| File name: | c90bb703a45863aa5e7fdc60a4ad32f933adca82ecddb1c42cf35a17f8078434.apk |
| Full analysis: | https://app.any.run/tasks/fda492f2-c18f-4f78-abc3-00c5d8a28343 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 20:44:49 |
| OS: | Android 14 |
| MIME: | application/vnd.android.package-archive |
| File info: | Android package (APK), with AndroidManifest.xml, with APK Signing Block |
| MD5: | 59FF51EF565D48A11E6FBB28B2B328ED |
| SHA1: | 75A1E2B8B6B874168429748CA7FA476AFCBE99EB |
| SHA256: | C90BB703A45863AA5E7FDC60A4AD32F933ADCA82ECDDB1C42CF35A17F8078434 |
| SSDEEP: | 98304:LjvbDV+R2I4mvG17Nx/uTx7CiHwYAf45qOT2DqTsC+DlX43AdV2lDKRziiPPuU1L:k4v7wC65QtYhY |
MALICIOUS
Executes system commands or scripts
- app_process64 (PID: 2204)
- app_process64 (PID: 2302)
- app_process64 (PID: 2410)
- app_process64 (PID: 2458)
SUSPICIOUS
Retrieves a list of running application processes
- app_process64 (PID: 2204)
- app_process64 (PID: 2302)
- app_process64 (PID: 2410)
- app_process64 (PID: 2458)
Abuses foreground service for persistence
- app_process64 (PID: 2204)
- app_process64 (PID: 2302)
- app_process64 (PID: 2410)
- app_process64 (PID: 2458)
Updates data in the storage of application settings (SharedPreferences)
- app_process64 (PID: 2204)
- app_process64 (PID: 2302)
Accesses system-level resources
- app_process64 (PID: 2204)
- app_process64 (PID: 2302)
- app_process64 (PID: 2410)
- app_process64 (PID: 2458)
Establishing a connection
- app_process64 (PID: 2302)
Acquires a wake lock to keep the device awake
- app_process64 (PID: 2302)
- app_process64 (PID: 2204)
- app_process64 (PID: 2410)
- app_process64 (PID: 2458)
Collects data about the device's environment (JVM version)
- app_process64 (PID: 2204)
- app_process64 (PID: 2410)
- app_process64 (PID: 2458)
Creates a WakeLock to manage power state
- app_process64 (PID: 2204)
- app_process64 (PID: 2302)
- app_process64 (PID: 2410)
- app_process64 (PID: 2458)
Starts itself from another location
- app_process64 (PID: 2204)
- app_process64 (PID: 2458)
- app_process64 (PID: 2302)
- app_process64 (PID: 2410)
Application launched itself
- app_process64 (PID: 2458)
- app_process64 (PID: 2204)
- app_process64 (PID: 2302)
- app_process64 (PID: 2410)
Connects to unusual port
- app_process64 (PID: 2302)
INFO
Retrieves data from storage of application settings (SharedPreferences)
- app_process64 (PID: 2204)
- app_process64 (PID: 2302)
- app_process64 (PID: 2410)
- app_process64 (PID: 2458)
Dynamically loads a class in Java
- app_process64 (PID: 2204)
- app_process64 (PID: 2410)
- app_process64 (PID: 2458)
Dynamically registers broadcast event listeners
- app_process64 (PID: 2204)
- app_process64 (PID: 2302)
- app_process64 (PID: 2410)
- app_process64 (PID: 2458)
Dynamically inspects or modifies classes, methods, and fields at runtime
- app_process64 (PID: 2204)
- app_process64 (PID: 2302)
- app_process64 (PID: 2410)
- app_process64 (PID: 2458)
Detects device power status
- app_process64 (PID: 2204)
- app_process64 (PID: 2302)
- app_process64 (PID: 2410)
- app_process64 (PID: 2458)
Gets the display metrics associated with the device's screen
- app_process64 (PID: 2204)
- app_process64 (PID: 2410)
- app_process64 (PID: 2458)
Retrieves the value of a global system setting
- app_process64 (PID: 2204)
- app_process64 (PID: 2302)
- app_process64 (PID: 2410)
- app_process64 (PID: 2458)
Retrieves the value of a secure system setting
- app_process64 (PID: 2204)
- app_process64 (PID: 2302)
- app_process64 (PID: 2410)
- app_process64 (PID: 2458)
Verifies whether the device is connected to the internet
- app_process64 (PID: 2302)
Creates and writes local files
- app_process64 (PID: 2302)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .apk | | | Android Package (62.8) |
|---|---|---|
| .jar | | | Java Archive (17.3) |
| .vym | | | VYM Mind Map (14.9) |
| .zip | | | ZIP compressed archive (4.7) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:01:15 14:50:46 |
| ZipCRC: | 0x1544c11c |
| ZipCompressedSize: | 3634 |
| ZipUncompressedSize: | 16136 |
| ZipFileName: | AndroidManifest.xml |
Total processes
139
Monitored processes
17
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 342 | /system/bin/netd | /system/bin/netd | init | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
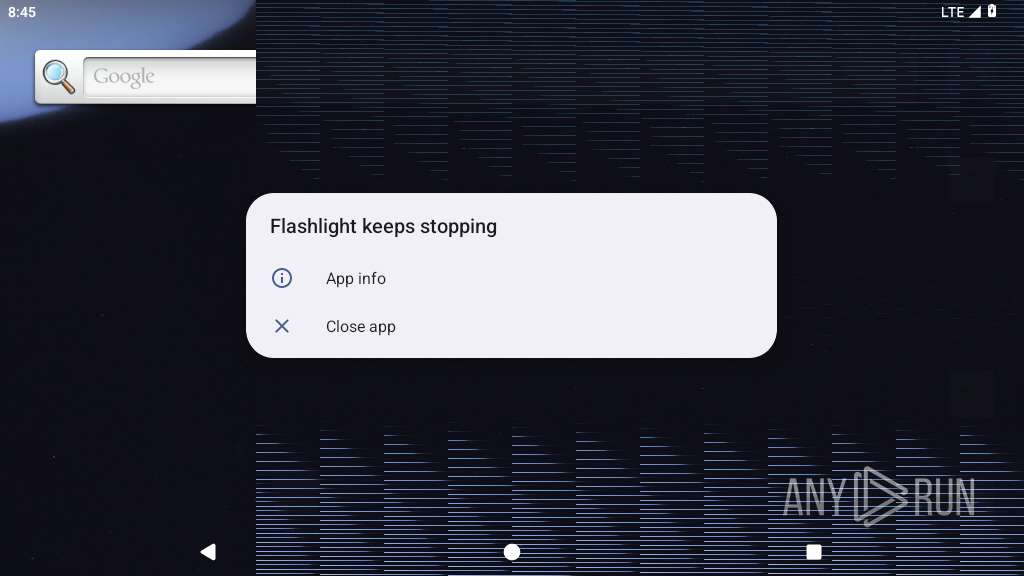
| 2204 | com.lahsuak.apps.flashlight | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 9 | ||||
| 2241 | logcat -c | /system/bin/logcat | — | app_process64 |
User: u0_a108 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2246 | logcat -v brief com.lahsuak.apps.flashlight | /system/bin/logcat | — | app_process64 |
User: u0_a108 Integrity Level: UNKNOWN Exit code: 9 | ||||
| 2302 | com.lahsuak.apps.flashlight | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 9 | ||||
| 2327 | logcat -c | /system/bin/logcat | — | app_process64 |
User: u0_a108 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2335 | logcat -v brief com.lahsuak.apps.flashlight | /system/bin/logcat | — | app_process64 |
User: u0_a108 Integrity Level: UNKNOWN Exit code: 9 | ||||
| 2410 | com.lahsuak.apps.flashlight | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 9 | ||||
| 2442 | logcat -c | /system/bin/logcat | — | app_process64 |
User: u0_a108 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2446 | logcat -v brief com.lahsuak.apps.flashlight | /system/bin/logcat | — | app_process64 |
User: u0_a108 Integrity Level: UNKNOWN Exit code: 9 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2204 | app_process64 | /data/data/com.lahsuak.apps.flashlight/shared_prefs/bugfender.preferences.xml | — | |
MD5:— | SHA256:— | |||
| 2204 | app_process64 | /data/data/com.lahsuak.apps.flashlight/app_bugfender/session-1742849108693/session.json | — | |
MD5:— | SHA256:— | |||
| 2204 | app_process64 | /data/data/com.lahsuak.apps.flashlight/shared_prefs/bugfender.device.key.xml | — | |
MD5:— | SHA256:— | |||
| 2302 | app_process64 | /data/data/com.lahsuak.apps.flashlight/shared_prefs/bugfender.preferences.xml | — | |
MD5:— | SHA256:— | |||
| 2302 | app_process64 | /data/data/com.lahsuak.apps.flashlight/shared_prefs/bugfender.device.key.xml | — | |
MD5:— | SHA256:— | |||
| 2302 | app_process64 | /data/data/com.lahsuak.apps.flashlight/app_bugfender/session-1742849123058/session.json | — | |
MD5:— | SHA256:— | |||
| 2302 | app_process64 | /data/data/com.lahsuak.apps.flashlight/app_bugfender/session-1742849123058/logs/logs | — | |
MD5:— | SHA256:— | |||
| 2302 | app_process64 | /data/data/com.lahsuak.apps.flashlight/app_bugfender/device_status.json | — | |
MD5:— | SHA256:— | |||
| 2410 | app_process64 | /data/data/com.lahsuak.apps.flashlight/shared_prefs/bugfender.preferences.xml | — | |
MD5:— | SHA256:— | |||
| 2410 | app_process64 | /data/data/com.lahsuak.apps.flashlight/shared_prefs/bugfender.device.key.xml | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
19
DNS requests
5
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 142.250.185.227:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
342 | netd | 8.8.8.8:443 | — | — | — | malicious |
447 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 216.239.35.0:123 | time.android.com | — | — | whitelisted |
— | — | 142.250.185.227:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
— | — | 216.58.212.132:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 8.8.8.8:853 | — | GOOGLE | US | malicious |
— | — | 142.250.102.81:443 | — | GOOGLE | US | unknown |
2302 | app_process64 | 87.119.220.245:42474 | — | Host Europe GmbH | FR | unknown |
2302 | app_process64 | 185.206.63.63:443 | — | Brutalsys S.l. | NL | unknown |
2542 | app_process32 | 142.250.186.163:443 | — | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.google.com |
| whitelisted |
connectivitycheck.gstatic.com |
| whitelisted |
time.android.com |
| whitelisted |
XO |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Android Device Connectivity Check |