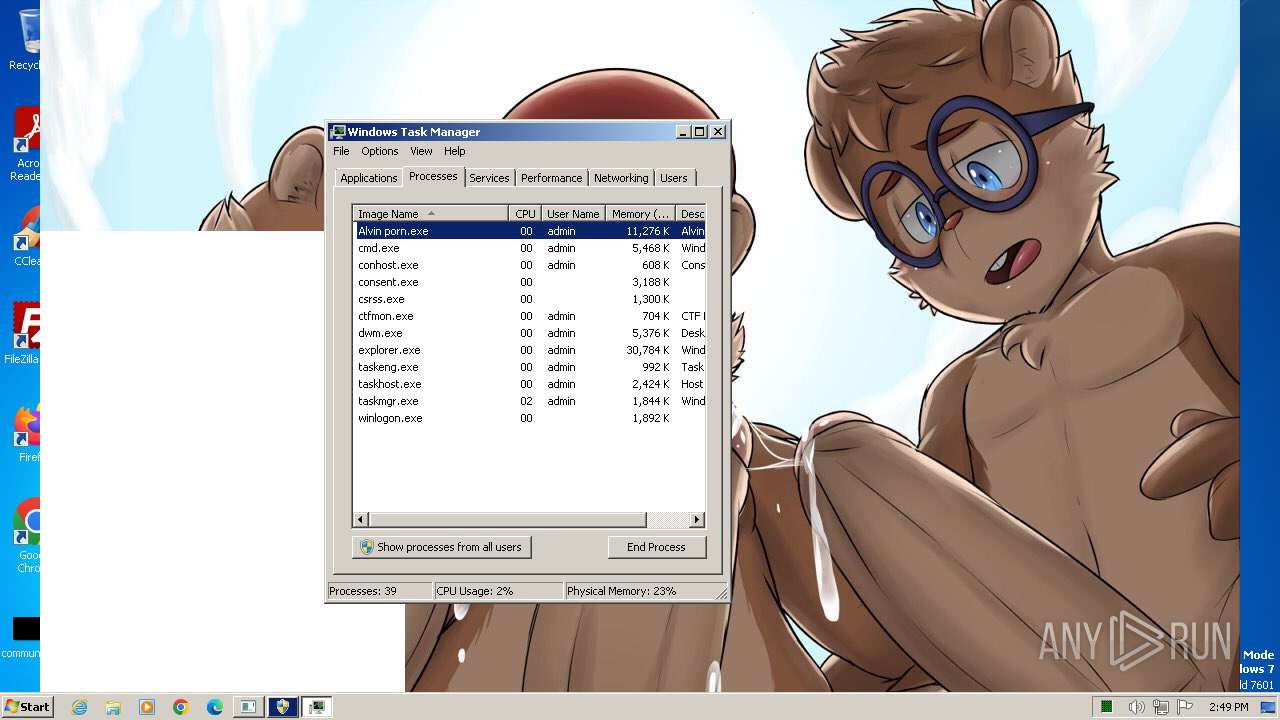
| File name: | Alvin porn.exe |
| Full analysis: | https://app.any.run/tasks/da953a96-1aab-4b21-ac1b-a61b51cd76d2 |
| Verdict: | Malicious activity |
| Analysis date: | April 22, 2024, 13:48:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 87271853FF9A649F799260D5A644B9BB |
| SHA1: | 1001BF3E56E0791D370103DC89DF294364036A29 |
| SHA256: | C8BBE86141C54FAD5A08A6259B13DA17187764CDCA56F664DA3810A186298A11 |
| SSDEEP: | 49152:cD9FFgRzuXlvg+E/E/4AQIxefpajEZ4l7afhsqFAeA3itIS3tSynT:w9FFRoC/4ATkJyYiqFAeAsBT |
MALICIOUS
Drops the executable file immediately after the start
- Alvin porn.exe (PID: 1072)
SUSPICIOUS
Reads the Internet Settings
- Alvin porn.exe (PID: 1072)
- cmd.exe (PID: 3248)
- cmd.exe (PID: 3544)
Reads security settings of Internet Explorer
- Alvin porn.exe (PID: 1072)
Starts CMD.EXE for commands execution
- Alvin porn.exe (PID: 1072)
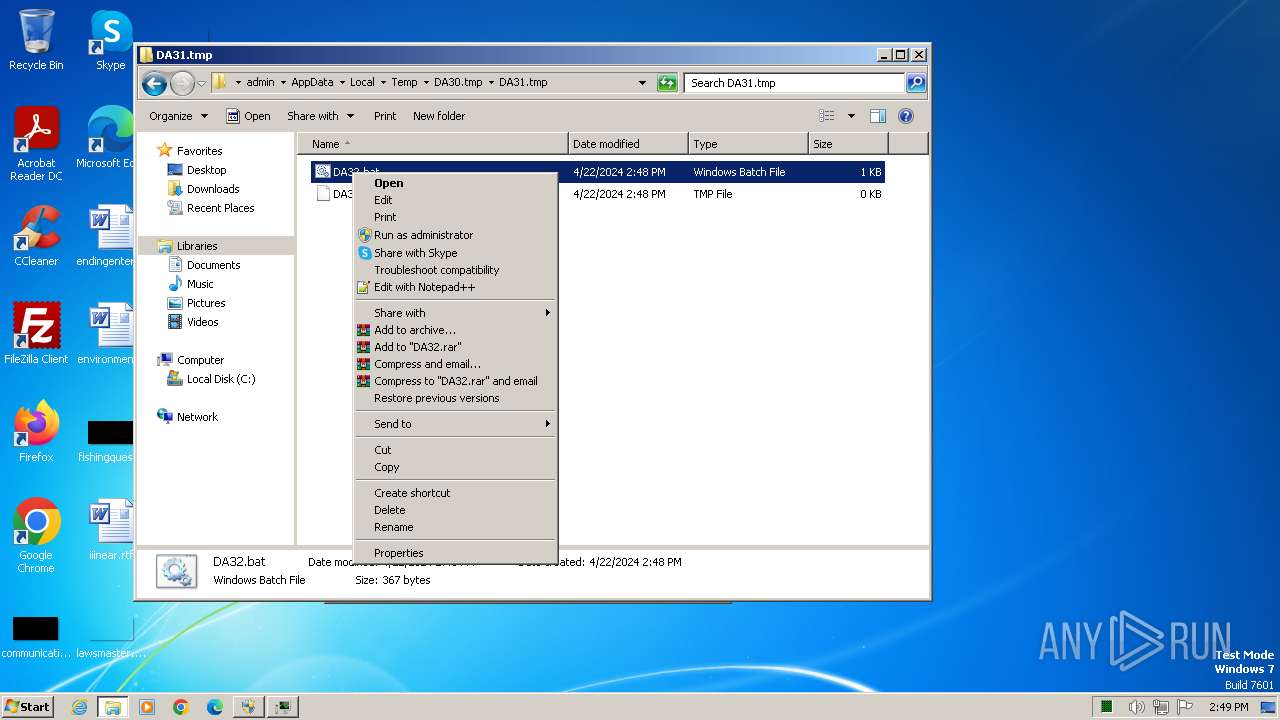
Executing commands from a ".bat" file
- Alvin porn.exe (PID: 1072)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 3544)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 3544)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 3544)
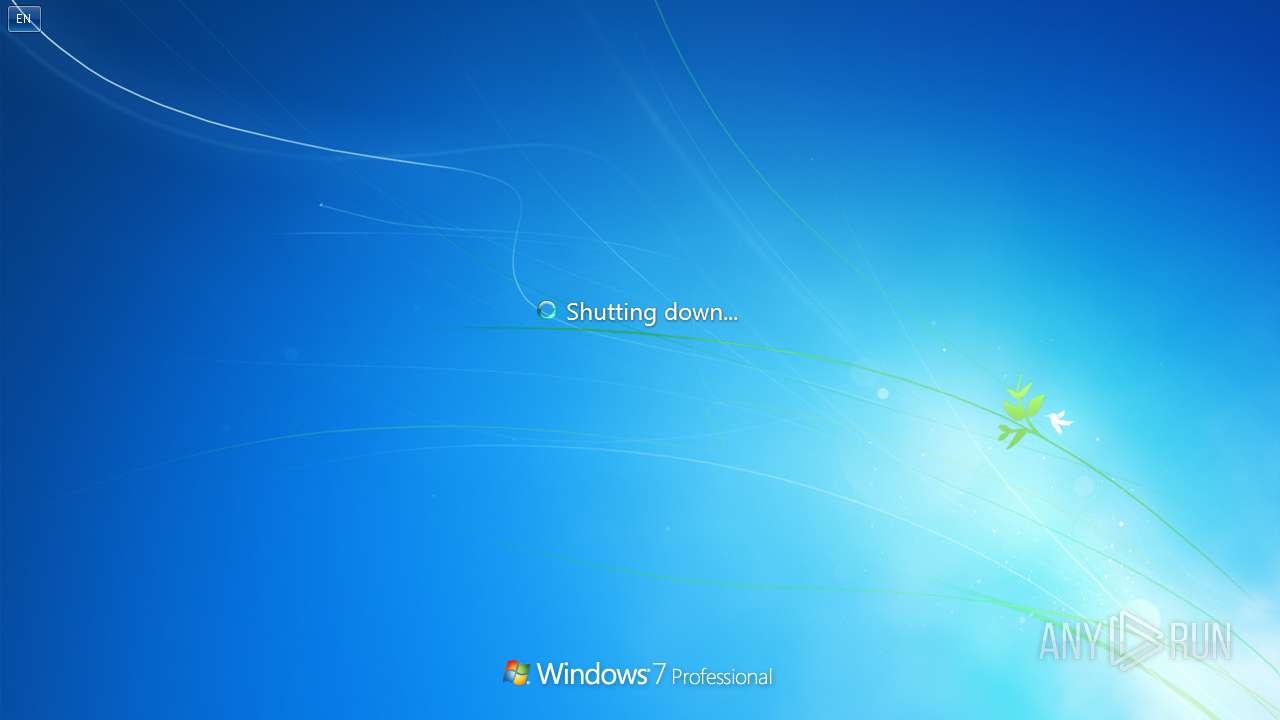
The system shut down or reboot
- cmd.exe (PID: 3544)
INFO
Checks supported languages
- Alvin porn.exe (PID: 1072)
Reads the computer name
- Alvin porn.exe (PID: 1072)
Create files in a temporary directory
- Alvin porn.exe (PID: 1072)
Manual execution by a user
- taskmgr.exe (PID: 3844)
- explorer.exe (PID: 2528)
- cmd.exe (PID: 3544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (61.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.6) |
| .exe | | | Win32 Executable (generic) (10) |
| .exe | | | Win16/32 Executable Delphi generic (4.6) |
| .exe | | | Generic Win/DOS Executable (4.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:02:01 20:18:00+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 67584 |
| InitializedDataSize: | 164352 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3db588 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
57
Monitored processes
13
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1072 | "C:\Users\admin\Desktop\Alvin porn.exe" | C:\Users\admin\Desktop\Alvin porn.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
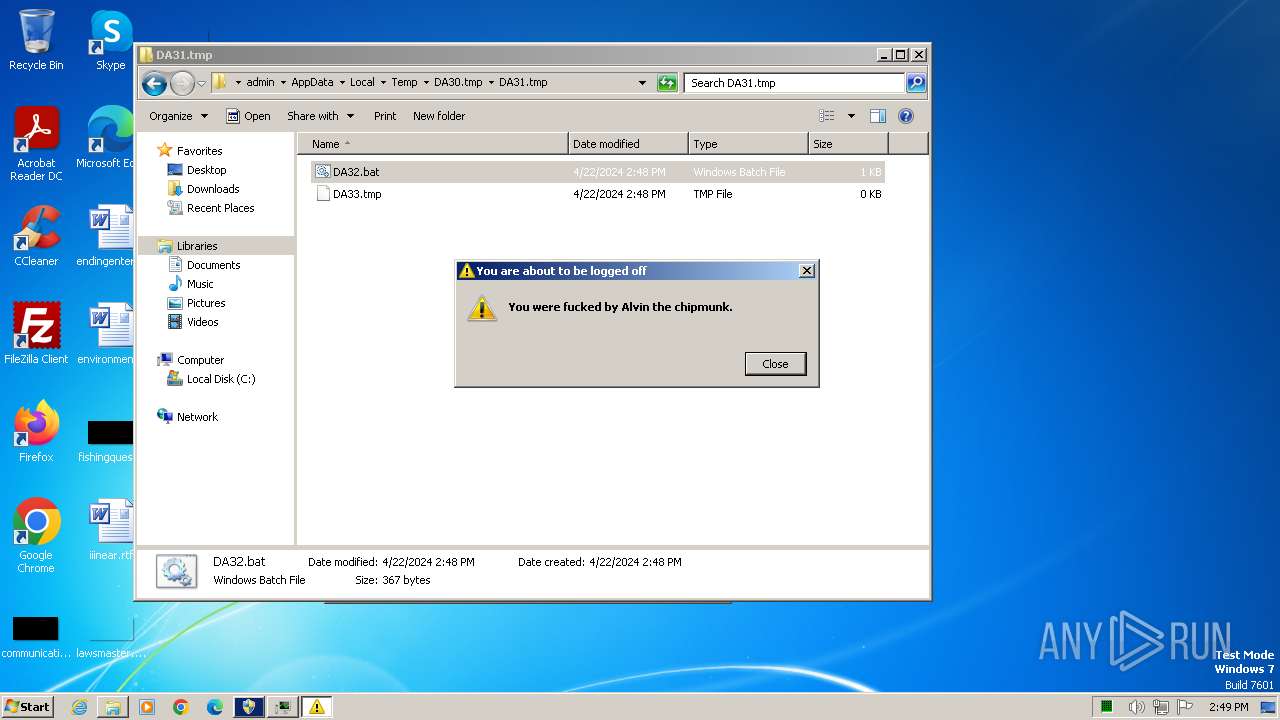
| 1092 | shutdown /s /t 3 /c "You were fucked by Alvin the chipmunk." | C:\Windows\System32\shutdown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1168 | cacls "Z:/bootmgr" /e /p {admin}:F | C:\Windows\System32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Control ACLs Program Exit code: 1332 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
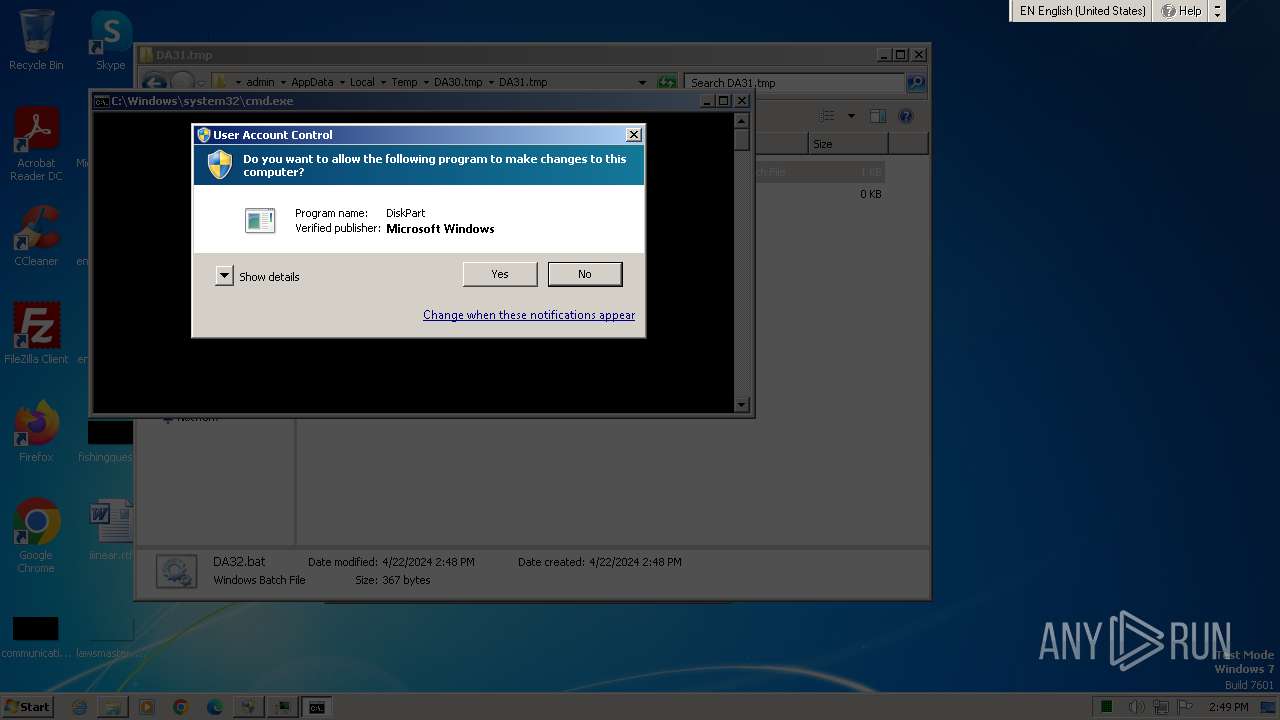
| 1864 | "C:\Windows\system32\diskpart.exe" /s tmp.txt | C:\Windows\System32\diskpart.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DiskPart Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2380 | "C:\Windows\system32\diskpart.exe" /s tmp.txt | C:\Windows\System32\diskpart.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DiskPart Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2528 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2644 | attrib "Z:/bootmgr" -s -h | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2772 | diskpart /s tmp.txt | C:\Windows\System32\diskpart.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DiskPart Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2812 | diskpart /s tmp.txt | C:\Windows\System32\diskpart.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DiskPart Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3116 | takeown /F bootmgr /A | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Takes ownership of a file Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 668
Read events
1 643
Write events
25
Delete events
0
Modification events
| (PID) Process: | (1072) Alvin porn.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1072) Alvin porn.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1072) Alvin porn.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1072) Alvin porn.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3248) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3248) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3248) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3248) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3544) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3544) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
0
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3248 | cmd.exe | C:\Users\admin\tmp.txt | text | |
MD5:EA0A4193FC6D68A4F5B90C69252F5315 | SHA256:9CD8B6417F3D4FF9F19EC3FE9523D4F6CE11697A0CDFD5B2DD7689FC0198B8FE | |||
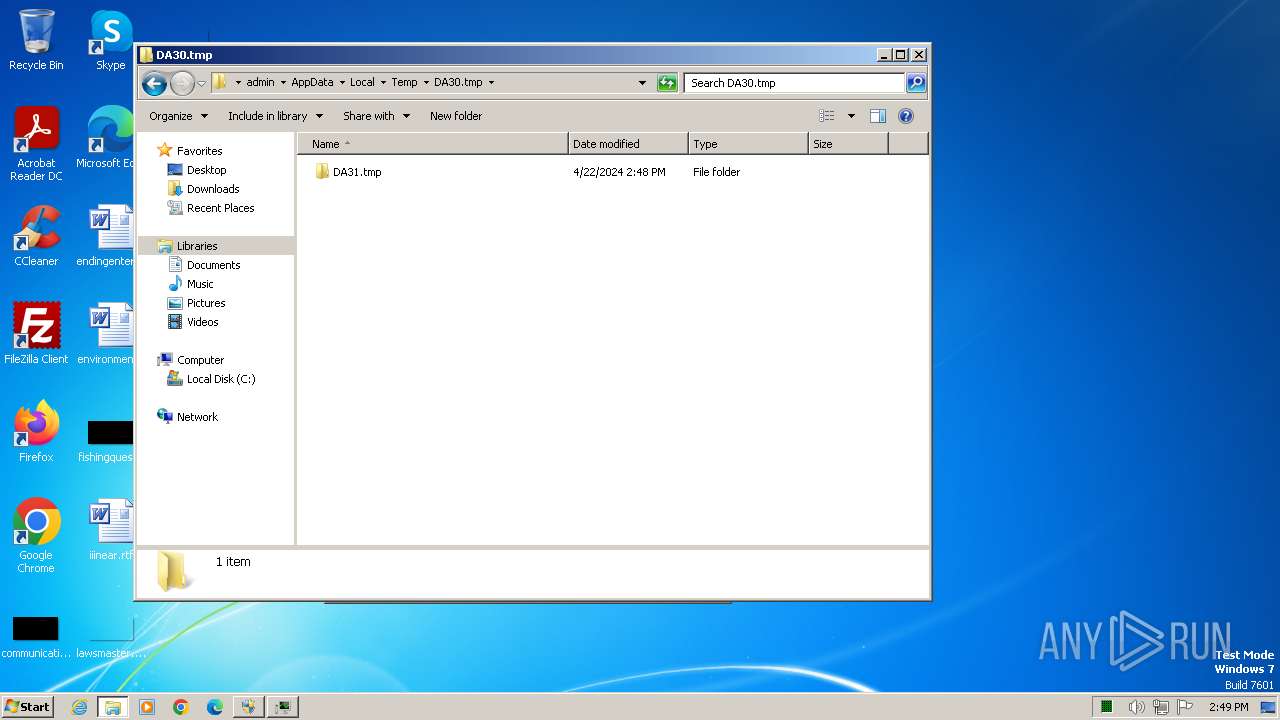
| 1072 | Alvin porn.exe | C:\Users\admin\AppData\Local\Temp\DA30.tmp\DA31.tmp\DA32.bat | text | |
MD5:5DF39A1A982A03BDCC0568B0671BA1BD | SHA256:FD7242AF792029B51C6C05A873A78ACB1A3EFBB4DFA854B24CEA90A22E5C2D8B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |