDB5A33F52BD373B98F | |||
| 1032 | CaptureBAT-Setup-2.0.0-5574.exe | C:\Program Files\Capture\CaptureProcessMonitor.sys | executable | |
MD5:A6F0F372910D8114B65775CABF165ACB | SHA256:2F42C45EA02A2E606B6696B2A287148483A0D020ED0CD4CB2D1E3789B494BBA8 | |||
| 1032 | CaptureBAT-Setup-2.0.0-5574.exe | C:\Program Files\Capture\FileMonitorInstallation.inf | binary | |
MD5:C2D8DFE752F2257DC12B983B82558566 | SHA256:219ABB4A859D8E62EFFC584BFE113D373C9FF471EA893B97449952E38C816270 | |||
| 1032 | CaptureBAT-Setup-2.0.0-5574.exe | C:\Program Files\Capture\ProcessMonitor.exl | text | |
MD5:2EC9BE16BEEAC6AFAA115B2A9EEC5258 | SHA256:E91BB5871E840777B45691643105F6F015A9ADFF215EA7F82287148D451B71AE | |||
| 1032 | CaptureBAT-Setup-2.0.0-5574.exe | C:\Program Files\Capture\CaptureBAT.exe | executable | |
MD5:7E0EDF894D47D0DECB15C9757933029E | SHA256:2EABFEAB8B5AE14805FFCB8AA63ACD1A5025FCD0A25933A5B18C8E63D2DF3A56 | |||
| 1032 | CaptureBAT-Setup-2.0.0-5574.exe | C:\Program Files\Capture\COPYING | text | |
MD5:751419260AA954499F7ABAABAA882BBE | SHA256:AB15FD526BD8DD18A9E77EBC139656BF4D33E97FC7238CD11BF60E2B9B8666C6 | |||
| 1032 | CaptureBAT-Setup-2.0.0-5574.exe | C:\Program Files\Capture\FileMonitor.exl | text | |
MD5:9F3139343EA67CBB703E8271B131FA78 | SHA256:69DA0C07B6A9D41CBF32372AA6513D0D0902764D35FA0103F84E6F3556B996C1 | |||
| 1032 | CaptureBAT-Setup-2.0.0-5574.exe | C:\Program Files\Capture\CaptureFileMonitor.sys | executable | |
MD5:D70F8AFF620E1203C45680DC827A6B3E | SHA256:B2E6F2062B2F81CD0F3E1F2503F387AE824A84A8DD77ED55CF92DA03FDEEC130 | |||
| 1032 | CaptureBAT-Setup-2.0.0-5574.exe | C:\Program Files\Capture\RegistryMonitor.exl | text | |
MD5:2E3F309CFA5C53CA4473CCF34C13E2A5 | SHA256:635A8489CCA2000A2208183BDCA3091D465B53563F9CD5EB152B80CA2C53A55C | |||
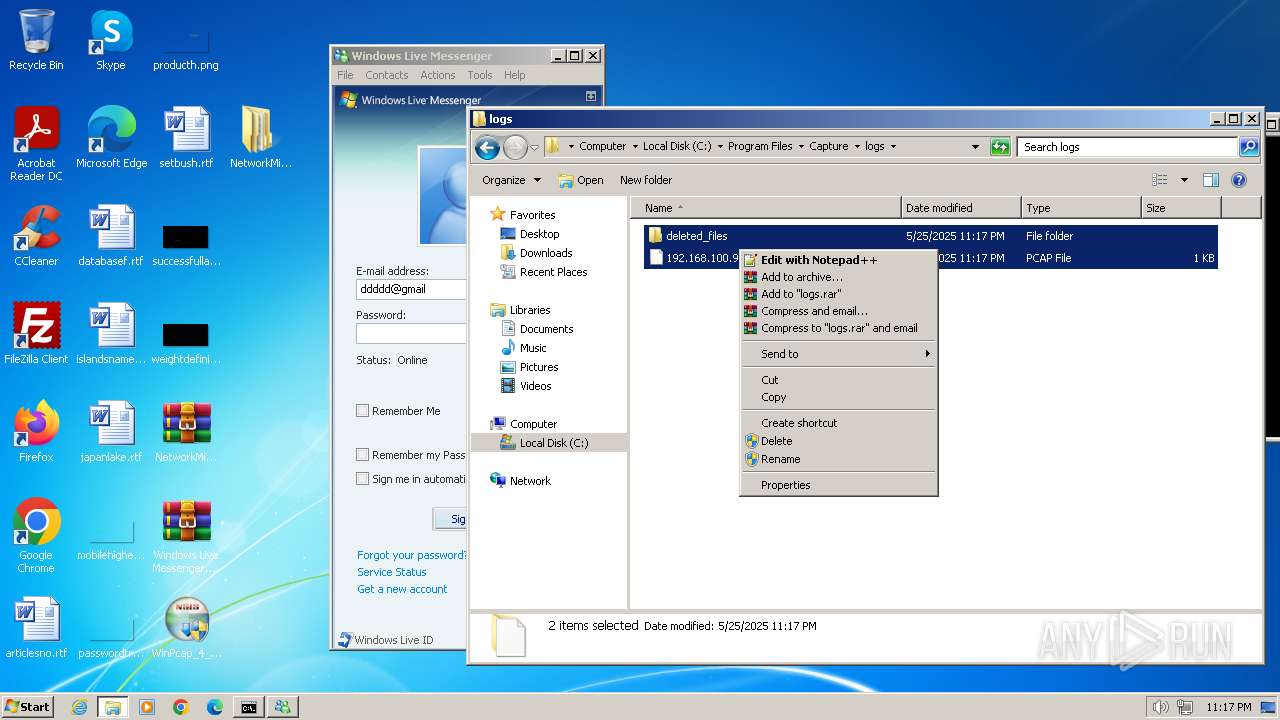
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
17
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1664 | sipnotify.exe | HEAD | 503 | 104.102.43.250:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133926884849210000 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1664 | sipnotify.exe | 104.102.43.250:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | DE | whitelisted |
1120 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
324 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
324 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2944 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3960 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
query.prod.cms.rt.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
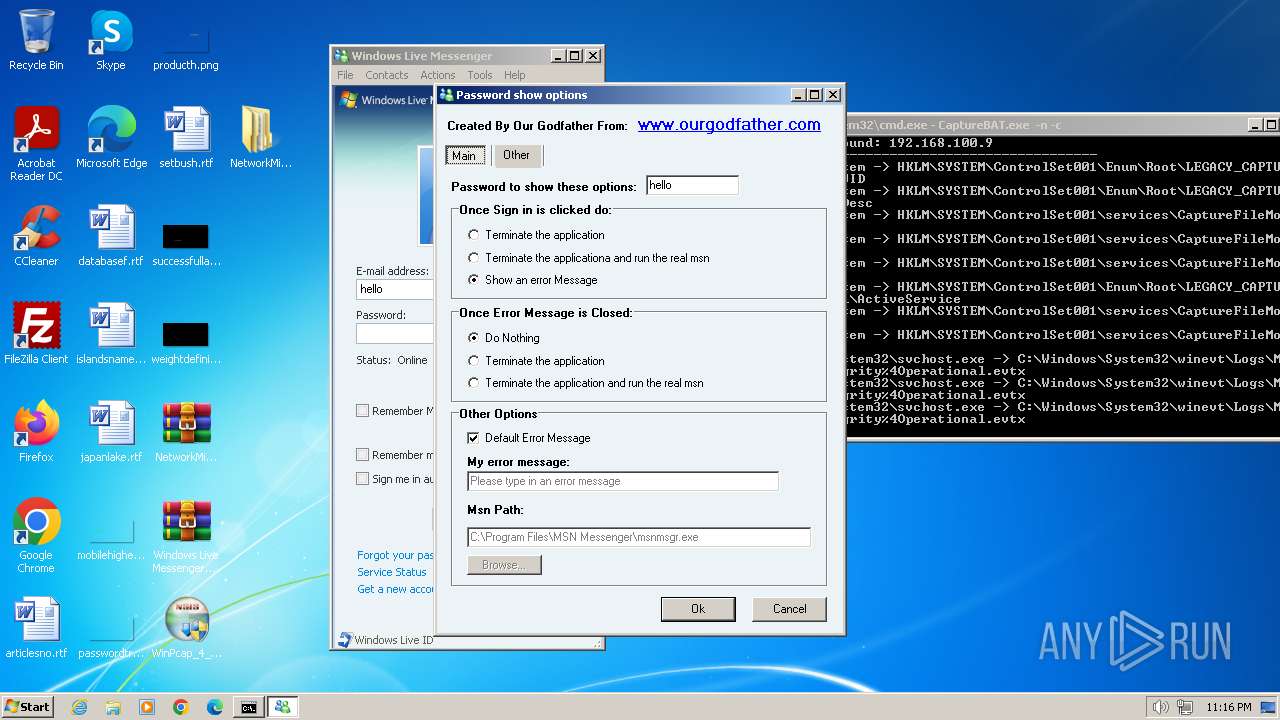
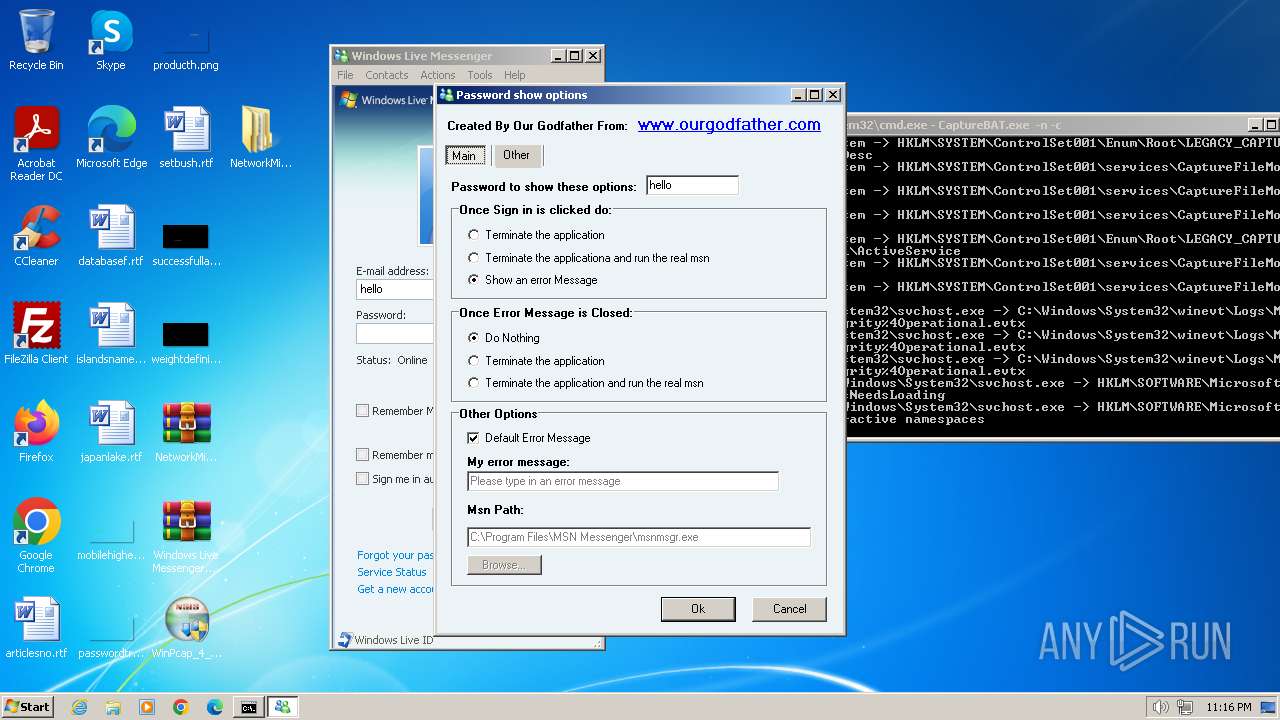
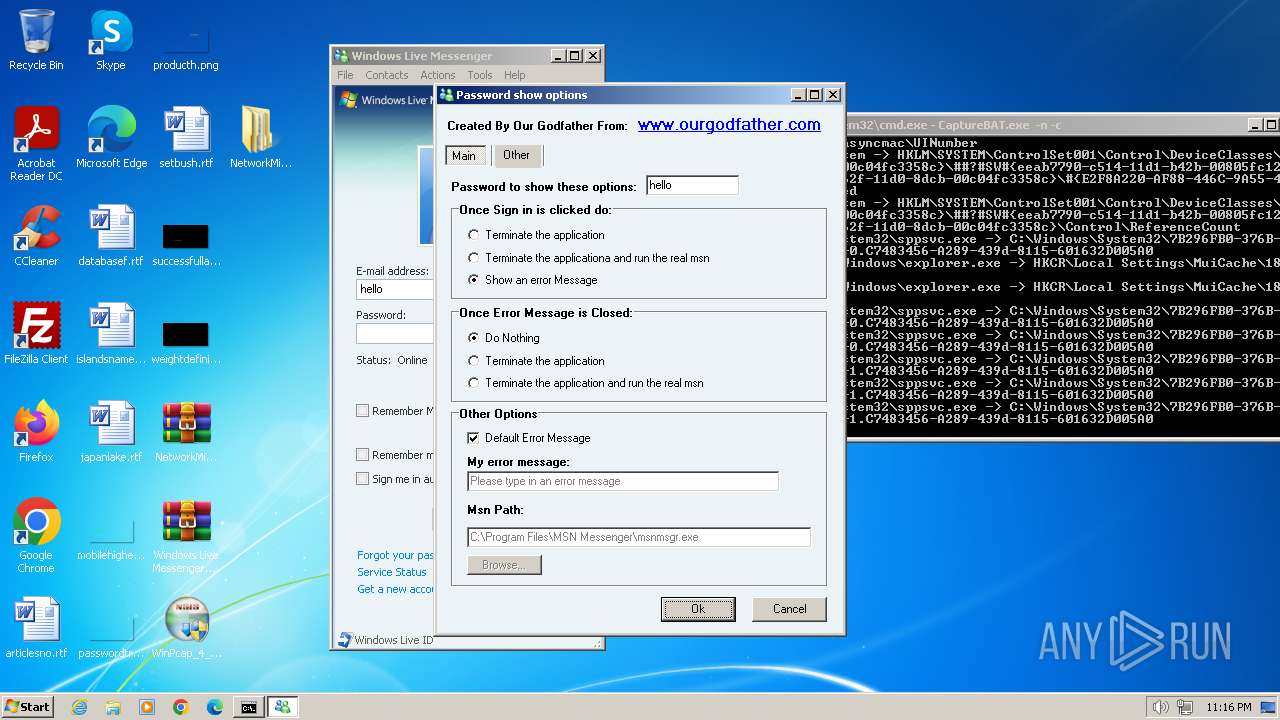
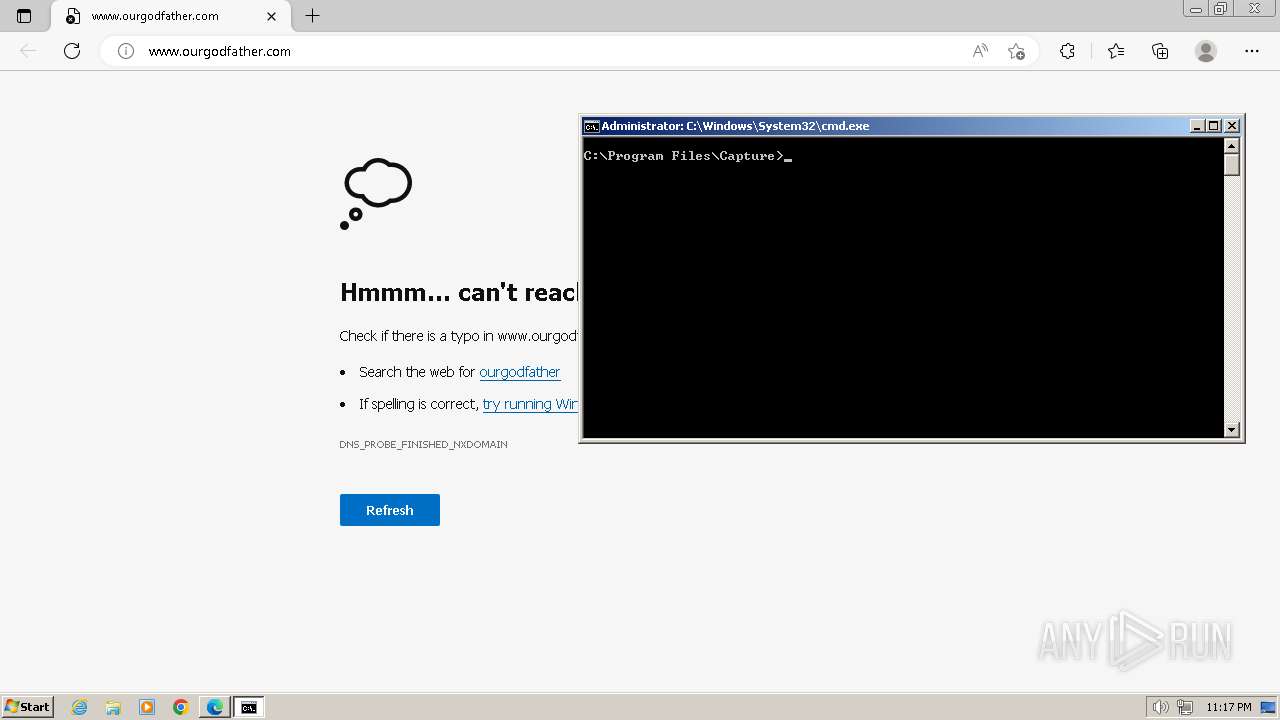
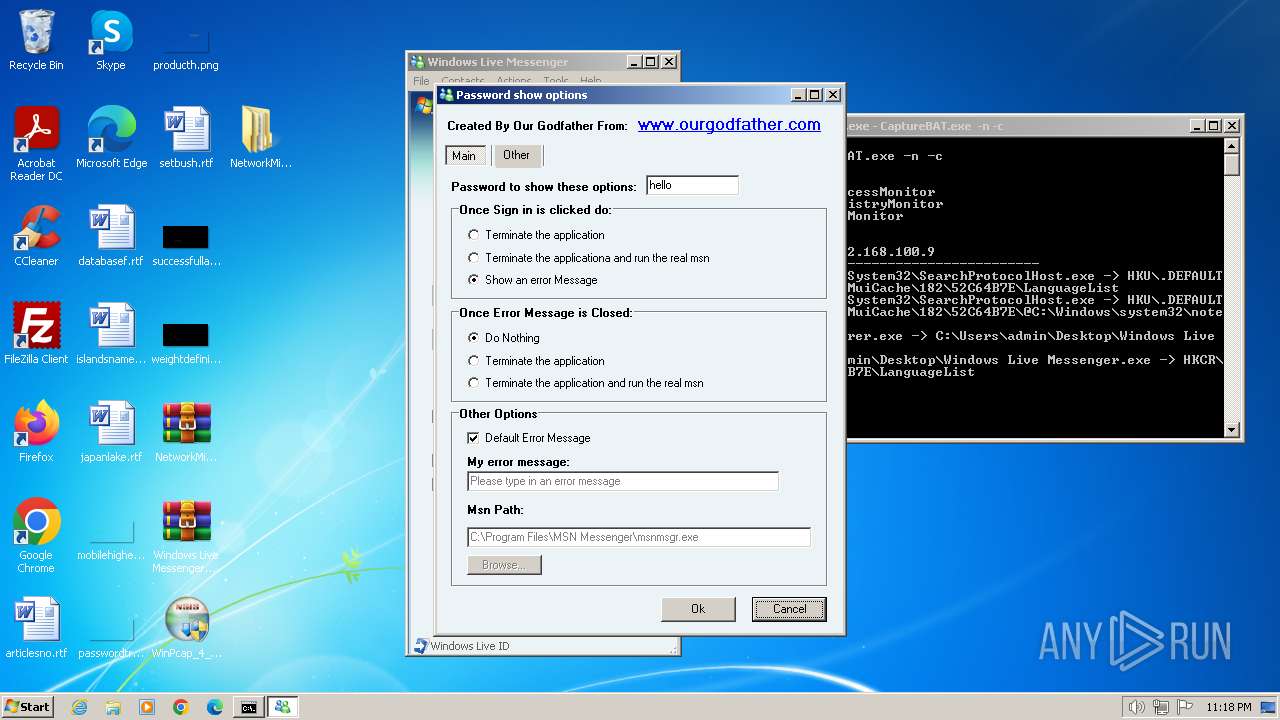
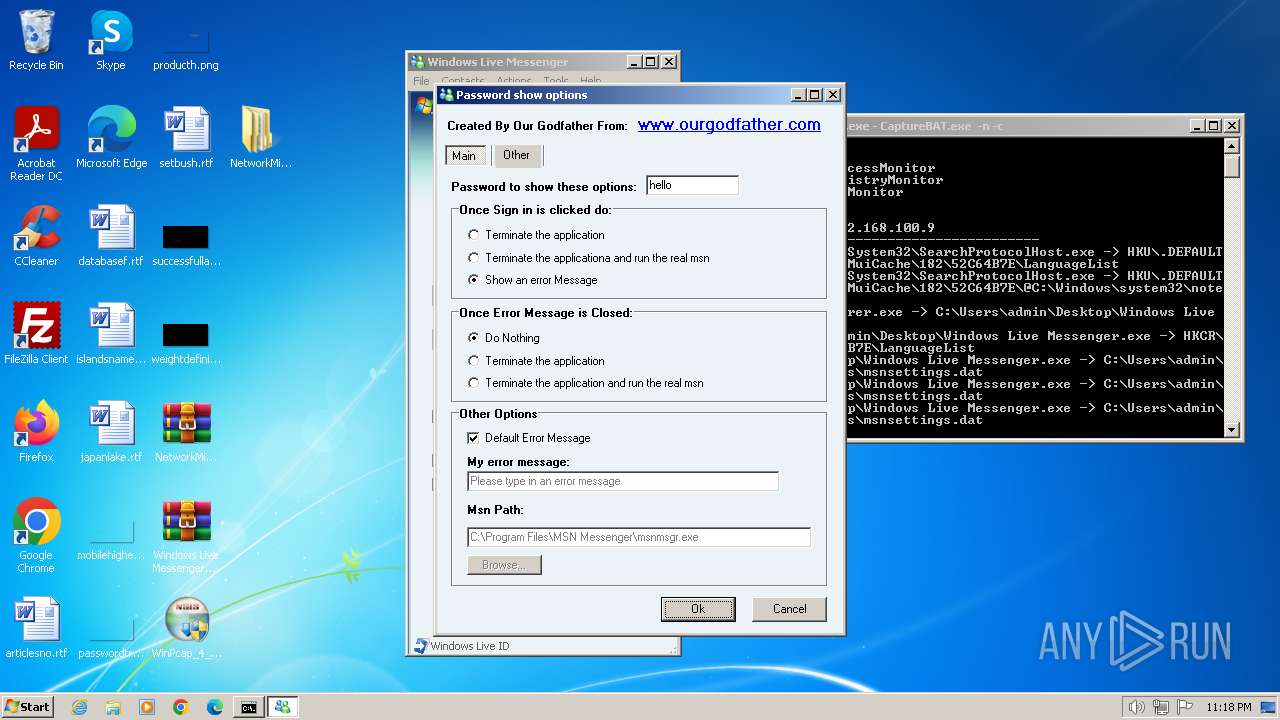
www.ourgodfather.com |
| unknown |