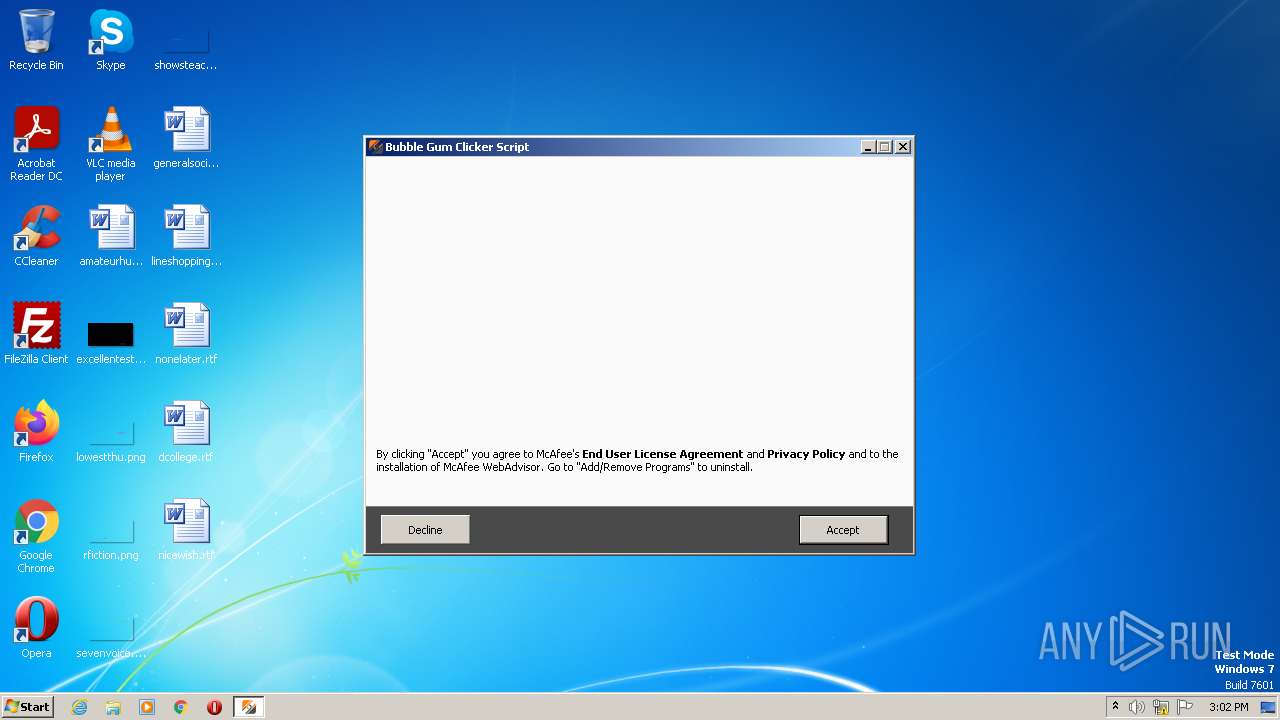
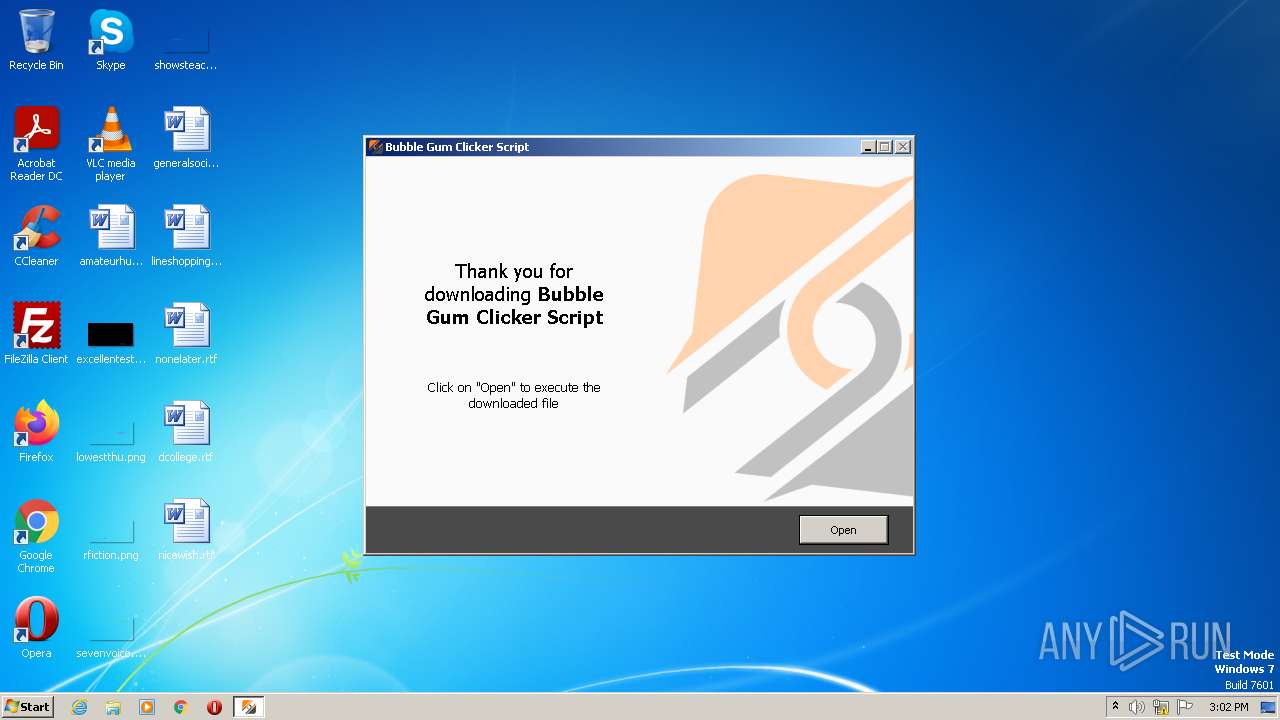
| File name: | Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.exe |
| Full analysis: | https://app.any.run/tasks/fcf2f35d-8b2d-4617-ad6b-4a088a1b2d21 |
| Verdict: | Malicious activity |
| Analysis date: | April 01, 2023, 14:01:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | B377549730870F40AACBB48CBC056936 |
| SHA1: | 6A16234B348AED99C57C3850AA31022F20356259 |
| SHA256: | C89A8D0A31B2002538195EF3E604A6F1CC9570F9B4749CB9AAD94D8F7A8369D6 |
| SSDEEP: | 49152:Iqe3f6aSzD7+H98AHaCfu6FNHCL+WuTmuKwED:dSinD7E9vBuQHCK5NKXD |
MALICIOUS
Application was dropped or rewritten from another process
- saBSI.exe (PID: 2560)
SUSPICIOUS
Executable content was dropped or overwritten
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.exe (PID: 2668)
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.exe (PID: 3676)
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp (PID: 3704)
Reads the Windows owner or organization settings
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp (PID: 3704)
Reads settings of System Certificates
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp (PID: 3704)
- saBSI.exe (PID: 2560)
Reads the Internet Settings
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp (PID: 3704)
- saBSI.exe (PID: 2560)
Adds/modifies Windows certificates
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp (PID: 3704)
Checks Windows Trust Settings
- saBSI.exe (PID: 2560)
Reads security settings of Internet Explorer
- saBSI.exe (PID: 2560)
INFO
Checks supported languages
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.exe (PID: 2668)
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp (PID: 920)
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp (PID: 3704)
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.exe (PID: 3676)
- saBSI.exe (PID: 2560)
Reads the computer name
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp (PID: 920)
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp (PID: 3704)
- saBSI.exe (PID: 2560)
Create files in a temporary directory
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.exe (PID: 2668)
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.exe (PID: 3676)
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp (PID: 3704)
- iexplore.exe (PID: 3380)
The process checks LSA protection
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp (PID: 920)
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp (PID: 3704)
- saBSI.exe (PID: 2560)
Application was dropped or rewritten from another process
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp (PID: 920)
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp (PID: 3704)
Reads the machine GUID from the registry
- Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp (PID: 3704)
- saBSI.exe (PID: 2560)
Creates files in the program directory
- saBSI.exe (PID: 2560)
Application launched itself
- iexplore.exe (PID: 3380)
Manual execution by a user
- taskmgr.exe (PID: 1748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| ProductVersion: | 2.0.0.13 |
|---|---|
| ProductName: | Linkvertise GmbH & Co. KG |
| OriginalFileName: | |
| LegalCopyright: | © Linkvertise GmbH & Co. KG |
| FileVersion: | 2.0.0.13 |
| FileDescription: | Linkvertise GmbH & Co. KG |
| CompanyName: | |
| Comments: | This installation was built with Inno Setup. |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 2.0.0.13 |
| FileVersionNumber: | 2.0.0.13 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 6.1 |
| ImageVersion: | 6 |
| OSVersion: | 6.1 |
| EntryPoint: | 0xb5eec |
| UninitializedDataSize: | - |
| InitializedDataSize: | 157184 |
| CodeSize: | 741376 |
| LinkerVersion: | 2.25 |
| PEType: | PE32 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| TimeStamp: | 2020:11:15 09:48:30+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 15-Nov-2020 09:48:30 |
| Detected languages: |
|
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | - |
| FileDescription: | Linkvertise GmbH & Co. KG |
| FileVersion: | 2.0.0.13 |
| LegalCopyright: | © Linkvertise GmbH & Co. KG |
| OriginalFileName: | - |
| ProductName: | Linkvertise GmbH & Co. KG |
| ProductVersion: | 2.0.0.13 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 10 |
| Time date stamp: | 15-Nov-2020 09:48:30 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000B361C | 0x000B3800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.35606 |
.itext | 0x000B5000 | 0x00001688 | 0x00001800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.97275 |
.data | 0x000B7000 | 0x000037A4 | 0x00003800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.0444 |
.bss | 0x000BB000 | 0x00006DE8 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x000C2000 | 0x00000F36 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.8987 |
.didata | 0x000C3000 | 0x000001A4 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.75636 |
.edata | 0x000C4000 | 0x0000009A | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.87222 |
.tls | 0x000C5000 | 0x00000018 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x000C6000 | 0x0000005D | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.38389 |
.rsrc | 0x000C7000 | 0x000216F0 | 0x00021800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.61632 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.18295 | 1830 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 2.80552 | 67624 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 3.40448 | 16936 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 3.76613 | 9640 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 4.12824 | 4264 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 4.64443 | 1128 | Latin 1 / Western European | English - United States | RT_ICON |
4086 | 3.16547 | 864 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4087 | 3.40938 | 608 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4088 | 3.31153 | 1116 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4089 | 3.33977 | 1036 | Latin 1 / Western European | UNKNOWN | RT_STRING |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
kernel32.dll (delay-loaded) |
netapi32.dll |
oleaut32.dll |
user32.dll |
version.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
dbkFCallWrapperAddr | 1 | 0x000BE63C |
__dbk_fcall_wrapper | 2 | 0x0000D0A0 |
TMethodImplementationIntercept | 3 | 0x00054060 |
Total processes
47
Monitored processes
8
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | "C:\Users\admin\AppData\Local\Temp\is-3UJJL.tmp\Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp" /SL5="$8012E,1785071,899584,C:\Users\admin\AppData\Local\Temp\Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.exe" | C:\Users\admin\AppData\Local\Temp\is-3UJJL.tmp\Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | — | Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1748 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2560 | "C:\Users\admin\AppData\Local\Temp\is-EJDIF.tmp\prod0_extract\saBSI.exe" /affid 91215 PaidDistribution=true | C:\Users\admin\AppData\Local\Temp\is-EJDIF.tmp\prod0_extract\saBSI.exe | Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | ||||||||||||
User: admin Company: McAfee, LLC Integrity Level: HIGH Description: McAfee WebAdvisor(bootstrap installer) Exit code: 4294967295 Version: 4,1,1,663 Modules
| |||||||||||||||
| 2668 | "C:\Users\admin\AppData\Local\Temp\Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.exe" | C:\Users\admin\AppData\Local\Temp\Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Linkvertise GmbH & Co. KG Exit code: 0 Version: 2.0.0.13 Modules
| |||||||||||||||
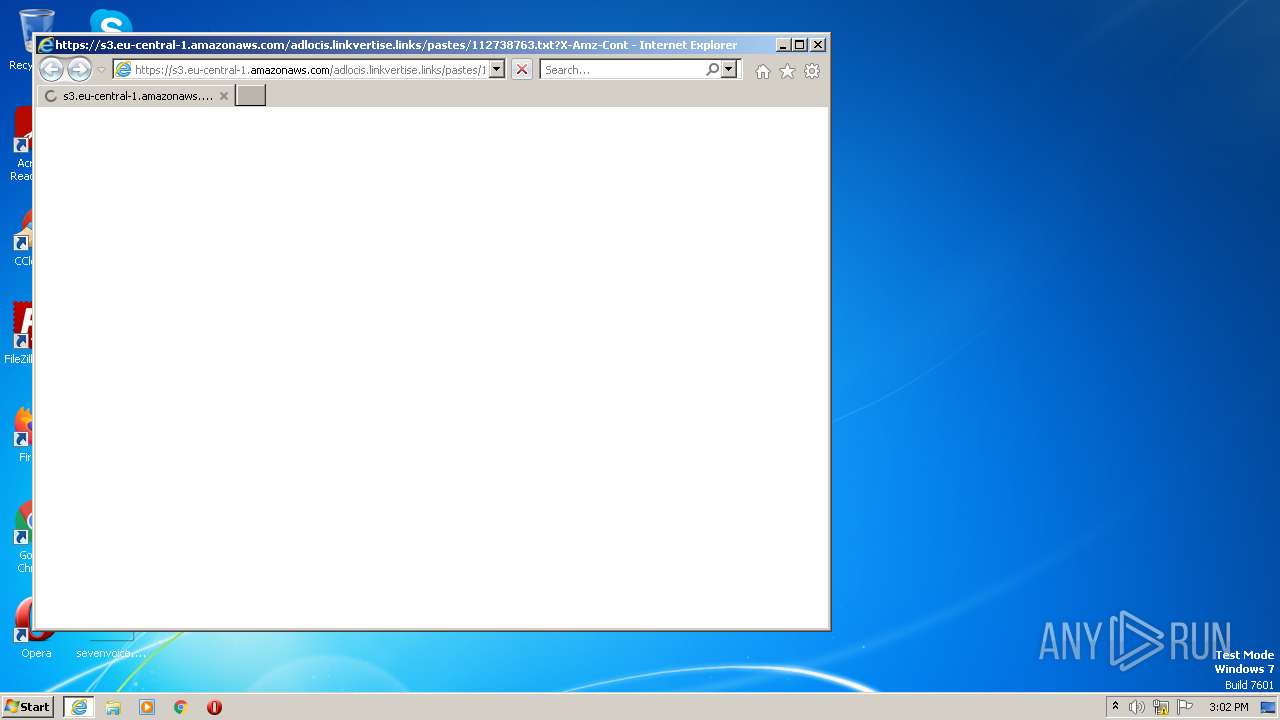
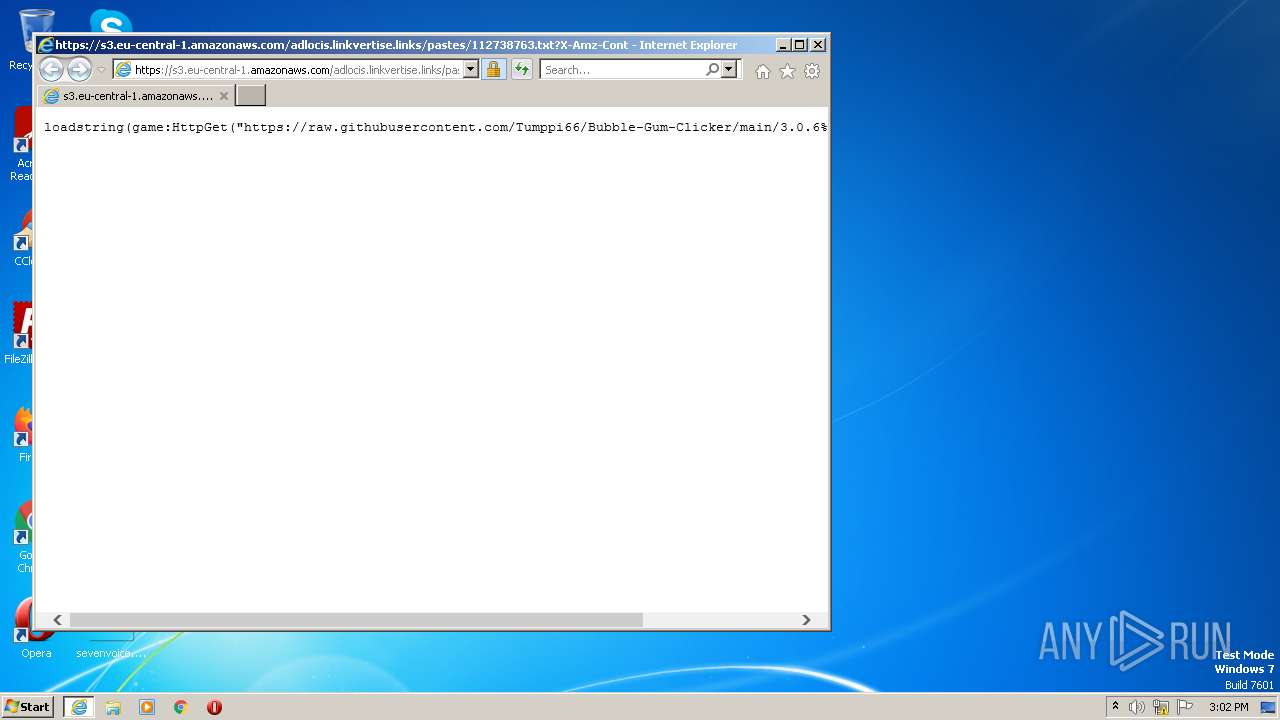
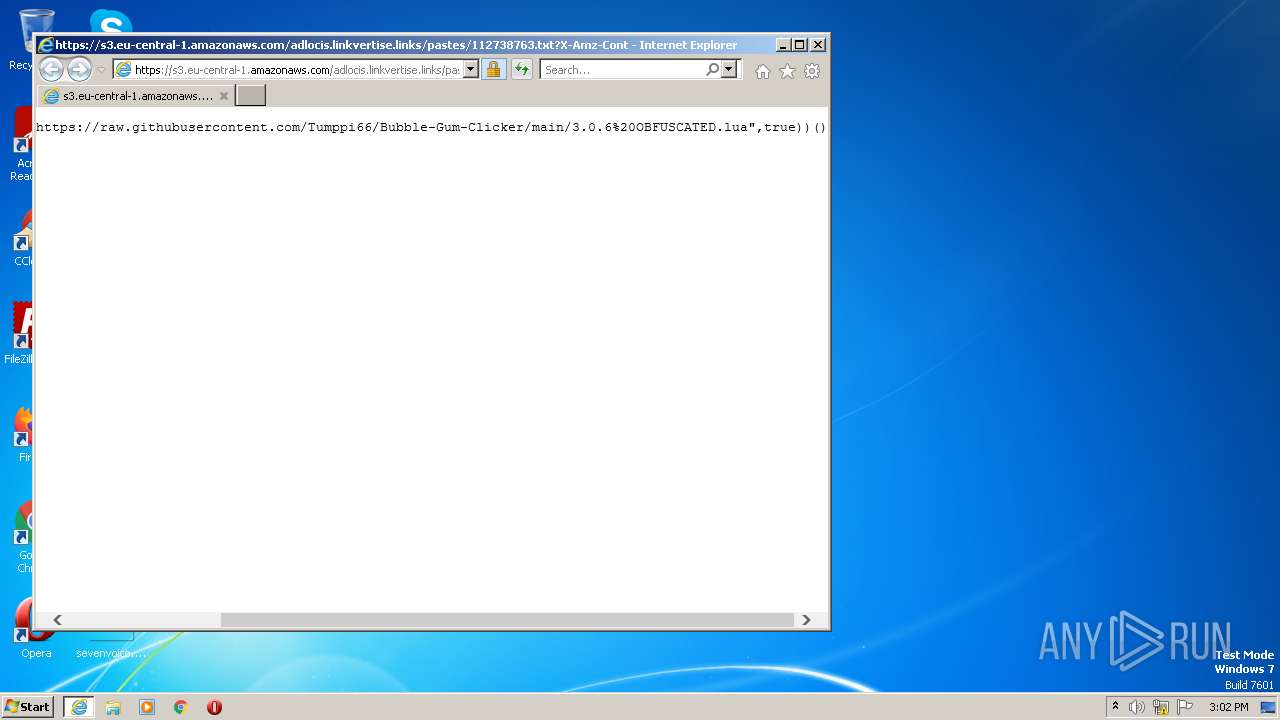
| 3380 | "C:\Program Files\Internet Explorer\iexplore.exe" https://s3.eu-central-1.amazonaws.com/adlocis.linkvertise.links/pastes/112738763.txt?X-Amz-Content-Sha256=UNSIGNED-PAYLOAD&X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIA6L5L3NKTBHJ3YVHU/20230401/eu-central-1/s3/aws4_request&X-Amz-Date=20230401T135640Z&X-Amz-SignedHeaders=host&X-Amz-Expires=432000&X-Amz-Signature=7b6baa1bdbd6c3d6eb0db6faa67179824e07ce61505fc952d67baf132668c735 | C:\Program Files\Internet Explorer\iexplore.exe | Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3676 | "C:\Users\admin\AppData\Local\Temp\Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.exe" /SPAWNWND=$80144 /NOTIFYWND=$8012E | C:\Users\admin\AppData\Local\Temp\Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.exe | Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Linkvertise GmbH & Co. KG Exit code: 0 Version: 2.0.0.13 Modules
| |||||||||||||||
| 3704 | "C:\Users\admin\AppData\Local\Temp\is-6R5D4.tmp\Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp" /SL5="$70136,1785071,899584,C:\Users\admin\AppData\Local\Temp\Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.exe" /SPAWNWND=$80144 /NOTIFYWND=$8012E | C:\Users\admin\AppData\Local\Temp\is-6R5D4.tmp\Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 4088 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3380 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
45 360
Read events
45 022
Write events
328
Delete events
10
Modification events
| (PID) Process: | (3704) Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3704) Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3704) Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3704) Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3704) Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3704) Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\Component Categories\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}\Enum |
| Operation: | write | Name: | Implementing |
Value: 1C00000001000000E7070400060001000E0002000D00F301010000001E768127E028094199FEB9D127C57AFE | |||
| (PID) Process: | (2560) saBSI.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2560) saBSI.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\DF3C24F9BFD666761B268073FE06D1CC8D4F82A4 |
| Operation: | write | Name: | Blob |
Value: 090000000100000034000000303206082B0601050507030206082B0601050507030306082B0601050507030406082B0601050507030106082B0601050507030819000000010000001000000014C3BD3549EE225AECE13734AD8CA0B80B000000010000003000000044006900670069004300650072007400200047006C006F00620061006C00200052006F006F0074002000470032000000620000000100000020000000CB3CCBB76031E5E0138F8DD39A23F9DE47FFC35E43C1144CEA27D46A5AB1CB5F1400000001000000140000004E2254201895E6E36EE60FFAFAB912ED06178F391D00000001000000100000007DC30BC974695560A2F0090A6545556C030000000100000014000000DF3C24F9BFD666761B268073FE06D1CC8D4F82A40F00000001000000200000004B4EB4B074298B828B5C003095A10B4523FB951C0C88348B09C53E5BABA408A3530000000100000040000000303E301F06096086480186FD6C020130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C02000000001000000920300003082038E30820276A0030201020210033AF1E6A711A9A0BB2864B11D09FAE5300D06092A864886F70D01010B05003061310B300906035504061302555331153013060355040A130C446967694365727420496E6331193017060355040B13107777772E64696769636572742E636F6D3120301E06035504031317446967694365727420476C6F62616C20526F6F74204732301E170D3133303830313132303030305A170D3338303131353132303030305A3061310B300906035504061302555331153013060355040A130C446967694365727420496E6331193017060355040B13107777772E64696769636572742E636F6D3120301E06035504031317446967694365727420476C6F62616C20526F6F7420473230820122300D06092A864886F70D01010105000382010F003082010A0282010100BB37CD34DC7B6BC9B26890AD4A75FF46BA210A088DF51954C9FB88DBF3AEF23A89913C7AE6AB061A6BCFAC2DE85E092444BA629A7ED6A3A87EE054752005AC50B79C631A6C30DCDA1F19B1D71EDEFDD7E0CB948337AEEC1F434EDD7B2CD2BD2EA52FE4A9B8AD3AD499A4B625E99B6B00609260FF4F214918F76790AB61069C8FF2BAE9B4E992326BB5F357E85D1BCD8C1DAB95049549F3352D96E3496DDD77E3FB494BB4AC5507A98F95B3B423BB4C6D45F0F6A9B29530B4FD4C558C274A57147C829DCD7392D3164A060C8C50D18F1E09BE17A1E621CAFD83E510BC83A50AC46728F67314143D4676C387148921344DAF0F450CA649A1BABB9CC5B1338329850203010001A3423040300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020186301D0603551D0E041604144E2254201895E6E36EE60FFAFAB912ED06178F39300D06092A864886F70D01010B05000382010100606728946F0E4863EB31DDEA6718D5897D3CC58B4A7FE9BEDB2B17DFB05F73772A3213398167428423F2456735EC88BFF88FB0610C34A4AE204C84C6DBF835E176D9DFA642BBC74408867F3674245ADA6C0D145935BDF249DDB61FC9B30D472A3D992FBB5CBBB5D420E1995F534615DB689BF0F330D53E31E28D849EE38ADADA963E3513A55FF0F970507047411157194EC08FAE06C49513172F1B259F75F2B18E99A16F13B14171FE882AC84F102055D7F31445E5E044F4EA879532930EFE5346FA2C9DFF8B22B94BD90945A4DEA4B89A58DD1B7D529F8E59438881A49E26D56FADDD0DC6377DED03921BE5775F76EE3C8DC45D565BA2D9666EB33537E532B6 | |||
| (PID) Process: | (2560) saBSI.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\DF3C24F9BFD666761B268073FE06D1CC8D4F82A4 |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000E4A68AC854AC5242460AFD72481B2A44530000000100000040000000303E301F06096086480186FD6C020130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C00F00000001000000200000004B4EB4B074298B828B5C003095A10B4523FB951C0C88348B09C53E5BABA408A3030000000100000014000000DF3C24F9BFD666761B268073FE06D1CC8D4F82A41D00000001000000100000007DC30BC974695560A2F0090A6545556C1400000001000000140000004E2254201895E6E36EE60FFAFAB912ED06178F39620000000100000020000000CB3CCBB76031E5E0138F8DD39A23F9DE47FFC35E43C1144CEA27D46A5AB1CB5F0B000000010000003000000044006900670069004300650072007400200047006C006F00620061006C00200052006F006F007400200047003200000019000000010000001000000014C3BD3549EE225AECE13734AD8CA0B8090000000100000034000000303206082B0601050507030206082B0601050507030306082B0601050507030406082B0601050507030106082B060105050703082000000001000000920300003082038E30820276A0030201020210033AF1E6A711A9A0BB2864B11D09FAE5300D06092A864886F70D01010B05003061310B300906035504061302555331153013060355040A130C446967694365727420496E6331193017060355040B13107777772E64696769636572742E636F6D3120301E06035504031317446967694365727420476C6F62616C20526F6F74204732301E170D3133303830313132303030305A170D3338303131353132303030305A3061310B300906035504061302555331153013060355040A130C446967694365727420496E6331193017060355040B13107777772E64696769636572742E636F6D3120301E06035504031317446967694365727420476C6F62616C20526F6F7420473230820122300D06092A864886F70D01010105000382010F003082010A0282010100BB37CD34DC7B6BC9B26890AD4A75FF46BA210A088DF51954C9FB88DBF3AEF23A89913C7AE6AB061A6BCFAC2DE85E092444BA629A7ED6A3A87EE054752005AC50B79C631A6C30DCDA1F19B1D71EDEFDD7E0CB948337AEEC1F434EDD7B2CD2BD2EA52FE4A9B8AD3AD499A4B625E99B6B00609260FF4F214918F76790AB61069C8FF2BAE9B4E992326BB5F357E85D1BCD8C1DAB95049549F3352D96E3496DDD77E3FB494BB4AC5507A98F95B3B423BB4C6D45F0F6A9B29530B4FD4C558C274A57147C829DCD7392D3164A060C8C50D18F1E09BE17A1E621CAFD83E510BC83A50AC46728F67314143D4676C387148921344DAF0F450CA649A1BABB9CC5B1338329850203010001A3423040300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020186301D0603551D0E041604144E2254201895E6E36EE60FFAFAB912ED06178F39300D06092A864886F70D01010B05000382010100606728946F0E4863EB31DDEA6718D5897D3CC58B4A7FE9BEDB2B17DFB05F73772A3213398167428423F2456735EC88BFF88FB0610C34A4AE204C84C6DBF835E176D9DFA642BBC74408867F3674245ADA6C0D145935BDF249DDB61FC9B30D472A3D992FBB5CBBB5D420E1995F534615DB689BF0F330D53E31E28D849EE38ADADA963E3513A55FF0F970507047411157194EC08FAE06C49513172F1B259F75F2B18E99A16F13B14171FE882AC84F102055D7F31445E5E044F4EA879532930EFE5346FA2C9DFF8B22B94BD90945A4DEA4B89A58DD1B7D529F8E59438881A49E26D56FADDD0DC6377DED03921BE5775F76EE3C8DC45D565BA2D9666EB33537E532B6 | |||
| (PID) Process: | (3704) Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
Executable files
10
Suspicious files
34
Text files
26
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2560 | saBSI.exe | C:\ProgramData\McAfee\WebAdvisor\saBSI.exe\log_00000057003F001D0006.txt | text | |
MD5:— | SHA256:— | |||
| 4088 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3704 | Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | C:\Users\admin\AppData\Local\Temp\is-EJDIF.tmp\botva2.dll | executable | |
MD5:67965A5957A61867D661F05AE1F4773E | SHA256:450B9B0BA25BF068AFBC2B23D252585A19E282939BF38326384EA9112DFD0105 | |||
| 4088 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | der | |
MD5:— | SHA256:— | |||
| 4088 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:— | SHA256:— | |||
| 3704 | Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | C:\Users\admin\AppData\Local\Temp\is-EJDIF.tmp\is-I9U98.tmp | image | |
MD5:DB6C259CD7B58F2F7A3CCA0C38834D0E | SHA256:494169CDD9C79EB4668378F770BFA55D4B140F23A682FF424441427DFAB0CED2 | |||
| 3704 | Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | C:\Users\admin\AppData\Local\Temp\is-EJDIF.tmp\prod0.zip | compressed | |
MD5:D6BE5546BBCE27020B742C5966838158 | SHA256:49082EF6E5B8CEAC180171309611EAC88DAC603684CDE04E3725945A6722BCE2 | |||
| 3704 | Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | C:\Users\admin\AppData\Local\Temp\is-EJDIF.tmp\finish.png | image | |
MD5:7AFAF9E0E99FD80FA1023A77524F5587 | SHA256:760B70612BB9BD967C2D15A5133A50CCCE8C0BD46A6464D76875298DCC45DEA0 | |||
| 3704 | Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | C:\Users\admin\AppData\Local\Temp\is-EJDIF.tmp\WebAdvisor.png | image | |
MD5:DB6C259CD7B58F2F7A3CCA0C38834D0E | SHA256:494169CDD9C79EB4668378F770BFA55D4B140F23A682FF424441427DFAB0CED2 | |||
| 3704 | Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | C:\Users\admin\AppData\Local\Temp\is-EJDIF.tmp\prod0 | compressed | |
MD5:D6BE5546BBCE27020B742C5966838158 | SHA256:49082EF6E5B8CEAC180171309611EAC88DAC603684CDE04E3725945A6722BCE2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
27
DNS requests
19
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3380 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
3380 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
4088 | iexplore.exe | GET | 200 | 52.222.250.112:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
4088 | iexplore.exe | GET | 200 | 18.66.121.98:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEAv6i6HBOhwEYEe42RhZroE%3D | US | der | 471 b | whitelisted |
4088 | iexplore.exe | GET | 200 | 52.222.250.185:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
4088 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6af7c745bf1c6015 | US | compressed | 4.70 Kb | whitelisted |
4088 | iexplore.exe | GET | 200 | 108.138.2.195:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
4088 | iexplore.exe | GET | 200 | 23.216.77.69:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3a1f345710d6ae33 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3704 | Bubble Gum Clicker Script - Linkvertise Downloader_Mz-8kN1.tmp | 18.66.107.23:443 | d17kz3i6hbr7d3.cloudfront.net | AMAZON-02 | US | unknown |
— | — | 104.208.16.0:443 | cu1pehnswad01.servicebus.windows.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2560 | saBSI.exe | 44.237.137.106:443 | apis.mosaic.analytics.awscommon.mcafee.com | AMAZON-02 | US | unknown |
2560 | saBSI.exe | 23.35.236.52:443 | sadownload.mcafee.com | AKAMAI-AS | DE | suspicious |
— | — | 23.35.236.52:443 | sadownload.mcafee.com | AKAMAI-AS | DE | suspicious |
4088 | iexplore.exe | 108.138.2.195:80 | o.ss2.us | AMAZON-02 | US | unknown |
4088 | iexplore.exe | 23.216.77.69:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | suspicious |
4088 | iexplore.exe | 52.222.250.185:80 | ocsp.rootg2.amazontrust.com | AMAZON-02 | US | whitelisted |
4088 | iexplore.exe | 52.222.250.112:80 | ocsp.rootg2.amazontrust.com | AMAZON-02 | US | whitelisted |
4088 | iexplore.exe | 18.66.121.98:80 | ocsp.sca1b.amazontrust.com | AMAZON-02 | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
d17kz3i6hbr7d3.cloudfront.net |
| whitelisted |
cu1pehnswad01.servicebus.windows.net |
| whitelisted |
apis.mosaic.analytics.awscommon.mcafee.com |
| unknown |
sadownload.mcafee.com |
| whitelisted |
s3.eu-central-1.amazonaws.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.sca1b.amazontrust.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2560 | saBSI.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2560 | saBSI.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
Process | Message |
|---|---|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-EJDIF.tmp\prod0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-EJDIF.tmp\prod0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-EJDIF.tmp\prod0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-EJDIF.tmp\prod0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-EJDIF.tmp\prod0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-EJDIF.tmp\prod0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|