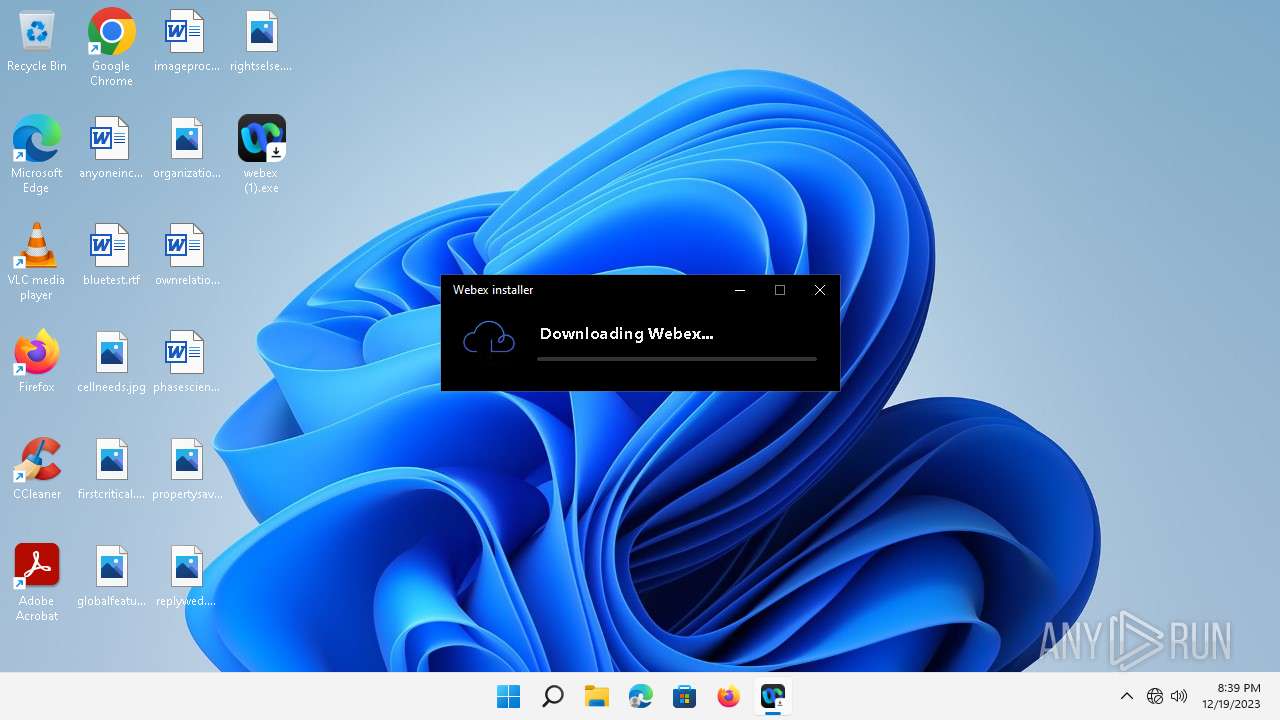
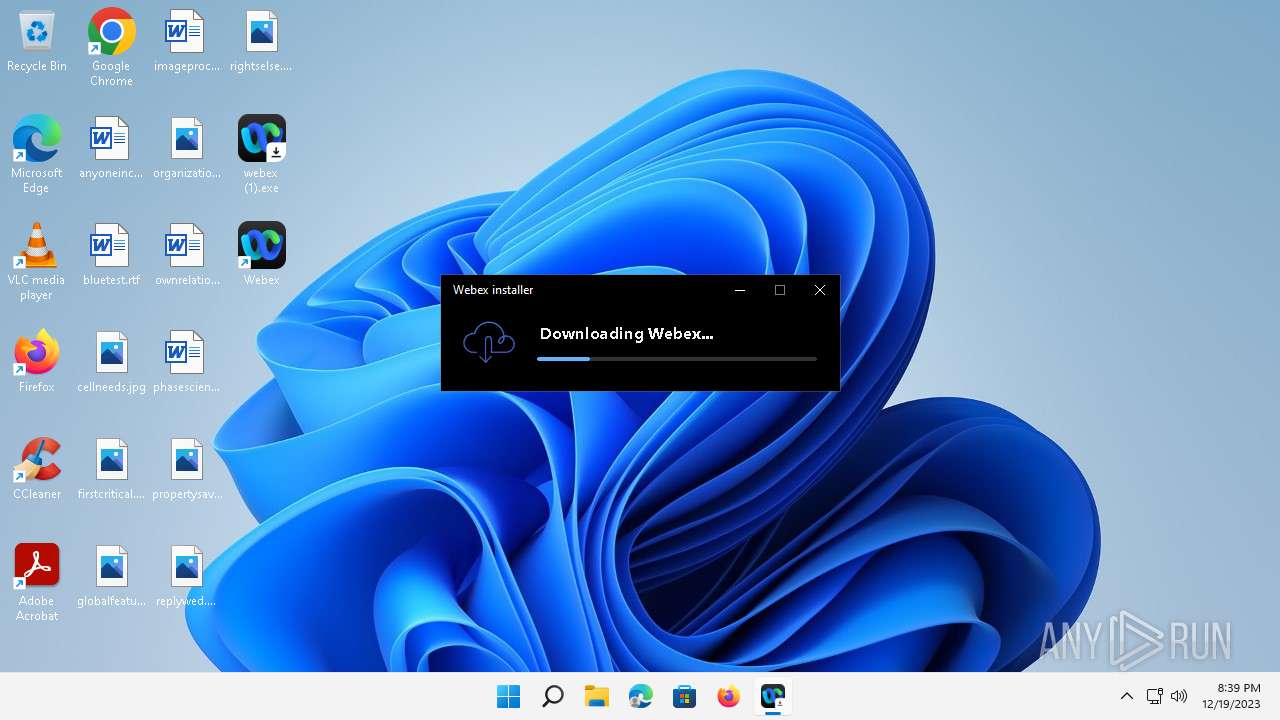
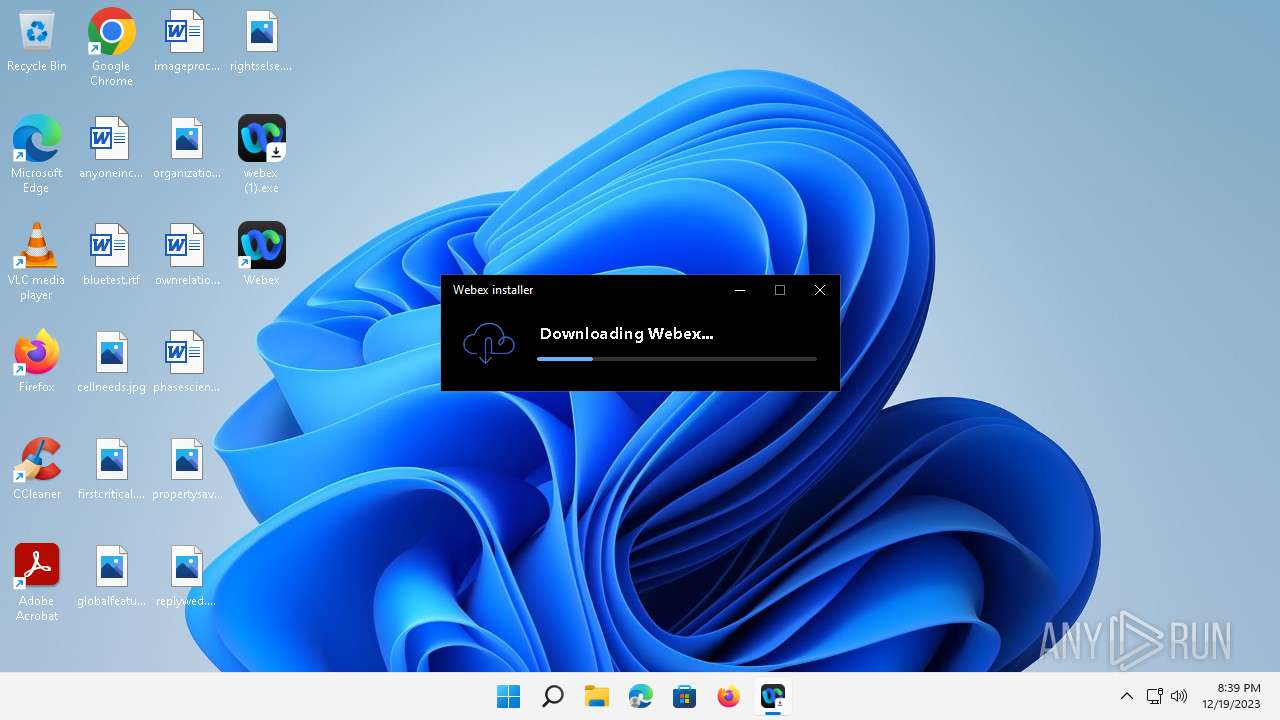
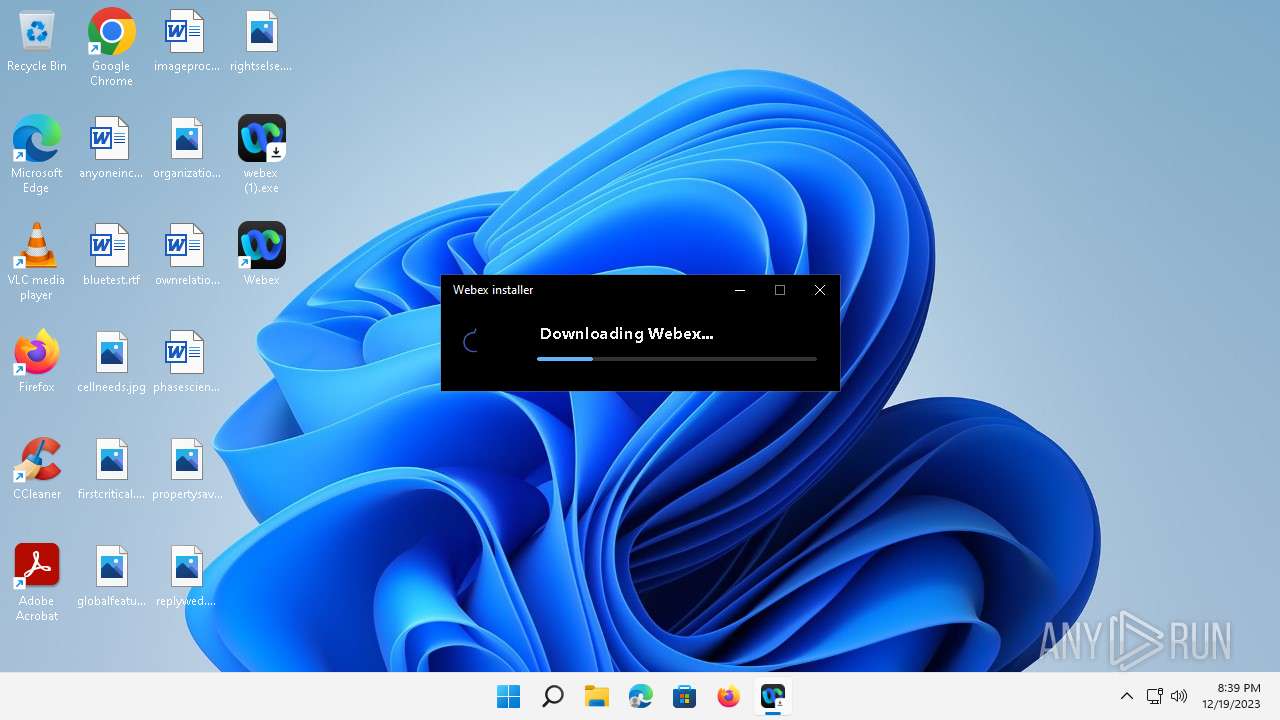
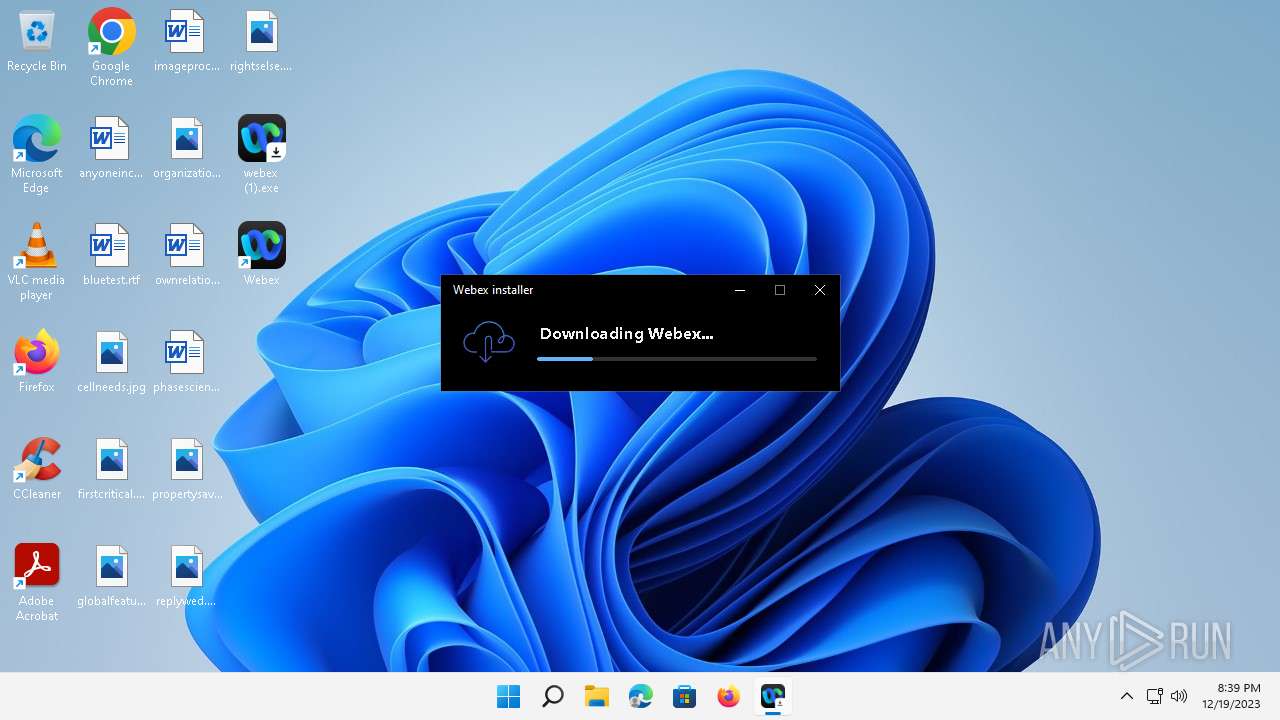
| File name: | webex (1).exe |
| Full analysis: | https://app.any.run/tasks/8a6ebe9a-0d2b-40d5-afa2-07fe7245230b |
| Verdict: | Malicious activity |
| Analysis date: | December 19, 2023, 20:39:08 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 4BEC11DFBBBCD15DADCE0C0A1A2F5999 |
| SHA1: | B064BAD795000799D5C3FF189AEBCAADEAF11C21 |
| SHA256: | C8C6ED9AA5DA354BFE9D9582827685537966DF9E2DB779A55A9B00A08678C164 |
| SSDEEP: | 49152:H05zqEqngpN6Foh2xUTxxKRD5QeyfFRshTmnevk9i5LQrzFr9OrY/uEakEgVgM/Z:sqEqnk6yh2xSKRD1Iidme8Q5LWxr97G8 |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 2192)
SUSPICIOUS
Reads settings of System Certificates
- webex (1).exe (PID: 1728)
Reads the Internet Settings
- webex (1).exe (PID: 1728)
Checks Windows Trust Settings
- msiexec.exe (PID: 2192)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2192)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 2364)
The process creates files with name similar to system file names
- msiexec.exe (PID: 2192)
INFO
Create files in a temporary directory
- webex (1).exe (PID: 1728)
Checks supported languages
- webex (1).exe (PID: 1728)
- msiexec.exe (PID: 2192)
- msiexec.exe (PID: 2364)
- msiexec.exe (PID: 4800)
Reads the computer name
- webex (1).exe (PID: 1728)
- msiexec.exe (PID: 2192)
- msiexec.exe (PID: 2364)
- msiexec.exe (PID: 4800)
Checks proxy server information
- webex (1).exe (PID: 1728)
Reads the machine GUID from the registry
- msiexec.exe (PID: 2192)
Creates files or folders in the user directory
- msiexec.exe (PID: 2192)
Application launched itself
- msiexec.exe (PID: 2192)
Reads Environment values
- msiexec.exe (PID: 4800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (76) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.6) |
| .exe | | | Generic Win/DOS Executable (5.6) |
| .exe | | | DOS Executable Generic (5.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:07:06 04:40:45+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.32 |
| CodeSize: | 1376256 |
| InitializedDataSize: | 53248 |
| UninitializedDataSize: | 2711552 |
| EntryPoint: | 0x3e56f0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.12.2.26612 |
| ProductVersionNumber: | 2.12.2.26612 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Unknown (1809) |
| CharacterSet: | Unicode |
| CompanyName: | Cisco Systems, Inc |
| FileDescription: | Webex |
| FileVersion: | 2.12.2.26612 |
| InternalName: | Webex |
| LegalCopyright: | Copyright (C) 2022 Cisco Systems Inc. |
| OriginalFileName: | - |
| ProductName: | Webex |
| ProductVersion: | 2.12.2.26612 |
Total processes
106
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1404 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1728 | "C:\Users\admin\Desktop\webex (1).exe" | C:\Users\admin\Desktop\webex (1).exe | explorer.exe | ||||||||||||
User: admin Company: Cisco Systems, Inc Integrity Level: MEDIUM Description: Webex Exit code: 0 Version: 2.12.2.26612 Modules
| |||||||||||||||
| 2192 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | "C:\Windows\system32\\taskkill.exe" /F /IM CiscoCollabHost.exe /T | C:\Windows\SysWOW64\taskkill.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2364 | C:\Windows\syswow64\MsiExec.exe -Embedding F0167E1D954F3578A795B9BABA4AFE8C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.22000.653 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3780 | msiexec.exe /i "C:\Users\admin\AppData\Local\Temp\bea0f3b5-cccb-4587-986f-ceda2b1b6d05.msi" /quiet /norestart AUTOSTART_WITH_WINDOWS=false | C:\Windows\SysWOW64\msiexec.exe | — | webex (1).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.22000.653 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4800 | C:\Windows\System32\MsiExec.exe -Embedding B6BCF4E347D6A5077C2383474CED35EA | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 152
Read events
15 139
Write events
4
Delete events
9
Modification events
| (PID) Process: | (2192) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-166304369-59083888-3082702900-1001\Software\Cisco Spark Native |
| Operation: | write | Name: | installed |
Value: 1 | |||
| (PID) Process: | (2192) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-166304369-59083888-3082702900-1001_Classes\Local Settings\MuiCache\48\52C64B7E |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2192) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-166304369-59083888-3082702900-1001_Classes\Local Settings\MuiCache\48 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3780) msiexec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 51 | |||
| (PID) Process: | (2192) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | delete value | Name: | C:\Config.Msi\e34d9.rbs |
Value: 31077051 | |||
| (PID) Process: | (2192) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2192) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2192) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-166304369-59083888-3082702900-1001\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2192) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-166304369-59083888-3082702900-1001\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | SessionHash |
Value: 8090C009AE47079820E43DFE94FB561AB51CA2C302C3C4FD1F91D91C56F48A29 | |||
| (PID) Process: | (2192) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-166304369-59083888-3082702900-1001\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Owner |
Value: 90080000C21F0374BB32DA01 | |||
Executable files
6
Suspicious files
22
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1728 | webex (1).exe | C:\Users\admin\AppData\Local\Temp\bea0f3b5-cccb-4587-986f-ceda2b1b6d05.msi | executable | |
MD5:83FC39D652D6685E7B59579A94C1BB48 | SHA256:F6850CFA06F6FF9FDD8AFA27CF2BACF45C61A43680400A73B4190E60DACA898C | |||
| 2192 | msiexec.exe | C:\Windows\Installer\MSI36FB.tmp | executable | |
MD5:A3AE5D86ECF38DB9427359EA37A5F646 | SHA256:C8D190D5BE1EFD2D52F72A72AE9DFA3940AB3FACEB626405959349654FE18B74 | |||
| 2192 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:2C81CA4076123BEB680E5512B4A04557 | SHA256:9BA2CA728317B49ABEAD596FC4B181B6B55816819CF0E5878DE2CE1D9FEF1011 | |||
| 2192 | msiexec.exe | C:\Windows\Installer\e34d7.msi | executable | |
MD5:83FC39D652D6685E7B59579A94C1BB48 | SHA256:F6850CFA06F6FF9FDD8AFA27CF2BACF45C61A43680400A73B4190E60DACA898C | |||
| 2192 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:643D03726EEB8FAF1EA28E87E7B0045F | SHA256:3E884E5C1A8BA93F204B4A1629F0659312429FAD61EFEE4B87DE6654DAE5EB8E | |||
| 2192 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8EC9B1D0ABBD7F98B401D425828828CE_18042D51F9AD69DAFE253165733E264E | binary | |
MD5:0912F76BB73C69CBD130B0CB9BB110C6 | SHA256:2A4848913BC5066363663CE25642A54380E46125C22B13CB59D65B324D31312B | |||
| 2192 | msiexec.exe | C:\Windows\Installer\e34da.msi | executable | |
MD5:83FC39D652D6685E7B59579A94C1BB48 | SHA256:F6850CFA06F6FF9FDD8AFA27CF2BACF45C61A43680400A73B4190E60DACA898C | |||
| 2192 | msiexec.exe | C:\Users\admin\AppData\Roaming\Microsoft\Installer\{5769D3D0-47C7-5BD4-A88C-01365D7507C6}\ProductIcon.ico | image | |
MD5:0A9BF46691CD4DC4D8ADB773ED79076D | SHA256:24D538CEC1A46EFF37DEBC694E13B29C9D7B60FB1BC3B1E0BD704DA1927C46AC | |||
| 2192 | msiexec.exe | C:\Windows\TEMP\~DFFCD16F03235EB26B.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 2192 | msiexec.exe | C:\Users\admin\Desktop\Webex.lnk | binary | |
MD5:61912AD71A91C0956C8B76CDBEC3C407 | SHA256:7953C2C7810D36A1B45811245D9B640177C0958F2C79C4F3CD5D10844FC902E8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
22
DNS requests
9
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
804 | smartscreen.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | binary | 471 b | unknown |
804 | smartscreen.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a8be6b76ed42b984 | unknown | compressed | 4.66 Kb | unknown |
2192 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | binary | 727 b | unknown |
2192 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAa0%2FGwHJUJ0q%2FupX4j4rA4%3D | unknown | binary | 727 b | unknown |
1412 | svchost.exe | GET | 200 | 2.21.20.140:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | text | 22 b | unknown |
3752 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | svchost.exe | 23.35.236.109:443 | — | AKAMAI-AS | DE | unknown |
4588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
804 | smartscreen.exe | 20.31.251.109:443 | checkappexec.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
804 | smartscreen.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1728 | webex (1).exe | 170.72.245.124:443 | client-upgrade-a.wbx2.com | — | US | unknown |
804 | smartscreen.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1732 | OfficeC2RClient.exe | 52.109.32.97:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | GB | unknown |
6108 | OfficeC2RClient.exe | 52.109.32.97:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | GB | unknown |
2864 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1728 | webex (1).exe | 143.204.98.51:443 | binaries.webex.com | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
checkappexec.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
client-upgrade-a.wbx2.com |
| unknown |
ocsp.digicert.com |
| whitelisted |
binaries.webex.com |
| whitelisted |
login.live.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
mrodevicemgr.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1412 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |