| download: | /vir/Email-Worm.Win32.NetSky.q |
| Full analysis: | https://app.any.run/tasks/77c14dc2-dff6-46a7-8298-a277e23d4aaf |
| Verdict: | Malicious activity |
| Analysis date: | February 16, 2025, 10:42:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 3 sections |
| MD5: | 3018E99857F31A59E0777396AE634A8F |
| SHA1: | 7031CFE76EE7B2C925F2C00372FB9EF7F983F60C |
| SHA256: | C8FFFB2E737514C551B2D7BCAF8BAA459564B059CAB1A35A3CEC4B3C270D4525 |
| SSDEEP: | 768:vWkliAnUQYkYKzqbjC5RqHjrYReyZx+l0oKriCPRDLk:+ySsz6jGeyZx+l0TRM |
MALICIOUS
Changes the autorun value in the registry
- Email-Worm.Win32.NetSky.q (PID: 1832)
SUSPICIOUS
Starts application with an unusual extension
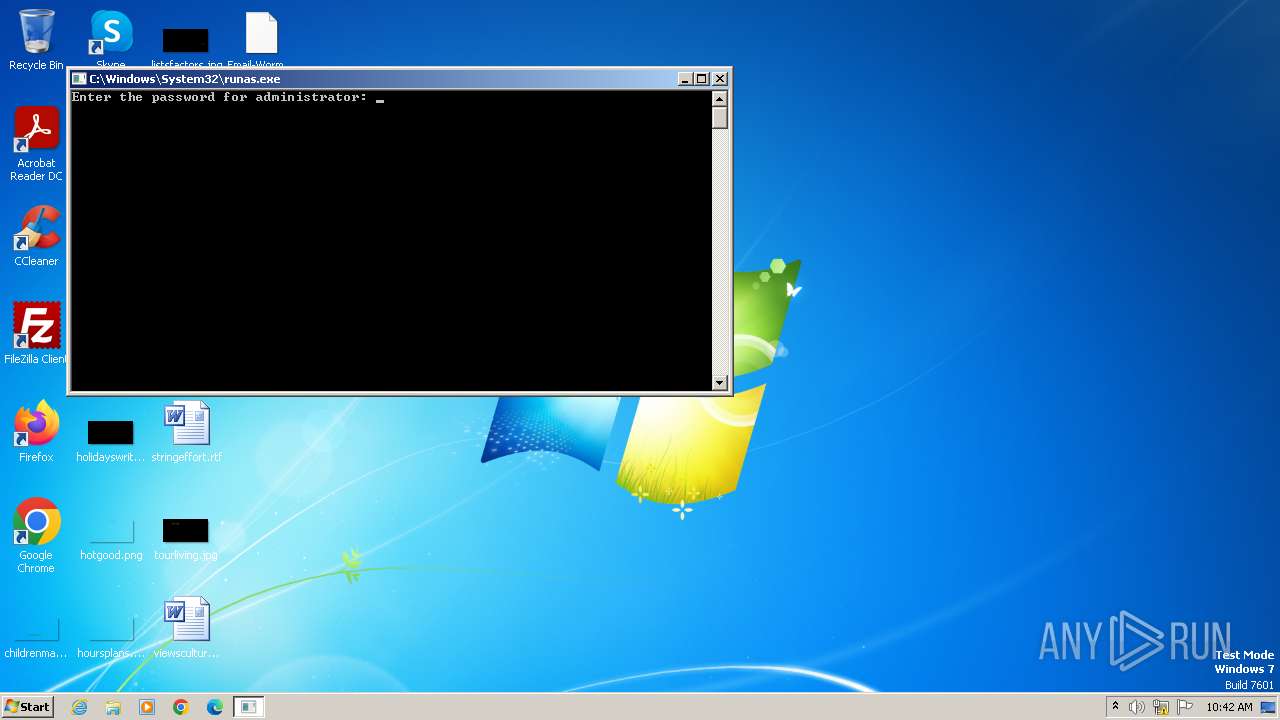
- runas.exe (PID: 1836)
Starts another process probably with elevated privileges via RUNAS.EXE
- runas.exe (PID: 1836)
Executable content was dropped or overwritten
- Email-Worm.Win32.NetSky.q (PID: 1832)
Connects to SMTP port
- Email-Worm.Win32.NetSky.q (PID: 1832)
Reads the Internet Settings
- Email-Worm.Win32.NetSky.q (PID: 1832)
Drops a file with a rarely used extension (PIF)
- Email-Worm.Win32.NetSky.q (PID: 1832)
INFO
Reads the computer name
- Email-Worm.Win32.NetSky.q (PID: 1832)
Disables trace logs
- Email-Worm.Win32.NetSky.q (PID: 1832)
Checks supported languages
- Email-Worm.Win32.NetSky.q (PID: 1832)
Checks proxy server information
- Email-Worm.Win32.NetSky.q (PID: 1832)
Creates files in the program directory
- Email-Worm.Win32.NetSky.q (PID: 1832)
Reads the machine GUID from the registry
- Email-Worm.Win32.NetSky.q (PID: 1832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.7) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.4) |
| .exe | | | DOS Executable Generic (23.4) |
| .vxd | | | VXD Driver (0.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | - |
| CodeSize: | 1024 |
| InitializedDataSize: | 29184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x12000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
40
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1832 | C:\Users\admin\Desktop\Email-Worm.Win32.NetSky.q | C:\Users\admin\Desktop\Email-Worm.Win32.NetSky.q | runas.exe | ||||||||||||
User: Administrator Integrity Level: HIGH Modules
| |||||||||||||||
| 1836 | "C:\Windows\System32\runas.exe" /user:administrator C:\Users\admin\Desktop\Email-Worm.Win32.NetSky.q | C:\Windows\System32\runas.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Run As Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 212
Read events
1 179
Write events
8
Delete events
25
Modification events
| (PID) Process: | (1832) Email-Worm.Win32.NetSky.q | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Email-Worm_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1832) Email-Worm.Win32.NetSky.q | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Email-Worm_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1832) Email-Worm.Win32.NetSky.q | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Email-Worm_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (1832) Email-Worm.Win32.NetSky.q | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Email-Worm_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (1832) Email-Worm.Win32.NetSky.q | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Email-Worm_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (1832) Email-Worm.Win32.NetSky.q | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Email-Worm_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (1832) Email-Worm.Win32.NetSky.q | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Norton Antivirus AV |
Value: C:\Windows\FVProtect.exe | |||
| (PID) Process: | (1832) Email-Worm.Win32.NetSky.q | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (1832) Email-Worm.Win32.NetSky.q | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (1832) Email-Worm.Win32.NetSky.q | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | system. |
Value: | |||
Executable files
1 141
Suspicious files
1
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1832 | Email-Worm.Win32.NetSky.q | C:\Windows\zip2.tmp | text | |
MD5:BC756E29716B32363CF480D5998456BD | SHA256:1269D8119EF41E48201BBFACD3A5D40FE8E59DA4E699A5FFA2369F57D63B7377 | |||
| 1832 | Email-Worm.Win32.NetSky.q | C:\Program Files\FileZilla FTP Client\docs\Kazaa Lite 4.0 new.exe | executable | |
MD5:3018E99857F31A59E0777396AE634A8F | SHA256:C8FFFB2E737514C551B2D7BCAF8BAA459564B059CAB1A35A3CEC4B3C270D4525 | |||
| 1832 | Email-Worm.Win32.NetSky.q | C:\Windows\userconfig9x.dll | executable | |
MD5:0A9FFA57D65083C92E0D3D69B00F2F0D | SHA256:9BFAF2F0B53F87D1452D4C2AA75027FFB8E66AEE1462C3D9EB7A6E55BCAC55C8 | |||
| 1832 | Email-Worm.Win32.NetSky.q | C:\Windows\zip3.tmp | text | |
MD5:BCD7FDD2D03C5126CBBF7F647F844DF6 | SHA256:7DADB037C879DC26CE4C304E6D405CD749191CFD181027754F55C346D5A42281 | |||
| 1832 | Email-Worm.Win32.NetSky.q | C:\Program Files\FileZilla FTP Client\docs\Britney Spears Sexy archive.doc.exe | executable | |
MD5:3018E99857F31A59E0777396AE634A8F | SHA256:C8FFFB2E737514C551B2D7BCAF8BAA459564B059CAB1A35A3CEC4B3C270D4525 | |||
| 1832 | Email-Worm.Win32.NetSky.q | C:\Program Files\FileZilla FTP Client\docs\Kazaa new.exe | executable | |
MD5:3018E99857F31A59E0777396AE634A8F | SHA256:C8FFFB2E737514C551B2D7BCAF8BAA459564B059CAB1A35A3CEC4B3C270D4525 | |||
| 1832 | Email-Worm.Win32.NetSky.q | C:\Windows\zip1.tmp | text | |
MD5:5D71F5745FBCD5B384BE389C1BD2935F | SHA256:37CFD3B6342323234319EA681B7A244355A27D4FF4DC040D4304EE508CD733AE | |||
| 1832 | Email-Worm.Win32.NetSky.q | C:\Windows\zipped.tmp | compressed | |
MD5:28293247F09C281393A9B6EE825C9B8C | SHA256:E5F499C231DD70A9C01551B7A8996A2CA5083373BC1833FED4B8A3064C077457 | |||
| 1832 | Email-Worm.Win32.NetSky.q | C:\Program Files\FileZilla FTP Client\docs\Harry Potter e book.doc.exe | executable | |
MD5:3018E99857F31A59E0777396AE634A8F | SHA256:C8FFFB2E737514C551B2D7BCAF8BAA459564B059CAB1A35A3CEC4B3C270D4525 | |||
| 1832 | Email-Worm.Win32.NetSky.q | C:\Program Files\FileZilla FTP Client\docs\Britney sex xxx.jpg.exe | executable | |
MD5:3018E99857F31A59E0777396AE634A8F | SHA256:C8FFFB2E737514C551B2D7BCAF8BAA459564B059CAB1A35A3CEC4B3C270D4525 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
16
DNS requests
21
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1108 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1832 | Email-Worm.Win32.NetSky.q | 108.178.0.170:25 | mx1.tmdhosting.com | SINGLEHOP-LLC | US | whitelisted |
1832 | Email-Worm.Win32.NetSky.q | 52.101.11.19:25 | adobe-com.mail.protection.outlook.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1832 | Email-Worm.Win32.NetSky.q | 17.57.165.2:25 | mx-in.g.apple.com | APPLE-ENGINEERING | US | whitelisted |
1832 | Email-Worm.Win32.NetSky.q | 202.12.124.217:25 | in2-smtp.messagingengine.com | — | — | unknown |
1832 | Email-Worm.Win32.NetSky.q | 51.81.61.70:25 | mx01.earthlink-vadesecure.net | OVH SAS | US | unknown |
1832 | Email-Worm.Win32.NetSky.q | 194.104.108.22:25 | de-smtp-inbound-1.mimecast.com | Mimecast Services Limited | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
sexnet.com |
| unknown |
mx1.tmdhosting.com |
| whitelisted |
adobe.com |
| whitelisted |
adobe-com.mail.protection.outlook.com |
| whitelisted |
apple.com |
| whitelisted |
mx-in-mdn.apple.com |
| whitelisted |
mx-in.g.apple.com |
| whitelisted |
pobox.com |
| unknown |
in2-smtp.messagingengine.com |
| unknown |