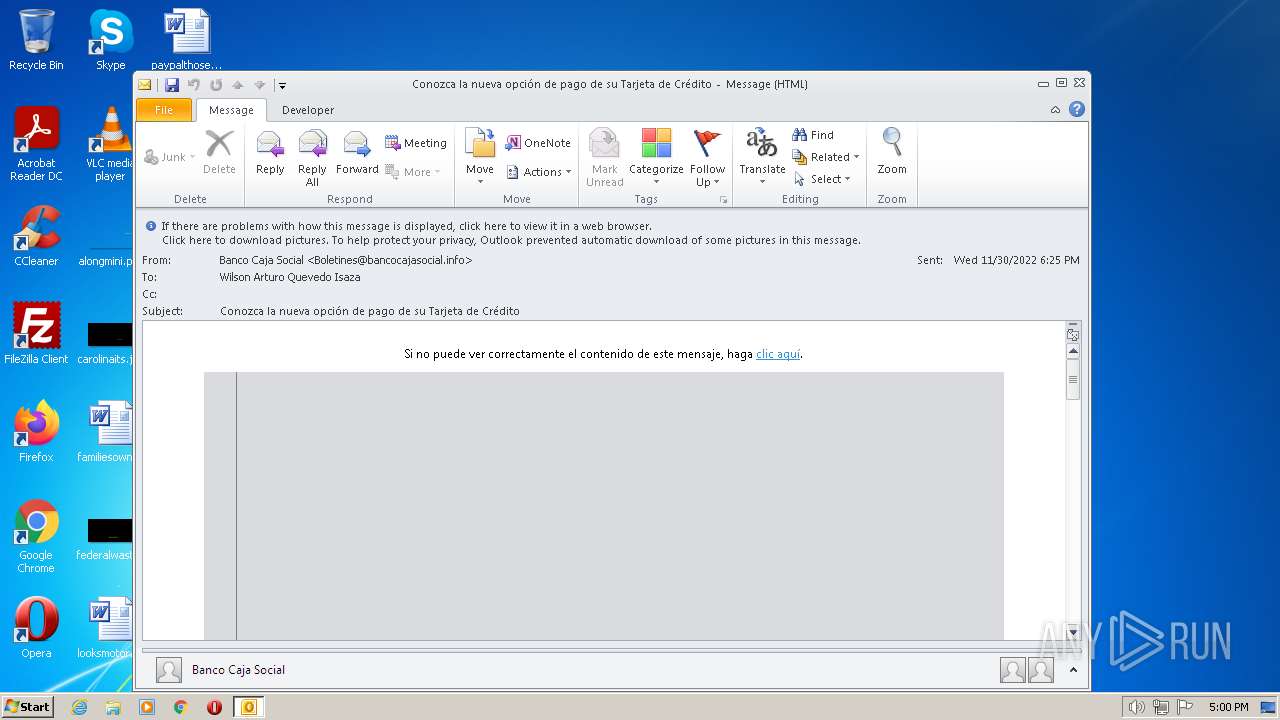
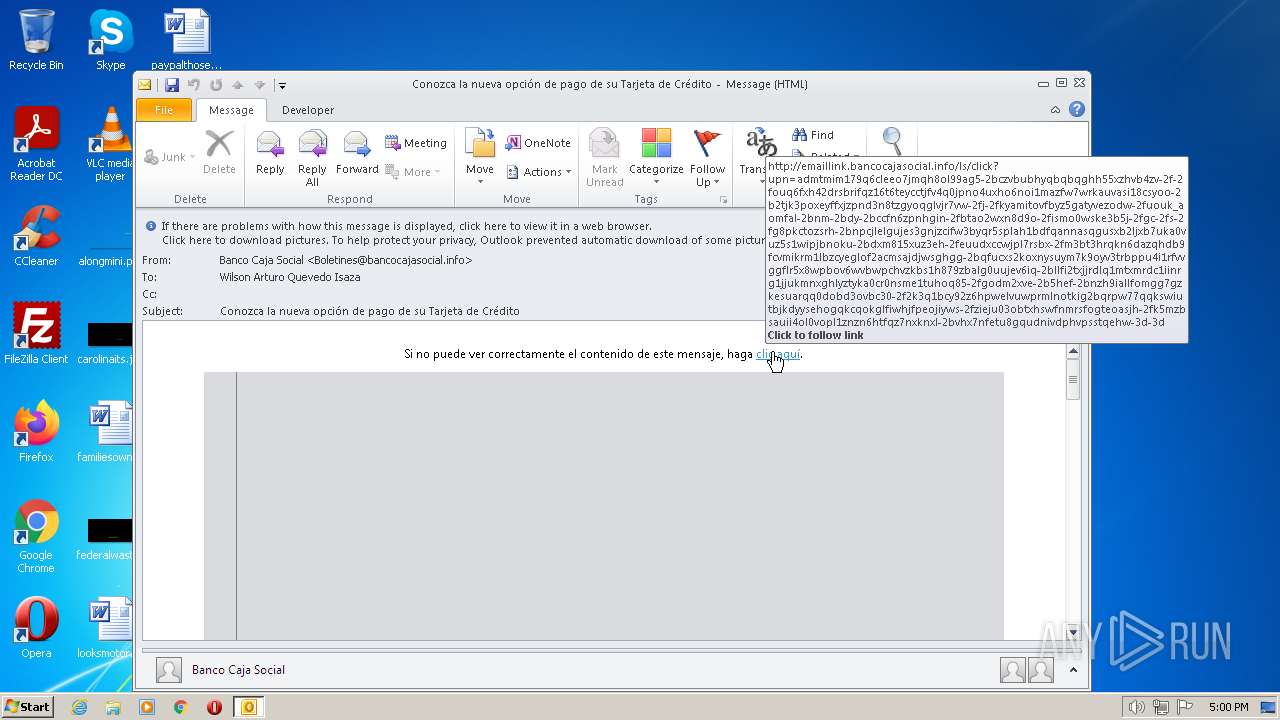
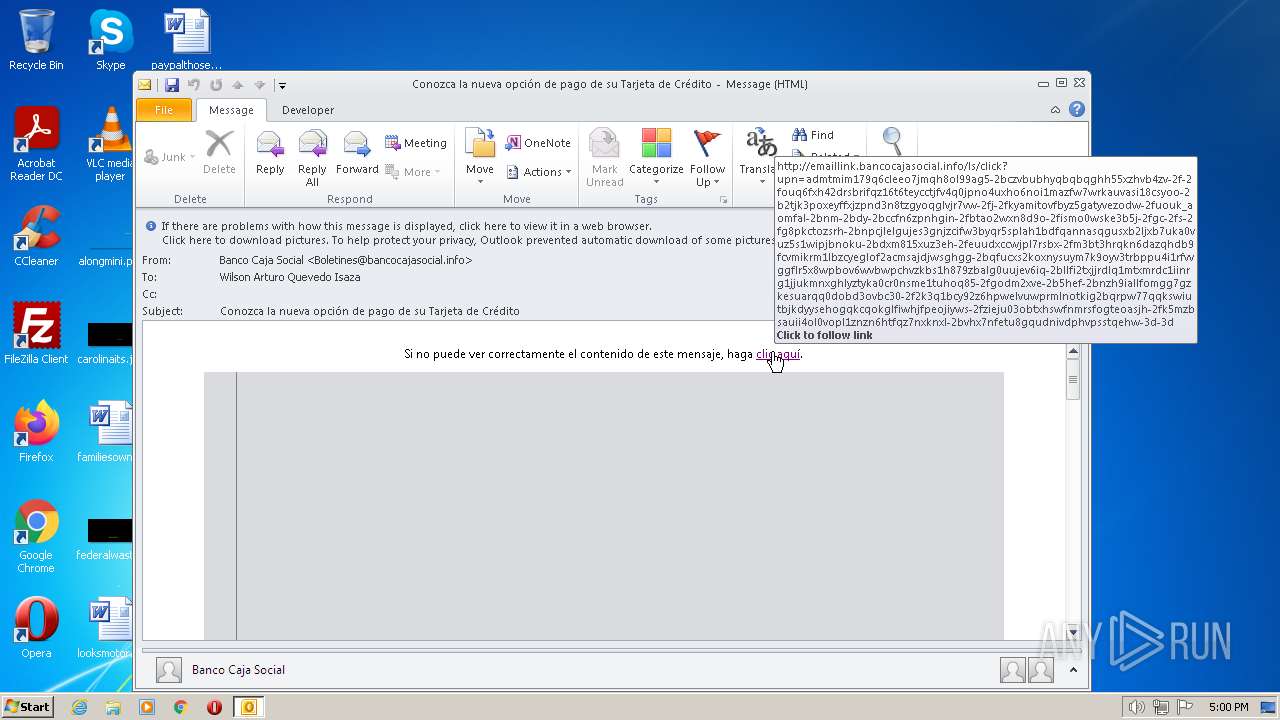
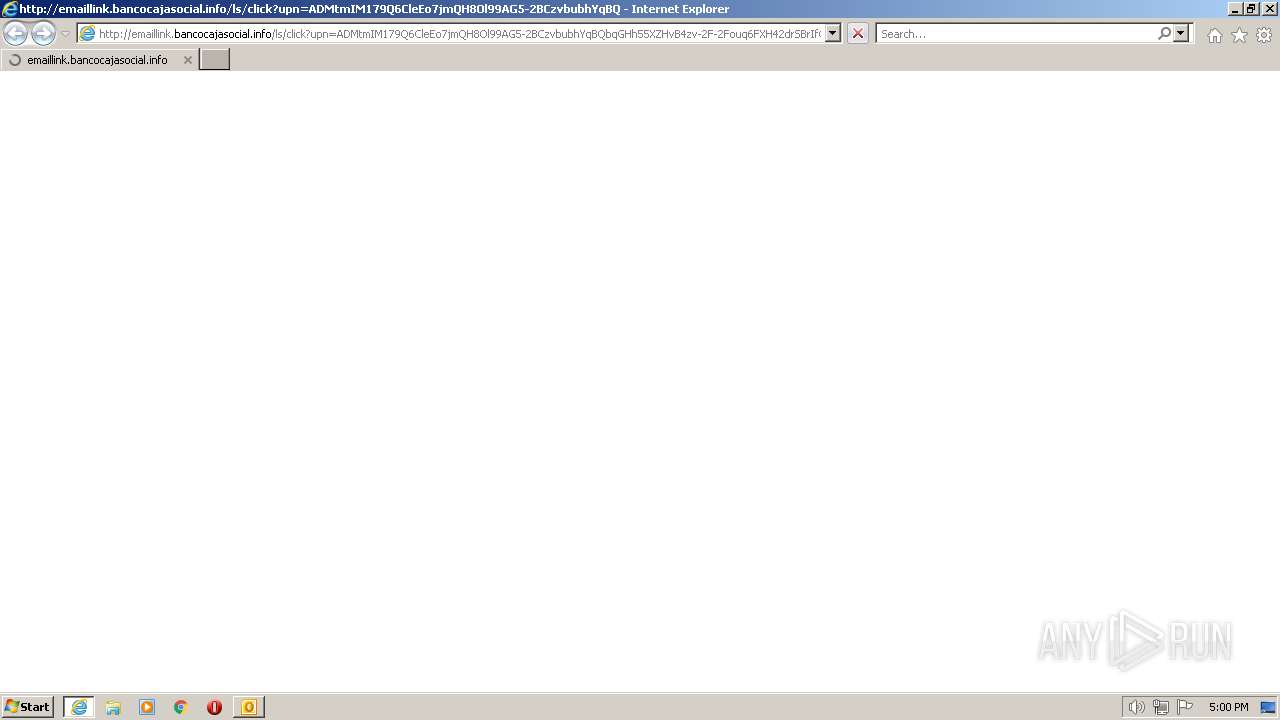
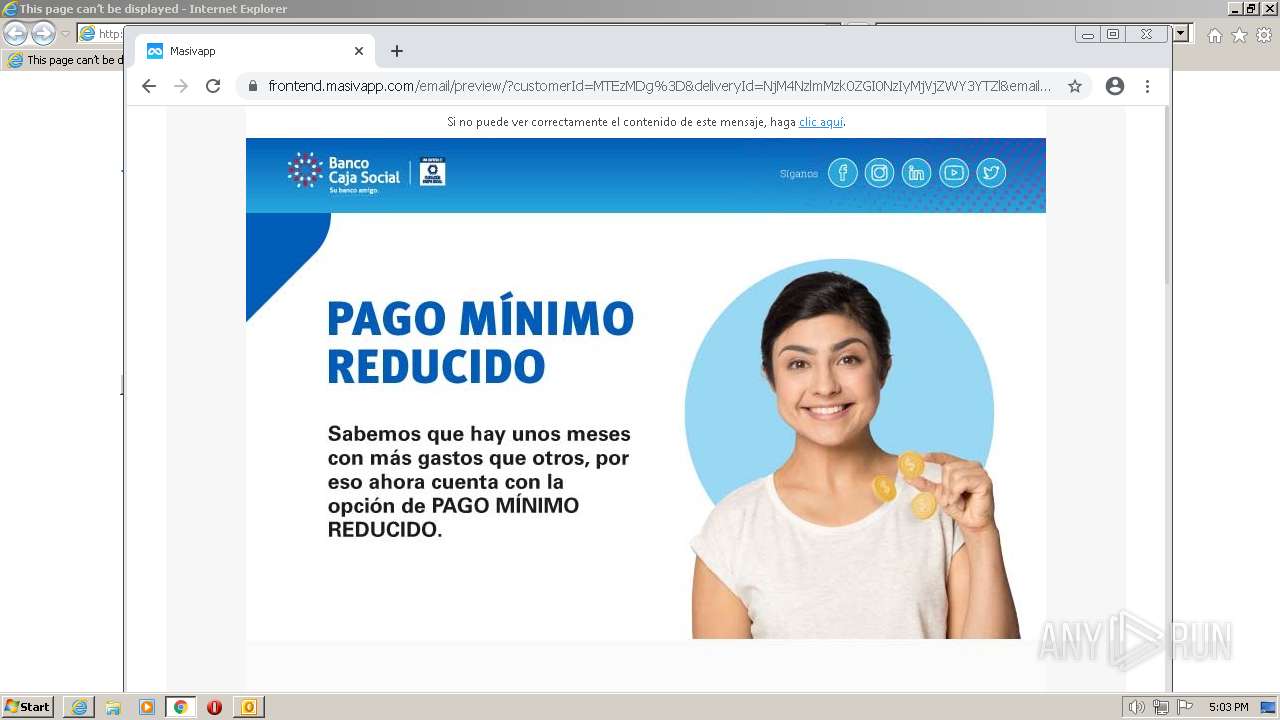
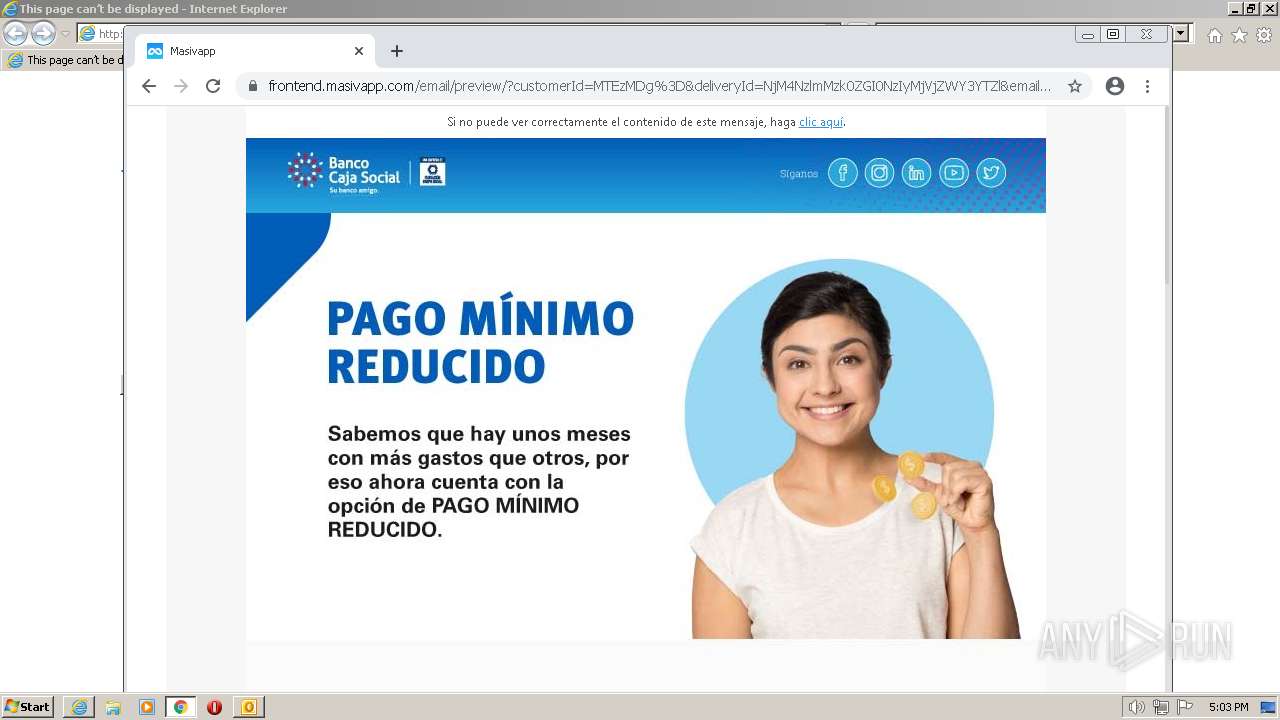
| File name: | Conozca la nueva opción de pago de su Tarjeta de Crédito.msg |
| Full analysis: | https://app.any.run/tasks/ca8f1800-734c-412c-860f-c6b5d554a94e |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2022, 17:00:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | BBEE3F952241FC5FA826603895D870C7 |
| SHA1: | 20D317122CC035EBBB382E9EF9B3C01C647416C3 |
| SHA256: | C8D456BEE4C0A79ECFCC66D6AA09B8508D3F139EECB33C32185697D030C47E75 |
| SSDEEP: | 768:nFTCjjXMTVK2q157GL1W53wFgXguT/mfD6Vq+zb34qcw7Q299TNEI5w4l5wUd3D0:nY3MVq1Z7PTm+wIb34y739rE0kU+Z0 |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Manual execution by a user
- chrome.exe (PID: 3128)
Application launched itself
- chrome.exe (PID: 3128)
- iexplore.exe (PID: 1808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
66
Monitored processes
28
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1024,16909477431536728111,10426348495718960696,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3584 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 292 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1024,16909477431536728111,10426348495718960696,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2932 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 788 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1024,16909477431536728111,10426348495718960696,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1704 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 996 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1024,16909477431536728111,10426348495718960696,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1608 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1220 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1024,16909477431536728111,10426348495718960696,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1856 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1328 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Conozca la nueva opción de pago de su Tarjeta de Crédito.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 1644 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,16909477431536728111,10426348495718960696,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1932 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
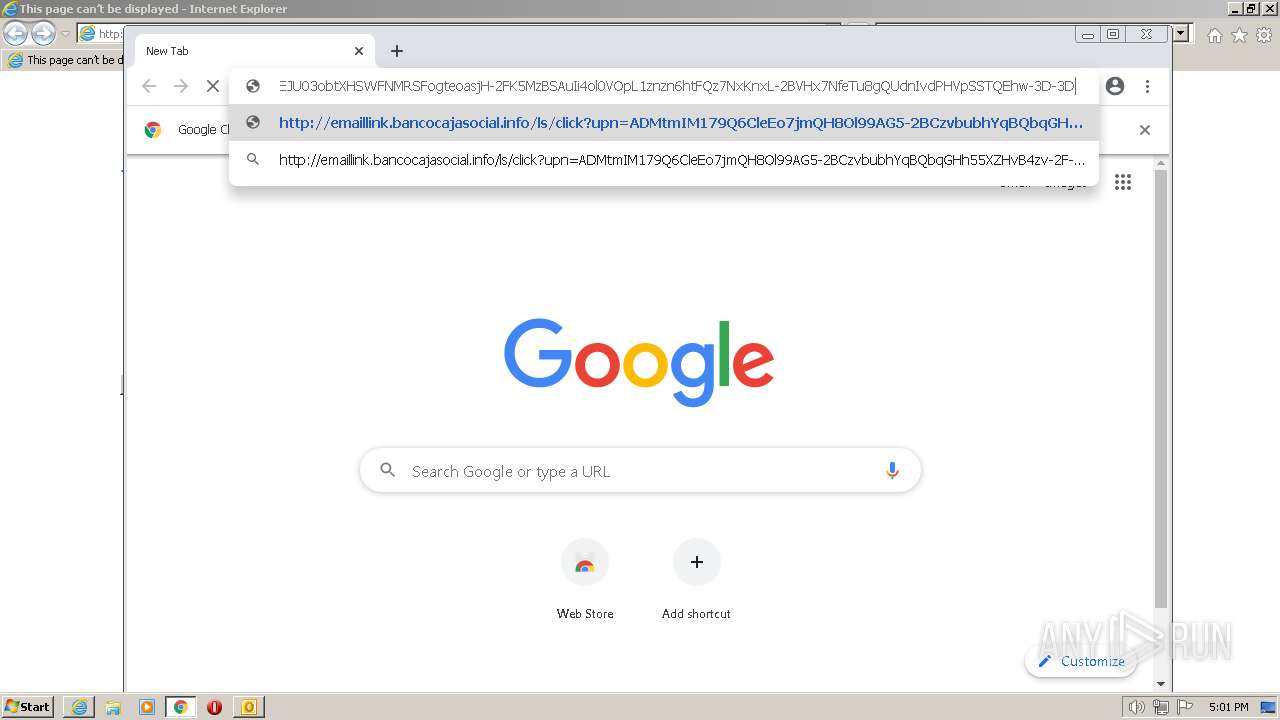
| 1808 | "C:\Program Files\Internet Explorer\iexplore.exe" http://emaillink.bancocajasocial.info/ls/click?upn=ADMtmIM179Q6CleEo7jmQH8Ol99AG5-2BCzvbubhYqBQbqGHh55XZHvB4zv-2F-2Fouq6FXH42drSBrIfQz16t6teYcCtjFV4Q0jPno4UXHO6nOI1MaZFw7WrKaUvAsI18csYOo-2B2tjk3poxeYFfXjZpnd3N8tZGYoQGlVjR7vw-2FJ-2FKYAMitOVFByz5GATyvEZoDw-2FuouK_AoMFAl-2BNM-2Bdy-2BcCFn6ZpnHgIN-2FbTAO2WXN8d9O-2FISMo0WSKE3b5J-2FGC-2Fs-2Fg8pkctOzSRH-2BNpcjlelgUJES3gNjzcifW3bYqr5sPlAh1bdfqANnasqGUSXB2LjXb7UkA0Vuz5S1wipjbnokU-2BDxm815XuZ3eH-2FeuuDxCCWjpl7rsbx-2Fm3bT3HRQKN6dazqHDB9fcvMikRM1LbzCyeGlof2aCMSaJdJWSgHGg-2BQFucXS2kOXNYsUym7K9OYv3TRBpPU4i1RFVVggFLR5X8wpboV6wvBWPChvZKbS1h879ZBALG0UUJev6iQ-2BlLfI2TXJJRDLq1MtXMrdC1Iinrg1JJUKmNXgHlYztykA0Cr0nSmE1TuHoQ85-2FGoDm2XVe-2B5HEf-2BNzH9iALLfOmgG7GzkEsuArqQ0dObD3ovbC30-2F2k3q1BCY92Z6HpWelvUwPRmlNOTkig2BqRPW77qqkSWIUTbjkdyysEhOGqKCqokgLfIWhjFPEOJIyWs-2FziEJU03obtXHSWFNMRSFogteoasjH-2FK5MzBSAuIi4ol0VOpL1znzn6htFQz7NxKnxL-2BVHx7NfeTu8gQUdnIvdPHVpSSTQEhw-3D-3D | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2292 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1024,16909477431536728111,10426348495718960696,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1740 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2308 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1024,16909477431536728111,10426348495718960696,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=2956 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
29 714
Read events
28 902
Write events
784
Delete events
28
Modification events
| (PID) Process: | (1328) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1328) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1328) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1328) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1328) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1328) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1328) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1328) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1328) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (1328) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
152
Text files
174
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1328 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVREFD4.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1328 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 1328 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 1328 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 2408 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:— | SHA256:— | |||
| 2408 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | der | |
MD5:— | SHA256:— | |||
| 2408 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | der | |
MD5:— | SHA256:— | |||
| 2408 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:— | SHA256:— | |||
| 2408 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2408 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\FC58E2B0A083F55A6C117565DA30A892 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
95
DNS requests
55
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | — | — | whitelisted |
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acjgztdbjqsnhhrv3mj6jj7z76ja_2896/jflookgnkcckhobaglndicnbbgbonegd_2896_all_mzwjwhzvfrv7zmanzi2bxlcnqi.crx3 | US | — | — | whitelisted |
2408 | iexplore.exe | GET | 200 | 104.18.32.68:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQDGy4fCbGU9PA9hJIqWLBqP | US | der | 472 b | whitelisted |
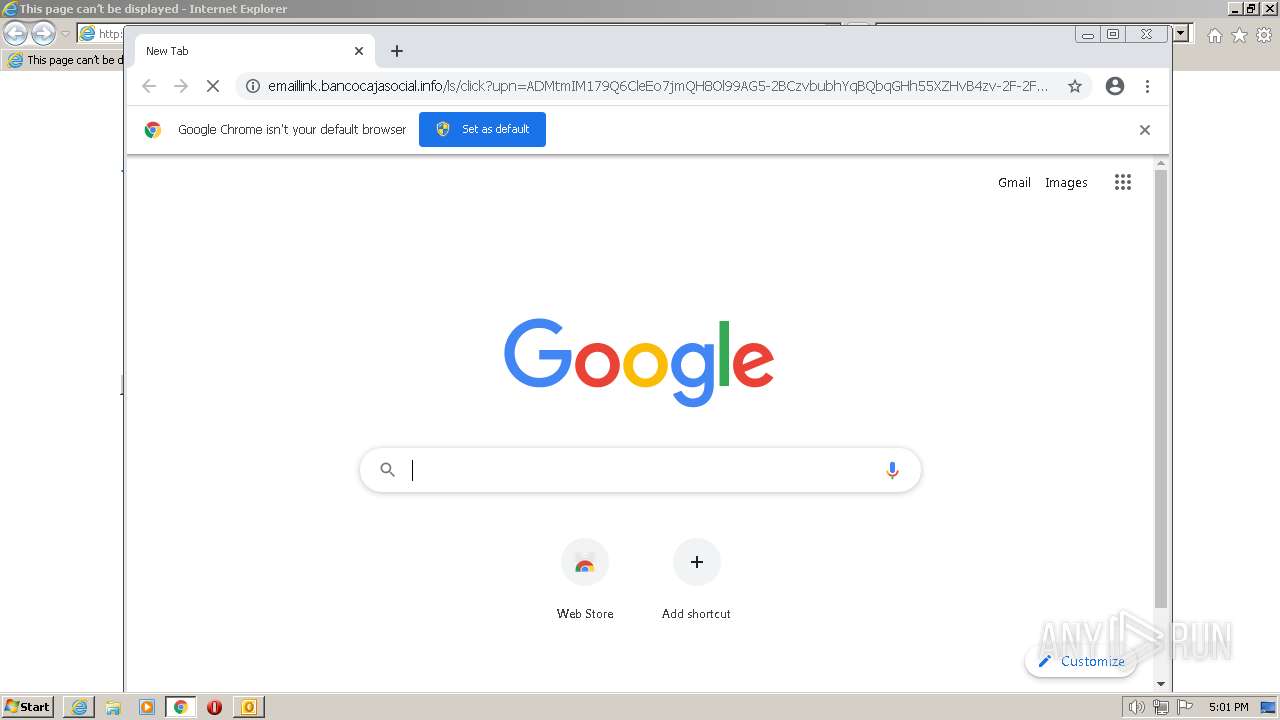
2408 | iexplore.exe | GET | 302 | 167.89.123.54:80 | http://emaillink.bancocajasocial.info/ls/click?upn=ADMtmIM179Q6CleEo7jmQH8Ol99AG5-2BCzvbubhYqBQbqGHh55XZHvB4zv-2F-2Fouq6FXH42drSBrIfQz16t6teYcCtjFV4Q0jPno4UXHO6nOI1MaZFw7WrKaUvAsI18csYOo-2B2tjk3poxeYFfXjZpnd3N8tZGYoQGlVjR7vw-2FJ-2FKYAMitOVFByz5GATyvEZoDw-2FuouK_AoMFAl-2BNM-2Bdy-2BcCFn6ZpnHgIN-2FbTAO2WXN8d9O-2FISMo0WSKE3b5J-2FGC-2Fs-2Fg8pkctOzSRH-2BNpcjlelgUJES3gNjzcifW3bYqr5sPlAh1bdfqANnasqGUSXB2LjXb7UkA0Vuz5S1wipjbnokU-2BDxm815XuZ3eH-2FeuuDxCCWjpl7rsbx-2Fm3bT3HRQKN6dazqHDB9fcvMikRM1LbzCyeGlof2aCMSaJdJWSgHGg-2BQFucXS2kOXNYsUym7K9OYv3TRBpPU4i1RFVVggFLR5X8wpboV6wvBWPChvZKbS1h879ZBALG0UUJev6iQ-2BlLfI2TXJJRDLq1MtXMrdC1Iinrg1JJUKmNXgHlYztykA0Cr0nSmE1TuHoQ85-2FGoDm2XVe-2B5HEf-2BNzH9iALLfOmgG7GzkEsuArqQ0dObD3ovbC30-2F2k3q1BCY92Z6HpWelvUwPRmlNOTkig2BqRPW77qqkSWIUTbjkdyysEhOGqKCqokgLfIWhjFPEOJIyWs-2FziEJU03obtXHSWFNMRSFogteoasjH-2FK5MzBSAuIi4ol0VOpL1znzn6htFQz7NxKnxL-2BVHx7NfeTu8gQUdnIvdPHVpSSTQEhw-3D-3D | US | html | 153 b | suspicious |
1808 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2408 | iexplore.exe | GET | 200 | 104.18.32.68:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 1.42 Kb | whitelisted |
1808 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
2408 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 2.18 Kb | whitelisted |
3612 | chrome.exe | GET | 302 | 167.89.123.124:80 | http://emaillink.bancocajasocial.info/ls/click?upn=ADMtmIM179Q6CleEo7jmQH8Ol99AG5-2BCzvbubhYqBQbqGHh55XZHvB4zv-2F-2Fouq6FXH42drSBrIfQz16t6teYcCtjFV4Q0jPno4UXHO6nOI1MaZFw7WrKaUvAsI18csYOo-2B2tjk3poxeYFfXjZpnd3N8tZGYoQGlVjR7vw-2FJ-2FKYAMitOVFByz5GATyvEZoDw-2FuouK_AoMFAl-2BNM-2Bdy-2BcCFn6ZpnHgIN-2FbTAO2WXN8d9O-2FISMo0WSKE3b5J-2FGC-2Fs-2Fg8pkctOzSRH-2BNpcjlelgUJES3gNjzcifW3bYqr5sPlAh1bdfqANnasqGUSXB2LjXb7UkA0Vuz5S1wipjbnokU-2BDxm815XuZ3eH-2FeuuDxCCWjpl7rsbx-2Fm3bT3HRQKN6dazqHDB9fcvMikRM1LbzCyeGlof2aCMSaJdJWSgHGg-2BQFucXS2kOXNYsUym7K9OYv3TRBpPU4i1RFVVggFLR5X8wpboV6wvBWPChvZKbS1h879ZBALG0UUJev6iQ-2BlLfI2TXJJRDLq1MtXMrdC1Iinrg1JJUKmNXgHlYztykA0Cr0nSmE1TuHoQ85-2FGoDm2XVe-2B5HEf-2BNzH9iALLfOmgG7GzkEsuArqQ0dObD3ovbC30-2F2k3q1BCY92Z6HpWelvUwPRmlNOTkig2BqRPW77qqkSWIUTbjkdyysEhOGqKCqokgLfIWhjFPEOJIyWs-2FziEJU03obtXHSWFNMRSFogteoasjH-2FK5MzBSAuIi4ol0VOpL1znzn6htFQz7NxKnxL-2BVHx7NfeTu8gQUdnIvdPHVpSSTQEhw-3D-3D | US | html | 153 b | suspicious |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 38.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3612 | chrome.exe | 142.250.185.237:443 | accounts.google.com | GOOGLE | US | suspicious |
3612 | chrome.exe | 142.250.186.46:443 | clients2.google.com | GOOGLE | US | whitelisted |
3612 | chrome.exe | 216.58.212.161:443 | clients2.googleusercontent.com | GOOGLE | US | whitelisted |
3612 | chrome.exe | 142.250.186.131:443 | www.gstatic.com | GOOGLE | US | whitelisted |
3612 | chrome.exe | 142.250.185.202:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
1328 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2408 | iexplore.exe | 167.89.123.54:80 | emaillink.bancocajasocial.info | SENDGRID | US | suspicious |
2408 | iexplore.exe | 34.225.253.91:443 | api.masiv.masivian.com | AMAZON-AES | US | unknown |
2408 | iexplore.exe | 8.238.29.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
2408 | iexplore.exe | 104.18.32.68:80 | ocsp.comodoca.com | CLOUDFLARENET | — | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
dns.msftncsi.com |
| shared |
emaillink.bancocajasocial.info |
| suspicious |
api.masiv.masivian.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
frontend.masivapp.com |
| suspicious |
api.bing.com |
| whitelisted |