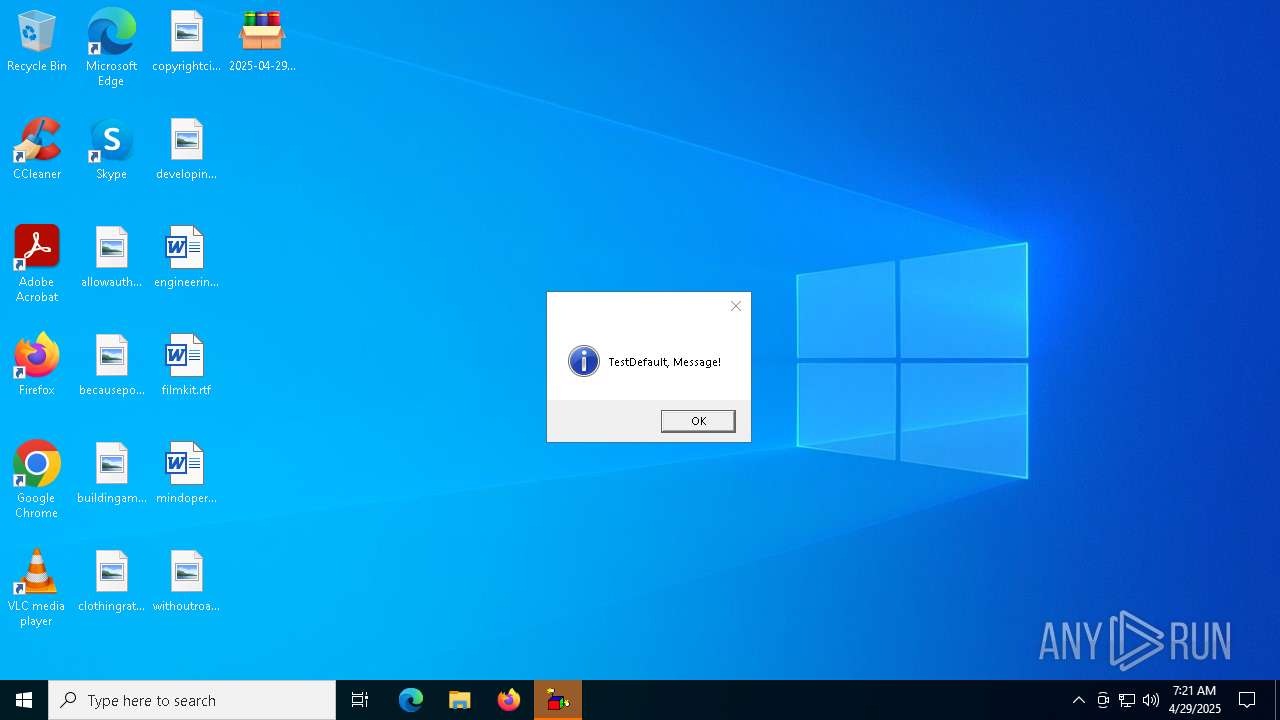
| File name: | 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer |
| Full analysis: | https://app.any.run/tasks/dbe37134-b913-476b-9d2e-2bb5e881e51a |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | April 29, 2025, 07:21:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 7871E79DF85901E4C6C6D74DBD0FD02F |
| SHA1: | 61CFAA7EA349B62A873FA4D7363B4F95F4AC4BBA |
| SHA256: | C8CB16F5495F84F15DCF844CFD3FC018BA3248D5252A3EFAE61DF2C60B84AC06 |
| SSDEEP: | 98304:HFrKdV/oZ648yOHjTBpppa2hWF05rtZ7F7oH5NihydnocnDngrtmTdm1DAEWJY13:HRCggh8u |
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 7456)
DCRAT mutex has been found
- refperf.exe (PID: 7840)
UAC/LUA settings modification
- refperf.exe (PID: 7840)
SUSPICIOUS
Executable content was dropped or overwritten
- 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer.exe (PID: 7412)
- refperf.exe (PID: 7840)
Reads security settings of Internet Explorer
- 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer.exe (PID: 7412)
- ShellExperienceHost.exe (PID: 8040)
- refperf.exe (PID: 7632)
- refperf.exe (PID: 7840)
Reads the date of Windows installation
- 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer.exe (PID: 7412)
- refperf.exe (PID: 7632)
- refperf.exe (PID: 7840)
Executing commands from a ".bat" file
- wscript.exe (PID: 7456)
- refperf.exe (PID: 7840)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 7456)
- refperf.exe (PID: 7632)
- refperf.exe (PID: 7840)
The process executes VB scripts
- 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer.exe (PID: 7412)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7456)
The process creates files with name similar to system file names
- refperf.exe (PID: 7840)
Executed via WMI
- schtasks.exe (PID: 2852)
- schtasks.exe (PID: 516)
- schtasks.exe (PID: 4408)
- schtasks.exe (PID: 6644)
- schtasks.exe (PID: 4896)
- schtasks.exe (PID: 5608)
- schtasks.exe (PID: 680)
- schtasks.exe (PID: 5392)
- schtasks.exe (PID: 5800)
- schtasks.exe (PID: 6004)
- schtasks.exe (PID: 7352)
- schtasks.exe (PID: 7300)
- schtasks.exe (PID: 900)
- schtasks.exe (PID: 6620)
- schtasks.exe (PID: 920)
- schtasks.exe (PID: 4608)
- schtasks.exe (PID: 3096)
- schtasks.exe (PID: 1272)
- schtasks.exe (PID: 7436)
- schtasks.exe (PID: 7344)
- schtasks.exe (PID: 7184)
- schtasks.exe (PID: 7336)
- schtasks.exe (PID: 7444)
- schtasks.exe (PID: 632)
- schtasks.exe (PID: 1328)
- schtasks.exe (PID: 5984)
- schtasks.exe (PID: 736)
- schtasks.exe (PID: 7320)
- schtasks.exe (PID: 7220)
- schtasks.exe (PID: 7216)
- schtasks.exe (PID: 6724)
- schtasks.exe (PID: 7560)
- schtasks.exe (PID: 7516)
- schtasks.exe (PID: 7592)
- schtasks.exe (PID: 7764)
- schtasks.exe (PID: 7548)
Likely accesses (executes) a file from the Public directory
- schtasks.exe (PID: 7592)
- schtasks.exe (PID: 7516)
- schtasks.exe (PID: 7764)
- slui.exe (PID: 4200)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 7604)
INFO
The sample compiled with english language support
- 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer.exe (PID: 7412)
- refperf.exe (PID: 7840)
Drops encrypted VBS script (Microsoft Script Encoder)
- 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer.exe (PID: 7412)
Reads the computer name
- 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer.exe (PID: 7412)
- refperf.exe (PID: 7632)
- refperf.exe (PID: 7840)
- ShellExperienceHost.exe (PID: 8040)
- OfficeClickToRun.exe (PID: 5260)
- csrss.exe (PID: 5384)
- ctfmon.exe (PID: 7808)
- ctfmon.exe (PID: 7692)
- upfc.exe (PID: 7600)
- UserOOBEBroker.exe (PID: 3768)
- Registry.exe (PID: 8104)
- UserOOBEBroker.exe (PID: 1184)
- MoUsoCoreWorker.exe (PID: 4620)
- cmd.exe (PID: 7356)
- cmd.exe (PID: 6564)
- RuntimeBroker.exe (PID: 7924)
- slui.exe (PID: 4200)
- lsass.exe (PID: 7348)
- ctfmon.exe (PID: 7436)
Checks supported languages
- 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer.exe (PID: 7412)
- refperf.exe (PID: 7632)
- refperf.exe (PID: 7840)
- ShellExperienceHost.exe (PID: 8040)
- OfficeClickToRun.exe (PID: 5260)
- csrss.exe (PID: 5384)
- ctfmon.exe (PID: 7808)
- ctfmon.exe (PID: 7692)
- upfc.exe (PID: 7600)
- Registry.exe (PID: 8104)
- UserOOBEBroker.exe (PID: 3768)
- UserOOBEBroker.exe (PID: 1184)
- RuntimeBroker.exe (PID: 7924)
- cmd.exe (PID: 6564)
- MoUsoCoreWorker.exe (PID: 4620)
- cmd.exe (PID: 7356)
- slui.exe (PID: 4200)
- lsass.exe (PID: 7348)
- ctfmon.exe (PID: 7436)
Process checks computer location settings
- 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer.exe (PID: 7412)
- refperf.exe (PID: 7632)
- refperf.exe (PID: 7840)
Reads Environment values
- refperf.exe (PID: 7632)
- refperf.exe (PID: 7840)
- csrss.exe (PID: 5384)
- OfficeClickToRun.exe (PID: 5260)
- ctfmon.exe (PID: 7808)
- Registry.exe (PID: 8104)
- upfc.exe (PID: 7600)
- ctfmon.exe (PID: 7692)
- UserOOBEBroker.exe (PID: 3768)
- UserOOBEBroker.exe (PID: 1184)
- RuntimeBroker.exe (PID: 7924)
- cmd.exe (PID: 6564)
- slui.exe (PID: 4200)
- lsass.exe (PID: 7348)
- MoUsoCoreWorker.exe (PID: 4620)
- cmd.exe (PID: 7356)
- ctfmon.exe (PID: 7436)
Reads the machine GUID from the registry
- refperf.exe (PID: 7632)
- refperf.exe (PID: 7840)
- csrss.exe (PID: 5384)
- OfficeClickToRun.exe (PID: 5260)
- ctfmon.exe (PID: 7808)
- upfc.exe (PID: 7600)
- ctfmon.exe (PID: 7692)
- Registry.exe (PID: 8104)
- UserOOBEBroker.exe (PID: 3768)
- UserOOBEBroker.exe (PID: 1184)
- RuntimeBroker.exe (PID: 7924)
- cmd.exe (PID: 6564)
- slui.exe (PID: 4200)
- MoUsoCoreWorker.exe (PID: 4620)
- cmd.exe (PID: 7356)
- ctfmon.exe (PID: 7436)
- lsass.exe (PID: 7348)
Creates files in the program directory
- refperf.exe (PID: 7840)
Process checks whether UAC notifications are on
- refperf.exe (PID: 7840)
Manual execution by a user
- csrss.exe (PID: 5384)
- OfficeClickToRun.exe (PID: 5260)
- ctfmon.exe (PID: 7692)
- ctfmon.exe (PID: 7808)
- upfc.exe (PID: 7600)
- UserOOBEBroker.exe (PID: 1184)
- UserOOBEBroker.exe (PID: 3768)
- Registry.exe (PID: 8104)
- cmd.exe (PID: 6564)
- RuntimeBroker.exe (PID: 7924)
- MoUsoCoreWorker.exe (PID: 4620)
- cmd.exe (PID: 7356)
- lsass.exe (PID: 7348)
- slui.exe (PID: 4200)
Create files in a temporary directory
- refperf.exe (PID: 7840)
Checks proxy server information
- slui.exe (PID: 7864)
Reads the software policy settings
- slui.exe (PID: 7864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:12:01 18:00:55+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 201216 |
| InitializedDataSize: | 255488 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1ec40 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
189
Monitored processes
65
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | w32tm /stripchart /computer:localhost /period:5 /dataonly /samples:2 | C:\Windows\System32\w32tm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Time Service Diagnostic Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | schtasks.exe /create /tn "OfficeClickToRunO" /sc MINUTE /mo 7 /tr "'C:\Program Files\Adobe\Acrobat DC\Esl\OfficeClickToRun.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | schtasks.exe /create /tn "cmdc" /sc MINUTE /mo 8 /tr "'C:\Recovery\OEM\cmd.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | schtasks.exe /create /tn "upfcu" /sc MINUTE /mo 9 /tr "'C:\Windows\ELAMBKUP\upfc.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | schtasks.exe /create /tn "lsassl" /sc MINUTE /mo 12 /tr "'C:\Program Files\Microsoft Update Health Tools\Logs\lsass.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | schtasks.exe /create /tn "csrss" /sc ONLOGON /tr "'C:\Program Files (x86)\WindowsPowerShell\csrss.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | schtasks.exe /create /tn "OfficeClickToRunO" /sc MINUTE /mo 14 /tr "'C:\Program Files\Adobe\Acrobat DC\Esl\OfficeClickToRun.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | C:\Recovery\OEM\UserOOBEBroker.exe | C:\Recovery\OEM\UserOOBEBroker.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
| 1272 | schtasks.exe /create /tn "RuntimeBrokerR" /sc MINUTE /mo 10 /tr "'C:\BrowserSavesBrokerPerf\RuntimeBroker.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | schtasks.exe /create /tn "cmd" /sc ONLOGON /tr "'C:\Recovery\OEM\cmd.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 500
Read events
11 479
Write events
21
Delete events
0
Modification events
| (PID) Process: | (7412) 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\ApplicationAssociationToasts |
| Operation: | write | Name: | VBEFile_.vbe |
Value: 0 | |||
| (PID) Process: | (7412) 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbe\OpenWithProgids |
| Operation: | write | Name: | VBEFile |
Value: | |||
| (PID) Process: | (7412) 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (7412) 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (7412) 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (7412) 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (7412) 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (7840) refperf.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (7840) refperf.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | ConsentPromptBehaviorAdmin |
Value: 0 | |||
| (PID) Process: | (7840) refperf.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | PromptOnSecureDesktop |
Value: 0 | |||
Executable files
13
Suspicious files
1
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7412 | 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer.exe | C:\BrowserSavesBrokerPerf\file.vbs | text | |
MD5:677CC4360477C72CB0CE00406A949C61 | SHA256:F1CCCB5AE4AA51D293BD3C7D2A1A04CB7847D22C5DB8E05AC64E9A6D7455AA0B | |||
| 7412 | 2025-04-29_7871e79df85901e4c6c6d74dbd0fd02f_black-basta_chapak_cova_cryptbot_darkgate_elex_hawkeye_luca-stealer.exe | C:\BrowserSavesBrokerPerf\QcSGzCLsdB9RkesO0hvmc.bat | text | |
MD5:6F788E31EC894BA143DF1B2962A7C49C | SHA256:01A8FA52E621250394415845BD2A968752C4192975E15FFA84878C5ABF5947D5 | |||
| 7840 | refperf.exe | C:\Program Files\Adobe\Acrobat DC\Esl\e6c9b481da804f | text | |
MD5:35CC3675660F365FC0596FC761D324F5 | SHA256:C57E9BBFD203CCD26D1B6D2182F4307526CF374DAC737349F8FC732D566D394D | |||
| 7840 | refperf.exe | C:\Windows\ELAMBKUP\ea1d8f6d871115 | text | |
MD5:DAFFD5696843DABF1E99E6E9EB6C0775 | SHA256:286F550E36BF08FE525B59B61759327EA8579F5D32D4C3C47AAD84486987456F | |||
| 7840 | refperf.exe | C:\BrowserSavesBrokerPerf\ctfmon.exe | executable | |
MD5:07A9953B03F7F5A93233DA11DE668B07 | SHA256:1AFB51C3A10639AA712772D9A5B4B64CF360D3954D2793D7498536BD839A37C4 | |||
| 7840 | refperf.exe | C:\Windows\ELAMBKUP\Registry.exe | executable | |
MD5:07A9953B03F7F5A93233DA11DE668B07 | SHA256:1AFB51C3A10639AA712772D9A5B4B64CF360D3954D2793D7498536BD839A37C4 | |||
| 7840 | refperf.exe | C:\Windows\ELAMBKUP\upfc.exe | executable | |
MD5:07A9953B03F7F5A93233DA11DE668B07 | SHA256:1AFB51C3A10639AA712772D9A5B4B64CF360D3954D2793D7498536BD839A37C4 | |||
| 7840 | refperf.exe | C:\Windows\ELAMBKUP\ee2ad38f3d4382 | text | |
MD5:A6BC24FB411678998D37D539267C8080 | SHA256:833AA5A39191007DE3FBDD61A593570F3A8746C6712F38034681E8DA91701A99 | |||
| 7840 | refperf.exe | C:\BrowserSavesBrokerPerf\26c12092da979c | text | |
MD5:9157DC08489067327FA7C8709EB094A7 | SHA256:B79DF5572439DBED7B3472CC06ED89B88A4099F7CC570FA2EDAC068A957201CC | |||
| 7840 | refperf.exe | C:\Program Files\Adobe\Acrobat DC\Esl\OfficeClickToRun.exe | executable | |
MD5:07A9953B03F7F5A93233DA11DE668B07 | SHA256:1AFB51C3A10639AA712772D9A5B4B64CF360D3954D2793D7498536BD839A37C4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
50
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 172.202.163.200:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 172.202.163.200:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
7548 | SIHClient.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7548 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 40.69.42.241:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
7548 | SIHClient.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
7548 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7548 | SIHClient.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
7548 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
7548 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
— | — | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7548 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |